?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.Abstract
The traditional convolutional neural network (CNN) has a limited receptive field and cannot accurately identify the importance of each channel, making it difficult to solve increasingly complex network security problems. To solve these problems, this paper combines ResNeXt with the Efficient Channel Attention (ECA) module and the Contextual Transformer (COT) block to construct a model to assess network conditions. The optimal hyperparameters of the model are selected by the Harris Hawks Optimization (HHO) algorithm. The model can accurately obtain the importance of each channel to assign weights to each channel while making full use of the rich contexts among neighbour keys, effectively enhancing the convolutional neural network. Furthermore, this paper calculates the network security situation value (NSSV) of the adopted datasets based on attack impact. Lastly, experiments on two cybersecurity datasets show that the comprehensive performance of the model on the three indicators of accuracy, precision and F-scores, as well as network security situation assessment, are superior to other models.
1. Introduction
With the rapid development of technologies such as artificial intelligence, cloud computing, the Internet of Things (IoT) and 5G, network and information technology are more and more important to the economy, society, and national defense. The increasingly complex network environment requires more effective cybersecurity solutions to protect systems and networks against cyber threats. Against this background, network security situation awareness (NSSA) technology came into being, which can solve network threats more proactively, quickly, and accurately. NSSA can integrate the detection of security events by various network components and perceive network security status and risks in real-time. It is a new way to solve problems in the field of network security.
The new notion of situation awareness (SA) was put forward by Endsley (Citation1988). The concept of SA was first applied to the field of network security by Bass and Gruber (Citation1999), and the notion of SA of intrusion detection framework after multi-sensor integration was proposed by Bass (Citation2000). Because Bass put forward the notion of NSSA, more and more scholars have carried out further research on NSSA. Gong et al. (Citation2017) discussed the mission scope of NSSA, redefined the concept of NSSA, and expounded the status of research and some existing problems of NSSA. Wu and Yang (Citation2022) summarised and sorted out the meaning of NSSA. Jiang et al. (Citation2022) systematically reviewed and analysed the levels of cyber situation awareness supported by visualisation, while examining the maturity of visualisation, challenges, and practices related to cyber situation awareness visualisation in preparation for a comprehensive analysis of the current state of cyber situation awareness in an organisational context. Based on the results that highlight the important concerns in cyber situation awareness visualisations, a list of future research directions is recommended. Nazir and Han (Citation2022) introduce the origin, concept, aim and characteristics of NSSA, discuss the current application research of NSSA in the fields of security, transmission, survivability, and system assessment, and outline the future development direction of NSSA. Based on the division of multiple conceptual models, NSSA mainly has three core functions, namely, network security situation element extraction, network security situation assessment and network security situation prediction.
CNNs have excellent learning ability and adaptability, so many fields adopt CNN to solve difficult problems. In recent years, the damage caused by cyber-attacks is getting more and more serious, and the attack methods have become more and more secretive. It is very meaningful to use CNN to solve cybersecurity risks. However, due to the limited receptive field and the inability to accurately identify the importance of each channel, the traditional CNN cannot quickly and accurately find out increasingly stealthy cyber-attacks. Therefore, this paper combines ResNext (Xie et al., Citation2017) with the CoT block (Li et al., Citation2022) and the ECA module (Wang et al., Citation2020) to construct a model and use HHO (Heidari et al., Citation2019) to select the hyperparameters, which can accurately identify the importance of each channel and make full use of the rich contexts among neighbour keys. This model enables CNNs to better assess network conditions. Since our model can effectively protect various networks, our method can also be applied to fields such as artificial intelligence, cloud computing, the IoT, and 5G, where there are many potential network vulnerabilities and threats due to rapid development.
This paper is derived and expanded from our conference paper under the approval of editors (Zhao et al., Citation2022). Compared with the conference papers, this paper adds experiments on the NSL-KDD dataset and since the selected dataset has no NSSV, this paper adopts a method for calculating NSSV based on attack impact to calculate the NSSV of the two datasets. Experiments show that our model has the best fit with the actual situation value.
The contributions of this paper are summarised as follows:
This paper discusses and analyses the existing methods in the field of NSSA and has a full understanding of the research status of NSSA. Compared with existing methods, this paper innovatively combines ResNeXt with the dual attention mechanism to effectively identify the importance of each channel and expand the receptive field, enhancing the role of CNNs in the field of NSSA.
Because the datasets used in this paper have no NSSV, an NSSV calculation method based on attack impact is adopted to calculate the NSSV of the datasets.
Experiments on the NSL-KDD dataset and UNSW-NB15 dataset show that the comprehensive performance of the model on network security situation assessment is superior to other models.
2. Related work
Network security situation assessment can accurately assess the network status, prevent network security risks, and ensure the normal operation of the network. Dempster–Shafer theory was used by Zheng (Citation2020) to improve the stability of assessing network conditions. The advantage of their model is that less prior knowledge is required during training, however, more training time is consumed due to the inference process. As the security concerns raised by the increasing reliance on the Internet of Things (IoT), Akwetey and Danquah (Citation2022) assessed Cyber Situational Awareness (CSA) elements to predict cyberattacks in the power generation sector. This method has great significance in predicting network attacks.
In recent years, more and more studies have applied machine learning and deep learning to network security to solve the problems encountered in NSSA. Cao et al. (Citation2021) applied ensemble learning to cybersecurity and used Random Forest (RF) algorithm to identify attacks in the network. However, the training time and space of the model will increase with the increasing number of decision trees (DT). Ke et al. (Citation2021) proposed the I-ABC-SVM algorithm to predict the network condition and improve the model performance. They optimised the parameters of the support vector machine (SVM) through the improved artificial bee colony algorithm (I-ABC). The advantages of Ke’s method are fast training and a small memory footprint, but it also has the disadvantage of relatively low prediction accuracy. To ensure network security, Yang et al. (Citation2021) applied adversarial deep learning to NSSA. This model is more accurate for identifying network attacks and can evaluate the network conditions more comprehensively and flexibly. To improve the network environment, Samuel (Citation2021) applied the DT-ANN model to network security. The DT can extract features, and the method extracts useful features through this function and inputs these features into ANN. Zhang, Xie, et al. (Citation2019) used a deep convolutional neural network (DCNN) to enhance the accuracy of identifying attack behaviours in the network. However, the traditional CNN may lose some information in the learning process due to its limited receptive field, so the improvement in accuracy is limited. To improve the network environment, Yuan (Citation2021) applied the PSO-RBF model to the field of network security. The Radial Basis Function (RBF) neural network is optimised by particle swarm optimisation (PSO) in the field of network security. Zhang, Zhang, et al. (Citation2019) applied an improved CNN with depthwise separable convolutions to the NSSA domain. The depthwise separable convolutions can convert traditional convolutions into several smaller convolutions to reduce the number of parameters. However, Since the model has only a few convolutional layers, it is difficult to obtain comprehensive feature information. A model combining the features of a bidirectional gate recurrent unit (BiGRU), the attention mechanism, and a parallel feature extraction network (PFEN) is proposed by Yang et al. (Citation2022). The model can extract key data from different network attack behaviours and can effectively and comprehensively evaluate network conditions.
Different from the above methods, after analysing the existing methods in the field of NSSA, this paper combines ResNeXt with the dual attention mechanism to effectively identify the importance of each channel and make full use of the rich contexts among neighbour keys, which optimises CNN and strengthens the ability of CNN to protect the network.
3. Convolutional neural network (CNN)
3.1. The ResNeXt block
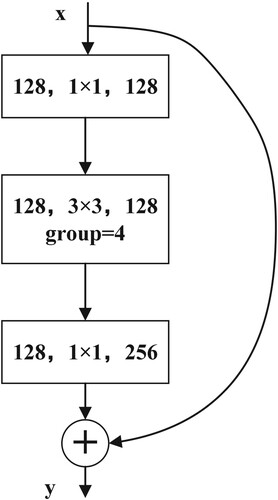
ResNeXt is a variant of ResNet (He et al., Citation2016), so it can have many convolutional layers without worrying about degradation. And since the topological structure of each branch is the same, the number of hyperparameters is reduced while maintaining high accuracy. The output of the ResNeXt block is:
(1)
(1) where
represents the topology structure,
indicates the input,
refers to the output, and
denotes the number of branches. Equivalent building blocks of ResNeXt is shown in Figure .
3.2. Efficient channel attention (ECA) module
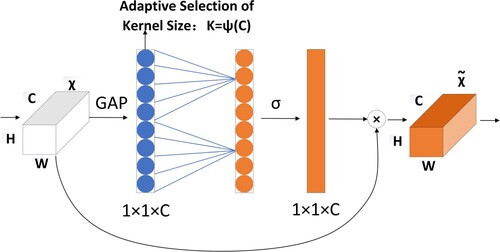
The SE module (Hu et al., Citation2018) can calculate the weight of each feature channel, knowing that the importance of each channel is different. However, the fully connected (FC) layer part of the SE module will make the model more complex, and the dimensionality reduction and dimensionality raising in the SE module may have negative effects. Therefore, the ECA module is proposed. This module reduces the number of parameters and makes the model less complex by avoiding dimensionality reduction and raising, which effectively increases the value of the channel attention mechanism. The specific structure of the ECA module is presented in Figure .
The core part of the ECA module can be implemented by a fast one-dimensional () convolution of size
. The convolution kernel size
denotes the number of neighbours participating in the attention prediction of this channel. The ECA module can adaptively determine the suitable
without manual resizing, where
is related to the channel dimension. The specific formula for calculating
is as follows:
(2)
(2) where
represents channel dimension and
indicates the nearest odd number of
.
and
are usually set to 1 and 2, respectively.
3.3. Contextual transformer (CoT) block
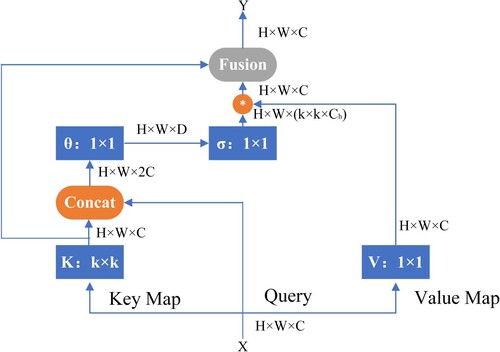
Since traditional CNNs can only model local information, they are lacking in long-distance modelling and perception. The transformer has great advantages in long-distance modelling. The Self-Attention structure in the original Transformer just calculates the attention matrix based on the interaction of query and key, and it cannot make full use of the rich contexts among neighbour keys. To alleviate this problem, the CoT block was proposed. It fully explores the contextual information among neighbour keys to improve self-attention learning in an efficient way, which improves the expressive ability of output features. The CoT block is presented in Figure .
In Figure , the size of input feature maps is . The queries, keys and values are set to
, respectively. First, CoT module uses
group convolution over all the neighbour keys within
grid spatially to obtain the contextualised keys
. After that, the contextualised keys
and queries
is concatenated to obtain the attention matrix
by two consecutive convolutions with the convolution kernel size of 3 × 3:
(3)
(3) Next, the attended feature map
(also known as the dynamic context) is obtained by aggregating the contextualised attention matrix
(4)
(4) where
denotes the local matrix multiplication operation that measures the pairwise relations between each query and the corresponding keys within the local
grid in space. Finally, the static context
and the dynamic context
are fused by the CoT block to output.
4. Harris hawks optimisation (HHO)
HHO originates from the group cooperative behaviour of the Harris’ hawks when preying. It is an excellent swarm intelligence algorithm with the advantages of requiring few control parameters and excellent global search ability.
4.1. Exploration phase
At this stage, all individuals of the Harris’ hawk are in a wait state, and it searches for prey in random places according to two strategies:
a: When q < 0.5, the hawk’s perching location is related to the position of the prey and other members of the population.
b: When q ≥ 0.5, the hawks will perch on random locations within the population's range.
These two strategies can be formulated as:
(5)
(5) where
and
indicate the upper and lower bounds of the search space,
represents the position of random individuals,
indicates the average location of all members in the population,
represents the position of the prey,
denotes the number of iterations,
represent the location of Harris’ hawks in the next iteration and
,
,
,
and
are random numbers inside (0,1).
4.2. Transition from exploration to exploitation
According to the escape energy of the rabbit, the Harris’ Hawk can switch between different attack modes. When the rabbit escapes, the escape energy will be reduced as:
(6)
(6) where
denotes the maximum of iterations,
indicates the initial value of the escaping energy of the rabbit, and
represent the escape energy of the rabbit.
4.3. Exploitation phase
Assuming that is the escape probability of the rabbit, according to the escape behaviour of the rabbit and the capture strategy of the Harris’ hawks,
and
will have different values and cause the hawks to adopt different attack strategies.
4.3.1. Soft besiege
The soft besiege is selected by Harris’ hawks when r ≥ 0.5 and |E| ≥ 0.5, and the attack behaviour can be expressed as:
(7)
(7)
(8)
(8) Among them,
indicates the distance between the prey’s position and the hawk’s current position in iteration
,
is a random number within (0,1) and
represents the escape distance of the rabbit throughout the escaping procedure.
4.3.2. Hard besiege
Harris’ hawks select the hard besiege when and
. In this case, the calculation of the current position of the hawk is as follow:
(9)
(9)
4.3.3. Soft besiege with progressive rapid dives
The soft besiege with progressive rapid dives is selected by Harris’ hawks when and
, and the attack strategy can be expressed as follow:
(10)
(10) If this movement brings worse results after updating the location, execute another attack strategy:
(11)
(11) where
is a random vector of size
and
represents the dimension of problem.
indicates the levy flight function. The
can be expressed as:
(12)
(12)
(13)
(13) Among them,
is usually set to 1.5 and
are random numbers within (0,1).
Hence, the final attack strategy is as follow:
(14)
(14)
4.3.4. Hard besiege with progressive rapid dives
The hard besiege with progressive rapid dives is selected to capture the prey when and |E| ≥ 0.5, and the hawks’ subsequent attack behaviour is determined by:
(15)
(15) where Y and Z are obtained by the following formulas (16) and (17).
(16)
(16)
(17)
(17)
5. Construction of network model based on dual attention mechanism and HHO-ResNeXt
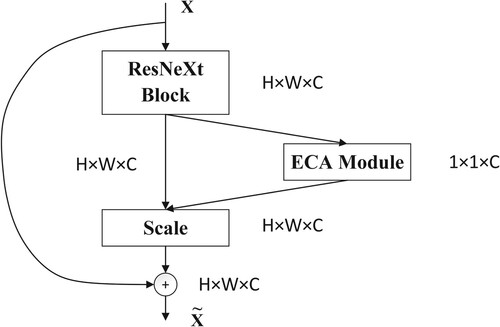
5.1. The ECA-ResNeXt block
Embedding the ECA module into the ResNeXt block can form the ECA-ResNeXt block, which is an important part of our model. The details of the ECA-ResNeXt block are shown in Figure . The input of the block is , and the output is
.
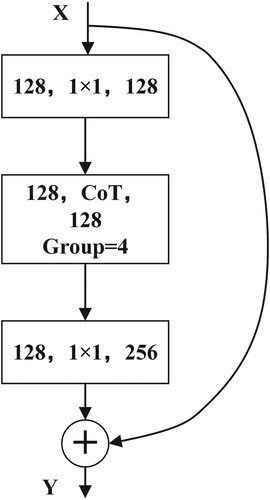
5.2. The CoTNeXt block
The COT block can replace the 3 × 3 convolution in the ResNeXt block to form the CoTNeXt block, which is one of the advantages of the COT block. The CoTNeXt block is the core of our model, and its details are shown in Figure . The input of the block is and the output is
.
5.3. The complete structure of our model
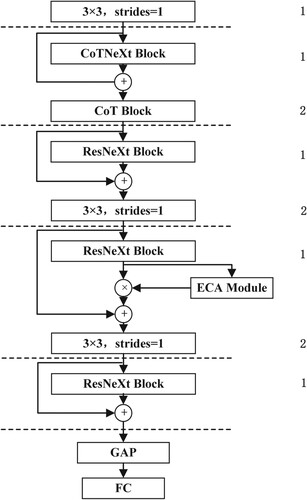
Our model mainly consists of six parts, as shown in Figure .
The first part is a convolutional layer, with its convolution kernel size of 3 × 3. A CotNeXt block and two CoT blocks constitute the second part. A ResNeXt block and two convolutional layers with the kernel size of 3 × 3 constitute the third part. The ECA-ResNeXt block which is formed by combining the ResNeXt block with the ECA module is the fourth part. A ResNext block is the fifth part, and the sixth part is constituted by a global average pooling (GAP) and a FC layer. Figure presents the structure of the model, and the hyperparameters of the model are listed in Table .
Table 1. Details of this model.
5.4. Network security situation assessment process
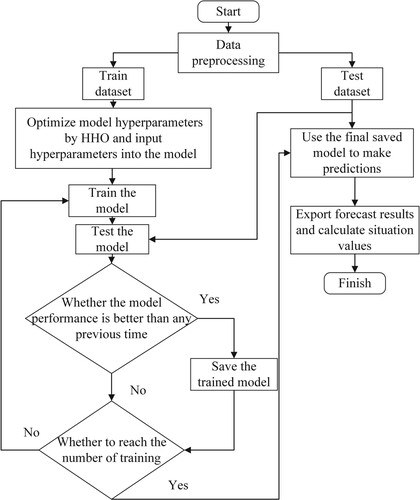
The flow chart of the situation assessment model based on the dual attention mechanism and HHO-ResNeXt is shown in Figure .
Specifically, the operation process of our proposed NSSA model can be summarised as the following five steps:
Acquire network security datasets and preprocess datasets, including numeralisation, normalisation, and data augmentation.
The obtained cybersecurity dataset is divided into the training dataset and the test dataset.
Part of the training dataset and the test dataset are used for the HHO optimisation operation, and the Mean Absolute Error (MAE) is used as the evaluation function during optimisation. After the optimisation, the optimised hyperparameters are input into the model.
The preprocessed training dataset is sent to the model built in this paper for training. After each epoch, the test dataset is sent to the model for testing, and the test results are compared with all previous test results. If the performance is the best this time, save the model after this training and continue training. Otherwise, directly perform the next training until the preset training times is reached.
Send the test dataset to the best-performing model for prediction, derive the prediction result and calculate the situation value.
6. Experiments
6.1. Dataset description
The NSL-KDD dataset (Revathi & Malathi, Citation2013) solves many of the problems in the KDDCUP99 dataset (Tavallaee et al., Citation2009), which is a standard dataset in the field of cybersecurity and is adopted by a lot of security research works. Each piece of data in this dataset consists of 41 features and is marked as normal and attack. There are 39 attack types in the dataset, which are divided into four categories. In our experiment, we used KDDTrain+.txt and KDDTest+.txt as the training dataset and the test dataset.
The UNSW-NB15 dataset (Moustafa & Slay, Citation2015, November) is an authoritative dataset used by many researchers to study cybersecurity. Each data in the dataset contains 49 features and there are a total of nine attack types. The test dataset and training dataset are UNSW_NB15_testing-set.csv and UNSW_NB15_training-set.csv respectively.
6.2. NSL-KDD Dataset Preprocessing
In this dataset, each piece of data originally has 42 features. Since the 42nd feature indicates the difficulty of correctly classifying each sample, i.e. meaningless to this experiment, we deleted it. There are many attack types in this dataset, so a mapping dictionary is established, and the attack types are divided into four categories: Dos, R2L, Probe, and U2R. This paper divides normal traffic into the Benign category.
There are three categorical features in the features of this dataset, namely protocol_type, service and flag. Since these three features are not numerical values, they need to be digitised by One-Hot Encoding. The number of features in this dataset after one-hot encoding is 122. For the convenience of operation, the feature matrix of the input network is generally a square matrix. Therefore, this paper expands the number of features after one-hot encoding. The specific implementation method is to add 22 “0” features after the 122nd feature, so that the number of features reaches 144. When loading the data into the model we transform it into a 12 × 12 feature map.
In the dataset, different features vary widely. To reduce the effect of this difference on the experiment, the features are normalised by min–max normalisation as:
(18)
(18) where
and
represent the maximum and minimum of each feature, respectively. And because the dataset is extremely unbalanced, this paper adopts the oversampling technique to balance the train dataset.
6.3. UNSW-NB15 dataset preprocessing
This dataset also contains 3 categorical features, so the processing is similar to NSL-KDD dataset. After this dataset is processed, the number of features becomes 196, and when loading the data into the model we transform it into a 14 × 14 feature map. This paper also normalises the UNSW-NB15 dataset following Equation (18). Because the ratio of the number of each attack type to the total number of samples in the training dataset is larger than that in the test dataset, which affects the model performance, this paper redistributes the training dataset and the test dataset.
6.4. Network security situation quantification
The two datasets selected in this paper do not have actual situation values, so by analysing the impact of various attacks on the network to generate the actual situation values of the datasets. represents the impact of various attack types on network security, and
represents the number of various attack samples in a group. Tables and show the impact of each attack type on the network in the two datasets, respectively.
Table 2. Impact of attacks in the NSL-KDD dataset.
Table 3. Impact of attacks in the UNSW-NB15 dataset.
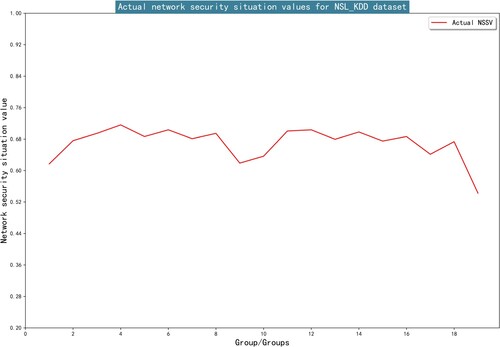
In the NSL-KDD dataset, every 1200 samples are divided into a group, and a total of 19 groups are achieved. The situation value (SV) of each group is calculated as:
(19)
(19) After situation values are calculated, normalise the situation values. The calculated actual NSSV of the test dataset are shown in Figure .
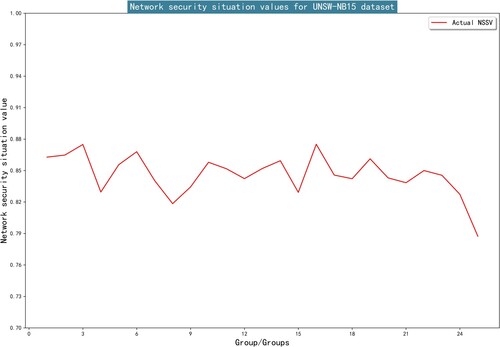
In the UNSW-NB15 dataset, every 3300 samples are divided into a group, and a total of 25 groups are achieved. The situation value SV of each group is calculated by Equation (19). After situation values are calculated, we normalise the SA. The actual NSSV of the test dataset calculated are shown in Figure .
6.5. Hyperparameters selection
In this experiment, our model is built based on the tensorflow-gpu-2.4.0 framework. The Mean Squared Error (MSE) is used as the evaluation function when using HHO to find the optimal parameters. The population size is five, and the maximum number of iterations is set to 10. In order to improve the optimisation efficiency and make the Harris’ hawk efficiently search for prey, a limit is set for the hyperparameters that need to be optimised.
The optimal hyperparameters are found by Harris’ hawks when MSE reaches the minimum value. The final hyperparameters are shown in Table .
6.6. Experiment results
6.6.1. Multi-class classification results
To verify the performance of the model, we compares our model with other methods, i.e. the algorithms compared with our model are the random forest algorithm proposed by Cao et al. (Citation2021), the decision tree and artificial neural network proposed by Samuel (Citation2021), the DCNN algorithm proposed by Zhang, Xie, et al. (Citation2019), The improved CNN algorithm proposed by Zhang, Zhang, et al. (Citation2019), ResNet proposed by He et al. (Citation2016), and ResNeXt proposed by Xie et al. (Citation2017). The evaluation indicators selected in this paper are accuracy, precision and F-scores. The experimental results of different models are shown in Table .
Table 4. Experiment results of different models.
The evaluation results of the three indicators are shown in Table . The comprehensive performance of our model on the three indicators of accuracy, precision and F-scores has achieved the best results on both datasets. Therefore, our model has the best comprehensive performance compared to other models.
6.6.2. Network security situation assessment results
To verify the situation assessment ability of the model, three typical evaluation indicators are selected to evaluate each model, namely Mean Absolute Error (MAE), Mean Square Error (MSE) and Mean Absolute Percentage Error (MAPE). These three evaluation indicators can be expressed as follows:
(20)
(20)
(21)
(21)
(22)
(22)
Among them, n represents the number of samples, and
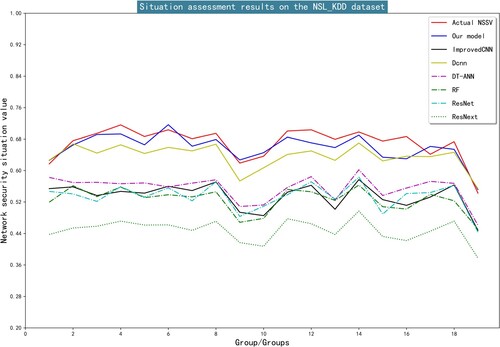
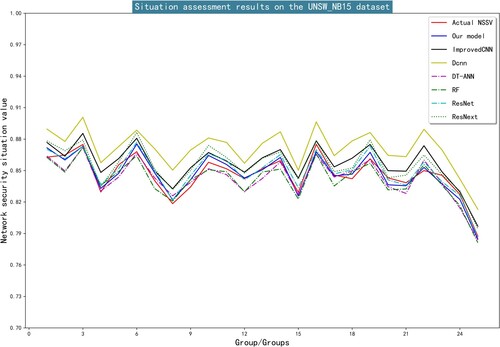
represents the true value of the sample and the predicted value of the sample, respectively. The smaller the values of these indicators, the better the model’s performance. Figures and show the situation assessment results of each model on the datasets used in this paper.
According to Figures and , our model has the highest fitting degree with the actual situation values, and the fitting deviation of the other six models is relatively large. The detailed data of the three evaluation indicators of each model are shown in Table .
Table 5. Network security situation assessment results of each model.
Table show the evaluation results of the three indicators, it can be observed that our model has the smallest MAPE, MSE and MAE on both datasets, which means that our model can excellently evaluate the network environment and eliminate potential hidden dangers. Therefore, compared with other methods, our model has the best comprehensive performance.
7. Conclusion
This paper proposes a network security situation assessment model based on dual attention mechanism and HHO-ResNeXt. Our model combines ResNeXt with ECA module and COT block. And we select the optimal hyperparameters of the model through the HHO algorithm. The model solves the problem that the traditional CNN cannot obtain the importance of each channel, and the receptive field is limited, dramatically improving the CNN's performance.
Experiments on NSL-KDD dataset and UNSW-NB15 dataset show that our proposed method has the best comprehensive performance and outperforms existing methods.
The experiment will be improved in the future in the following directions:
Our results are based on simulation experiments, and the method has not been applied to the real network for practice. Therefore, our model will be applied to the real environment for further testing in the future.
The experiments are only conducted on two datasets, which are not enough. To verify the effectiveness of our model, it is necessary to conduct experiments on more datasets.
Disclosure statement
No potential conflict of interest was reported by the author(s).
Additional information
Funding
References
- Akwetey, H. M., & Danquah, P. (2022). Predicting cyber-attack using cyber situational awareness: The case of independent power producers (IPPs). International Journal of Advanced Computer Science and Applications, 13(1), 700–709. https://doi.org/10.48550/arXiv.2202.01778
- Bass, T. (2000). Intrusion detection systems and multisensor data fusion. Communications of the ACM, 43(4), 99–105. https://doi.org/10.1145/332051.332079
- Bass, T., & Gruber, D. (1999). A glimpse into the future of id. The Magazine of USENIX & SAGE, 24(3), 40–49.
- Cao, Y., Zhu, G., Qi, X., & Zou, J. (2021). 基于随机森林的入侵检测分类研究 [Research on intrusion detection classification based on random forest]. Computer Science, 48(S1), 459–463. https://doi.org/10.11896/jsjkx.200600161
- Endsley, M. R. (1988). Design and evaluation for situation awareness enhancement. In Proceedings of the Human Factors Society Annual Meeting (Vol. 32, No. 2, pp. 97–101). Sage Publications.
- Gong, J., Zang, X., Su, Q., Hu, X., & Xu, J. (2017). 网络安全态势感知综述 [Survey of network security situation awareness]. Journal of Software, 28((04|4)), 1010–1026. https://doi.org/10.13328/j.cnki.jos.005142
- He, K., Zhang, X., Ren, S., & Sun, J. (2016). Deep residual learning for image recognition. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition (pp. 770–778). IEEE Computer Society.
- Heidari, A. A., Mirjalili, S., Faris, H., Aljarah, I., Mafarja, M., & Chen, H. (2019). Harris hawks optimization: Algorithm and applications. Future Generation Computer Systems, 97, 849–872. https://doi.org/10.1016/j.future.2019.02.028
- Hu, J., Shen, L., & Sun, G. (2018). Squeeze-and-excitation networks. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition (pp. 7132–7141). IEEE Computer Society.
- Jiang, L., Jayatilaka, A., Nasim, M., Grobler, M., Zahedi, M., & Babar, M. A. (2022). Systematic literature review on cyber situational awareness visualizations. IEEE Access, 10, 57525–57554. https://doi.org/10.1109/ACCESS.2022.3178195
- Ke, G., Chen, R. S., Chen, Y. C., & Yeh, J. H. (2021). Network security situation prediction method based on support vector machine optimized by artificial Bee colony algorithms. Journal of Computers, 32(1), 144–153. https://doi.org/10.3966/199115992021023201012
- Li, Y., Yao, T., Pan, Y., & Mei, T. (2022). Contextual transformer networks for visual recognition. IEEE Transactions on Pattern Analysis and Machine Intelligence, 45(2), 1489–1500. https://doi.org/10.1109/TPAMI.2022.3164083
- Moustafa, N., & Slay, J. (2015, November). UNSW-NB15: A comprehensive data set for network intrusion detection systems (UNSW-NB15 network data set). In 2015 Military Communications and Information Systems Conference (MilCIS) (pp. 1–6). Canberra, ACT, Australia: IEEE.
- Nazir, H. M. J., & Han, W. (2022). Proliferation of cyber situational awareness: Today’s truly pervasive drive of cybersecurity. Security and Communication Networks, 2022, 1–16. https://doi.org/10.1155/2022/6015253
- Revathi, S., & Malathi, A. (2013). A detailed analysis on NSL-KDD dataset using various machine learning techniques for intrusion detection. International Journal of Engineering Research & Technology (IJERT), 2(12), 1848–1853.
- Samuel, O. S. (2021). Cyber situation awareness perception model for computer network. International Journal of Advanced Computer Science and Applications, 12(1), https://doi.org/10.14569/IJACSA.2021.0120147
- Tavallaee, M., Bagheri, E., Lu, W., & Ghorbani, A. A. (2009, July). A detailed analysis of the KDD CUP 99 data set. In 2009 IEEE Symposium on Computational Intelligence for Security and Defense Applications (pp. 1–6). IEEE.
- Wang, Q., Wu, B., Zhu, P., Li, P., Zuo, W., & Hu, Q. (2020, June). ECA-Net: Efficient channel attention for deep convolutional neural networks. In Proceedings of the 2020 IEEE/CVF Conference on Computer Vision and Pattern Recognition (pp. 13–19). IEEE.
- Wu, W., & Yang, C. (2022). An overview on network security situation awareness in internet. International Journal of Network Security, 24(3), 450–456. https://doi.org/10.6633/IJNS.202205_24(3).08
- Xie, S., Girshick, R., Dollár, P., Tu, Z., & He, K. (2017). Aggregated residual transformations for deep neural networks. In Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition (pp. 1492–1500). IEEE.
- Yang, H., Zeng, R., Xu, G., & Zhang, L. (2021). A network security situation assessment method based on adversarial deep learning. Applied Soft Computing, 102, 107096. https://doi.org/10.1016/j.asoc.2021.107096
- Yang, H., Zhang, Z., Xie, L., & Zhang, L. (2022). Network security situation assessment with network attack behavior classification. International Journal of Intelligent Systems, 37(10), 6909–6927. https://doi.org/10.1002/int.22867
- Yuan, L. (2021). Prediction of network security situation awareness based on an improved model combined with neural network. Security and Privacy, 4(6), e181. https://doi.org/10.1002/spy2.181
- Zhang, R. C., Zhang, Y. C., Liu, J., & Fan, Y. D. (2019). Network security situation prediction method using improved convolution neural network. Computer Engineering and Applications, 55((06|6)), 86–93. https://doi.org/10.3778/j.issn.1002-8331.1808-0016
- Zhang, S., Xie, X., & Xu, Y. (2019). Intrusion detection method based on a deep convolutional neural network. Journal of Tsinghua University (Science and Technology), 59(1), 44–52. https://doi.org/10.16511/j.cnki.qhdxxb.2019.22.004
- Zhao, D., Ji, G., & Zeng, S. (2022). A network security situation assessment method based on multi-attention mechanism and HHO-ResNeXt. In Xiaofeng Chen (Ed.), International Symposium on Security and Privacy in Social Networks and Big Data (pp. 199–211). Springer.
- Zheng, W. (2020). Research on situation awareness of network security assessment based on Dempster-Shafer. In MATEC Web of Conferences (Vol. 309, p. 02004). EDP Sciences.