?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.ABSTRACT
VANET provides communication between vehicles. VANET nodes are highly dynamic. Therefore, it is essential to increase the stability of the communication between nodes. The cluster head and cluster node provide stable communication between vehicles. Vehicle communications are being challenged by factors such as security, confidential communication, and severe delay. This work proposes an Artificial Intelligence (AI)-based Sugeno fuzzy inference system to overcome these issues. The proposed secure trust-based cluster techniques are less complex, with lesser communication delays, lower overhead, and more efficient in accurately locating trusted nodes for communication. Vehicular Ad hoc Networks (VANET) should send data between vehicles and use traffic safety indicators using an Enhanced Cluster-based routing protocol. AI-TASFIS is Artificial Intelligence-based Trust Authentication Sugeno fuzzy inference system that uses ANFIS-based Sugeno Fuzzy inference systems to calculate the node weights for choosing trusted cluster head and cluster member that reduces malicious attacks like Black Hole Attacks, Wormhole attacks, and Timing Attacks while transferring data packets. Simulation results show that the proposed Artificial Intelligence (AI)-based Sugeno fuzzy inference system provides network security, reduces end-to-end delay, and increases packet delivery ratio and throughput.
Introduction
With the increase in intelligent cities, the demand for intelligent journey traffic tracking and congestion management, the primary traits of smart cities, is also increasing. The increase in visitor congestion and the inefficiency of wireless conversation systems for site visitor control have started the idea of Intelligent Transportation Systems (ITS). Using VANET, one could achieve ITS essential dreams, along with congestion control, visitor safety, effective use of infrastructure, and secure vehicle-to-vehicle communication. The vehicle installed in an ad hoc community improves and integrates the Wi-Fi conversation era, sensible transportation systems, and automobile manufacturing technology. These are considered unique subdivisions of Mobile Ad-Hoc Networks (MANETs) and automobile nodes with unique characteristics and requirements.
VANET is a group of cell organizations and (roadside unit) corporations working together to alternate essential statistics regarding avenue conditions and other vehicles. Routing is necessary for the robust operation of VANET, and overall network performance is intently related to it. The achievement of VANET relies upon the reliability of sending messages from the supply node to the target node. In addition, real-time sharing of embedded information and road protection services is considered a crucial part of the routing process, supplying passengers with the necessary records to make safety selections.
Fuzzy is commonly known for its capacity to cope with complex and misguided problems, and it is by far the most promising era in this dynamic and challenging situation. On the other hand, significant quantities of statistics in the delivery device are critical for distributing facts. Effective use of dense records requires powerful methods of historic processing statistics, including Machine Learning (ML). There are two types of fuzzy inference systems: the Mamdani fuzzy inference system and the Sugeno fuzzy inference system. The first introduced system was Mamdani fuzzy logical system, combining linguistic control rules derived from experienced human operators to form a control system. In the Mamdani system, the output of each rule is a fuzzy set. On the other hand, Sugeno FIS uses a weighted average to calculate the sharp output.
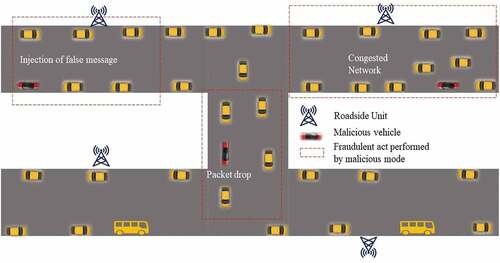
describes the impact of a malicious node in the communication zone of VANET. If a malicious node is present, this node can induce a heavily congested network, inject a false message into the stream, and intentionally drop the packet. Machine Learning system and an artificial intelligence (AI)-based fuzzy inference system use multiple indicators of neighboring vehicles and fuzzy logic to determine which vehicle is at the best no-traffic shortest path and which vehicle is the trusted vehicle to transfer data packets. The node with the minimum distance, speed, progression, and angular deflection from the current forward node to the target is selected as the next hop. However, the protocol only considers the vehicle’s current condition when making a decision and does not consider the impact of the decision. Based on our Fuzzy rule, a trusted cluster head and a trusted cluster member are only allowed to do the communication. Adaptive neuro-fuzzy inference systems are used to select secure and trusted cluster head and cluster members for broadcasting safety messages and the shortest path is selected for transferring emergency-based messages.
The main contribution of the paper includes
Adaptive neuro-fuzzy inference system (ANFIS) is used to select a trusted cluster head and cluster member.
The input parameters are trained in ANFIS so that malicious nodes are blocked at the initial stage of communication.
Sugeno fuzzy inference is used for the transmission of emergency-based messages in VANET by analyzing the transmission range, weight of the node and hop count which makes faster transmission of messages.
Enhanced cluster-based routing protocols are used to provide high packet delivery ratio, reduce delay, high throughput, and to provide secure and trusted communication between nodes.
Related Works
Lin et al. (Citation2020) proposed a paper on vehicle assistance repeaters in complex communication situations and supported land-based communications. A UAV subnet needs to focus on existing work routing protocol and not efficiently use UAV and its flexibility. Lu et al. (Citation2020) proposed an article on the authentication program that protects against malicious marginal attackers and aims to send deceptive signals to attack the VANET. Shah et al. (Citation2018) discussed that the authentication system uses the channel status of the environmental radio signal shared by the mobile device. It uses reinforcement learning to select its service margin (e.g., vehicle-fitted unit), authentication method, and parameters along the same trajectory. Cárdenas et al. (Citation2021) proposed a paper where a network of vehicles that has groups of vehicles connected wirelessly is called a transient network. Clustered networking is an era designed to enhance the verbal exchange functionality of an automobile network. Shu et al. (Citation2021) discussed that each cluster has a cluster head (CH), which is used to maintain the whole group, and all conversation is completed through CH. In other phrases, inter-cluster and intra-cluster communication are used between vehicle nodes. Maalej et al. (Citation2018) discussed that routing protocols designed for automotive networks must be flexible and adapt to such networks inherent dynamic network behaviors. Therefore, assertive automobile communication will enhance overall driving performance and reduce unforeseen troubles. According to Wu et al. (Citation2015), a Vehicle Ad hoc Network (VANET) permits intelligent traffic systems to provide various beneficial services but is susceptible to many intrusions. Fukuoka et al. (Citation2019) discussed the Intrusion Detection System (IDS), which mitigates safety threats by detecting abnormal community behavior of nodes. However, the cutting-edge IDS answers most effective exist to stumble on typical community pastimes on the neighborhood subnet and not at the VANET. Hung et al. (Citation2019) provided a handy solution that includes multi-technique item detection, authentication, and mapping which are primarily based on stereo camera frame, point scanning, V2 V (Vehicle-2-Vehicle), and primary safety records transmission fusion. Najib and Moh (Citation2020) discussed on existing multi-hop broadcast protocol automobile ad hoc networks that are no longer considered a way to alter the transmission parameters of the community environment. According to Zhou et al. (Citation2018), along with the diffusion surroundings that determine the channel errors fee, the size of the records packet payload also has a first-rate impact on the data packet loss price. Method of evaluating the network conduct of a brief wireless network is based totally on information switch movement evaluation.
Arafat and Moh (Citation2019) discussed that for the safe and dependable operation of future self-sufficient cars, a Vehicle-To-Vehicle (V2 V) communication network is required. According to Li et al. (Citation2019), however, Vehicle to Infrastructure (V2I) communication remains needed due to the scaling issues of completely self-regulating networks. To address these provider challenges to a point, the Vehicle Ad hoc Network (VANET) has been an exquisite way to enhance car offerings and programs by equipping vehicles with wireless and processing abilities. Tang et al. (Citation2019) discussed on Unnamed Aerial Vehicles (UAVs) that are broadly utilized in numerous navy and civilian applications and offerings. Nodes regularly omit a few broadcast messages at the institution key. Yang et al. (Citation2020) discussed that establishing and maintaining an end-to-end connection in a Vehicle Ad Hoc Network (VANET) is challenging due to the high mobility of vehicles, dynamic vehicle spacing, and varying vehicle density. Vehicle motion forecasting can meet these challenges by providing enhanced average VANET performance based on greater route planning and consistent service availability. Hossain et al. (Citation2020) discussed that the Vehicle ad hoc Network (VANET) is designed to aid the quickest development variety of automobiles. In this regard, it is hoped that every V2 V customer will use larger bands to generate directional, increase the spatial reuse price, and synchronize transmission. Nie et al. (Citation2019) proposed that the Vehicle Ad hoc Network (VANET) is expected to play a crucial role in lowering street injuries and visitor congestion. Large quantities of records need to be exchanged to ensure this role. Fatemidokht et al. (Citation2021) discussed that in the early degrees of VANET, several research issues want to be addressed, including protection and security problems due to open wireless networks in city programs. Khan et al. (Citation2019) discussed that detecting VANET anomalies is particularly tricky as the VANET architecture has been modified compared to the conventional Wi-Fi network. Ghaleb et al. (Citation2020) discussed the improved movement of motors and common connectivity disruptions that make routing a difficult task in these networks. Therefore, there are numerous issues and obstacles in developing a robust routing protocol that satisfies delays in the web. An et al. (Citation2019) proposed a non-linear control system design is carried out, summarizing the concepts in radio connection analysis. An, Liu, and Wen (Citation2017) discussed the Fuzzification-rule intersection of rule pairs that never occurs was discovered using a new event-sharing theory. According to Mendel, Chimatapu, and Hagras (Citation2020), fuzzification can reduce, increase, or decrease the number of second-tier rule partitions, all of which depend on the systematic micro engraving of state space. The practical application of multi-dimensional models and restructuring reduces computational overlays in the linear non-structural analysis. Alolaiyan et al. (Citation2019) proposed a paper on fuzzy sets, Pacification is a step of data pre-processing, and there is little research into using fuzzy rough sets. Ajayi, Babahaji, and Aghdam (Citation2021) proposed a simple opacity method that derives a fuzzy distinction from the most essential features selection application cuts.
Proposed Work
Vehicle Ad hoc Network (VANET) is one of the most promising technologies in the intelligent transportation system that provides traffic safety. A trust-based accreditation program for selecting an authenticated and trusted cluster-based vehicular ad hoc networking has been proposed in this paper. Cluster vehicles are used to increase the reliability of communication. Trust is a grouping of direct and indirect acceptance nodes, and the cluster head is selected based on its estimated trust.
To provide secure and reliable communication, Artificial Intelligence (AI)-based Trust Authentication Sugeno Fuzzy inference systems are proposed in which rules are framed according to specific scenarios and parameters. The adaptive transformation of the rotation security broadcast is realized through the simulation of the proposed Artificial Intelligence (AI)-based Trust Authentication Sugeno Fuzzy inference systems. The NS3.34 simulator is used to show performance improvements in packet delivery ratio, end-to-end delays, packet loss rates, and throughput.
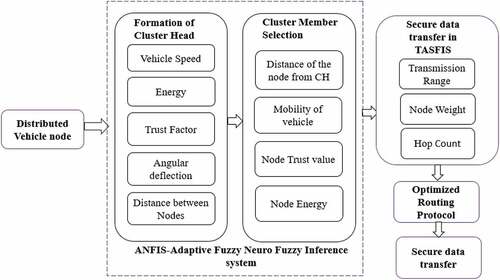
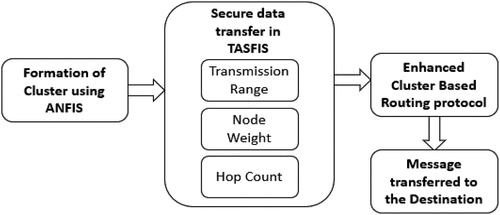
describes the proposed block diagram for a vehicle-to-vehicle communication which is based on the Sugeno fuzzy inference system included with the adaptive neuro-fuzzy inference system. Initially, the cluster head and cluster node are formed by calculating the weight of the node using ANFIS. The vehicle node with the highest weight is selected as the cluster head and vehicles traveling in the same locality are selected as the cluster node. The weight of the particular node is framed by the Sugeno Fuzzy inference system IF-THEN rules. The defuzzified output is the weight of the node. Next, node-to-node secure data transfer is initiated by TASFIS for emergency messages that need to be transmitted immediately. The Sugeno Fuzzy Inference system is used to select a genuine node for emergency data transfer. Section 3.1 gives a brief explanation of the ANFIS model.
Adaptive Neuro-Fuzzy Inference System Model for VANET
The Adaptive neuro-fuzzy inteference system (ANFIS) is a Takagi Sugeno-type fuzzy system with a neural learning network. These structures use Artificial Neural Networks (ANN) and fuzzy logic. ANFIS analyses the node weights training in the neural network and evaluates the Sugeno fuzzy inference system that results in the accurate learning and fine-tuning function of membership function parameters based on linguistic and numerical functions.
If two rules are used, then If-Then rules are used in the ANFIS structure is given as
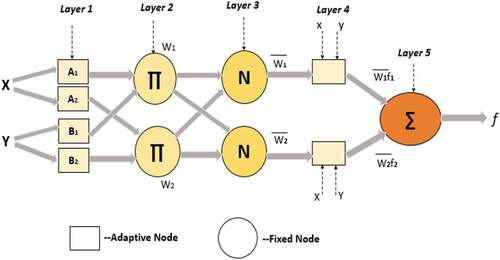
shows that there are five layers in the ANFIS architecture. The five layers contain adaptive nodes, the other layers contain fixed nodes. X and Y are inputs, A1 and B1 are linguistic variables, .
are consequent parameters.
Layer 1: First layer membership function as node function with the adaptive parameters for every node
where X is input values, is fuzzy variable membership function,
is adaptive parameters.
Layer 2: In this layer of each node called the fixed node, it is performed based Sugeno fuzzy model
Layer 3: In the fixed node calculates each node weights (speed, energy, time) or strength,
Layer 4: Each node =, is an adaptive value with node function
Layer 5: Fixed particular node calculates overall output as the summation of all input values from layer
Updated premise and result values to reduce errors based on the ANFIS algorithm
where A and B are set of inputs to apply an artificial neural network-based FIS functionally equivalent to a diffusion inference system, one can apply all the typical neural network training algorithms. In the proposed work, cluster head and cluster member are selected using the Adaptive Fuzzy Neuro-Fuzzy Inference system.
Cluster Head Formation
In the cluster formation with VANET, the nodes are split into smaller groups of mobile vehicles equipped with computing and network equipment. Each collection of the group has a cluster head (CH) who is responsible for all management and coordination tasks of the cluster. The VANET clustering algorithm combines an AI algorithm with an Adaptive neuro-fuzzy inference technique to make clustering more stable and efficient.
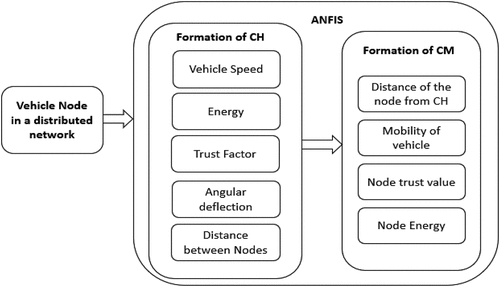
depicts the block diagram for the formation of cluster head and cluster node selection. Weight-based clustering has been developed to meet these challenges. Vehicles traveling within the same road section, speed, energy, trust, distance between nodes, and angular deflection of the vehicle node are considered suitable for selecting the cluster head. The cluster head is the node selected based on the node weight. The inputs are trained using ANFIS and based on trained parameters crisp weight is got at the output layer. This node with the highest weight is selected as a cluster head.
Algorithm Steps
Cluster Head Formation:
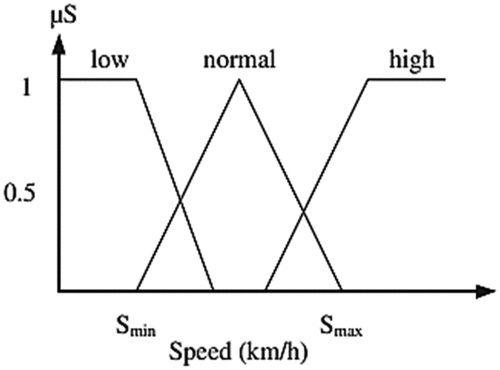
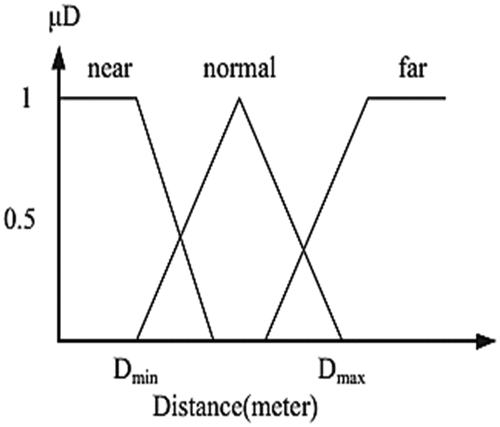
In the proposed work for the selection of the cluster head, five parameters are taken as the input with three membership functions each. These fuzzified inputs are given to the Sugeno Fuzzy inference system. IF-THEN rules are framed using AND Connectors. Then ANFIS models are trained using the rules framed. For the selection of the cluster head, five inputs are used with the three membership functions hence there were 243 rules framed for electing the cluster head. With these 243 rules, 70% are used for training data, 30% for data testing, and 10% are used for data checking. shows the fuzzified input membership functions for ANFIS and shows the calculation of the weight factor.
Table 1. Fuzzified input membership function for ANFIS.
Table 2. Calculation of weight factor.
Number of IF-THEN rules framed = 35 = 243 rules.
show the highway constraint of the network topology, and the vehicle naturally moves in groups on the road with distance and speed. These factors cause the development of VANET clustering algorithms to reduce bandwidth usage and give high efficiency and reliability to VANET communication.
Selection Parameter for the Formation of the Cluster Member
The vehicles will be in a distributed ad hoc structure at the initial stage. The ANFIS model chooses the cluster head based on the node’s weight. These cluster heads are chosen to decrease the bandwidth usage and increase the efficiency of the communication network.
After the selection of the cluster head, cluster members are selected. Road side unit sends the CH Vehicle identity to all the other nodes, then the nodes traveling on the same roadside send the message to the CH requesting to join as a cluster member. Now cluster head checks the distance of the node from its location, the speed of the vehicle, Node energy, and the Trust factor of the node. Each node is trained using ANFIS. Here, for selecting a cluster member, four inputs are given with three membership functions, and 81 rules are framed for selecting a cluster member. After getting trained using ANFIS, higher weights nodes are selected as a cluster member, and the node with the low weight is rejected from the communication link. Cluster member is a node that joins the cluster head. Each node joining the cluster head should be adequately validated.
Number of IF-THEN rules framed = 34 = 81 rules.
Node-to-Node Trust Authentication for Packet Transmission
After the cluster head selection, the vehicle node sends the message to the cluster head to become its cluster member. The cluster head should allow only the nodes which come under its covering range, it should only accept the trusted node, not the malicious node The trustworthiness estimation is done by the cluster head (CH) for selecting the cluster member.
Steps for trust-based authentication
Initially, it transfers the key pairs and permits would be distributed to the formal nodes that wanted to join the ad-hoc network. It can enter the key manually or by secure transmission protocol to protect the vehicle transmitting the information. A private key (symmetric key) is only one secret key and the certificate can be used to communicate with other vehicles on the VANET. The vehicle communicates with CA via RSU (Roadside Unit). After cluster head and cluster member selection the nodes can either transfer the data inside its cluster or with another cluster. When data are transmitted from one node to another then node-to-node trust authentication should be carried out. Where T-Trust degree, Tdtd, is the direct trust degree. The authentication node will submit its identity and certificate to the received node. The authentication node first checks the Certified Authority (CA) with the cluster head public key. It challenges the node by sending the private key to the destination to check the corresponding public key.
This selection of CH and CM efficiently transfers broadcasted messages with a minimum delay. Every vehicle consists of an on-board unit that connects with other nodes using DSRC – dedicated short-range communication protocol. The message format in VANET can be divided into two types as basic safety messages and emergency-driven messages. Basic safety messages include anti-crash warnings, pedestrian crossing, etc. The emergency message alerts the driver that there is an accident ahead and chooses an alternate path when providing a way to an ambulance. When some vehicle users have been stalked, emergency-type messages are forwarded to other users to seek attention from the genuine user to get help.
Trust Authentication Sugeno Fuzzy Inference Systems (TASFIS)
describes the block diagram of the secure data transfer using TASFIS. The Trust Authentication Sugeno fuzzy inference system is used in VANET to select a safe route for transferring emergency-driven messages. Based on the Trust Authentication Sugeno fuzzy algorithm, the node weight, transmission range, and hop count is taken with three membership function each. The Sugeno method has developed a systematic approach to generating fuzzy rules from a particular input/output dataset. Trust Authentication Sugano type FIS calculates weighted average output. IF-THEN rules used in TASFIS help the node user to select the optimal and safest path to transfer the emergency data packets. In TASFIS, minimum rules are only framed using Sugeno fuzzy inference system to get crisp output. shows the rules framed for secure data transfer from one node to another node.
Table 3. Rule-based vehicle status.
Number of IF-THEN rules framed = 33 = 27 rules.
Enhanced Cluster-Based Routing Protocol
In the proposed work, packet transmission is done based on the designed algorithm. Cluster heads are elected based on the average speed a node maintains, the distance of the node from its cluster member, angular deflection, trust metrics, and the energy of the node. The parameters are trained using an adaptive neuro-fuzzy inference system to select the best and trusted node as a cluster head responsible for transferring secure messages to other nodes. After the cluster head cluster member is formed, it is again trained using ANFIS and ensured that only a trusted node joins the cluster head. If a node wants to leave and join the other cluster, it can leave the network and join the other cluster head by sending a request message. Packets are transmitted within its cluster head and member. This cluster head and cluster member communication of the network increases the efficiency of the network, reduces traffic delay of the network, increases node lifetime reduces the bandwidth usage of the network.
Result and Discussion
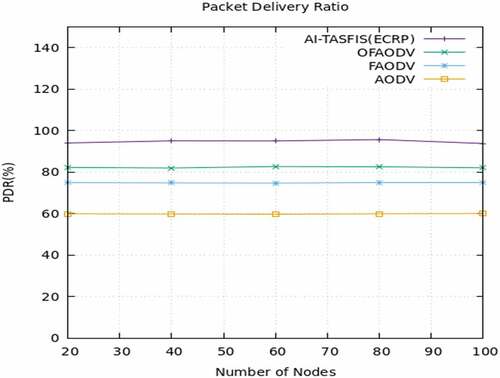
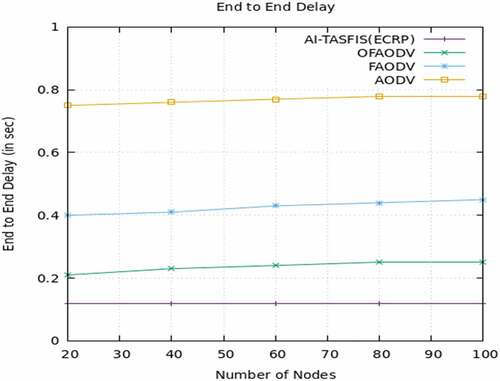
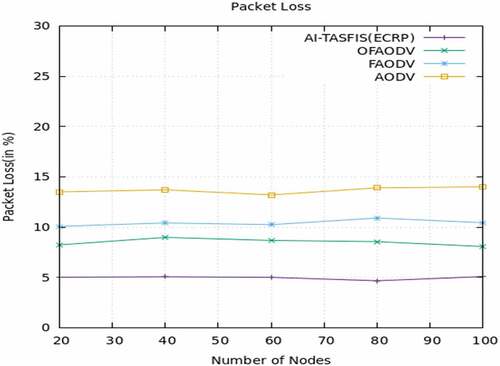
The proposed work is done using Network Simulator-3.34 and experimental results are analyzed. The proposed protocol AI-TASFIS(ECRP) is Artificial Intelligence-Trust Authentication Sugeno Fuzzy inference system with Enhanced Cluster-based Routing protocol performance are analyzed and compared with the existing routing protocol. Fahad and Ali (Citation2020) proposed a paper on Fuzzy-based multiobjective routing protocol in VANET and compared routing algorithms such as the Optimized fuzzy Ad-hoc on-demand Distance Vector (OFAODV), Fuzzy Ad-hoc On-demand Distance Vector (FAODV), and AODV routing protocol [26]. The proposed method is compared with the existing method in performance measures such as throughput, packet delivery ratio, End-to-End Delay, and Packet loss ratio. shows the simulation parameter used.
Table 4. Simulation parameters.
Throughput:
Throughput is defined as the total number of packets received at the destination to the time taken.
End-to-End Delay (s):
End-to-end delay refers to the sum of all delays in the link caused by intermediate nodes – the total time taken by a packet to reach from a sender to receiver vehicle. It is computed as the sum of all communication delays.
Packet delivery ratio (%):
The packet delivery ratio is defined as the ratio of the total packets received at the destination to the total packets generated at the source node.
Packet loss ratio (%):
Packet loss ratio is defined as the ratio of the number of lost packets to the received packets.
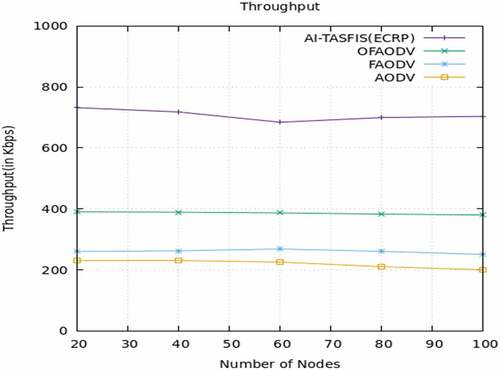
show the performance analysis of throughput, packet delivery ratio, packet loss ratio, and end-to-end delay of existing and proposed approach.
Table 5. Performance analysis of throughput and packet delivery of existing and proposed approach.
Table 6. Performance analysis of packet loss ratio and end-to-end delay of existing and proposed approach.
show the performance analysis of throughput, packet delivery ratio, end-to-end delay, and packet loss ratio. respectively. The proposed algorithm AI TASFIS(ECRP) is compared with the existing protocol OFAODV, FAODV, and AODV. When compared to the existing algorithm. AI TASFIS(ECRP) provides a high packet delivery ratio of 95%, lower End-to-End delay of 0.16s, high throughput of 732.310 kbps, and less packet loss ratio of 5%
Conclusion
Vehicle Ad Hoc Network (VANET) and its support services are essential to an intelligent transportation system. Fuzzy packages are suitable for approximate reasoning, and estimates can be used to make conclusions when information is incomplete or uncertain. Artificial Intelligence-based Sugeno Fuzzy Inference System (AI-TASFIS) has the knowledge and experience of experts in the design of regulatory systems. The process by which a set of Fuzzy control rules defines input/output relations. Artificial Intelligence calculates a vehicle’s reliability based on its trust metrics. AI-TASFIS concentrates both on emergency and basic safety messages. The simulation results show the effectiveness of the proposed method. In the proposed Artificial Intelligence-based Sugeno Fuzzy Inference System (AI-TASFIS) analysis, the packet delivery ratio is 95%, delay performance is 0.16 s, throughput performance is 732.311 kbps, and packet delivery ratio is 95%. By adopting AI technology, the effectiveness of the proposed can be further improved.
Data Availability
All the data used are mentioned in the manuscript itself.
Disclosure statement
No potential conflict of interest was reported by the author(s).
Additional information
Funding
References
- Ajayi, O., M. Babahaji, and A. Aghdam. 2021, September. A multi-spectral approach to fuzzy quantum modelling of nonlinear systems. IEEE Journal of Radio Frequency Identification 5(3):254–3525. doi: 10.1109/JRFID.2021.3066884.
- Alolaiyan, H., U. Shuaib, L. Latif, and A. Razaq. 2019. T-intuitionistic fuzzification of lagrange’s theorem of intuitionistic fuzzy subgroup. IEEE Access 7:158419–26. doi:10.1109/ACCESS.2019.2950167.
- An, J., X. Liu, and G. Wen. 2017. Stability analysis of delayed takagi-sugeno fuzzy systems: A new integral inequality approach. Journal of Nonlinear Sciences and Applications 10 (4):1941–59. doi:10.22436/jnsa.010.04.53.
- An, J., Y. Yu, J. Tang, and J. Zhan. 2019. Fuzzy-based hybrid location algorithm for vehicle position in VANETs via fuzzy Kalman filtering approach. Advances in Fuzzy Systems 2019: Article ID 5142937, 11 pages. doi: 10.1155/2019/5142937.
- Arafat, M. Y., and S. Moh. 2019.Routing protocols for unmanned aerial vehicle networks: A survey. IEEE Access 7: 99694–720. doi: 10.1109/ACCESS.2019.2930813
- Cárdenas, L. L., A. M. Mezher, P. A. Barbecho Bautista, J. P. Astudillo León, and M. A. Igartua. 2021.A multimetric predictive ANN-based routing protocol for vehicular ad hoc networks. IEEE Access 9: 86037–53. doi: 10.1109/ACCESS.2021.3088474
- Fahad, T. O., and A. A. Ali. 2020. Multiobjective optimized routing protocol for VANETs. Hindawi Advances in Fuzzy Systems 2018: Article ID 7210253, 10 pages. 10.1155/2018/7210253.
- Fatemidokht, H., M. K. Rafsanjani, B. B. Gupta, and C.-H. Hsu. 2021, July. Efficient and secure routing protocol based on artificial intelligence algorithms with UAV-assisted for vehicular ad hoc networks in intelligent transportation systems. IEEE Transactions on Intelligent Transportation Systems 22(7):4757–69. doi: 10.1109/TITS.2020.3041746.
- Fukuoka, K., M. Yamamoto, T. Yokotani, M. Saito, and Y. Terashima. 2019. Network behavior estimation method for wireless ad-hoc networks by analyzing data transmission traffic. Twelfth International Conference on Mobile Computing and Ubiquitous Network (ICMU), Kathmandu, Nepal, pp. 1–4.
- Ghaleb, F. A., B. A. S. Al-Rimy, A. Almalawi, A. M. Ali, A. Zainal, M. A. Rassam, S. Z. M. Shaid, and M. A. Maarof. 2020.Deep Kalman neuro fuzzy-based adaptive broadcasting scheme for vehicular ad hoc network: A context-aware approach. IEEE Access 8: 217744–61. doi: 10.1109/ACCESS.2020.3040903
- Hossain, M. A., R. M. Noor, K.-L.A Yau, S. R. Azzuhri, M. R. Z’Aba, and I. Ahmedy. 2020. Comprehensive survey of machine learning approaches in cognitive radio-based vehicular ad hoc networks. IEEE Access 8: 78054–108. doi: 10.1109/ACCESS.2020.2989870
- Hung, S., X. Zhang, A. Festag, K. Chen, and G. Fettweis. 2019. Vehicle-centric network association in heterogeneous vehicle-to-vehicle networks. IEEE Transactions on Vehicular Technology 68 (6):5981–96. doi:10.1109/TVT.2019.2910324.
- Khan, A. A., M. Abolhasan, W. Ni, J. Lipman, and A. Jamalipour. 2019, July. A hybrid-fuzzy logic guided genetic algorithm (H-FLGA) approach for resource optimization in 5G VANETs. IEEE Transactions on Vehicular Technology 68(7):6964–74. doi: 10.1109/TVT.2019.2915194.
- Lin, N., L. Fu, L. Zhao, G. Min, A. Al-Dubai, and H. Gacanin. 2020, July. A novel multimodal collaborative drone-assisted VANET networking model. IEEE Transactions on Wireless Communications 19(7):4919–33. doi: 10.1109/TWC.2020.2988363.
- Li, X., Y. Wang, P. Vijayakumar, D. He, N. Kumar, and J. Ma. 2019, Nov. Blockchain-based mutual-healing group key distribution scheme in unmanned aerial vehicles ad-hoc network. IEEE Transactions on Vehicular Technology 68(11):11309–22. doi: 10.1109/TVT.2019.2943118.
- Lu, X., L. Xiao, T. Xu, Y. Zhao, Y. Tang, and W. Zhuang. 2020, March. Reinforcement learning based phy authentication for VANETs. IEEE Transactions on Vehicular Technology 69(3):3068–79. doi: 10.1109/TVT.2020.2967026.
- Maalej, Y., S. Sorour, A. Abdel-Rahim, and M. Guizani. 2018.Vanets meet autonomous vehicles: Multimodal surrounding recognition using manifold alignment. IEEE Access 6: 29026–40. doi: 10.1109/ACCESS.2018.2839561
- Mendel, J. M., R. Chimatapu, and H. Hagras. Comparing the performance potentials of singleton and Non-singleton type-1 and interval type-2 fuzzy systems in terms of sculpting the state space. IEEE Transactions on Fuzzy Systems 28(4):April. 2020 783–94. doi:10.1109/TFUZZ.2019.2916103.
- Najib, R. A., and S. Moh. 2020.Routing protocols for unmanned aerial vehicle-aided vehicular ad hoc networks: A survey. IEEE Access 8: 77535–60. doi: 10.1109/ACCESS.2020.2989790
- Nie, L., Y. Wu, H. Wang, and Y. Li. 2019.Anomaly detection based on spatio-temporal and sparse features of network traffic in VANETs. IEEE Access 7: 177954–64. doi: 10.1109/ACCESS.2019.2958068
- Shah, Y. A., H. A. Habib, F. Aadil, M. F. Khan, M. Maqsood, and T. Nawaz. 2018.CAMONET: Moth-flame optimization (MFO) based clustering algorithm for VANETs. IEEE Access 6: 48611–24. doi: 10.1109/ACCESS.2018.2868118
- Shu, J., L. Zhou, W. Zhang, X. Du, and M. Guizani. 2021, July. Collaborative intrusion detection for VANETs: A deep learning-based distributed SDN approach. IEEE Transactions on Intelligent Transportation Systems 22(7):4519–30. doi: 10.1109/TITS.2020.3027390.
- Tang, Y., N. Cheng, W. Wu, M. Wang, Y. Dai, and X. Shen. 2019, April. Delay-minimization routing for heterogeneous VANETs with machine learning based mobility prediction. IEEE Transactions on Vehicular Technology 68(4):3967–79. doi: 10.1109/TVT.2019.2899627.
- Wu, C., X. Chen, Y. Ji, F. Liu, S. Ohzahata, T. Yoshinaga, and T. Kato. 2015.Packet size-aware broadcasting in VANETs with fuzzy logic and RL-based parameter adaptation. IEEE Access 3: 2481–91. doi: 10.1109/ACCESS.2015.2502949
- Yang, Y., Z. Gao, Y. Ma, B. Cao, and D. He. 2020, Aug. Machine learning enabling analog beam selection for concurrent transmissions in millimeter-wave v2v communications. IEEE Transactions on Vehicular Technologyy 69(8):9185–89. doi: 10.1109/TVT.2020.3001340.
- Zhou, H., H. Wang, X. Chen, X. Li, and S. Xu. 2018.Data offloading techniques through vehicular ad hoc networks: A survey. IEEE Access 6: 65250–59. doi: 10.1109/ACCESS.2018.2878552