?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.ABSTRACT
Robust JPEG steganographic algorithms are proposed to transmit covert message against JPEG compression. The existing robust JPEG steganographic algorithms are working with the side information about JPEG compression quality factor of a lossy channel. However, massive recent experimental results reveal that the performance of the present robust JPEG steganographic algorithms is poor if the side information is unknown. Thus, this paper proposes a new robust JPEG steganographic algorithm to satisfy the requirement. First, the error diffusion of steganographic embedding encoder is analyzed. Then, a new robust JPEG steganographic algorithm is proposed based on the analysis result. A series of experiments are conducted on 10,000 images from BOSSbase 1.01 image library. The results show that the proposed method can resist JPEG compression efficiently with acceptable resistance to steganalysis statistical detection.
1. INTRODUCTION
Steganography is an art of covert communication [Citation1–5]. It can transmit secret message through public communication channels without causing attention of watcher, especially in a controlled communicating situation (such as prisoner-communication in the prison under the monitoring of guard). In recent years, with the development of mobile communication technology, many social medias such as FaceBook, WeChat, and Instagram transmit enormous images through intelligent mobile terminal [Citation6]. JPEG compression is always applied on the images of social medias after considering the bandwidth, tariff, traffic and other restrictions of intelligent mobile terminal. This kind of lossy operation often destroys the message hidden by traditional steganographies [Citation7]. Therefore, robust steganography on resisting JPEG compression is proposed to protect the message against the lossy compression with acceptable resistance to steganalysis statistical detection, and then it is the focus of this manuscript.
When it comes to the words “robust steganography”, it is natural to think of “robust watermark”. The robust watermarking technology has been researched for more than two decades, and some kinds of robust watermarking methods (such as spread spectrum modulation [Citation8], feature-based algorithm [Citation9], and scale invariant feature transformation [Citation10]) are proposed to reduce the effect of various lossy operations on cover image object. In general speaking, the priority purpose of robust watermarking is to guarantee the existence of embedded information against the various attacks (such as JPEG compression, rotation, cropping, down-sampling, and so on), and the completeness of the embedded information is on the second stage [Citation11]. Meanwhile, the designs of most robust watermarking ignore the ability of resisting steganalysis detection for there is no related requirement [Citation12]. Thus, the robust watermarking algorithm cannot be simply used as a steganography to transfer secret message on security consideration.
In recent years, the adaptive steganography becomes a hotpot in the research of information hiding [Citation1,Citation2]. A design is widely used by the recent adaptive steganographies – “embedding cost function + steganographic embedding code” [Citation13]. The cooperation between the function and embedding code (STCs, Syndrome Trellis Codes [Citation14]) can concentrate embedding modifications to the proper areas (hard to detect the change on them) [Citation1,Citation13,Citation15,Citation16]. Because the embedding cost function mainly influence the distribution of modifications on cover image, many embedding cost functions are proposed in the recent proposed adaptive JPEG steganographies, such as New Perturbed Quantization [Citation17] algorithm, Uniform Embedding Distortion [Citation18] (UED) algorithm, Efficient Block-entropy Steganographic scheme [Citation19] algorithm and JPEG UNIversal WAvelet Relative Distortion [Citation20] (J-UNIWARD) algorithm. These adaptive steganographic algorithms work in the lossless communication channel and receive high performance on resisting steganalysis statistical detection methods [Citation21–24].
Nevertheless, the above adaptive steganographic algorithms suffer setbacks in the lossy channel, and robust steganographic algorithm is proposed to protect the embedded message. In the previous work, Zhang et al. proposed robust steganographic algorithms DCT Coefficient Relationship-based Adaptive Steganography (DCRAS [Citation7]) and Feature Region-based Adaptive Steganography (FRAS [Citation25]), and they can resist JPEG compression efficiently with acceptable detection resistance. However, these robust algorithms need to know the quality factor of the JPEG compression used in the lossy channel (side information), and they can hardly protect the embedded message if the lossy channel compresses the stego object in a different quality factor.
To solve the problem above, a new robust JPEG steganography with no side information is proposed in this manuscript. A series of experiments are conducted on 10,000 images from BOSSbase 1.01 image library, and the results reflect that the proposed robust JPEG steganographic algorithm can resist JPEG compression in a quality factor range (65,85) with acceptable resistance to steganalysis statistical detection. The main works of this manuscript are as follows:
(1) The error diffusion of steganographic embedding code STCs is analyzed. The relationship between the parameters of STC and the error probability of extracted message in the lossy channel is pointed out: the height and width of sub-matrix of STCs have a positive correlation with the error probability of extracted message.
(2) A new robust JPEG steganographic algorithm with no side information is proposed. It is based on the error diffusion analysis result and the relationship between DCT coefficients. The method of reduction error diffusion in the lossy channel can apply to another robust JPEG steganography.
The rest of this manuscript is organized as follows. Section 2 introduces the related researches of adaptive JPEG steganography and robust JPEG steganography. Then, the analysis of error diffusion of STCs in the lossy channel and the proposed robust JPEG steganographic algorithm are described in Sections 3 and 4, respectively. In Section 5, the results of comparative experiments on resisting JPEG compression and steganalysis detection are presented. Section 6 summarizes the full manuscript.
2. RELATED WORKS
2.1 Adaptive JPEG Steganography
A JPEG image is obtained from an original spatial image through several processes, such as color space conversion, down-sampling, blocking, applying block DCT transformation independently, quantizing the resulting DCT coefficients by quality factor (QF) to integer numbers, and encoding the coefficients for the storage operation. The embedding modification of JPEG adaptive steganography algorithm is usually applied on the rounded DCT coefficients after quantizing.
Many adaptive JPEG steganographic algorithms are composed of embedding cost function and steganographic embedding code. This framework [Citation13] is originated from the minimal distortion model proposed by Fridrich et al. [Citation26]. It achieves good performance on resisting detection for the embedding modifications are hidden in the DCT coefficients with higher resistance to detection. On the research of how to define proper embedding cost function, Holub et al. proposed an adaptive steganographic algorithm J-UNIWARD on JPEG image in the article [Citation20]. Wavelet decomposition coefficients are used to describe the suitability of an element on resisting statistical detection. The embedding cost function on cover and stego DCT coefficient sequences
and
is defined as follows:
(1)
(1)
where
is the inverse function that transforms the DCT coefficients to spatial domain,
denotes the uvth coefficient of rth (r = 1,2,3) wavelet decomposition, and
is used to prevent the molecule from zero (in current,
).
2.2 Robust JPEG Steganography
In [Citation7], we proposed a framework for designing a robust steganographic algorithm. The framework combines the robust measure of robust watermarking with the design of adaptive steganographic algorithm, in order to resist both JPEG compression and steganalysis detection.
In the framework, for the sender, the embedding domain is determined first; then, design the message embedding modification method with strong robustness to JPEG compression; then, the embedding cost function is defined to elevate the resistance to steganalysis detection; in the next, the error correction coding is applied to further improve the robustness of embedded message. Finally, use the steganographic embedding code to embed the message into the cover object through the designed modification method above. For the receiver, the STCs is first decoded to obtain the interfered information flow, and then the error correction code is used to reduce the bit error rate, and finally get the original embedded message.
Based on the robust JPEG steganographic framework above, DCRAS and FRAS algorithms are also proposed in articles [Citation7,Citation25]. DCRAS and FRAS algorithm owns much better JPEG compression resisting performance than typical adaptive JPEG steganographic algorithm, such as J-UNIWARD, UED, and so on. But they need the side information about the quality factor of the attacking JPEG compression. If the stego object is suffered by a JPEG compression with a different quality factor. These algorithms can no longer protect the embedded message any more. That is because the quality factor is used to generate the robust cover object against JPEG compression, and the generated object is strong related to the quality factor in these algorithms. How to generate a robust cover object without the knowledge of quality factor is needed for robust JPEG steganography. On this problem, this paper will propose a new robust JPEG steganographic algorithm.
3. ERROR DIFFUSION OF STCs
3.1 Construction of STCs Embedding Matrix
The main purpose of the steganographic embedding code is to minimize the cost value caused by embedding the secret message in the steganographic algorithm. The most popular embedding form is matrix embedding [Citation1], and it can be described as
(2)
(2)
where
denote the cover object and stego object of
length, respectively. And
denotes the secret message with
bits.
denotes the embedding matrix, and
is the embedding cost function describing the distortion caused by changing cover element. How to find a
that satisfies Equation (2) is the main purpose of steganographic embedding coding.
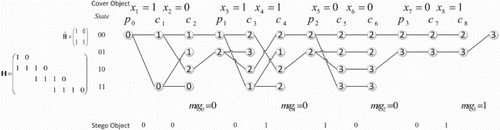
At present, most algorithms of the adaptive steganography and robust steganography use STCs [Citation14] to embed a secret message into the cover object. STCs embedding code is based on the idea of the Viterbi decoding algorithm and find suitable solution of by limited exhaustive, pruning, and traceable operations. A brief example of STCs is presented in Figure . From the example, we can see that the STCs algorithm can work efficiently because of the special construction of the embedding matrix
, and the detail of
is shown in Figure .
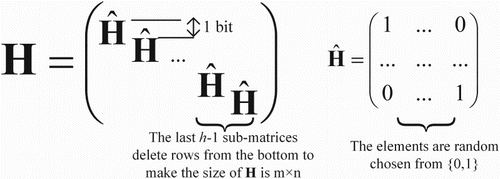
From the figure we can see that, is composed by
sub-matrices
lined in diagonal. Notice that some rows of the last
sub-matrices are deleted to guarantee the size of
is
. This special construction makes the sender can find a stego nearly satisfies Equation (2) by the exhaustive process, and the computational complexity is acceptable on a personal computer. Embedding experiments in the article [Citation14] show that the performance of STCs is gradually near to the theoretical bound with the height of
grows.
3.2 Analysis of Error Diffusion
In the lossy channel of JPEG compression, the DCT coefficients are changed and caused error bits in the steganographic extraction process. Article [Citation6] points out that the occurrence of error bits in robust stego object of DCRAS after JPEG compression is random.
We suppose the error probability of the robust stego object after JPEG compression is
.
is generated by STCs with
, and the embedding matrix is composed by
sub-matrices
. According to Equation (2) of matrix embedding, the embedded
bits message
is extracted on the binary field by
(3)
(3)
The construction of H indicates that an element
of y effects h elements in the extracted message. It is because the other elements of the corresponding column of
are definitely 0. On the other hand, for the same reason, an element
of msg is influenced by hw continuous elements of y. Thus, the error bits number expectation
on the row of H corresponding to
is
(4)
(4)
where the symbol
denotes the probability of “1” elements in sub-matrix
. As described in [Citation11], the elements of
are suggested to be chosen randomly chosen from set {0, 1},
can be regarded as
. Thus, the error probability of the elements in
is
. Notice that the computation of Equation (3) is on the binary field, and
on this field. It means that if the number of errors is even, the extracted message is correct. Because the extracted message
is computed by hw elements from
, the error probability
of
can be expressed as
(5)
(5)
Because the value of
is less than 0.1 in many situations based on the experiments in [Citation4],
can be estimated by
(6)
(6)
From Equation (6), we can get that, the larger values of height and width of cause higher error probability of extracted message in the lossy channel.
4. PROPOSED ROBUST STEGANOGRAPHIC ALGORITHM
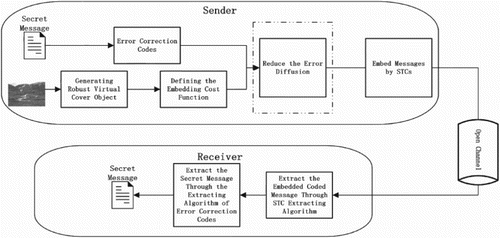
In this section, the robust steganographic algorithm without side information of quality factor is proposed. The basic flow chart of the proposed algorithm is shown in Figure , which mainly includes generating robust virtual cover object, defining embedding cost function, coding the secret message by error correction encoder, reducing the error diffusion of STCs, embedding coded message through STCs and the corresponding extracting algorithms. This section will introduce how to generate the robust virtual cover object, define the embedding cost function and reduce the error diffusion.
4.1 Construction of Robust Virtual Cover Object
Based on the relative relationship between DCT coefficients, a robust against JPEG compression virtual cover object is generated:
(1) Decoding the JPEG image I to achieve a set of nonoverlapping
DCT coefficients blocks
,
, B is the number of the blocks, and
is the ith coefficient in the kth block.
(2) Generating robust virtual cover object
based on the relationship between coefficient
and
. The symbol
is the rounded mean value of three DCT coefficients
at the same in-block position of three neighboring blocks. The element
of the generated cover object
satisfying:
(7)
(7)
4.2 Design of Embedding Cost Function
After the robust virtual cover object is created, the popular minimal distortion model [Citation13,Citation26] is used to concentrate the embedding modifications on the elements in the less distortion region to increase the performance on resisting detection. First, embedding cost function is defined to describe the distortion value caused by embedding message on cover object . The cost function is designed based on the combination of the J-UNIWARD embedding cost function
[Citation18] of formula (1) and the robust virtual cover object. It is shown as follows:
(11)
(11)
where
and
, respectively, denote the cost values
of modification magnitude 1 and 2 in the J-UNIWARD embedding cost function, and wet_cost denote the cost value that not advanced to be modified in the STCs embedding process (usually be set to a quite large value such as
). Then, the robust virtual stego object
is obtained after embedding secret message into
by STCs code, and the modification is mapped into image DCT coefficients
by formula (8) to obtain the DCT coefficients stego object.
4.3 Reduction of Error Diffusion
Based on the analysis result Section 3.2, the error probability can be reduced by shrinking the hw of sub-matrix . Because the height h of
effects, the performance of steganographic embedding and computational complexity a lot, the value of h is often in the range
on embedding efficiency and complexity consideration. Another way to reduce the error diffusion of STCs under the situation is to get a small value w. According to the construction of embedding matrix of STCs in Section 3.1, the value of w is due to the embedding rate
.
Thus, we can increase the embedding rate of STCs by following steps:
Sort the elements of robust virtual cover object
computed from the same in-block position
of
DCT coefficients in a row
.
Compute the required length
of virtual cover object based on the reduced embedding rate
.
Select
elements from the set
in an order shared by the sender and receiver.
The sort of the is to make the elements in the same in-block position adjoined in the selected
elements virtual cover object. This process is to increase the ability of resisting detection of the proposed method. As shown in Figure , it tells that the embedding modifications of J-UNIWARD are related to the in-block position, and concentrate to the low-frequency positions. Thus, we suggest the first 10 sort(X(i,j)) in a permutation as
(12)
(12)
Then, error correction encoder RS [Citation27] with parameter (6,15) is applied on the secret message, and the robust virtual stego object is obtained after embedding the encoded secret message into the selected
-element virtual cover object by STCs code. The modifications are mapped into image DCT coefficients
by formula (8) to obtain the DCT coefficients stego object.
5. EXPERIMENTS
5.1 Experimental Setups
The experimental results were carried out by the Matlab R2010a, and the spatial image database used in the experiments was BOSSbase v1.01 (proposed by Patrick Bas, Tomas Filler, Tomas Pevny at ICASSP 2013, containing 10,000 images of size , download: http: //agents.fel.cvut.cz/stegodata/), the image database contains natural scenery, artificial facilities, and human portraits pictures, at the same time, the photos are shot from eight cameras of different companies to ensure the diversity.
In the resisting JPEG compression experiments, the measure of resisting JPEG compression of the steganographic algorithm is the extraction error rate , which is defined as the ratio of the bit-length
of the errors in the extracted message after the stego object is JPEG compressed to the bit-length m of the original embedded secret message, that is,
. The closer value to 0 indicates the higher performance on resisting JPEG compression.
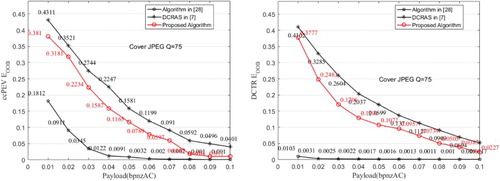
In the resisting detection experiment, the popular detection features (such as ccPEV [Citation28] and DCTR [Citation23] detection feature libraries with 548 and 8000 dimensions, respectively) are extracted from the cover image set and stego image set. Then half of the features are used to train the classifier and use the trained classifier to classify the remaining images to test the detection resisting performance of steganographic algorithm. The measurement is “out of bag estimate of the testing error”, and denoted as , which is an unbiased value and indicates the test error rate of the classifier. The higher the value, the better performance of the steganographic algorithm owns.
5.2 Experiments of Resisting JPEG Compression
In this section, we randomly select 1000 spatial images from the BOSSbase v1.01 image database to, respectively, generate 1000 cover images when quality factor is 75, and then use J-UNIWARD [Citation20], robust watermarking algorithm [Citation29], DCRAS [Citation7] and the improved method in this paper to transmit secret message. The embedding rate varies from 0.01 bpnzAC (bits per non-zero Alternating Current coefficient) to 0.1 bpnzAC with 0.01 interval and 1000 stego images are generated on each embedding rate with each embedding algorithm. To simulate the no side information of quality factor of JPEG lossy channel, the stego images generated by DCRAS algorithm are obtained to resist 80 quality factor JPEG compression. Then, the JPEG compression attacks with the quality factor of 65, 75, and 85 are applied to the stego images. Then, the corresponding message extraction algorithms are run after the lossy compression, and the extracted message is compared with the original message by bit. Last, the extraction error rates of the tested methods are calculated, and the results are shown in Figures .
Figure 5: Results of resisting JPEG compression with quality factor 65 on cover object of quality factor 75
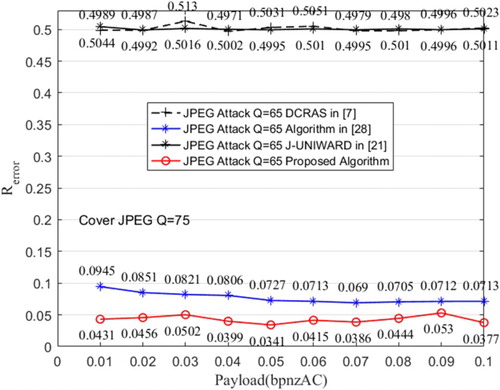
Figure 6: Results of resisting JPEG compression with quality factor 75 on cover object of quality factor 75
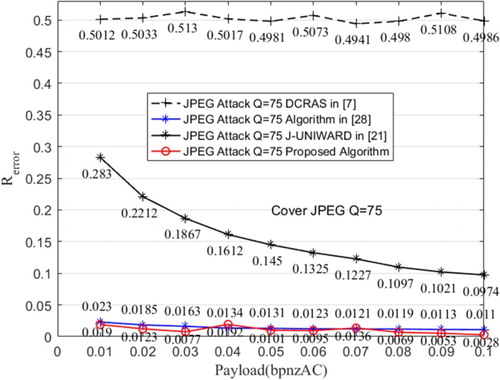
Figure 7: Results of resisting JPEG compression with quality factor 85 on cover object of quality factor 75
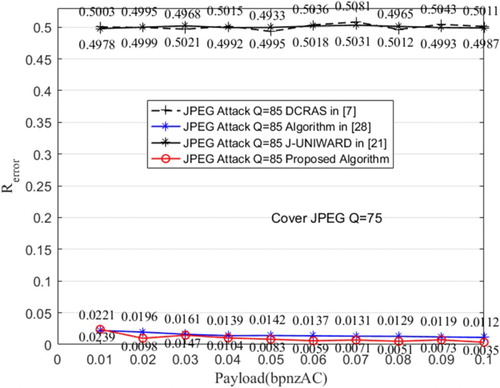
It can be seen from the figures that the secret carriers obtained by J-UNIWARD algorithm and DCRAS algorithm are unable to resist the lossy compression. At the same time, the extraction error rate of the robust watermarking algorithm in the [Citation29] is between 3% and 10%. It owns better JPEG compression resisting performance than typical adaptive JPEG steganographic algorithm but the error rate is still high. The correctness rate of the extraction error rate of the proposed algorithm about 0.3–3%, and it means that the proposed algorithm can resist JPEG compression efficiently.
5.3 Experiments of Resisting Statistical Detection
In this section, we construct the cover image set with QF = 75 from all 10,000 spatial images in the BOSSbase v1.01 image database, and test the resisting performance of detection on the proposed algorithm, the robust watermarking algorithm [Citation29], and DCRAS [Citation7] algorithm. The embedding rate varied from 0.01 to 0.1 bpnzAC, 10,000 stego images are generated on each embedding rate with different testing algorithms. Then, the detection features of the cover set and the stego set are extracted by the detection feature library, and then the ensemble integration classifier [Citation30] is trained by the extracted features (from 5000 cover-stego pairs). In the next, the trained classifier is used to classify the remaining 10,000 images (5000 cover images and 5000 stego images are random distributed). The results of are shown in Figure , where Figure (a) presents the results on detection library ccPEV [Citation28] (a typical library of 548 features), and Figure (b) shows the results of the DCTR detection algorithm (DCTR is one of the most effective detection library for JPEG steganography, and it contains 8000 features [Citation23]). It can be seen from Figure that the detection error rate
of robust watermarking algorithm is low, the possible reason is that the anti-detectability is not considered in the design of robust watermarking algorithm, resulting in the embedded image is easy to be detected. At the same time, the
of the proposed algorithm is less than the
of DCRAS algorithm at most 7%. This is because the STCs used in the proposed method only to find the solution of Equation (2) in a part of the whole cover object, and better solution can be found if considering the whole cover object. Thus, the ability of the proposed method is reduced when compared to DCRAS algorithm.
6. CONCLUSIONS
In view of the problem that the JPEG compression quality factor is unknown in some lossy channels. This paper proposed a new robust JPEG steganographic algorithm to satisfy the situation without knowledge of JPEG compression quality factor. It generates a robust virtual cover object based on the relationship between DCT coefficients. A series of experiments are conducted and the results show that the proposed robust algorithm can achieve high extraction accuracy in various JPEG compression situations without knowing the quality factor of compression and can resist steganalysis statistical detection methods.
Without any doubts, better coding performance can be obtained if the steganographic embedding code is combined with the error correction code, it may be the focus of the next work. How to elevate the extraction accuracy to 100% is a curious question. Furthermore, exploiting new method to resist stronger lossy attacks (such as rotation, cropping, down-sampling, etc.) is another interesting topic of robust steganography.
ORCID
Additional information
Funding
Notes on contributors

Z. Bao
Zhenkun Bao received his BS and MS from the Zhengzhou Information Science and Technology Institute, in 2011 and 2014, respectively. Now, he is a doctoral candidate of Computer Applications of Zhengzhou Information Science and Technology Institute. His current research interests include image steganography and steganalysis technique.
Email: [email protected]

X. Luo
Xiangyang Luo received his BS, MS and PhD from Zhengzhou Information Science and Technology Institute, in 2001, 2004, and 2010, respectively. He has been with Zhengzhou Information Science and Technology Institute since July 2004. From 2006 to 2007, he was a visiting scholar of the Department of Computer Science and Technology of Tsinghua University. He is the author or co-author of more than 50 refereed international journal and conference papers. His research interest includes image steganography and steganalysis.

Y. Zhang
Yi Zhang received his BS and MS from the Zhengzhou Information Science and Technology Institute, in 2014 and 2017, respectively. Now, she is a doctoral candidate of Computer Applications of Zhengzhou Information Science and Technology Institute. Her current research interests include image steganography and steganalysis technique.
Email: [email protected]

C. Yang
Chunfang Yang received his BS and MS from the Zhengzhou Information Science and Technology Institute, in 2005 and 2008, respectively. Now, he is a doctoral candidate of Computer Applications of Zhengzhou Information Science and Technology Institute. His current research interests include image steganography and steganalysis technique.
Email: [email protected].

F. Liu
Fenlin Liu received his BS from Zhengzhou Information Science and Technology Institute in 1986, MS from Harbin Institute of Technology in 1992, and PhD from the Northeast University in 1998. Now, he is a professor of Zhengzhou Information Science and Technology Institute. He is the author or co-author of more than 90 refereed international journal and conference papers. His research interests include information hiding and security theory.
Email: [email protected].
References
- A. D. Ker, P. Bas, R. Bohme, R. Cogranne, S. Craver, T. Filler, J. Fridrich, and T. Pevny, “Moving steganography and steganalysis from the laboratory into the real world,” in Proceedings of ACM Workshop on Information Hiding and Multimedia Security, Montpellier, 2013, pp. 45–58.
- J. Fridrich, Steganography in Digital Media: Principles, Algorithms, and Applications. Cambridge: Cambridge University Press, 2009.
- C. Qin, C. C. Chang, Y. H. Huang, and L. T. Liao, “An inpainting-assisted reversible steganographic scheme using a histogram shifting mechanism,” IEEE Trans. Circuits Syst. Video Technol., Vol. 23, no. 7, pp. 1109–18, 2013. doi: 10.1109/TCSVT.2012.2224052
- C. Qin, C. C. Chang, and Y. P. Chiu, “A novel joint data-hiding and compression scheme based on SMVQ and image inpainting,” IEEE Trans. Image Process., Vol. 23, no. 3, pp. 969–78, 2014. doi: 10.1109/TIP.2013.2260760
- C. Qin, C. C. Chang, and T. J. Hsu, “Reversible data hiding scheme based on exploiting modification direction with two steganographic images,” Multimedia Tools Appl., Vol. 74, no. 15, pp. 5861–72, 2015. doi: 10.1007/s11042-014-1894-5
- Y. Zhang, C. Qin, W. Zhang, F. Liu, and X. Luo, “On the fault-tolerant performance for a class of robust image steganography”, Signal Process., Vol. 146, pp. 99–111, Feb. 2018. doi: 10.1016/j.sigpro.2018.01.011
- Y. Zhang, X. Luo, C. Yang, D. Ye, and F. Liu, “A framework of adaptive steganography resisting JPEG compression and detection,” Secur. Commun. Netw., Vol. 9, no. 15, pp. 2957–71, Apr. 2016. doi: 10.1002/sec.1502
- G. Tiwari, “A review on robust watermarking with its applications and comparative analysis,” Int. J. Signal Process. Image Process. Pattern Recognit., Vol. 8, no. 6, pp. 85–90, Jun. 2015.
- J. S. Tsai, W. B. Huang, Y. H. Kuo, and M. F. Horng, “Joint robustness and security enhancement for feature-based image watermarking using invariant feature regions,” Signal Process., Vol. 92, no. 6, pp. 1431–45, Jun. 2012. doi: 10.1016/j.sigpro.2011.11.033
- E. D. Tsougenis, G. A. Papakostas, D. E. Koulouriotis, and V. D. Tourassis, “Performance evaluation of moment-based watermarking methods: A review,” J. Syst Softw., Vol. 85, no. 8, pp. 1864–84, Sep. 2012. doi: 10.1016/j.jss.2012.02.045
- X. Y. Wang, Y. N. Liu, H. Xu, A. L. Wang, and H. Y. Yang, “Blind optimum detector for robust image watermarking in nonsubsampled shearlet domain,” Inf. Sci., Vol. 372, pp. 634–54, Apr. 2016. doi: 10.1016/j.ins.2016.08.076
- C. C. Chang, T. S. Nguyen, and C. C. Lin, “A reversible compression code hiding using soc and smvq indices,” Inf. Sci., Vol. 300, pp. 85–99, Jul. 2015. doi: 10.1016/j.ins.2014.12.028
- T. Filler, and J. Fridrich, “Design of adaptive steganographic schemes for digital images,” in Proc. IS&T/SPIE Electronic Imaging, Media Watermarking, Security, and Forensics XIII, Vol. 7880, pp. 0F–1–0F–14, Mar. 2011.
- T. Filler, J. Judas, and J. Fridrich, “Minimizing embedding impact in steganography using trellis-coded quantization,” in Proc. IS&T/SPIE Electronic Imaging, Media Forensics and Security XII, Vol. 7541, pp. 05–1–05–14, Mar. 2010.
- B. Li, S. Tan, M. Wang, and J. Huang, “Investigation on cost assignment in spatial image steganography,” IEEE Trans. Inf. Forensics Sec., Vol. 9, no. 8, 1264–77, Sep. 2014. doi: 10.1109/TIFS.2014.2326954
- V. Holub and J. Fridrich, “Designing steganographic distortion using directional filters,” in Proceedings of IEEE International Workshop on Information Forensics & Security, Guangzhou, 2013, pp. 234–9.
- F. Huang, J. Huang, and Y. Shi, “New channel selection rule for JPEG steganography,” IEEE Trans. Inf. Forensics Sec., Vol. 7, no. 4, pp. 1181–91, Apr. 2012. doi: 10.1109/TIFS.2012.2198213
- L. Guo, J. Ni, and Y. Shi, “An efficient JPEG steganographic scheme using uniform embedding,” in Proceedings of the IEEE International Workshop on Information Forensics and Security, Costa Adeje, Tenerife, 2012, pp. 169–74.
- C. Wang and J. Ni, “An efficient JPEG steganographic scheme based on the block entropy of DCT coefficients,” in Proceedings of the IEEE International Conference on Acoustics, Speech and Signal Processing, Kyoto, 2012, pp. 1785–8.
- V. Holub, J. Fridrich, and T. Denemark, “Universal distortion function for steganography in an arbitrary domain,” EURASIP J. Inf. Sec., Vol. 2014, no. 1, 1–13, Jan. 2014. doi: 10.1186/1687-417X-2014-1
- J. Kodovsky, and J. Fridrich, “Calibration revisited,” in Proceedings of the 11th ACM Workshop on Multimedia and Security, Princeton, NJ, 2009, pp. 63–74.
- J. Fridrich, and J. Kodovsky, “Rich models for steganalysis of digital images,” IEEE Trans. Inf. Forensics Sec., Vol. 7, no. 3, 868–82, Mar. 2012. doi: 10.1109/TIFS.2012.2190402
- V. Holub, and J. Fridrich, “Low-complexity features for JPEG steganalysis using undecimated DCT,” IEEE Trans. Inf. Forensics Sec., Vol. 10, no. 2, pp. 219–28, Feb. 2015. doi: 10.1109/TIFS.2014.2364918
- Y. Ma, X. Luo, X. Li, Z. Bao, and Y. Zhang, “Selection of rich model steganalysis features based on decision rough set-positive region reduction,” IEEE Trans. Circuits Syst. Video Technol., published online, Jun. 2018. doi:10.1109/TCSVT.2018.2799243.
- Y. Zhang, X. Luo, C. Yang, and F. Liu, “Joint JPEG compression and detection resistant performance enhancement for adaptive steganography using feature regions selection,” Multimedia Tools Appl., Vol. 76, no. 3, pp. 1–20, Mar. 2017.
- J. Fridrich and T. Filler, “Practical methods for minimizing embedding impact in steganography,” in Proc. IS&T/SPIE Electronic Imaging, Photonics West, Vol. 6505, pp. 02–01–02–15, 2007.
- I. S. Reed, and G. Solomon, “Polynomial codes over certain finite fields,” J. Soc. Ind. Appl. Math., Vol. 8, no. 2, pp. 300–4, Feb. 1960. doi: 10.1137/0108018
- T. Pevny and J. Fridrich, “Merging Markov and DCT features for multi-class JPEG steganalysis,” in Proceedings of SPIE – The International Society for Optical Engineering, Vol. 6505, pp. 650503–650503–13, 2007.
- D. Y. Chen, M. Ouhyoung, and J. L. Wu, “A shift-resisting public watermark system for protecting image processing software,” IEEE Trans. Consum. Electron., Vol. 46, no. 3, 404–14, Mar. 2000. doi: 10.1109/30.883385
- J. Kodovsky, J. Fridrich, and V. Holub, “Ensemble classifiers for steganalysis of digital media,” IEEE Trans. Inf. Forensics Sec., Vol. 7, no. 2, pp. 432–44, Feb. 2012. doi: 10.1109/TIFS.2011.2175919