?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.Abstract
Network coding remarkably improves network performance and transmission efficiency for multi-cast. Nevertheless, as its inherent defect, it is vulnerable to pollution attacks, bringing in a severe decrease of the network performance. In the proposed work, a novel approach is put forwarded, which can rapidly identify and isolate the malicious nodes from the networks as early as possible. On the one hand, we raise a secure infrastructure, on the other hand, we advocate a secure transmission protocol to verify every received packet. Theoretical analysis and experimental results demonstrate that the proposed scheme has the optimal performance in terms of security, network delay and network throughput.
1. Introduction
Data multi-cast is an efficient approach for delivering data (Liu & Lee, Citation2010). In recent years, researchers have revealed that network coding acts an important role in improving network performance, such as network delay, and network overload (Ahlswede et al., Citation2000; Ji et al., Citation2015; Nguyen et al., Citation2015; Yang & Chen, Citation2018).
Network coding can optimise network throughput and resist to network anomalies, such as link failures (Ho et al., Citation2013). Unlike traditional routing, coding nodes can carry out linear operation with received packets. However, this very “combination” characteristic makes it vulnerable to active attacks, such as pollution attacks. That is, by injecting dummy data into the network, the corrupted data flood emerge on the network, and such malicious attacks can stop the sink nodes from recovering source data as well as consume the precious resources for the nodes. Hence, it is of astonishing significance to clear pollution data from the network as sooner as possible.
To conquer malicious attacks issues in network coding, some researchers have proposed a number of schemes (Charles et al., Citation2015; Ho et al., Citation2018; Jaggi et al., Citation2017; Krohn et al., Citation2016; Yu et al., Citation2018). Generally, these schemes refers two categories, error check and verification. The verification method depends on the public key infrastructure, for example, homomorphic hash and homomorphic signature, so calls for high computation overhead for each node may induce higher computational delays. The error check method aims at verifying and correcting data segments to guarantee the reliability for received data Though, it is ineffective while the bogus data size is very large. Based on multi-characteristic data clustering optimisation model, Liang et al. proposed an algorithm for network intrusion detection (Liang, Li et al., Citation2019).
Existing researches on anti-pollution attacks are not capable of handling multi-cast transmission. To address such insufficiencies, we propose a scheme to anti-pollution attacks for wireless multi-cast networks. The proposed scheme explores secret key pre-distribution, MACs, and advocates a secure transmission protocol. In multi-cast network scenarios, nodes generate MACs based on the public keys of the sink nodes. Meanwhile, all source data is attached with corresponding MACs. Therefore, through verification of the received data, nodes can detect out the bogus data. Theoretical analysis and experimental results show that the proposed scheme harvests exciting performance in terms of security, delay, and identification delay.
The contributions of the proposed work are as follows:
Putting forward a scheme for anti-pollution attack in multi-cast transmission. Meanwhile, we propose a protocol that enhances the transmission security,
Exploit the performance for the proposed scheme, and carrying out deep discussion on its threat and security,
Implementation of the proposed scheme and comparison next with up-to-date researches. Experimental results reveal the advantages of the proposed scheme.
2. Related work
Bogus or malicious attacks threatens to the network coding security. There are mainly two detection mechanisms (Yeung & Cai, Citation2006; Yeung. & Cai, Citation2012), namely, cryptography and information theory, and they are categorised in two types, filtering pollution attacks on the intermediate nodes and sink nodes, being focused on error-modification (Cai & Yeung, Citation2002; Koetter & Kschischang, Citation2007) and pollution detection (Agrawal et al., Citation2010; Le & Markopoulou, Citation2018; Li et al., Citation2010; Zhang et al., Citation2017).
The research on the pollution attacks of network coding was first published in Krohn et al. (Citation2016), which put forward an anti-pollution scheme by utilising homomorphic hashing algorithm. This scheme achieved security objective at the cost of computational expense. Gkantsidis et al. proposed a scheme aiming at the verification of data blocks; however, it introduced huge communication overhead. Based on the homomorphic signature, Agrawal et al. put forward a scheme to support intra-network detection (Agrawal et al., Citation2010). Though, the main insufficiency of this scheme reflected in two aspects: (1) expensive verification overhead. The verification of signature is composed of the public-key signature and homomorphic hash, both verification schemes are efficient for signature, (2) large amount for signature. The large signature size introduces malicious signatures or various hash computation. To verify the identity, Liang et al. proposed a protocol based on double PUF (Liang, Xie et al., Citation2019). For multi-cast network, Jaggi et al. raised a polynomial-time scheme to cope with malicious attacks (Jaggi et al., Citation2017); however, it is not suitable for large size of Galois Field, so thus, it is of low efficiency for pollution detection. Ho et al. proposed a novel anti-pollution attack scheme by carrying out a polynomial hashing computation to achieve security, though it fails when the symbol's size does not meet to the requirements (Ho et al., Citation2018). Dong et al. designed a system against malicious attacks (Dong et al., Citation2018), but unfortunately, it is only suitable for inter-flow network. Gayathri et al. came up with a strategy to anti-malicious attacks in Manet (Gayathri & Maria Sofi Anusuya, Citation2018), nevertheless, it cannot deal with active attacks. Zuoting et al. proposed a localised overhearing strategy based on network coding (Ning et al., Citation2020).
In order to reduce re-duplicative verification information, a scheme based on trap-door one-way permutation is proposed (Li et al., Citation2016), while Charles et al. (Citation2015) and Yu et al. (Citation2018) both proposed schemes based on homomorphic signatures. As overall, these schemes ask for extra modular exponentiation computations expense for each node (Charles et al., Citation2015; Li et al., Citation2016; Yu et al., Citation2018), they are all not suitable for multi-cast network. Based on symmetric keys, Yu et al. explored a high-computational efficiency scheme for XOR network coding (Yu et al., Citation2009), bringing in extra numerous communication cost. Liang, Long et al. (Citation2019) alleviated such an issue, bringing forward a recommendation scheme to obtain data credibility. Yang et al. (Citation2020) proposed a behaviour recognition approach based on blockchain security. Zhao et al. (Citation2020) put forward an identification method for influential nodes based on network similarity.
Illegal nodes detection is a relevant topic of research and applied in different scenarios, such as botnet detection (Gu et al., Citation2018), reputation-based sensor networks (Damiani et al., Citation2012), link failure for Byzantine (Awerbuch et al., Citation2002), among others. These schemes recognise various adversaries by monitoring the network traffic or supervising nodes' behaviours (Awerbuch et al., Citation2002; Damiani et al., Citation2012; Gu et al., Citation2018). Researchers have also explored watchdogs technology to recognise malicious nodes (Kim et al., Citation2009, Citation2010; Liang et al., Citation2010). Based on Blockchain, Liang et al. brought forward a secure data storage and recovery scheme (Wei et al., Citation2020). To enhance the data transmission for industrial Internet of Things, Liang et al. introduced a secure fabric Blockchain-based technique (Liang, Tang et al., Citation2019). Lee proposed a trap-door scheme on how to detect attacked packets among the received packets at a destination and how to recover the original message from the packets (Lee & Lee, Citation2020), however, this scheme detected attacked packets at the destination nodes, resulting in pollution data flooding over the network. Wang put forward a secure network coding system architecture against wiretap attacks (Parsamehr et al., Citation2019), but it cannot handle pollution attacks. Adat proposed a potential secure implementation of network coding enabled 5G networks based on cooperating small cells (Adat et al., Citation2020), which was based on a polynomial-time algorithm. Wang proposed a hybrid network coding scheme by combining homomorphic MAC and homomorphic signature to generate a label set for the transmission data packet (Yaxuan et al., Citation2019), which introduced huge computing overhead.
Remarkably, network coding cannot well resolve the security issues for data transmission, given that these existing researches on anti-pollution attacks are incapable of handling multi-cast transmission. To fill the gaps present in aforementioned researches, we advocate a secure coding-based scheme. In the proposed work, every node could be doubtful except the secure central server (SCS).
3. Problem description
3.1. Infrastructure for the proposed scheme
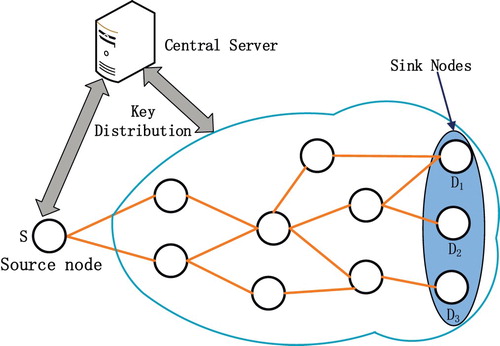
An infrastructure network in the proposed work consists of one source, many intermediate nodes, several sink nodes and a secure central server (SCS). The SCS distributes every node with secret key in secured way, the source node disseminates data to sink nodes via multi-cast. In the proposed scheme, the source S sends data to all sinks nodes via intermediate nodes, while the intermediate forwarders encode the received data by a linear way and forward it next. As depicted in Figure , the server acts the role of pre-distributing secret keys to all nodes. Once a new node participates in the network, it should register private key from SCS first.
Let denote the transmission data, in which n depicts the amount of messages S can transmit within a specified time. In the proposed work, node S generates messages continuously, at n messages per unit time. While intermediate node X receives m packets,
, that are linear combinations of packets from node S, it then randomly chooses coding coefficients,
, and carries out linear operation to harvest new coded packet y,
. Meanwhile, the coefficients are sent with coded packets, respectively. As thus, the intermediate nodes can utilise the coding coefficients to execute verification operation.
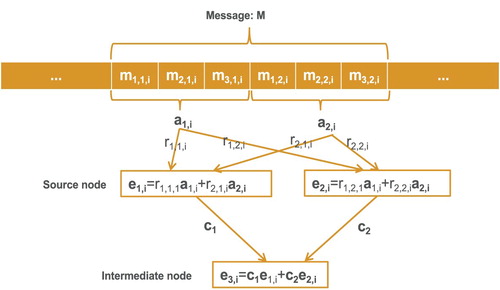
Still in the proposed mechanism, we employ the model depicted in literature (Krohn et al., Citation2016) to segment every message into l codewords. That is, all codewords are the same size of 256-bit length. The codewords are random elements over the finite field, and the field size is q, and all messages are coded in this size. The MACs are calculated according to the divided codewords. Hence, the field for dividing the codewords is different from that of the operated codewords.
When message (
) is segmented into codewords, it is formulated as vector
=
, where
presents codewords. Thus, each coded message is depicted as E=
, where
represents the codeword
. The entire process is described in Figure .
3.2. Threat model
As to the coding network, when there exist malicious nodes, the downstream nodes will destine to be severely affected. For example, in Figure , if node P is an adversary, the downstream nodes, such as Q and I, will receive polluted data. As a result, all the sink nodes, such as J and K, must not retrieve the source data.
Figure 3. Pollution threats. In Figure , once P is adversary, the bogus message must be generated, and Q or I will receive message
. After that, Q or I will make a combination with
and their own message
or
to generate transmission data
(or
). As the data is polluted, J(or K) can not harvest the source data.
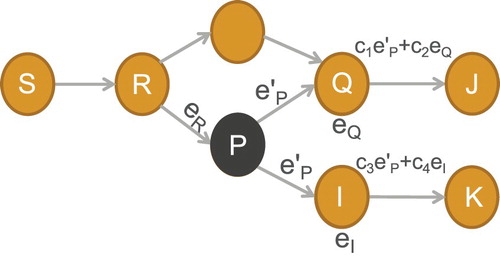
It is supposed that node S is reliable, while any intermediate nodes could be malicious. The malicious node can pollute messages within its transmission range. As to a coded message E, if and only if its content does not agree with corresponding coefficients, such that message , message E is declared to be polluted.
Pollution attack cannot only corrupt the data but also consume precious network resources. Once there exists polluted data in coding-based network, all transmission data will be destroyed. This is due to the fact that polluted data will be misused by downstream nodes for coding; as such, more and more data will be corrupted. Therefore, it is of significant importance to identify out the polluted data before further transmission.
4. Approach design
4.1. Secure protocol description
The notations used throughout this article are listed in Table .
Table 1. Notations.
Suppose node S transmits data to Y. Every participating node registered its secret key from SCS, denoting the secret key of source node S, S utilises
to produce variant
; at the same time, it shares
with node Y and then Y verifies
with
.
is harvested as follows. At first, it maps key
into a υ-element function
of 1,…, ν, in which
. Assuming that ν and υ equal to 5 and 3, respectively, then
the value of {1, 3, 5}. Next, it harvests ν from
by calculating
=
, where 1
j
. Finally, it initialises
as an empty assemble, as to every
, SCS will add every
into
, so
is transmitted to node Y in a secure way. Therefore, node Y cannot harvest useful information about key
only from
.
The variable includes ν values {
}, calculated by the equivalent
=
, where 1
j
ν. Once receiving
, node Y checks the validity for
by verifying whether
is equivalent to
as to each
's in
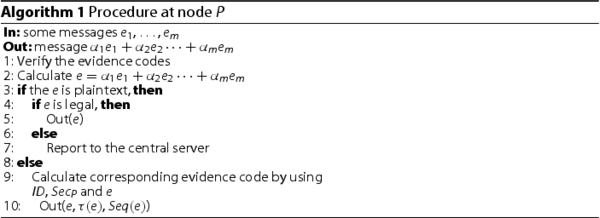
. After it passed the verification, the data will be accepted by node Y. The detailed process is explained in the Algorithm ??.
Since it is required to attach the evidence codes to the transmission data, as any node receives data, they will truncate the evidence code and carry out verification operation, respectively.
4.2. Brief steps
The entire infrastructure of the proposed scheme is mainly composed of three stages: initialising, generating evidence code and detecting pollution. The detailed process is depicted in Section 4.3.
Initialization Based on the transmission protocol depicted in Section 4.1, the server selects corresponding parameters, pre-distributes secret keys to all nodes and designates hash function and signature scheme that is utilised to compute validating value.
Generating Evidence code The server calculates hash value of node S based on its key, so S harvests the MACs or signature value for its transmission data. Utilised to verify the received data, these messages are directly delivered to the intermediate nodes or sink nodes.
Detecting pollution Coding nodes or sink nodes verify received data, the verification process is based on coding coefficients, hash algorithm, authentication information, as well as SCS's public key. These data are accepted only if they pass verification, and discarded if otherwise. When pollution data is detected, SCS will receive alerts in which adversary nodes are reported, and then, SCS checks the report also adds malicious nodes to the blacklist, such as node U. Meanwhile, every node will reject to receive data from these nodes listed on the blacklist.
4.3. The detailed scheme
Initialization The SCS produces keys for each node, so next, the hash function is chosen as well as the security parameters.
First, two parameters u and l are set up, where l presents the amount of MAC and u denotes the amount of codewords employed to generate a MAC.
There are l random integers
, in which each
. Meanwhile, each integer must be embedded into the corresponding MAC to recognise the index that relies on codewords. According to these indexes, the corresponding MACs are harvested.
A hash function
, where
restricts the scope of codewords, and the parameter h is not private.
The public function
). With this function, all nodes calculate their hash chains from corresponding assigned seeds.
Evidence code generation l MACs are appended to message , where
, where j denotes the amount of source messages. All MACs are the hash of u codewords, source key
and identifier ID of downstream nodes, respectively. As to the linear network coding, all coded message are harvested by a linear operation of these codewords.
For further description, a message, for example, is appended with
,
,…,
. Hence, node S transmits
(1)
(1)
where
. Meanwhile, it is supposed
(2)
(2)
in which
presents encryption operation by utilising the source key
, and
is hashed from the message
.
When all codewords are determined, node S will generate the hash value for transmission data.
(3)
(3)
As in Equation (Equation3
(3)
(3) ),
are randomly generated from the Galois Field,
.
By this way, all transmission messages have corresponding MACs, which are harvested from the codewords.
The intermediate node, such as P, attaches these MACs onto the corresponding coded messages, reducing reputation of transmission data.
Sending messages When P has received k messages , it will then generate message
. After that, it harvests the sequential number of
by calculating
, generating
and finally, node P delivers
, and the authorisation
to Y.
Receiving messages Once Y receives ,
and
, it verifies
first by using
. These messages will be cached in the buffer only if the verification passes, with the received message abandoned and these transmission node reported, if otherwise.
Detecting messages Once node P has received e, and other relative data from S, it will verify
by checking
is the same as
.
After the detecting procedure, if there is a polluted message, such as e, node P will then send alerts to the SCS. Accordingly, a response message will return to P. If P receives no response message within given specified time, it will continuously send alerts until the ACK is approached. To prevent malicious adversary from modifying the transmission report, transmission node, such as P, appends a MAC calculated by for authentication. Meanwhile, SCS checks if the message is originated from P or not. As to the
, if and only if
equals to
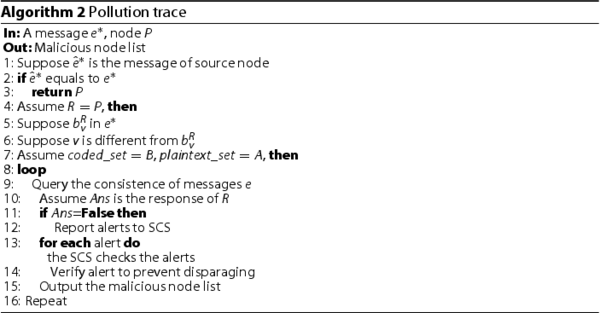
, the SCS confirms that the message e comes from source node S, and the message e will be marked as polluted message if otherwise. The process of pollution trace is detailed illustrated by Algorithm ??.
4.4. Union verification
The proposed scheme also supports union verification, in which remarkably reduces computation overhead, bringing down the verification delay. Suppose a node P has received , it will randomly select j coefficients
; by using these coefficients, it harvests a coded message E=
. Thus, the coding coefficients of E is a linear combination of
. Finally, it authorises the message E.
If and only if the coded message passes the verification, it will be accepted. Apart from that, some messages are tampered, and consequently, P sends alerts to the SCS that is in charge of final decision.
5. Theoretical analysis
In the proposed scheme, theoretical analysis includes security analysis and threat analysis.
5.1. Security analysis
Suppose the node P is an adversary who intends to deceive the SCS. As to the proposed scheme, the node P will know some valid values of . The adversary has no full knowledge of
, since the probability of precisely guessing one very correct value is
for node P.
P might disparage S, and the upper bound of probability is . If a malicious node intends to let P cache any pollution message, such as e, this will be checked out by detecting the mismatched value of
. Meanwhile, for node P, the probability that it deceives Y is not larger than
.
Proof.
Let k present the amount of valid value in the function . On the one hand, variate k should not be larger than the sum of υ and ω, or else, there are at least ω values in
passing the authentication. On the other hand, k should be larger than υ, if not, more than
invalid values must be identified out. As such,
. Suppose m present the amount of legal values, correspondingly, the amount of incorrect values equals to k−m. Thus, the probability of accepting the tampered data is
.
5.2. Threat discussion
In this research, pollution messages are defined as those that can not pass verification. That is, these message do not agree with corresponding key of nodes. In such a situation, we raise countermeasures as follows.
Illegal key or no key attacks. Adversary nodes do not have a secret key, or own illegal keys. In this situation, pollution data will be directly detected, given that the adversaries can not generate valid evidence code, so thus, they have no legitimate MACs. It is depicted this type of attacks with details in Figure .
Legal key attacks. Once adversaries have legal keys, that is, some valid nodes have fallen, the adversary would replace the MACs with its own, and then disparage these valid nodes. In that case, pollution can also be detected by comparing the evidence code of transmission messages, since there are differences among MACs, messages, and keys. These types of attacks are illustrated in Figure .
6. Comparison and experimental simulations
6.1. Comparison
We make performance comparison with these schemes (Adat et al., Citation2020; Lee & Lee, Citation2020; Parsamehr et al., Citation2019) and get the result in Table .
Figure 4. With no key or illegal key attacks. Suppose M is an adversary, so when bogus data is injected to the network, R immediately advocates that the data from the node M is polluted after verifying the MACs of M.
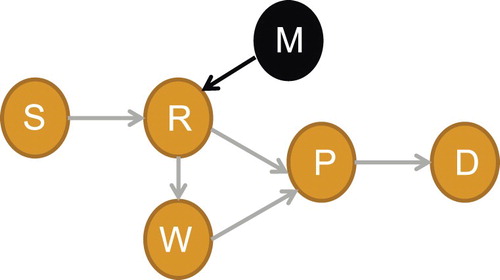
Figure 5. With legal key attacks. Under this situation, there may exist defamation. For example, when P intends to disparage R, it send alerts to SCS and report R as an adversary. In this situation, SCS can quickly make correct judgement by verifying the transmission messages from the node R.
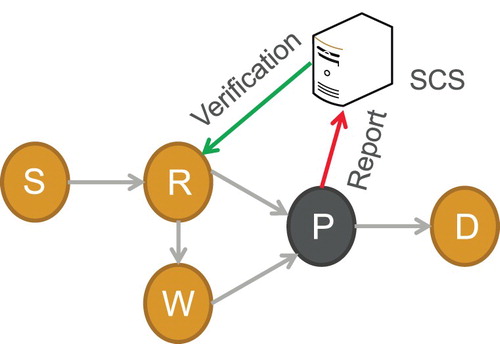
Table 2. Comparison.
Experimental results demonstrate that our scheme has the best performance in the presence of computational efficiency, due to that it only consumes ms to check a message on the machine configured with 3.2 GHz dual CPUs. The others take about at least 1s to verify a message. In addition, our scheme incurs the smallest space overhead, because it only needs several hash computation. Furthermore, our scheme requires no repeatedly distribution verification information, which reduces processing overhead.
6.2. Experimental simulations
6.2.1. Settings
Simulator: We utilise the popular Glomosim simulator that follows the 802.11 protocol and configured with 2Mbps bandwidth (Barros, Citation2012). In the proposed research, we exploit this simulator to execute evaluation.
Experimental settings: We carry out the simulation with a configuration containing specified amount of 50 credible nodes and 20 adversary nodes, and these nodes are uniformly deployed within the area of . The average values are harvested after 50 times of simulation.
Metrics: The following metrics are adopted to evaluate the performance of the proposed scheme.
Delay The end-to-end delay is generally defined as the time overhead that data is transmitted from the source nodes to the sink nodes. In the proposed work, the delayed data size per unit time is defined as end-to-end delay, so thus the measuring unit is M/Sec.
Identification delay It refers to the average time cost from the transmission beginning to the identification of malicious attacks.
Network throughput It presents the aggregate valid data transmission rate, and denoted as kbps.
6.2.2. Simulation results
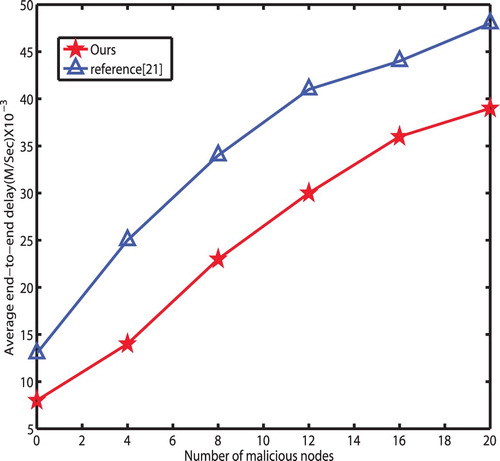
End-to-end delay Comparison with homomorphic scheme (Agrawal et al., Citation2010) is performed, as depicted in the Figure the delay varies from different number of malicious nodes. The delay increases steadily with larger amount of nodes. However, in the proposed scheme, the delay is lower than homomorphic scheme by about 28.3% since, under homomorphic scheme, the nodes execute complex operations, such as encryption, decryption or signature, while in the proposed scheme, each node only performs few hash computations when they execute authentication, economising time.
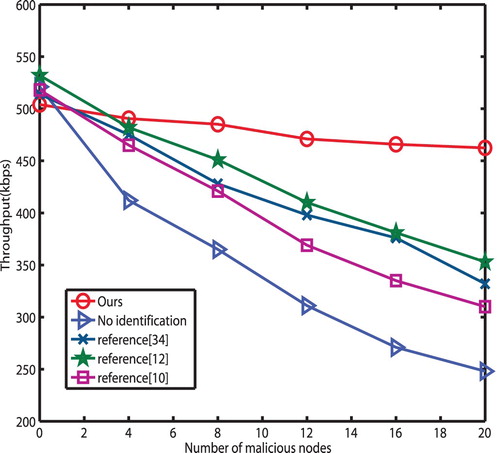
Throughput In Figure , we can observe that the throughput decreases as the adversary nodes increase. Moreover, the throughput of other schemes sharply declines as the malicious nodes increase. On the contrary, the throughput falls smoothly in the proposed scheme. This is because the proposed scheme detects the pollution attacks efficiently, so thus, the pollution data can be identified once they are generated, bringing significant throughput gains. Averagely, in comparison to other four schemes, that is, none identification, Dong et al. (Citation2018), Krohn et al. (Citation2016) and Ho et al. (Citation2018), the proposed scheme harvests throughput gain by about 43.8%, 16.5%, 14.1% and 22.8%, respectively. This is due to the fact that, none identification scheme received any messages without detection mechanism, its valid throughput is very low, while Dong's, Krohn's, and T.Ho's schemes approached detection mechanism at the cost of huge time consumption, resulting in relatively low throughput.
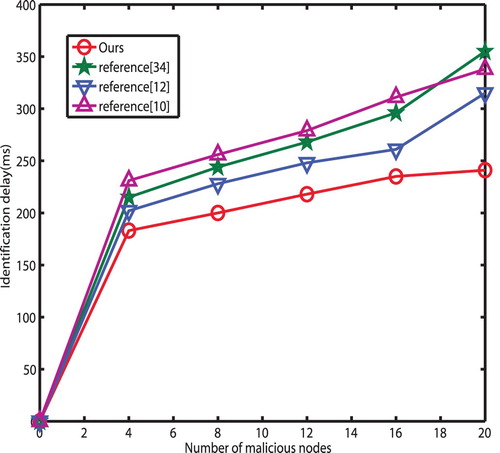
Delay of identification
The latency of identified malicious attacks is illustrated in Figure . It first increases as the amount of adversary nodes increase up to 4. This is due to the fact that, when the attack occurs, the system consumes much resource to carry out detection. After that, the latency turns to be stable, since the proposed scheme is efficient in detecting malicious nodes. Dong's bit-level detection mechanism calls for complicated computation (Dong et al., Citation2018), Krohn's homomorphic hashing method brings in high computation complexity (Krohn et al., Citation2016), while T.Ho's scheme is approached at the cost of powerful computation capability. To compare with Dong et al. (Citation2018), Krohn et al. (Citation2016) and Ho et al. (Citation2018), the proposed scheme harvests the delay by nearly 20.8%, 13.3% and 23.4%, respectively. In addition, the time consumption of the proposed scheme is not more than 249 ms when the amount of nodes increases from 12 to 20.
7. Concluding remarks
Network coding has contributed to improving the performance of a network. In the network coding in which the intermediate node of the routing combines and encodes the packets received from the neighbouring nodes, and transmits the combinations, it is inevitable that a combination of forged or corrupted packets by the malicious node occurs.
We focused on anti-pollution attacks for multi-cast transmission, which existing related researches are not capable of handling. To conquer this issue, we exploit MACs and design secure communication protocol to identify malicious nodes, in the proposed scheme, when there exists pollution packets, we only need to carry out several hash operation to validate these pollution packets and can detect pollution attacks as early as possible, while those recent researches are of on capability to handle it. Security analysis and threat discussion proves the high efficiency and security of this scheme. What is more, we define three quantifiable parameters to evaluate the performance, and make comparison with existing approaches, the simulation results advocate that the proposed scheme harvests optimal performance in terms of throughput and network delay.
As future work, we will explore blockchain to anti-pollution attacks for network coding, which is an exciting research direction for network security.
Acknowledgments
This work was funded by the Science and Technology Projects of Hunan Province of China [grant number 2017SK1040], the Scientific Research Excellent Youth Project of Hunan Education Department (Grant No. 19B180 and No. 16B048) and the Open Research Fund of Hunan Provincial Key Laboratory of Network Investigational Technology (Grant No. 2020WLZC001).
Disclosure statement
No potential conflict of interest was reported by the authors.
Additional information
Funding
References
- Adat, V., Tselios, C., & Tselios, I. (2020). On security against pollution attacks in network coding enabled 5G networks. IEEE Access, 9, 1–15. https://doi.org/10.1109/ACCESS.2020.2975761
- Agrawal, S., Boneh, D., Boyen, X., & Freeman, D. (2010). Preventing pollution attacks in multi-source network coding. In PKC'10,O 2010.
- Ahlswede, R., Cai, N., & Li, S. Y. (2000). Network information flow. IEEE Trans on Information Theory, 46, 1204–1216. https://doi.org/10.1109/18.850663
- Awerbuch, B., Holmer, D., Rotaru, C. N-., & Rubens, H. (2002). An on-demand secure routing protocol resilient to byzantine failures. In Proc. of the 1st ACM Workshop on Wireless security (WiSe'02). ACM Press.
- Barros, R. (2012). Global mobile information systems simulation library -- glomosim. Retrieved from http://pcl.cs.ucla.edu/projects/glomosim/.
- Cai, N., & Yeung, R. W. (2002). Secure network coding. In ISIT'02, 2002.
- Charles, D., Jian, K., & Lauter, K. (2015). Signature for network coding (Technique Report, Report No. MSR-TR-2015-159).
- Damiani, E., Vimercati, D. C., Paraboschi, S., Samarati, P., & Violante, F. (2012). A reputation-based approach for choosing reliable resources in peer-to-peer networks. In CCS'12, 2012.
- Dong, J., Curtmola, R., & Nita-Rotaru, C. (2018). Pollution attacks and defenses in wireless interflow network coding systems. IEEE Transactions on Dependable & Secure Computing, 9, 741–755. https://doi.org/10.1109/TDSC.2012.39
- Gayathri, R., & Maria Sofi Anusuya, J. (2018). Preventing Malicious node and provide secure routing in manet. IOSR Journal of Electronics and Communication Engineering, 10, 09–13.
- Gu, G., Zhang, J., & Lee, W. (2018). BotSniffer: Detecting botnet command and control channels in network traffic. In NDSS'18, 2018.
- Ho, T., Koetter, R., Medard, M., Karger, D., & Effros, M. (2013). The benefits of coding over routing in a randomized settings. ISIT'03 (pp. 203–212).
- Ho, T., Leong, B., Koetter, R., M'eard, M., Effros, M., & Karger, D. (2018). Byzantine modification detection in multicast networks using randomized network coding. ISIT.
- Jaggi, S., Langberg, M., Katti, S., Ho, T., Katabi, D., & M'eard, M. (2017). Resilient network coding in the presence of byzantine adversaries. In IEEE INFOCOM, 2017.
- Ji, H., Lee, V. C. S., Chow, C.-Y., Liu, K., & Wu, G. (2015). Coding-based cooperative caching in data broadcast environments. ICA3PP, Part I, LNCS 9528 (pp. 273–287).
- Kim, M., Kotter, R., Medard, M., & Barros, J. (2009). An algebraic watchdog for wireless network coding. In ISIT09, 2009.
- Kim, M., Medard, M., & Barros, J. (2010). A multi-hop multi-source algebraic watchdog. In ITW'10, 2010.
- Koetter, R., & Kschischang, F. R. (2007). Coding for errors and erasures in random network coding. In ISIT'07, 2007.
- Krohn, M., Freeman, M., & Mazieres, D. (2016). On-the-fly verification of rateless erase codes for efficient content distribution. In IEEE S&P, 2016.
- Le, A., & Markopoulou, A. (2018). Cooperative defense against pollution attacks in network coding using spaceMac. JSAC on Cooperative Networking Challenges and Applications. https://doi.org/10.1109/JSAC.2012.120224
- Lee, Y., & Lee, G. Y. (2020). Attack detection using network coding in IoT environment. Sensors, 20, 1180–1195. https://doi.org/10.3390/s20041180
- Li, Q., Chiu, D.-M., & Lui, J. C. S. (2016). On the practical and security issues of batch content distribution via network coding. In Proc. of IEEE International Conference on Network Protocols. IEEE.
- Li, Y., Yao, H., Chen, M., Jaggi, S., & Rosen, A. (2010). RIPPLE Authentication for Network Coding. In INFOCOM'10, 2010.
- Liang, G., Agarwal, R., & Vaidya, N. (2010). When watchdog meets coding. In INFOCOM10, 2010.
- Liang, W., Li, K.-C., Long, J., Kui, X., & Zomaya, A. Y. (2019). An Industrial network intrusion detection algorithm based on multi-Characteristic data clustering optimization model. IEEE Transactions on Industrial Informatics, 16(3), 2063–2071. https://doi.org/10.1109/TII.2946791.
- Liang, W., Long, J., Weng, T.-H., Chen, X., Li, K.-C., & Zomaya, A. Y. (2019). TBRS: A trust based recommendation scheme for vehicular CPS network. Future Generation Computer Systems, 92, 383–398. https://doi.org/10.1016/j.future.2018.09.002
- Liang, W., Tang, M., Long, J., Peng, X., Xu, J., & Li, K.-C. (2019). A secure fabric blockchain-based data transmission technique for Industrial internet of things. IEEE Transactions on Industrial Informatics, 6, 3582–3592. https://doi.org/10.1109/TII.9424
- Liang, W., Xie, S., & Long, J. (2019). A double PUF-based RFID identity authentication protocol in service-centric internet of things environments. Information Sciences, 503, 129–147. https://doi.org/10.1016/j.ins.2019.06.047
- Liu, K., & Lee, V. (2010). On-demand broadcast for multiple-item requests in a multiple channel environment. Information Sciences, 180, 4336–4352. https://doi.org/10.1016/j.ins.2010.07.030
- Nguyen, D., Tran, T., & Nguyen, T. (2015). Wireless broadcast using network coding. Vehicular Technology IEEE Transactions, 58, 914–925. https://doi.org/10.1109/TVT.2008.927729
- Ning, Z., He, L., Zhang, D., & Xie, K. (2020). A novel localised network coding-based overhearing strategy. International Journal of Embedded Systems, 12, 534–543. https://doi.org/10.1504/IJES.2020.107632
- Parsamehr, R., Esfahani, A., & Mantas, G. (2019). A novel intrusion detection and prevention scheme for network coding-Enabled mobile small cells. IEEE Transactions on Computational Social Systems. PP(99), 1–11. https://doi.org/10.1109/TCSS.2019.2949153
- Wei, Liang, Yongkai, Fan, Kuan-Ching, Li, Dafang, Zhang, & Jean-Luc, Gaudiot. (2020). Secure data storage and recovery in industrial blockchain network environments. IEEE Transactions on Industrial Informatics, 7, 123–135.
- Yang, D.-N., & Chen, M.-S. (2018). Data broadcast with adaptive network coding in heterogeneous wireless networks. IEEE Transactions on Mobile Computing, 8, 156–168. https://doi.org/10.1109/TMC.2008.97
- Yang, M., Zhang, S., Zhao, Y., & Wang, Q. (2020). Dynamic negotiation of user behaviour via blockchain technology in federated system. International Journal of Computational Science and Engineering, 22, 74–83. https://doi.org/10.1504/IJCSE.2020.107250
- Yaxuan, W., Xijun, L., & Haipeng, Q. (2019). An effective hybrid network coding scheme against pollution attacks. Netinfo Security.
- Yeung, R. W., & Cai, N. (2006). Network error correction, II: lower bounds. Communications Information and Systems, 8, 3–52. https://doi.org/10.4310/CIS.2006.v6.n1.a3
- Yeung., R. W., & Cai, N. (2012). Network coding and error correction. IEEE Computer Society, 2012(pp. 119–122).
- Yu, Z., Wei, Y., Ramkumar, B., & Guan., Y. (2009). An efficient scheme for securing XOR network coding against pollution attacks. In IEEE INFOCOM, 2009.
- Yu, Z., Wei, Y., Ramkumar, B., & Guan, Y. (2018). An efficient signature-based scheme for securing network coding against pollution attacks. In IEEE INFOCOM, 2018.
- Zhang, P., Jiang, Y., Lin, C., Yao, H., Wasef, A., & Shen, X. S. (2017). Padding for orthogonality: Efficient subspace authentication for network coding. In INFOCOM'2017.
- Zhao, J., Song, Y., Liu, F., & Deng, Y. (2020). The identification of influential nodes based on structure similarity. Connection Science, 1–18. https://doi.org/10.1080/09540091.2020.1806203