?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.ABSTRACT
In today's social networking era, information security breaches are at an all-time high, especially when it comes to texts and images, which should come as no surprise. Integrity is therefore crucial for information sharing over an unprotected connection. As a result, image/text encryption is a crucial preprocessing step in today's information transmission. Sensitive information may be sent via image encryption, which facilitates a variety of procedures. Here the proposed method is a combination of the Modified Caesar Cipher and the Card Deck Shuffle Algorithm for image encryption. The Card Deck Shuffle Algorithm rearranges the pixels from the result of the Modified Caesar approach, which encrypts the pixel value of each image. The method employs an n + 8 variable bit key (n is frequently more than 18 in real-world applications), which needs more than brute force attacks to be successful. The method described here may be used to secure images in a variety of multimedia applications.
1. Introduction
Data and communication are the core of our world in the twenty-first century. Sensitive information in the data has to be secured. Data is transformed into an unreadable format utilizing a variety of approaches in the field of cryptography to preserve data privacy. Images play a key role in the daily millions of multimedia exchanges. To transmit sensitive data securely, including images and videos, image encryption has emerged as a key subject.
Some strategies used to secure images and data privacy include encryption and data-hiding methods like steganography. Numerous academics have contributed several image encryption algorithms, each with its special principles, effectiveness, operating ranges, and application fields. There are several widely used methods for encrypting images and videos that are now available. Image encryption is used in the commercial world, the medical field, the military, and multimedia systems.
With varied principles, effectiveness, working scopes, and application fields in mind, several researchers have contributed several alternative image encryption techniques. Various standard algorithms are already available that apply to images and videos in order to encrypt them efficiently as can be seen in Chakraborty et al. (Citation2016), Liu et al. (Citation2014), Mohammad et al. (Citation2017), Cheng et al. (Citation2000), Zhang (Citation2016), Seal et al. (Citation2017), and Ye (Citation2011). DES (Standard, Citation1977), AES (Naim & Ali Pacha, Citation2021; Raja & Suruliandi, Citation2018; Sanchez-Avila & Sanchez-Reillol, Citation2001), IDEA (Leong et al., Citation2000), RSA, and Hill Cipher are examples of conventional algorithms and their modifications (Yang et al., Citation2019). However, as Wadi and Zainal (Citation2014) noted, because of their time complexity and pattern appearance, these approaches are not the best choice for image encryption. Methods have also been proposed which implement Chaotic Logistic Maps (Mandal et al., Citation2012) and DNA cryptography (Akkasaligar & Biradar, Citation2020) Another field that is utilized in the development of image compression and encryption algorithms is deep learning. Few of these works include Maniyath and Thanikaiselvan (Citation2020), Hu et al. (Citation2016), Hu et al. (Citation2017), and Anh et al. (Citation2017).
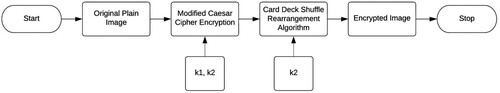
The paper introduces and examines a new efficient and safe image encryption technology. In contrast to the examples mentioned before, this method is simple and lightweight across all of its stages making it robust and effective. The proposed algorithm in this paper employs Caesar Cipher concepts as well as a newly suggested scrambling technique known as the Card Deck Shuffle Rearrangement. The proposed methodology can be seen in . Previously modifications to Caesar Cipher have been proposed like using different key for odd and even index of pixel numbers (Goyal & Kinger, Citation2013), generating random numbers for key generation (Srikantaswamy & Phaneendra, Citation2012) or doing double substitution (Dar, Citation2014). But the modified Caesar Cipher proposed in this algorithm uses a replacement approach that replaces the value of each succeeding pixel with a different value leading to better encryption. For scrambling, transposition techniques like rail fence Cipher (Siahaan, Citation2017; Talbert, Citation2006), columnar Transposition (Lasry et al., Citation2016), Double Transposition and their improvements (Godara et al., Citation2018; Ritter, Citation1991) have been previously proposed. The Card Deck Shuffle Rearrangement Algorithm proposed in this paper is a new transposition technique based on how cards are shuffled in a deck using the riffle shuffle method. As sub-decks of a deck are made for the riffle shuffle, a number of subsets of pixels are formed, and the pixels are then rearranged according to these subsets. The method scrambles the pixels of the image efficiently and thus makes the encrypted image resistant to brute force attacks. Caesar Cipher has been combined with other Ciphers as seen in Saini (Citation2015), Shrivastava et al. (Citation2013), and Qowi and Hudallah (Citation2021) making the overall algorithm more efficient. Similar is the case in the proposed method which combines the above proposed two algorithms in order to provide better encryption.
The rest of the paper is organized as follows: Section 2 covers Key Extraction. Section 3 contains the Modified Caesar approach. The Card Deck Shuffle Rearrangement Algorithm has been discussed in Section 4. Section 5 contains the experimental setup used to perform encryption and decryption. The results achieved from them are discussed in Section 6. Section 7 concludes the paper and various references are provided.
2. Related works
In ‘Modified Caesar Cipher with Image Steganography’, Srivastava et al. (Citation2023) and Deshpande et al. (Citation2023) propose two different methods for encryption. the first one uses Caesar Cipher technique with image steganography. The image is encrypted first and then stored in the pixels of an image to increase the security. In the second method, a third level of security is added. The message's encoded image is linked by the sender to a security key which can be n-digits long. The receiver also receives the key along with the image and if it matches the sender's key, then the image is decoded.The amalgamation of Caesar Cipher and steganography will provide a safe medium for transmitting and storing data.
In ‘Image Encryption Using RSA and Advanced Caesar Cipher Method’, Maity et al. (Citation2022) propose a method which leverages the advantages of symmetric and asymmetric key cryptography. For the symmetric part RSA encryption with 64-bit plaintext and key is used. For the asymmetric part Modified Caesar Cipher based on the formula CT = (CT+k)mod26 is used where k is generated randomly within the range 0 to 108. The pixel values are first encrypted using RSA and then concatenating with random values and then it is given to modified Caesar Cipher for further encryption. PSNR and entropy yesting results suggested that the proposed methodology work with great accuracy.
Rachmawati et al. (Citation2019) and Osman et al. (Citation2019) propose a new methodology which employs various encryption techniques. First encrypt the images using the Columnar Transposition Cipher algorithm then encrypt the file using the Caesar Cipher algorithm utilizing a customized combination of and Linear Congruential generators. Subsequently, Lempel Ziv Welch, will next be used to compress the encrypted image file. The findings of this study demonstrated that the secrecy, integrity, and security of data could be maintained by combining the above mention techniques.
In ‘A novel image encryption algorithm based on chaotic shuffling method’, Wang et al. (Citation2017) suggest a brand-new image encryption algorithm that uses a chaotic shuffling-diffusion technique. First, the row coordinates of the image's jumbled pixels are labelled using a chaotic sequence produced by a first logistic map. Second, the column coordinates of the pixels in the jumbled image are labelled using a second logistic map. Then, we may achieve the effect of scrambling the image by shifting the position of pixels using our novel pixel exchange model that we have developed. Third, a third logistic map creates a matrix the same size as the simple image in order to expand the key space according to MOD operation and XOR operation alone.The results show that this algorithm has properties of big key space, high sensitivity to key, and less prone to different attacks, thus providing higher security and is viable for image encryption.
‘In The image encryption algorithm with plaintext-related shuffling’ Zhang (Citation2016) proposes a new image encryption system that uses a hyper-chaotic system to generate secret code streams for encryption. The system has desirable features such as fast encryption speed, large key space, high key sensitivity, and effective resistance to differential attacks. The Cipher-text image is noise-like, making it suitable for use in actual communications.
3. Key extraction
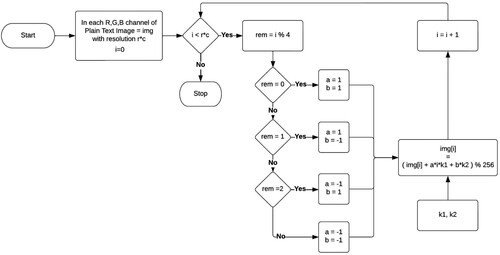
This is the first step of the proposed algorithm. This algorithm uses a n + 8 variable bit size key. The first n bits and the last 8 bits of the key are divided into 2 separate keys and
. The decimal value of n can be anywhere between 2 to s, where is the size of the channel or the total number of pixels in the channel which is given by r*c.
can have 256 values, that is, it can be any number between 0 to 255 hence the 8 bits.
Algorithm 1. Key Extraction Algorithm
4. Modified Caesar Cipher encryption
This is the second step of the proposed algorithm. The Caesar Cipher is named after Julius Caesar who, according to Suetonius, employed it with a three-shift to safeguard communications of military importance. A Caesar Cipher, also known as Caesar's Cipher, shift Cipher, Caesar's code, or Caesar shift in cryptography, is one of the most basic and well-known encryption techniques. It's a substitution Cipher in which each letter in the plaintext is replaced with a letter that's a certain number of places down the alphabet. With a left shift of 3, for example, D would become A, E would become B, and so on. While considering RGB images, The Classic Caesar Cipher shifts the intensity of a pixel up by a certain number denoted by the key. It is given by Equation (Equation1(1)
(1) )
(1)
(1)
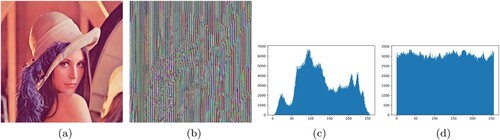
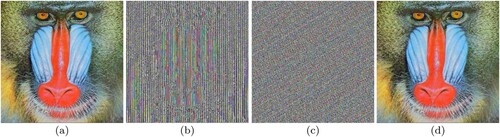
When the classic Caesar encryption method is used to encrypt images, it is found that the images are not properly encrypted. This can be seen in and when each pixel of the original baboon and lena image was shifted up by a random key value. The histograms of both can be compared and it is observed in the classic Caesar encryption that the histogram has merely shifted and overall hasn't changed at all.
Figure 2. Classic Caesar Cipher encryption on Baboon image, (a) Original Baboon image, (b) Encrypted Baboon image, (c) Original Baboon image histogram, (d) Encrypted Baboon image histogram.
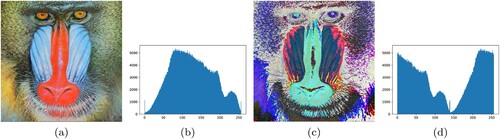
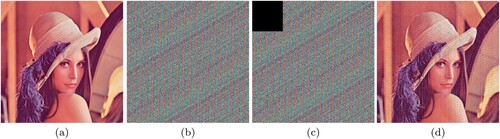
Figure 3. Classic Caesar Cipher encryption on Lena image, (a) Original Lena image, (b) Encrypted Lena image, (c) Original Lena image histogram, (d) Encrypted Lena image histogram.
Thus to make the encryption more efficient, it was required to shift the value of each pixel by a variable number. Because each pixel's value will be altered differently in the proposed methodology, it is a modified form of the Caesar Cipher. To make this possible both the keys and
which were extracted from the main key are utilized to shift the value of each subsequent pixel by a variable value. This value and the new pixel value is given in Equation (Equation2
(2)
(2) )
(2)
(2) where, a and b coefficient values are:
where, i = index of that pixel in RGB channel
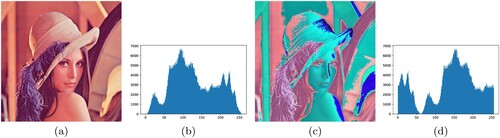
Thus due to this modified Caesar Cipher, the encrypted image cannot be deciphered easily. The contrast of both the original Baboon and Lena images has very high disparity and variance. This can be seen in and . Unlike the histograms of classic Caesar encryption, the histograms of modified Caesar encryption have overall completely changed in terms of values and their frequencies. The histograms are also not biased towards any particular frequency, i.e. they do not have an obvious mode present. Thus due to this modification, each pixel value has more or less the same frequency.
Figure 4. Modified Caesar Cipher encryption on Baboon and Lena image, (a) Original Baboon image, (b) Encrypted Baboon image, (c) Original Baboon image histogram, (d) Encrypted Baboon image histogram.
Algorithm 2. Modified Caesar Cipher Algorithm
As this was the first stage, now this encrypted image will be passed on to the next stage i.e. to the Card Deck Shuffle Rearrangement Algorithm for scrambling. .
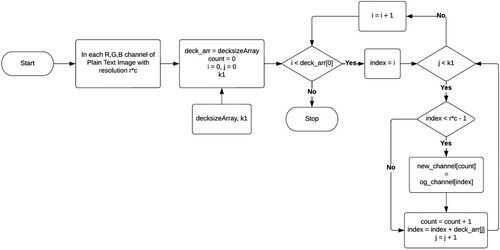
5. Card Deck Shuffle Rearrangement
This is the final stage of the encryption process (). This algorithm is a form of transposition Cipher used for rearrangement of pixel values. The previous stage of modified Caesar encryption was able to encrypt the image pretty well but to make the overall algorithm even stronger, it is required to now scramble the pixels. This double encryption greatly increases data security. Moreover, the double-stage encryption would also require double-stage decryption, making it more difficult for attackers to decipher the contents of the image.
Transposition Cipher: A transposition Cipher is a form of encryption in which the locations of plaintext units (which are frequently letters or groups of characters) which are pixels in the algorithm's use-case, are moved according to a regular scheme, such that the Ciphertext is a permutation of the plaintext. That is, the order of the units is altered (the plaintext is reordered).
This algorithm is based on how a deck of cards is shuffled using the riffle shuffle. While playing cards, the deck of cards is usually shuffled with various techniques. One such popular technique is the riffle shuffle. In this, the deck is cut and divided into two smaller decks or sub-decks, mainly the upper half and lower half. Then Half of the deck is held in each hand with the thumbs inside, then the cards are released by the thumbs so that they fall interleaved to the table. So cards of each deck are stacked alternately. .
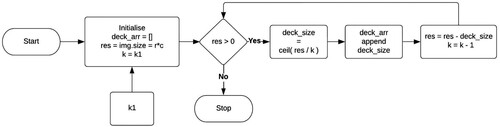
The method proposed in this paper deals with images. Each pixel of the image can be considered as a card, so the entire image becomes the deck. The algorithm will not be limiting itself to just two sub-decks and rearranging. There can be n number of sub-decks where n is any number between 2 and the total number of pixels – 1. This brings us to the first key i.e. which was extracted from the main key. This key signifies the number of sub-decks in which the image is desired to be divided for the shuffling to take place.
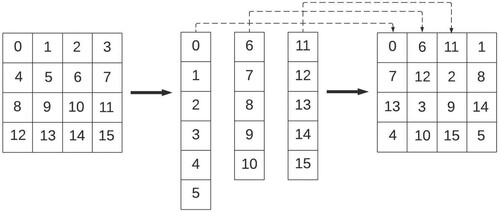
An example to understand this is given in . In the example, an image has been considered consisting of 16 pixels with dimensions 4 * 4. The value of in the example has been taken as 3. This means that the algorithm will divide the image into 3 sub-decks for the rearrangement to take place. To proceed further the algorithm will now calculate the sub-deck array or the decksize array. The decksize array is an array that contains the deck size or the number of pixels each of the decks will contain. Now the question arises: what is the need for this special array? The answer is that the size or the no of pixels in the image won't always be perfectly divisible by the no of decks that are desired. In the example, the 16 pixel image is to be divided into 3 sub-decks. Thus obviously all decks won't be of equal size, there will be a difference of 1 in some decks to cover all the pixels in the image. Therefore the decksize array for the example is : decksizeArray = [6, 5, 5]. .
Algorithm 3. Decksize Array Calculation Algorithm
Thus each index of the decksize array will give us the value of how many maximum pixels will be there in that single deck. For the 16-pixel image and k1 = 3, and , the first sub-deck of 6 pixels is created followed by 2 sub-decks of 5 pixels each. This can again be seen in . So the first sub-deck consists of pixels indexed from 0 to 5, the second sub-deck of pixels of index 6 to 10, and the 3rd and final sub-deck of pixels of index 11 to 15.
Now comes the rearrangement part where the sub-decks are riffle shuffled. Thus, the algorithm picks the first pixels of each sub-decks and places them consecutively, so the pixel of index 0 i.e. the first pixel of sub-deck 1, then the pixel of index 6 i.e. first pixel of sub-deck 2, and then the pixel of index 11 i.e. first pixel of sub-deck 3 is placed in the encrypted image. Then it picks the 2nd pixels of each sub-deck and places them after that. It continues in this manner until all sub-decks have been covered. With the decksize array, the algorithm can now skip to indices whose pixels are to be inserted in the new array. For example, if it starts at 0 in the first iteration, it will move to 0+6, which is the sixth index, then 6+5, which is the eleventh index. As a result, the old array's 0,6,11 index will be equal to the new array's 0,1,2 index. Thus, the final picture in obtained as shown in .
It can see that the pixels have been evenly distributed which means that pixels with a particular range of indices are not clustered in one particular region but are spread out throughout the entire encrypted image thus giving much better scrambling. In real life nowadays, images easily have a resolution of a few hundred pixels. This gives a person freedom to choose the desired number of sub-decks from a large range of values, thus having a large number of rearrangements possible in stage 2 after stage 1.
Algorithm 4. Decksize Array Calculation Algorithm
6. Experimentation and results
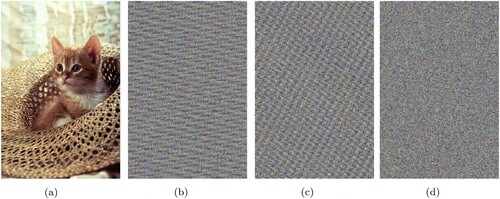
The outcomes and analysis of the results when various images were encrypted and decrypted using the proposed algorithm are presented in this section. In , , , , and the implementation results with not only the final encrypted image, but with also the mid stage encrypted image right after the modified Caesar encryption is performed can be seen. The images which are used for implementation and testing are of various colours and size and are standard images which include baboon, lena, cat, peppers, tulips and house. Not only does the final encrypted image look very noisy, but in no way can the original image be deciphered by just looking as the encrypted one. This hence indicates the success of the proposed algorithm.
Figure 10. (a) Original Peppers image, (b) Image after Modified Caesar Cipher encryption, (c) Final encrypted image after Card Deck Shuffle Rearrangement, (d) Decrypted image.
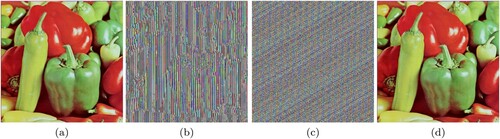
Figure 11. (a) Original Tulips image, (b) Image after Modified Caesar Cipher encryption, (c) Final encrypted image after Card Deck Shuffle Rearrangement, (d) Decrypted image.

Figure 12. (a) Original Cat image, (b) Image after Modified Caesar Cipher encryption, (c) Final encrypted image after Card Deck Shuffle Rearrangement, (d) Decrypted image.
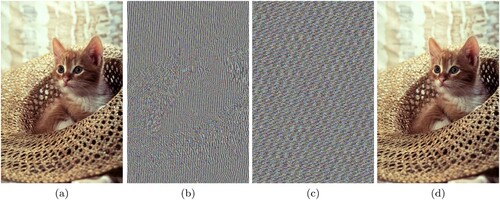
Figure 13. (a) Original House image, (b) Image after Modified Caesar Cipher encryption, (c) Final encrypted image after Card Deck Shuffle Rearrangement, (d) Decrypted image.
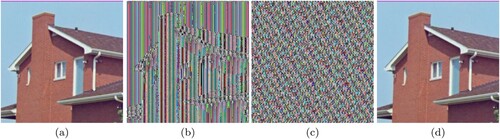
Figure 14. (a) Original Lena image, (b) Image after Modified Caesar Cipher encryption, (c) Final encrypted image after Card Deck Shuffle Rearrangement, (d) Decrypted image.
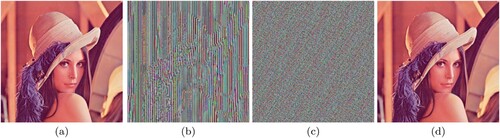
Figure 15. (a) Original Baboon image, (b) Image after modified Caesar Cipher encryption, (c) Final encrypted image after Card Deck Shuffle Rearrangement, (d) Decrypted image.
The following subsections will discuss the results in terms of various security aspects and tests against which the algorithm is assessed.
6.1. Analysis of time complexity
Let the image's resolution be R * C, where R and C are the number of rows and columns of pixels, and let the number of channels, or depth, be D. In the first step, the algorithm applies the modified Caesar Cipher to each pixel of the image. So, it goes through each channel's pixel value. So the time for traversal is O(R*C*D), and the time for substitution is O. (1). The second and last step is rearranging the cards in the deck. In this case, too, the algorithm goes through each pixel and moves it to a different index. This is how the encrypted image is made. So the time to move each pixel is O(R*C*D), and the time to move each pixel is O. (1).
So, the total amount of time it takes to run the algorithm is O(2*R*C*D).
6.2. Histogram analysis
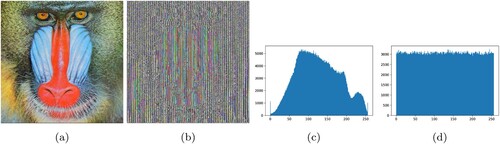
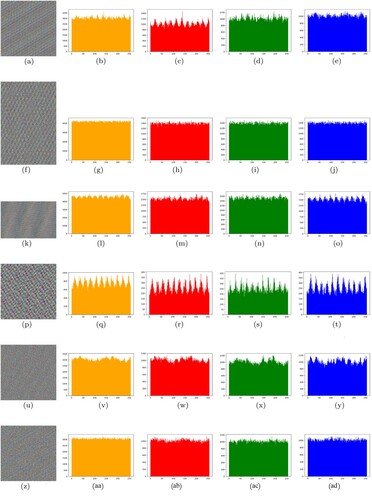
The intensity distribution of an image may be understood using the histogram of that image. The number of pixels at each intensity level is graphically represented by histograms. A simple image's normal intensity distribution typically has peaks and valleys in its histogram, which might cause the information to leak. The attacker may use this information leak to conduct statistical assaults on the image. Thus, the encrypted image must have a histogram with a uniform intensity distribution in order to defend against different statistical attacks.
displays the histograms of several plain images and the corresponding encrypted images that were produced using the proposed algorithm. It can be seen that the distribution of all the encrypted photos is overall uniform. As a result, there will be little information leakage and encrypted images will be protected from different statistical assaults.
Figure 16. Image encryption results by applying modified Caeser Cipher and Card Deck Shuffle rearrangement algorithm. Histograms are for the entire image. (a) Encrypted Peppers image. (b) Overall Histogram of (a). (c) Histogram of Red Channel of (a). (d) Histogram of Green Channel of (a). (e) Histogram of Blue Channel of (a). (f) Encrypted Cat image. (g) Overall Histogram of (f). (h) Histogram of Red Channel of (f). (i) Histogram of Green Channel of (f). (j) Histogram of Blue Channel of (f). (k) Encrypted Tulips image. (l) Overall Histogram of (k). (m) Histogram of Red Channel of (k). (n) Histogram of Green Channel of (k) (o) Histogram of Blue Channel of (k). (p) Encrypted House image. (q) Overall Histogram of (p). (r) Histogram of Red Channel of (p). (s) Histogram of Green Channel of (p). (t) Histogram of Blue Channel of (p). (u) Encrypted Lena image. (v) Overall Histogram of (u). (w) Histogram of Red Channel of (u). (x) Histogram of Green Channel of (u). (y) Histogram of Blue Channel of (u) (z) Encrypted Baboon image. (aa) Overall Histogram of (z). (ab) Histogram of Red Channel of (z). (ac) Histogram of Green Channel of (z) and (ad) Histogram of Blue Channel of (z).
6.3. Analysis of the keyspace and its security implications
The keyspace of an algorithm is the total number of possible key values and their permutations that can be used to encrypt an image. The algorithm proposed in this paper uses a two-part, n + 8-bit main key. The primary key is partitioned into subkeys (n bits) and
(8 bits) that are utilized independently throughout the algorithm. The keyspace of key
, represented by the value n, is dependent on the total number of pixels in the image. If the image dimensions are R and C, then n represents the minimum number of bits required to represent the total number of pixels in binary. Thus, the total possible values for the key
is
. The size of
is fixed at 8 bits because it represents any binary number between 0 and 255, thus 256 values. Thus, the total possible values for key
is
.
A brute-force attack can be thwarted if the keyspace is sufficiently large and the algorithm offers sufficient variations to generate more potential outcomes than the attacker can traverse. The proposed methodology makes use of 2 keys which are used in the 2 stages, and the main key used has a total of combinations. As modern images have hundreds of pixels for height and width, n can readily take on values greater than 16, making the total number of key combinations greater than 226. In addition, the variable keyspace adds to the attacker's confusion. The two-step encryption process also makes brute force attacks challenging. Hence The algorithm performs admirably when it comes to defending against brute force attacks.
6.4. Analysis of the key sensitivity
A high amount of key sensitivity is a must for any encryption algorithm. Key sensitivity means that even a small change in key should result in a large overall change in the encrypted image. This makes it difficult for an attacker to guess the actual key. This section explores the key sensitivity of the proposed algorithm and the same can be seen in .
Figure 17. Key Sensitivity Analysis for Cat Image (Key B was obtained when one bit was changed in key A). (a) Original Cat Image. (b) Encrypted Image with key A. (c) Encrypted Image with key B and (d) Difference between (b) and (c).
To do this, the original cat image has been taken and encrypted with key A. Then to create a minor change in key A, a random bit was altered in key A to get key B. Now the original cat image was encrypted with key B. Comparing both encrypted images of key A and key B the difference can clearly be seen in (d). Both the encrypted images are completely different with no kind of correlation between them.
As a result, it can be said that the proposed algorithm's encryption process is highly key sensitive, which increases the benefits of using this approach in real-world circumstances.
6.5. Correlation analysis
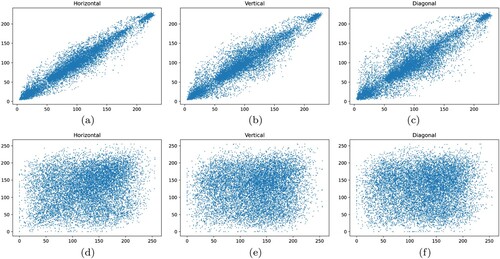
Correlation between neighbouring pixels quantifies the relationship between two adjacent pixels in an image. The correlation between neighbouring pixels in simple images is quite high. High correlation may facilitate statistical attacks by attackers. In order to guarantee the security of the data and avoid leakage, any reliable image encryption system needs to be able to handle this. The relationships between neighbouring pixels in the original source image and the encrypted image are examined using correlation analysis as a method of determining how secure the proposed algorithm is.
From the original and encrypted images, around 4000 random pairs of adjacent pixels are selected to conduct the correlation analysis. These pairings are chosen from the horizontal, vertical, and diagonal directions respectively. The intensity values of the neighbouring pixel pairs are then compared against one another to create a scatter plot that shows the correlation analysis. Plots are generated in all 3, horizontal, vertical, and diagonal directions. If any two neighbouring pixels are equivalent in intensity, their mark on the plot will be along the diagonal of the scatter plot. Therefore, a highly dense diagonal line will be shown in the plot of an image with a high correlation factor (Hua et al., Citation2019).
As can be seen in , the majority of the points in the scatter plots of original source images are located along the diagonal. This concentration of diagonal points demonstrates the high correlation in the original source image (Bao & Zhou, Citation2015). In contrast, the points on the three plots generated for the encrypted images along the horizontal, vertical, and diagonal directions are highly dispersed and randomly distributed over the image's data range. This leads to the conclusion that the encrypted image produced by the proposed algorithm has a very low correlation rate and a high amount of randomization. This further highlights the effectiveness of the proposed algorithm.
6.6. Recover-ability test
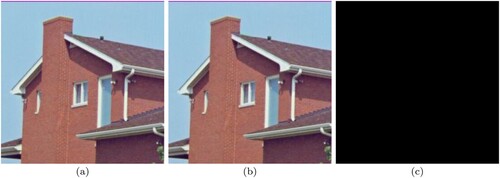
The ability to retrieve 100% of the original source image after decryption is one of the fundamental criteria for any encryption technique. An analysis of the difference between the source image and the decrypted image can be used to determine this. If the assessment demonstrates that there is absolutely no difference between the source image and the image produced after the decryption process i.e. if the image produced after performing the difference is totally black (all its pixel values are 0), then this confirms that there was no loss of image data and that the technique is lossless and meets the test of recover-ability.
(a) and (a) are the original tulips image and the original house image. After decrypting it using the proposed algorithm, the generated resultant images are shown as (b) and (b). The resultant image of the difference between the original and decrypted images can be seen in (c) and (c), both of which are completely black (i.e. the intensity value of all its pixels is zero). These results demonstrate that the proposed algorithm completely satisfies the recover-ability test and is fully lossless.
6.7. Noise resistance analysis
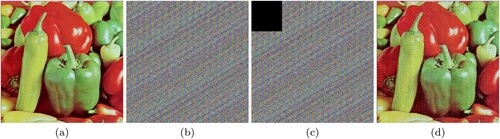
This section will now examine how noise resistant the decryption of the proposed algorithm is. During transmission, an image may become infected with some sort of noise. An algorithm must be able to decrypt loss-induced images with the least amount of distortion and data loss so as to manage the introduced noise, which might occur during data transfer or when noise is purposefully inserted. Therefore, two encrypted photos were intentionally given noise, and the corresponding decrypted images were produced to demonstrate this property.
Figure 20. House, (a) source image (b) decrypted image (c) image depicting difference in (a) and (b).
(a) and (a) are the original pepper image and the original lena image. After encrypting it using the proposed algorithm, the generated resultant images are shown as (b) and (b). Then the noise was intentionally added to a block of 128 * 128 = 16,384 pixels of the encrypted image as shown in (c) and (c), and then the decrypted images of these noise-induced encrypted images was obtained, shown by (d) and (d). Thus it can be seen that there are only small changes when both sets of decrypted images are compared. Also, the original images haven't been affected much as the contents of the original images can be deciphered. Thus it is possible to claim that the proposed algorithm is highly noise resistant.
7. Industrial significance and working scope
Today more than 80% of the entire data in the world is unstructured data, consisting of images, videos, and documents. Every person is sharing such type of data with one another. Data privacy is the need of the hour. In various sections of this paper, the working, experimentation, and results of the proposed algorithm have been covered. In addition to meeting all security requirements, it was also able to strongly encrypt the images such that they were incomprehensible. The scope of this algorithm is vast as various standard test images of humans, objects, animals, and plants were securely encrypted using the algorithm. The flexibility can also be extended to other forms of unstructured data. Moreover, Data can easily be infected with noise during transmission and it was found that the proposed algorithm was highly noise resistant with minimal data loss upon some of its data being corrupted by noise and is 100% lossless making it a good candidate for not only general purposes applications in messaging, emails and cloud technologies but several other real-world applications across various industries as well.
In today's interconnected world where information security breaches are rampant, particularly in the realm of text and images, the industrial significance of employing a combination of the Modified Caesar Cipher and the Card Deck Shuffle Algorithm for image encryption cannot be overstated. The integrity of data shared over unprotected connections is paramount, making image/text encryption an indispensable preprocessing step in contemporary information transmission. This method, boasting a robust n + 8 variable bit key, often exceeding 18 bits in real-world applications, offers a formidable defense against unauthorized access. Its versatility and practicality make it applicable in diverse industrial settings, safeguarding sensitive information, ensuring regulatory compliance, enhancing the security of multimedia applications, and fortifying data transmission against potential threats.
8. Conclusion and future scope
This paper introduced a new 2-stage image encryption algorithm. The first stage consists of a modified implementation of the Caesar Cipher where not one but two keys are used which enable us to substitute each consecutive pixel with a completely different value introducing a high degree of randomness in the image before passing it to the next stage. Stage 2 consists of a newly developed transposition Cipher called the card deck rearrangement algorithm which is based on the shuffling of cards for rearrangement using riffle shuffle where the deck size of each sub-deck is a controlled parameter based on the first key. The 2 keys used are provided in a combined n + 8 bit key formed where n is the minimum number of bits used to represent the total number of pixels in the image. Hence in today's world, n can easily take values more than 18 taking the total key combinations to more than . When tested for various security tests and analyses for histograms, correlations, recover-ability, and noise resistance, the algorithm performed really well and gave the desired results which are expected from a highly efficient and robust encryption scheme. Initially made for just grayscale images, this algorithm was up-scaled for colour images too. Future modifications in the stages of algorithms will enable it to be used on other forms of data such as videos and documents giving it a mammoth future scope.
Disclosure statement
No potential conflict of interest was reported by the author(s).
References
- Akkasaligar, P. T., & Biradar, S. (2020). Selective medical image encryption using DNA cryptography. Information Security Journal: A Global Perspective, 29(2), 91–101.
- Anh, L. D., Vo, B., & Pedrycz, W. (2017). Information granulation construction and representation strategies for classification in imbalanced data based on granular computing. Journal of Information and Telecommunication, 1(2), 113–126. https://doi.org/10.1080/24751839.2017.1323476
- Bao, L., & Zhou, Y. (2015). Image encryption: Generating visually meaningful encrypted images. Information Sciences, 324, 197–207. https://doi.org/10.1016/j.ins.2015.06.049
- Chakraborty, S., Seal, A., Roy, M., & Mali, K. (2016). A novel lossless image encryption method using DNA substitution and chaotic logistic map. International Journal of Security and Its Applications, 10(2), 205–216. https://doi.org/10.14257/ijsia
- Cheng, Q., Hua, Y., & Stoica, P. (2000). Asymptotic performance of optimal gain-and-phase estimators of sensor arrays. IEEE Transactions on Signal Processing, 48(12), 3587–3590. https://doi.org/10.1109/78.887058
- Dar, S. B. (2014). Enhancing the security of Caesar Cipher using double substitution method. International Journal of Computer Science & Engineering Technology, 5(7), 772–774.
- Deshpande, K., Girkar, J., & Mangrulkar, R. (2023). Security enhancement and analysis of images using a novel Sudoku-based Encryption Algorithm. Journal of Information and Telecommunication, 7(3), 270–303. https://doi.org/10.1080/24751839.2023.2183802
- Godara, S., Kundu, S., & Kaler, R. (2018). An improved algorithmic implementation of rail fence Cipher. International Journal of Future Generation Communication and Networking, 11(2), 23–32. https://doi.org/10.14257/ijfgcn
- Goyal, K., & Kinger, S. (2013). Modified Caesar Cipher for better security enhancement. International Journal of Computer Applications, 73(3), 0975–8887. https://doi.org/10.5120/12722-9558
- Hu, F., Pu, C., Gao, H., Tang, M., & Li, L. (2016). An image compression and encryption scheme based on deep learning. CoRR, abs/1608.05001.
- Hu, F., Wang, J., Xu, X., Pu, C., & Peng, T. (2017). Batch image encryption using generated deep features based on stacked autoencoder network. Mathematical Problems in Engineering, 2017, 1–12.
- Hua, Z., Zhou, Y., & Huang, H. (2019). Cosine-transform-based chaotic system for image encryption. Information Sciences, 480, 403–419. https://doi.org/10.1016/j.ins.2018.12.048
- Lasry, G., Kopal, N., & Wacker, A. (2016). Cryptanalysis of columnar transposition Cipher with long keys. Cryptologia, 40(4), 374–398. https://doi.org/10.1080/01611194.2015.1087074
- Leong, M.-P., Cheung, O. Y., Tsoi, K. H., & Leong, P. H. W. (2000). A bit-serial implementation of the international data encryption algorithm idea. In Proceedings 2000 IEEE Symposium on Field-Programmable Custom Computing Machines (Cat. No. PR00871) (pp. 122–131). IEEE.
- Liu, X., Mei, W., & Du, H. (2014). Optical image encryption based on compressive sensing and chaos in the fractional Fourier domain. Journal of Modern Optics, 61(19), 1570–1577. https://doi.org/10.1080/09500340.2014.946565
- Maity, A., Ghosh, R., & Bhadra, S. (2022). Image encryption using RSA and advanced Caesar Cipher method. In 2022 International Conference on Advancements in Smart, Secure and Intelligent Computing (ASSIC) (pp. 1–5).
- Mandal, M. K., Banik, G. D., Chattopadhyay, D., & Nandi, D. (2012). An image encryption process based on chaotic logistic map. IETE Technical Review, 29(5), 395–404. https://doi.org/10.4103/0256-4602.103173
- Maniyath, S. R., & Thanikaiselvan, V. (2020). An efficient image encryption using deep neural network and chaotic map. Microprocessors and Microsystems, 77, Article 103134. https://doi.org/10.1016/j.micpro.2020.103134
- Mohammad, O. F., Rahim, M. S. M., Zeebaree, S. R. M., & Ahmed, F. (2017). A survey and analysis of the image encryption methods. International Journal of Applied Engineering Research, 12(23), 13265–13280.
- Naim, M., & Ali Pacha, A. (2021). New chaotic satellite image encryption by using some or all the rounds of the AES algorithm. Information Security Journal: A Global Perspective, 32(3), 187–211.
- Osman, T., Psyche, S. S., Deb, T., Firoze, A., & Rahman, R. M. (2019). An algorithmic approach to estimate cognitive aesthetics of images relative to ground truth of human psychology through a large user study. Journal of Information and Telecommunication, 3(2), 156–179. https://doi.org/10.1080/24751839.2018.1542574
- Qowi, Z., & Hudallah, N. (2021). Combining Caesar Cipher and Hill Cipher in the generating encryption key on the Vigenere Cipher Algorithm. In Journal of Physics: Conference Series (Vol. 1918, pp. 042009). IOP Publishing.
- Rachmawati, D., Hardi, S. M., & Pasaribu, R. P. (2019). Combination of columnar transposition Cipher Caesar Cipher and lempel ziv welch algorithm in image security and compression. Journal of Physics: Conference Series, 1339(1), Article 012007.
- Raja, S., & Suruliandi, A. (2018). Secured image compression using AES in Bandelet domain. International Journal of Computational Science and Engineering, 17(2), 208–219. https://doi.org/10.1504/IJCSE.2018.094930
- Ritter, T. (1991). Transposition Cipher with pseudo-random shuffling: The dynamic transposition combiner. Cryptologia, 15(1), 1–17. https://doi.org/10.1080/0161-119191865731
- Saini, B. (2015). Modified Caesar Cipher and rail fence technique to enhance security. Int J Trend Res Dev, 2(5), 348–350.
- Sanchez-Avila, C., & Sanchez-Reillol, R. (2001). The Rijndael block Cipher (AES proposal): A comparison with des. In Proceedings IEEE 35th Annual 2001 International Carnahan Conference on Security Technology (Cat. No. 01CH37186) (pp. 229–234). IEEE.
- Seal, A., Chakraborty, S., & Mali, K. (2017). A new and resilient image encryption technique based on pixel manipulation, value transformation and visual transformation utilizing single-level haar wavelet transform. In Proceedings of the First International Conference on Intelligent Computing and Communication (pp. 603–611). Springer.
- Shrivastava, G., Sharma, R., & Chouhan, M. (2013). Using letters frequency analysis in Caesar Cipher with double columnar transposition technique. International Journal of Engineering Sciences & Research Technology, 2(6): June, 2013.
- Siahaan, A. P. U. (2017). Rail-fence-cryptography-in-securing-information.
- Srikantaswamy, S., & Phaneendra, D. H. (2012). Improved Caesar Cipher with random number generation technique and multistage encryption. International Journal on Cryptography and Information Security (IJCIS), 2(4), 39–49. https://doi.org/10.5121/ijcis
- Srivastava, M., Srivastava, U., & Srivastava, S. (2023). Modified Caesar Cipher with image steganography. In 2023 6th International Conference on Information Systems and Computer Networks (ISCON) (pp. 1–6).
- Standard, D. E. (1977). Federal information processing standards publication 46. National Bureau of Standards, US Department of Commerce, FIPS Publication 46-3, 23, 1–18.
- Talbert, R. (2006). The cycle structure and order of the rail fence Cipher. Cryptologia, 30(2), 159–172. https://doi.org/10.1080/01611190500380082
- Wadi, S., & Zainal, N. (2014). High definition image encryption algorithm based on AES modification. Wireless Personal Communications, 79(2), 811–829. https://doi.org/10.1007/s11277-014-1888-7
- Wang, X., Wang, S., Zhang, Y., & Guo, K. (2017). A novel image encryption algorithm based on chaotic shuffling method. Information Security Journal: A Global Perspective, 26(1), 7–16.
- Yang, H., Ning, Y., & Wang, Y. (2019). Research on RSA and Hill hybrid encryption algorithm. International Journal of Computational Science and Engineering, 20(1), 1–6. https://doi.org/10.1504/IJCSE.2019.103241
- Ye, R. (2011). A novel chaos-based image encryption scheme with an efficient permutation-diffusion mechanism. Optics Communications, 284(22), 5290–5298. https://doi.org/10.1016/j.optcom.2011.07.070
- Zhang, Y. (2016). The image encryption algorithm with plaintext-related shuffling. IETE Technical Review, 33(3), 310–322. https://doi.org/10.1080/02564602.2015.1087350