?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.Abstract
Nowadays, broadband wireless networks and 5G have improvements in the quality and dependability of network services for high-speed mobile vehicles. Within an open communication environment on the Internet of vehicles named IoV, personal details will be revealed on the Wi-Fi network. Considering information security and privacy, this research concentrates on how to protect secure information transmission in real time through IoV, and also wants to avoid illegal vehicles, passers-by or drivers from joining connection and planting or altering significant data. This research provides a multilevel security infrastructure with M-tree based elliptic curve digital signature algorithm (ECDSA) for securing data transmission in both IoV and cloud environments. While transmitting, this study provides several flexible and scalable schemes to manage security issues, which dynamically adjust the framework depending on the rapidly changing IoV topology and speed up the time to synchronise the reconstruction of the system key, and decrease the quantity of phases to resynchronise the system key. Moreover, most research of key management without secure data transmission, we integrate the M-tree key management with secure data transmission to achieve the secure IoV. Simultaneously, the provided key management for the multi-level security is quite appropriate to adaptable and expandable IoV.
KEYWORDS:
1. Introduction
As the Internet of vehicles becomes popular and intelligent, vehicles can establish a connection with more open devices, and thereby the security issues are created. Nowadays, IoV attracts great attention to researchers. Because the IoV may communicate with vehicles, roadside equipment and even cloud services mutually. For the foreseeable future, IoV is going to carry out a big data application and analysis on cloud computing. Simultaneously, the V2X technologies will be employed to strengthen driving safety. Those are vehicles to infrastructure named V2I, vehicles to roadside equipment named V2R, vehicles to vehicles named V2V, vehicles to pedestrians named V2P, vehicles to transportation named V2T, and vehicles to groups named V2G and vehicles to networks named V2N. In particular, V2V is gradually becoming more and more popular. Currently, IEEE would like to propose the security and communication framework named IEEE1609/802.11P.
Nowadays, many countries are continually investing in autopilot and driverless vehicle research. The 5G is going to encourage us to evolve into the leading driving technology for autopilot and driverless vehicles. IoV is a mass-connected network, which integrates the necessary information like vehicle speed, route and location. The vehicle can supplement the collection of its own information about the status and environmental information through sensors, GPS, radars, cameras and image processing devices. Thanks to cloud computing technology, diverse IoV information transmissions are combined with each computer in a vehicle to measure, analyze and process a vast quantity of data. Afterwards, the vehicles find the best path or the possible path, and report the status of the road condition to the control centre immediately. The monitoring system may programme the traffic signal cycle, depending on the real-time traffic conditions to reduce the traffic bottleneck.
The premature phase of vehicle to everything (V2X) counts on typical wireless transmission and adopts a similar technique with Wi-Fi networks, yet its dependability is weak and undefended to intrusion and interference offences. So far, with the progressive popularity of 5G being developed, lots of countries are working towards the development of 5G technology. Thus, the original IoV concept is gradually being changed to the IoV application. In the foreseeable future, 5G is going to definitely offer reliable and efficient V2X services. Meanwhile, except for communicating with one another, the vehicle may also deliver messages via roadside devices and adopt IoV to identify unusual car accidents. In the event of an accident, short-range communication may be initiated. It stores information about accidents or scene information and delivers the videos or accident details to the platform of cloud services. Afterwards, V2X may assist in the completion of accident summary for the vehicle and in restoring the location of the traffic accident at which the accident occurred, such as the precise GPS particulars of the vehicle, the position of the roadside devices, and travel routes and journey information of the vehicle with pictures to examine the behaviour of drivers before car accidents.
Nevertheless, since the IoV open communication surroundings, within an open Internet of vehicle communication environment, personal details are going to be revealed on the Wi-Fi network. Taking into account information security, privacy, the security of information as well as the protection of personal data, the purpose of this study is to safeguard transmitted information in real time and to avoid unauthorised vehicles, drivers or passers-by from being involved in the communication and implementation or modification of critical transmitted information. This study develops a virtual machine on the cloud service platform that comprises services such as key management, identity verification, security certification, the public key infrastructure PKI and the certification authority (CA) server. At the border entrance, the cloud service category manager (CSCM) takes charge of transmitting the type of service required from the vehicles to the end of the cloud service platform, and thoroughly analyzing and dealing with a variety of messages coming from vehicles and RSU.
Moreover, this research must examine how to guarantee security between the vehicle with vehicle (V2V), the vehicle with roadside equipment (V2R), the vehicle with group (V2G) and the vehicle messages with the cloud service platform, as the vehicle moves and communicates with the RSU using the sensor of the onboard OBU. In short, IoV requires a secure data communication framework to guarantee the information security delivered among OBU, RSU and the cloud service platform. This research also takes into consideration that the IoV infrastructure and topology are changing so rapidly, when the vehicle is involved or deviating from the secure transmission of the IoV. Besides, the connected route can change, and vehicles can be connected to various base stations. As a result, this study needs to offer a secure key management mechanism that can address dynamic change in topology. Moreover, the proposed scheme involves multiple paths and can be made quickly and effectively to process the secure transmission of data in IoV, when there is a proactive change in the IoV topology. As a result, based on dynamic M-tree structures, this research provides a multi-level security key management protocol for IoV with secure data transmission to address IoV weaknesses in key management and security problems. This will improve the information security of IoV.
The rest of this paper is structured as follows. Section 2 introduces the related work. Section 3 presents the process of ECDSA digital signature of IoV. Section 4 introduces the framework of multi-level security. Section 5 describes the security key management agreement based on M-tree and secure data transmission modes. Section 6 is the analysis of security and performance. Eventually, conclusions and further work are derived from Section 7.
2. Related work
Over the past few years, lightweight security mechanisms, including PUF-based authentication (Zhang et al., Citation2021) and elliptic curve Diffie–Hellman protocol, have been adopted to various application domains, such as medical information systems (Xiao et al., Citation2021), wireless sensor networks (Hua, Citation2021; Lin et al., Citation2016) and smart environments (Xia et al., Citation2021).
Due to the unique characteristics of vehicular networks, restricted computing resources and unstable communication, security issues in IoV applications tend to be performed by lightweight cryptographic schemes. Not only authentication, but also key operations possibly related to key agreement (Xu et al., Citation2021), key management (Hua et al., Citation2021; Zhang et al., Citation2021) and key distribution (Vijayakumar et al., Citation2017) protocols are concerned in these issues. Further, wireless high-frequency transmission by 5G (Hu et al., Citation2021) or 6G technology (Pandi et al., Citation2022) will support higher capacity and much lower latency for data transmission of IoV and VoX applications.
IoV is considered a mission-critical infrastructure. Vehicles aggregate real-time data with other vehicles, RSU and cloud servers, and transmit aggregated data to OBU. IoV data can be analyzed either locally or on a cloud server, and actions are taken depending on the request type. Because IoV has wide-scale interconnecting networks with a large number of vehicles. Obviously, there exists a great risk of privacy and security issues. Through the encryption mechanism and digital signature cryptographic protocols can address those concerns. Additionally, the simultaneous need for the encryption mechanism and the digital signature, these mechanisms are amalgamated named signcryption. In order to eliminate the issue of key escrow related to the signcryption, a certificateless approach is generally considered.
In 2007, Xiaodong et al. exploited a group signature to inspect multiple signatures (Xiaodong et al., Citation2007; Yong et al., Citation2013), and thus improved the efficiency of authentication. The proposed scheme is based on bilinear paring. However, this mechanism exists a serious defect that the paring operations at least need two members to complete and cannot be extended, and therefore this proposed mechanism is not scalable for IoV. Additionally, this mechanism exploits lots of exponential operations that consume computing power and increase the complexity of operation.
In 2007, Raya et al. proposed the LAB scheme (Maxim & Jean, Citation2007). Initially, this mechanism places every OBU in abundance of private keys and their correlative anonymous certifications within a pool with 43,800 certificates. Then, a vehicle arbitrarily chooses one of its anonymous certifications and adopts its corresponding private key to sign the transmitted data. The receiver adopts the public key of the sender with the anonymous certificate to verify the source data. Those anonymous certificates are used to replace the identity of the vehicles. Every certificate only exists for a short period of time to match the privacy requirement of the vehicle. Although, the proposed LAB scheme achieves the purpose of the supposed privacy requirement, this mechanism needs to maintain quite a huge number of certificates and the identities of authority for all vehicles, and therefore becomes inefficient and not scalable for a large number of IoVs.
In 2013, Hu et al. provided a privacy-preserving scheme for vehicle Ad Hoc networks using group signature protocol (Citation2013). In this study, each vehicle keeps secret keys and public keys to avoid disclosing its identity. Nevertheless, as the increasing quantity of vehicles in the revocation list increases, the consuming time of completing group signature also increases linearly. In other words, this proposed scheme consumes lots of extra time.
In 2018, Nisha et al. provided a scheme to ensure the security of vehicles using the blockchain mechanism (Ali et al., Citation2019; Kulathunge & Dayarathna, Citation2019; Nisha et al., Citation2018). At the same time, Ali et al. exploited a certificateless signature to prove the integrity of transmitted data in IoV, and used a blockchain to store the identity of authorised vehicles and also adopted other blockchain to store unauthorised or revoked vehicles.
In 2015, Xiaodong et al. proposed a security protocol named GSIS for VANETs, which combines group signature with identity-based signature to achieve privacy-preserving (Hong et al., Citation2016; Xiaodong & Rongxing, Citation2015). This study exploits group signature to protect the communication between multiple OBUs, where the transmitted data are anonymously signed by the sender, meanwhile, the authorities can recover the identities of senders. Additionally, RSUs adopt identity-based cryptography to sign the transmitted data from RSUs, and make sure the authenticity of RSUs. Since the identity is implied in RSUs, and therefore can reduce the great overhead of signatures.
2020 Joon et al. proposed a secure key and authentication agreement to conquer the security issue in IoV (Citation2020). This study only exploits XOR operations and hash functions to achieve this agreement. In this study, vehicles and RSUs register at the TA (Trusted Authentication) server and perform the secure key protocol instead of a tamper-proof device TPD. Afterwards, vehicles use the session key to encode and decode the transmitted data to RSUs. After receiving the transmitted data, RSUs inspect the received data and forward them to the cloud platform.
In 2021, Insaf et al. proposed an anonymous certificate encryption scheme for IoV on the basis of the Hyper elliptic Curve (HEC) (Citation2021). This given system ensures an official analysis of security as part of the Random Oracle Model (ROM) for confidence, affordability, and anonymous receiver. Additionally, the proposed certificateless cryptography mechanism avoids the issue of key escrow problem and guarantees the anonymity of the receiver in open wireless channels. However, this scheme without the capability to allocate partial private key on an open channel, and thus needs a secure channel to share partial private key with vehicles in IoV environments.
In 2021, Mu et al. proposed an efficient secure attribute-based encryption system for IoV using association rules (Citation2021). This study adopts the features of frequency between vehicle nodes through the max-miner association rules algorithm, and aims to construct frequent item sets and carry out secure communication in vehicle nodes belonging to the same classification set. In this scheme, only ECUs that meet the ciphertext requirements can decipher the data, ensuring data confidentiality while reducing the risk of attacks on the in-vehicle network. However, the access frequency features cannot report the real situation, if an outsider vehicle joins this network and would like to communicate with the group will be turned down.
The IoV system is susceptible to various security and privacy hazards. Although the above methods provide signcryption, authentication or encryption of data for IoVs networks, all of the aforementioned methodologies are based on complex cryptographic mechanisms and bilinear pairing, and all of them have high calculation and communication costs and are incompatible with IoV environments. In other words, they also suffer from the problems of complicated operations, scalability and consume lots of computing time. Therefore, a light security system is needed to ensure protection from a variety of known and unknown threats. This study would like to propose a high efficiency, flexible and scalable mechanism to deal with the security transmissions in IoV.
3. The process of ECDSA digital signature of IoV
As the IoV computer has limited computing resources, this research surveys numerous conventional signature algorithms. We find that the elliptic curve signature (ECDSA) possesses the benefits of rapid rate, strong and small signature. Besides, the ECDSA usage has become increasingly widespread. The functionality of the ECDSA resembles many algorithms of signature (Yasin & Erkan, Citation2021). It exploits a private key to sign the message and using a public key to inspect the signature. Moreover, the ECDSA operation mode is similar to the other cryptographic schemes, but the key of ECDSA is retained in CNG (cryptography API: next generation). Through CNG, this study is able to securely maintain key pairs, public keys and refer to them utilising simple string names.
Moreover, compared ECDSA to RSA (Ron Rivest, Shamir, Adleman), this study observes that ECDSA utilises a smaller key length to reach a similar level of RSA security, even though ECDSA requires complex implementing methods. The theoretical foundation for ECDSA is to resolve the problem of discrete logarithm of the elliptic curve named ECDLP (Shoma et al., Citation2015). Nevertheless, the benefits of RSA are convenient to implement and also can be used for encrypting and deciphering simultaneously. Moreover, RSA is slower and the length of the signature is significantly longer, and the theoretical foundation for RSA is to handle the factoring of very large integers. A comparison between ECDSA and RSA can be found in Table (Dhanashree et al., Citation2018; Nils et al., Citation2004).
Table 1. Comparing ECDSA to RSA.
Taking into account the current phase, the sensing device took along by the vehicle’s OBU generally has no strong computer power. This research primarily concentrates on the IoV surroundings and presents a cryptographic signature protocol using an elliptic curve and a mechanism for transmitting information security. Therefore, we adopt the ECDH (elliptic curve Diffie-Hellman) key exchange protocol to carry out our key management mechanism and secure data transmission among V2V, V2R and V2G. As ECDH replaces exponential with multiplication and addition (Ram & Manoj, Citation2013), it uses less necessary memory to the OBU sensors, minimises intricate encrypting and deciphering calculations for the CPU, and ensures a rapid and effective transmission of information security. In addition, the study suggests that vehicles must also communicate with at the end of cloud service platforms, and as a result, this study utilises ECDSA to guarantee the secure data transmission of IoV to cloud platforms, and thus obtain the fully secure IoV architecture.
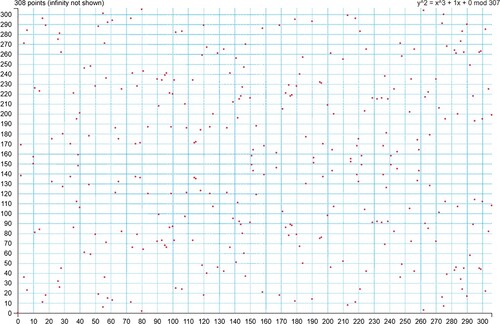
Furthermore, in practical environments, this study should combine the elliptic curve cryptographic system with the OBU sensors and RSU roadside equipment. Taking into account the need for deployment, we first choose a GF(p) finite field, and estimate the quantity of OBUs and the roadside device. Therefore, this study selects a proper elliptic curve y2 = x3 + ax + b mod p, where a = 1, b = 1, p = 307 in F307, for instance, the following elliptic curve y 2 = x 3 + x + 1 mod 307, where p is a prime and G is the elliptic curve Ep (a, b) generator point. The selected elliptic curve conforms to the next qualifications (Daisy et al., Citation2015): (1) n is a prime and the G order; (2) yG2 = xG3 + axG + b mod p; (3) nG = 0 and n < p. Thanks to this elliptical curve, this survey generates a total of 307 points, as illustrated by Figure . Moreover, taking into consideration the quantity of vehicle OBUs and roadside devices, this study allows the elliptic curve and coefficients to be flexibly adjusted and expanded to generate the deployed points required to fit the needs of vehicles and roadside devices.
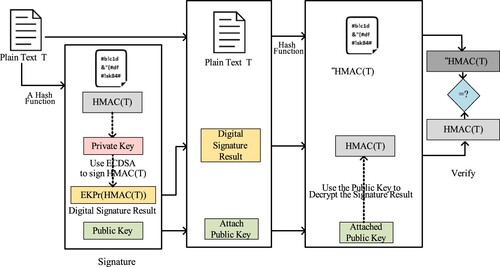
ECDSA is comprised of ECC (Amit et al., Citation2016; Zhe et al., Citation2017) and DSA. The whole process of signing, as shown in Table and Figure , is comparable to DSA. However, the obvious distinction during the signing is the algorithm, which utilises ECC to perform the signature. Afterwards, this study obtains the final result of the signature being divided into (r, s). The process for signing is the following.
Table 2. Sender and receiver perform ECDSA signature process.
4. The framework of a multi-level security
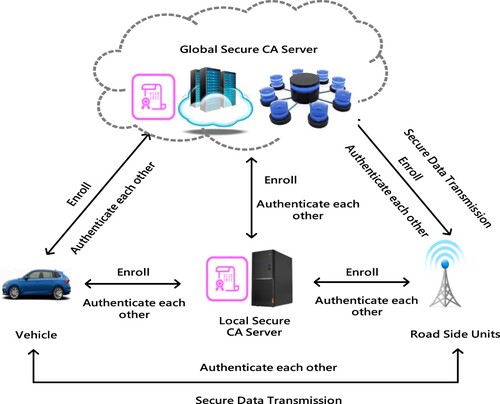
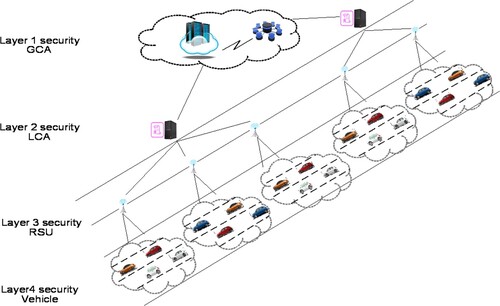
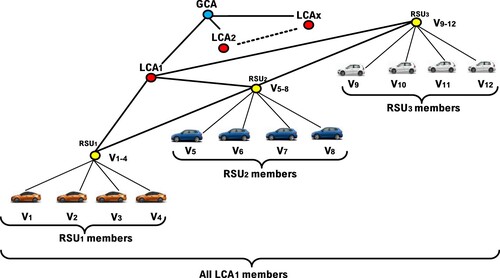
As IoV needs to integrate vehicles, roadside devices and cloud service servers. As a result, each security level is considered similar to the hierarchical authorisation of companies, and each security level has individual duties and is responsible for its own security task. The main purpose of this study is to propose a mechanism of the key management of the multi-level security for IoV via an M-tree framework. Because each vehicle is deployed at the lowest level of the key management scheme, then this study maps the leaf node to a vehicle on layer 4 on the security level. Additionally, RSUs are in charge of gathering the data delivered from the OBUs of the vehicle. This study places the RSUs in layer 3 of the security level, and the LCA (local certificate authority CA) in layer 2. The GCA (global CA) and cloud server correspond to the top level on layer 1 of the security level.
This research also takes into account detection devices of OBU that the vehicles carried at this stage generally have no sufficient computing resources. Here, many vehicles are split into multiple groups, and a group is considered a key management unit. Consequently, we can effectively lower the time complexity of updating and synchronising keys of the entire system, and exploit the ECDH (Elliptic Curve Diffie-Hellman) key interchange protocol to exchange keys, manage and en/decipher data to guarantee the secure data transmission between V2V, V2R and V2G. Besides, because the topology of the IoV is changing quite fast, we must also take into account the management of updating and synchronising keys for IoV.
Consequently, the main purpose of this study is to provide a key management agreement based on a multi-level security framework to combine the elliptic curve cryptosystem with IoV and cloud service platforms (Sathishkumar & Rajakumar, Citation2017). As V2V or V2R equipment executes secure data transmission, this study employs the ECDH session key to perform the secure data transmission for point-to-point. While the communication is between a vehicle and the group vehicle V2G, this research employs the group key management mechanism to compute a common group key for protecting the security of transmitted data. Additionally, this study deploys a VM virtual machine server at the end of the cloud to serve as the root base station GCA, which is an administrator of the entire system and is responsible for the key management agreement.
Moreover, this study deploys a secure LCA in the V2G communication environment to server as the local group leader. LCA is responsible for the key exchange protocol of ECDH, and updating and synchronising the group key. In other words, LCA is the leader of local RSUs, and takes charge of the local group key management and synchronisation.
Figure depicts the authority framework. Initially, a deployed trusted and secure GCA server is located in this entire system. GCA takes in charge of the issuance of key pairs and the digital certificate. If a vehicle wants to take part in this system, the aforementioned information needs to be applied to GCA. Additionally, OBU, RSU or related devices have to be embedded in the ECC cryptosystem.
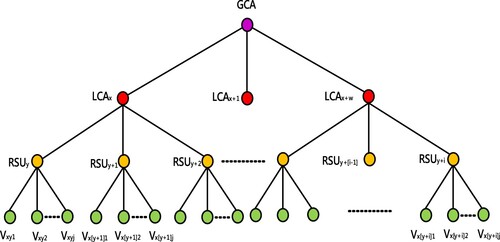
Afterwards, this study proposes a M-tree framework, as illustrated by Figures and , to map IoV equipment to the related security level. The lowest level represents the vehicle. Because the vehicle serves as the role of sender and receiver during the secure data transmission. Additionally, the roadside device RSU serves as a mediator role, and RSUs are located on level 3 of M-tree, since the vehicle transmits data through the RSU to other vehicles or to the cloud service control manager CSCM and GCA, which gathers all delivered data from vehicles, and this study arranges the CSCM and GCA on level 1. Eventually, we employ an M-tree with multiple degrees to correlate the whole system of the key management of the multi-level security, and thus our presented scheme can efficiently address the dynamic key management.
In this presented research, this study divides M-tree into several groups as the group key management unit. Then, we compute the session key of every leaf node located at the lowest layer, and upward deliver the session key along the route of its ancestor node. Afterwards, the computation of the ancestor node RSU, we can gain the partial group key of level 3 and subsequently forwards it to upper LCA. Eventually, all LCAs perform a similar process and upload the partial group key result to GCA. Consequently, GCA gathers all coming from partial group keys, and eventually calculates the whole IoV system key. In the same way, when an RSU located in level 3 departs, only the replaced RSU passes upwards along its ancestor node to recompute the newer partial group key, subsequently transmits it to LCA and LCA can instantly figure out the newer partial group key, and then forward the newer result to GCA located on the top level. Finally, the whole system comes back to regularity and gains the new system key. Therefore, the proposed scheme indeed accelerates the performance of key resynchronisation. When GCA at the top level collapses, the substituted GCA just needs to gather each LCA’s key to quickly restore the whole system key. Figure depicts the M-tree framework of LCA. The entire system consists of the following elements.
Certificate Authority: CA has constant power and plenty of computing and storage resources. It is the secure trusted centre of IoV and is responsible for issuing digital certificates for RSUs, OBUs and vehicles. In this study, we divide CA into GCA (Global CA) and LCA (Local CA). GCA is in charge of the secure trusted centre of the entire IoV, and LCA is in charge of the secure trusted centre of the local area. They serve registration and revocation of certification, and also key management in IoV. Additionally, LCAs also issue the public and private key pairs of OBUs and RSUs, and maintain the identity of OBUs and RSUs.
Road Side Unit: RSU is an equipment located along the roadside, and serves as the middle device to forward information from OBUs to LCA. Therefore, while transmitting information to RSU, we should consider the security issue. The main tasks of RSUs are to (1) forward an encrypted message form OBUs, and (2) assist LCA to efficiently verify the real identity of OBU. Additionally, RSUs need the authorisation of LCA and GCA. Besides, RSUs will not reveal any transmitted messages. Here, this study assumes that RSU is strongly secure and cannot be compromised. At the same time, RSU cannot sign delivered messages in the name of either OBU or LCA. Unlike vehicles, this study assumes that RSUs have no computational, energy and capacity constraints. Therefore, RSUs are able to serve as mediators to transfer messages from OBUs.
On-Board Unit: OBU is a device installed on vehicles, which has to be registered to GCA with certificates, key pairs and public system parameters before joining IoV. Additionally, OBU can communicate with RSUs via wireless communications and generates the necessity for a tamper-proof device in each vehicle. OBU can perform signature, encryption, decryption, and security operations. When the OBUs of vehicles are on the road, they steadily broadcast information periodically, including position, current time, traffic, speed, direction, accident events, etc. The above information will be processed, aggregated and delivered to the drivers and cloud platform via RSUs.
5. The M-tree based key management with multi-modes secure data transmission
This section utterly discusses the main purpose of our presented the key management agreement of the multi-level security. First of all, GLA uses the elliptic curve cryptosystem to produce several key pair sets. Subsequently, this study embeds the key pair into the OBU of the joining vehicle, and divides vehicles into several groups. Moreover, this study employs the ECDH key agreement to produce session keys between the vehicles depending on the M-tree degree. Afterwards, vehicles deliver the produced session key to its own upper RSU located at level 3. Similarly, the RSU produces the session key between RSUs utilising the ECDH key agreement depending on the M-tree degree, and then delivers the produced session key to its upper LCA. The following describes the process in detail.
In the beginning, the whole system had a prime generator known as the base point P of the Diffie–Hellman agreement. Additionally, each vehicle randomly chooses its individual private key Vx utilising the ECC cryptosystem to produce a correlated public key Px, and Px = VxP. Consequently, we combine the private key Vx with the public key Px as a pair (Vx, Px) for vehicle X. In the same way, (Vy, Py) represents the key pair of the vehicle Y. Within the proposed multilevel security scheme, the leaf node is the same as the vehicle owning a key pair. In the presented system, this research supposes the neighbouring vehicle V1 and the vehicle V2 are located at level 4 with key pairs (V1, P1) and (V2, P2), respectively. Then V1 and V2 employ ECDH to compute the common session key S = V1V2P for both vehicles, and P is the ECDH generator. Afterwards, both vehicles upward send S to their same ancestor node RSU located at level 3. For briefness, this study illustrates a binary tree. V1 and V2 are located at the lowest level as leaf nodes, and both vehicles can infer the same session key V1V2P for V1 and V2. Similarly, V3 and V4 gain the same session key V3V4P. Subsequently, V1 and V2 upward send V1V2P upward to their common ancestor node RSU1. Afterwards, V3 and V4 upward send the session key V3V4P to their common ancestor nodes RSU 2. Since RSU 1, RSU 2, RSU 3 … RSUz are all located at level 3, after similar processes referred to above, then RSU1 and RSU2 together compute the common session key RSU1RSU2P = V1V2V3V4P. Subsequently, RSU1 and RSU2 respectively upward deliver their common session key to their ancestor node LCA. After receiving it, LCA obtains V1V2V3V4P. In the same way, if there exist other LCAs, they perform the above process and upward to their parent node GCA. Consequently, GCA figures out the system key V1V2V3V4 … VzP, and Z indicates the final vehicle. Because this scheme just utilises addition and multiplication instead of exponential operations, therefore this mechanism saves a significant amount of computing resources.
Moreover, this study takes into account when the vehicle or RSU takes apart from IoV. We have to recalculate the whole system key. However, this study provides a very efficient way to deal with the reorganisation of the system key. This system only needs to recalculate from the level of the departing node along the upward route to the GCA node. At last, the IoV network gains the newer system key. Besides, the necessity of the whole process takes just LogmN stages, where m stands for the M-tree degree and LogmN stands for the M-tree height. Generally, since this study employs ECDH, the benefit is that we almost ignore the M-tree degree, the vehicle just transmits the ViP value to its ancestor RSU depending on the route from its parent node LCA to GCA, and this mechanism rapidly and efficiently gains the system key. Additionally, our multi-level security mechanism may also offer various managements of various levels and protect devices using different security levels. For instance, before deployment, RSUs need more verification and security. However, we cannot request to equip with ECC key pairs in each vehicle’s OBUs, and therefore give more loose restrictions on vehicles. In addition, LCA, GCA, CSCM and cloud servers must pass multiple strict authentication to take part in IoV. Consequently, the presented system is exactly like the hierarchical concept in an enterprise or in an army, and there are various levels with various security permissions.
Moreover, taking into account the rapid changing of topology and the quantity of vehicles in IoV, the proposed mechanism quickly transforms the multi-level security framework into a dynamic framework of M-tree. These include an RSU that can be connected to at most M-1 vehicles. It is known as an M-tree with M order, and 2 ≤ the degree of nodes ≤M. The M-tree possesses the below features.
The degree of the root node is at least 2 degrees.
The M-tree conforms to an M-way search tree.
The bottom level places the leaf node.
The M-tree satisfies ⌈M/2⌉ ≤ the degree of other nodes ≤M, with the exception of root and leaf nodes.
Consequently, the following is that we infer the quantity of members for an M-tree. The full M-tree has the maximum members M0+ M 1+ M 2+ … M h−1, and the M-tree height is h.
(1)
(1) The binary tree named B-tree with degree two is the M-tree’s special case, which has the minimum members 1 + 2(r0 + r1 + r2+ … rh−2), and r equals ⌈M/2⌉, and the B-tree height is h.
1 + 2(r0 + r1 + r2+ … rh−2)
(2)
(2)
According to the aforementioned inference, we can immediately change the M-tree degree dynamically, depending on the quantity of vehicles to meet the scalability of the practical vehicle environment. Because this research employs the more flexible, scalable and expandable ECC cryptosystem (Jia et al., Citation2019; Kuljeet et al., Citation2019), which is also more efficient. The study describes the steps of the proposed multi-level security as follows.
Step1. The identity of every vehicle is Vi with a key pair represented (Vi, Pi). Subsequently, Vi figures out ViP as its public key, where P is a generator of ECC.
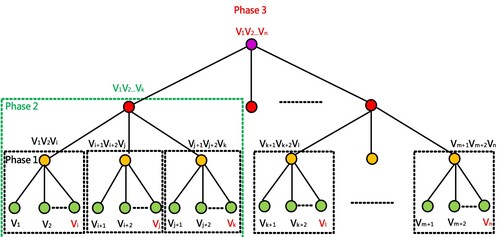
Step2. Depending on the algorithm of M-tree, we suppose that the M-tree degree is 3. Figure and Table describe the M-tree structure and notation, respectively. Here, this research illustrates a 3-way tree to present Vxy1, Vxy2 and Vxy3 cooperatively computing the common session key Vxy1Vxy2Vxy3P. For simplicity, this study denotes Vxy1Vxy2Vxy3P as Vxy1-3P, and subsequently delivers RSUy with the computed session key. Similarly, the following result indicates that this study repeats the alike procedure and infers the session key.
(3)
(3)
(4)
(4)
(5)
(5)
(6)
(6)
Table 3. The usage of notations in secure data transmission.
Step3. Finally, on the cloud service platform, GCA is going to gain all the session keys coming from LCAx, LCAx+1, … , LCAx+w. Subsequently, GCA computes the whole system key = Vxy1Vxy2Vxy3 … Vx[y+i]jP through ECDH operations, according to the equations (1)∼(6).
Following these steps above, then every vehicle, RSU, LCA and GCA can utilise the same system key to encipher and decipher the transmitteVSPd data, and thus complete the secure data transmission of IoV.
5.1. The algorithm of secure data transmission
Initial phase:
Each RSU computes the local group key according to the M-tree structure of ECCDH.
Execution phase:
At the beginning, the source vehicle Vxyi determines whether the destination vehicle Vwzj belongs to the same LCAx group.
Perform x & w operations.
If x = w, then the source vehicle Vxyi and the destination vehicle Vwzj belong to the same LCAx authority, and then perform y & z operation.
{If y = z, then the source vehicle Vxyi and the destination vehicle Vwzj belong to the same RSUy authority. Subsequently, Vxyi and Vwzj perform secure data transmission using the group key of RSUx to ensure security.
Else Vxyi and Vwzj belong to the same LCAx but belong to the different RSU. Then RSUy and RSUz exploit LCAx to perform the group exchange agreement via ECDH to achieve the same group key of LCAx for the future secure data transmission of Vxyi and Vwzj.
}
Else the source vehicle Vxyi and the destination vehicle Vwzj belong to the different LCAx authority and RSU authority, then RSUy and RSUz exploit ECDSA signature agreement to perform the secure data transmission.
5.2. Secure data transmission modes
For increasing the efficiency of secure data transmission, this study proposes the group key mode and the ECDSA mode to deal with different scenarios. The group key mode accelerates the speed of secure communication once the members obtain the same group key. Only the vehicle owns the same group key that can take part in the communication. Others cannot take part in secure communication without the group key. Nevertheless, the ECDSA mode gives an optional way to achieve secure data transmission. When the members of IoV are abundant and huge, the time complexity of obtaining the system key takes longer time. The member can exploit the ECDSA mode to deal with secure data transmission, since the member has already owned the certificate, and thus the vehicle can sign the transmitted data to protect the transmitted data. The detailed presentation is as follows.
The secure data transmission of IoV belongs to the same RSU authority: the group key agreement via RSU
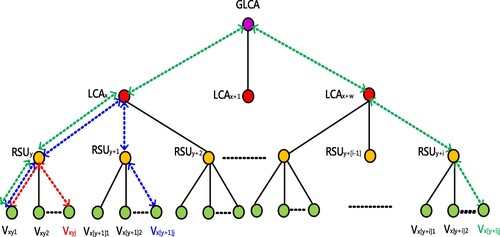
When the source vehicle Vxy1 and destination Vxyi are located in the same RSUy, as shown in the red dot line of Figure , and therefore they adopt the group key of RSUy for the secure communication of all members. Initially, both vehicles perform ECDH cryptography agreement. For simplicity, here illustrates a B-tree structure. Vxy1 and Vxy2 execute the ECDH agreement and obtain the common session key Vxy1Vxy2*P, Vxy3 and Vxy4 obtain the common session key Vxy3Vxy4*P, the remaining vehicle Vxyi execute the same operation and forwards its key to RSUy, and then RSUy calculates the common group key for GKRSUy = Vxy1Vxy2Vxy3Vxy4 … Vxyj*P. Subsequently, if Vxy1 would like to deliver the data to Vxyj, the detailed secure procedure is as follows.
Initially, Vxy1 adopts the hash function to calculate HMAC(DVxy1), and then enciphers the aggregations of ToS, TS, the routing path, original data and HMAC(DVxy1) via the group key RSUy. Subsequently, Vxy1 sends the enciphered result to RSUy.
Once the enciphered data are received, RSUy deciphers the received data utilising the group key RSUy. Subsequently, RSUy performs the hash function on the original data DVxy1, and verifies if it equals to the received HMAC(DVxy1). If there is a difference, it means during the transmission, the data are tampered with other vehicles. Otherwise, RSUy puts its ID into the routing path (IDVxy1IDRSUy), and then enciphers the merged data of ToS, TS, the rouging path, the original data (DVxy1|DRSUy) and its HMAC(DVxy1|DRSUy) via the group key of RSUy. Eventually, RSUy sends the enciphered result to Vxyj.
After receiving the enciphered data, Vxyj deciphers them using the group key of RSUy, and verifies the integrity of HMAC(DVxy1|DRSUy). If the HMAC is correct, then the secure data transmission is complete.
The secure data transmission of IoV belongs to the same LCA and different RSU: the group key agreement via LCA
When the source vehicle Vxy1 and destination Vx(y+1)j are located in the different RSU, but in the same LCAx, as shown in the blue dot line of Figure . In this situation, this study has to perform the group key exchange operation to achieve the new group key for LCA. In the beginning, RSUy obtains its group key GKRSUy = Vxy1Vxy2 … Vxyj*P using the ECDH agreement, and RSUy+1 obtains its group key GKRSUy+1 = Vx(y+1)1Vx(y+1)2 … Vx(y+1)j*P. Subsequently, RSUy and RSUy+1 individually forward their group key to LCAx. After receiving, LCAx performs the group key exchange operations and obtains the newer group key GKLCAx = GKRSUy * GKRSUy+1 = Vxy1Vxy2 … VxyjVx(y+1)1Vx(y+1)2 … Vx(y+1)j*P. Additionally, this study employs the common group key GKLCAx to execute the secure data transmission from Vxy1 to Vx(y+1)j as follows.
At the beginning, Vxy1 adopts the hash function to calculate HMAC(DVxy1), and then enciphers the merged data of ToS, TS, the rouging path, the original data and HMAC via the group key GKLCAx. Subsequently, Vxy1 sends the enciphered result to RSUy.
Once the enciphered data are received, RSUy deciphers the received data with the group key GKLCAx. Subsequently, RSUy performs the hash function on the original data DVxy1, and verifies if it equals to the received HMAC(DVxy1). If there is a difference, it means during the transmission, the data are tampered with other vehicles. Otherwise, RSUy put its ID into the routing path (IDVxy1IDRSUy), and then enciphers the merged data of ToS, TS, the rouging path, the original data (DVxy1|DRSUy) and its HMAC(DVxy1|DRSUy) via the group key GKLCAx. Eventually, RSUy forwards the enciphered result to LCAx.
Once the enciphered data are received, LCAx deciphers the received data with the group key GKLCAx. Subsequently, LCAx performs the hash function on the original data (DVxy1|DRSUy), and verifies if it equals to the received HMAC(DVxy1|DRSUy). If there is a difference, it means during the transmission, the data are tampered with other vehicles. Otherwise, LCAx puts its ID into the routing path (IDVxy1|IDRSUy|IDLCAx), and then enciphers the merged data of ToS, TS, the rouging path, the original data (DVxy1|DRSUy|DLCAx) and its HMAC(DVxy1|DRSUy|DLCAx) via the group key GKLCAx. Eventually, LCAx forwards the enciphered result to RSUy+1.
Similar to the above procedure, RSUy+1 deciphers the enciphered data and verifies the integrity of the received data. Afterwards, RSUy+1 puts the related data into the corresponding column of the combination. Finally, RSUy+1 forwards the enciphered result to Vx(y+1)j.
After receiving the enciphered data, Vx(y+1)j performs the above similar procedure, and verifies the integrity of HMAC(DVxy1|DRSUy|DLCAx|DRSUY+1), and completes the secure data transmission from Vxy1 to Vx(y+1)j.
The secure data transmission of IoV belongs to the different LCA: the ECDSA mechanism
When the source vehicle Vxy1 and destination Vx(y+i)j are located in the different LCAs, as shown in the green dot line of Figure . For reducing the computing time of the group key exchange, this study adopts ECDSA mechanism to secure data transmission. The detailed procedure is as follows.
First, Vxy1 signs the transmitted data [ToS|TS|IDVxy1|DVxy1||HMAC(DVxy1)] with its own private key using ECDSA, and then forwards the signature result to RSUy.
Upon receipt of the transmitted data, RSUy deciphers the signature result utilising the public key of Vxy1, and verifies the original data [ToS|TS|IDVxy1|DVxy1||HMAC(DVxy1)] whether they are correct. If the transmitted data are tampered with, then discard this data, otherwise RSUy adds its IDRSUy into the routing path and computes HMAC(DVxy1|DRSUy) using the hash function. Then, RSUy signs the entire data using its private key, and delivers the signature result to LCAx.
After receiving, LCAx adopts the RSUy’s public key to decipher the enciphered data, and then verifies the original data of [ToS|TS|(IDVxy1IDRSUy)|(DVxy1|DRSUy)||HMAC(DVxy1|DRSUy)] whether it is correct. Subsequently, LCAx adds its identity IDLCAx into the routing path and computes HMC(DVxy1|DRSUy|DLCAx). Consequently, LCAx signs the entire data using its private key, and then sends the signature result to GCA.
When GCA obtains the transmitted data, it performs the above similar procedure and delivers the signature result to LCAx+w.
After receiving, LCAy utilises the public of GCA to decipher the enciphered data, and then verifies the original data of [ToS|TS|(IDVxy1IDRSUyIDLCAxIDGLCA)|(DVxy1|DRSUy|DLCAx|DGLCA)||HMAC(DVxy1|DRSUy|DLCAx|DGLCA)] whether they are tamped with, and repeats the similar procedures, adds its identity IDLCAx+w into the routing path and computes HMAC(DVxy1|DRSUy|DLCAx|DGLCA|DLCAx+w). Eventually, LCAx+w signs the entire data using its private key, and then sends the signature result to RSUy+i.
When RSUy+i receives the transmitted data, it adopts the public key of LCAy to decipher the enciphered data, after that verifies the original data whether they are tamped with. Subsequently, RSUy+i adds its identity IDRSUy+i into the routing path and computes HMAC(DVxy1|DRSUy|DLCAx|DGLCA|DLCAx+w|DRSUy+i). Consequently, RSUy+i signs the entire data using its private key, and then sends the signature result to Vx(y+j)j.
Finally, when Vx(y+j)j receives the data coming from RSUy+i, it utilises the public key of RSUy+i to decipher the enciphered data, and performs the hash function on the source data (DVxy1|DRSUy|DLCAx|DGLCAx|DLCAx+w|DRSUy+i), and verifies if they equal to the received HMAC(DVxy1|DRSUy|DLCAx|DGLCA|DLCAx+w|DRSUy+i). If they are different, it means during the transmission, the data are tampered with other vehicles. Otherwise, the original data from each vehicle are correct. According to the proposed mechanism, this study achieves the secure data transmission of IoV belonging to the different LCAs.
In an actual IoV environment, because V2V, V2I, V2P and V2G usually strongly demand rapidity, in addition to the topological architecture of the IoV is changing quickly. This research employs the proposed dynamic M-tree key management agreement and takes advantage of the ECDH and ECDSA to solve the problems of insufficient computing resources on the vehicle, RSUs and the cryptographic system issues between the vehicles.
The secure data transmission framework for IoV and the cloud server platform
When data goes through RSU and Internet to arrive at the cloud service platform, the submitted data must be protected against modification. This research uses a PKI infrastructure to securely transmit data and perform identity authentication. Furthermore, we exploit ECDSA to finish the secure transmission of data between vehicles, RSUs and cloud services on the cloud platform.
Because PKI utilises the digital signature of EDCSA to verify the participator identity, this scheme is highly appropriate to authenticate the identity of infrastructure devices, roadside devices, intelligent lights, signage and cloud platform servers. In this way, this research exploits digital signatures to guarantee the authenticity of the information source and to prevent impersonation, man-in-the-middle, and information replay attacks. This allows us to improve the reliability of the securely transmitted data from IoV infrastructure to a cloud services platform.
At the deployment stage, each vehicle member initially requests a certificate via the GCA of the cloud platform. The GCA server is in charge of the issuance of certificates to vehicles, RSU devices, vehicle service provider (VSP) and users. At the same time, the GCA server also is responsible for renewing certificates, revoking certificates and maintaining CRL (certificate revocation list).
When vehicles are required to demand a cloud service, this research utilises RSU to reach the cloud platform to perform secure data transmission. Because RSU and VSP are stationary installations and seldom altered, the identity of participants, such as RSU and VSP, may be confirmed by digital signatures. In the meantime, RSU also may help perform secure data transmission. This lowers the calculation load on OBU of vehicle. The framework of the GCA server is shown on the top left corner in Figure .
Figure 8. The whole framework of the secure data transmission between IoV and the cloud service platform.
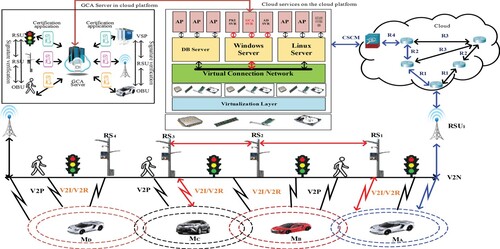
Firstly, at the early stage of this study, a secure virtual machine is chosen as a GCA server from the cloud platform.
Stage 1. The RSU of the road equipment, the vehicles and the VSP first apply to GCA for a certificate.
Stage 2. If a vehicle requires a VSP service, initially, the vehicle delivers the source data, the type of service ToS demand, itself identity ID, and the time stamp TS. This computation uses a hash function to generate the HMAC code of the above data as HMAC(ToS|TS|ID|source data). Subsequently, this study merges the plaintext data with the HMAC outcome, and employs ECDSA to sign and encipher the entire data via a private key, then after that delivers the signature result to the cloud platform.
Stage 3. The result of the signature is delivered to the boundary CSCM (cloud service category manager) via Internet routers.
Stage 4. Afterwards, CSCM utilises the vehicle’s public key for deciphering enciphered data, then computes the newer HMAC″ code of the received source data, and then verifies if HMAC″ equals to the received HMAC. When HMAC″ equals to HMAC, that indicates the source data are accurate and have not changed as the transmission process progresses.
Stage 5. Depending on the ToS from vehicles, CSCM will send the request to the respective application service on the cloud platform.
This research assumes when the MA vehicle transmits the data and request to CSCM along V2N, RSU1 and Internet routers. Once the delivered data has been received, subsequently CSCM delivers this request to the relevant cloud service, depending on the request of ToS coming from the vehicle. Figure shows the path of the blue colour. The following steps describe in detail the secure transmitting of data from the vehicle to the cloud service platform.
If the vehicle MA would like to deliver the M(DVA) message to the cloud services platform, MA initially delivers M(DVA) to the connected base station RSU1 by V2N, as indicated by the path MA ↔ V2N ↔ RSU1 ↔ R1 ↔ R2 ↔ R4 ↔ CSCM ↔ cloud service platform in Figure . Firstly, the vehicle MA places the required ToS, the time stamp, itself ID and the transmitted data M(DVA) in the respective column, subsequently enters the aforementioned data as the hash function input, and produces the HMAC(ToS|TS|IDMA|M(DVA)). This research then uses MA’s private key to sign and encipher HMAC(ToS|TS|IDMA|M(DVA)) utilising ECDSA and merges the original data with the signature result. Finally, MA sends all data to RSU1.
Once the enciphered data are received, RSU1 instantly deciphers the enciphered data utilising the MA’s public key, after that utilises the hash function to figure out the obtained source (ToS|TS|IDMA|M(DVA)) to gain a newer HMAC″. Afterwards, we check HMAC″ with the obtained source HMAC, and validate if HMAC″ equals to the source HMAC. When HMAC″ does not match HMAC, this represents that the source data are altered while transmitting, else the received data are valid, and then RSU1 delivers EKSigMA[ToS|TS|IDMA|M(DVA)||HMAC(ToS|TS|IDMA|M(DVA))] to the R1 cloud router.
Once the enciphered data are received, router R1 forwards it to R4 passing through routers R2 and R3 depending on the routing table. During this phase, the router can utilise its security protocol to protect the network packet.
Once R4 obtains the enciphered data, R4 forwards it to the border CSCM server. Meanwhile, CSCM uses the MA’s public key to decipher the enciphered data, and subsequently computes the newer HMAC″ code of the received source data [ToS|TS|IDMA|M(DVA)] utilising the hash function. Afterwards, this research verifies HMAC″ with the received source HMAC, and subsequently determines if HMAC″ = HMAC. When it makes any difference, this represents that the source data are altered during the transmitting path of RSU1→R1→R2→R4→CSCM. If not, CSCM sends the request to the relevant cloud application service, depending on the requested ToS from MA.
Generally, the proposed framework using the ECDSA signature protocol can securely transmit data between V2V, V2I, V2P, and V2G in IoV, and also secure the transmitting of data between the OBU of the vehicle and the cloud server platform as well. Finally, this research prevents harmful vehicles or malicious network devices from joining the transmission of data.
The architecture of secure data transmission for the cloud server platform: secure Map Reduce operations
When the CSCM sends the data to the related cloud service server (CSS) to perform Map/Reduce operation according to ToS, in order to confirm the identity and security of Mapper and Reducer for participants deployed in the cloud, this study uses VM Ware to simulate and construct several virtual servers to jointly execute Hadoop and Map/Reduce operations. Because there are so many servers in the cloud, the system must verify the identity of the participants before it cooperatively performs security operations. This study uses Kerberos to authenticate the participating servers before performing secure Map/Reduce operations to keep the data secure (Mukti et al., Citation2018; Subodh & Rajesh, Citation2020), as shown in Figure .
Figure 9. The Kerberos authentication protocol for the Mappers and Reducers of the cloud service platform.
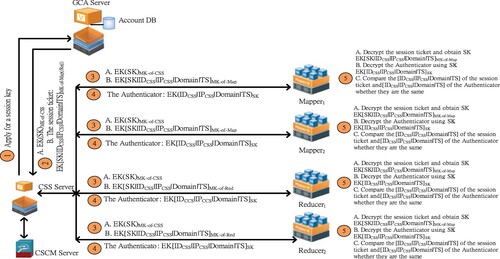
At the beginning of this system, we selected a secure GCA (as the key distribution centre), Mappers and Reducers from the cloud servers with mutual trust. The account database of GCA DB stores the account secrets of virtual servers such as CSS, Mappers, Reducers and other cloud service servers as follow-up identification operations. When the CSS requests the Map/Reduce operation, at the initial registration stage: CSS, Mappers and Reducers generate a group of personal passwords through the random number generator and store them into the account database of the GCA server.
Step1. Apply for a session key Initially, CSS requests a session key SK from the GCA VM server.
Step2. The master key and the enciphered session key: When GCA (a key distribution centre) receives the request, and then calculates a session key SK. In order to ensure that only CSS and Mappers/Reducers know SK, GCA respectively extracts the password of CSS and the Mappers/Reducers which take part in this operation, from the account DB. Subsequently, GCA performs a hash operation and respectively obtains the master key of CSS and the Mappers and Reducers, such as MKCSS(/Map/Red) = HASH(PasswordCSS(/Map/Red)). After that, CSS uses itself master key MKCSS to encipher the SK via a symmetric encryption scheme and obtains EK(SK)MK-of-CSS, and then uses MKMap and MKred to perform symmetric encryption operations on SK, IDCSS, IPCSS, its Domain and TS to respectively obtain EK[SK|IDCSS|IPCSS|Domain|TS]MK-of-Map and EK[SK|IDCSS|IPCSS|Domain|TS]MK-of-Red. For simplicity, we present it as EK[SK|IDCSS|IPCSS|Domain|TS]MK-of-Map(/Red) also named the session ticket. So far, GCA has a session ticket that consists of SK, CSS and Mappers/Reducers encrypted by MK. Eventually, GCA delivers EK(SK)MK-of-CCS and the session ticket EK[SK|IDCSS|IPCSS|Domain|TS]MK-of-Map(/Red) to CSS.
Step3. When CSS receives the above message, then forwards EK(SK)MK-of-CSS and the session ticket EK[SK|IDCSS|IPCSS|Domain|TS]MK-of-Map(/Red) to the Mappers/Reducers, which take part in this operation.
Step4. In order to provide more effective identity authentication, after receiving the encrypted session key SK, CSS uses its own MKCSS to decipher the received EK(SK)MK-of-CSS from GCA and obtain SK. Then the authenticator is generated, and contains the IDCSS, IPCSS, Domain and TS to be the duration of the subsequent confirmation request. Subsequently, this study enciphers the authenticator using SK and obtains EK[IDCSS|IPCSS|Domain|TS]SK. After that, CSS delivers the authenticator EK[IDCSS|IPCSS|Domain|TS]SK to the Mappers/Reducers, which take part in this operation.
Step5. When the Mappers/Reducers receive the above message, then decipher EK[SK| IDCSS|IPCSS|Domain|TS]MK-of-Map(/Red) using itself MKMap(/Red) to obtain SK, and then can decipher the received authenticator EK[IDCCS|IPCCS|Domain|TS]SK using SK to compare the [IDCSS|IPCSS|Domain|TS] of the session ticket and the deciphered result [IDCSS|IPCSS|Domain|TS] of the authenticator whether they are the same to ensure the identity of CSS. After CSS and Mappers/Reducers verify each other’s identities, and this study can perform the secure Map/Reduce operations.
The above secure data transmission modes provide a flexible and scalable option to protect data. The proposed mechanisms finish the secure data transmission from vehicles to cloud, and also integrate cloud platform with IoV. When a source vehicle wants to deliver data to a destination vehicle, under the same RSU or LCA, this study adopts a group key mechanism to secure data. Nevertheless, a huge IoV can exploit ECDSA to improve the efficiency of secure data transmission between vehicles. Additionally, this study also considers the secure transmission of data between vehicles and the cloud service platform. We provide a complete secure architecture to achieve this target, and make sure the identity of VM members joining the secure map/reduce operations.
6. The analysis of security and performance
In this section, we analyze and estimate our presented secure data transmission scheme. While transmitting data, the system must guarantee data integrity and avoid modification. Furthermore, we must make sure of the identity of participants in order to avoid impersonation from taking part in the process of data transmission. The following describes the detailed analysis of security.
Signature verification proof
According to the ECDSA algorithm, the receiver has to verify the identity of the sender. This study infers the following operations and ensures the signature of sender.
From the above inference, this study can prove that indeed r = xc, and thus this study can ensure the signature is correct.
Identity verification
In this study, although there is no authentication process when GCA made a request to CSS. However, if CSS_A pretends or claims to be CSS_B, then CSS_A will obtain the session key SK of CSS_B and Mapper/Reducers. However, the subsequent GCA uses CSS_B’s password to calculate the master key of CSS_B and uses the master key of CSS_B to encrypt SK.
However, only those who really know the CSS_B’s password can decipher and obtain the session key SK. Therefore, CSS_A cannot decipher and obtain the session key SK without CSS_B’s password, so it can confirm the identity of participants.
Confidentiality of Vehicle-to-Vehicle
Once malicious vehicles are interested in communicating with each other, through the route of transmission, only the two connected vehicles own the same session key via the ECDH key exchange protocol, after that utilise the session key for enciphering and deciphering transmitted data. Just the vehicle or RSU owns the common session key that can encipher or decipher the transmitted data (Zhang et al., Citation2021). The vehicle with no session key which cannot be included in the process of secure transmission, in spite of the harmful vehicle impersonates others, and thus this study can guarantee confidentiality of information transmission for Vehicle-to-Vehicle.
Confidentiality of Vehicle-to-Group
Just vehicles that have the same group key are allowed to participate in the group to communicate (Dan et al., Citation2004; Zhang et al., Citation2011), while vehicles with no group key are not allowed to join the communication. Even though an outside vehicle is listening or receiving a transmission, it is unable to decipher the encrypted message by the group vehicle as it has no group key. This method prevents messages from leaking or altering and ensures the confidentiality of messages between vehicles and groups.
System scalability
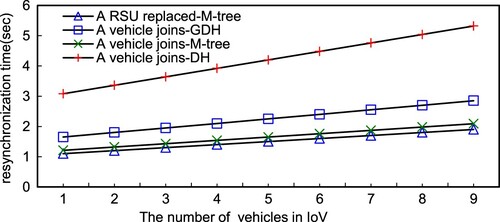
In this study, we utilise a dynamic M-tree structure to achieve the group key management. The benefit of M-tree is flexibility and scalability. As this research expands the quantity of vehicles, the whole system constantly retains the O(logM N) time complicity, where M stands for the M-tree degree and N stands for the quantity of vehicles, to figure out the group key. Moreover, even a great number of vehicles join the communication, the system just needs logMN stages to deal with the resynchronisation of the group key and obtain the common group key, as shown in Table . This mechanism is very well adapted to the wide range of vehicles in the IoV environment. Figure shows the dashed green square as the new connecting vehicles, and the investigation result indicates that the system still needs the same quantity of phases for handling key interchange and computing the group key. Besides, when a vehicle leaves, the whole system only has to compute the subtree of the leaving vehicle, then can reconstruct the newer group key of the vehicles. Therefore, this mechanism has flexibility and scalability.
Efficiency of the key management
Table 4. Resynchronisation cost of the system key for IoV.
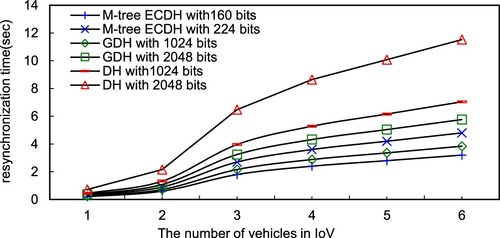
In this study, we compare the proposed key management of M-tree with None-tree and B-tree schemes on re-synchronising the system key. From Table , if vehicles participate in or take apart from IoV, the entire system needs to resynchronise the system key. As a result, the ECDH with M-tree and B-tree schemes outperform the None-tree scheme on communication and operational costs, since the M-tree scheme just takes two unicast phases and one multiplication phase. However, the None-tree scheme takes phases utilising DH.
Synchronisation time of a vehicle joining or leaving
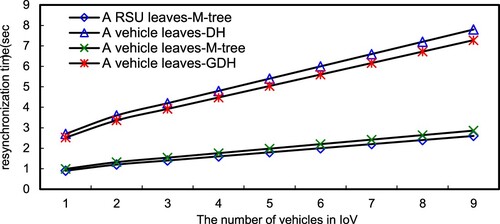
Initially, this system needs to construct the system key. Figure depicts the construction time of the system key on different schemes. As a result, the M-tree based scheme outperforms GDH and DH under the same secure levels. Since the M-tree structure only needs to update the keys along the parent nodes, GDH and DH have to exchange the share key for each other that needs phases, and then obtain the system key. Additionally, a vehicle or an RSU joins/leaves the IoV, the entire system needs to reconstruct the entire system key. Figure demonstrates that a vehicle joins IoV. The M-tree based scheme takes less resynchronisation time to reconstruct the system key then GDH and DH, since M-tree only needs to recalculate the joining node and the parent node. Similarly, when a vehicle leaves, the M-tree based scheme also outperforms GDH and DH, as shown in Figure .
7. Conclusions
Thanks to the development of 5G, automated driving without a driver will be right around the corner. Because IoV has an open communication environment, personal information is disclosed to the wireless network. Therefore, the problem of information security for IoV is going to be a significant theme. The proposed agreement of the multi-level security key management for IoV relies on the structure of an M-tree with the capacity to dynamically adjust the framework depending on the rapidly changing IoV topology. Additionally, this mechanism speeds up the time to synchronise the reconstruction of the system key, and decreases the quantity of phases to resynchronise the system key. Moreover, the provided key management for the multi-level security is quite appropriate to adaptable and expandable IoV environments. As well, the system effectively lowers operation and communication costs. In comparison to a B-tree, this study employs an M-tree that is more effective than the conventional key management. Moreover, the use of addition and multiplication operations can take the place of complex exponential operations and decrease the computing loading of OBU and RSU, and is better suited for IoV without plenty of calculating resources. Consequently, this study utilises a smaller key length of ECDSA to reach Diffee-Hellman or RSA security level, and secure the transmitted data among IoV devices and cloud service platforms. Thus this study can ensure information security and achieve secure IoV.
Data availability statement
The data that support the findings of this study are available on request.
Disclosure statement
No potential conflict of interest was reported by the author(s).
References
- Ali, I., Gervais, M., Ahene, E., & Li, F. (2019). A blockchain-based certificateless public key signature scheme for vehicle-to-infrastructure communication in VANETs. Journal of Systems Architecture, 99. https://doi.org/10.1016/j.sysarc.2019.101636
- Amit, D., Neeraj, K., Mukesh, S., Mohammad, S. O., & Kuei, F. H. (2016). Secure message communication among vehicles using elliptic curve cryptography in smart cities. International Conference on Computer, Information and Telecommunication Systems. https://ieeexplore.ieee.org/document/7546385
- Daisy, P. B. T., Albert, R. S., & Vimal, J. A. (2015). Elliptic Curve Cryptography based Security Framework for Internet of Things and Cloud Computing. International Journal of Computer Science and Technology, https://www.researchgate.net/publication/305913586
- Dan, B. X., Boyen, H., & Shacham. (2004). Short group signatures. Lecture Notes in Computer Science, 3152, 41–55. https://doi.org/10.1007/978-3-540-28628-8_3
- Dhanashree, T., Rohan, S., Het, S., Nikita, N., & Vishal, P. (2018). Prominence of ECDSA over RSA Digital Signature Algorithm. 2nd International Conference on IoT in Social, Mobile, Analytics and Cloud. https://ieeexplore.ieee.org/document/8653689/
- Hong, Z., Jingyu, W., Jie, C., & Shun, Z. (2016). Efficient conditional privacy-preserving and authentication scheme for secure service provision in VANET. Tsinghua Science and Technology, 21(6), 620–629. https://ieeexplore.ieee.org/document/7787005 https://doi.org/10.1109/TST.2016.7787005
- Hu, J., Liang, W., Hosam, O., Hsieh, M. Y., & Su, X. (2021). 5GSS: A framework for 5G-secure-smart healthcare monitoring. Connection Science, 1–23. https://doi.org/10.1080/09540091.2021.1977243
- Hu, X., Guobin, Z., Zhong, C., & Fagen, L. (2013). Efficient communication scheme with confidentiality and privacy for vehicular networks. Computers and Electrical Engineering, 39(6), 1717–1725. https://doi.org/10.1016/j.compeleceng.2012.11.009
- Hua, Y. L. (2021). Integrate the hierarchical cluster elliptic curve key agreement with multiple secure data transfer modes into wireless sensor networks. Connection Science, 1–27. https://doi.org/10.1080/09540091.2021.1990212.
- Insaf, U., Muhammad, A. K., & Mohammed, H. A. (2021). Anonymous certificateless Signcryption Scheme for secure and efficient deployment of Internet of vehicles. Sustainability Journal MDPI, 13(19), 10891. https://doi.org/10.3390/su131910891
- Jia, W., Jianqiang, L., Hui, H. W., Leo, Y. Z., Lee, M. C., & Qiuzhen, L. (2019). Dynamic scalable elliptic curve cryptographic scheme and its application to in-vehicle security. IEEE Internet of Things Journal, 6(4), 5892–5901. https://ieeexplore.ieee.org/document/8463502
- Joon, Y. L., Sung, J. Y., Myeong, H. K., Young, H. P., Sang, W. L., & Bo, H. C. (2020). Secure key agreement and authentication protocol for message confirmation in vehicular cloud computing. Applied Sciences, 10, 18. https://doi.org/10.3390/app10186268
- Kulathunge, A., & Dayarathna, H. (2019). Communication framework for vehicular ad-hoc networks using Blockchain: Case study of Metro Manila Electric Shuttle automation project. In Proceedings of the 2019 International Research Conference on Smart Computing and Systems Engineering. pp. 85–90. https://ieeexplore.ieee.org/document/8842814
- Kuljeet, K., Sahil, G., Georges, K., François, G., Syed Hassan, A., & Mohsen, G. (2019). A secure, lightweight, and privacy preserving authentication scheme for V2G connections in Smart Grid. IEEE Conference on Computer Communications Workshops. https://ieeexplore.ieee.org/document/8845140
- Lin, H. Y., Hsieh, M. Y., & Li, K. C. (2016). Flexible group key management and secure data transmission in mobile device communications using elliptic curve Diffie-Hellman cryptographic system. International Journal of Computational Science and Engineering, 12(1), 47. https://doi.org/10.1504/IJCSE.2016.074558
- Maxim, R., & Jean, P. H. (2007). Securing vehicular ad hoc networks. Journal of Computer Security. Special Issue on Security of Ad Hoc and Sensor Networks, 15(1), 39–68. https://doi.org/10.5555/1370616.1370618
- Mu, H., Mengli, Z., Pengzhou, C., Zhikun, Y., & Haixin, Q. (2021). Implementing an efficient secure attribute based encryption system for IoV using association rules. Symmetry Journal MDPI, 13(7), https://doi.org/10.3390/sym13071177
- Mukti, R., Nigar, S., Himel, D., & Hossain, A. (2018). A new version of Kerberos authentication protocol using ECC and Threshold Cryptography for Cloud Security. Joint 7th International Conference on Informatics, Electronics & Vision and 2nd International Conference on Imaging, Vision & Pattern Recognition. https://ieeexplore.ieee.org/document/8641010
- Nils, G., Arun, P., Avinderpal, W., Hans, E., & Sheueling, C. S. (2004). Comparing elliptic Curve Cryptography and RSA on 8-Bit CPUs. Lecture Notes in Computer Science, 3156, 119–132. https://doi.org/10.1007/978-3-540-28632-5_9
- Nisha, M., Priyadarsi, N., Arushi, A., Xiangjian, H., Deepak, P., & Puthal, D. (2018). Blockchain based secured identity authentication and expeditious revocation framework for vehicular networks. In Proceedings of the 17th IEEE International Conference on Trust, Security and Privacy in Computing and Communications/12th IEEE International Conference on Big Data Science and Engineering. pp. 674–679. https://ieeexplore.ieee.org/document/8455967
- Pandi, V., Maria, A., Sergei, A. K., & Joel, J. P. C. R. (2022). An anonymous batch authentication and key exchange protocols for 6G enabled VANETs. IEEE Transactions on Intelligent Transportation Systems, 23(2), 1630–1638. https://doi.org/10.1109/TITS.2021.3099488
- Ram, R. A., & Manoj, A. (2013). Elliptic curve Diffie-Hellman Key Exchange Algorithm for securing hypertext information on Wide Area Network. International Journal of Computer Science and Information Technologies, 4(2), 363–368. http://citeseerx.ist.psu.edu/viewdoc/summary?doi=10.1.1.299.9663
- Sathishkumar, N., & Rajakumar, K. (2017). A study on vehicle to vehicle collision prevention using Fog, Cloud, Big Data and Elliptic Curve Security based on Threshold Energy Efficient Protocol. Second International Conference on Recent Trends and Challenges in Computational Models. https://ieeexplore.ieee.org/document/8057548
- Shoma, K., Yasuyuki, N., Shunsuke, M., & Thomas, A. (2015). Volunteer computing for solving an Elliptic Curve Discrete Logarithm Problem. Third International Symposium on Computing and Networking. https://ieeexplore.ieee.org/document/7424699
- Subodh, C., & Rajesh, D. (2020). Secured map building using Elliptic Curve Integrated Encryption Scheme and Kerberos for Cloud-based Robots. Fourth International Conference on Computing Methodologies and Communication. https://ieeexplore.ieee.org/document/9076465
- Vijayakumar, P., Azees, M., Chang, V., Deborah, J., & Balamurugan, B. (2017). Computationally efficient privacy preserving authentication and key distribution techniques for vehicular ad hoc networks. Cluster Computing, 20(3), 2439–2450. https://doi.org/10.1007/s10586-017-0848-x
- Xia, X., Ji, S., Vijayakumar, P., Shen, J., & Rodrigues, J. (2021). An efficient anonymous authentication and key agreement scheme with privacy-preserving for smart cities. International Journal of Distributed Sensor Networks, 17(6). https://doi.org/10.1177/15501477211026804.
- Xiao, L., Xie, S., Han, D., Liang, W., Guo, J., & Chou, W. K. (2021). A lightweight authentication scheme for telecare medical information system. Connection Science, 33(1), 1–17. https://doi.org/10.1080/09540091.2021.1889976
- Xiaodong, L., & Rongxing, L.. (2015). GSIS: Group signature and ID-based signature-based secure and privacy preserving protocol. In Vehicular Ad Hoc network security and privacy (pp. 21–49). Wiley-IEEE Press. https://onlinelibrary.wiley.com/doi/10.1002/9781119082163.ch2
- Xiaodong, L., Xiaoting, S., Pin, H. H., & Xuemin, S. (2007). GSIS: A secure and privacy-preserving protocol for vehicular communications. IEEE Transactions on Vehicular Technology, 56(6), 3442–3456. https://ieeexplore.ieee.org/document/4357367 https://doi.org/10.1109/TVT.2007.906878
- Xu, Z., Liang, W., Li, K. C., Xu, J., & Jin, H. (2021). A blockchain-based roadside unit-assisted authentication and key agreement protocol for Internet of vehicles. Journal of Parallel and Distributed Computing, 149, 29–39. https://doi.org/10.1016/j.jpdc.2020.11.003
- Yasin, G., & Erkan, A. (2021). Design and implementation of an efficient Elliptic Curve Digital Signature Algorithm (ECDSA). IEEE International IOT, Electronics and Mechatronics Conference. https://ieeexplore.ieee.org/document/9422589
- Yong, J. K., Yong, M. K., Yong, J. C., & Hyong, C. O. (2013). An efficient bilinear pairing-free certificateless two-party authenticated Key Agreement Protocol in the eCK model. Journal of Theoretical Physics and Cryptography, 3, 1–10. https://arxiv.org/abs/1304.0383
- Zhang, C., Ho, P., & Tapolcai, J. (2011). On batch verification with group testing for vehicular communications. Wireless Network, 7(8), 1851–1865. https://doi.org/10.1007/s11276-011-0383-2
- Zhang, L., Xu, J., Obaidat, M., Li, X., & Vijayakumar, P. (2021). A PUF-based lightweight authentication and key agreement protocol for smart UAV networks. IET Communications, 1–18. https://doi.org/10.1049/cmu2.12295
- Zhe, L., Jian, W., Zhi, H., & Hwajeong, S. (2017). Efficient Elliptic Curve Cryptography for embedded devices. ACM Transactions on Embedded Computing Systems, 16(2). https://doi.org/10.1145/2967103