?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.ABSTRACT
Elliptic Curve Cryptography (ECC) is a promising cryptosystem as it presents the ideal choice for implementing public-key cryptography in resource-limited devices, such as those found in envisioned Internet of Things applications, e.g. wireless sensors. Elliptic Curve ElGamal (ECEG) is a renowned member of the ECC family. However, it requires encoding the message before encryption and decoding it after decryption. To better improve the processing time and to avoid sharing a lookup table, we propose, in this document, a new method that exchanges encoding parameters and authenticates endpoints at the same time. So, our new protocol ensures the authentication of communication parties and integrity of ephemeral encoding parameters. The robustness of our solution is proven by the Scyther tool. Experimental tests have been carried out, and the performance of the new methods is provided and compared with RSA and related work. Security and performance analysis show that our new scheme has achieved improved functionality and higher security while maintaining low computational.
1. Introduction
The Internet of Things (IoT) is transforming human life through intelligent automation and has become an inescapable part of human activities. The IoT paradigm appears to be the most promising area for technological advancement, as it will change the way we view communication. Several technologies are driving this modern paradigm, such as Wireless Sensor Networks (WSN), cloud services, middleware, Radio Frequency Identification (RFID) tags, and more. As a result, IoT and its various technologies are spreading in various fields such as industry, agriculture, medicine, and military. Meanwhile, each IoT system is designed to provide a specific service. The delivery depends on the information collected at the perception layer, and it is the lowest layer of the IoT. Most resource-constrained devices are openly deployed in the perception layer called WSN. In the WSN, a large number of sensor nodes are deployed to monitor a wide area. These nodes have limitations that relate to processing power, communication bandwidth, storage memory, device size, and availability of device power. In addition, the operating conditions are most often harsh or even hostile. So, as they are prone to security attacks, it is quite easy to intercept a wireless transmission and alter the information content. Thus they should be equipped with security mechanisms to defend against attacks such as node capture, physical tampering, eavesdropping, denial of service, etc. (Fang et al., Citation2020). Moreover, the gaps in constrained resources do not allow the use of traditional network security techniques in sensor networks. Security issues are more complex in WSNs due to unreliable communication channels and unmonitored operations. Existing security techniques require more energy for their implementation because these techniques are not developed with precision in view of the specification of WSNs. Thus, preserving battery life is the primary requirement, as many devices run for months or years on a single battery. This is why we should strive to reduce power consumption by using lightweight security mechanisms. With existing security threats, there are many difficulties in using a symmetric encryption system to improve WSN security. Meanwhile, public-key cryptography forms the basis of most secure communication today, as there is no need for both parties to communicate before the message is encrypted. However, using asymmetric cryptography for secure communication presents a challenge, since sensor nodes within a WSN have limited computational capabilities. Asymmetric encryption is more complex and requires more computing power than symmetric encryption, but it guarantees authentication and non-repudiation of encryption (Al-shabi, Citation2019; Zhang, Citation2021). In our research, we focus on studying public key cryptosystems to propose a new lightweight solution that ensures authentication, integrity, and confidentiality. The most popular public key algorithms are ECC (Elliptic Curve Cryptography) and RSA (Rivest–Shamir–Adleman). However, the main advantage of ECC over other public key algorithms such as RSA is the key size, since it requires a shorter key length to provide the same level of security. This is why this ECC is particularly suitable for wireless communication (Mallouli et al., Citation2019).
In our work, we propose a new mutual lightweight authentication-based Elliptic curve ElGamal (ECEG) protocol. ECEG is a public-key cryptographic equivalent of the ElGamal encryption scheme which uses the discrete logarithm of the elliptic curve problem. The Encoding (converting message to a point) and Decoding (converting a point to a message) are mandatory functions in Encryption and Decryption in the elliptic curve. The mapping method converts a plaintext message into the coordinates of the predefined EC points. Baccouri et al. (Citation2022) propose a new encoding method based on ephemeral parameters implemented using the C programming language, on a Linux platform. The ephemeral encoding method and the performance of the cryptosystem for eight recommended curves are presented and discussed. The implementation performances demonstrate that the proposed new encoding method improves the ECEG cryptosystem security, without significantly increasing the computation time. However, when Alice wants to exchange the ephemeral parameters with Bob, her message can be compromised, and subsequently, the whole network will be compromised. Therefore, it is important to guarantee their confidentiality and integrity, as well as authenticate both parties. In this paper, we present a novel method that achieves both confidentiality of exchanged encoding parameters and lightweight mutual authentication in wireless communication by leveraging ephemeral parameters. To achieve this, we introduce a new method named the ‘Lightweight Authentication Scheme Based on Elliptic Curve El Gamal '. Our approach provides a comprehensive solution that not only ensures the privacy of encoding parameters but also efficiently verifies the identities of communication parties. The utilization of ephemeral encoding parameters during each session significantly enhances security by preventing potential risks associated with static or reused values. The contribution of the research work is as follows:
Confidentiality and integrity of the ephemeral encoding parameters of the ECEG cryptosystem
Mutual authentication of the two communicating parties.
This novel method effectively mitigates the need for additional channel bandwidth overhead by streamlining the mutual authentication phase to a single round trip. This not only minimizes resource utilization but also showcases the strength of our approach. To validate the efficacy and assess the obtained outputs:
We implement the new scheme in a controlled environment using the C language, incorporating NIST curves (Standards for Efficient Cryptography Group, Citation2000, September). This allows us to realize our proposed enhancements and thoroughly test the protocol.
We rigorously analyse and validate the security strength of our protocol using a formal approach, employing the Scyther simulation tool. Through this process, we assess the resilience of our scheme against potential attacks and vulnerabilities.
Furthermore, we compare our implementation's outputs with RSA and other related protocols to provide a comprehensive evaluation. The comparative analysis demonstrates the efficiency of our scheme, highlighting its superior performance and security attributes.
By undertaking these steps, we provide a robust assessment of our proposed protocol, ensuring its efficacy, security, and overall performance in comparison to existing implementations. The article is structured as follows: Section 2 covers the mathematical context of ECC, while Section 3 presents related work. In Section 4, the proposed method for lightweight mutual authentication and exchange encoding parameters is described. Section 5 analyses the proposed solution using the Scyther security protocol verification tool. Section 6 provides details on the implementation results and a comparison with the implementation results of RSA and the referred work. Finally, Section 7 concludes the article.
2. Mathematical background
2.1. Elliptic curve cryptography
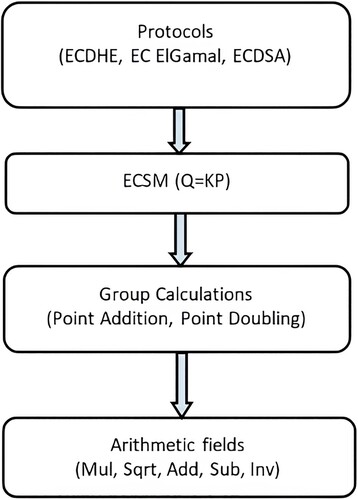
In 1985, a new conception of a public-key cryptographic system using elliptic curves called ECC was independently proposed by Neal Koblitz and Victor Miller (VenkataGiri & Murty, Citation2021). Elliptic Curve Cryptography (ECC) is based on simple mathematical functions to calculate in one direction, but very difficult to reverse. The discrete logarithm of the elliptic curve problem (ECDLP) is the foundation of ECC security, ECDL is a so-called ‘trapdoor’ or ‘one-way’ function. Using protocols based on elliptic curves for encryption, it is not possible to find an elliptic curve element even with the knowledge of the base point or generator point of the curve. ECC is very difficult for the attacker to break as it relies on the discrete Elliptic Curve Logarithm problem. ECC is an approach that uses fewer key sizes to provide more security and help reduce storage transmission requirements, and ECC can provide the same level of security compared to the level of security offered by RSA (Mohamed, Citation2014; William, Citation2006). ECC is a public key cryptography which does not require a secret key shared between the communication parties. Each user or device participating in the wireless communication has a key, pair, a public key, and a private key. The public key is distributed to all users via wireless communication, while the private key is known only to a particular user. The generalized shape of an elliptic curve illustrated in (Lara-Nino et al., Citation2018) is presented in a simplified manner to identify particular sets of curves called families. A hierarchy shown in should be followed to define the sets of algorithms needed to create an ECC cryptosystem. First, you should select the type of protocol to use; in our case, the ECEG is selected. After that, the algorithms for performing Elliptic Curve Point Multiplication (ECPM) should be defined, followed by the algorithms for performing an arithmetic operation in the field. Finally, the addition and the doubling of the points are done in the form of a sequence of operations on different coordinates of the entry points; these coordinates are field elements.
Figure 1. Taxonomy of elliptic curves (Lara-Nino et al., Citation2018).
2.2. Prime field
The finite field or Galois field is a set of q elements denoted GF (q) with two binary operations, called addition and multiplication, which satisfy certain demands for arithmetic properties. These operations on elliptic curves can be performed much faster and more accurately on a finite field because using real numbers produces the rounding error, then using integers increases the computational capability of the operations on an elliptic curve with precision and efficiency. The finite field called prime field GF (P) is composed of a set of integers 0, 1, 2, …, p–1 of which p is the prime number. Curve cryptography is generally defined on two finite fields: the prime domain GF (P) and the binary domain GF (). Using GF (P), one can benefit from the fact that arithmetic operations are presented in many libraries, otherwise using GF (
) can make the hardware implementation faster and more compact (Islam et al., Citation2018). There are different coordinate systems that can be used to represent the elliptic curves, such as the affine coordinates, Jacobian coordinates and mixed coordinates. Although the affine coordinates are the most known. In our discussion, we have implemented an elliptic curve on a finite field Prime for the ElGamal Elliptic Curve cryptosystem and the operations are defined on the affine coordinate system which is represented by the vector (x, y).
2.3. ECC over prime field
Either p > 3 and an odd prime number, the general cubic equation of the elliptic curve E on Fp is defined by the following Weierstrass equation of the form:
(1)
(1) However, for our purpose, we consider the finite prime fields Fp. Equation (Equation1
(1)
(1) ) becomes
(2)
(2) where
The discrimination D ensures that the elliptic curve does not contain repeated factors. It verifies that the curve is called a non-super singularity form since the super-singular curves are not safe. The main ECC operation is scalar multiplication. Both P and Q be two points on the elliptic curve such that Q = KP, where k is a scalar. Knowing P and Q, it is impossible to recover k, if k is too large. But it is easier to get Q where K and P are given. Scalar multiplication has the following form:
, k times. To obtain Q, we should add P to itself k−1 times, which results on another point in the same curve. More precisely, they are methods for calculating
, k being the private key and P a point on the curve. The finite field element and all the results of the operation like addition, subtraction, multiplication, and division involving integers are in the interval
. n is the order of the curve, then each private key during key generations should be randomly chosen between 1 and n−1 . The generated public key is a point on the curve and is obtained by multiplying the private key by the base point chosen by the administrator at the start.
2.4. Modular arithmetic
To provide a smaller set of numbers with certain properties, modular arithmetic is applied in elliptic-curve cryptography. To do this, modular arithmetic establishes a group of numbers as a ‘set’ in a modulo p group. This group includes all integers from 0 to p−1 and rotates itself and represents only the values in the elements of this group. Modular arithmetic allows us to generate an elliptic curve and can facilitate the calculation of elliptic curves; therefore, it is a fundamental part of elliptic curve cryptography as it limits the number of variables in a set. The remainders of the numbers divided by p represent their values.
2.4.1. Subtraction
Let . We can calculate negative numbers in modular arithmetic by moving backward through the set. Since the result of a−b is negative and out of range [0,16], the result is wrapped into range [0,16] by adding
with 17 until the result is in range [0,16].
2.4.2. Multiplication
Let . Since the result of
which is outside the range [0,16], the result is wrapped in the range [0.16] by subtracting 17 from 600 until the result is in the range [0.16].
2.4.3. Addition
Let . Since the result of a + b = 50 which is outside the range [0,16], the result is wrapped around the range [0,16] by subtracting 17 from 50 until the result is in range [0,16].
2.4.4. Division
a/b means in Fp. Simply put: , or, in plain words, a over b is equal to a times the multiplicative inverse of b. This fact is not surprising, but gives us a basic method to perform division: find the multiplicative inverse of a number and then perform a single multiplication.
2.4.5. Multiplicative inverse
The multiplicative inverse of p is the number that when multiplied by p will produce a value of 1 in some mod. For example, 6 is the multiplicative inverse of 3 (and vice versa) in mod 17, since 6 * 3 = 18 = 1 (6 times 3 equals 18, which is equal to one in mod 17, since it is 17*1 with a remainder of 1). It works only with modular primes. An algorithm such as Euclid's Extended Algorithm can be used to find the reciprocal of an effective number. In general, finding the multiplicative inverse is an expensive operation.
3. Related work
The main challenge in WSN is to provide strong security with less overhead to a sensor node. ECC has been used in encryption, digital signatures, and key establishment to provide integrity, authentication, confidentiality, and non-repudiation (Kumar et al., Citation2012). Consequently, different improved schemes based on ECC are presented in the literature.
Many researchers work to ensure authentication, since it is a significant security prerequisite for secure communications. In this section, we will present some related work that proposes an authentication protocol using elliptic-curve cryptography. Referring to various techniques that have been developed over the years, authentication schemes according to Hammi et al. (Citation2020) can be classified into six domains. In this section, we will focus on two authentication classes as follows:
| (1) | One-time password (OTP) schemes. | ||||
| (2) | Mutual authentication schemes. | ||||
3.1. One-time password (OTP) schemes
Hammi et al. (Citation2020) propose a novel approach to OTP generation that leverages cryptography Device to Device (D2D) and does not use a server-side challenge response to generate keys. Therefore, the proposed solution ensures the integrity of all communication exchanges by generating a new key for each exchange. They implement the solution to assess computational overhead on constrained and unconstrained devices. They compare the performance of their approach with two of the most widely used OTP techniques, namely, hash message authentication code-based OTP (HOTP) and time-based OTP (TOTP) algorithms. The evaluation demonstrates the high efficiency of the proposed solution, especially for constrained devices.
Nikooghadam and Amintoosi (Citation2019) perform cryptanalysis of Qui et al. system (Qiu et al., Citation2018) and show that the referred solution is unable to provide mutual authentication and is prone to Denning–Sacco attacks and denial of service attacks. To solve the security flaws of Qui et al. scheme, they propose an ECC-based mutual authentication protocol. The protocol has three phases: registration, authentication and key agreement, and password update. They formally analyse the security of the proposed scheme using the Scyther tool to demonstrate the correctness of the approach. They compare the proposed method and other related works in terms of computational complexity and communication. They show that the proposed scheme involves a minimum of computation and communication complexity.
Elias et al. (Citation2022) propose OTP system based on Elliptic Curve Cryptography to avoid sending OTP via an open network. The authentication process is performed in two phases: 1 user identification and 2-actual authentication. The generated OTP and User password are never sent through the open network. OTP is generated simultaneously on the server side and on the client side. Therefore, the client himself can verify the OTP without sending it to the server. Additionally, the OTP can be used as the session key for all session transactions.
To overcome the limitation of the uni-modal biometric technique, Sridevi (Citation2020) proposed an authentication scheme based on a concept of biometrics and OTP. The first step to authorize the user to access the confidential data of the system uses multiple biometric features of an individual. He used fusion techniques at the score level and at the decision level. This provides the first step in authentication. After the matching, one of the classifier merge methods can be performed. Based on the match score, the merge is performed. Each biometric trait provides a match score based on the input feature set. These scores provided by the biometric traits are weighted. Equal weighting of all traits and use of a user-specific match threshold are used to derive a new score. If there is a match, OTP will be generated using Elliptic Curve Cryptography method. The generated OTP is sent by mail to the user. The user is identified as a legitimate user if the user-generated OTP matches the newly generated OTP.
Kaur et al. (Citation2022) present a novel one-way hash and nonce-based two-factor secure authentication scheme with traditional user IDs, password, and OTP verification procedure. The proposed authentication procedure includes two phases: the registration phase and the log-in phase. In the registration phase when the cloud user registers, the server validates and verifies all the information provided and sends an email and an OTP mobile number to validate the customer. Then after OTP validation, the client receives the generated EC-public key from the server for secure communication. In the third step, the client chooses password and subscription details, service and duration and he sends them to the server. After that, the server stores all information for user identification credential in server database and generates cloud certificate using the ECC method. Then the server again encrypts the encrypted subscription certificate using received client nonce and finally sends double encrypted subscription certificate to the client. To get the subscription certificate, the client decrypts again the certificate with nonce and server public key.
Yan et al. (Citation2021) propose a three-factor authentication protocol for WSN with the enhancement of OTP. They examined the security shortcomings of a client confirmation convention for WSN, which is as proposed by Li et al. (2018) for Industrial IoT by adding a one-time password (OTP) (Li et al., Citation2018, June). The improvement is achieved by adding a one-time password (OTP) after the user's biometric information has been verified by the gateway node to deal with additional network attack. The authentication method involves four phases: initiation phase, registration phase, authentication and key agreement phase, and password change phase. Security and Complexity Analysis are elaborated by the authors to prove that the enhancement of the proposed method is impervious to several well-known attacks and it is more reliable than existing protocols with lower computational cost and presents reduction in power consumption.
Panja et al. (Citation2022) present a secure fingerprint-based authentication scheme using elliptic-curve cryptography in electronic transactions to prevent unauthorized users from accessing private data. The HMAC-SHA-256 hashing technique and ECEG public-key encryption are used to speed up the authentication process. A specific customer's fingerprint pattern is used as the private key in the HMAC-SHA-256 hash algorithm. In the proposed model, the final encryption of the generated OTP is performed using ElGamal elliptic curve cryptography before transmitting it over the Internet. The performance of the proposed model was measured using a comparative analysis with other algorithms. They conclude that the NIST recommended curves can be used to achieve the best performance for the proposed mode.
Mahto and Yadav (Citation2015) propose an enhanced security model of OTP system using ECC with finger-print biometric and with less key length. The vascular patterns of the user's palm are analysed using a palmar vein biometric system. This information is used to create the public key of the user to encrypt the OTP. Here, the OTP is generated using a conventional method, and the proposed model is secure using ECC. The security provided is valuable; however, the method requires a sophisticated biometric palm vein sensor.
Ramasamy et al. (Citation2020) propose securing OTP generation using elliptic curve cryptography for mobile commerce applications. The secret key is generated from the customer's facial image. After generating the OTP, the user's image and the plaintext of the OTP are encrypted as ciphertext and transmitted to the user's mobile. After receiving the ciphertext, the eyes are located in the image. The iris is segmented and matched with the template database. Then the decrypted plaintext is entered as an OTP for the current transaction. The proposed model has been shown to be very effective against measures of false acceptance rate and false rejection rate and is validated on the Q-Fire dataset. The computational complexity is very reduced because it uses the convolution operator for the location of the centre of the iris.
3.2. Mutual authentication schemes
Lamrani Alaoui et al. (Citation2021) propose an ECC-Based Authentication Protocol for RFID. First, they explain two basic protocols that offer mutual authentication, confidentiality, forward security, anonymity, unlikability, scalability, and resistance against the most important security attacks. Then they discuss the initialization and the actual authentication phase, for two schemes. The first scheme (v1.1) requires the storage of the identities and related key material of all active tags, while the second scheme (v1.2) only needs the list of revoked tags. An additional phase is proposed on both protocols (v2.1 and v2.2) to enable multi-reader authentication. They compare the efficiency of their schemes for the computational time, communication costs, storage costs and protection level. They show that the proposed schemes have small computing overhead, small storage costs for the code, and better protection rates than other related protocols.
Benssalah et al. (Citation2021) propose a protocol that takes advantage of the strengths of Dinarvand and Barati's protocol (Dinarvand & Barati, Citation2019) and takes into account the flaws. They analyse the security of Liu et al. (Citation2018); Naeem et al. (Citation2019), and Dinarvand and Barati protocols. They show that those protocols have a critical weakness. The authors explain that improper use of ECC cryptographic primitives can destroy the entire security of a given ECC-based scheme. So, to overcome critical weakness and inherit the strengths of Dinarvand and Barati protocol, they give recommendations. To resist to attacks, when designing new authentication schemes ECC-based, used curves and its parameters should be carefully chosen. Additionally, to perform scalar point multiplication, the Montgomery algorithm should be implemented. Through formal and informal security models, they assess that the proposed protocol could withstand all known attacks.
Noori et al. (Citation2022) propose an ECC-based secure RFID mutual authentication for IoT in healthcare environment. After studying and revised the proposals of Alamr et al. (Citation2018), they found that the proposed scheme had higher computational costs, higher communication costs, and higher elliptic curve points during operation. Thus they propose a scheme based on this research that has two phases: the initialization phase and the authentication phase. Using AVISPA for security analysis, they prove that the proposed scheme reduces the execution time of the multiplication of the points of the elliptic curve and the costs of calculation and communication. They obtained AVISPA safe output, and the effectiveness and robustness of the proposed scheme were proven.
Chen et al. (Citation2022) propose a provably secure authentication to overcome the weaknesses and flaws of Sadri et al. protocol (Sadri & Asaar, Citation2021). They show that Sadri et al. protocol is insecure against user impersonation attacks, stolen smart card attacks and sensor capture attacks. The protocol consists of four phases: pre-deployment phase, user registration phase, sensor registration phase and log-in and authentication phase. They use ROR model and BAN logic to demonstrate their proposed protocol is provably secure, they compare their work with related protocols in term of computation cost and they conclude that the proposed protocol does not have the best performance, but it ensures better security than other protocols.
Khan et al. (Citation2020) propose a layered secure framework for authentication and Encryption Using Improved ECC for IoT-based medical sensor data. The framework has four layers connected to each other: People Layer, Device Layer, Cloud Layer, and Facility Layer. The proposed scheme comprises three stages: authentication, encryption, and decryption. The authentication phase associates biometric parameters in addition to user credentials and it consists of three steps: registration, login, and verification. Data are encrypted using the improved ECC encryption technique. Therefore, to improve security, improved ECC is proposed, so an additional key (secret key) is generated to increase the system's security. The strength of the proposed framework is proven by formal security analysis and simulation. The system satisfies security requirements such as low encryption, decryption time, and communication overhead.
Nikooghadam and Amintoosi (Citation2019) propose a secure two-factor authentication and key agreement protocol for SIP using ECC. The protocol consists of three steps: registration, authentication then key agreement, and password update. They formally analyse the security of the proposed scheme and they compare the computation and communication costs of the proposed scheme with other related authentication schemes. They conclude that the proposed authentication scheme is able to achieve very low computational complexity and minimum communication complexity, compared to some other ECC-based schemes.
Kumari, Yahya Abbasi et al. (Citation2019) propose a secure mutual authentication protocol using ECC. The proposed protocol has three phases: Set up phase, Extraction phase, and Mutual authentication and session key phase. The aim of the proposed scheme is to ensure that users authenticate each other and establish a session key. The authors discuss and analyse the security investigation of the proposed protocol and finally they discuss the proposed protocol with other proposed protocols in similar environment. They conclude that their protocol does not require the calculation of bilinear pairing which makes it more efficient in communication environment and it is strong against the most known attacks as man-in-the-middle attack and re-play attack.
Sowjanya et al. (Citation2021) design an improved lightweight Elliptic Curve Cryptography based anonymous authentication protocol for IoMT. This proposed design removes the security weaknesses of the protocol of He et al., provides mutual authentication between Tier 1 and Medical Server (MS) of Tier 3 during the registration phase. Authors prove the security strength of the proposed protocol by using detailed security analysis. They simulate the proposed protocol using the AVISPA tool along with an informal security analysis, securing one-time password generation using elliptic-curve cryptography with self-portrait photograph for mobile commerce application.
Noori et al. (Citation2022) propose a scheme based on ECC to establish mutual authentication within RFID technology in the IoT. They review and analyse the scheme proposed by Chien (Citation2017). They found that the proposed scheme had higher computational and communication costs. The proposed scheme has two phases: the initialization phase and the authentication phase. AVISPA software has been used for security analysis. The results show that the proposed scheme has lower computational costs, lower communication costs and less elliptic curve point multiplication time compared with those of similar protocols.
The proposed system achieves mutual authentication in only two steps and satisfies all essential security requirements of RFID-based healthcare systems (Ibrahim & Dalkılıç, Citation2017). Authors use WISP5 built-in random number generator to generate random number of the proposed protocol. To make keys untraceable and unpredictable, they use ECDH to produce the secret key, ECDSA to realize mutual authentication, AES embedded in WISP5 to encrypt data, tiny ECC, Shamir's trick optimization to compute (u1G+u2R') that is used in ECDSA verification, and Montgomery's ladder with coordinates as point multiplication.
Sadhukhan et al. (Citation2020) propose an ECC-based three factor remote user authentication scheme that runs on the IoT environment preserving privacy and data confidentiality of the communicating user. The proposed scheme is designed in accordance with the well-accepted fifth model proposed by Xue et al. (Citation2013). The proposed scheme has five phases namely: Registration phase, Login phase, Mutual authentication and session key negotiation phase, Password change phase, and Symmetric key update phase. After successful authentication, the node transfers data to the user without any interference from the gateway. Hence, the transmission cost is reduced. They prove the security strength of the proposed protocol using two different approaches: informal security analysis and the formal AVISPA simulation tool. By comparing their scheme with other related schemes, they conclude that the proposed scheme is more efficient than the existing schemes in terms of security and performance.
Kumari, Jangirala et al. (Citation2019) propose enhanced elliptic curve cryptography (ECC) based two-factor mutual authentication for smart cards. The ESEAP (ECC-based SEcure Authentication Protocol) contains the following phases: 1 – Initialization phase, 2 – Registration phase, 3 – Login and authentication phase, 4 – Password change phase, 5 – Revocation phase and 6 – Re-registration phase. They show the correctness of the proposed protocol by the formal security analysis which is based on random oracle model and they compare ESEAP with other related protocols and found that it requires minimum computation and communication cost.
Zhao (Citation2014) propose an RFID authentication protocol that utilizes ECC to enhance the security of Liao and Hsiao (Citation2014) authentication protocol in healthcare environments. Upon examining their solution, Zhao discovered a key compromise issue with the first version of the protocol. To address this vulnerability, Zhao recommended an optimization in the authentication phase. Once the tag receives , it generates a random number
and computes
. The tag also computes two parameters,
and
, and multiplies them by kx and ky, respectively, to derive
. This helps to overcome the key compromise problem since an adversary cannot generate a legal message
such that
. Consequently, the server can authenticate the tag by verifying the accuracy of
. Zhao's refined protocol supports mutual authentication between the tag and server, and it is suited to healthcare settings.
To meet the security requirements, various existing approaches combine multiple technologies and security solutions, such as ECC protocols and OTP functions. However, this combination often results in high computational costs and communication overhead. Additionally, most of these proposed solutions necessitate more than one round-trip communication for mutual authentication, involving over three phases during the authentication process. In our paper, we aim to address these challenges and present a more efficient security solution tailored to the constraints of wireless sensor networks.
In our previous work (Baccouri et al., Citation2022), we tackled the issue of overhead bandwidth and avoided exchanging the entire lookup encoding table by proposing the exchange of only two encoding variables before the encryption step, providing the same ASCII map table. However, the exchanged encoding parameters could potentially be compromised during transmission. To overcome this concern and achieve mutual authentication, we introduce a novel method that ensures the confidentiality of exchanged encoding parameters and facilitates mutual authentication between the communicating parties. Our proposed scheme aims to minimize the computational time and energy consumption of sensors. This approach involves two simultaneous processes:
The confidentiality and integrity of the encoding parameters are ensured using the ECEG protocol and a hash function.
Additionally, we utilize these encoding parameters, a hash function, and XOR operations to mutually authenticate the communicating parties.
By employing the ECEG protocol, we achieve a high level of security with less key length, which aligns with the requirements of WSN. The authentication process occurs during the exchange of encrypted encoding parameters, requiring only one round trip to ensure mutual authentication, confidentiality, and integrity. When we ensure the security of encoding parameters before the encryption phase, we add an additional security layer to the entire cryptosystem. It is important to note that the encoding parameters mentioned in our paper are ephemeral, meaning they are only valid for one session. Even if the same selected elliptic curve is used for other sessions or other communicating sensors in the wireless network, the generated parameters are unique. The nonces generated are used only once and are highly unlikely to be repeated, especially when we choose to use recommended elliptic curves. In the upcoming section, we will present a new lightweight mutual authentication protocol based on ECEG, utilizing ephemeral encoding parameters.
4. Proposed method
Since wireless network entities communicate over an insecure channel, we need to authenticate these entities before exchanging data. In addition, the data exchanged should respect the standards of confidentiality and integrity. However, the authentication method should be strong enough to withstand different attacks, such as eavesdropping, replay attacks, MITM attacks. At the same time, this authentication should present a lightweight solution to preserve sensor energy. For this purpose, in this work, we propose a novel lightweight mutual authentication method based on the ElGamal elliptic curve cryptosystem using encoding parameters. The core of the idea is inspired by the OTP concept. Our solution exploits the ephemeral encoding parameters that are used during a single communication session to ensure the authentication phase. We have chosen ECC over the prime finite field Fp. The elliptic curve equation is defined as
(3)
(3) With
Fp and
.
As hypothesis, Alice is on the encryption side and Bob is on the decryption side. When Alice wants to send a message to Bob securely, she performs an Elliptic Curve Scalar Multiplication (ECSM) using the base point G and the random integer , which is Alice's secret key. By performing
, Alice obtains as a result her public key
which she can share with Bob. Similarly, Bob performs the same steps to obtain his public key using a random integer of his choice
and the base point G lying on the curve E.
becomes Bob's public key which he shares with Alice. The parameters of the domain of the elliptic curve over the finite prime field Fp are known by all participants. In addition, all parties should agree on all elements defining the elliptic curve, then the domain parameters of the scheme can be described by a sixfold such that
.
P: The prime number that defines the field and at the same time decides the shape of the curve.
a and b: Define the characteristic of the elliptic curve is chosen according to the security requirement.
G: The generator point or the base point,
, an element in E (
), which has the highest order n.
n: The order of G, large prime. The order of a point G or the number of possible points we can generate through multiplication of G such that
up to n times = O (Point at infinity).
h: if # E (
) = r is the number of points on an elliptic curve, then ‘h’ is the cofactor where
.
Before encrypting the message with ECEG, it should be prepared to apply ECEG calculations to match the character to a point on the elliptic curve. Our ephemeral mapping scheme (Baccouri et al., Citation2022) is classified under ASCII-based mapping; we used the following equation of scalar multiplication:
(4)
(4) where
G: the point generator of Ep,
k: ASCII character code,
α and β : integer known to Alice and Bob.
The full ASCII single-digit character is converted by the two ephemeral parameters (α and β) into a set of coordinates on the elliptic curve, eliminating nonlinearity and masking the identity of the ASCII character. The ephemeral parameters α and β are randomly generated by the sender which are updated with each new session. When Alice and Bob exchange ephemeral encoding parameters, a temporary ASCII-map is generated locally for each session.
In this work, we offer a new solution which guarantees the confidentiality of the exchanged encoding parameters and authenticates the two communication sides at the same time. For this purpose, we will cypher the two encoding parameters (α and β) to ensure their confidentiality at each new session. Furthermore, these encoding ephemeral parameters will be used with hashing and XOR functions to ensure authentication and integrity.
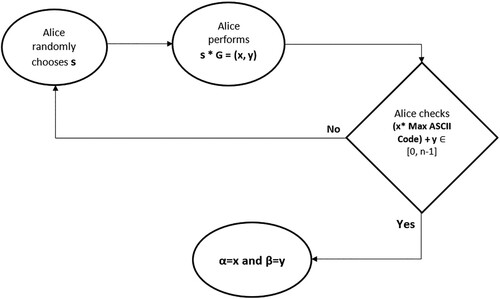
4.1. α and β generation phase
In this step, Alice use the point generator G and the order of the selected curve.
| (i) | Alice chooses randomly an integer s where | ||||
| (ii) | Alice performs | ||||
| (iii) | Alice verifies x and y with the following condition: ((x* Max ASCII Code) + y) ∈ | ||||
| (iv) | If x and y verify the condition, then | ||||
We use the condition in step 2 to ensure that using α and β, all mapped points are belonged to the selected ECEG during the encoding phase. The illustration of the encoding system is given in .
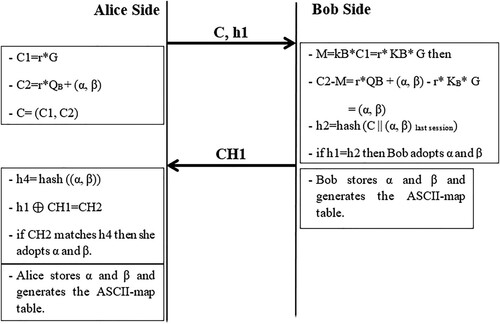
4.2. α and β transmission and the mutual authentication phase
To ensure the confidentiality and integrity of α and β, Alice should encrypt them using the ECEG cryptosystem. Additionally, Alice and Bob authenticate each other using the current and last encoding settings, hash, and XOR operations.
Alice Side:
First, Alice selects a random integer r, then performs
and
+(α, β) to get
.
Second, Alice performs h1=hash (C ∥ (α, β)
), (α, β)
are the encoding parameters of last session.
Finally, Alice sends Bob C and h1.
Bob Side:
When Bob gets the message:
First, Bob decrypts C to get (α, β) by computing
the
.
Second Bob calculates h2= hash (C ∥ (α, β)
) and compares h1 and h2.
If h1 match h2, Bob authenticates Alice and he concludes the integrity of (α, β) and then generates the ASCII map table using α and β.
Third, Bob calculates h3=hash ((α, β)) then performs h3 ⊕ h1 = CH1.
Finally, Bob sends CH1 to Alice.
Alice Side: When Alice receives CH1:
First, she executes h4= hash ((α, β)).
Then, she performs CH2= h1 ⊕ CH1. if CH2 matches h4, Alice authenticates Bob and she is sure that Bob get the correct (α, β).
After that, she uses α and β to generate the ASCII-map table.
The illustration of the proposed system is given in .
The proposed method ensures secure exchange of encoding parameters and offers lightweight mutual authentication based on ephemeral parameters, hash function, and XOR operations. The hash function is widely used in cryptography to ensure the authenticity and integrity of information exchanged.
During this phase, Alice and Bob establish a secure communication channel by utilizing the exchanged secret encryption parameters. This ensures mutual authentication, confidentiality, and integrity of the messages exchanged between them. The process is executed in a single round, facilitating the exchange of an elliptic point and guaranteeing that Bob receives the accurate encrypted message. To achieve this, Alice and Bob generate identical ASCII mapping tables, as outlined in , which serve as a basis for matching based on the secret encryption parameters. The mapping scheme detailed in Baccouri et al. (Citation2022) is employed to produce these tables. By storing the encrypted point and utilizing the exchanged encryption parameters, subsequent communications utilizing ECEG encryption are established securely. The significance of this approach lies in the integration of mutual authentication within the exchange of encrypted encoding parameters. Through a single round trip, Alice (sender) and Bob (receiver) authenticate each other, ensuring the confidentiality and integrity of the communication. By securing the encoding parameters prior to the encryption phase, an additional layer of security is introduced to the entire cryptosystem. This comprehensive process enhances the overall security and reliability of the scheme.
Table 1. ASCII-map table.
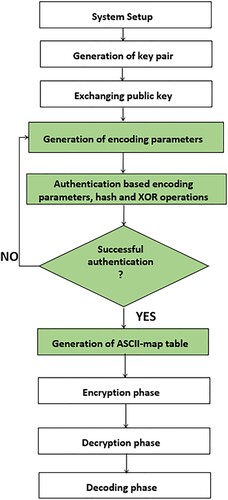
4.3. Overall design idea of our scheme
By referring to Baccouri et al. (Citation2022), we add new phases referent to our ephemeral encoding method. Therefore the implementation of the ECEG can be divided into nine phases which are explained in .
The first phase of solution implementation is system setup when we require that both entities in the WSN environment agree on the same set of ECC domain parameters. In the second phase, both Alice and Bob generate their public key using the selected curve and domain parameters. After that, they exchange their public key and verify, respectively, the validity of received key. The fourth phase presents our new method to generate encoding ephemeral parameters. After choosing randomly an integer s and multiply it by the point generator G, Alice verifies that the obtained ephemeral point can justify the condition. If she can use this ephemeral point, she goes to the fifth step to transmit securely the two parameters. In this phase, we exchange alpha and beta, and we use it to authenticate Alice and Bob at the same phase in one round. The phase 6, both Alice and Bob get the same secret encoding parameters. So they can perform the same mapping table ASCII map with no need to exchange the whole table. In the phase 7, after encoding the input message, Alice can encrypt one by one character and send them to Bob. In the decryption phase, Bob decrypts the message using the public key of Alice to get the encoded message. Finally, to decode and get the clear message, he should match the mapping table until finding the corresponding input message. The main operation to be carried out during a protocol using elliptic curves is the multiplication of a point by a scalar. In our proposed protocol, we utilize two random encoding parameters presented as an affine point on the selected elliptic curve. These encoding parameters are exchanged between Alice and Bob. The generated elliptic encoding point is used to authenticate the two communicating parties in the WSN and to generate the same ASCII-map tables for both Alice and Bob. The authentication phase, performed using Hash and XOR functions, is based on the generated encoding parameters of the current and last sessions to prevent replay and MITM attacks. According to ECDLP, it is computationally difficult for an adversary to obtain the value of ‘ s’ by calculating (α, , and it is also nearly impossible to obtain the value of ‘ r’ where
. Similarly, if an adversary obtains C1 and C2, it is also nearly impossible to discover Bob's private key
and obtain the encoding parameters (α, β).
We use C as a generated one-time password for a single login session. Once used, the password expires and cannot be used for the next log-in session, preventing replay attacks. The computation of h1 using the last session encryption parameters ensures the prevention of MITM attacks, as the receiver can verify the sender's identity using the stored last session encryption parameters from the previous communication session. For the first communication session, the system administrator generates random encoding elliptic curve points corresponding to each sensor in the system. These points are stored in each sensor as an initiator vector for calculating h1. When the sender receives CH1, it can check if the receiver is obtaining the correct encoding elliptic point and verify the receiver's identity by running and checking CH2 using Hash and XOR functions. Thus our proposed scheme presents a lightweight mutual authentication scheme based on the ECEG cryptosystem using our ephemeral encoding method. Each communicating party in the WSN can securely exchange encoding parameters and authenticate at the same time without overloading the bandwidth.
5. Security analysis
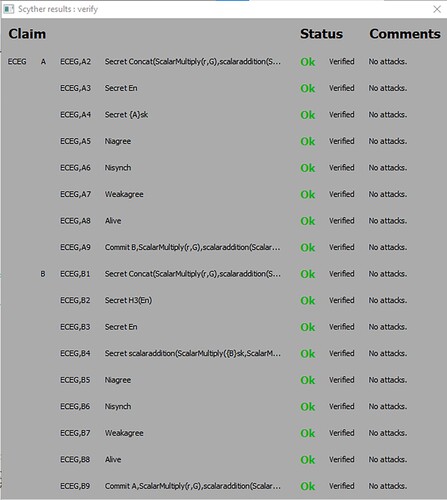
We have used the Scyther tool to check out the formal security of our proposed enhanced ECEG protocol and its robustness against various covert attacks. The Scyther works according to security claims.
5.1. Description of Scyther tool and SPDL
Our proposed scheme enhances the security and guarantees authentication, confidentiality, and integrity. So, to prove the robustness of our new solution, we use an automatic scanning tool. Automatic scanning is the newest approach used in the scanning of security protocol; indeed, all possible attacks will be tested by the tool used. Various tools are used to analyse security protocols and to check for the possibility that an attack may occur when the protocol is used.
Scyther is a GUI-based tool used as security protocol verification automation tool. It can validate protocols with an infinite number of sessions and nonces. In addition, it is able to characterize protocols, producing a finite representation of all possible protocol behaviours (Cremers, Citation2008). Scyther uses a Security Protocol Description Language (SPDL), a Python-like language, for the implementation of the proposed security protocol, which enforces the semantics. The SPDL is used to specify protocol verification regarding security claims. Scyther first attempts to assert the claims defined in the specified protocol; then, it enforces the security claims automatically generated by the Scyther tool; and finally, the complete characterization of the defined roles.
5.2. Formal verification using the Scyther tool
The lightweight mutual authentication protocol based on ECEG has undergone a rigorous security verification process using Scyther. This verification entailed a comprehensive analysis of the protocol's behaviour, focusing on the roles of A (Alice) and B (Bob), and the deployment of a series of critical claims to ensure its security properties.
In the domain of formal verification, the initial and crucial step involves specifying the security properties that the LA-ECEG protocol must exhibit during its execution. In our manuscript, we have meticulously categorized and defined various claims:
Nisynch Claim: This claim ensures the protocol's capacity to effectively manage potential desynchronization issues, adeptly addressing synchronization problems.
Niagree Claim: It guarantees mutual agreement between both parties (Alice and Bob) regarding specific values, safeguarding against unintended alterations and maintaining a consistent stance.
Secret Claim: This claim verifies the confidentiality of sensitive information, including cryptographic keys, encryption parameters, and shared secrets, assuring their inaccessibility to unauthorized entities.
Weak Agreement Claim: It ensures a predetermined level of consensus between the parties, signifying unanimity on specific protocol aspects.
Alive Claim: This claim validates the liveness of the protocol, assuring uninterrupted operation with both parties remaining active participants.
Commit Claim: It affirms the commitment of both Alice and Bob to the values exchanged during protocol execution, with a particular focus on the integrity of key values such as C1 and C2.
The utilization of the Scyther tool for verification encompasses the following aspects:
Scyther employs formal methods, including symbolic analysis and model checking, to comprehensively assess the protocol's security.
It systematically explores potential attack scenarios, encompassing both active and passive attacks, to validate the claims.
Scyther's analysis provides intricate insights into the protocol's resilience against security threats such as replay attacks or man-in-the-middle attacks.
Throughout the verification process, we conducted a meticulous examination of the protocol's behaviour concerning these claims, culminating in a comprehensive assessment of its security properties:
All claims, spanning confidentiality, agreement, liveness, and commitment were successfully verified as ‘OK '.
This rigorous process furnishes substantial evidence supporting the security of the protocol, providing a robust defense against potential threats and attacks.
The outcomes of the verified claims are depicted in , affirming the successful verification of both manually defined and automatically generated claims as ‘OK '. This underscores our unwavering confidence in the protocol's security, demonstrating its resilience against a spectrum of active and passive attacks.
The thorough security verification process, facilitated by the Scyther tool, serves as compelling evidence of the protocol's robustness and resilience. It underscores the protocol's capacity to withstand potential security threats and attacks, instilling a high level of confidence in its ability to meet the desired security requirements.
6. Results and comparison
In this section, we present the implementation details of our proposed enhanced cryptosystem and conduct a thorough analysis of its time complexity in comparison to RSA outputs. We then proceed to compare the efficiency of our protocol with related work on Elliptic Curve Cryptography (ECC) in terms of encryption and decryption time complexity. Additionally, we assess the space complexity of our mutual authentication approach and compare it to related work that utilizes blockchain-based authentication.
Comparing the RSA and ECC algorithms based on their security levels is essential for gaining insights into their practical implementation and cryptographic robustness. Notably, the National Institute of Standards and Technology (NIST) has played a significant role in standardizing ECC and recommending secure elliptic curve fields with finite fields. Our proposed enhanced scheme adheres to NIST recommendations by incorporating elliptic curves such as Secp160r2, Secp224r1, Secp256r1, and Secp384r1. Additionally, we implement the RSA algorithm with varying key sizes ranging from 1024 to 7680 bits.
The choice of key size directly influences the security level provided by a cryptographic algorithm. As a general rule, larger key sizes are recommended as the desired security level increases to ensure an appropriate level of cryptographic strength. Key sizes, typically measured in bits, serve as widely used indicators for the security levels of both symmetric and asymmetric cryptographic algorithms. For instance, in symmetric algorithms like AES, the security level is equal to the key size. In contrast, for asymmetric algorithms like RSA and ECC, the mentioned key sizes correspond to specific security levels. In the context of RSA and ECC, a primary distinction lies in the trade-off between size and cryptographic strength. ECC can offer the same level of cryptographic strength as an RSA-based system but with significantly smaller key sizes. provides a clear demonstration of this comparison, showcasing how ECC key sizes are smaller than RSA key sizes while delivering equivalent security levels (Mahto & Yadav, Citation2017). The security level of the RSA cryptosystem is determined by the difficulty of the integer factorization problem (IFP), whereas the Enhanced ECEG relies on the elliptic curve discrete logarithm problem (ECDLP). ECC's advantage lies in the fact that the best-known algorithm for solving ECDLP requires full exponential time, while solving the IFP of RSA takes sub-exponential time. Furthermore, a literature analysis supports ECC's advantage in terms of space complexity compared to RSA, particularly in memory-constrained devices (Vahdati et al., Citation2019).
Table 2. Key size of RSA and ECC (Mahto & Yadav, Citation2017).
In our implementation, we compare the efficiency of the enhanced ECEG (ECEG with proposed encoding method) algorithm with RSA in terms of time complexity. By examining the time complexity and key sizes of the enhanced ECEG and RSA algorithms, we can evaluate their suitability for various use cases and security requirements. This analysis enables us to make informed decisions about which algorithm to choose based on factors such as performance, security level, and available computational resources.
To perform scalar multiplication, several approaches have been proposed, of which Montgomery's algorithm is the most widely used; as a result, it is going to reduce the time for multiplication and to prevent side-channel attacks (Hao et al., Citation2022). Montgomery's algorithm eliminates the division operation and effectively uses the reduction operation. Moreover, its execution allows to increase the performance of PM because it only uses the x coordinate and removes the y coordinate (Basu Roy & Mukhopadhyay, Citation2019). In our work, we utilize the SHA-2 algorithm as the hash function.
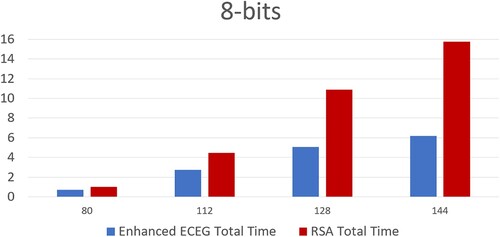
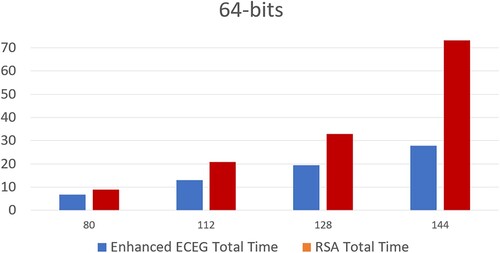
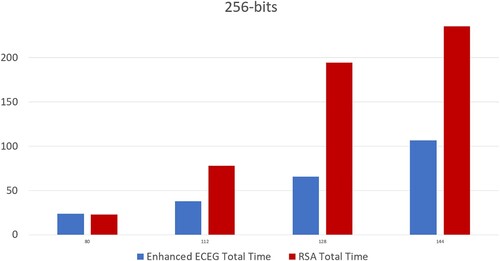
The experiments were conducted on an Intel(R) Core(TM) i7-5600U CPU, Intel 2.60 GHz MHz, with a total physical memory of 8.00 GB, running on the Windows platform. The findings of the first study provide crucial insights into the efficiency of the enhanced ECEG algorithm in comparison to the widely-used RSA algorithm, with a specific focus on time complexity analysis. Through a comprehensive investigation, we conducted a detailed comparison of the time complexities of both algorithms for various input message sizes (8-bit, 64-bit, and 256-bit), as illustrated in , , and , respectively.
The key observation from the time complexity analysis, as presented in , for different security levels (80-, 112-, 128- and 144-bit), is the consistent superiority of the enhanced ECEG algorithm over RSA in terms of both encryption and decryption times. Notably, as the security level increases, the enhanced ECEG algorithm exhibits a substantial reduction in computational time, primarily due to the utilization of shorter key sizes. This highlights the inherent trade-off between key size and computational time, where the enhanced ECEG algorithm's ability to achieve efficient computations with smaller key sizes outperforms RSA.
Table 3. Time complexity analysis of RSA and enhanced ECEG algorithms with 8-bit input (in seconds).
Expanding our evaluation to 64-bit input messages in , we further validate the efficiency of the enhanced ECEG algorithm. Across all security levels examined, it consistently demonstrates lower encryption and decryption times compared to RSA, reaffirming the advantages of using shorter key sizes. This trade-off between key size and computational time becomes even more evident in scenarios where quick decryption is critical, making the enhanced ECEG algorithm an attractive choice for applications requiring efficient data access.
Table 4. Time complexity analysis of RSA and enhanced ECEG algorithms with 64-bit input (in seconds).
Extending the analysis to 256-bit input messages in , we find that the enhanced ECEG algorithm continues to showcase computational superiority over RSA. Despite larger input message sizes, it maintains faster encryption and decryption times, further underscoring the benefits of leveraging shorter key sizes for improved efficiency.
Table 5. Time complexity analysis of RSA and enhanced ECEG algorithms with 256-bit input (in seconds).
Our research highlights the compelling trade-off between key size and computational time offered by the enhanced ECEG algorithm. The ability to achieve faster computations while maintaining a high level of cryptographic strength is particularly advantageous for resource-constrained environments, such as Wireless Sensor Networks (WSNs).
In conclusion, the time complexity analysis consistently demonstrates the efficiency of the enhanced ECEG algorithm compared to RSA, especially in scenarios where faster decryption times and smaller key sizes are desired. This trade-off between key size and computational time has significant implications for cryptographic algorithm selection in practical applications, emphasizing the enhanced ECEG algorithm's potential as an efficient alternative to RSA in security-critical settings. The research results contribute valuable insights and offer new perspectives on the trade-offs involved in cryptographic algorithm design and implementation. Future studies may further explore the practical implications of this trade-off in various cryptographic applications.
In the second study, we extend our comparison to related work in the field of ECC. We benchmark our proposed protocol against a relevant ECC-based implementation (Mahto & Yadav, Citation2017), examining their encryption and decryption time complexities. Compared to the ECC implementation, our enhanced ECEG algorithm demonstrates superior efficiency. and , and provide a comparison between enhanced ECEG and ECC in terms of encryption and decryption time complexity. Our proposed method outperforms the implemented ECC in terms of computational speed for both encryption and decryption operations. Additionally, the proposed encoding method does not significantly impact the overall execution time of the cryptosystem.
Figure 10. ECC (Mahto & Yadav, Citation2017) versus enhanced ECEG with 8 bit computation time.
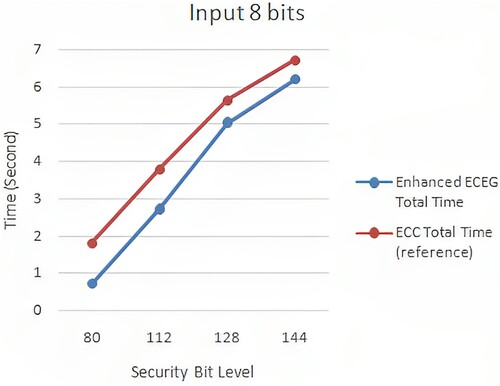
Figure 11. ECC (Mahto & Yadav, Citation2017) versus enhanced ECEG with 64-bit computation time.
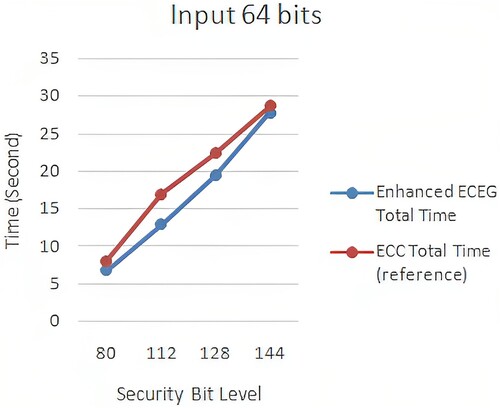
Figure 12. ECC (Mahto & Yadav, Citation2017) versus enhanced ECEG with 256-bit computation time.
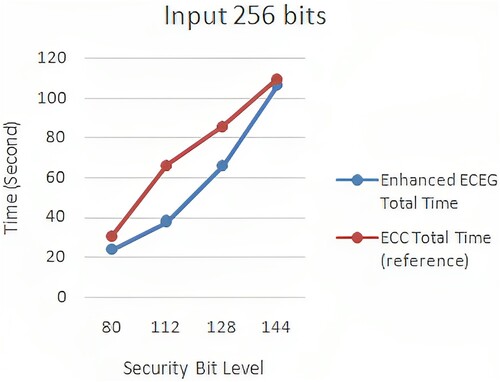
Table 6. Enhanced ECEG and ECC (Mahto & Yadav, Citation2017) with 8-, 64-, and 256-bit time complexity (in seconds).
Furthermore, our enhanced ECEG algorithm enhances the level of security by utilizing ephemeral encoding parameters that are randomly generated for each new communication session. This adds an extra layer of protection against potential attacks.
presents a detailed comparison of enhanced ECEG and ECC in terms of time complexity for different key sizes. The results clearly show that enhanced ECEG achieves lower encryption and decryption times compared to ECC. , , and visually represent the comparison for 8-bit, 64-bit, and 256-bit inputs, respectively. These figures further demonstrate the superior efficiency of enhanced ECEG over ECC.
In conclusion, our enhanced ECEG algorithm emerges as a promising solution for cryptographic operations in WSNs and beyond. The combination of superior efficiency, enhanced security, and mutual authentication capabilities positions our proposed algorithm as a strong contender for secure and lightweight communication in resource-constrained environments.
In the third study, we present , which provides a comprehensive analysis of the time and space complexity of authentication in our proposed scheme based on different ECEG key sizes. The table offers valuable insights into the computational time required for authentication as well as the space cost in bits. The authentication time, measured in seconds, represents the duration taken to complete the authentication process using the corresponding ECEG key size. As the ECEG key size increases, the authentication time generally tends to increase as well. This is demonstrated in the table, where larger key sizes such as Secp384r1 have higher authentication times compared to smaller key sizes like Secp160r2.
Table 7. Time and space complexity of authentication.
The authentication space, measured in bits, indicates the amount of memory required to store the necessary variables during the authentication process. The space cost is calculated by considering the storage requirements for each variable, including C=(C1, C2), h1, and CH1.
For example, for a prime modulus of 160 bits (Secp160r2), the total space cost is 832 bits. This breakdown consists of C requiring 320 bits, h1 requiring 256 bits, and CH1 requiring 256 bits. Similarly, for a prime modulus of 224 bits (Secp224r1), the total space cost is 960 bits, with C requiring 448 bits, h1 requiring 256 bits, and CH1 requiring 256 bits.
In the case of a prime modulus of 384 bits (Secp384r1), the total space cost is 1280 bits, where C requires 768 bits, h1 requires 256 bits, and CH1 requires 256 bits. Finally, for a prime modulus of 256 bits (Secp256r1), the total space cost is 1024 bits, with C requiring 512 bits, h1 requiring 256 bits, and CH1 requiring 256 bits.
These calculations provide valuable insights into the space requirements for storing different variables within the proposed authentication scheme. They allow for an understanding of the memory consumption associated with different ECEG key sizes, aiding in the evaluation and optimization of the overall system's resource utilization. We compare our proposed authentication scheme with the blockchain-based authentication scheme presented in Zheng et al. (Citation2022). In their scheme, the authors analyse the computational and communication requirements by considering various cost factors.
However, it is important to note that the authors of Zheng et al. (Citation2022) do not include the computation time for scalar multiplication in their implementation. Scalar multiplication is a crucial operation in elliptic curve cryptography and has a significant impact on the overall time complexity of the authentication process.
In our proposed scheme, if we consider just the cost of hash functions, we can compare the time complexity in terms of hash operations with the scheme in Zheng et al. (Citation2022) since the authors only consider the cost of hash operations and exclude other operations like scalar multiplication. Our proposed authentication scheme requires four fewer hash operations compared to the blockchain-based solution.
Table 8. Comparison of space and time complexity.
Nonetheless, it is worth noting that blockchain technology offers several advantages for authentication, including increased security, privacy, transparency, and user control. By leveraging the unique features of blockchain, authentication processes can become more reliable, efficient, and resistant to attacks. Therefore, we acknowledge the potential of optimizing our solution by incorporating blockchain technology to further enhance security and efficiency.
In terms of space complexity, our proposed scheme outperforms the scheme presented in Zheng et al. (Citation2022). As shown in , our scheme has a space complexity of 1024 bits, while the scheme in Zheng et al. (Citation2022) requires a space complexity of 2357 bits. These results clearly demonstrate that our proposed scheme offers more efficient resource utilization by requiring less space to store authentication-related information.
Considering the limitations in the analysis of time complexity in Zheng et al. (Citation2022), we emphasize the efficiency of our proposed authentication scheme in terms of reduced space requirements. As we explore the potential of integrating blockchain technology into our solution, we aim to further optimize the scheme and leverage the benefits offered by blockchain for enhanced security and efficiency in authentication processes.
7. Conclusion
In this paper, we present a lightweight authentication scheme based on the Elliptic Curve ElGamal cryptosystem, which incorporates ephemeral encoding parameters. The effectiveness and robustness of our proposed method are confirmed through validation using the Scyther verification tool. A comprehensive security analysis is conducted to compare our enhanced ECEG with RSA and related ECC implementations, revealing that our protocol outperforms these alternatives in terms of time complexity.
Additionally, we assess the space complexity of our authentication method in comparison to a blockchain-based authentication approach. The results unequivocally show that our proposed scheme utilizes resources more efficiently, requiring less space to store authentication-related information.
Overall, our proposed scheme significantly enhances WSN security by implementing ephemeral encoding parameters for authentication without compromising computation time. These findings highlight the practicality and effectiveness of our lightweight authentication solution, positioning it as a promising choice for secure communication in resource-limited environments.
Lightweight Authentication Scheme Based on Elliptic Curve El Gamal v2 23 09 23.tex
Download Latex File (93.6 KB)Disclosure statement
No potential conflict of interest was reported by the author(s).
References
- Alamr, A. A., Kausar, F., Kim, J., & Seo, C. (2018). A secure ECC-based RFID mutual authentication protocol for internet of things. The Journal of Supercomputing, 74(9), 4281–4294. https://doi.org/10.1007/s11227-016-1861-1
- Al-shabi, M. A. (2019). A survey on symmetric and asymmetric cryptography algorithms in information security. International Journal of Scientific and Research Publications (IJSRP), 9(3), 576–589. (ISSN: 2250-3153). http://doi.org/10.29322/IJSRP.9.03.2019.p8779
- Baccouri, S., Fatrhat, H., Gharbi, N., Tahar, R., Azzabi, T., & Attia, P. R. (2022). Ephemeral encoding message in the elliptic curve cryptography for IoT. In 2022 5th international conference on advanced systems and emergent technologies (IC_ASET) (pp. 172–177). http://doi.org/10.1109/IC_ASET53395.2022.9765938
- Basu Roy, D., & Mukhopadhyay, D. (2019). High-speed implementation of ECC scalar multiplication in GF(p) for generic montgomery curves. IEEE Transactions on Very Large Scale Integration (VLSI) Systems, 27(7), 1587–1600. http://doi.org/10.1109/TVLSI.2019.2905899
- Benssalah, M., Sarah, I., & Drouiche, K. (2021). An efficient RFID authentication scheme based on elliptic curve cryptography for internet of things. Wireless Personal Communications, 117(3), 2513–2539. http://doi.org/10.1007/s11277-020-07992-x
- Chen, C. M., Liu, S., Li, X., Kumari, S., & Li, L. (2022). Design and analysis of a provable secure two-factor authentication protocol for internet of things. Security and Communication Networks, 2022. http://doi.org/10.1155/2022/4468301
- Chien, H.-Y. (2017). Elliptic curve cryptography-based RFID authentication resisting active tracking. Wireless Personal Communications, 94(4), 2925–2936. https://doi.org/10.1007/s11277-016-3756-0
- Cremers. (2008). The Scyther tool verification, falsification, and analysis of security protocols. In International conference on computer-aided verification (pp. 414–418). Springer.
- Cremers. (2012). Scyther: Semantics and verification of security protocols. Eindhoven University of Technology.
- Dinarvand, N., & Barati, H. (2019). An efficient and secure RFID authentication protocol using elliptic curve cryptography. Wireless Networks, 25(1), 415–428. https://doi.org/10.1007/s11276-017-1565-3
- Elias, E. P., Santhanavijayan, A., Janet, B., & Arul, K. R. J. (2022). OTP system based on ECC key exchange. In 2022 International conference on communication, computing and internet of things (IC3IoT), Chennai, India (pp. 1–6). http://doi.org/10.1109/IC3IOT53935.2022.9768019
- Fang, W., Zhang, W., Chen, W., Pan, T., Ni, Y., & Yang, Y. (2020). Trust-based attack and defense in wireless sensor networks: A survey. Wireless Communications and Mobile Computing, 2020, 1–20. https://doi.org/10.1155/2020/2643546
- Hammi, B., Fayad, A., Khatoun, R., Zeadally, S., & Begriche, Y. (2020). A lightweight ECC-based authentication scheme for internet of things (IoT). IEEE Systems Journal, 14(3), 3440–3450. http://doi.org/10.1109/JSYST.2020.2970167
- Hao, Y., Zhong, S. A., Ma, M., Jiang, R., Huang, S., Zhang, J., & Wang, W. (2022). Lightweight architecture for elliptic curve scalar multiplication over prime field. Electronics, 11(14), 2234. http://doi.org/10.3390/electronics11142234
- Ibrahim, A., & Dalkılıç, G. (2017). An advanced encryption standard powered mutual authentication protocol based on elliptic curve cryptography for RFID, proven on WISP. Journal of Sensors, 2017, 1–10. http://doi.org/10.1155/2017/2367312
- Islam, M. M., Hossain, M. S., Hasan, M. K., Shahjalal, M., & Jang, Y. M. (2020). Design and implementation of high-Performance ECC processor with unified point addition on twisted Edwards curve. Sensors (Basel), 20(18), 5148. PMID: 32927594; PMCID: PMC7571177. http://doi.org/10.3390/s20185148
- Kaur, S., Kaur, G., & Shabaz, M. (2022). A secure two-factor authentication framework in cloud computing. Security and Communication Networks, 2022, 1–9. http://doi.org/10.1155/2022/7540891
- Khan, M. A., Quasim, M. T., Alghamdi, N. S., & Khan, M. Y. (2020). A secure framework for authentication and encryption using improved ECC for IoT-based medical sensor data. IEEE Access, 8, 52018–52027. http://doi.org/10.1109/ACCESS.2020.2980739
- Kumari, A., Jangirala, S., Abbasi, M. Y., Kumar, V., & Alam, M. (2019). ESEAP: ECC based secure and efficient mutual authentication protocol using smart card. Journal of Information Security and Applications, 51, 102443. http://doi.org/10.1016/j.jisa.2019.102443
- Kumari, A., Yahya Abbasi, M., Kumar, V., & Khan, A. A. (2019). A secure user authentication protocol using elliptic curve cryptography. Journal of Discrete Mathematical Sciences and Cryptography, 22(4), 521–530. http://doi.org/10.1080/09720529.2019.1637155
- Lamrani Alaoui, H., El Ghazi, A., Zbakh, M., Touhafi, A., & Braeken, A. (2021). A highly efficient ECC-based authentication protocol for RFID. Journal of Sensors, 2021, 1–16. http://doi.org/10.1155/2021/8876766
- Lara-Nino, C. A., Diaz-Perez, A., & Morales-Sandoval, M. (2018). Elliptic curve lightweight cryptography: A survey. IEEE Access, 6, 72514–72550. http://doi.org/10.1109/ACCESS.2018.2881444
- Li, X., Peng, J., Niu, J., Wu, F., Liao, J., & Choo, K. R. (2018, June). A robust and energy efficient authentication protocol for industrial internet of things. IEEE Internet of Things Journal, 5(3), 1606–1615. http://doi.org/10.1109/JIOT.2017.2787800
- Liao, Y. P., & Hsiao, C. M. (2014). A secure ECC-based RFID authentication scheme integrated with ID-verifier transfer protocol. Ad Hoc Networks, 18, 133–146. https://doi.org/10.1016/j.adhoc.2013.02.004
- Liu, G., Zhang, H., Kong, F., & Zhang, L. (2018). A novel authentication management RFID protocol based on elliptic curve cryptography. Wireless Personal Communications, 101(3), 1445–1455. https://doi.org/10.1007/s11277-018-5771-9
- Mahto, D., & Yadav, D. K. (2015). Enhancing security of one-time password using elliptic curve cryptography with biometrics for e-commerce applications. In Proceedings of the 2015 third international conference on computer, communication, control and information technology (C3IT) (pp. 1–6). http://doi.org/10.1109/C3IT.2015.7060172
- Mahto, D., & Yadav, D. K. (2017). RSA and ECC: A comparative analysis. International Journal of Applied Engineering Research, 12(19), 9053–9061.
- Mallouli, F., Hellal, A., Saeed, N. S., & Alzahrani, F. A. (2019). A survey on cryptography: Comparative study between RSA vs ECC algorithms, and RSA vs El-Gamal algorithms. In 2019 6th IEEE International conference on cyber security and cloud computing (CSCloud)/ 2019 5th IEEE international conference on edge computing and scalable cloud (EdgeCom) (pp. 173–176). IEEE.
- Mohamed, M. A. (2014). A survey on elliptic curve cryptography. Applied Mathematical Sciences, 8, 7665–7691. https://doi.org/10.12988/ams.2014.49752
- Naeem, M., Chaudhry, S. A., Mahmood, K., Karuppiah, M., & Kumari, S. (2020). A scalable and secure RFID mutual authentication protocol using ECC for internet of things. International Journal of Communication Systems, 33(13), e3906. https://doi.org/10.1002/dac.v33.13
- Nikooghadam, M., & Amintoosi, H. (2019). A secure and robust elliptic curve cryptography–based mutual authentication scheme for session initiation protocol. Security and Privacy, 3(1), e92. http://doi.org/10.1002/spy2.92
- Noori, D., Shakeri, H., & Niazi Torshiz, M. (2022). An elliptic curve cryptosystem-based secure RFID mutual authentication for internet of things in healthcare environment. EURASIP Journal on Wireless Communications and Networking, 2022(1), 64. http://doi.org/10.1186/s13638-022-02146-y
- Panja, A., Mondal, S., Islam, K. A., Ghosh, T. K., & Karforma, S. (2022). An efficient and secure fingerprint based authentication scheme using elliptic curve cryptography. Webology (ISSN: 1735-188X), 19(2). https://www.webology.org/.
- Qiu, S., Xu, G., Ahmad, H., & Guo, Y. (2018). An enhanced password authentication scheme for session initiation protocol with perfect forward secrecy. PLoS One, 13(3), e0194072. PMID: 29547619; PMCID: PMC5856360. http://doi.org/10.1371/journal.pone.0194072
- Ramasamy, P., Ranganathan, V., Palanisamy, V., & Kadry, S. (2020). Securing one-time password generation using elliptic-curve cryptography with self-portrait photograph for mobile commerce application. Multimedia Tools and Applications, 79(23-24), 17081–17099. http://doi.org/10.1007/s11042-019-7615-3
- Sadhukhan, D., Ray, S., Biswas, G. P., Khan, M. K., & Dasgupta, M. (2020). A lightweight remote user authentication scheme for IoT communication using elliptic curve cryptography. The Journal of Supercomputing, 77(2), 1114–1151. https://doi.org/10.1007/S11227-020-03318-7
- Sadri, M. J., & Asaar, M. R. (2021). An anonymous two-factor authentication protocol for IoT-based applications. Computer Networks, 199, 108460. https://doi.org/10.1016/j.comnet.2021.108460
- Sowjanya, K., Dasgupta, M., & Ray, S. (2021). Elliptic curve cryptography based authentication scheme for internet of medical things. Journal of Information Security and Applications, 58, 102761. http://doi.org/10.1016/j.jisa.2021.102761
- Sravana Kumar, Suneetha, ChandrasekhAR (2012). Encryption of data using elliptic curve over finite fields. International Journal of Distributed and Parallel Systems , 3(1).
- Sridevi, R. (2020). Checking user authentication by biometric one time password generation using elliptic curve cryptography.
- Standards for efficient cryptography group (2000, September). Recommended elliptic curve domain parameters, SEC 2.
- Vahdati, Z., Yasin, S., Ghasempour, A., & Salehi, M. (2019). Comparison of ECC and RSA algorithms in loT devices. Journal of Theoretical and Applied Information Technology, 97(16), 4293.
- VenkataGiri, J., & Murty, A. (2021). Elliptic curve cryptography design principles. In 2021 International conference on recent trends on electronics, information, communication & technology (RTEICT) (pp. 889–893). http://doi.org/10.1109/RTEICT52294.2021.9573662
- William, S. (2006). Cryptography and network security-principle and practices, elliptic curve cryptography (4th ed., pp. 310–313). PHI Publisher.
- Xue, K., Ma, C., Hong, P., & Ding, R. (2013). A temporal-credential-based mutual authentication and key agreement scheme for wireless sensor networks. J Netw Comput Appl, 36(1), 316–323. https://doi.org/10.1016/j.jnca.2012.05.010
- Yan, S. C., Wei, A. T., Bong, J. H., Teh, Q. L., Sivalingam, S., Khoo, S. Y., & Nafy, T. M. (2021). Authentication of loT device with the enhancement of one-time password (OTP). Journal of IT in Asia, 9(1), 29–40. http://doi.org/10.33736/jita.3841.2021
- Zhang, Q. (2021, January). An overview and analysis of hybrid encryption: The combination of symmetric encryption and asymmetric encryption. In 2021 2nd International conference on computing and data science (CDS) (pp. 616–622). IEEE. http://doi.org/10.1109/CDS52072.2021.00111
- Zhao, Z. (2014). A secure RFID authentication protocol for healthcare environments using elliptic curve cryptosystem. Journal of Medical Systems, 38(5), 46. https://doi.org/10.1007/s10916-014-0046-9
- Zheng, J., Wang, X., Yang, Q., Xiao, W., Sun, Y., & Liang, W. (2022). A blockchain-based lightweight authentication and key agreement scheme for internet of vehicles. Connection Science, 34(1), 1430–1453. http://doi.org/10.1080/09540091.2022.2032602