?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.Abstract
In this study, we propose an image encryption algorithm based on ZigZag transform with Durstenfeld Shuffling Algorithm (DSA), where we adopt confusion–diffusion architecture. Our encryption method is simpler to implement than high-dimensional chaos-based approaches, and its computational complexity is very low, which make it very fast and suitable for real-world applications. Additionally, its dependence on plaintext image makes it adaptive and hence very robust against brute force and differential attacks. Experimental analyses using histogram, correlation, NIST, NPCR, UACI and PSNR values suggest that our proposed algorithm is strong and secure against statistical and differential attacks.
1. Introduction
Developments in information and communication technologies have enabled easier and low-cost generation, transmission and storage of vast amounts of data at every aspect of business, industry and daily life. Especially in the last two decades, due to the growth of the Internet and the use of mobile devices, primary type of data being generated and shared has become images (Ben Slimane et al., Citation2018). In addition, security of images must be ensured to protect them against unauthorised access and to keep their confidentiality as they may contain highly sensitive and personal information. Therefore, secure storage and sharing of image data has become more important than ever, and image encryption has become a topic of high interest among researchers and practitioners (Li et al., Citation2019).
Image data has some intrinsic characteristics that make it more challenging for encryption approaches. First, size of images in practical applications is very large in general, which makes it difficult to encrypt them in a reasonable amount of time. Second, image data contains too much redundancy and very high correlation between adjacent pixels, which renders encryption schemes useless if they are not sufficiently strong because attackers can easily discover ways to reveal information in decrypted images via some statistical approaches. Because of these characteristics, traditional encryption methods such as Data Encryption Standard (DES), Triple DES (TDES), Advanced Encryption Standard (AES) and Rivest–Shamir–Adleman (RSA), which are commonly employed in secure communication of textual data, are not appropriate for encrypting image data (Lyle et al., Citation2022). Image data requires the development of encryption methods that particularly consider its special characteristics.
Image encryption methods usually follow a common architecture proposed by Fridrich (Citation1998) and divided into two distinct phases known as confusion (permutation) and diffusion (substitution) (Elghandour et al., Citation2021). The goal of the confusion phase is to eliminate the correlation between adjacent pixels of the plaintext image by scrambling the positions of them without modifying their values. In the diffusion phase, on the other hand, pixel values are systematically modified to alter the statistical properties of the image. Chaos-based encryption schemes have been very popular for image encryption since they propose solutions to provide necessary mechanisms needed in these two phases. Especially their high sensitivity to initial conditions, randomness and non-periodicity have placed chaos-based schemes into the focus of the image encryption research. Despite their effectiveness in image encryption, high-dimensional chaotic systems are known to be very costly to implement in both software and hardware due to their high computational complexity (Elghandour et al., Citation2021). Low-dimensional ones, on the other hand, provide lower chaotic performance and, as a result, lower security. We can see in the literature that a large body of research is focused on combining chaotic systems of different dimensionalities or combining chaos-based methods with other methods to achieve both computational efficiency and high security. Interested readers are referred to Kumari et al. (Citation2017), Ben Slimane et al. (Citation2018), Zhou et al. (Citation2021), Lyle et al. (Citation2022) and Fang et al. (Citation2022) for a very comprehensive and complete literature on image encryption and particularly on chaos-based encryption. Additionally, there are other representative methods such as based on one-time keys (Liu & Wang, Citation2010), bit-level permutation (Liu & Wang, Citation2011), DNA rule (Liu et al., Citation2012; X. Y. Wang et al., Citation2015), based on mathematical model (X. Y. Wang et al., Citation2010), based on parallel computing (X. Wang et al., Citation2019), based on piecewise coupled map lattice (X. Wang & Yang, Citation2021), based on matrix semi-tensor product theory (X. Wang & Gao, Citation2020a, Citation2020b), based on fractal sorting matrix (Xian & Wang, Citation2021; Xian et al., Citation2022), based on compressive sensing (X. Wang et al., Citation2021), based on dynamic random growth technique (X. Wang et al., Citation2015) and based on Anti-Dynamic Degradation Theorem (X. Wang & Liu, Citation2022).
In this study, we propose an image encryption method based on ZigZag transform (Chai et al., Citation2018) with Durstenfeld Shuffling Algorithm (DSA) (Durstenfeld, Citation1964, July), respecting the special requirements of encrypting image data. Our method utilises ZigZag transform with DSA in different steps to achieve necessary level of confusion. Additionally, we employ a series of XOR operations to achieve required level of diffusion to be secure and robust against statistical attacks. Our encryption method is simpler to implement than high-dimensional chaos-based approaches, and its computational complexity is very low, which make it very fast and suitable for real-world applications. The main contributions and novelty of our encryption method are as follows:
Our proposed method has low computational complexity due to its simple structure and non-reliance on complex operations, however, it has better or similar performance characteristics than chaos-based encryption methods.
It is suitable for real-world applications where real-time encryption/decryption performance is a key requirement, since it takes only 0.25 s to encrypt or decrypt a colour image of dimensions
.
It is adaptive in nature because the plaintext image is used for generating encryption keys, therefore, a small change in the plaintext creates an extremely different ciphertext, making statistical and differential attacks ineffective.
It has a very large key space, and it is extremely sensitive to keys.
It is very robust to noise and occlusion attacks.
The histograms and correlation charts of the encrypted images do not reveal any useful information to attackers.
With systematic experimentation, we present and verify the effectiveness and robustness of our proposed method, comparing it with recent different methods.
The rest of this paper is organised as follows. In Section 2, we provide an essential background on ZigZag transform and Durstenfeld Shuffle Algorithm. In Section 3, we give an elaborate description of our proposed algorithm. In Section 4, we present our experimental results, security analyses and discussion. Finally, in Section 5, we conclude this paper.
2. Preliminary background
2.1. ZigZag transform
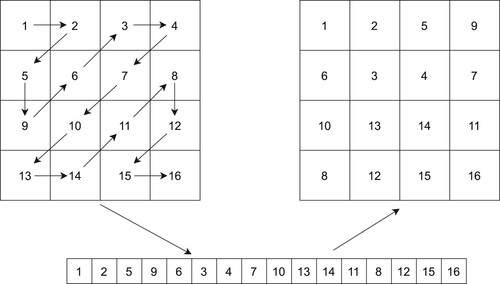
ZigZag transform is a form of permutation to scramble the pixels of an image. In ZigZag transform, pixels are traversed beginning from the top left corner of the image and following a Z-shaped path until the bottom right corner; hence the name (Chai et al., Citation2018; Xingyuan et al., Citation2019). Scanned pixels are stored in an one-dimensional array and then they are read from this array in a certain order to form a two-dimensional matrix. The order that the pixels are traversed is always the same for classical ZigZag transforms with a regular and predictable pattern (X. Wang & Guan, Citation2020). Traversal of the pixels can also begin from the other corners of the image, but the idea is the same. ZigZag transform is widely used to scramble image pixels for image encryption purposes. Classical ZigZag transform is shown in Figure applied to a sample matrix.
2.2. Durstenfeld shuffle algorithm
Shuffling is a process of randomising the positions of the elements in a list or array. In cryptology, shuffling is used to randomise the order of symbols in a message to make it more difficult for an attacker to discover the original message (Beimel et al., Citation2020). In statistics, shuffling is used to randomly permute the order of a sample, so that different orderings can be used to estimate the same quantity (Herranz et al., Citation2021).
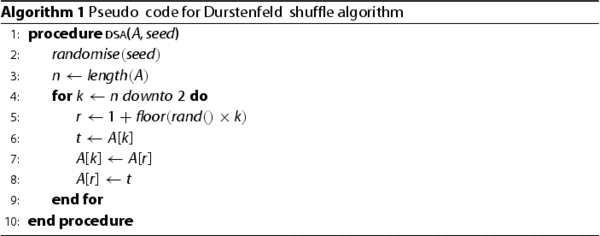
In this study, we employed Durstenfeld Shuffle Algorithm (DSA) in our encryption process, which is a very efficient shuffle algorithm known to have time and space complexity for a list of n items (Durstenfeld, Citation1964, July; S. Wang, Wang et al., Citation2020). DSA works simply as follows. Assume that we have an array
with n elements to shuffle. DSA essentially divides A into to two subsequent parts
and
in an iteration
, where
is the part that needs shuffling while
is the part already shuffled. At each iteration k, DSA picks a random number
, chooses an item
from the unshuffled part
and exchanges it with
. With this exchange, the item
is moved into the new shuffled part
, where it does not move anymore in the remaining iterations. We illustrate DSA in Algorithm 1. Random number generators generate the same number sequence for the same seed, which makes it possible to utilise them for encryption and decryption processes. Therefore, DSA algorithm in Algorithm 1 takes a seed parameter along with the array A to shuffle.
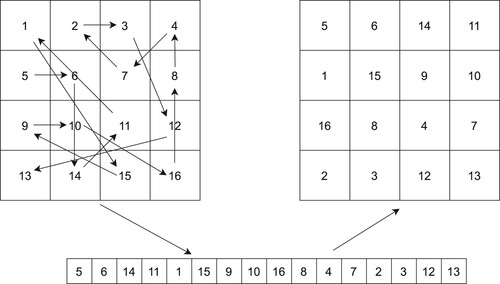
To improve the ZigZag transform, we use DSA to shuffle an image such that the pixels are traversed following a totally random path unlike the classical ZigZag transform which always uses regular and predictable path. Our improved version of ZigZag transform with DSA is seen in Figure .
3. Algorithm description
3.1. Image encryption process
In this paper, we consider a plaintext image P and an encrypted image with dimensions of
, where M is the height and N is the width in pixels. The image P can be a colour image with RGB layers (24-bit) or it can be a greyscale image with a single layer (8-bit).
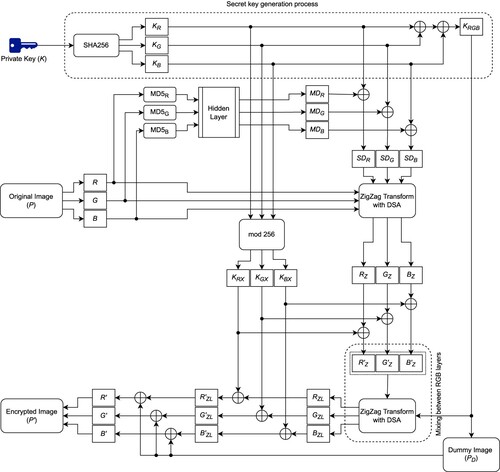
The encryption process we propose is shown in Figure . It mainly consists of seven steps as explained as follows. In addition to P, a private key K is used as an input to the process.
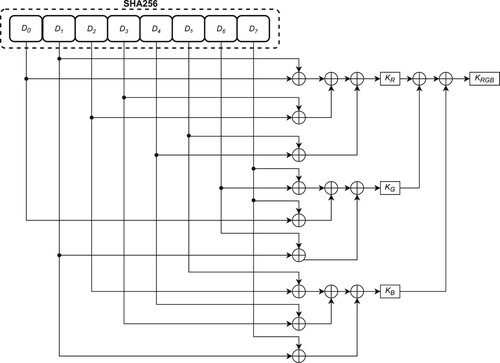
Step 1 - Secret Key Generation: As the first step of the encryption process, we calculate the SHA256 hash of the private key K and obtain an intermediate key of length 256 bits, as SHA256 algorithm always produces 256-bit hashes regardless of the length of K. Then, we split this hash into 8 equal length blocks of 32 bits and convert each block into its decimal value as .
We combine pairs of the block values in a series of XOR operations to compute the key values
,
and
to encrypt RGB channels of P separately. At this point, to decide which block to XOR with which other block, we use the reference information given in Table . For example, we XOR
and
to obtain
which is one of the three intermediate key values for R channel. Note that generated intermediate keys are different from each other. This process is illustrated in Figure diagrammatically.
Table 1. Guiding information to select pairs of blocks to XOR.
We use the following formulae to compute all encryption keys for R channel: (1)
(1)
(2)
(2)
(3)
(3)
(4)
(4) Similarly, we use the following formulae to compute all encryption keys for G channel:
(5)
(5)
(6)
(6)
(7)
(7)
(8)
(8) Then, we use the following formulae to compute all encryption keys for B channel:
(9)
(9)
(10)
(10)
(11)
(11)
(12)
(12) Finally, we combine these three keys to obtain a single key to use in Step 5 as follows:
(13)
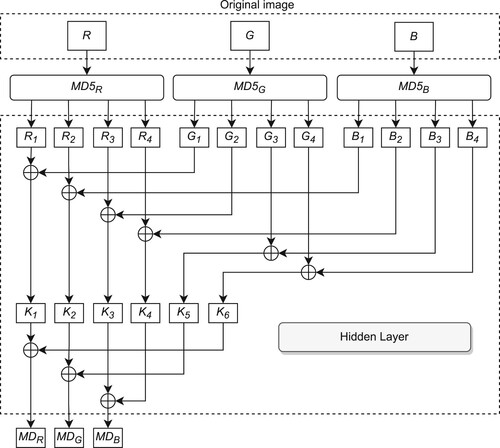
(13) Step 2 – Hidden Key Generation: In this step, we first generate MD5 hashes of the RGB channels separately as
,
and
. Then, we combine different bytes of these hashes with each other in a series of XOR operations to obtain our hidden keys as
,
and
. Figure shows one possible configuration for this process in detail. We use these hidden keys to make our system resistant to differential attacks as single pixel change in plaintext images causes significant differences in the generated ciphertext images.
Step 3 - XOR Keys Generation: In Step 1, we generate three different encryption keys ,
and
for RGB channels, respectively. In the coming steps, we use these key values to XOR with pixel values in corresponding channels. We, however, do not use these key values directly for XOR because they may be greater than 255 which is the maximum pixel value in a channel. Therefore, we take the modulo 256 of each key value before using with XOR and obtain XOR keys
,
and
as follows:
(14)
(14)
(15)
(15)
(16)
(16) Step 4 - ZigZag Transform with DSA: In Step 1, we generate three different encryption keys
,
and
, and in Step 2, we generate three hidden keys
,
and
for RGB channels, respectively. In this step, we XOR these keys with each other respectively to obtain seed values
,
and
. Using these seeds and DSA, we shuffle the pixels of each channel separately. DSA requires a random number generator (RNG), and we use
as the seed of RNG for shuffling the R channel. Similarly, we shuffle G and B channels using
and
. After the shuffling, we obtain shuffled channels as
,
and
. Then, we XOR the pixels in each shuffled channel with the corresponding XOR keys
,
and
, respectively. As a result of this, we obtain XORed RGB channels as
,
and
. The process is shown in the following equations:
(17)
(17)
(18)
(18)
(19)
(19)
(20)
(20)
(21)
(21)
(22)
(22) Step 5 - Mixing Between RGB Layers: In Step 4, the image P is already strongly encrypted. In this step, we increase the complexity and the strength of the encryption by mixing
,
and
channels among themselves. First, we concatenate them and obtain a single-dimensional array. Then, we shuffle this array using DSA to get the desired inter-channel mixing effect. Note that, pixels in a channel not only change their places across other channels but also change their places within their own channels due to the randomisation. Since we employ a single DSA in this step, we use
as the seed of RNG. Next, we extract RGB channels back from this array by taking the first one third part of it for R, subsequently the rest for G and B channels as
,
and
, as given in the following equation, where
represents concatenation:
(23)
(23) Step 6 - XORing RGB Channels with XOR Key: In this step, we XOR the pixels in each channel
,
and
with XOR keys
,
and
to obtain
,
and
, as follows:
(24)
(24)
(25)
(25)
(26)
(26) Step 7 - Final Ciphertext Generation: Finally, we generate a single-channel dummy image
with the same dimensions as P using RNG with the seed
. This dummy image is used to further modify the pixel values of the encrypted image as part of the diffusion process. This provides an extra level of resistance to statistical attacks. Then, we XOR the pixels in each channel
,
and
with the corresponding pixel values of
. As a result, we obtain final encrypted RGB channels
,
and
to make up the final encrypted image
as follows:
(27)
(27)
(28)
(28)
(29)
(29) The encryption process explained in this section deals with only 24-bit colour image with RGB layers. However, when it comes to a 8-bit greyscale image, the same process can be used without making any changes. The only requirement is that all RGB layers must contain the same 8-bit layer of the greyscale image.
3.2. Image decryption process
To decrypt an encrypted image, we need to employ the same operations in reverse direction. However, there is a requirement that the hidden keys ,
and
must be supplied to the receiver by the sender to use them in the decryption process. With these hidden keys and the private key, it is a straightforward process to decrypt a ciphertext image.
4. Experimental results and security analyses
4.1. Encryption and decryption results
We conducted encryption and decryption experiments with common colour benchmark images Lena Pepper, Baboon and Barbara of size on a workstation with Intel Core i7-4700 CPU at 2.4 GHz with 4 cores, 16 GB RAM and MS Windows 10 Pro 64 bit OS. The algorithm was implemented and tested in MATLAB 2020b environment.
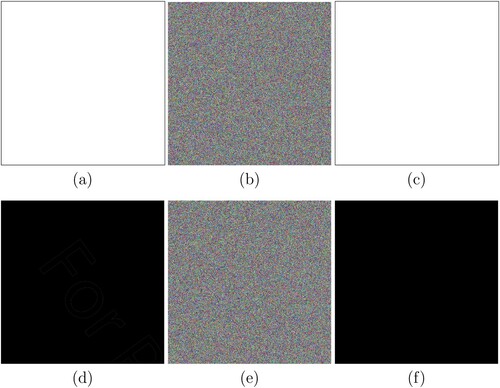
We used the private key “maltepe@” for encryption. We present the results in Figure . It is clearly seen that the original plaintext images were obtained after decryption without any loss. We tested our method on all white and all black images as well, showing that encryption and decryption were performed successfully as seen in .
4.2. Algorithm complexity analysis
Our proposed method consists of seven steps, each of which has contribution to the total complexity of the encryption process with different amounts. In Step 1, we only generate secret encryption keys based on the private key using SHA256. Therefore, this step adds a very small and constant amount of complexity to the whole encryption process.
In Step 2, we generate hidden keys for each channel of the plaintext image using MD5 hashing. To do this, this step requires three iterations, one for each MD5 calculation, over the pixels of the image where there are pixels. Thus time complexity of this step can be expressed as
.
Step 3 does not involve any operations on the image pixels as this step only calculates XOR Keys with a few very small modulo operations. Hence, this step can totally be ignored in terms of computational complexity.
Step 4 is one of the most computationally intensive one because we apply ZigZag Transform with DSA to scramble the pixel values of each channel of the plaintext image. Computational complexity of DSA is proportional to the number of elements to shuffle (n) and it is . Therefore, total complexity of this shuffling process is
. After shuffling the channels, we XOR the pixels in each shuffled channel with their corresponding XOR keys. This operation has also the complexity of
as well.
In Step 5, we employ a sort of mixing among the pixel values between the channels of the image encrypted until this step. This operation involves another shuffling with DSA, introducing an additional complexity.
Step 6 performs a series of XOR operations on the pixels in each channel with their corresponding XOR keys. This operations has the complexity of .
In Step 7, we first generate a single-channel dummy image with the same dimensions with random pixel values. This has the time complexity of . Then, we XOR the pixels in each channel of the encrypted image with the corresponding pixel values of the dummy image, whose time complexity is
.
When we combine the computational complexities of our proposed method's steps, we find that total time complexity is , and, therefore, it can simply be expressed as
. As a result, our proposed method has a linear time complexity with respect to number of pixels in plaintext images, and it can effectively be applied in real-world scenarios where efficiency is a key requirement as well as encryption strength.
4.3. Key analysis
4.3.1. Key space
In our proposed method, we first apply SHA256 to a given private key K to obtain a 256-bit intermediate key. Then, we use this intermediate key for the subsequent operations. Therefore, the key space of our method is , which is comparably larger than the requirement of
as suggested by Alvarez and Li (Citation2006).
4.3.2. Sensitivity analysis of key
We encrypted colour Lena of size with the private key
“maltepe@”. Then, we experimented with different keys with slight differences to decrypt the ciphertext image. The keys were “Maltepe@”, “malTepe@”, “ma1ltepe”, “maltrpe_”, and “maltePe” as an attacker would possibly try. We present the decrypted images with these incorrect keys as well as the correct key in Figure .
Figure 8. Decryption results with correct and incorrect keys: (a) decrypted image with the correct key maltepe@, (b)–(f) images decrypted with keys with little difference (Maltepe@, malTepe@, ma1ltepe, maltrpe_, maltePe).

When we analyse the experimental results, we find that the original image can only be obtained by decrypting with the correct key. This shows that our method is very sensitive to the key. To present this sensitivity, we computed Number of Pixel Change Rate (NPCR) values for the decrypted images in Figure as given in Table . NPCR is calculated between two images and
as follows (Wu et al., Citation2011; Zhang & Wang, Citation2015):
(30)
(30) where M and N represent the width and height of the images respectively.
is 0 if the pixel values of images
and
at coordinate
are the same, and 1 otherwise. In general, NPCR values are required to be very close to 99.6093%. As seen in Table , the NPCR values of images decrypted by incorrect keys are very close to this ideal value, which demonstrates the sensitivity of our method to the key.
Table 2. NPCR (%) values of decrypted images with different keys.
4.4. Histogram analysis
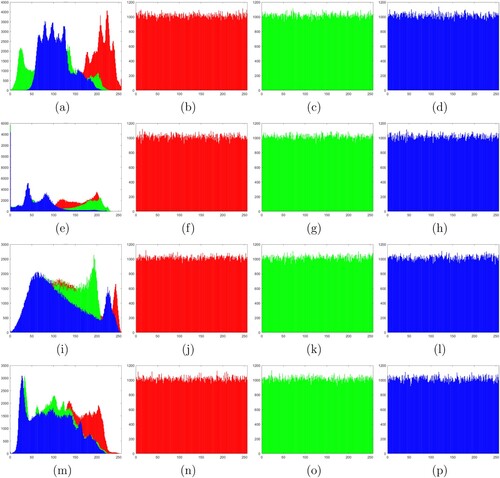
Histogram is a powerful tool to analyse the distribution of pixel values of an image. If the distribution of a ciphertext image is uneven, then an attacker can obtain important information through statistical analysis. Therefore, a good encryption algorithm is expected to generate ciphertext images with even distribution to make the ciphertext image resistant to statistical analysis (Zhang & Wang, Citation2014). In Figure , we present the histogram of each channel before and after encryption of colour images Lena, Pepper, Baboon and Barbara. It is seen that the histograms of plaintext images are uneven before encryption, and the corresponding histograms of ciphertext images are even after encryption. Therefore, our method generates ciphertext images resistant to statistical analysis.
Figure 9. Histogram analysis: (a) histogram of the plaintext Lena in all channels, (b)–(d) histograms of the ciphertext image Lena in channels R, G and B, respectively, (e) histogram of the plaintext Pepper in all channels, (f)–(h) histograms of the ciphertext image Pepper in channels R, G and B, respectively, (i) histogram of the plaintext Baboon in all channels, (j)–(l) histograms of the ciphertext image Baboon in channels R, G and B, respectively, (m) histogram of the plaintext Barbara in all channels, (n)–(p) histograms of the ciphertext image Barbara in channels R, G and B, respectively.
4.5. Correlation between adjacent pixels
There is usually a high correlation between adjacent pixel values in plaintext images, which makes them vulnerable to statistical attacks. Unlike plaintext images, ciphertext images are required to show very low correlation between adjacent pixel values. Therefore, it is necessary for an encryption algorithm to reduce the correlation between adjacent pixels of a ciphertext image. We calculated the correlation coefficients between adjacent pixels of plaintext and ciphertext images of Lena using Equation (Equation31(31)
(31) ).
(31)
(31)
(32)
(32)
(33)
(33)
(34)
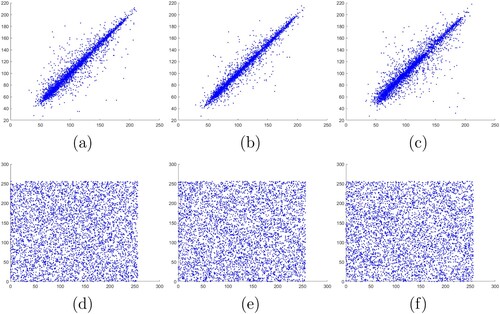
(34) We randomly picked 5000 pairs of adjacent pixels of RGB channels in the plaintext image Lena and its corresponding ciphertext image from horizontal, vertical and diagonal directions. The correlations between adjacent pixels are compared from each direction for RGB channels as shown in Figures , , and , respectively.
Figure 10. Correlation between adjacent pixels in channel R of Lena: (a)–(c) horizontal, vertical and diagonal correlations in plaintext, (d)–(f) horizontal, vertical, diagonal correlations in ciphertext.
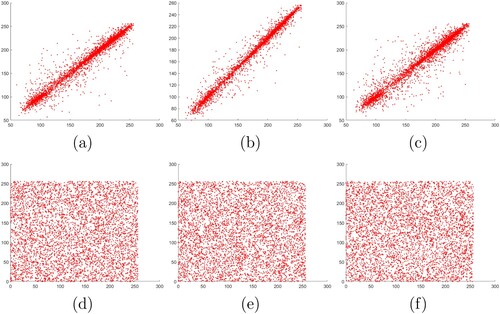
Figure 11. Correlation between adjacent pixels in channel G of Lena: (a)–(c) Horizontal, vertical, and diagonal correlations in plaintext, (d)–(f) horizontal, vertical, diagonal correlations in ciphertext.
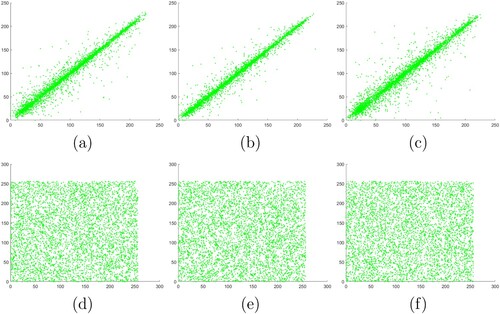
Figure 12. Correlation between adjacent pixels in channel B of Lena: (a)–(c) horizontal, vertical and diagonal correlations in plaintext, (d)–(f) horizontal, vertical, diagonal correlations in ciphertext.
We present the correlation coefficients of plaintext and ciphertext images Lena in all RGB channels in Table , comparing our method to several previous studies. It is obvious that there is a high correlation between adjacent pixels in the plaintext image, and that there is a low correlation between adjacent pixels in the ciphertext image. Thus our method can effectively resist statistical attacks.
Table 3. Correlations between adjacent pixels of plaintext and ciphertext images of Lena.
4.6. Information entropy
Information entropy is the degree of randomness of information, and it is calculated as in Equation (Equation35(35)
(35) ).
(35)
(35) where
is the probability of symbol
, which is the probability of different pixel values (from 0 to 255) in the image.
The information entropy of plaintext and ciphertext images of Lena in all channels is given in Table , comparing them with the findings of several previous studies. For a secure encryption algorithm, the entropy of ciphertext images is required to be as close to 8 bits as possible for each RGB channel. As seen in Table , our method generates ciphertext images with very high information entropy values. The results from the entropy analysis are in good agreement with the results from the histogram analysis. Therefore, we can state that it is difficult to disclose information from ciphertext images generated by our method, and those ciphertext images can resist statistical attacks.
Table 4. Entropy analysis results (in bits).
4.7. Sensitivity analysis to plaintext
As well as being sensitive to key, a good encryption method is required to be sensitive to plaintext, which means a slight change in the plaintext results in entirely different ciphertext. This way, the encryption system can resist against attacks known as differential attacks. In a differential attack, an attacker changes a single pixel in the plaintext image and generates ciphertext images for both plaintext images to analyse the relationship between them to guess the encryption mechanism. When the ciphertext images are completely different, attacker's attempts will reveal no meaningful and useful information. To this end, we changed the pixel value of a random location in Lena from its original value to 0 and generated ciphertexts using the same private key. Then, we compared ciphertexts in terms of NPCR and Unified Average Changing Intensity (UACI) values. UACI is calculated between two images and
as follows (X. Wang et al., Citation2012; Wu et al., Citation2011):
(36)
(36) where M and N represent the width and height of the images respectively. We present different values of NPCR and UACI for Lena in Table as the average of 500 repetitions for the above process. In general, the values of NPCR and UACI are required to be as close as possible to 99.6093% and 33.4635%, respectively. According to the obtained results, both NPCR and UACI values are very close to these ideal values, which demonstrate our method's sensitivity to the plaintext, and its resistance against differential attacks.
Table 5. NPCR and UACI values of ciphertext images of Lena for plaintext sensitivity analysis.
4.8. Robustness analysis
Robustness is the resistance of encryption system to disturbances, and thus, it is a crucial attribute. To test the robustness of our proposed encryption algorithm, we employed noise attacks as well as occlusion attacks.
First, we tested our algorithm against noise attacks using common noise types such as Gaussian noise and salt-and-pepper noise (Zhou et al., Citation2021). After encrypting the plaintext image, we added Gaussian noise with different variances as well as salt-and-pepper noise with different intensities to the ciphertext image. Then we decrypted this noise-added ciphertext with the same private key. In Figure , we present decrypted images after adding Gaussian noise with variances of 0.01 and 0.1, and salt-and-pepper noise with intensities of 0.01 and 0.05. It is clear that with a limited amount of noise, decrypted images are comprehensible. Therefore, we can state that our proposed encryption algorithm is robust against noise attacks.
Figure 13. Experimental results for a noise attack. Gaussian noise decryption results with variance of (a) 0.01 and (b) 0.1. Salt-and-pepper noise decryption results with intensity of (c) 0.01 and (d) 0.05.

We applied occlusion attack as a second type of robustness test. Again after encrypting the plaintext image, we occluded 1/16, 1/4 and 1/2 of the ciphertext images with black pixels in different shapes as rectangles and a plus. Then, we decrypted the ciphertexts with occlusions with the same private key. In Figure , we present decrypted images. As seen in the figure, as the size of the occlusion increases, the quality of the decrypted image degrades. However, they are still very well understandable, and the loss of information is at a minimum level. Even half of the ciphertext is occluded, we are able to recover the plaintext as a whole to some extent. Thus we can express that our proposed encryption algorithm is robust against occlusion attacks as well. Besides visual results, we also provide the Peak Signal-to-Noise Ratio (PSNR) (Zhou et al., Citation2021) results to show the robustness of our method in Table along with NPCR and UACI values. PSNR between plaintext image and decrypted image
can be calculated as follows:
(37)
(37)
(38)
(38) where M and N represent the width and height of the images respectively.
Figure 14. Experimental results for occlusion attacks. The encrypted images with (a) 1/16, (b) 1/4 and (c) 1/2 occlusion, (d) Plus occlusion, (e)–(h) are the corresponding decrypted images.

Table 6. Quantitative results of occlusion attack resistance.
4.9. NIST test of randomness
To create shuffling with DSA, we use random sequence generated by an RNG and we need to test the randomness of the sequences generated to make sure they are suitable for image encryption. We adopted SP800-22 test suit which consists of 15 sub-tests from the National Institute of Standards and Technology (NIST) to measure the randomness of the sequences used in our method (X. Wang, Guan et al., Citation2020). The test scores represent the corresponding P-values where a test is considered a pass when where α is the significance level and generally is taken as
. We present the NIST test results in Table . It is clearly seen from the test results that all P-values are greater than
and we can confidently state that the sequences used in the encryption have reasonably good randomness.
Table 7. NIST test results.
5. Conclusion
We propose an image encryption algorithm based on ZigZag transform with DSA in this paper. Our encryption method is simpler to implement than high-dimensional chaos-based approaches, and its computational complexity is very low. Additionally, its dependence on plaintext image makes it adaptive and hence very robust against brute force and differential attacks. Experimental results with NPCR values suggest that our encryption algorithm is very sensitive to the encryption key. In addition, histograms of the encrypted images are even. Moreover, the correlation coefficients of adjacent pixels in the encrypted images in all three directions are very close to zero. Besides, the entropy values calculated from the encrypted images are significantly close to ideal value of 8. These results of histogram, correlation and entropy analyses show that our method generates ciphertext images resistant to statistical analysis. In addition to these analyses, we performed sensitivity analysis to plaintext using NPCR and UACI metrics, and according to the obtained results, both NPCR and UACI values are remarkably close to the ideal values, which demonstrates our method's sensitivity to the plaintext, and its resistance against differential attacks. Furthermore, we performed robustness analysis with noise and occlusion attacks, and show that our method is secure and robust against these types of attacks according to NPCR, UACI and PSNR values. Finally, according to our timing experiments, both encryption and decryption of a colour image of size take about 0.25 s which make it very fast and suitable for real-world applications, along with its security and robustness. Secure and fast image encryption is a requirement not only of personal daily use but also of industrial use. For instance, in Internet of Things (IoT) and Internet of Vehicles (IoV) settings, lots of sensitive images are likely to be collected and transmitted, where a simple, fast, efficient, and low-cost encryption and decryption would be a key factor. Our proposed method is highly suitable for such industrial applications with its simple to implement and low-complexity structure.
Acknowledgments
The authors would like to thank Kaan Bıçakcı for his invaluable suggestions and support for the research.
Disclosure statement
The authors report there are no competing interests to declare.
Funding
This research did not receive any specific grant from funding agencies in the public, commercial or not-for-profit sectors.
References
- Alvarez, G., & Li, S. (2006). Some basic cryptographic requirements for Chaos-based cryptosystems. International Journal of Bifurcation and Chaos, 16(8), 2129–2151. https://doi.org/10.1142/S0218127406015970.
- Arpacı, B., Kurt, E., Çelik, K., & Ciylan, B. (2020). Colored image encryption and decryption with a new algorithm and a hyperchaotic electrical circuit. Journal of Electrical Engineering & Technology, 15(3), 1413–1429. https://doi.org/10.1007/s42835-020-00393-x.
- Beimel, A., Haitner, I., Nissim, K., & Stemmer, U. (2020). On the round complexity of the shuffle model. In R. Pass & K. Pietrzak (Eds.), Theory of cryptography (pp. 683–712). Springer International Publishing.
- Ben Slimane, N., Aouf, N., Bouallegue, K., & Machhout, M. (2018). A novel chaotic image cryptosystem based on DNA sequence operations and single neuron model. Multimedia Tools and Applications, 77(23), 30993–31019. https://doi.org/10.1007/s11042-018-6145-8.
- Chai, X., Zheng, X., Gan, Z., & Chen, Y. (2020). Exploiting plaintext-related mechanism for secure color image encryption. Neural Computing and Applications, 32(12), 8065–8088. https://doi.org/10.1007/s00521-019-04312-8.
- Chai, X., Zheng, X., Gan, Z., Han, D., & Chen, Y. (2018). An image encryption algorithm based on chaotic system and compressive sensing. Signal Processing, 148, 124–144. https://doi.org/10.1016/j.sigpro.2018.02.007.
- Devaraj, P., & Kavitha, C. (2016). An image encryption scheme using dynamic S-boxes. Nonlinear Dynamics, 86(2), 927–940. https://doi.org/10.1007/s11071-016-2934-7.
- Durstenfeld, R. (1964, July). Algorithm 235: Random permutation. Communications of the ACM, 7(7), 420. https://doi.org/10.1145/364520.364540.
- Elghandour, A. N., Salah, A. M., Elmasry, Y. A., & Karawia, A. A. (2021). An image encryption algorithm based on bisection method and one-dimensional piecewise chaotic map. IEEE Access, 9, 43411–43421. https://doi.org/10.1109/ACCESS.2021.3065810.
- Fang, P., Liu, H., Wu, C., & Liu, M. (2022). A survey of image encryption algorithms based on chaotic system. The Visual Computer, 2022(6), 1–29. https://doi.org/10.1007/s00371-022-02459-5.
- Firdous, A., & Missen, M. M. S. (2019). A highly efficient color image encryption based on linear transformation using chaos theory and SHA-2. Multimedia Tools and Applications, 78(17), 24809–24835. https://doi.org/10.1007/s11042-019-7623-3.
- Fridrich, J. (1998). Symmetric ciphers based on two-dimensional chaotic maps. International Journal of Bifurcation and Chaos, 08(6), 1259–1284. https://doi.org/10.1142/S021812749800098X.
- Gan, Z., Chai, X., Zhang, M., & Lu, Y. (2018). A double color image encryption scheme based on three-dimensional Brownian motion. Multimedia Tools and Applications, 77(21), 27919–27953. https://doi.org/10.1007/s11042-018-5974-9.
- Herranz, J., Martínez, R., & Sánchez, M. (2021). Shorter lattice-based zero-knowledge proofs for the correctness of a shuffle. In M. Bernhard, A. Bracciali, L. Gudgeon, T. Haines, A. Klages-Mundt, S. I. Matsuo, D. Perez, M. Sala, & S. Werner (Eds.), Financial cryptography and data security. FC 2021 international workshops (pp. 315–329). Springer Berlin Heidelberg.
- Kumari, M., Gupta, S., & Sardana, P. (2017). A survey of image encryption algorithms. 3D Research, 8(4), 1–35. https://doi.org/10.1007/s13319-017-0148-5.
- Li, C., Zhao, F., Liu, C., Lei, L., & Zhang, J. (2019). A hyperchaotic color image encryption algorithm and security analysis. Security and Communication Networks, 2019, 1–9. https://doi.org/10.1155/2019/8132547.
- Liu, H., & Wang, X. (2010). Color image encryption based on one-time keys and robust chaotic maps. Computers & Mathematics with Applications, 59(10), 3320–3327. https://doi.org/10.1016/j.camwa.2010.03.017.
- Liu, H., & Wang, X. (2011). Color image encryption using spatial bit-level permutation and high-dimension chaotic system. Optics Communications, 284(16–17), 3895–3903. https://doi.org/10.1016/j.optcom.2011.04.001.
- Liu, H., Wang, X., & Kadir, A. (2012). Image encryption using DNA complementary rule and chaotic maps. Applied Soft Computing, 12(5), 1457–1466. https://doi.org/10.1016/j.asoc.2012.01.016.
- Lyle, M., Sarosh, P., & Parah, S. A. (2022). Adaptive image encryption based on twin chaotic maps. Multimedia Tools and Applications, 81(6), 8179–8198. https://doi.org/10.1007/s11042-022-11917-0.
- Wang, S., Wang, C., & Xu, C. (2020). An image encryption algorithm based on a hidden attractor chaos system and the Knuth–Durstenfeld algorithm. Optics and Lasers in Engineering, 128, Article ID 105995. https://doi.org/10.1016/j.optlaseng.2019.105995.
- Wang, X., Feng, L., & Zhao, H. (2019). Fast image encryption algorithm based on parallel computing system. Information Sciences, 486, 340–358. https://doi.org/10.1016/j.ins.2019.02.049.
- Wang, X., & Gao, S. (2020a). Image encryption algorithm based on the matrix semi-tensor product with a compound secret key produced by a Boolean network. Information Sciences, 539, 195–214. https://doi.org/10.1016/j.ins.2020.06.030.
- Wang, X., & Gao, S. (2020b). Image encryption algorithm for synchronously updating Boolean networks based on matrix semi-tensor product theory. Information Sciences, 507, 16–36. https://doi.org/10.1016/j.ins.2019.08.041.
- Wang, X., & Guan, N. (2020). A novel chaotic image encryption algorithm based on extended Zigzag confusion and RNA operation. Optics & Laser Technology, 131, Article ID 106366. https://doi.org/10.1016/j.optlastec.2020.106366.
- Wang, X., Guan, N., Zhao, H., Wang, S., & Zhang, Y. (2020). A new image encryption scheme based on coupling map lattices with mixed multi-chaos. Scientific Reports, 10, 1–15. https://doi.org/10.1038/s41598-020-66486-9.
- Wang, X., Liu, C., & Jiang, D. (2021). A novel triple-image encryption and hiding algorithm based on chaos, compressive sensing and 3D DCT. Information Sciences, 574, 505–527. https://doi.org/10.1016/j.ins.2021.06.032.
- Wang, X., Liu, L., & Zhang, Y. (2015). A novel chaotic block image encryption algorithm based on dynamic random growth technique. Optics and Lasers in Engineering, 66, 10–18. https://doi.org/10.1016/j.optlaseng.2014.08.005.
- Wang, X., & Liu, P. (2022). A new full chaos coupled mapping lattice and its application in privacy image encryption. IEEE Transactions on Circuits and Systems I: Regular Papers, 69(3), 1291–1301. https://doi.org/10.1109/TCSI.2021.3133318.
- Wang, X., Teng, L., & Qin, X. (2012). A novel colour image encryption algorithm based on chaos. Signal Processing, 92(4), 1101–1108. https://doi.org/10.1016/j.sigpro.2011.10.023.
- Wang, X., & Yang, J. (2021). A privacy image encryption algorithm based on piecewise coupled map lattice with multi dynamic coupling coefficient. Information Sciences, 569, 217–240. https://doi.org/10.1016/j.ins.2021.04.013.
- Wang, X. Y., Yang, L., Liu, R., & Kadir, A. (2010). A chaotic image encryption algorithm based on perceptron model. Nonlinear Dynamics, 62(3), 615–621. https://doi.org/10.1007/s11071-010-9749-8.
- Wang, X. Y., Zhang, Y. Q., & Bao, X. M. (2015). A novel chaotic image encryption scheme using DNA sequence operations. Optics and Lasers in Engineering, 73, 53–61. https://doi.org/10.1016/j.optlaseng.2015.03.022.
- Wu, Y., Noonan, J. P., & Agaian, S. (2011). NPCR and UACI randomness tests for image encryption. Journal of Selected Areas in Telecommunications (JSAT), 1(2), 31–38.
- Xian, Y., & Wang, X. (2021). Fractal sorting matrix and its application on chaotic image encryption. Information Sciences, 547, 1154–1169. https://doi.org/10.1016/j.ins.2020.09.055.
- Xian, Y., Wang, X., & Teng, L. (2022). Double parameters fractal sorting matrix and its application in image encryption. IEEE Transactions on Circuits and Systems for Video Technology, 32(6), 4028–4037. https://doi.org/10.1109/TCSVT.2021.3108767.
- Xingyuan, W., Junjian, Z., & Guanghui, C. (2019). An image encryption algorithm based on ZigZag transform and LL compound chaotic system. Optics & Laser Technology, 119, Article ID 105581. https://doi.org/10.1016/j.optlastec.2019.105581.
- Yang, C. H., & Chien, Y. S. (2020). FPGA implementation and design of a hybrid chaos-AES color image encryption algorithm. Symmetry, 12(2), 189. https://doi.org/10.3390/sym12020189.
- Zhang, Y. Q., He, Y., Li, P., & Wang, X. Y. (2020). A new color image encryption scheme based on 2DNLCML system and genetic operations. Optics and Lasers in Engineering, 128, Article ID 106040. https://doi.org/10.1016/j.optlaseng.2020.106040.
- Zhang, Y. Q., & Wang, X. Y. (2014). A symmetric image encryption algorithm based on mixed linear–nonlinear coupled map lattice. Information Sciences, 273, 329–351. https://doi.org/10.1016/j.ins.2014.02.156.
- Zhang, Y. Q., & Wang, X. Y. (2015). A new image encryption algorithm based on non-adjacent coupled map lattices. Applied Soft Computing, 26, 10–20. https://doi.org/10.1016/j.asoc.2014.09.039.
- Zhou, Y., Li, C., Li, W., Li, H., Feng, W., & Qian, K. (2021). Image encryption algorithm with circle index table scrambling and partition diffusion. Nonlinear Dynamics, 103(2), 2043–2061. https://doi.org/10.1007/s11071-021-06206-8.