ABSTRACT
With the increase in the number of employees working remotely from home following the COVID-19 pandemic, cyberattacks have grown in quantity and strength. While companies invest tremendous resources in technical defense practices and protection tools, the main weak link is still the human factor. The current study aims to provide theoretical and empirical evidence of the antecedents that contribute to active cyber defense as well as cyber risk behaviors. Based on a sample of 338 employees who worked from home or on-site during and after COVID-19, we examined the effects of organizational training on employee defense behaviors. The results of the current study suggest that the workplace and the amount of confidence in the defense measures play an important role in contributing to cyber risk behavior. Therefore, it is crucial that managers raise employee awareness of the hazards and educate them on the different defense methods that they can apply.
Introduction
In the post COVID-19 era, there has been a fundamental change in the working practices. Companies worldwide now allow their employees to work from home (WFH) at least part-time during the week.Citation1 This change in the workplace not only requires organizations to adjust strategically, but it also amplifies the hazards derived from cyberattacks to organizational computerized assets. This is because the countermeasures devices used to mitigate cyber risks at the employees’ home networks are in most cases considered less effective than those that exist in the firms’ premises. Moreover, the weakness of cybersecurity systems escalated during the COVID-19 pandemic, when organizations had to face an increase in cyberthreats—such as the exploitation of software and system vulnerabilities, an increase in the number and variety types of cyberattacks, the lack of access control systems, and leaks in customers’ data that infringed their privacy—along with many other threat.Citation2 Economically, cyber damages were valued at $6 trillion during the pandemic and are estimated to reach $10.5 trillion by 2025.Citation3
To protect the firm from cyberattacks, organizations need to increase employee awareness of cyberthreats and invest in advanced protection and detection tools (Intrusion Prevention & Detection Tools). However, a predominant weakness in cybersecurity systems, both regarding operational technology (i.e., “OT”) and information technology (i.e., “IT”), results from employee cyber risk behaviors that are not aligned with the firm’s cyber policies and guidelines. Such employees considered to be the weakest link in the chain.Citation4 Unfortunately, expecting from and relying on the workforce to comply and behave according to the firm’s guidelines and policies, even when employees have acquired a certain amount of cyber awareness through cybersecurity training, is not trivial. Oftentimes, employees are either not aware of the guidelines, have minor knowledge of the cyber defense tools, or (from the opposite perspective) have too much confidence or trust in the ability of external forces, including governments, to defend companies from malicious attacks.Citation5
During the COVID-19 era, issues concerning cyber risk behaviors escalated because companies had less control over the company’s devices and their use while employees worked from home.Citation6 Pandharipande and ParasharCitation7 argued that during the pandemic, in addition to the increased adoption of technology that resulted in new cyber risks, there was an observed rise in the likelihood and severity of cyberthreats as individuals failed to prioritize cybersecurity practices while organizations increasingly relied on digital technology. The authors also mentioned that insufficient cyber-security measures to handle cyberthreats in employees’ homes made the latter more vulnerable to attacks.
While previous studies highlighted the issues of cyber risk behaviors, cybersecurity awareness, or cybersecurity knowledge about the readiness to engage in cyber defense behaviors,Citation5,Citation6,Citation8 our understanding of the impact of organizational training on employees’ awareness and their cybersecurity knowledge and behaviors is still insufficient. This lacuna has led to a call for more studies that explore the cognitive side of employees’ intentions to protect their company from cyberattacks.Citation9 In addition, the relationship between organizational training and employee behaviors must adjust to the new working practices, mainly WFH, which reduce employers’ control over the employees’ cyber risk and defense behaviors. Hence, the current study aims to answer the following questions: What are the factors that influence cyber defense behaviors among employees? And are those behaviors affected by the current workplace (i.e. WFH or the organization’s premises)?
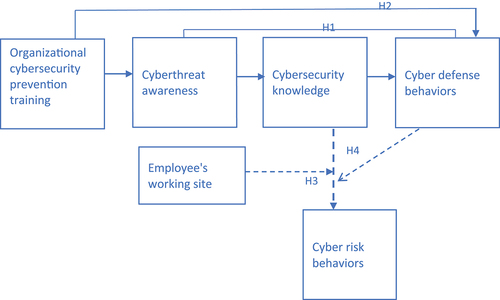
We based our research on the Theory of Planned Behavior (TPB)Citation10 and Protection Motivation Theory (PMT),Citation11 and their impact on cybersecurity behaviors.Citation8,Citation12–14 Following the results of our study, we suggest that organizational cybersecurity training increases employee cyberthreat awareness, which leads to additional cybersecurity knowledge and to the implementation of cyber defense behaviors. On the other hand, cyber defense behaviors and the workplace (i.e., the employee’s home or the company’s premises) moderate the relationship between cybersecurity knowledge and cyber risk behaviors. This is seen in the case of employees who worked from home and implemented fewer defense procedures, and also among those who worked on-site in highly defense-oriented companies and expressed higher cyber risk behaviors. We suggest that the study’s’ findings may derive from either insufficient knowledge or, in the latter group, from too much confidence in the organization’s defensive cybersecurity abilities.
The paper is organized as follows: Section Two presents the conceptual background and the model’s hypotheses. Section Three details the research methodology. In Section Four we report the research hypotheses’ analyses and the results. Lastly, Section Five presents the research’s theoretical and practical contributions as well as its limitations and recommendations for future research.
Theoretical background
Cyberthreat awareness, cybersecurity knowledge, and cyber defense behaviors
The tremendous cost of cyberattack damages to an organizations’ assets is often associated with an insufficient organizational cybersecurity infrastructure that is used to counter many and different cyberthreats. However, the literature and cyber log analysis show that in the majority of instances, it is the human element that constitutes the primary contributor to cyber breaches.Citation15 This issue escalated throughout the COVID-19 pandemic, when employees worked remotely with less control over their cyber behavior and added vulnerability to increases in cyberattacks. During this period, organizations obtained cybersecurity mainly through the use of cybertechnological solutions (e.g., firewalls, antivirus software), while employers paid less attention to their employees’ behaviors.Citation15 Since the human factor is often considered the weakest link in defending the organization’s assets from security attacks, scholars have tried to decipher the antecedents of cybersecurity behaviors, often known as “security hygiene”.Citation12 In doing so, they leaned mostly on both the Theory of Planned Behavior (TPB)Citation10,Citation16 and the Protection Motivation Theory (PMT).Citation11,Citation17,Citation18
TPB was developed by Ajzen,Citation10,Citation16 who posits that individual behaviors result from intentions to behave that are influenced by the attitude regarding the likelihood that this behavior will have the expected result, in addition to a subject examination of the expected risks and benefits from that action. PMT, which was developed by Rogers,Citation17 focuses on threat-coping mechanisms, and posits that individuals decide how to respond to a threat based on the assessment of the latter’s severity, the probability of its actual occurrence, and the efficacy of the protective response.
In the context of compliance with cybersecurity policies, TPB suggests that employees will be more akin to apply security defense behaviors if they have a positive attitude about the cybersecurity process and its contribution to defending the firm from undesirable results. However, positive attitudes can only occur if the employees are aware of the problems concealed in cyberattacks.Citation17,Citation19 Herath and RaoCitation20 have indicated that awareness of the cost of cyberthreats to the company impacts employees’ concerns regarding security breaches, which ultimately can lead to higher compliance with the organization’s cyber defense behaviors. Thus, in order to motivate employees to engage in additional cyber defense behaviors, organizations should raise the former’s awareness of cyberthreats, which has been found to prevent significant attacks and damage to business operations.Citation19
Based on PMT, we can assume that workers that have more awareness of cyberthreats will make an effort to acquire knowledge regarding how to secure their devices, which will multiply their cyber defense behaviors. Although only a few studies explore whether awareness impacts employees’ cybersecurity knowledge, Zwilling et al.Citation8 found that increased cyber awareness does contribute to acquiring additional knowledge regarding cybersecurity, which in turn leads to further defense behaviors. Likewise, in an extensive systematic literature review, Corallo et al.Citation19 demonstrated that cybersecurity and information security awareness raise the employees’ level of knowledge regarding possible security threats, system vulnerabilities, and security risks. This knowledge benefits companies by encouraging employees to identify cyberattacks, reduce or prevent cyber risks behaviors, improve employees reaction to cyberattacks, and ultimately increase the security and stability of the cyber systems.Citation19,Citation21,Citation22 Hence, our first hypothesis is as follows:
H1:
Cyberthreat awareness is positively related to cyber defense behaviors via the mediation of cybersecurity knowledge.
Organizational training for cybersecurity and cyber defense behaviors
According to PMT theory, employees will protect themselves from cybersecurity hazards when they consider that there is a threat and also estimate that they have sufficient skills to cope with the potential risk. However, often they lack adequate awareness or knowledge concerning how to defend themselves from cyberattacks. In his 2018 study, HadlingtonCitation23 showed that more than half of the responders reported that they did not know how to defend their company from cyberattacks, and 55% admitted lacking the necessary abilities to comply with this responsibility. Thus, in order to protect their company, organizations are obligated to provide training programs to educated employees based on the company’s cyber behaviors guidelines and policies.Citation24–26 He et al.Citation25 demonstrated how cyber-security training methods raised employee awareness of susceptibility, severity, and security intentions, which led to more constructive cyber defense behaviors. Likewise, AlshaikhCitation27 found that raising awareness by training employees on the company’s cyber defense guidelines, as part of a security culture, contributed to an increase in employee reports of cyber incidents (e.g., phishing e-mails). On the other hand, the lack of cyber defense training was found to be a factor that explains the negative relationship between training programs and employees’ risky cyber behaviors.Citation24
Training employees to comply with cyber guidelines is essential because these raise cybersecurity awareness and contribute to cyber defense behaviors.Citation28 Employees that are more aware of their companies’ cybersecurity regulations show higher concern about security breaches, higher responsibility to protect their personal information, and higher competence to manage cybersecurity tasks, compared to employees that have no organizational cybersecurity training or are not aware of the company’s cybersecurity regulations. In addition, employees that are more aware of the organizational cybersecurity guidelines also report having additional knowledge about how to protect their computerized devices.Citation29 Accordingly, in the current study, we suggest that training will contribute to the readiness to activate more defense methods since they raise employee awareness of cyber hazards, which contributes to cybersecurity knowledge. Hence, our second hypothesis:
H2:
The relationship between organizational cybersecurity training and employee cyber defense behaviors is mediated serially by cyberthreat awareness and cybersecurity knowledge.
Cyber risk behaviors and workplace site
Implementation of cyber defense systems is crucial in order to reduce the cost of cyberattacks. However, this can only be achieved if employees avoid engaging in cyber risk behaviors. As such, it is crucial to understand what are the antecedents of employee risk behaviors. Cyber risk behaviors are a pressing concern in today’s digital age as they pose significant threats to individuals, organizations, and societies at large.Citation30 Examples include clicking on suspicious links, using weak passwords, or failing to update software regularly. These behaviors are often driven by a lack of awareness and knowledge regarding cyberthreats and best practices for protecting digital assets.Citation8 In spite of the ubiquitous nature of the phenomenon, less is known about cyber risk behaviors among workers working remotely from home.
During the COVID-19 pandemic, companies had to readjust to the new governmental demands that affected working habits and increased the numbers of employees that were allowed to work remotely, mostly from home. Since only few studies have examined the impact of WFH on cyber risk behaviors.Citation31,Citation32 It is important to examine if the place of work (home vs. organizational premises) influences the cyber risk behaviors, and what are the factors that intervene in this relationship. As shown by Tessian’s 2020 report,Citation32 more than 50% of IT leaders admit that they can get away with riskier behavior when working remotely, a finding that might explain why 84% of those same leaders state that data loss prevention is more difficult when employees work remotely
WFH increases cyber vulnerability due to several reasons. First, organizations have less control over their employees’ cyber risk behaviors, especially since some of those employees use their personal devices at home, and the firm has only minor control over said usage (e.g., which app they download, installation of antivirus software, etc.). For example, Tessian’s reportCitation32 showed that according to 48% of the employees, main reason for not following safe data was that they were not being supervised by IT managers. In addition, Goel et al.Citation6 found that employees admitted using their IT work devices for personal use as well as sending e-mails and watching news online. Moreover, more than half admitted that they enabled their computerized work devices to be used by their family and friends, which increased the potential for risky behaviors and cyberattacks.
Second, the sudden changes caused by the pandemic led to the distribution of cybersecurity training programs. This means that employees may have suffered from a lack of cybersecurity knowledge and insufficient understanding concerning how to defend the company’s devices.Citation31 Previous studies suggested that cyber risk behaviors result from an inadequate understanding of potential threats or of effective protective measures.Citation33 Employees without adequate cybersecurity knowledge may underestimate the risks associated with their online activities, leading them to make decisions that compromise their digital security.Citation34 To overcome this obstacle, organizations spend efforts to increase their employees’ cybersecurity knowledge through different training programs.Citation35 Hence, we expect to see a reduction in risk behaviors among employees who gain additional cybersecurity knowledge. The question is whether employees working from home show the same pattern of reduction in risk behaviors as do employees who continue to work within the organization’s premises and may have a higher exposure to cybersecurity knowledge.
Few studies have dealt in the cybersecurity knowledge of WFH workers.Citation31 Therefore, we can only assume that on-site employees have a better chance to participate in organizational cybersecurity training programs. Studies on part-time workers have shown that in comparison to full-time employees, they perceive their organization’s vulnerability to cyberattacks to be lower.Citation36 Scholars have suggested that part-time employees receive less, if any, training in cybersecurity, and are not aware of the organization’s security guidelines or procedures. Since these programs aim to raise employee cybersecurity knowledge.Citation26 We expect employees who continue to work at the organization’s premises to show less risky behaviors, compared to WFH employees, regardless of their amount of cybersecurity knowledge. On the other hand, since WFH employees are less monitored by their company, will be more affected by their level of cybersecurity knowledge, even compare to employees that work from the organization’s premises. Hence, our third hypothesis:
H3:
The workplace (home vs. the organization’s premises) moderates the relationship between cybersecurity knowledge and risk behaviors.
Working from home also means that any malicious attack exact a price from the employees’ personal devices that they use in their homes. According to PMT,Citation18 employees are more likely to behave securely based on their evaluation of the costs of cyber protection behaviors.Citation12 This means that employees working from home are more likely to protect their devices, since the personal price for cybersecurity misbehaviors is high. On the other hand, Employees working on site transfer the cost of their loss to the firm; as such, they have a lower motivation to protect their devices from cyberattacks. Moreover, employees who use the organization’s facilities may be more confident that the company has embedded in them additional means of defense to protect itself from malicious attacks, a fact that can increase the number of cyber risk behaviors due to the belief that the company can protect itself. In their study, Zwilling et al.Citation8 found that individuals who relied on their country to protect them from cyberattacks exhibited additional cyber risk behaviors compared to individuals who relied on their own behaviors. While Zwilling et al.Citation8 observed the difference at the country level, we argue that the same pattern can be seen at the micro level. That is, employees who work at their company’s premises and believe that the firm has implemented cyber defense measures and means to protect them from cyberattacks, engage in greater quantities of cyber risk behaviors compared to employees who also work on-site but assume that the company employs less cyber defense means. On the other hand, when working at home, on their personal computer, workers are more concerned about not engaging in cyber risk behaviors. But this is only true if they have enough cybersecurity knowledge and know-how to defend their equipment. Employees who do not have the means to defend their devices also engage in more risky behaviors.
Since cyber defense behaviors are influenced by cyberthreat awareness via the mediation or cybersecurity knowledge, as demonstrated in former studies,Citation19 our last hypothesis suggests that knowledge will also influence cyber risk behaviors, by moderating the relationship between cyber defense behaviors and working site. And that the relationship between working site and cyber risk behavior will be moderated by the cyber defense behaviors being performed either at home (by the employee) or on-site. Hence, our last hypothesis is the following:
H4:
Cyberthreat awareness is related to risk behaviors via the mediation of cybersecurity knowledge, and is moderated by cyber defense and cyber risk behaviors.
The total model and the hypotheses are present in
Methodology
Sample and data collection procedures
The study employed an anonymous online questionnaire created through Google Forms™. It distributed to a selected group of recruited Israeli respondents and was conducted by i-panel™, one of the largest and most prominent panel and survey management companies in Israel. The company has access to a broad sample of employees in various occupations and fulfilling a variety of work roles. Prior to the distribution of the questionnaire, we instructed i-panel managers to sort employees based on the following criteria: all of them were above 21 years of age and had worked full-time within their current organization for at least a year. Following the research pre-criteria, the company sampled the subjects using convenience sampling methods. The Institutional Ethics Review Board approved the study protocol.
A total of 350 Israeli individuals responded to the survey. We filtered out the participants who did not complete the survey (n = 12). Thus, the final sample included N = 338 employees from different organizations who were working at least part-time from home during the COVID-19 pandemic (n = 261) or at the company’s premises (n = 77). Since the sample size was unequal, we measured homogeneity using Levene’s Test for Equality of Variances.Citation37 The results confirmed that the differences in the group were not significant throughout all of the variances, hence these did not affect the robustness of the equal variance assumption.
The final study sample demographics were as follows: Mage = 43.45 years (SD = 11.59), 60.7% were women, 22.2% had either a degree or worked in computer science or related subjects (e.g., programing, computer engineering, QA), and 84.6% worked in an organization under the supervision of the Israeli cyber regulations authority.
Measurements
Unless otherwise specified, a 5-point Likert scale was used to score responses using a range from (1) Strongly disagree to (5) Strongly agree.
Cyberthreat awareness was measured using Spremić and Šimunic’sCitation38 constructs with some adaptations. We asked the participants to rate their level of awareness of 16 cyber hazards (for example, phishing, SQL injection, Ddos, injection of viruses to computers, etc.).
Cybersecurity knowledge was based on Spremić and Šimunick’sCitation38 cyberthreat awareness questionnaire. We asked the participants to rate the level of knowledge required to protect their organization from different hazards (for example, phishing, SQL injection, Ddos, injection of viruses to computers, etc.).
Cyber risk behaviors were measured using Hadlington’sCitation23 constructs with several adaptations. We asked the participants about the behaviors they engaged in during the COVID-19 pandemic while being on the computer in which they worked, either from home or in the organization (sample items: sharing passwords with friends and colleagues, using the same password for multiple websites).
Cyber defense behaviors were developed using the constructs of Georgiadou et al.Citation15 We presented to the participants different defense methods and asked them to circle which of the different procedures they used (sample items: two-factor authentication, inscription of hard disk, or installation of antivirus software). We calculated the number of tools that each of the participants used, from 0 (None of the above) to 5 tools.
Organizational cybersecurity training for Cybersecurity was measured based on Georgiadou et al.Citation15 constructs. We first asked the participants if during the COVID-19 period they received training regards cybersecurity defense methods from their employers ((1) Yes, (0) No). The participants were asked about the type of cyber protection training they received during COVID-19 (sample item: online training program). Then we calculated the number of training programs that each of the participant received from his/her employers, from 0 (None of the above) to 4 training techniques.
Control variables. We controlled for employees’ gender, age, and computer knowledge (i.e., whether the employee had a degree in a computer-related area such as programming and computer engineering, or worked in the computer field). We also controlled for the type of organization according to the Israeli National Cyber Directorate’s definition of cyber-regulated entities.Citation39 We established the type of regulation using four questions regarding the company’s size, sector, the number of organizations to which it provides services, and the amount of damage it may incur in case of a cyberattack. If the respondents answered positively to any one of the questions, the firm was categorized as being regulated by the cyber authorities. Lastly, we established the employee’s actual place of work at the time of the COVID-19 pandemic, that is, whether he/she worked at least part-time from home. The questionnaire appears in Appendix A.
Results
We tested for common method bias (CMB) using Harman’s single-factor test,Citation40 which is the most acceptable method to test for this phenomenon. The result of the total variance explained by a single factor was less than 36%, which is below the threshold of 50%. Therefore, although we cannot rule out CMB as a contributing factor in the current study, it does not seem to be significant. Next, we measured the correlation between the research variables. presents descriptive statistics, correlations, and a reliability test among the study variables.
Table 1. Statistics and correlations among the study variables.
Research hypotheses
In order to test the study’s hypotheses and the overall study model, we framed our analysis around the mediated model suggested by hypotheses 1 and 2 and utilized the SPSS PROCESS macro (HayesCitation41; Models 4 and 6) to estimate a conditional analysis using a method described by Preacher et al.Citation42 We used information from the bootstrap sampling distribution (n = 5000) to estimate unstandardized coefficients with 95% bias-corrected confidence intervals (Cis) for the indirect effects.
We began our analysis by testing the mediation model posited by Hypothesis 1. Unless otherwise specified, we controlled for the company’s regulatory status and the employees’ age, gender, computer knowledge, and workplace during COVID-19. In the first step, as shown in , Model 1, both cyberthreat awareness (β = .52, p < .01) and gender (β = −.50, p < .01) were associated with cybersecurity knowledge, such that workers with higher awareness to potential threats and male employees reported having increased cybersecurity knowledge. In the second step (Model 2), the results demonstrated that cybersecurity knowledge (β = .32, p < .01), cyberthreat awareness (β = .19, p < .05), as well as workplace (β = .74, p < .01) and regulation (β = .64, p < .01) were associated with cyber defense behaviors. Thus, employees who used additional defense methods to protect the organization’s device were those who had higher cyberthreat awareness and cybersecurity knowledge, worked in a cyber-regulated company, and worked from home.
Table 2. Regression results for mediation and conditional indirect effects.
Combining these results, we examined the indirect effects of cyberthreat awareness on cyber defense behaviors via cybersecurity knowledge. The indirect effect was significant (indirect standardized effect = .11, SE = .02, 95% confidence interval CI [.05, .16]) and supports Hypothesis 1. Thus, higher awareness of cyberthreats led to added knowledge regarding cybersecurity methods, which contributed to the application of additional cyber defense procedures.
Next, we test the mediation model posited by Hypothesis 2, suggesting that cyberthreat awareness and cybersecurity knowledge serially mediate the positive relationship between organizational cybersecurity training and cyberdefense behaviors. , Models 3–5, presents the results of the dual meditation model. As shown in Model 3, organizational training (β = .17, p < .04), regulation (β = .27, p < .05) and workplace (β = .27, p < .05) were significantly associated with cyberthreat awareness, such that higher cyberthreat awareness showed among employees who worked in a company with more organizational cybersecurity training, in a company under cybersecurity regulatory supervision, and employees who were male. Organizational training (β = .39, p < .01), cyberthreat awareness (β = .46, p < .01) and gender (β = −.47, p < .01) were significantly associated with cybersecurity knowledge, such that cybersecurity knowledge was higher among employees who worked in companies with added cybersecurity training, had more awareness of cyberthreats, and were male. Lastly, Model 5 shows that cyber defense behavior was correlated with regulation (β = .50, p < .05), workplace (β = .70, p < .01), cyberthreat awareness (β = .17, p < .05), cybersecurity knowledge (β = .24, p < .05), and organizational cybersecurity training (β = .26, p < .07). Thus, cyber defense behaviors were more extensive among employees who worked in companies that conducted more cybersecurity training, had increased cyberthreat awareness and knowledge regarding cybersecurity defense, were employed by cyber-regulated companies, and worked from home.
Combining these results, we examined the indirect effects of organizational cybersecurity training on employee cyber defense behaviors via cyberthreat awareness and cybersecurity knowledge. The indirect effect was significant (indirect standardized effect = .01, SE = .06, 95% confidence interval CI [.00, .02]); this finding supports Hypothesis 2. That is to say, employees who worked at organizations offering a larger quantity of cybersecurity training programs showed higher awareness to cyberthreats, which led to increased knowledge about how to defend their devices from threats, and ultimately to additional cyber defense behaviors.
Employee cyber risk behaviors
Our last two hypotheses stated that cyber risk behaviors are associated with cyberthreat awareness via the mediation of cybersecurity knowledge, but are also moderated by the workplace during COVID-19 (work from home or at the company’s premises) and cyber defense behaviors. We framed our analysis around the mediated moderation model and again used the SPSS PROCESS macro (HayesCitation41; Model 18) to estimate a conditional analysis using a method described by Preacher et al.Citation42 We used information from the bootstrap sampling distribution (n = 5000) to estimate unstandardized coefficients with 95% bias-corrected confidence intervals (Cis) for the indirect effects. The results appear in .
Table 3. Regression results for mediation and conditional indirect effects.
Overall, the results indicated that the mediation-moderation model was significant (effect = .29 (.04), 95% bias-corrected confidence interval BCCI [−.21, −.02]), which supports our last hypothesis. The indirect effect of awareness on cyber risk behaviors via the mediation of cybersecurity knowledge was significant but only for employees who worked at the company’s premises during COVID-19, and applied more defense measurements (indirect effect = .29, 95% bias-corrected confidence interval BCCI [.09, .53]).
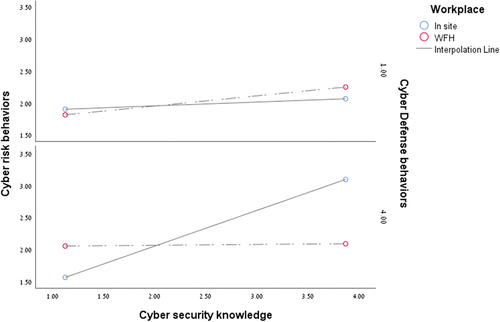
As shown in , both cyber defense behaviors (β = −.29, p < .05) and age (β = −.01, p < .01) were negatively correlated to cyber risk behaviors. Older employees who applied increased quantities of cyber defense protection methods engaged in less cyber risk behaviors. We also found that all of the interaction were significant, including the interaction between cybersecurity knowledge and workplace (β = .31, p < .10). To examine the nature of the interaction, we conducted simple slope analysesCitation43 which indicated that the effect of cybersecurity knowledge on cyber risk behaviors was positive and significant for participants who continued to work at the company’s premises during COVID-19 (t = 2.57, p < .05), but not for employees who worked from home (t = 0.96, ns), contrary to the direction of our third hypothesis (See ).
Figure 2. Results of the interaction between cybersecurity knowledge and cyber risk behaviors with the moderation of workplace ((1) home, (0), company’s premises).
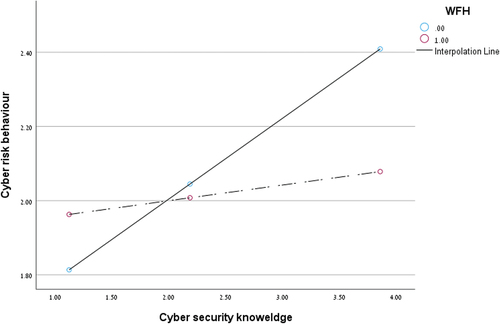
With that, the triple interaction between cybersecurity knowledge, employee workplace during COVID-19, and the amount of defense methods on cyber risk behaviors was significant (β = −.21, p < .01). The interaction is plotted in . To examine the nature of the interaction, we conducted simple slope analysesCitation43 which indicated that the positive effect of cybersecurity knowledge on cyber risk behaviors was apparent for participants who continued to work at the company’s premises during COVID-19 and installed additional cyber defense methods (t = 3.89, p < .01), and for participants who worked from home and installed few defense measurements (t = .15, p < .05). The direction of the relationship indicated that in both cases, these employees engaged in numerous cyber risk behaviors compared to the other groups.
Discussion
The present study aimed to provide theoretical and empirical evidence on the antecedents of the organization’s defense against from cyberattacks, either by installing more defense measures or by reducing cyber risk behaviors, especially when employees work remotely from home. We found that employees who worked in companies that invested in cybersecurity training programs exhibited additional cyber defense behaviors. This result confirms those of the few studies that explored the relationship between training and cyber hygiene behaviors,Citation44 and is consistent with TPB.Citation10 TPB suggests that the individual’s attitude is the motivation for engaging in specific behaviors; therefore, by raising awareness to the need for security, companies should be able to make employees change their behaviors and install more defense measures. In addition, PMTCitation11 suggests that the reaction toward a potential threat depends on the evaluation of its severity. Therefore, the implementation of training programs is essential in order to raise employee awareness to the problem of cyber breaches and attacks.
In accordance with both theories, the study findings demonstrate that the relationship between training and behaviors is mediated by awareness and knowledge. That is, intensive cybersecurity training programs contribute to raise employee awareness regarding cybersecurity hazards, which in turn increases employee knowledge about cybersecurity methods; this knowledge is ultimately actualized in the activation of additional defense measures and the reduction of cyber risk behaviors. Since only few studies have looked at the cognitive aspects of employee behavior with regard to cyber risks,Citation9 our study makes an important contribution to the understanding of how to motivate employees to apply security defense behaviors. Thus, we suggest that it is not the training by itself that motivates employees to promote engagement in additional defense behaviors; rather, it is the understanding of the cost of being attacked and the added knowledge of how to prevent those attacks that motivates them to protect their devices. Further studies should continue to observe how raising knowledge contributes to the enhancement of employee self-efficacy in cyber defense issues.
Lastly, we found that while cybersecurity knowledge is negatively correlated to cyber risk behaviors, this relationship is also moderated by other factors, specifically the workplace and the amount of confidence in defense mechanisms. Employees showed more risky behaviors when they worked remotely from home and applied minor means of defense, or when they worked at the company’s premises and had an extensive cybersecurity system at their disposal. While both types of employees showed higher cyber risk behaviors, the motivation for this tendency may be different for each group.
According to PMT, when employees consider the cost of the threat to be high, their incentive to tackle the problem rises. However, to attack the hazard they need to have both a relevant understanding and abilities to cope with the threats. When employees work from home, the company has less control over their behaviors or the devices they use.Citation31 Thus, perhaps WFH employees who are unaware of cyberthreats do not feel the need to acquire cybersecurity knowledge, since they do not understand the full impact of being attacked. Hence, they will apply less defense methods, and in addition will engage in larger quantities of cyber risk behaviors compared to WFH employees who have already implemented more defense measures to protect themselves from cyberattacks. This explanation may also be supported by the 2021 study by Pranggono and Arabo,Citation45 who noted that the pandemic caused an increase in anxiety among employees, which resulted in greater numbers of cyberattacks and less expected behaviors by the employees themselves. On the other hand, their study also highlights the importance of cybersecurity awareness and behaviors among employees, especially while working from home.
Contrary to WFH employees, those who continued to work on-site acted differently. We found that employees who worked at the company’s premises and implemented more security measures showed higher cyber risk behaviors. This group also felt a mediation effect between awareness, knowledge, and risk behaviors. Higher awareness led to increased cybersecurity knowledge, which should have led to a reduction in cyber risk behaviors. Unfortunately, these groups behaved completely in the opposite way. One explanation is that these groups have strong confidence in their organization’s ability to protect them from cyberattacks. As scholars have previously suggested, employees who work at the company’s premises often believe that it is the latter’s responsibility to protect their devices, which leads them to engage in further cyber risk behaviors.Citation23 Additionally, the cost of cyberattacks is direct and higher for employees who work from home, and more ambiguous for those working on-site. Thus, employees may be more willing to take higher risks if they are not directly affected by the damage caused by cyberattacks. As such, employees who work at the company’s premises and have both awareness and knowledge may feel either less responsible or overconfident in the company’s cybersecurity systems, which leads to a stronger tendency toward taking additional cyber risks.
Managerial implications
Since cyberattacks exact a high price from the company, managers often wonder how to change employee behaviors, especially when those employees work remotely. Leaning on TPB,Citation8,Citation10 researchers suggest that behaviors can only be altered if the employees have a positive attitude and genuine desire to react. Thus, it is crucial that managers raise the employees’ awareness of the hazards concealed in the latter’s cyber risks behaviors and train them on the different defense methods that they can apply to protect themselves as well as the organization’s devices.Citation35
The contribution of cyber defense training is even more crucial in the post-COVID era, when employees continue working remotely from home and managers have less possibilities of supervising their cybersecurity behaviors while using the company’s devices. Borkovich and SkoviraCitation31 found that employees who worked from home during the pandemic admitted that they engaged in additional cyber risk behaviors, based on the assumption that they could get away more easily with riskier behaviors while working remotely. Cybersecurity training for employees working from home is crucial to ensure the protection of sensitive information and maintain a secure work environment. However, developing robust training programs that increase cybersecurity awareness and knowledge is not trivial.Citation35 Employees need to be educated about the specific cybersecurity risks associated with working from home. This includes understanding the potential vulnerabilities of home networks, the use of personal devices, and the risks associated with public Wi-Fi networks. Employees should be educated on methods to secure network and device setups, including patching devices regularly, implementing strong passwords, enabling two-factor authentication, and securing home routers with strong encryption and passwords. In addition, employees should be trained to recognize and avoid phishing attempts, which often increase when people work remotely. Training should cover how to identify suspicious e-mails, links, attachments, and requests for sensitive information. Employees should also be cautious about sharing personal or work-related information on social media platforms. Furthermore, employees should be informed about regulation and procedures enacted by the organization for cybersecurity protection purposes, and also about the ways to report and who to report to in case of suspicious activity.
In addition, since WFH is becoming more common, IT managers must think about adjusting their training methods to the new labor trends and worksites. Today, a variety of teaching and training methods has become available, including physical and virtual procedures such as text-based instruction, video-based instruction, video training, online gaming, and more recently, AI-based cybersecurity awareness training programs.Citation35,Citation46–48 For example, one of the most popular tools to increase phishing awareness is IronScalesTM. This software allows organizations to carry out simulated phishing campaigns, which include sending fake phishing e-mails to employees as a means of assessing their vulnerability to such attacks. Employees exposed to lifelike phishing scenarios within a controlled setting gain heightened awareness of the strategies and methodologies employed by malicious actors in the cyber realm. By using this tool, organizations manage to increase the awareness of employees to various types of phishing threats.
Limitation and future research
This study has several limitations, which can be used as a starting point for future research. First, the present study regards the different types of cyber risk behaviors, as well as the various defense methods, as one single coherent construct. There are, however, some cyber risk behaviors that may be more common, while others may be less evident to nonexpert employees. Hence, employees may be more aware of specific cyber risk behaviors or cyber defense methods, and at the same time neglect others that may require more professional knowledge. Future studies need to defragment the types of hazards and defenses in order to observe whether employees behave differently when confronted with more common threats or adopt more common defensive actions. Understanding the relationship between familiarity and behaviors can contribute to more effective training programs.
Second, the study does not take into account how well cyber defense behaviors and awareness are enforced by the company or the employee’s manager. Enforcement efforts may vary between companies, which can be classified on a continuum ranging from low-risk companies with no enforcement policies, to companies that must comply with the ISO 27,001 or NIST 800–53 standards and are regulated by stronger restrictions. In future studies, a comparison and distinction between these two categories of firms may contribute to the elaboration and interpretation of the current research model.
Third, our study uncovered psychological and social motivators for risky behavior, such as peer pressure or counterproductive work behaviors,Citation49 which were found also in previous studies.Citation50 Future studies in this domain should ask whether some motives are stronger than others and how to develop effective strategies for cybersecurity compliance among employees. The study by Mwagwabi and JiowCitation50 also who showed that personal norms are a stronger predictor than fear of security threats among young people when making decisions about protecting their devices. This differs from the attitudes and behaviors of adults toward cybersecurity compliance. Thus, an interesting implication of the study refers to the importance of educating and training employees to engage in the expected behavior, especially if their confidence on the firm’s protection tools is strong.
Lastly, one of our study’s main limitations refers to the cultural impact on employee behaviors. In the current study we observed Israeli employees. However, former studies.,Citation5,Citation8 emphasized cultural differences in awareness, knowledge, and cyber behaviors between countries. In fact,Citation8 found that although Israel is considered to be highly cyber-oriented compared to other European countries (specifically, Slovenia, Poland, and Turkey), the Israeli participants demonstrated the highest levels of risk behavior compared to all other participants. The scholars suggested that since Israel invests heavily on defense measures, including cyber defense operations, individuals feel more confident to rely on their cyber protection systems, and therefore they do not hesitate to engage in additional cyber risk behaviors. Cultural differences may also be related to different cultural values.Citation51 Some countries have been found to be high on uncertainty avoidance (UAI) values; thus, employees in these countries may be more averse to unexpected circumstances and attempt to avoid them by applying more protection measures. In contrast, employees in countries with a greater degree of openness to unexpected concerns may exhibit increased cyber risk behaviors. In light of these differences, future studies should take cultural aspects into account when implementing behavioral approaches to cybersecurity.
Conclusion
The COVID-19 pandemic altered our daily routines and created disruptions which lead to added vulnerabilities. While many companies have introduced more sophisticated security defense systems to protect themselves from cyberattacks, at the end of the day, they are still dependent on the human willingness to implement those defense procedures and behave in accordance with them. Since the costs of cyberattacks are high—and are expected to rise in future years—companies must invest in training and educating employees on cybersecurity issues and keeping them up-to-date in this field. This process should adjust to the new working styles as the pandemic changed many of the past working assumptions. Companies that do not adopt the needed adjustments may find that the cost of protecting themselves from cyber hazards is higher than expected.
Disclosure statement
No potential conflict of interest was reported by the author(s).
Additional information
Funding
References
- Delegach M, Klein G, Katz-Navon T. Furlough and its effects on employees after returning to work: the roles of psychological contract breach and violation, and perceived organizational support. J Manage Organ. 2022;1–18. doi:10.1017/jmo.2022.71.
- Kumar R, Sharma S, Vachhani C, Yadav N. What changed in the cyber-security after COVID-19? Comput Secur. 2022;120:102821. doi:10.1016/j.cose.2022.102821.
- Wolinsky J. The importance of protecting work from anywhere employees against cyber-attacks. Ceoworld Magazine. [accessed 2022 Sep 13]. https://ceoworld.biz/2022/09/13/the-importance-of-protecting-work-from-anywhere-employees-against-cyber-attacks/.
- Crossler RE, Johnston AC, Lowry PB, Hu Q, Warkentin M, Baskerville R. Future directions for behavioral information security research. Comput Secur. 2013;32:90–101. doi:10.1016/j.cose.2012.09.010.
- Klein G, Zwilling M, Lesjak D. A comparative study in israel and slovenia regarding the awareness, knowledge, and behavior regarding cyber security. In: Khosrow-Pour M, editor. Research anthology on business aspects of cybersecurity. Hershey (PA): IGI Global; 2022. p. 424–39.
- Goel L, Zhang JZ, Williamson S. IT assimilation: construct, measurement, and implications in cybersecurity. Enterp Inf Syst-Uk. 2022;17(7):1–30. doi:10.1080/17517575.2022.2052187.
- Pandharipande A, Parashar R. Repercussions of coronavirus on cyber-security threats. Biosci Biotech Res Comm. 2020;13(14):45–48. doi:10.21786/bbrc/13.14/11.
- Zwilling M, Klien G, Lesjak D, Wiechetek Ł, Cetin F, Basim HN. Cyber security awareness, knowledge and behavior: a comparative study. J Comput Info Syst. 2022;62(1):82–97. doi:10.1080/08874417.2020.1712269.
- Ifinedo P. Effects of security knowledge, self-control, and countermeasures on cybersecurity behaviors. J Comput Inf Syst. 2023;63(2):380–96. doi:10.1080/08874417.2022.2065553.
- Ajzen I. from intentions to actions: a theory of planned behavior. In: Kuhl J Beckmann J, editors. Action control. SSSP: springer series in social psychology. Berlin, Heidelberg: Springer Berlin Heidelberg; 1985. p. 11–39. doi:10.1007/978-3-642-69746-3_2.
- Rogers RW. A protection motivation theory of fear appeals and attitude change1. J Psychol. 1975;91(1):93–114. doi:10.1080/00223980.1975.9915803.
- Blythe JM, Coventry L, Little L. Unpacking security policy compliance: the motivators and barriers of employees’ security behaviors. In Eleventh Symposium On Usable Privacy and Security; July 22–24, 2015, Ottawa, Canada. 2015. p. 103–22.
- Gillam AR, Foster WT. Factors affecting risky cybersecurity behaviors by US workers: an exploratory study. Comput Human Behav. 2020;108:106319. doi:10.1016/j.chb.2020.106319.
- Maalem Lahcen RA, Caulkins B, Mohapatra R, Kumar M. Review and insight on the behavioral aspects of cybersecurity. Cybersecurity. 2020;3(1):1–18. doi:10.1186/s42400-020-00050-w.
- Georgiadou A, Mouzakitis S, Askounis D. Working from home during COVID-19 crisis: a cyber security culture assessment survey. Secur J. 2022;35(2):486–505. doi:10.1057/s41284-021-00286-2.
- Ajzen I. The theory of planned behavior: frequently asked questions. Human Behav Emerging Technol. 2020;2(4):314–24. doi:10.1002/hbe2.195.
- Rogers RW. Cognitive and physiological processes in fear-based attitude change: a revised theory of fear appeals and attitude change. Social psychophysiology: a sourcebook. New York (NY): Guilford; 1983. p. 153–76.
- Floyd DL, Prentice‐Dunn S, Rogers RW. A meta‐analysis of research on protection motivation theory. J Appl Soc Psychol. 2000;30(2):407–29. doi:10.1111/j.1559-1816.2000.tb02323.x.
- Corallo A, Lazoi M, Lezzi M, Luperto A. Cybersecurity awareness in the context of the industrial internet of things: a systematic literature review. Comput Ind. 2022;137:103614. doi:10.1016/j.compind.2022.103614.
- Herath T, Rao HR. Protection motivation and deterrence: a framework for security policy compliance in organizations. Eur J Inf Syst. 2009;18(2):106–25. doi:10.1057/ejis.2009.6.
- Aldawood H, Skinner G. Analysis and findings of social engineering industry experts explorative interviews: perspectives on measures, tools, and solutions. IEEE Access. 2020;8:67321–9. doi:10.1109/ACCESS.2020.2983280.
- Li L, He W, Xu L, Ash I, Anwar M, Yuan X. Investigating the impact of cybersecurity policy awareness on employees’ cybersecurity behavior. Int J Inf Manage. 2019;45:13–24. doi:10.1016/j.ijinfomgt.2018.10.017.
- Hadlington LJ. Employees attitudes toward cyber security and risky online behaviors: an empirical assessment in the United Kingdom. Int J Cyber Criminol. 2018;12(1):262–74. doi:10.5281/zenodo.495776.
- Daengsi T, Pornpongtechavanich P, Wuttidittachotti P. Cybersecurity awareness enhancement: a study of the effects of age and gender of Thai employees associated with phishing attacks. Educ Inf Technol. 2021;27(4):4729–52. doi:10.1007/s10639-021-10806-7.
- He W, Ash I, Anwar M, Li L, Yuan X, Xu L, Tian X. Improving employees’ intellectual capacity for cybersecurity through evidence-based malware training. JIC. 2020;21(2):203–13. doi:10.1108/JIC-05-2019-0112.
- Zhang Z, He W, Li W, Abdous MH. Cybersecurity awareness training programs: a cost–benefit analysis framework. Ind Manage Data Syst. 2021;121(3):613–36. doi:10.1108/IMDS-08-2020-0462.
- Alshaikh M. Developing cybersecurity culture to influence employee behavior: a practice perspective. Comput Secur. 2020;98:1–10. doi:10.1016/j.cose.2020.102003.
- Simonet J, Teufel S. The influence of organizational, social and personal factors on cybersecurity awareness and behavior of home computer users. ICT Systems Security and Privacy Protection: 34th IFIP TC 11 International Conference, SEC 2019, Lisbon 2019; June 25-27; Portugal: Proceedings. Springer International Publishing, 2019. p. 194–208.
- Li L, He W, Xu L, Ivan A, Anwar M, Yuan X. Does explicit information security policy affect employees’ cyber security behavior? A pilot study. Enterprise systems conference: IEEE 2014 Aug 2; Shanghai, China. p. 169–73.
- Chowdhury NH, Adam MT, Teubner T. Time pressure in human cybersecurity behavior: theoretical framework and countermeasures. Comput Secur. 2020;97:101931. doi:10.1016/j.cose.2020.101931.
- Borkovich DJ, Skovira RJ. Working from home: cybersecurity in the age of COVID-19. Issues Info Syst. 2020;21:234–46.
- Sadler T. State of data loss prevention; 2020. Tessian Report. https://www.tessian.com/resources/#report/.
- Albrechtsen E, Hovden J, Stølen K. Investigating employees’ information security behavior: a literature review. Comput Secur. 2018;76:144–59.
- Kim S, Kim D, Jang D, Lee C. The relationship between cybersecurity knowledge and information security behavior: an empirical investigation among South Korean employees. Inf Manage. 2020;57:103250.
- He W, Zhang Z. Enterprise cybersecurity training and awareness programs: recommendations for success. J Organ Comput Electron Commerce. 2019;29(4):249–57. doi:10.1080/10919392.2019.1611528.
- Anwar M, He W, Ash I, Yuan X, Li L, Xu L. Gender difference and employees’ cybersecurity behaviors. Comput Human Behav. 2017;69:437–43. doi:10.1016/j.chb.2016.12.040.
- Levene H. Robust tests for equality of variances. Contrib Probab Stat. 1960;278–92.
- Spremić M, Šimunic A. Cyber security challenges in digital economy. In: Proceedings of the World Congress on Engineering. Vol. 1. Hong Kong, China: International Association of Engineers; July 2018. p.341–46.
- Housen-Couriel D. National cyber security organisation, Israel. Washington (DC): NATO Cooperative Cyber Defence Centre of Excellence; 2017.
- Podsakoff PM, MacKenzie SB, Lee JY, Podsakoff NP. Common method biases in behavioral research: a critical review of the literature and recommended remedies. J Appl Psychol. 2003;88(5):879–903. doi:10.1037/0021-9010.88.5.879.
- Hayes AF. Introduction to mediation, moderation, and conditional process analysis: methodology in the social sciences. Kindle ed. New York (USA); 2013. p. 193.
- Preacher KJ, Rucker DD, Hayes AF. Addressing moderated mediation hypotheses: theory, methods, and prescriptions. Multivariate Behav Res. 2007;42(1):185–227. doi:10.1080/00273170701341316.
- Aiken LS, West SG. Multiple regression: testing and interpreting interactions. Thousand Oaks, California: Sage Publications; 1991.
- McCrohan KF, Engel K, Harvey JW. Influence of awareness and training on cyber security. J Internet Commerce. 2010;9(1):23–41. doi:10.1080/15332861.2010.487415.
- Pranggono B, Arabo A. COVID‐19 pandemic cybersecurity issues. Internet Technol Letters. 2021;4(2):1–6. doi:10.1002/itl2.247.
- Ansari MF. A quantitative study of risk scores and the effectiveness of AI-based cybersecurity awareness training programs. IJSSAN. 2022;3(3):1–8. doi:10.47893/IJSSAN.2022.1212.
- González-Manzano L, de Fuentes JM. Design recommendations for online cybersecurity courses. Comput Secur. 2019;80:238–56. doi:10.1016/j.cose.2018.09.009.
- Willems C, Meinel C. Online assessment for hands-on cyber security training in a virtual lab. Proceedings of the 2012 IEEE Global Engineering Education Conference (EDUCON); IEEE; 2012 Apr 17. 2012. p. 1–10.
- Hadlington L, Binder J, Stanulewicz N. Exploring role of moral disengagement and counterproductive work behaviours in information security awareness. Comput Human Behav. 2021;114:106557. doi:10.1016/j.chb.2020.106557.
- Mwagwabi F, Jiow JH. Compliance with security guidelines in teenagers. AJIS. 2021;25:1–25. doi:https://doi.org/10.3127/ajis.v25i0.2953.
- Hofstede G. Dimensionalizing cultures: the Hofstede model in context. Online Readings Psychol Culture. 2011;2(1):2307–919. doi:10.9707/2307-0919.1014.
Appendix A.
Questionnaire (without demographic information)
Organizational regulation type: Please circle the answer that characterizes the organization in which you work (Yes/No).
Does the organization have over 200 employees?
Does the organization provide service to more than 1,000 organizations?
Will a cyberattack or cyber sabotage incident affecting the organization cause damage of more than NIS 5 million?
Does your organization belong to the IT sector (hi-tech, information transfer, finance, etc.)?
Cyberthreat awareness (Spremić & Šimunic, 2018; Zwilling et al., 2022)
The following table presents a number of cyberthreats to the organization. To what extent are you aware of the existence of the following threats (1- Not at all; 5- To a very great extent)?
Prevention of access to existing organizational information
Loss of organizational information
Damage to the organization’s computer equipment
Spying on other organizations
Hostile takeover of computers and communication equipment
Blockage of business processes in the organization
Takeover of critical IT infrastructures (e.g., hospital, power plants, trains)
Use of IT technologies to carry out terrorist attacks
Knowledge of personal details about you
Introducing viruses/harmful elements to computers
Use of organizational insiders (e.g., employees) to carry out cyberattacks
Theft of someone else’s identity
Social engineering
DdoS
Phishing
SQL injection.
Cybersecurity knowledge (Spremić& Šimunick, 2018): To what extent do you have the necessary knowledge to protect the organization’s assets in the following cases (1- Not at all; 5- To a very great extent)? The indicators are identical to those presented in Question 2.
Cyber risk behavior: How often do you engage in the specific behaviors listed below while being on the computer that you use to work at home? (It can also be your personal computer during and after the COVID-19 pandemic (Hadlington, 2018).
Sharing passwords with friends and colleagues
Using or creating passwords that are not very complicated (e.g., surname and date of birth).
Using the same password for multiple websites
Using online storage systems to exchange and keep personal or sensitive information
Entering payment information on websites that have no clear security information/certification
Using free-to-access public Wi-Fi
Relying on a trusted friend or colleague to advise you on aspects of online-security
Downloading free antivirus software from an unknown source.
Disabling the antivirus on your work computer so that you can download information from websites
Bringing in your own USB to work in order to transfer data onto it
Checking that software for your smartphone/tablet/laptop/PC is up-to-date.
Downloading digital media (music, films, games) from unlicensed sources
Sharing your current location on social media
Accepting friend requests on social media because you recognize the photo
Clicking on links contained in unsolicited e-mails from an unknown source
Sending personal information to strangers over the Internet
Clicking on links contained in an e-mail from a trusted friend or work colleague
Checking for updates to any antivirus software you have installed
Downloading data and material from websites on your work computer without checking its authenticity
Storing company information on your personal electronic device (e.g., smartphone/tablet/laptop).
Cyber defense behaviors (Georgiadou, Mouzakitis, & Askounis, 2022): Which of the following apply to the devices you currently use for your working-from-home employment? (You may select more than one answer.)
Password protection
Two-factor authentication
Automatic screen lock
Antivirus software installed
Antispam software installed
None of the above.
Organizational cybersecurity training (Georgiadou, Mouzakitis, & Askounis, 2022):
During the COVID-19 pandemic, did you receive training concerning cybersecurity defense methods from your employers? (Yes/ No)
What was the type of training received during the COVID-19 pandemic? (You may select more than one answer.)
Online training program
User manual documentation (distributed in any way)
Instructions available on the corporate portal or website
Instructions provided via email
None of the above.
Working from home or at the office (Georgiadou, Mouzakitis, & Askounis, 2022):
7.1 Prior to the COVID-19 crisis, were you able to work from home? (Yes/ No)
7.2 (New question) Did you work from home during the COVID-19 pandemic, or are you working part of the days from home now? (Yes/ No)