ABSTRACT
A web service is an application that is published on the web and can be discovered and used automatically. In many cases, a web service cannot provide the capability that the user has requested. Therefore, according to the user request, it should be possible to combine various services and produce a new composite service for the user request. Context is the information that can be used to characterize the situation of an entity. In this paper, we present our context model for web service composition and implement the newly proposed framework for context-aware web service composition and show how the newly proposed framework reduces the number of failures and composition time.
Introduction
Web service composition is the process of constructing a composite service from atomic services in order to achieve a specific task. Traditionally, composition requests are precompiled and stored in repositories. This approach is impractical when dealing with a potentially large number of contextual commands. So, automated web service composition is essential (Vukovic Citation2007). AI (Artificial Inteligence) planning techniques are used for automated web service composition.
Context is the information that can be used to characterize the situation of an entity. An entity is a person, a place, or object that is considered in interaction between a user and an application. A system is context-aware if the context is used to provide relevant information (Dey, Salber, and Abowd Citation2001).
Context-aware applications are conformed to changes in computing environment. For example, they may react to context changes such as devices available, time constraints, location, and user requirements. A framework was developed for finding a restaurant and this framework includes mechanisms for automatic recovery from failures that may occur during the web service composition and execution process. This framework is based on TLPlan planning and uses user context information and does not consider service context information (Vukovic Citation2007).
Context-aware web service composition using planning techniques was done based on user requests and user context information, and services context information was not considered. Therefore, the number of failures and composition time were increased.
In this paper, the proposed framework that is called CA-SCP (Context-aware service composition based on planning), the preliminary choice for web services composition is made at the planning stage. Then, the final choice is made from the preselected options based on user context information and service context information. As a result, the appropriate services are run based on the user requests and the quality of services. Also, the number of failures and composition time will be decreased. The proposed framework is based on planning and introduces a new approach for web service composition, wherein both the user context and the service context are taken into account while taking composition decisions.
This paper is organized as follows. First, some background on AI planning and context models are presented. Then, we present our context model and the proposed architecture and introduce a new planning algorithm and discuss the performance of the planners. Finally, evaluation results and related work are displayed. The last section concludes the paper.
Background
Planning
AI planning techniques are used for automated web service composition. Planning is an approach of problem-solving and focuses on selecting suitable actions and ordering them in an appropriate sequence so as to achieve some goals. It allows businesses and organizations to cut costs considerably while at the same time increases their ability to handle the dynamic nature and complexity of today’s business environment (Chan, Bishop, and Baresi Citation2007).
Hierarchical task network planning
Hierarchical Task Network (HTN) is one of the best methods for planning problems. Simple Hierarchical Ordered Planner 2 (SHOP2) is a domain-independent HTN planning system. The appropriate algorithm for our problem is JSHOP2. The reasons for our choice are detailed below.
HTN planning creates plans by task decomposition. The goal of HTN planners is to produce a sequence of actions that perform some activity or task by using task decomposition. The planning domain describes a set of operators and a set of methods, which define the decomposition of a task into subtasks (Chan, Bishop, and Baresi Citation2007).
One difference between SHOP2 and most other HTN planning systems is that SHOP2 plans for tasks in the same order that they will later be executed. This reduces the complexity of reasoning by removing a great deal of uncertainty about the domain, thereby making it easy to incorporate substantial expressive power into the planning system. SHOP2 allows use of different types of precondition constraints for service operators. A key idea in using any HTN planner is to design a set of methods that encode something similar to standard operating procedures that capture multistep techniques for refining a task. Some kinds of domain characteristics are much more natural to express in an HTN formalism (Nau et al. Citation2003).
JSHOP2 is the Java implementation of SHOP2 based on the decomposition of tasks. JSHOP2 knows the current state of the world at each step of the planning process. Also, JSHOP2 in the preconditions of operators and methods can mix numeric and symbolic computations. It can be used to create domain-specific planning algorithms (Ilghami Citation2006).
JSHOP2 planning consists of the following parts (García Citation2011; García and Ortega Citation2009):
Tasks: A task represents an activity for execution. A task consists of a task symbol, which is followed by a list of arguments. The task symbol is the name of the planning operator to use, and the arguments are the parameters for the operator. A task may be primitive or complex. A complex task decomposes into smaller tasks by using a method.
Operators: Operators show how a primitive task can be performed. They are applied to a system in order to change the situation. Operators consist of a precondition and a list of symbols. The precondition specifies the conditions under which an operator can be performed. In SHOP2, the operator precondition can be omitted, but this is not the case in JSHOP2. Also, the range of possible symbol names in JSHOP2 is not as large as in SHOP2.
Methods: Methods show how to decompose a complex task into subtasks. Methods are defined with the precondition and the task list. The precondition describes the conditions under which the decomposition is performed. The task list is the sequence of simpler tasks that is performed in order to apply the method.
Axioms: The precondition of each method or operator may include conjunctions, disjunctions, numerical computations, and external function calls. In addition, axioms can infer preconditions that are not explicitly asserted in the current state. These axioms are written in a Lisp-like syntax. For example, (:—head tail) shows head is true if tail is true.
Context models
A context model defines how context data are structured and stored. A context model is needed to define and store context data in a machine processable form. Context modeling approaches are classified based on the data structures used for representing and exchanging contextual information in system (Dustdar, Baldauf, and Rosenberg Citation2007; Nalepa and Bobek Citation2013):
Key-value models. These models represent the simplest data structure for context modeling. They are used in various service frameworks to describe the capabilities of services. The key is usually a name that defines a context property. The value represents current state of the context property. When the keys match the actual context values, an action is triggered. Key-value model does not provide formalization of the model.
Markup scheme models. These models use a hierarchical data structure consisting of markup tags with attributes and content.
Graphical models. These models use a graphical notation to express knowledge. For example, UML (Unified Modelling Language) diagrams are used for supporting software development, ERD (Entity Relationship Diagram) diagrams are used in designing relational databases schemes, and BPMN (Business Process Model and Notation) is used in process modeling.
Object-oriented models. Modeling context by using object-oriented techniques is used in these models. These models use various objects to represent different context types.
Logic-based models. Logic-based models have a high degree of formality. Typically, facts, expressions, and rules are used to define a context model. These models are used to manage the aforementioned terms and allow to add, update, or remove new facts. The inference process can be used to derive new facts based on existing rules in the systems. These models enable automated inductive and deductive reasoning on context information.
Ontology-based models. Ontologies represent a description of the concepts and relationships. Therefore, ontologies are a suitable instrument for modeling contextual information and high and formal expressiveness and the possibilities for applying reasoning techniques.
Context modeling
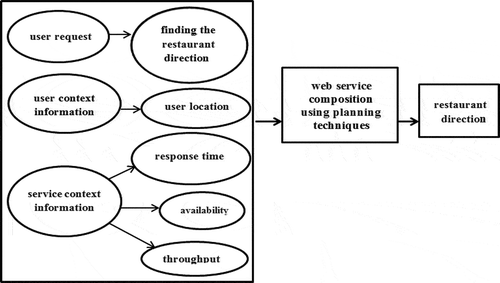
Context model of the issue of this article is the key-value model. The reasoning of choice in key-value model is that this model describes a simple matching engine and the context property and the capabilities of system. The scenario for this article is finding the direction of a restaurant requested by user. The context in this system is represented by three keys: user request, user context information, and service context information. Due to user requests, user context information, and service context information, when the keys match the context values, web service composition is performed and restaurant direction of user requests is specified. User request is finding restaurant direction. User context information includes user location. Service context information includes response time, availability, and throughput. For example, user is located in Loc1 and requests to access the restaurant Name1. shows the context model of the issue of this article.
CA-SCP architecture
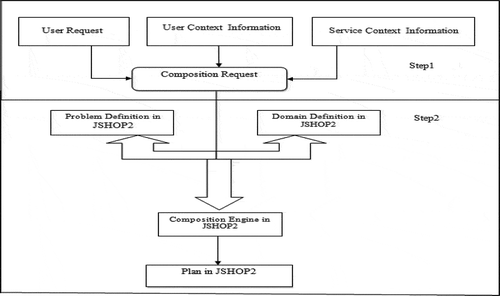
This section describes the architecture of the proposed framework that is called CA-SCP. The architecture of the CA-SCP framework for context-aware web service composition consists of two main steps. The first step is the composition request that is created by user. The process of web service composition is started with user requests. The next section includes user context information. Also, service context information is used in the composition request. The next layer uses user requests, user context information, and service context information to produce a planning domain and a planning problem for the service composition. JSHOP2 uses the domain definition and the problem definition and produces a planner to perform list of services. The problem definition defines user requests, user context information, and service context information. In the domain definition, web service composition is based on user context information and service context information. The advantage of the new planning strategy for web service composition is the proposed framework uses user requests, user context information, and service context information. So, the services that do not have the appropriate conditions are not selected in web service composition, and the appropriate services are run based on the user requests and the quality of services. Also, the number of failures and composition time will be decreased. shows the CA-SCP architecture.
The scenario is finding a restaurant. Web services consist of a restaurant finder service, which provides a directory of available restaurants, a directions finder service, which computes the driving directions to a given restaurant and a translation service. The process of web service composition is started with user requests. For example, user requests for direction to Name1 restaurant. User context information includes user location, and user is driving. For example, user is located in Loc1 and is driving. Also, service context information includes response time, availability, and throughput. The next layer uses user requests, user location, response time, availability, and throughput and produces a planning for the service composition. JSHOP2 planning uses the domain definition and the problem definition and shows direction to Name1 restaurant.
Implementation
Planning in JSHOP2 consists of two files, the domain file and the problem file. The domain file defines the methods and the operators. The problem file defines objects that take part in the problem and the initial state and goals (García and Ortega Citation2009).
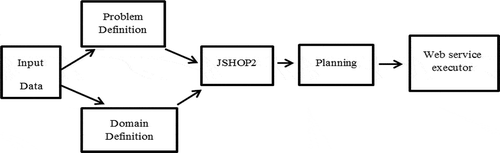
In our new planning algorithm, the problem definition defines user requests, user context information, and service context information. In the domain definition, web service composition is based on user context information and service context information, and both the user context and the service context are considered in service composition. So, the services that do not have the appropriate conditions are not selected in web service composition. As a result, the appropriate services are run based on the user requests and the quality of services. JSHOP2 uses the domain definition and the problem definition and produces a planner to perform list of services. displays steps for planning.
Domain definition
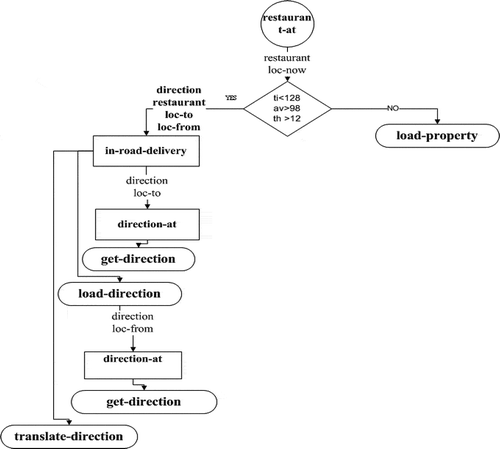
The domain defines the methods and the operators. displays implementation of the operators and methods for this example. shows the domain definition. The methods and the operators consist of the following:
Load-property operator shows response time and availability and throughput if their values do not conform to response time < 128, availability > 98, and throughput > 12. These conditions are for the implementation of appropriate services based on papers (Al-Masri and Mahmoud Citation2007; Vaadaala, Rajeswara, and Venkateswara Citation2013).
Load-direction operator shows restaurant, direction, and user location.
Get-direction operator shows direction, user current location, and user goal location.
Translate-direction operator is used for translation of the direction.
Restaurant-at method finds restaurant and shows restaurant and user current location.
In-road-delivery method finds direction and translates direction and shows direction, restaurant, user current location, and user goal location.
Direction-at method finds direction and shows direction and user location.
The definition of the problem will change when the user request and goals change. The definition of the domain will be the same, and all the problems are run in the domain.
Problem definition
The problem file defines objects that take part in the problem and the initial state and goals. The problem definition describes the environment that is applied to the domain. It also displays initial value of the variables and the relationships between different models components. It is necessary to define the plan (García and Ortega Citation2009). displays the problem definition. The problem definition describes restaurant, user current location, user goal location, response time, availability, and throughput.
In unordered tasks, restaurant-at shows restaurant and user current location. Property-at shows restaurant, user current location, response time, availability, and throughput. The application consists of a series of directions and roads. A direction belongs to a road, and direction cannot get out of that road. Each road is accessed in some locations. For example, road2 is accessed in Loc2-1, Loc2-2, and Loc2-3.
JSHOP2GUI1.0.1
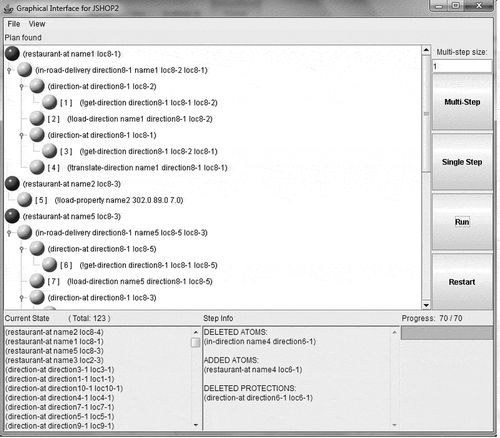
Although the JSHOP2 command line obtains a planning, it is difficult to analyze the different steps during the planning process. The graphical user interface (GUI) for JSHOP2 solves this problem by providing a way to analyze the task decomposition tree. The goal of the GUI is a quick and easy way to work with a program and users can see the graphical stages of the planning. Its main advantage is easy analysis of the results and finds possible errors in the algorithm (García and Ortega Citation2009). displays JSHOP2GUI program execution. The actions performed by JSHOP2GUI to find plans and a series of steps are represented in the GUI.
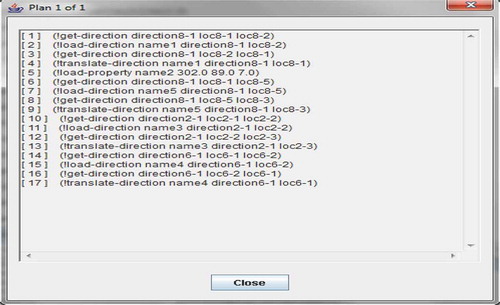
The main window of the GUI shows the task decomposition tree, and each node represents a task atom, and complex task is decomposed into subtasks. A blue node displays an unordered task, and yellow nodes display the planning process. The leaf nodes have a number surrounded by brackets preceding their task atom name that displays the position of action in the sequence of actions in the planning process. When a plan is found, a dialog box will be displayed that sequentially lists the current plan and how many total plans can be found in the problem (Shin Citation2006). shows what number the plan can be found in the problem.
The current state window displays the state of the world when the selected task atom was encountered in the planning process. The step information window displays related information about the current step in the planning process. In reduced step, this window displays the name of the method used to decompose the complex task. In state-changed step, this window displays the changes made to the current state by the initial task. The control buttons allow the user to iterate through steps of the planning process (Shin Citation2006).
Evaluation
This section presents the evaluation of the implementation of the CA-SCP framework for context-aware service composition. Experiment environment consists of the following:
CPU: Intel Core(TM)i5 (2.40 GHz);
MEMORY: 4.00 GB;
OS: Windows 7 (64-bit);
JAVA: 1.5.0.09.
Experiments
The experiments are similar to the proposed approach by Vukovic (Citation2007). The experimental evaluation shows the framework’s ability in the following experiments:
the increasing number of composition requests;
the reduction of number of failures;
the increasing number of composition requests that have achieved to the goals.
There are two steps in the experiments. First, according to the CA-SCP framework, service context information in service composition is considered. Secondly, service context information in service composition is not considered. The results of the second step are similar to the results of the experiments in base thesis (baseline) (Vukovic Citation2007). The experiments use QWS dataset developed by Eyhab Al-Masri and Qusay H. Mahmoud. The parameters that are measured in experiments include composition time and the number of failures. Our scenario for the implementation of web service composition is as follows:
We are located in Loc8-1 place and want to go Name1 restaurant. Service context information to find Name1 restaurant includes response time which equals 93, availability which equals 96, and throughput which equals 13. This service has the appropriate specifications and runs.
We are located in Loc8-3 place and want to go Name2 or Name5 restaurants. Service context information to find Name2 restaurant includes response time which equals 302, availability which equals 89, and throughput which equals 7. Also, service context information to find Name5 restaurant includes response time which equals 102, availability which equals 91, and throughput which equals 15. So, the service that has appropriate specifications is run and shows the direction of Name5 restaurant to the user.
We are located in Loc6-5 place and want to go Name7 restaurant. Service context information to find Name7 restaurant includes response time which equals 284, availability which equals 86, and throughput which equals 3. This service does not have the appropriate specifications and does not run.
displays the time that the planner could not find a solution for the composition request and the request has failed. The average time of a failed request takes approximately 333 ms (Vukovic Citation2007).
Figure 9. The average time of failed requests (Vukovic, Citation2007).
Experiment-1: Measuring the increasing number of composition requests
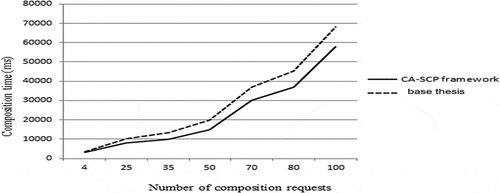
This experiment displays composition time to which the system responds to increasing number of concurrent composition requests. The number of concurrent composition requests was increased from 1 to 100. First, according to the CA-SCP framework, service context information and user context information and user requests are considered in service composition. shows comparison of number of concurrent composition requests and composition time in the CA-SCP framework.
Table 1. Number of composition requests and composition time in the CA-SCP framework.
Secondly, according to the base thesis, user context information and user requests are considered, and service context information is not considered in service composition. In the CA-SCP framework, the services that do not have the appropriate conditions are not selected in web service composition. According to the fact that the average time of a failed request takes approximately 333 ms, the time of service composition will increase in the base thesis. So, the composition time in the CA-SCP framework is less than the base thesis and in the CA-SCP framework, for 100 requests, 15% of composition time is improved. shows comparison of number of concurrent composition requests and composition time.
Experiment-2: Measuring the reduction of number of failures
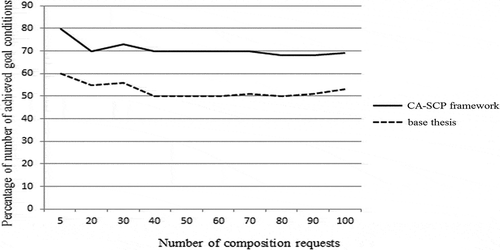
In this experiment, the number of achieved goal conditions was compared to the total number of goal conditions. First, according to the CA-SCP framework, service context information and user context information and user requests are considered in choosing services for implementation. Secondly, according to the base thesis, user context information and user requests are considered and service context information is not considered in choosing services for implementation, and the number of failures in the base thesis will increase. shows the results of this experiment.
In the CA-SCP framework, the services that do not have appropriate conditions are not selected in web service composition, and the percentage of number of achieved goal conditions is increased. So, the number of failures in the CA-SCP framework is less than the base thesis, and in the CA-SCP framework, for 100 composition requests, 30% of failures is improved.
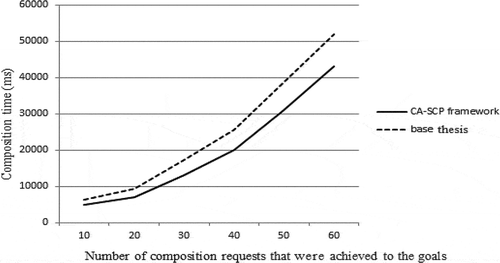
Experiment-3: Measuring the increasing number of composition requests that have achieved to the goals
This experiment displays increasing number of composition requests that have achieved to the goals on the composition time. The number of composition requests that have achieved to the goals varied from 1 to 60. First, according to the CA-SCP framework, service context information and user context information and user requests are considered in choosing services for implementation. shows the number of composition requests and composition time in the CA-SCP framework.
Table 2. Number of composition requests and composition time in the CA-SCP framework.
Secondly, according to the base thesis, user context information and user requests are considered and service context information is not considered in service composition, and a number of requests may fail. According to the fact that the average time of a failed request takes approximately 333 ms, the time of service composition will increase in the base thesis. shows the results of this experiment. So, the composition time in the CA-SCP framework is less than the base thesis, and in the CA-SCP framework, for 100 requests, 17% of composition time is improved.
Related work
This section describes related work in two main research categories: planning-based web service composition and context-aware web service composition.
Planning-based web service composition
In the following, we introduce web service composition methods based on AI planning. compares the planning methods.
Table 3. Comparison of the planning methods.
PDDL (Planning Domain Definition Language) is a widely accepted language used in AI planning to make planning problems and domains uniform. Planning tasks specified in PDDL consist of two files, a domain file and a problem file. The domain file is composed of the predicates that are used to describe the knowledge in the world and the actions that can change the world states. The problem file includes objects in the world, initial state, and goal specification (Yang and Zheng Citation2010). Golog is a logic programming language built on top of the situation calculus. The Golog language is a high-level programming language, and it is particularly designed for the specification and execution of complex actions in dynamic domains. Further, Golog is adopted as a natural formalism for representing and reasoning about problems (Chan, Bishop, and Baresi Citation2007; Peer Citation2005). OWLS-Xplan consists of several modules for preprocessing and planning. It takes a set of available OWL-S services, a domain description consisting of relevant OWL ontologies and a planning query as input, and returns a plan sequence of composed services that satisfies the query goal. For this purpose, OWLS-Xplan first converts the domain ontology and service descriptions in OWL and OWL-S, respectively, to equivalent PDDL2.1 problem and domain descriptions using its OWLS2PDDL converter (Klusch and Gerber Citation2006). SWORD is a toolset for web service composition. In SWORD, a service is represented by a rule that expresses that given certain inputs, the service is capable of producing particular outputs. A rule-based expert system is used to automatically determine whether a desired composite service can be realized using existing services. If so, this derivation is used to construct a plan that when executed instantiates the composite service (Ponnekanti and Fox Citation2002).
Context-aware web service composition
In this section, we present an overview of the existing context-aware web service composition approaches. compares these approaches.
Table 4. Comparison of context-based web services composition approaches.
Vukovic (Citation2007) developed a framework for finding a restaurant. This framework includes mechanisms for automatic recovery from failures that may occur during the web service composition and execution process. This framework is based on TLPlan planning and uses user context information and does not consider service context information. Gupta and Bhanodia (Citation2014) presented a mechanism for dynamically recovering failure of composite web services. This method is based on the policy of subset replacement in a set of composite web services. This implemented method enables the user to avail the entire complex and intricate services offered by today’s business organizations and thus helps in meeting the user’s requirements. In the case of failure or non-functioning of a web service, the proposed method covers up the failure by replacing the failed web services by their equivalent subset calculated using QoS parameters. Nadkarni et al. (Citation2011) introduced a composition algorithm that can provide feedback to the user regarding the cause of failure in the composition process. Such feedback will help guide the user to reformulate the goal service and iterate the composition process. They proposed a failure analysis technique for composition algorithms that views web service behavior as multiple sequences of input/output events. This technique identifies possible cause of composition failure and suggests possible recovery options to the user. Zhou et al. (Citation2011) developed an architecture for context-aware pervasive service composition (CAPSC), which aims at enabling a pervasive system to provide user service compositions that are relevant to the situation at hand. This architecture enables applications that are flexible and adaptive to changes. Many efforts have been made on context definition, quality of contextual information, context management platforms, and extended context-aware applications. They investigate a design process for building CAPSC applications and categorize these applications into three groups such as peer coordination adaptation, process service adaptation, and utility service adaptation. Furno and Zimeo (Citation2013) presented a design approach that exploits semantics for modeling contexts and related systems behaviors. The context model extends the OWL-S ontology to enrich the expressiveness of each section of an OWL-annotated service, by means of conditions and adaptation rules. These additional descriptions can be exploited by a discovery or composition tool to automatically find the services better-tuned to the requestor’s behaviors and the particular situations of the environment. Pietschmann, Voigt, and Meißner (Citation2009) presented an approach for the service-oriented and context-aware composition of rich web-user interfaces. They specify a generic model for configurable web components, a corresponding service-based deployment method and a run-time system. To validate their approach, they build a prototype illustrating the dynamic composition of the user interface from components of different technologies, and communication via a generic interface. Zeng et al. (Citation2008) presented a new framework for dynamic service composition and optimization. In this approach, individual web services are choreographed into composite Web services whose integration logics are expressed as composition schema. They implemented a prototype to validate the feasibility and benefits of the proposed approach. The results of the proposed approach show that the computation cost is still acceptable when the number of tasks and inference rules are fairly large. Baidouri et al. (Citation2012) introduced an approach for the context-aware composite service metamodel. This approach uses a strategy pattern that allows dynamic composition without any duplication or regression risks and generates the Context-Aware Composition Builder tool. They presented their Context-Aware Composition Builder tool that reposes in a pattern and exploit context-aware composite service metamodel in dynamic composition of services depending on the current user context. Luo et al. (Citation2006) developed a framework that enables context-aware composition of web service. This framework performs capability matches and composes service flow based on goal-driven. Then, it filters out unsuitable compositions of matched services according to available context information. They modeled composite service with Petri nets and validate the correctness of the model by using an analysis method, called reachability tree, thus ensuring a smooth execution of a composite service.
Conclusions
In this paper, we have presented our context model and the CA-SCP framework for context-aware web service composition based on planning. We have implemented a web service composition using JSHOP2GUI. Context helps to identify the appropriate services for the main purpose. In our new planning strategy, at the planning stage, web service composition is based on user requests, user context information, and service context information. The services that do not have the appropriate conditions are not selected in web service composition. As a result, the appropriate services are run based on the user requests and the quality of services. So, the number of failures and composition time will be decreased.
Future work in context-aware web service composition can include that user can directly select the path of tasks decomposition in JSHOP2GUI1.0.1, based on service context information and user context information.
References
- Al-Masri, E., and Q. H. Mahmoud 2007. Discovering the best web service. In Proceedings of the16th International Conference on World Wide Web, 1257–58. New York, USA.
- Baidouri, H., H. Hafiddi, M. Nassar, and A. Kriouile. 2012. Towards a Context-Aware Composition of Services. International Journal of Computer Science and Network Security 12 (3):133–140.
- Chan, M., J. Bishop, and L. Baresi. 2007. Analysis of planning techniques for web service composition. Department of Computer Science, University of Pretoria, South Africa.
- Dey, A., D. Salber, and G. Abowd. 2001. A conceptual framework and a toolkit for supporting the rapid prototyping of context-aware applications. Human-Computer Interaction 16:97–166.
- Dustdar, S., M. Baldauf, and F. Rosenberg. 2007. A survey on context-aware Systems. International Journal of Ad Hoc and Ubiquitous Computing 2 (4):263–277.
- Furno, A., and E. Zimeo. 2013. Context-aware design of semantic web services to improve the precision of compositions. Context-Aware Systems and Applications 109:97–107.
- García, F. J. P. 2011. Refactoring planning for design smell correction in Object-oriented software. Doctoral dissertation, Department of computer engineering, Almería University.
- García, C. M., and G. M. Ortega. 2009. Route planning algorithms: Planific @ Project. International Journal of Artificial Intelligence and Interactive Multimedia 1 (2):57–66.
- Gupta, S., and P. Bhanodia. 2014. A flexible and dynamic failure recovery mechanism for composite web services using subset replacement. International Journal of Science and Research 3 (12):1886–1890.
- Ilghami, O. 2006. Documentation for JSHOP2. Technical Report CS-TR-4694, Department of Computer Science, University of Maryland, College Park, MD.
- Klusch, M., and A. Gerber 2006. Evaluation of service composition planning with OWLS-XPlan. Proceeding of 2006 IEEE/WIC/ACM International Conference on Web Intelligence and Intelligent Agent Technology, 117–120. Washington, DC, USA.
- Luo, N., J. Yan, M. Liu, and S. Yang 2006. Towards context-aware composition of web services. Proceedings of the 5th International Conference on Grid and Cooperative Computing, GCC’06, 494–99. Changsha, Hunan, China.
- Nadkarni, D., S. Basu, V. Honavar, and R. Lutz 2011. Failure analysis for composition of web services represented as labeled transition systems. Proceedings of the 7th international conference on Web services and formal methods, 161–75. NJ, USA.
- Nalepa, G. J., and S. Bobek. 2013. Rule based solution for context-aware reasoning on mobile devices. Computer Science and Information Systems 11 (1):171–193.
- Nau, D., T. Au, O. Ilghami, U. Kuter, J. W. Murdock, D. Wu, and F. Yaman. 2003. SHOP2: An HTN planning System. Journal of Artificial Intelligence Research 20:379–404.
- Peer, J. 2005. Web service composition as AI Planning—a survey. Technical report, University of St. Gallen, Switzerland.
- Pietschmann, S., M. Voigt, and K. Meißner 2009. Dynamic composition of service-oriented web user interfaces. Proceedings of the 4th Intl. Conf. on Internet and Web Applications and Services (ICIW 2009), 217–22. Venice, Italy.
- Ponnekanti, S. R., and A. Fox 2002. Sword: A developer toolkit for web service composition. Proceedings of the 11thWorld Wide Web Conference (Web Engineering Track), Honolulu Hawaii, USA.
- Shin, J. 2006. A graphical interface for JSHOP2. Department of Computer Science, University of Maryland, College Pak, USA.
- Vaadaala, V., R. R. Rajeswara, and R. K. Venkateswara. 2013. Classification of web services using JForty Eight. International Journal of Electronics Communication and Computer Engineering 4:181–184.
- Vukovic, M. 2007. Context aware service composition. doctoral dissertation, university of Cambridge computer laboratory.
- Yang, B., and Q. Zheng. 2010. Composing semantic web services with PDDL. Information Technology Journal 9 (1):48–54.
- Zeng, L., A. H. H. Ngu, B. Benatallah, R. Podorozhny, and H. Lei. 2008. Dynamic composition and optimization of Web services. Distrib Parallel Databases 24:45–72.
- Zhou, J., E. Gilman, J. Palola, J. Riekki, M. Ylianttila, and J. Sun. 2011. Context-aware pervasive service composition and its implementation. Personal and Ubiquitous Computing 15 (3):291–303.