?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.ABSTRACT
The rapid development of information technology promotes the development and application of Telecare Information System (TMIS). However, TMIS also has security problems such as information leakage, false authentication, and key loss. In order to solve the safety problems of TMIS, this paper combines Physical Unclonable Function (PUF) and Elliptic Curve Cryptography (ECC) technology to propose an access control and authentication scheme suitable for TMIS. The proposed scheme uses PUF and compact PUF identity authentication models to implement secure mutual authentication between tag and server. The key information in the scheme is generated by PUF, which not only reduces the cost of algorithm design but also avoids the risk of information leakage and key loss. In addition, this article uses ECC technology to encrypt the PUF response information and random numbers, which can ensure that this data information will not be leaked to the attacker. Then through the ProVerif verification tool and security attribute analysis, it is proved that the scheme is safe in the face of major attacks. The comparative analysis results show that the proposed scheme has higher security and is more suitable for TMIS.
1. Introduction
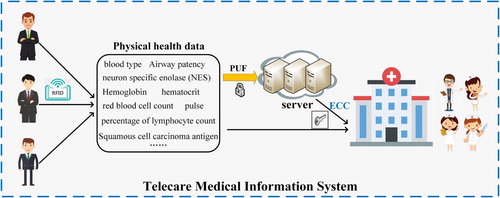
Telecare Medical Information System (TMIS) has changed the traditional medical service method, which allows patients to access the hospital's information system through the Internet, so that they can easily get doctor's telemedicine services (Kumar et al., Citation2019). As shown in Figure , the TMIS system provides patients and doctors with a more reasonable treatment plan, avoiding high medical expenses and excessive medical treatment time (Li et al., Citation2018). However, a large amount of private information is stored in the TMIS system. If this information is maliciously accessed or leaked, it will lead to incalculable consequences (Amin et al., Citation2019). The safe storage, transmission and integrity (Kui et al., Citation2020) of information are very important to the system. The failure of the data node and consequent loss of data brings a considerable loss of data information to the entire storage system (Liang et al., Citation2020). In this case, storing and extracting the value of information are critical (Liang et al., Citation2021). To protect the security of the system, TMIS can authenticate the identity of the requesting visitor through Radio Frequency IDentification (RFID).
Many secure technologies, including data transmission, data protection, or attack detection, are proposed to ensure the security of Internet of Things (IoT) (Liang et al., Citation2020). RFID (Chen et al., Citation2019) is widely used in the IoT (Liang et al., Citation2020) field and can provide security for medical information. RFID technology uses radio waves to access, receive and store the data on the tag, and use these data information to verify the identity of the tag (Mansoor et al., Citation2019). Tag, reader, and database are important parts of the RFID system. In the verification process, the tag will first send the request verification information and ID to the reader for authentication, and then the reader will extract the corresponding data from the database according to the ID information to authenticate the identity of the tag (Benssalah et al., Citation2016). At present, the proposed RFID authentication scheme is mainly to verify whether the key information stored by the tag is consistent with the key information stored by the server.
Such schemes are vulnerable to side-channel attacks (Majzoobi et al., Citation2012). An attacker can steal the information stored in the tag through a side-channel attack, and then the attacker can launch a fake attack to deceive the system's authentication. Therefore, the key information stored on the tag will not only increase the security cost of the tag, but also has poor security performance. A system with security vulnerabilities will not only leak private information, but also cause significant economic losses (Malialis et al., Citation2015).
With the increasing number of Intellectual Property (IP) cores being digitalised, it is highly required to have in place mechanisms to protect IP (Liang et al., Citation2020). Physical Unclonable Function (PUF) is a physical entity embodied in a physical structure, a hardware circuit that depends on chip characteristics and profound submicron variations during manufacturing to uniquely characterise each chip (Li et al., Citation2019; Liang et al., Citation2019). Because the hardware is easily affected by environmental noise during the manufacturing process, there are many microscopic differences between each hardware. These microscopic differences are difficult to control manually, and will affect the time delay of the signal transmission and vibration frequency in the hardware. PUF uses these microscopic differences in hardware to generate uncloned and unpredictable response information. The mapping function of PUF is similar to the hash function, which can generate unique unpredictable response information for any challenge information (Maurya & Bagchi, Citation2018). However, because PUF is less expensive to implement than hash functions, it is more suitable for implementation on lightweight devices. At present, PUF technology has been widely used in security fields such as identity authentication, IP circuit protection, key generation, copyright protection and hardware identification (Gao et al., Citation2017).
The security of user privacy information is very important for system deployment and operation (Zhang et al., Citation2020). The identity authentication process of TMIS occurs in a public channel, which is vulnerable to attackers. Attackers can disrupt the authentication process through eavesdropping, interception, and forgery method, and launch malicious attacks such as forgery attacks, replay attacks, and side-channel attacks. These attacks can lead to malicious access, data loss and intellectual property infringement (Liang et al., Citation2020).
The system can be protected from attacks by designing a secure identity authentication scheme and intrusion detection technology (Liang et al., Citation2021). To solve the security problems in the identity authentication process of TMIS, this paper proposes an access control and authentication scheme based on PUF and ECC technology. The main contributions of the paper are as follows:
The proposed authentication scheme uses PUF and ECC encryption technology to encrypt communication information, and each round of authentication information is encrypted by PUF keys or random numbers.
The scheme in this paper uses a PUF structure to generate random key information, which can solve the problem of insecure key storage and reduce the manufacturing cost of the TMIS device.
This paper uses the ProVerif tool to test the security attribute of the proposed scheme, and the experimental results show that the proposed scheme can withstand various attacks in the ProVerif environment.
Through the analysis of security characteristics, it can be found that the scheme in this paper is safe and lightweight. The proposed scheme also compares other related TMIS identity authentication schemes, and the analysis result shows that the proposed scheme has lower storage and communication costs.
The remaining content is organised as follows: Section 2 will introduce the related work of this article. Section 3 will propose the identity authentication scheme of this article. Section 4 will analyse the performance of the scheme in this paper, including ProVerif analysis, security performance analysis, and cost analysis. Section 5 will summarise and looks forward to the content of this article.
2. Related work
In view of the security problems in the TMIS system, many researchers have proposed related solutions. Siddiqui et al. (Citation2014) proposed a reliable three factor remote authentication scheme and used cloud computing technology to expand the application scenarios of TMIS, allowing users to access TMIS services through smart devices. To reduce the cost of TMIS verification, Xu et al. (Citation2014) proposed an access control and key establishment protocol based on ECC and two factors. Although the authentication cost of this scheme is low, Islam and Khan (Citation2014) proved that there are many security problems in the (Xu et al., Citation2014), for example, the password cannot be updated correctly and the replay attack cannot be resisted. Therefore, Islam et al. proposed an anonymous two-factor authentication scheme (Islam & Khan, Citation2014). In terms of security and computational cost, this protocol is superior to the solution (Xu et al., Citation2014). Xie et al. (Citation2014) proposed a three-party authentication and key agreement scheme based on ECC technology for TMIS. Amin and Biswas (Citation2015) proposed a three element-based access control protocol, which solves some security risks in TMIS, such as replay attacks and man-in-the-middle attacks. However, Wazid et al. (Citation2016) proved that the scheme (Amin & Biswas, Citation2015) cannot resist internal attacks, user simulation attacks, etc. Therefore, Wazid et al. (Citation2016) proposed an improved remote access control scheme based on three-factors. This scheme provided secure biometric identification and anonymity for the TMIS system.
In addition, Srivastava et al. (Citation2015) proposed a security authentication protocol based on synchronisation secrets, which uses a hash function and synchronisation secret value technology to protect the privacy of TMIS. But Li et al. proved that the protocol has serious security problems. The attacker can access the user's private information by stealing the server (Li et al., Citation2015). Therefore, Li et al. proposed an improved access control method in 2015 (Li et al., Citation2015). This solution adds an authentication mechanism between the database and the reader to resist server loss attacks. However, Zhou et al. (Citation2019) proved that this scheme has low security performance, which cannot resist replay attacks and asynchronous attacks, and cannot protect the anonymity of tags and readers. Therefore, Zhou et al. (Citation2019) proposed a solution based on secondary residue and timestamp, which protects the security of private data through a hash function and resists replay attacks by adding a timestamp. However, Safkhani and Vasilakos (Citation2019) proved through analysis that the method (Zhou et al., Citation2019) cannot resist asynchronous attacks, and the implementation cost of this protocol is too high, which is not conducive to the implementation of the cost-constrained TMIS system. In addition, Safkhani et al. also certified that the method of Zheng et al. (Citation2018) is vulnerable to the threat of replay attacks. Regarding the security issues of the scheme (Zheng et al., Citation2018), Safkhani et al. proposed an modified method (Safkhani & Vasilakos, Citation2019). The protocol randomises all transmitted information and verifies the timeliness of the information through timestamps. Farash et al. also proposed a lightweight access control protocol based on elliptic curve cryptography (ECC) (Farash et al., Citation2016), and proved the performance of the method through a random oracle model. But this method only provides a one-way verification function. Then, Li et al. (Citation2018) designed a secure remote access control method based on chaotic mapping, which can provide good security for the TMIS system. But the scheme (Li et al., Citation2018) cannot resist the side-channel attack. Tewari and Gupta (Citation2020) designed an efficient access control scheme for the healthcare system, which provides strong location confidentiality. However, the protocol will expose the random number information of each round of authentication in the communication channel. As the number of communications increases, this authentication mechanism may expose the protocol to the threat of replay attacks. Moreover, the protocol needs to determine the ID information of the tags before authentication. As the number of device tags increases, the implementation cost of the solution increases sharply. Subsequently, Salem and Amin (Citation2020) proposed a privacy protection protocol based on the El-Gamal cryptographic system to improve the medication security of patients in TMIS. However, the storage cost of this protocol is too high.
Suh and Devadas (Citation2007) proposed to apply PUF technology to the RFID field to solve the problem of high authentication cost. However, this protocol directly exposes PUF mapping information in public communication channels. Attackers can launch replay attacks on the system by intercepting this information. Subsequently, Majzoobi et al. (Citation2012) proposed the resilient PUF authentication protocol, which uses machine learning to establish a compact PUF structure for PUF, through which the verifier can verify the identity of the prover. In addition, the scheme adopts the substring matching authentication mechanism, which reduces the implementation cost of the system. But this scheme only realises one way authentication, and the attacker can impersonate the verifier and then steal the secret data from the prover. Akgün and Çalayan (Citation2015) implemented a scalable RFID authentication protocol using PUF. The protocol has the privacy and security protection of constant identification time, and stores the key information of the tag through PUF to resist key leakage attacks. According to different application scenarios, Gope et al. (Citation2018) designed a lightweight privacy protection access control scheme and a PUF authentication method that supports noisy environments. The first scheme is mainly used in a stable authentication environment, that is, PUF can produce stable and accurate output response. The second solution is mainly used in unstable environments, that is, PUF cannot guarantee the correct output response. However, these two schemes need to store a large number of temporary identities of tags, which increases the cost of the system and has low scalability. Gao et al. (Citation2016) designed a parameter-based authentication protocol. The protocol uses server assisted computing to reduce the hardware complexity of the device and maintain high security. Xu et al. (Citation2018) proposed a PUF-based lightweight RFID security protocol to achieve effective verification of a single tag. Bendavid et al. proved that Xu et al. (Citation2018) is vulnerable to desynchronisation attacks and secret disclosure attacks (Bendavid et al., Citation2018). Therefore, Bendavid et al. (Citation2018) designed a method to improve the scheme of Xu et al. (Citation2018) by revising the form of the message to avoid malicious attacks. Liang et al. (Citation2020) designed a PUF-based lightweight access control protocol, which uses the unclonability of PUF to generate unique key information for authentication. However, the protocol will expose the identity information of the tag, which is vulnerable to tracking attacks.
3. A lightweight identity authentication scheme
3.1. Predefined phase
PUF is an emerging hardware-based encryption technology that can generate unique response information according to different challenge information (Rostami et al., Citation2014). Because PUF's response information has unpredictable characteristics, PUF is often used as a unique identifier for a device. PUF's challenge-response information depends on the random differences of its own structure, and different differences will produce completely different behaviours. Although the attacker cannot physically clone the PUF by controlling the random differences in the hardware during the manufacturing process, many current studies have shown that machine learning technology (Jiang et al., Citation2020), Majzoobi et al. (Citation2012) can train the compact PUF structure of the PUF through legal means.
Strong PUF is a kind of PUF, which is widely used in the field of information security due to its strong challenge-response pair. The typical strong PUF structure is the arbiter PUF. The arbiter PUF controls the transmission path of the two signals in the device through the challenge information C, and then judges the output value according to the transfer speed of the signal. Since the signal delay parameter in the arbiter PUF is obtained by a combination of linear addition and subtraction, the arbiter PUF belongs to a linear PUF structure. The mapping process of the arbiter PUF can be predicted by the following model (Lim et al., Citation2005):
(1)
(1) where
is related to the following challenge information,
(2)
(2) According to Formula (Equation1
(1)
(1) ), if the result is greater than zero, the output is “1”; otherwise, the output is “0”. (Equation1
(1)
(1) ) can be rewritten as (Majzoobi et al., Citation2012):
(3)
(3) Among them,
is the delay parameter vector, and
is the transformed challenge vector. In
, r is the response bit, and Sign is the sign function. Compact PUF obtained by the above model and machine learning method has the same challenge response behaviour as PUF, and can achieve the purpose of identity recognition by establishing a compact PUF-PUF verification model. This paper will design a lightweight identity authentication scheme suitable for the TMIS system through the compact PUF-PUF verification model. The symbols required in the scheme are shown in Table .
Table 1. Symbols description.
ECC is an encryption algorithm with high security and high processing speed. The application of ECC is mainly based on two recognised thorny problems (Li et al., Citation2020):
Suppose P is the n-th order additive cyclic group of an elliptic curve (EC) over a finite field, and G is a generator of P.
• Diffie-Hellman problem: It is difficult to calculate abG in polynomial time when aG and bG are known.
• Discrete logarithm problem: Given , Q = kG, where k is an integer less than n. When G and Q are known, it is difficult to calculate k in polynomial time.
3.2. Proposed scheme
The scheme proposed in this paper uses PUF, ECC, and RFID technologies to implement a lightweight security authentication scheme suitable for TMIS. In order to describe the implementation process of the scheme more clearly, this article uses PUFM to represent the compact PUF structure in the authentication process and uses the server to represent the RFID reader and database. The authentication process in this article is mainly divided into three stages: the registration stage, the server verification label stage, and the tag verification server stage.
3.2.1. Registration phase
This phase is carried out in a secret and secure environment, in which the attacker cannot intercept the communication data information. In the identity authentication scheme proposed in this article, the registry assigns a unique information to each tag structure. A legal institution integrates a PUF circuit structure in each tag, and saves the PUFM in the server.
In addition, the registry needs to select some parameters to initialise the system. The registry chooses the EC on the finite field
and the physical unclonable function
, where p is a large 7 prime number. Then the registration centre selects an additive cyclic group P of order n on
, whose base point is G. Finally, the registry publishes parameters
in public channel.
3.2.2. Server verification tag phase
Figure shows the authentication process of this scheme. The process of the server to verify the tag is performed in an insecure public channel. The specific steps for the server to verify the tag are as follows:
Step 1:
The tag calculates the random number and the information
, and then transfers
to the server.
Step 2:
The server generates , and computes
and
. Then transmits
to the tag.
Step 3:
The tag starts to compute and
, then generates a random number
, computes
,
,
,
and
. Finally, the tag transmits the information
to the server.
Step 4: When the server receives the message , it starts to calculate
,
,
,
. After gets the
information, the server finds PUFM that matches
in the database. Then computes
.
. If
, the server verifies the tag successfully.
3.2.3. Tag verification server phase
The process of the tag verification of the server is carried out in an insecure public channel. The process of the tag verification the server is shown in the following steps:
Step 5:
The server computes a random number , and information
,
,
,
and session key
. Finally, the server transmits
to the tag.
Step 6: When the tag obtains the response information of the server, it starts to calculates
,
,
,
. If
, the tag verifies the server successfully. Then the tag calculates the session key
. At this point, the mutual authentication process ends.
4. Analysis of safety characteristics
4.1. ProVerif verification
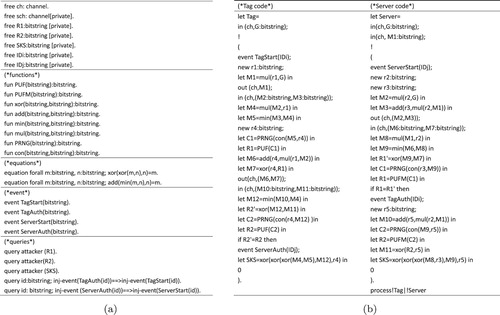
ProVerif is an analysis tool that is widely used and verifies the security of the scheme (Blanchet et al., Citation2018). ProVerif can find potential security issues in the scheme, such as key leaks and ID leaks. This paper uses ProVerif to simulate the realisation process of the proposed scheme and verify the safety of the proposed scheme. The specific process is shown in Figure .
Table shows the ProVerif symbols corresponding to the symbols of the proposed scheme. Figure (a) defines some relevant parameters of the scheme: ch and sch represent public and secret channel, respectively, R1, R2 are the key authentication information of the scheme, SKS is the session key jointly established by tag and server, IDi and IDj are the identity information for the tag and the server respectively. Then ProVerif defines 8 basic functions. “PUF” and “PUFM” represent the physical unclonable functions. “xor” represents the xor algorithm. “add” is the addition function. “min” represents the subtraction function. “mul” represents the scalar multiplication function. “PRNG” stands for pseudo random number generator. “con” is a function of string concatenation. ProVerif also defines the events in the equation and scheme. Finally, ProVerif queries about the security of the key R1, R2, SKS and tested whether the authentication process is reasonable.
Table 2. ProVerif symbols.
Then it is necessary to convert the authentication process of this scheme into ProVerif code to authenticate the security of the scheme. As shown in Figure (b), it represents the formal verification codes of the tag and the server. At last, uses the command to execute the above code.
The verification result of ProVerif is shown in Figure . The first three queries in Figure show that R1, R2, SKS in the proposed scheme is safe. The fourth query shows that TagStart and TagAuth are executed sequentially. The last query shows that ServerStart and ServerAuth are also executed in sequence. Experiments prove that the proposed scheme can resist various attacks of ProVerif and has good security performance.
4.2. Safety performance analysis
The tag and the server transmit data information through a public channel, and attackers may intercept, forge and prevent the exchange of information. Therefore, it is important for TMIS to propose a secure scheme to encrypt medical information from leakage. We have compared the proposed scheme with other related schemes such as (Farash et al., Citation2016; Li et al., Citation2018; Salem & Amin, Citation2020). Table shows some common attacks on authentication schemes, such as replay attacks, man-in-the-middle attacks, and so on (Ahamad & Khan Pathan, Citation2020).
Table 3. The comparison of safety performance.
4.2.1. Resists replay attacks
Replay attacks mean that an attacker steals relevant authentication credentials through network monitoring and other methods, and continuously replays the information to achieve the purpose of fraudulent authentication. Replay attacks are a common attack, mainly used in identity authentication systems with missing key updates. The scheme proposed in this paper adds a random number to each piece of communication information, and the information content is unique in each round of certification, so the attacker cannot attack the proposed scheme through replay attacks.
4.2.2. Resists man-in-the-middle attacks
Man-in-the-middle (MITM) attacks mean that an attacker creates a virtual terminal controlled by the attacker at two ends of the normal communication, and establishes contact between the two ends of the normal communication. In this case, the normal communication ends will establish a dialogue with the attacker and exchange communication information, and the attacker can tamper with the information content of the information sending end and send it to the information receiving end. MITM attack is a common and powerful attack in the field of information security. To resist MITM attacks, the proposed scheme implements mutual authentication, and uses PUF to generate a one-time-key and random number to encrypt communication information. If a MITM attack steals information , also unable to get the key key information
. In addition, since we have implemented mutual authentication, an attacker tampering with information
can be easily detected by our agreement. Since the attacker cannot pass the authentication of the TMIS device through the forge information, the attacker's access request will be rejected and cannot obtain the user's secret information in the TMIS device. Therefore, the scheme proposed in this paper can resist MITM attacks.
4.2.3. Forward secrecy
It means that long-term use of master key information will not lead to the disclosure of past session keys, and can ensure the security of historical communications when the key is leaked. The proposed scheme is based on the PUF-PUFM identity authentication model, which verifies the legitimacy of PUF (PUFM) to realise the purpose of mutual authentication. In the process of each round of authentication, PUF challenge information is generated by the random numbers of both parties, so the data information of the current verification process will not expose the previous private information. Therefore, the proposed scheme has forward secrecy.
4.2.4. Anonymity
Anonymity can protect the user's identity information from being leaked, and can resist attackers' tracking attacks. In the proposed scheme, the server finds the PUFM structure corresponding to the PUF by receiving the information transmitted by the tag. The transmitted
information is encrypted by the ECC encryption algorithm, and the attacker cannot obtain the
information, so the proposed scheme is anonymous.
4.2.5. Resists impersonation attacks
In this article, each tag structure integrates a unique PUF structure. PUF has natural physical unclonability and unpredictability (Liang et al., Citation2020). Therefore, the attacker cannot achieve the purpose of cloning the tag through physical means, and cannot obtain the key information required for authentication. So, the proposed scheme can resist impersonation attacks.
4.2.6. Resists side channel attacks
It means that the attacker obtains relevant key information from the physical realisation of the cryptographic system by analysing power consumption, time information and other means, so as to realise the cracking of the cryptographic system. In a side-channel attack, attackers can steal relevant information stored in electronic devices, and use the obtained key information to forge a legitimate device. The scheme proposed in this article generates and manages keys through PUF, and does not store the important information in the device, so it can resist side-channel attacks.
4.3. Cost comparison
This part will analyse and compare the performance of the proposed scheme in storage cost, communication cost and computational complexity. Assuming that the length of and the random number of the scheme are 64 bits in this article, the lengths of the ECC algorithm, PUF response message, and challenge message are 160, 128, and 64 bits, respectively.
4.3.1. Storage cost
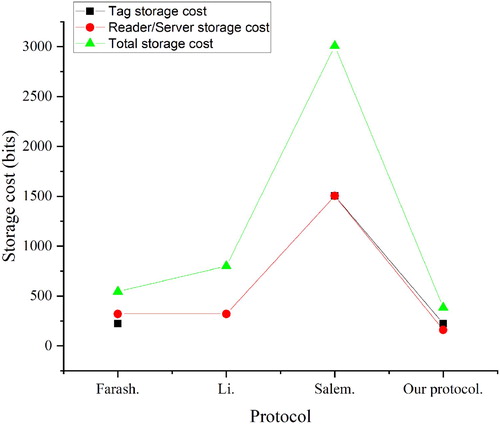
Figure compares the storage cost of the proposed scheme with other related schemes. Because the key information stored in the device may be stolen by an attacker, less key storage can bring higher security to the system.
This article only needs to store ID and elliptic curve base point information in the registration stage. Therefore, the storage cost of the key in this article is the least, the tag and the server are 224 and 160 bits respectively. However, the tag and the server of the scheme (Salem & Amin, Citation2020) require 1504 bits to store the key information respectively, and the storage cost of the scheme is too high. The storage cost of other schemes (Farash et al., Citation2016; Li et al., Citation2018) are higher than proposed scheme, so the proposed scheme has lower storage cost and is more suitable for TMIS systems with limited costs. We compare the proposed scheme with the schemes of Farash et al. (Citation2016); Li et al. (Citation2018); Salem and Amin (Citation2020), and the details of this part are shown in Table .
Table 4. The comparison of storage cost.
4.3.2. Communication cost
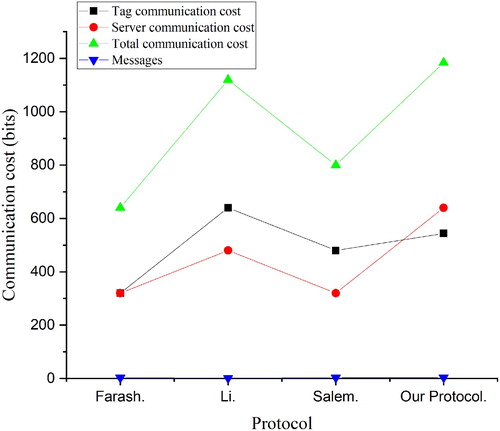
Figure compares the communication cost of the proposed scheme with other relevant schemes (Farash et al., Citation2016; Li et al., Citation2018; Salem & Amin, Citation2020). The communication costs of the tag and the server of the proposed scheme is 544 and 640 bits respectively. The proposed scheme also needs 4 messages to achieve authentication. The communication cost of the proposed scheme in this paper is similar to Li et al. (Citation2018), but higher than the schemes of Farash et al. (Citation2016); Salem and Amin (Citation2020). However, the proposed scheme implements mutual authentication and has better security performance. The communication information of the proposed scheme will not expose the key authentication information , so it is feasible to increase the communication cost appropriately to improve the security performance. We compare the proposed scheme with the schemes of Farash et al. (Citation2016); Li et al. (Citation2018); Salem and Amin (Citation2020), and the details of this part are shown in Table .
Table 5. The comparison of communication cost.
4.3.3. Computational complexity
Table shows the computational complexity of the proposed scheme and other relevant schemes (Farash et al., Citation2016; Li et al., Citation2018; Salem & Amin, Citation2020). The scheme Farash et al. (Citation2016) uses the hash function and scalar multiplication. The scheme Li et al. (Citation2018) uses the hash function and Chebyshev chaotic map algorithm. The scheme Salem and Amin (Citation2020) uses the hash function, modular exponentiation, modular multiplication and multiplicative inverse. The scheme in this article uses PUF, PRNG and scalar multiplication algorithms. Compared with the hash function, PUF has a lower implementation cost, so the scheme in this article also has advantages in implementation cost compared with other schemes.
Table 6. The comparison of computational complexity.
5. Summary and outlook
TMIS is an important medical information platform that provides a new way of communication and information acquisition for doctors and patients. Since the medical information system contains a large amount of private data of users, it is very important to protect the security of the information. Based on PUF and ECC technology, this paper proposes a safe and efficient access authentication scheme suitable for TMIS. This solution uses PUF to generate unique unpredictable key information, which does not need to be pre-existed in the device and has better security and lower cost. In addition, the program encrypts each round of communication information with random numbers, which can resist various malicious attacks including replay attacks. The solution also uses ECC technology to protect the security of PUF response information, thereby verifying the user's identity without exposing private information. Experimental analysis shows that the proposed scheme has good security performance, lower storage and communication costs, and is suitable for TMIS systems. However, although PUF has excellent safety performance, the current PUF technology still has problems such as poor stability and hardware aging. The next step of the research work will in-depth study and improve the stability and practicability of PUF. In addition, TMIS is an advanced information platform. Whether there are other security issues, we need to continue to study and analyse.
Disclosure statement
No potential conflict of interest was reported by the author(s).
Additional information
Funding
References
- Ahamad, S. S., & Khan Pathan, A. S. (2020). A formally verified authentication protocol in secure framework for mobile healthcare during COVID-19-like pandemic. Connection Science, 9, 1–23. https://doi.org/10.1080/09540091.2020.1854180
- Akgün, M., & Ça v{g}layan, M. U. (2015). Providing destructive privacy and scalability in RFID systems using PUFs. Ad Hoc Networks, 32, 32–42. https://doi.org/10.1016/j.adhoc.2015.02.001
- Amin, R., & Biswas, G. (2015). A secure three-factor user authentication and key agreement protocol for tmis with user anonymity. Journal of Medical Systems, 39(8), 43. https://doi.org/10.1007/s10916-015-0258-7
- Amin, R., Islam, S. H., Gope, P., Choo, K. K. R., & Tapas, N. (2019). Anonymity preserving and lightweight multimedical server authentication protocol for telecare medical information system. IEEE Journal of Biomedical and Health Informatics, 23(4), 1749–1759. https://doi.org/10.1109/JBHI.6221020
- Bendavid, Y., Bagheri, N., Safkhani, M., & Rostampour, S. (2018). Iot device security: Challenging “a lightweight rfid mutual authentication protocol based on physical unclonable function”. Sensors, 18(12), 4444. https://doi.org/10.3390/s18124444
- Benssalah, M., Djeddou, M., & Drouiche, K. (2016). Dual cooperative RFID-telecare medicine information system authentication protocol for healthcare environments. Security and Communication Networks, 9(18), 4924–4948. https://doi.org/10.1002/sec.v9.18
- Blanchet, B., Smyth, B., Cheval, V., & Sylvestre, M. (2018). ProVerif 2.00: Automatic cryptographic protocol verifier, user manual and tutorial. Version from 05–16.
- Chen, Y. C., Chen, R. S., Sun, H. M., & Wu, S. F. (2019). Using RFID technology to develop an intelligent equipment lock management system. International Journal of Computational Science and Engineering, 20(2), 157–165. https://doi.org/10.1504/IJCSE.2019.103810
- Farash, M. S., Nawaz, O., Mahmood, K., Chaudhry, S. A., & Khan, M. K. (2016). A provably secure RFID authentication protocol based on elliptic curve for healthcare environments. Journal of Medical Systems, 40(7), 21. https://doi.org/10.1007/s10916-016-0521-6
- Gao, Y., Li, G., Ma, H., Al-Sarawi, S. F., Kavehei, O., Abbott, D., & D. C. Ranasinghe (2016). Obfuscated challenge-response: a secure lightweight authentication mechanism for PUF-based pervasive devices. 2016 IEEE International Conference on Pervasive Computing and Communication Workshops (PerCom Workshops) (pp. 1–6). Sydney, NSW, Australia: IEEE. https://doi.org/10.1109/PERCOMW.2016.7457162
- Gao, Y., Ma, H., Abbott, D., & Al-Sarawi, S. F. (2017). PUF sensor: exploiting PUF unreliability for secure wireless sensing. IEEE Transactions on Circuits and Systems I: Regular Papers, 64(9), 2532–2543. https://doi.org/10.1109/TCSI.2017.2695228
- Gope, P., Lee, J., & Quek, T. Q. (2018). Lightweight and practical anonymous authentication protocol for RFID systems using physically unclonable functions. IEEE Transactions on Information Forensics and Security, 13(11), 2831–2843. https://doi.org/10.1109/TIFS.2018.2832849
- Islam, S. H., & Khan, M. K. (2014). Cryptanalysis and improvement of authentication and key agreement protocols for telecare medicine information systems. Journal of Medical Systems, 38(10), 17. https://doi.org/10.1007/s10916-014-0135-9
- Jiang, Y., Liang, W., Tang, J., Zhou, H., Li, K. C., & Gaudiot, J. L. (2020). A novel data representation framework based on nonnegative manifold regularisation. Connection Science, 38, 1–17. https://doi.org/10.1080/09540091.2020.1772722
- Kui, X., Feng, J., Zhou, X., Du, H., Deng, X., Zhong, P., & Ma, X. (2020). Securing top-k query processing in two-tiered sensor networks. Connection Science, 9, 1–19. https://doi.org/10.1080/09540091.2020.1753173
- Kumar, V., Ahmad, M., & Kumari, A. (2019). A secure elliptic curve cryptography based mutual authentication protocol for cloud-assisted TMIS. Telematics and Informatics, 38, 100–117. https://doi.org/10.1016/j.tele.2018.09.001
- Li, X., Peng, J., Obaidat, M. S., Wu, F., Khan, M. K., & Chen, C. (2020). A secure three-factor user authentication protocol with forward secrecy for wireless medical sensor network systems. IEEE Systems Journal, 14(1), 39–50. https://doi.org/10.1109/JSYST.4267003
- Li, C. T., Shih, D. H., & Wang, C. C. (2018). Cloud-assisted mutual authentication and privacy preservation protocol for telecare medical information systems. Computer Methods and Programs in Biomedicine, 157, 191–203. https://doi.org/10.1016/j.cmpb.2018.02.002
- Li, C. T., Weng, C. Y., & Lee, C. C. (2015). A secure RFID tag authentication protocol with privacy preserving in telecare medicine information system. Journal of Medical Systems, 39(8), 147. https://doi.org/10.1007/s10916-015-0260-0
- Li, X., Wu, F., Khan, M. K., Xu, L., Shen, J., & Jo, M. (2018). A secure chaotic map-based remote authentication scheme for telecare medicine information systems. Future Generation Computer Systems, 84, 149–159. https://doi.org/10.1016/j.future.2017.08.029
- Li, D., Zhu, Q., Wang, H., Liu, W., Feng, Z., & Zhang, J. (2019). A novel computational model for SRAM PUF min-entropy estimation. International Journal of Computational Science and Engineering, 19(2), 215–222. doi:0.1504/IJCSE.2019.100242.
- Liang, W., Fan, Y., Li, K. C., Zhang, D., & Gaudiot, J. L. (2020). Secure data storage and recovery in industrial blockchain network environments. IEEE Transactions on Industrial Informatics, 16, 6543–6552. https://doi.org/10.1109/TII.9424
- Liang, W., Huang, W., Long, J., Zhang, K., Li, K. C., & Zhang, D. (2020). Deep reinforcement learning for resource protection and real-time detection in IoT environment. IEEE Internet of Things Journal, 7, 6392–6401. https://doi.org/10.1109/JIoT.6488907
- Liang, W., Long, J., Li, K. C.., Xu, J., Ma, N., & Lei, X. (2020). A fast defogging image recognition algorithm based on bilateral hybrid filtering. ACM Transactions on Multimedia Computing, Communications, and Applications. doi:10.1145/3391297.
- Liang, W., Xiao, L., Zhang, K., Tang, M., He, D., & Li, K. C. (2021). Data fusion approach for collaborative anomaly intrusion detection in blockchain-based systems. IEEE Internet of Things Journal. https://doi.org/10.1109/JIOT.2021.3053842.
- Liang, W., Xie, S., Long, J., Li, K. C., Zhang, D., & Li, K. (2019). A double PUF-based RFID identity authentication protocol in service-centric internet of things environments. Information Sciences, 503, 129–147. https://doi.org/10.1016/j.ins.2019.06.047
- Liang, W., Xie, S., Zhang, D., Li, X., & Li, K. C. (2020). A mutual security authentication method for RFID-PUF circuit based on deep learning. ACM Transactions on Internet Technology. https://doi.org/10.1504/IJCSE.2019.100242
- Liang, W., Zhang, D., Lei, X., Tang, M., Li, K. C., & Zomaya, A. (2020). Circuit copyright blockchain: blockchain-based homomorphic encryption for IP circuit protection. IEEE Transactions on Emerging Topics in Computing. https://doi.org/10.1109/TETC.2020.2993032
- Lim, D., Lee, J. W., Gassend, B., Suh, G. E., Van Dijk, M., & Devadas, S. (2005). Extracting secret keys from integrated circuits. IEEE Transactions on Very Large Scale Integration (VLSI) Systems, 13(10), 1200–1205. https://doi.org/10.1109/TVLSI.2005.859470
- Majzoobi, M., Rostami, M., Koushanfar, F., Wallach, D. S., & Devadas, S. (2012). Slender PUF protocol: A lightweight, robust, and secure authentication by substring matching. 2012 IEEE Symposium on Security and Privacy Workshops (pp. 33–44). San Francisco, CA, USA: IEEE. https://doi.org/10.1109/SPW.2012.30.
- Malialis, K., Devlin, S., & Kudenko, D. (2015). Distributed reinforcement learning for adaptive and robust network intrusion response. Connection Science, 27(3), 234–252. https://doi.org/10.1080/09540091.2015.1031082
- Mansoor, K., Ghani, A., Chaudhry, S. A., Shamshirband, S., Ghayyur, S. A. K., & Mosavi, A. (2019). Securing IoT-based RFID systems: A robust authentication protocol using symmetric cryptography. Sensors, 19(21), 4752. https://doi.org/10.3390/s19214752
- Maurya, P. K., & Bagchi, S. (2018). A secure PUF-based unilateral authentication scheme for RFID system. Wireless Personal Communications, 103(2), 1699–1712. https://doi.org/10.1007/s11277-018-5875-2
- Rostami, M., Majzoobi, M., Koushanfar, F., Wallach, D. S., & Devadas, S. (2014). Robust and reverse-engineering resilient PUF authentication and key-exchange by substring matching. IEEE Transactions on Emerging Topics in Computing, 2(1), 37–49. https://doi.org/10.1109/TETC.6245516
- Safkhani, M., & Vasilakos, A. (2019). A new secure authentication protocol for telecare medicine information system and smart campus. IEEE Access, 7, 23514–23526. https://doi.org/10.1109/ACCESS.2019.2896641
- Salem, F. M., & Amin, R. (2020). A privacy-preserving RFID authentication protocol based on El-Gamal cryptosystem for secure TMIS. Information Sciences, 527, 382–393. https://doi.org/10.1016/j.ins.2019.07.029
- Siddiqui, Z., Abdullah, A. H., Khan, M. K., & Alghamdi, A. S. (2014). Smart environment as a service: Three factor cloud based user authentication for telecare medical information system. Journal of Medical Systems, 38(1), 201. https://doi.org/10.1007/s10916-013-9997-5
- Srivastava, K., Awasthi, A. K., Kaul, S. D., & Mittal, R. (2015). A hash based mutual RFID tag authentication protocol in telecare medicine information system. Journal of Medical Systems, 39(1), 369. https://doi.org/10.1007/s10916-014-0153-7
- Suh, G. E., & Devadas, S. (2007). Physical unclonable functions for device authentication and secret key generation. 2007 44th ACM/IEEE Design Automation Conference (pp. 9–14). San Diego, CA, USA: IEEE.
- Tewari, A., & Gupta, B. (2020). An internet-of-things-based security scheme for healthcare environment for robust location privacy. International Journal of Computational Science and Engineering, 21(2), 298–303. https://doi.org/10.1504/IJCSE.2020.105742
- Wazid, M., Das, A. K., Kumari, S., Li, X., & Wu, F. (2016). Design of an efficient and provably secure anonymity preserving three-factor user authentication and key agreement scheme for TMIS. Security and Communication Networks, 9(13), 1983–2001. https://doi.org/10.1002/sec.1452
- Xie, Q., Hu, B., Dong, N., & Wong, D. S. (2014). Anonymous three-party password-authenticated key exchange scheme for telecare medical information systems. PloS One, 9(7), e102747. https://doi.org/10.1371/journal.pone.0102747
- Xu, H., Ding, J., Li, P., Zhu, F., & Wang, R. (2018). A lightweight RFID mutual authentication protocol based on physical unclonable function. Sensors, 18(3), 760. https://doi.org/10.3390/s18030760
- Xu, X., Zhu, P., Wen, Q., Jin, Z., Zhang, H., & He, L. (2014). A secure and efficient authentication and key agreement scheme based on ECC for telecare medicine information systems. Journal of Medical Systems, 38(1), 1629. https://doi.org/10.1007/s10916-013-9994-8
- Zhang, S., Yao, T., Sandor, V. K. A., Weng, T. H., Liang, W., Su, J., & Jin, H. (2020). A novel blockchain-based privacy-preserving framework for online social networks. Connection Science, 1–21. https://doi.org/10.1080/09540091.2020.1854181
- Zheng, L., Song, C., Cao, N., Li, Z., Zhou, W., Chen, J., & Meng, L. (2018). A new mutual authentication protocol in mobile RFID for smart campus. IEEE Access, 6, 60996–61005. https://doi.org/10.1109/ACCESS.2018.2875973
- Zhou, Z., Wang, P., & Li, Z. (2019). A quadratic residue-based RFID authentication protocol with enhanced security for TMIS. Journal of Ambient Intelligence and Humanized Computing, 10(9), 3603–3615. https://doi.org/10.1007/s12652-018-1088-5