?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.Abstract
5G-assisted device-to-device (D2D) communication plays an instrumental role in minimizing latency, maximizing resource utilization, improving speed, and boosting system capacity. However, the technology confronts several challenges to realize its enormous potential fully. Security and privacy concerns are at the top of the list that can jeopardize the regular operation of D2D communication by executing various assaults such as free-riding and impersonation. Although several researchers suggested different solutions to these concerns, most are too heavy for resource-constrained devices or are vulnerable to security risks. Consequently, we proposed a lightweight and provably secure D2D communication protocol comprising initialization, device discovery, and link setup phases. The protocol is light in terms of computational overhead and communication latency while verifiably secure through formal security analysis. The protocol relies on a new network function, called D2D Security Management Function (DSMF), located near the devices to facilitate secure communication and improve performance. Moreover, we used deep learning-based UE trust score forecasting to better handle and prioritize communication requests when the network is overloaded. The comparative analysis against state-of-the-art security schemes concerning computational and communication overheads shows that our protocol is a superior alternative for resource-constrained IoT devices wishing to perform D2D communication in a 5G network.
1. Introduction
With the fast progression of the technology and its widespread adoption, it is anticipated that mobile users’ needs would lead to the development of a variety of applications and services based on the interconnection of large-scale devices. 5G enables a wide range of applications to benefit from faster connections, more scalable settings for machine-to-machine interactions, and low latency and exceptionally dependable connectivity (Kim, Citation2020). IoT is at the heart of these applications, spanning almost everything from basic embedded sensors to complex, innovative industries to critical medical device communication. However, because all communications must pass via the core network, the traffic volume on wireless networks increases with IoT devices. Such arrangements adversely impact the performance of the network. The D2D communication technique can serve as a possible solution to this problem (Uchida et al., Citation2019).
D2D communication is a technique of sharing data that involves creating a direct communication channel between neighbouring devices independent of the core network and base stations (Haus et al., Citation2017). D2D communication can alleviate the load on the mobile communication network by splitting the network's mobile traffic (Liu et al., Citation2015). Moreover, it can provide a connection with extremely low latency, overcome the network capacity issue through a direct link, and expand the coverage to enable other User Equipment (UE) with poor connections to access information (Kar & Sanyal, Citation2018). In general, D2D plays a crucial role in maximizing the use of available resources, minimizing communication latency, enhancing data rates, and boosting system capacity (Adnan & Ahmad Zukarnain, Citation2020). Apart from the various benefits to the current cellular networks, D2D communication is projected to become the foundation of beyond 5G (5GB) based IoT to build new creative application services.
Despite the numerous advantages of D2D communications, there are various challenges concerning an effective interface and power management, device discovery and mode selection, and security and privacy. Especially regarding the security and privacy challenges, different security attacks threaten the regular operation of D2D communication. For instance, location spoofing, jamming, free-riding, privacy violation, impersonation, and eavesdropping are the most common (Zhang et al., Citation2019).
Consequently, it is eminent to safeguard devices from these attacks by designing robust security protocols that satisfy different security properties such as anonymity, mutual authenticity, confidentiality, integrity, availability, and perfect forward secrecy while being lightweight. In this regard, there are different solutions suggested to tackle such security issues through various approaches. Seok et al. (Citation2020) proposed a D2D Authentication and Key Agreement (AKA) protocol on a 5G IoT network using ECDH and digital signatures, while Chow and Ma (Citation2020) offered a new protocol that addresses the security threats, like free-riding attacks, found in the former. Nevertheless, they still have security flaws. In contrast, Shang et al. (Citation2019) and Shang et al. (Citation2020) used a certificateless approach to implement AKA in D2D communication. However, all the above approaches rely heavily on public-key cryptography, thus being improper for resource-constrained IoT devices. It is worth noting that it is not an easy task to develop security mechanisms for D2D communication given the hybrid nature of the communication on top of the tight resource constraints of the devices participating in the network.
This paper proposes a lightweight and secure D2D communication protocol with initialization, device discovery, and link setup phases. The protocol, unlike its predecessors, is more lightweight in terms of computational overhead and communication latency while provably secure against attacks that violate important security properties like anonymity, mutual authenticity, secure key exchange, and perfect forward secrecy. Our protocol heavily relies on the trust established by the 5G core network and the UE during the primary authentication. This trust enabled us to secure the channel by using cryptographically light operations, such as symmetric key encryption and message authentication codes. Furthermore, we developed a deep learning-based solution to address the request prioritizing problem, reducing network strain when the proposed protocol runs across ultra-dense D2D networks. We used the sequence-to-sequence regression Long Short-Term Memory (LSTM) model to anticipate UE trust levels to identify which UEs must be addressed with priority when network traffic is high. The main contributions of the paper are summarized as follows:
We proposed a lightweight and provably secure D2D communication protocol with initialization, device discovery, and link setup phases.
We proposed a new network function called DSMF near the UEs for efficient D2D communication.
We used deep learning-based forecasting that predicts UE trust scores for request prioritization to lessen network loads.
We formally evaluated the security of the protocol through two formal verification approaches (BAN-Logic (Burrows et al., Citation1989) and Scyther (Cremers, Citation2008)).
We compared the proposed protocol against state-of-the-art D2D security protocols.
The remainder of this paper proceeds as follows. In Sections 2 and 3, the article discusses related works and the system model of 5G-based D2D communication, respectively. Section 4 discusses D2D communication security and privacy. We provide the suggested protocol and its formal security evaluation in Sections 5 and 6, respectively. Section 7 provides the results of the comparative analysis, and Section 8 concludes the paper.
2. Related work
Different researchers offered various ways to solve the security and privacy problems in D2D communication. For example, Baskaran and Raja (Citation2017) suggested a D2D authentication and secret key sharing protocol to guard against security risks in the Long-Term Evolution Advanced (LTE-A) environment. However, because the MME (Mobility Management Entity) computes the user's public-key pair, the user's private key's reliability is insufficient. Furthermore, the protocol is designed exclusively for D2D communication in an LTE-A network environment, making it unsuitable for the current 5G cellular networks.
Seok et al. (Citation2020) proposed a D2D AKA protocol that employs ECDH and digital signatures in a 5G IoT network. Despite the study's importance of being the first to handle D2D communication in a 5G setting, it does not take user authentication into account while negotiating the ECDH key. As a result, the protocol is vulnerable to security risks, particularly the free-riding and Man-In-The-Middle (MITM) attacks.
Chow and Ma (Citation2020) designed a security protocol to address the problems identified in Seok et al. (Citation2020). By looking for nearby users in the 5G network and subsequent mutual authentication and secure key agreement procedures, the protocol ensures anonymity through Globally Unique Temporary Identifier (GUTI) while preventing eavesdropping, replay, MITM, and free-riding attacks. However, like in Baskaran and Raja (Citation2017), the user's public key pair is generated by the AMF, and the protocol does not carry out the key confirmation procedure. Moreover, there is a risk of a DoS (Denial of Service) attack because of the digital signature's lack of timeliness.
Other studies suggested certificateless approaches for 5G-based D2D communications. Shang et al. (Citation2019, Citation2020), for instance, proposed a protocol designed to support the D2D group communication in 5G cellular networks leveraging Certificateless Public Key Cryptography (CL-PKC) with ECC and Digital Signatures. Besides, other researchers proposed a D2D communication security approach using ID-based encryption. However, ID-based encryption lacks practicality and is not optimal for IoT environments because of the heavy characteristics of public keys cryptography. The related works that are proposed to protect D2D communication are summarized in Table .
Table 1. Summary of related works.
The studies presented above are unsuitable enough for 5G network-based D2D communication or fail to meet critical security criteria. Thus, this article offers a novel security protocol suited for D2D communication while simultaneously meeting different security requirements. More significantly, following the primary authentication of the 5G network, our approach makes the best use of the trust developed by UE and AMF. The suggested security protocol, as a result, enables safe and efficient D2D authentication and key agreement.
3. System model
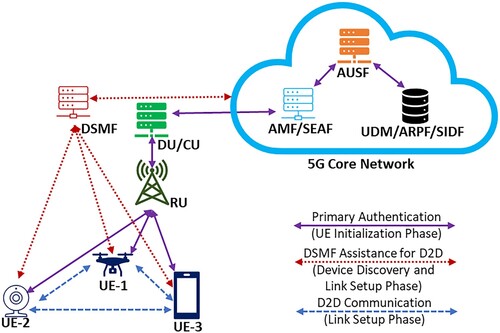
The system model for 5G-based D2D communication consists of various components and links based on the 5G reference architecture (TS23.501, Citation2021). The main elements of this model are the UE, 5G Radio Access Network (RAN), DSMF, and the 5G Core Network, as shown in Figure . Moreover, the communication path comprises the back-haul (between UE and 5G-RAN) and front-haul (between 5G RAN and the 5G Core) links. Here, we provide a brief description of each component.
Concerning D2D communication, each UE performs a primary authentication to achieve mutual authenticity with the 5G network. Devices can also carry out the primary authentication via non-3GPP technology through Non-3GPP Interworking Function (N3IWF), making the procedure independent of the underlying radio access technology.
5G-AKA (5G Authentication and Key Agreement) or EAP-AKA’ (Extensible Authentication Protocol) serve as the preferred primary authentication in 5G. The procedure involves different virtual network functions, residing in both serving and home networks, like Access and Mobility Management Function (AMF), Security Anchor Function (SEAF), Authentication Server Function (AUSF), Unified Data Management (UDM), Authentication Credential Repository and Processing Function (ARPF), and Subscription Identifier De-Concealing Function (SIDF).
AMF is the first network function in the core network to receive all UE connections through gNB or N3IWF. Besides managing essential services such as registration, mobility, and connection, it supports the confidentiality and integrity of signalling data while protecting the subscribers’ privacy. In proximity with AMF, SEAF plays a critical role in providing the authentication functionality for UE to be authenticated to its home network via the AMF in the serving network.
AUSF primarily carries out the authentication function in the home network for the 3GPP and non-3GPP access. In authenticating the UE, AUSF delivers a key (KSEAF) to the SEAF, where the latter derives the KAMF for the AMF. AMF then uses this key to maintain the confidentiality and integrity of the messages exchanged between itself and the UE while also computing KgNB that UE and the corresponding gNB will utilize to safeguard future communications.
UDM oversees several services such as registration and deregistration, retrieval of user subscription data, and supply of updated authentication-related subscriber data. Moreover, it accommodates the ARPF to pick an authentication method while also computing keying materials for AUSF. When UDM/ARPF receives the authentication request containing Subscription Concealed Identifier (SUCI), it is sent to SIDF to decrypt it and return the Subscription Permanent Identifier (SUPI). Receiving SUPI, AMF generates the 5G Globally Unique Temporary Identifier (5G-GUTI) and communicates it to the UE for subsequent requests. The primary use of 5G-GUTI is to identify the UE globally and uniquely without revealing its permanent identity. Moreover, 5G-GUTI embeds the Globally Unique AMF Identifier (GUAMI), which helps identify a particular AMF and the network.
In 5G, gNB is functionally split into three parts: Radio Unit (RU), Distribution Unit (DU), and Centralized Unit (CU), with RU being the nearest to UE and CU the farthest. There can be a variety of ways to place these components depending on the deployment model. This system model adopted a scenario where RU resides at the cell site and the CU and DU co-located at the edge. Our newly designed network function, DSMF, also resides at the edge to facilitate D2D communication. We will describe the detailed operation of DSMF in the proposed protocol section.
There are three distinct paths concerning the communication links: the first is the primary authentication line that the UE communicates with the 5G Core Network via 5G-RAN. The second is the DSMF assisted link setup path in which DSMF receives D2D communication requests from UEs and provides keys for protecting the channel between the UEs. The final one is for the actual D2D communication between UEs with the established keys.
4. The security and privacy of D2D communication
4.1. Security and privacy issues
Various threats hinder the regular interactions between peers in D2D communication. Unfortunately, the security and privacy component of the D2D communication environment was largely overlooked by both industry and academia (Adnan & Ahmad Zukarnain, Citation2020). Some of the most common security threats and attacks that are executed on D2D communications are eavesdropping, tampering, masquerading, replay attack, and free-riding attacks (Haus et al., Citation2017).
An attacker can eavesdrop on the transmitted information within D2D communication to execute a range of attacks such as tampering (in which an adversary modifies the eavesdropped messages while infecting genuine peers by disseminating malicious materials). Cryptographic solutions are often employed to thwart such security threats. Specific to D2D, different authors provided solutions to address these issues (Haus et al., Citation2017; Wang et al., Citation2018). On the other hand, a masquerading attack enables an attacker to impersonate an honest D2D peer to deceive the other. Ensuring mutual authenticity among devices wishing to exchange information through D2D communication in both cellular and ad-hoc connectivity can serve a good purpose in mitigating such threats. A passive attack that retransmits or delays a message communicated between devices is a replay attack, which can be effectively alleviated by guaranteeing message freshness. The free-riding attack, particularly common to D2D communication, happens when a malicious D2D peer receives data or service but denies contributing its part. Building cooperative incentive structures to establish fairness and assuring availability in such structures are necessary to protect the communication from such attacks (Zhang & Lin, Citation2017). A practical solution to resolve a free-riding attack, for example, is provided in Baskaran and Raja (Citation2017).
In addition to security, different privacy issues concerning information, identity, and location also threaten D2D communications (Gandotra et al., Citation2017). Aside from security concerns, devices in D2D communication take privacy very seriously. It is significant due to the versatility of devices participating in the hybrid communication setup. Hence, the communication system should enable privacy measures to protect the “what,” “who,” and “where” of the devices. These three vital privacy elements correspond to the anonymity of information exchanged, the identity of devices, and location (Zhang & Lin, Citation2017).
4.2. Threat model
D2D communications, as mentioned in the previous subsection, pose many security issues, primarily because the devices operate wirelessly where an adversary has access to a vast quantity of sensitive information (ciphered or plain). As a result, anyone with malevolent purpose and technical competence can exploit these flaws to conduct an assault, therefore bringing the dangers to light. Consequently, recognizing and modelling the risks posed to these communication systems are essential for the devices to function correctly in the event of a threat.
We picked the strongest opponent anticipated in the Dolev-Yao (DY) threat model (Dolev & Yao, Citation1983) capable of intercepting messages transmitted from/to UE to/from the 5G network and among the UEs. Furthermore, the attacker can originate or receive transmissions on behalf of authorized devices or a network under this paradigm. Essentially, the adversary is regarded as the channel itself, with minor exceptions such as the inability to correctly guess the keys used to encrypt and authenticate messages transmitted between legitimate entities, the failure to retrieve messages from a message digest, or the inability to correctly guess the random numbers utilized in the protocol within the time range allowed.
4.3. Security and privacy requirements
Despite their broad uses and rising popularity, IoTs have been associated with a slew of security and privacy issues, according to several researches (Caputo et al., Citation2020; He et al., Citation2021; Liu et al., Citation2020; Schafer & Edwards, Citation2017; Wong & Yiu, Citation2020). D2D communication, which is expected to be utilized by resource constrained IoT devices, should consider the appropriate security and privacy requirements for the aforementioned possible concerns. The following are the security criteria for D2D communication as identified in Zhang and Lin (Citation2017).
Lightweight cryptographic operation: an authentication and key agreement protocol should fully acknowledge the limited resources concerning power, processing, storage, and communication posed on D2D communication.
Anonymity: it should be difficult, if not impossible, to reveal the information, location, and identity of devices through messages sent and received during the device discovery process.
Mutual Authentication: the devices participating in the D2D communication should know whom they are talking to and vice versa.
Confidentiality: after a successful key exchange, the attacker should not obtain the key and the plain data protected by it.
Integrity: an unauthorized user should not modify the protected message transmitting between the D2D users.
Perfect Forward Secrecy: an attacker should not obtain the D2D session participants’ current session keys from the previous session key.
5. Proposed protocol
The proposed protocol comprises three stages, UE Initialization Phase, Device Discovery Phases, and Link Setup Phase, and different participants like UE, DSMF, AMF/SEAF, and ARPF/UDM. In designing this protocol, we took the following essential assumptions.
Each DSMF belongs to the 5G serving network.
The AMF/SEAF knows the unique identifier of the DSMF (IDDSMF) and DSMF has the unique identifier of the SEAF (IDSEAF) before the run of the protocol.
Each DSMF shares a secret key KSEAF-DSMF with its 5G serving network’s SEAF.
Once the primary authentication concludes, UE(i) shares the session key KSEAF-UE(i) with the corresponding SEAF.
To provide privacy and anonymity, the proposed protocol counts on 5G-GUTI, which is temporarily assigned to each UE after the primary authentication and periodically updated.
shows the different notations and their meanings as used in the protocol.
Table 2. Notations.
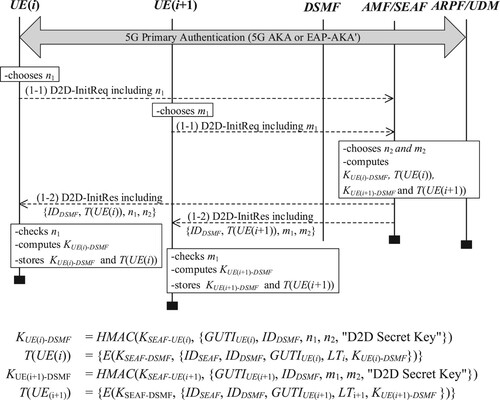
5.1. UE initialization phase
The first stage of the D2D communication is the initialization of UE, as shown in Figure . It starts with the primary authentication (through 5G-AKA or EAP-AKA’) to allow the 5G network and UE to authenticate mutually. The resulting keys and keying materials are then utilized to secure the subsequent communications. Moreover, each UE is assigned with the temporary identifier GUTI, which conceals its SUPI and is updated regularly.
Aside from the “normal” course of actions in D2D communication, two important cases require the instantiation of this phase: expired ticket and new GUTI assignment. While the former case refers to the expiration of the lifetime of a ticket generated for a particular UE, the latter refers to different scenarios where an AMF decides to change the current GUTI. According to TS 133 501 (V16.7.1) (TS33.501, Citation2021), there can be at least three such cases where AMF can issue a new GUTI to the UE: during registration request message (initial registration, mobility registration update, or periodic registration update), service request message in response to paging, and a message from lower layers about the resumption of an RRC connection for a UE in IDLE mode. Figure illustrates the message flows in this phase.
(1-1) D2D-InitReq
After the 5G primary authentication, the devices that want to communicate through D2D send the D2D-InitReq message to AMF/SEAF independently. These messages include random integers n1 and m1 from UE(i) and UE(i+1), respectively.
(1-2) D2D-InitRes
Upon receiving the D2D-InitReq message, AMF/SEAF generates random nonce for each of the requesting devices (i.e. n2 and m2 for UE(i) and UE(i+1), respectively, in this case). Next, it computes a session key KUE(i)-DSMF (or KUE(i+1)-DSMF) and a ticket T(UE(i)) (or T(UE(i+1))) as shown in Figure . Finally, it sends the D2D-InitRes containing IDDSMF, LTi (or LT(i+1)), T(UE(i)) (or T(UE(i+1))), and the random nonce n1 and n2 (or m1 and m2) for each of the requesting devices. Each device then checks if the received nonce is the same as it sent out in the D2D-InitReq message. If the verification succeeds, the devices compute the session keys and store them with the received tickets and lifetime, which concludes the UE initialization phase of the D2D protocol.
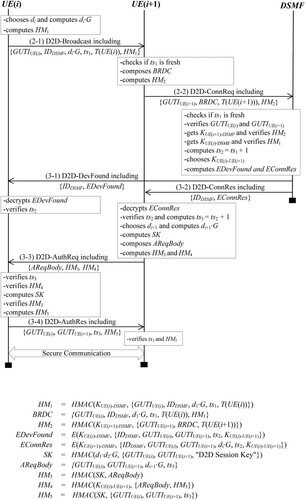
5.2. Device discovery phase
Once the 5G network authenticates the UEs and the necessary materials (session keys and tickets) for D2D communication are ready, the device discovery phase proceeds.
(2-1) D2D-Broadcast
When devices receive the required materials, such as session keys, lifetimes, and tickets, for D2D communication, they can prepare a broadcast message for device discovery. The set of domain parameters is assumed to be shared between the communicating devices before executing the protocol. For instance, as shown in Figure , UE(i) prepares a broadcast message for device discovery by first generating the ECDH private-key public-key pair. It picks a random integer di in the interval [1 … n-1] as its private key and computes the public key Qi = di·G using scalar multiplication. Next, it forms and broadcasts the D2D-Broadcast message including {GUTIUE(i), IDDSMF, Qi, ts1, T(UE(i)), HM1}, where HM1 is the HMAC value computed over the entire message using KUE(i)-DSMF. The primary purpose of including HM1 is to protect the broadcast message from message tampering and to allow DSMF to prevent resource exhaustion attacks.
(2-2) D2D-ConnReq
When a neighbour device UE(i+1) receives the D2D-Broadcast message, it first verifies the freshness of the included ts1if it intends to communicate with UE(i) directly. In a positive case, that device forms BRDC = {GUTIUE(i), IDDSMF, Qi, ts1, T(UE(i)), HM1}, followed by computing an HMAC value HM2 over {GUTIUE(i+1), BRDC, and T(UE(i+1))} using KUE(i+1)-DSMF and sending all together to DSMF as part of the connection request message D2D-ConnReq.
5.3. Link setup phase
As a final stage of the proposed protocol, this phase assists the communicating peers to securely exchange keys that will protect the link for subsequent communication.
(3-1) D2D-DevFound and (3-2) D2D-ConnRes
When receiving a D2D-ConnReq message (i.e. by UE(i+1) for this case), DSMF first checks the freshness of the timestamp ts1. If that succeeds, it uses KSEAF-DSMF to decrypt the received tickets into their original information. The lifetimes of both tickets LTi and LT(i+1) are then validated. Meanwhile, DSMF verifies the two devices’ authenticity through the received temporary identities, GUTIUE(i) and GUTIUE(i+1), which are then compared with the identities decrypted from the tickets. In turn, it applies the decrypted session keys KUE(i+1)-DSMF and KUE(i)-DSMF to check the validity of the two HMAC values HM2 and HM1, respectively. Once all the verification tests are passed, DSMF successfully authenticates UE(i) and UE(i+1) and believes that they wish to communicate with each other directly. This leads DSMF to compute ts2 = ts1 +1 and choose a session key KUE(i)-UE(i+1) for the involved UEs. Subsequently, it distributes this session key to UE(i) (through the D2D-DevFound message) and UE(i+1) (via the D2D-ConnRes message) as shown in the steps (3-1) and (3-2) of Figure , respectively. Note that such secure key distribution is achieved through the values EDevFound (encrypted with KUE(i)-DSMF) and EConnRes (encrypted with KUE(i+1)-DSMF).
(3-3) D2D-AuthReq
When UE(i+1) receives the D2D-ConnRes message containing IDDSMF and EConnRes from DSMF, it decrypts the latter into {IDDSMF, GUTIUE(i), GUTIUE(i+1), Qi, ts2, KUE(i)-UE(i+1)}. It then verifies ts2. If the verification holds, it computes ts3 = ts2 + 1. Next, it chooses an arbitrary integer di+1 from the interval [1, n-1] as its ECDH private key. Thereafter, it computes the ECDH public key Qi+1 = di+1·G using scalar multiplication. After that, it computes the ECDH session key SK = HMAC(di+1·Qi, {GUTIUE(i), GUTIUE(i+1), “D2D.Session Key”}). It then assigns {GUTIUE(i), GUTIUE(i+1), Qi+1, ts3} to AReqBody and computes HM3 and HM4. Finally, it sends UE(i) the D2D-AuthReq message containing {AReqBody, HM3, HM4}. Here, the ECDH key is removed from the UE(i+1)’s memory to guarantee perfect forward secrecy by prohibiting the recovery of SK.
(3-4) D2D-AuthRes
When UE(i) receives the D2D-DevFound message from DSMF, it decrypts the included EDevFound into {IDDSMF, GUTIUE(i), GUTIUE(i+1), ts2, KUE(i)-UE(i+1)} and verifies ts2. In addition, upon receipt of the D2D-AuthReq message from UE(i+1), it obtains {GUTIUE(i), GUTIUE(i+1), Qi+1, ts3} by extracting AReqBody from that message. Afterward, it checks ts3 followed by verification of HM4 with KUE(i)-UE(i+1). At this point, if the above test is successful, UE(i) will believe that UE(i+1) not only possesses KUE(i)-UE(i+1) but also wishes for direct communication. Such a belief allows UE(i) to compute the ECDH session key SK = HMAC(di·Qi+1, {GUTIUE(i), GUTIUE(i+1), “D2D Session Key”}) while preventing resource exhaustion attack. UE(i) then validates HM3 with the newly generated session key SK. If this validation holds, it will be sure that UE(i+1) owns SK. Eventually, it concludes the link setup phase of the proposed protocol by responding to the D2D-AuthReq message. To do so, it first computes HM5 = HMAC(SK, {GUTIUE(i), GUTIUE(i+1), ts3})), forms the D2D-AuthRes message as {GUTIUE(i), GUTIUE(i+1), ts3, HM5}, and sends back to UE(i+1). UE(i) deletes the ECDH private key from its memory to support the perfect forward secrecy. On receiving the D2D-AuthRes message, UE(i+1) validates ts3 and HM5. If this validation holds, then the link setup phase successfully concludes. In addition, UE(i+1) is sure that its correspondent is ready for direct secure communication based on SK. Consequently, both devices can start to communicate over the established secure channel securely.
5.4. Request forecasting
A potential network load is expected in DSMF as it processes numerous D2D connection requests. After checking, verifying, and computing different values and cryptographic operations, DSMF prepares two responses (one for the D2D-ConnRes and another for D2D-DevFound) for each request of a UE. As a result, DSMF must prioritize requests to reduce the heavy burden it endures.
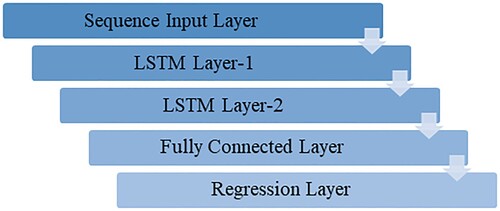
To reduce the burden of the network, when the proposed protocol works in an ultra-dense D2D communication scenario, deep learning-based solutions can be applied to prioritize the requests. Among several possibilities explored in this direction of research to understand if the inclusion of deep learning solutions can fasten the applicability of the proposed protocol, the sequence-to-sequence regression LSTM model (Pełka & Dudek, Citation2020) is adopted. In this model, trust is used as a factor of prediction and forecasting, as shown in Figure , with the help of time-series forecasting using a deep learning tool in MATLAB. The model uses four-fifths of the data sequence for training and the leftover fifth for testing. Features and responses are one as only one series (Trust score) must be forecasted. The number of hidden units in each LSTM layer is set to 100 and trained for 400 epochs at a learning rate of 0.005 and learning dropping at 225. However, the choice of deep learning model is not an ideology behind this paper; rather, the focus is to consider request (priority) forecasting for better serving the network when the proposed protocol is used for secure communications.
Figure 4. An illustration of the sequence-to-sequence regression LSTM model used for the request (priority)-forecasting for UEs in the event of an overburdened network.
The trust-movement of the UE’s is calculated by assigning the highest value of 1 (i.e. ) initially when the network initiates and the UE connects itself for the first time to the network. Then, based on the three phases of the protocol, a trust value is calculated for the active instances of the UE. Next, the LSTM forecasting is used to rank the requests of the UE when the network is overwhelmed, and D2D communication may degrade. The trust of a UE is calculated as a normalized score by taking the average of the score at the previous instance and the current instance, such that:
(1)
(1) Where Kt is the number of key updates performed when broadcasting. Dt is the number of device discovery requests leading to additional delays because of connection failures. Lt is the non-responsive time of the UE used to calculate a point until which prediction is possible before the network keys kick in and the network is reset with primary authentication, which does not affect the privacy of the UE. For the simplicity, the non-responsive time is considered the communication latency incurred by the proposed protocol. It helps to build a complete active profile of the UE. γ1, γ2, and γ3 are the precedence constants for the associated properties of the UE within the protocol. In the case of multiple features, these can be extended further, ensuring that their cumulative upper bound is 1. The forecast of trust value for a given interval is collected, and then the average values of the UEs’ trust are compared and ranked to determine the UEs’ priority. This ranking assists in determining which UE’s must be handled with priority when the network load is high, and many broadcast requests are pending to be handled with the limited handling capacity of the DSMF. Algorithm 1 helps capture the exact idea of priority forecasting of UEs for countering overheads and enabling D2D communications even if the network is overwhelmed.
Table
Table 3. Settings for request-forecasting.
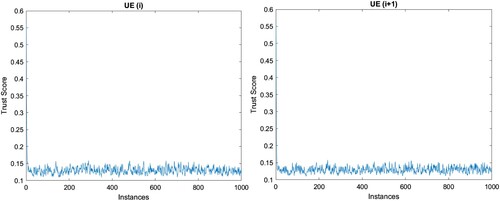
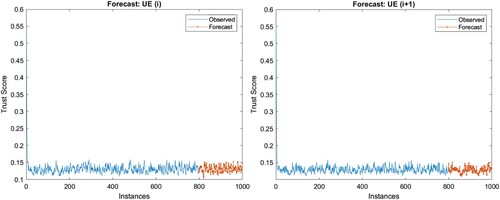
Based on the sequence-to-sequence regression LSTM, the forecast values of UE(i) and UE(i+1) can be identified as shown in Figure , which shows that the mean trust score in the predictive interval for UE(i) (0.134) is higher than UE(i+1) (0.125). Thus, this priority can be used to handle the requests when the network is overloaded. However, to make this approach successful, the network load should be forecasted accurately to an extent. Then a similar interval can be used to forecast requests from the UEs and decide if the UE must be handled with priority. Forecasting of the network load is crucial as it will determine the model for the priority ranking of UEs. Alongside, the historical data of the UE will also assist in accurately forecasting the trust score, which makes the comparison useful and deterministic. The open problem here is that how many data points should be used to forecast the trust score for the UE as deep learning itself poses an issue of slow convergence rate.
Figure 6. Forecast of trust score of UE(i) (RMSE=0.0133) and UE(i+1) (RMSE=0.0123) for 20% of remainder instances over 80% trained sequence.
summarizes each phase of the proposed protocol along with their functions, message protection mechanisms and involved entities and keys.
Table 4. Summary for the phase of the proposed protocol.
In summary, the proposed protocol brings crucial performance and security benefits by
Reducing the latency and burden of the 5G core network by adopting DSMF and issuing a ticket for each UE.
Lessening the network load of DSMF by forecasting requests based on trust levels of UEs.
Optimizing computational overhead via ECDH based lightweight key exchange and best use the trust established between UE and SEAF during the primary authentication to generate the session key and the corresponding ticket.
Preserving privacy by anonymizing the identities of the UEs through 5G-GUTI.
Guaranteeing protection of session keys by ensuring perfect forward secrecy through ephemeral ECDH algorithm. Moreover, each UE’s ECDH private key is removed from its memory immediately after the key exchange to prevent an attacker from recovering the session key.
6. Formal security evaluation
This section employs a formal security verification technique to assess the security of the proposed D2D security protocol and ensures that it meets the security criteria. The main objective here is to provide a strict and thorough method of verifying the validity of the protocol by using logical inferences and model checking techniques. Accordingly, BAN-logic (Burrows et al., Citation1989) and Scyther (Cremers, Citation2008) are often used to conduct the formal verification of security protocols (Ahamad & Khan Pathan, Citation2021; Zhou et al., Citation2011). The proposed protocol also uses these mechanisms to carry out the formal security analysis.
6.1. Formal verification with BAN-Logic
Named after its three inventors Burrows, Abadi, and Needham, BAN-Logic is a set of rules used to formally analyse security protocols through a series of procedures referred to as Idealization, Assumption, Goal, and Derivation.
As the first step, to make it appropriate for the subsequent phases, the suggested protocol is changed into an idealized form where the flow of messages between distinct roles is transformed and expressed using BAN-Logic notations. Only protected messages (like ciphered texts, digitally signed messages, and message authentication codes) transform into an idealized form. Next, appropriate assumptions that may not be explicitly stated in the protocol are declared to help complete the proofs. Subsequently, different security goals like mutual authentication, secure key exchange, replay attack protection, Etc., are stated using BAN-Logic notation. Finally, the derivations step proceeds by using the idealizations, assumptions, and BAN-Logic rules to prove the goals.
Tables and summarize the notations and rules of BAN-Logic, respectively. In addition, a new rule, Diffie-Hellman Rule (DH), is defined to derive the exchange of session key SK. The DH rule states that when a role P believes that another role Q sends the Diffie-Hellman public key and P believes its Diffie-Hellman public key, P can believe the Diffie-Hellman session key.
Table 5. BAN-Logic Notations.
Table 6. BAN-Logic Rules.
Table 7. Security Requirements Satisfied in The Proposed Protocol.
The derivation process for the proposed D2D protocol is illustrated in Figure . In the figure, the idealized messages are represented from (I1) to (I5), the assumptions from (A1) to (A11), and the goals from (G1) to (G8). Finally, the derivations are shown in the steps (D1) to (D32), where (D7), (D12), (D20), (D21), (D25), (D27), (D29), and (D32) show the derived goals corresponding to (G1) to (G8), respectively. As per the result, since all goals were derived successfully, the protocol can be considered secure against attacks that violate the security goals. Table summarizes the security requirements specified in Section 4 with the BAN-Logic derivation results.
6.2. Formal verification with Scyther
The former formal verification method has some limitations in performing validation (Boyd & Mao, Citation1993), which calls for automated verification mechanisms to compensate for the limitation and provide complete formal verification. In this section, we use the automated security verification tool called Scyther to validate the proposed protocol. In utilizing Scyther to formally analyse security schemes such as the D2D security protocol, the protocol is first converted into SPDL (Security Protocol Description Language) (Cremers & Mauw, Citation2012).
The protocol modelled in SPDL contains distinct participants/roles like UE1, UE2, DSMF, and SEAF. Each role includes different behaviour such as generating nonce, computing session keys and transporting messages. The verification codes used in this section are shown in Table , while the verification result is shown in Figure .
Table 8. The event description.
The results from both BAN-logic and Scyther show that the proposed protocol is secure against attacks that proceed by violating the security requirements set.
7. Comparative analysis of D2D protocols
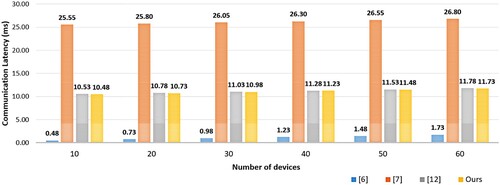
This section performs a comparative analysis of different D2D protocols concerning computational overhead and communication latency. Accordingly, we computed the overheads associated with the computation and communication for Seok et al. (Citation2020), Chow and Ma (Citation2020), Baskaran and Raja (Citation2017), and our protocol as shown in Tables and , respectively.
Table 9. Computational overhead comparison.
Table 10. Communication overhead comparison.
The computational overhead comparison indicates that all the three protocols use computationally demanding public-key operations like digital signature and verification. The protocols are designed for D2D communication over 5G, so they must be convenient for resource constrained IoT devices. Hence, by relying heavily on secure hash operations rather than public-key encryption or digital signatures, the proposed protocol enhances performance for D2D communication peers.
Notably, the proposed protocol lessens the load on the 5G core while simultaneously lowering the communication latency by adopting DSMF and issuing a ticket for each UE. In addition, the computationally lightweight characteristic of the protocol is realized through an ECDH based lightweight key exchange and 5G primary authentication-initiated trust.
The communication overhead comparison is carried out by measuring the roundtrip time required for the UEs to communicate with each other and with the 5G network. In the communication overhead analysis, η denotes the cost of performing a round trip time in a cell (the communication cost among UEs and between a UE and gNB), and δ identifies the total cost incurred due to the communication latency between a gNB and the core network. Here, we assumed that the RU and DU are collocated, and we computed η as the roundtrip time from/to UE to/from RU/DU. We also calculated δ as the sum of the roundtrip times among RU/DU, CU, and core network with this assumption. Finally, numerical values for η and δ from (Brown, Citation2018) are introduced in the formulae shown in Table .
Figure depicts the result of the communication overhead for different values of n (total number of devices). As displayed in the figure, Seok et al. (Citation2020) showed the lowest cost. However, the protocol is vulnerable to free-riding and MITM attacks (as it does not consider user authentication while negotiating the ECDH key) besides using heavy cryptographic algorithms (like digital signature signing and verification). Moreover, the remaining two protocols exhibit a higher latency, which makes our protocol preferable.
8. Conclusion
IoT has altered a broad number of application sectors, bringing substantial benefits to a diverse use case (Liang et al., Citation2020a, Citation2020b, Citation2021; Xiao et al., Citation2021; Zhang et al., Citation2021; Zheng et al., Citation2021). About D2D communications in 5G cellular networks, IoT applications can benefit significantly from decreased communication delay, enhanced computing resource usage, improved connection speed, and increased system capacity. However, to reap these benefits of D2D communication, various challenges, such as security and privacy, must be tackled. Accordingly, this paper designed a lightweight and secure D2D communication protocol that heavily relies on the trust established during the 5G primary authentication. The protocol leverages this trust to use cryptographically lighter operations, like HMAC, to secure the channel between the communicating entities. Besides, to facilitate secure communication of devices and enhance performance (especially communication latency), a new network function (DSMF) is located near the UE. We also used LSTM-based UE trust forecasting to prioritize communication requests to lessen the network load on DSMF. In addition, we provided a formal security verification of the proposed protocol against five essential security requirements (mutual authenticity, secure key exchange, confidentiality, integrity, and perfect forward secrecy) using BAN-Logic and Scyther. The anonymity of UEs, an essential privacy requirement in D2D communication, is also realized through the 5G-GUTI. The results from both formal approaches show that the protocol satisfies these security requirements. Finally, we presented a comparative analysis of our protocol against the state-of-the-art D2D security protocols concerning computational overhead and communication latency. Consequently, our protocol is found to be a better choice for computationally limited IoT devices wishing to execute a D2D communication in 5G as it is secured and efficient at the same time. While our primary focus is on resource-limited UEs, devices with no computational restrictions may still use the protocol and save time and energy while benefiting from the provably secure environment.
As part of our future work, we would like to address two critical challenges. The first one is related to how the protocol behaves when a UE is assigned with a new GUTI. New GUTI assignments can happen during the link setup and/or after a successful link setup. For the former case, a UE that received a ticket from AMF/SEAF with GUTI1 in the UE initialization phase and attempting to execute the link setup phase (particularly steps (3-3) and (3-4) in Figure ) with a freshly allocated GUTI2 would fail since the two GUTIs are different. For the latter case, even if secure communication can be achieved with the original GUTI, a UE may be assigned with a new GUTI. Hence, although the devices can still interact using the DSMF-generated key, there may be some security/privacy concerns because the original GUTI is no longer associated with the UE (or both UEs). The second point is about using actual 5G-based D2D communication data for more accurate request predictions. Furthermore, testing with and comparing different deep learning methods on such data might increase the efficiency of the present system.
Disclosure statement
No potential conflict of interest was reported by the author(s).
Additional information
Funding
Reference
- Adnan, M. H., & Ahmad Zukarnain, Z. (2020). Device-to-device communication In 5G environment: Issues, solutions, and challenges. Symmetry, 12(11), 1762. https://doi.org/10.3390/sym12111762
- Ahamad, S. S., & Khan Pathan, A.-S. (2021). A formally verified authentication protocol In secure framework for mobile healthcare during COVID-19-like pandemic. Connection Science, 33(3), 532–554. https://doi.org/10.1080/09540091.2020.1854180
- Baskaran, S. B. M., & Raja, G. (2017, December 14–16). A lightweight incognito key exchange mechanism for LTE-A assisted D2D communication. 9th International Conference on Advanced Computing (ICoAC) (pp. 301–307).
- Boyd, C., & Mao, W. (1993, May 23–27). On a limitation of BAN logic. Workshop on the Theory and Application of Cryptographic Techniques (pp. 240–247).
- Brown, G. (2018). New Transport Network Architectures for 5G RAN. White Paper. Retrieved June 29, 2021, from https://www.fujitsu.com/us/images/New-Transport-Network-Architectures-for-5G-RAN.pdf
- Burrows, M., Abadi, M., & Needham, R. M. (1989). A logic of authentication. Proceedings of the Royal Society of London. A. Mathematical and Physical Sciences, 426(1871), 233–271. https://doi.org/10.1098/rspa.1989.0125
- Caputo, D., Verderame, L., Ranieri, A., Merlo, A., & Caviglione, L. (2020). Fine-hearing google home: Why silence will not protect your privacy. Journal of Wireless Mobile Networks, Ubiquitous Computing, and Dependable Applications, 11(1), 35–53. http://doi.org/10.22667/JOWUA.2020.03.31.035
- Chow, M. C., & Ma, M. (2020, July 8–10). A lightweight D2D authentication scheme against free-riding attacks in 5G cellular network. Proceedings of the 2nd International Electronics Communication Conference (pp. 143–149).
- Cremers, C., & Mauw, S. (2012). Operational semantics. In B. David & P. Kenny (Eds.), Operational semantics and verification of security protocols (pp. 13–35). Springer.
- Cremers, C. J. F. (2008, July 7–14). The Scyther tool: Verification, falsification, and analysis of security protocols. International Conference on Computer Aided Verification (pp. 414–418).
- Dolev, D., & Yao, A. (1983). On the security of public key protocols. IEEE Transactions on Information Theory, 29(2), 198–208. https://doi.org/10.1109/TIT.1983.1056650
- Gandotra, P., Jha, R. K., & Jain, S. (2017). A survey on device-to-device (D2D) communication: Architecture and security issues. Journal of Network and Computer Applications, 78, 9–29. https://doi.org/10.1016/j.jnca.2016.11.002
- Haus, M., Waqas, M., Ding, A. Y., Li, Y., Tarkoma, S., & Ott, J. (2017). Security and privacy In device-to-device (D2D) communication: A review. IEEE Communications Surveys & Tutorials, 19(2), 1054–1079. https://doi.org/10.1109/COMST.2017.2649687
- He, D., Zhang, D., Li, Y., Liang, W., & Hsieh, M.-Y. (2021). An efficient and DoS-resilient name lookup for NDN interest forwarding. Connection Science, 33(3), 735–752. https://doi.org/10.1080/09540091.2021.1875988
- Kar, U. N., & Sanyal, D. K. (2018). An overview of device-to-device communication In cellular networks. ICT Express, 4(4), 203–208. https://doi.org/10.1016/j.icte.2017.08.002
- Kim, H. (2020). 5G core network security issues and attack classification from network protocol perspective. Journal of Internet Services and Information Security, 10(2), 1–15. http://doi.org/10.22667/JISIS.2020.05.31.001
- Liang, W., Huang, W., Long, J., Zhang, K., Li, K.-C., & Zhang, D. (2020a). Deep reinforcement learning for resource protection and real-time detection In IoT environment. IEEE Internet of Things Journal, 7(7), 6392–6401. https://doi.org/10.1109/JIOT.2020.2974281
- Liang, W., Xiao, L., Zhang, K., Tang, M., He, D., & Li, K.-C. (2021). Data fusion approach for collaborative anomaly intrusion detection in blockchain-based systems. IEEE Internet of Things Journal. http://doi.org/10.1109/JIOT.2021.3053842
- Liang, W., Zhang, D., Lei, X., Tang, M., Li, K.-C., & Zomaya, A. (2020b). Circuit copyright blockchain: Blockchain-based homomorphic encryption for IP circuit protection. IEEE Transactions on Emerging Topics in Computing, 9(3). http://doi.org/10.1109/TETC.2020.2993032
- Liu, J., Zhang, S., Kato, N., Ujikawa, H., & Suzuki, K. (2015). Device-to-device communications for enhancing quality of experience In software defined multi-tier LTE-A networks. IEEE Network, 29(4), 46–52. https://doi.org/10.1109/MNET.2015.7166190
- Liu, N., Yu, M., Zang, W., & Sandhu, R. S. (2020). Cost and effectiveness of TrustZone defense and side-channel attack on ARM platform. Journal of Wireless Mobile Networks, Ubiquitous Computing, and Dependable Applications, 11(4), 1–15. http://doi.org/10.22667/JOWUA.2020.12.31.001
- Pełka, P., & Dudek, G. (2020, July 19–24). Pattern-based long short-term memory for mid-term electrical load forecasting. International Joint Conference on Neural Networks (IJCNN) (pp. 1–8).
- Schafer, B., & Edwards, L. (2017). “I spy, with my little sensor”: fair data handling practices for robots between privacy, copyright and security. Connection Science, 29(3), 200–209. https://doi.org/10.1080/09540091.2017.1318356
- Seok, B., Sicato, J. C. S., Erzhena, T., Xuan, C., Pan, Y., & Park, J. H. (2020). Secure D2D communication for 5G IoT network based on lightweight cryptography. Applied Sciences, 10(1), 217. https://doi.org/10.3390/app10010217
- Shang, Z., Ma, M., & Li, X. (2019, December 9–13). A certificateless authentication protocol for D2D group communications in 5G cellular networks. IEEE Global Communications Conference (GLOBECOM) (pp. 1–7).
- Shang, Z., Ma, M., & Li, X. (2020). A secure group-oriented device-to-device authentication protocol for 5G wireless networks. IEEE Transactions on Wireless Communications, 19(11), 7021–7032. https://doi.org/10.1109/TWC.2020.3007702
- TS23.501, 3GPP. (2021). Technical specification group services and system aspects; system architecture for the 5G system; (Release 16). In 3rd Generation Partnership Project (3GPP): Vol. 16.9.0 (pp. 1–454). 3GPP TS.
- TS33.501, 3GPP. (2021). 5G; Security architecture and procedures for 5G System; (Release 16). In 3rd Generation Partnership Project (3GPP): Vol. 16.7.1 (pp. 1–259). 3GPP TS.
- Uchida, N., Sato, G., & Shibata, Y. (2019). Device-to-device communication based DTN for disaster information system by using emergent user policy and locational information. Journal of Internet Services and Information Security, 9(3), 41–51. http://doi.org/10.22667/JISIS.2019.08.31.041
- Wang, L., Liu, J., Chen, M., Gui, G., & Sari, H. (2018). Optimization-based access assignment scheme for physical-layer security In D2D communications underlaying a cellular network. IEEE Transactions on Vehicular Technology, 67(7), 5766–5777. https://doi.org/10.1109/TVT.2017.2789022
- Wong, S. K., & Yiu, S.-M. (2020). Location spoofing attack detection with pre-installed sensors In mobile devices. Journal of Wireless Mobile Networks, Ubiquitous Computing, and Dependable Applications, 11(4), 16–30. http://doi.org/10.22667/JOWUA.2020.12.31.016
- Xiao, L., Xie, S., Han, D., Liang, W., Guo, J., & Chou, W.-K. (2021). A lightweight authentication scheme for telecare medical information system. Connection Science, 33(3), 1–17. https://doi.org/10.1080/09540091.2021.1889976
- Zhang, A., & Lin, X. (2017). Security-aware and privacy-preserving D2D communications In 5G. IEEE Network, 31(4), 70–77. https://doi.org/10.1109/MNET.2017.1600290
- Zhang, J., Cheng, Z., Cheng, X., & Chen, B. (2021). OAC-HAS: Outsourced access control with hidden access structures In fog-enhanced IoT systems. Connection Science, 33(4), 1060–1076. https://doi.org/10.1080/09540091.2020.1841096
- Zhang, S., Wang, Y., & Zhou, W. (2019). Towards secure 5G networks: A survey. Computer Networks, 162, 106871. https://doi.org/10.1016/j.comnet.2019.106871
- Zheng, Z., Zhou, Y., Sun, Y., Wang, Z., Liu, B., & Li, K. (2021). Applications of federated learning in smart cities: Recent advances, taxonomy, and open challenges. Connection Science. https://doi.org/10.1080/09540091.2021.1936455
- Zhou, J., Xu, Y., & Li, X. (2011). A security mechanism for RFID with dependable proxy. Intelligent Automation & Soft Computing, 17(6), 815–825. https://doi.org/10.1080/10798587.2011.10643190