Abstract
The current environment is highly dynamic and undergoing continuous change, and the recent outbreak of the COVID-19 pandemic has shown how firms and governments need to act promptly to face unexpected threats. In this regard, location-based applications have been implemented successfully in China and South Korea, but in some Western countries, serious privacy issues have been raised. With these premises in mind, this paper has the aim of examining the factors that motivate or discourage users to adopt mobile applications able to trace location. The proposed model is based on the combination of the Protection Motivation Theory, the Theory of Planned Behavior, and the Technology Acceptance Model. A variance-based Structural Equations Modeling approach has been used to test the conceptual model using Partial Least Squares (PLS). The findings show that perceived usefulness positively influences attitude. In addition, subjective norms and self-efficacy were found to be the key drivers of the intention to adopt location-based applications, whilst perceived severity emerged as an important barrier. Finally, this study provides empirical evidence for the positive and significant relationship between the intention to use this type of apps and actual behavior. Academic and managerial implications are drawn and future research directions are suggested.
JEL CODES:
1. Introduction
The use of smartphones has increased remarkably in the last decade. In 2011, the global penetration rate as share of the population was less than a 10%, increasing up to 38% in 2018 (Statista, Citation2020a). If we compare the data by countries, in 2018 we find that the median for the ownership rate in the advanced economies was 76% vs. 45% in the emerging ones (Statista, Citation2020b). Consequently, as the use of internet on mobile phones increases, mobile services are expanding through the development of applications for varied purposes, such as mobile banking, mobile commerce, mobile learning, or mobile government, to name a few.
Many of these mobile applications track users’ location to provide a better service (Xu et al., Citation2009) and assist with offering a greater functionality (Shimonski, Citation2015, p. 157). For example, a mobile app with user-generated content that provides information on the quality of restaurants may present suitable information by detecting users’ location and help them find a place to eat around their spot. In some location-based mobile apps (LBMA), disclosing the location is necessary for benefitting from the app service (i.e. if the user needs a transportation service, he/she will have to disclose his/her location to the service provider). Conversely, other LBMA may ask the user for permission to identify his/her location, but this feature won’t be necessary for the app to operate. In these cases, the user can enable location tracking for some other specific services, such as sharing with other users where he/she is located.
Among the potential benefits of LBMA, in the last months, several countries have developed mapping and contact tracing applications because of the COVID-19 pandemic. These apps could help fight the spread of the disease successfully. This has been the case in China and South Korea. In these countries, LBMA might identify citizens who could have been in contact with an individual who tested positive after the interaction, or alert users of potentially risky encounters through location sharing.
Despite the potential benefits, the use of the information recruited through LBMA might bring some adverse effects by jeopardising users’ privacy. In the case of non-government-related apps, privacy concerns emerge when users accept terms and conditions that legitimate the developers to sell their data to third parties. On the other hand, LBMA developed by governments for contact tracing also raise privacy issues regarding the fear of mass digital surveillance, freedom of expression and freedom of association (Amnesty International, Citation2020). Given this predicament, one of the objectives of LBMA designers should be to understand the factors underlying the decision to download and use these apps.
Previous studies have combined the Technology Acceptance Model (TAM) with the Theory of Planned Behaviour (TPB) to examine the predictors of technology adoption (Cheung & Vogel, Citation2013; Lu et al., Citation2009; Shen, Citation2015; Xiong et al., Citation2013). Other, have tested the Protection Motivation Theory (PMT), focusing on users’ privacy protection behaviour (Keith et al., Citation2011; Mohamed & Ahmad, Citation2012; Wottrich et al., Citation2019; Youn, Citation2009). In the present study, we consider both perspectives and test a research model that presents measures from the three theoretical approaches. Our purpose is to examine at the same time the drivers that boost users in the decision to install and use LBMA, and the barriers that prevent them from doing so.
This research aims to contribute to the development of the TAM, the TPB, and the PMT in combination, and to gain insight in the determinants of adopting (or not) LBMA. The existing literature provides insight regarding the behaviour of privacy protection when using these types of apps and services (Keith et al., Citation2011; Wottrich et al., Citation2019) and not enough attention has been given to the behaviour of adopting LBMA by itself. Our research differs from the aforementioned, and attempts to contribute to the literature by improving the understanding about the drivers and barriers of LBMA adoption. It stems from interest in the actual context of smartphone usage where tracing applications are becoming a habit for users.
In pursuing this aim, we conducted an online questionnaire amongst smartphone or tablet users (n = 820). We adopted a variance-based structural equation modelling approach, namely Partial Least Squares (PLS) modelling, using the software SmartPLS 3.2.7 (Ringle et al., Citation2015) to test the conceptual model and the related hypotheses.
The paper is structured as follows. In the next section, we present the theoretical background that justifies the hypotheses tested. Then, we describe the methodology and data collection approach. We discuss the results and the practical implications for LBMA developers. Finally, we present the conclusions, limitations and future research directions.
2. Theoretical background and hypotheses
In his seminal work, Davis (Citation1989) developed the TAM inspired by the Theory of Reasoned Action (TRA) (Fishbein & Ajzen, Citation1975) and the TPB (Ajzen, Citation1991). The TRA had the aim to predict behavioural intention through two key determinants (i.e. attitude and subjective norms). The TPB extended the TRA by examining how attitudes, subjective norms, and perceived behavioural control influence intentions to perform a particular behaviour. It also corroborated the positive relationship between intention and actual behaviour.
The TAM added two constructs to the external variables included in the TPB for predicting workers’ acceptance of electronic mail systems in their jobs: perceived usefulness and perceived ease of use (Malhotra & Galletta, Citation2005; Venkatesh & Davis, Citation2000). These variables are related to Bandurás (1982) research on self-efficacy, which suggests that perceived ease of use and perceived usefulness serve as predictors of users’ behaviour. It also has roots in the cost-benefit paradigm. There is a trade-off between the cost and the effort required to accept a new technology (perceived ease of use), and the subjective benefits (perceived usefulness) of doing so.
The first theoretical extension of this model, the TAM2, introduces other determinants of behavioural intention in the original approach, such as subjective norms, derived from the TPB (Venkatesh & Davis, Citation2000). The inclusion of this variable seeks to reflect the effect that social influence processes may have on the adoption of a new technology, even when the user is not favourable to it. In this research, the authors posit that users may internalise subjective norms, transforming their unfavourable beliefs toward the potential usefulness of a given technology and finally adopting it.
Since the TAM was developed to explain the factors determining the adoption of a technology (Davis, Citation1989), its acceptance has been wide. Recent research tests TAM in diverse areas, proving its relevance in the adoption of new learning technologies (Abdullah & Ward, Citation2016; Scherer et al., Citation2019; Šumak et al., Citation2011), mobile commerce (Pipitwanichakarn & Wongtada, Citation2019; Salimon et al., Citation2017), and mobile applications (Min et al., Citation2019; Rafique et al., Citation2020; Shen, Citation2015) to name a few.
Previous research has tested the TAM in combination with other constructs such as self-efficacy to predict the intention to use location-based services (Keith et al., Citation2011). Rogers (Citation1975) introduced the concept of self-efficacy in the PMT. This theory assumes that individuals are motivated to protect themselves when facing a threat (Youn, Citation2005). It seeks to examine the cognitive processes that occur when individuals face a threat. These processes are based on individuals’ perception of the threat itself (threat appraisal) and their ability to protect themselves from the threat (coping appraisal). The coping appraisal is represented by two factors: the response efficacy or the effectiveness of the recommended behaviour to remove the threat; and the self-efficacy, or the belief in onés ability to perform a protective behaviour. The threat appraisal is represented by two other constructs: perceived vulnerability, meaning the perceived probability of being harmed by the threat; and perceived severity, which refers to the perceived degree of harm that the subject will suffer (Bandura, Citation1997; Maddux & Rogers, Citation1983).
The PMT has been tested to understand privacy concerns related with the use of social networking sites (Mohamed & Ahmad, Citation2012), home wireless security (Woon et al., Citation2005), and mobile apps (Wottrich et al., Citation2019), among others. Our study differs from the aforementioned as we study not the behaviour of privacy protection itself, but the use of LBMA that may generate privacy concerns. Hence, we focus on the decision to install mobile apps that will track users’ location and their capacity to change settings established by default.
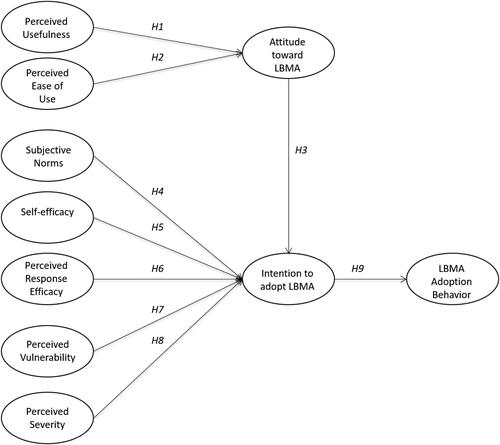
For this purpose, we present a structural equation model that builds on the TPB for the scales of attitude, subjective norms and behavioural intention, on the TAM2 for the scales of perceived usefulness and perceived ease of use, and on the PMT for the scales of perceived vulnerability, perceived severity, response efficacy, and self-efficacy.
2.1. Drivers for the adoption of LBMA
2.1.1. Perceived usefulness, perceived ease of use and attitude
The TAM is built upon two main variables that determine the adoption of a technology. These variables are perceived usefulness and perceived ease of use (Davis, Citation1989). On the one hand, perceived usefulness refers to users’ recognition that a given technology will help perform a concrete task (Davis, Citation1989). In the LBMA context, it could refer to any of the purposes that the applications have such as finding restaurants in a particular area, or tagging your location so your friends can know where you are. On the other hand, perceived ease of use is defined as ‘the degree to which a person believes that using a particular system would be free of effort’ (Davis, Citation1989, p. 320). In our study, this variable means that users identify a low or free effort from using a LBMA. If they perceive the app is easy to use, they will be more likely to adopt it.
This model of technology adoption (TAM) has been tested in diverse contexts. A study conducted in Hong Kong examined the influence of perceived ease of use and perceived usefulness in the adoption of Internet banking (Yiu et al., Citation2007). More specifically, in the context of mobile devices and due to the rapid development of smartphones, personal digital assistants (PDAs), wireless tablets, and laptop computers, both the perceived ease of use and perceived usefulness have been tested as determinants of the acceptance of mobile payment systems (Liébana-Cabanillas et al., Citation2017). Likewise, perceived ease of use influences the adoption of e-learning such as Massive Open Online Courses (Wu & Chen, Citation2017). Perceived usefulness seems to determine the intention to use mobile internet (Alalwan et al., Citation2018), the attitude toward the adoption of mobile applications (Shen, Citation2015), mobile wallets (Shin, Citation2009), and toward the use of online travel sites (Muñoz et al., Citation2012), and it plays a role in whether users share their locations (Chang & Chen, Citation2014; Tsai et al., Citation2009).
Consequently, users who perceive that using an LBMA will help them in their goals will be more likely to have a positive attitude toward its adoption. If they perceive the application as useful for their everyday lives, they will have a positive attitude toward using it. Likewise, if they perceive that the application is easy to use, they will have a positive attitude toward its adoption.
H1: Perceived usefulness positively influences users' attitude toward adopting the LBMA.
H2: Perceived ease of use positively influences users’ attitude toward adopting the LBMA.
Previous studies have tested the TAM adding attitude as a precedent of behavioural intention based on the TPB (Cheung & Vogel, Citation2013; Shen, Citation2015; Xiong et al., Citation2013). Ha and Stoel (Citation2009) conducted an online survey with college students to examine the factors that affect consumer acceptance of e-shopping. They integrated several factors into a TAM and found that attitude influenced behavioural intention toward e-shopping. Xiong et al. (Citation2013) collected data from small businesses in China and found a group of variables that determined ICT acceptance and the effects on business development. They found that attitude positively influences the intention to adopt ICT by small business owners. In another paper, Tsai et al. (Citation2009) found that individuals’ attitude determined whether they shared their spots in location-based services. Other studies confirmed the relationship between attitude and the intention to disclose users’ location in social networks (Chang & Chen, Citation2014; Koohikamali et al., Citation2015). In our study, attitude refers to the extent to which a potential user is interested in adopting an LBMA. Considering the relationship that attitude and intention have demonstrated in previous research, we posit that if a potential LBMA user has a positive attitude toward the app, he/she will intend to use it.
H3: Attitude positively influences users’ intention of adopting the LBMA.
2.1.2. Subjective norms
This variable is included as a predictor of behavioural intention in the TPB (Ajzen, Citation1991), which posits that an individual would decide to perform a behaviour or not, influenced by his perception of what his referents think about the behaviour itself. If he thinks that his referents support this behaviour, he will be predisposed to perform it.
In the specific context of technology acceptance, subjective norms or social influence would refer to users’ perception that most people who are important to them think they should or should not adopt the technology (Xiong et al., Citation2013). Koohikamali et al. (Citation2015) conducted a study with active online location-based social network apps users. They found a positive effect of subjective norms and attitudes on location disclosure through this type of applications.
Theoretical extensions of the TAM, such as TAM2 have included subjective norms as a determinant in the equation, adapted from the TPB (Schepers & Wetzels, Citation2007; Venkatesh & Davis, Citation2000). Later on, Cheung and Vogel (Citation2013) examined the effect of this variable in the intention to adopt collaborative learning technologies. Regarding location-based services, Zhou (Citation2012) conducted a study with actual users recruited through two telecommunication operators in China and finds that subjective norms play a key role in the intention to use location-based services. Later on, Chang and Chen (Citation2014) examined the factors that determine the disclosure of location-related information on Facebook and the results show that subjective norms also have a positive effect on the intention to disclose. Subsequently, in our model, we hypothesise that a potential LBMA user, who perceives that his/her referents, such as friends, family or partners, support the use of the LBMA, will intend to use it.
H4: Subjective norms positively influence users’ intention toward adopting the LBMA.
2.1.3. Self-efficacy
Although PMT has been extensively tested in health-related research (Witte & Allen, Citation2000), in the last decades it has also extended its influence on the technological context. The concept of self-efficacy is a key variable for social change that has been widely studied in social cognitive theory. It refers to individuals’ belief of having the necessary competence to perform a task or succeed in a situation (Bandura, Citation1982; Maddux & Rogers, Citation1983).
In the context of internet use, self-efficacy is defined as ‘the belief in one's capabilities to organize and execute courses of Internet actions required to produce given attainments’ (Hsu & Chiu, Citation2004). More specifically, mobile self-efficacy would refer to onés belief in its own aptitudes to understand and use mobile devices (Keith et al., Citation2011). By extension, LBMA self-efficacy would denote the belief in the capabilities of understanding how to install, use, and eliminate LBMA, turn location tracking on and off, and change features and defaults in the app.
Chiu and Wang (Citation2008) conducted an online survey with students who had taken Web-based courses and found that self-efficacy was positively related to Web-based learning continuance. In a similar context, Cheung and Vogel (Citation2013) examined the factors that affect the acceptance of Google applications for collaborative learning. They find that self-efficacy has a positive effect on the intention to use the system. Other studies shows that self-efficacy beliefs related with protection measures are positively related to the intention to adopt safe behaviours online (LaRose et al., Citation2005; Lee et al., Citation2008). Consequently, as the relationship between self-efficacy and intention has been well established in previous research, we hypothesise that users who believe in their own capacities to understand and use LBMA, will intend to use them.
H5: Self-efficacy positively influences users’ intention toward adopting the LBMA.
2.1.4. Perceived response efficacy
This measure refers to whether individuals believe that a recommended course of action will be effective in protecting them from a threat (van Bavel et al., Citation2019; Woon et al., Citation2005). Previous research has found that perceived response efficacy is positively related with the backing up of data for computer users (Crossler, Citation2010). In another study, Chenoweth et al. (Citation2009) conducted a survey with undergraduate students and found that response efficacy influences the intention to use anti-spy software as a protective behaviour. It also has a positive effect on the intention to use strong passwords (Zhang & McDowell, Citation2009). However, Mohamed and Ahmad (Citation2012) found no relationship with privacy concerns on social networking sites.
In this study, we refer to perceived response efficacy as individuals’ beliefs about the use, advantages, and disadvantages of LBMA. For example, if subjects think that not using or eliminating LBMA from their smartphones will have too many disadvantages for them; if they get frustrated when they try to change defaults; or if they think that it takes too long to learn how to do it; they will have a lower perceived response efficacy. Hence, we hypothesise that users who think they are able to protect themselves from potential threats confronted when using LBMA, will intend to adopt them.
H6: Perceived response efficacy positively influences users’ intention toward adopting the LBMA.
2.2. Barriers for the adoption of LBMA
2.2.1. Perceived vulnerability
This construct refers to the perceived likelihood of being affected by a threat. Previous research has linked perceived vulnerability with the backing up of data in computers (Crossler, Citation2010). It increases the intention to adopt virus protection behaviour (Lee et al., Citation2008) and the intention to use anti-spy software as a protective technology (Chenoweth et al., Citation2009). In the context of privacy, this variable has been positively related with Internet privacy concerns (Dinev & Hart, Citation2004). More specifically, Mohamed and Ahmad (Citation2012) conducted a survey in a Malaysian university and found perceived vulnerability to be an antecedent of information privacy concerns with social networking sites. Finally, in a recent study, Wottrich et al. (Citation2019) examined how protection motivation theory-related variables may have an effect on the privacy protection intention in relation to mobile apps. Their results showed a positive effect of perceived vulnerability. Hence, we posit that LBMA potential users, who perceive they could be affected negatively by this type of apps, would be less willing to adopt them.
H7: Perceived vulnerability negatively influences users’ intention toward adopting the LBMA.
2.2.2. Perceived severity
When confronted with a threat, individuals consider how dangerous its consequences are likely to be. If they perceive a greater threat, they would be more likely to adopt protective behaviours (LaRose et al., Citation2005). In a study on anti-spy software, Chenoweth et al. (Citation2009) found that perceived severity is related with the intention to use these systems as a protective technology. Likewise, Crossler (Citation2010) showed the link between perceived severity and the backing up of data for computer users. It also positively influences privacy concerns on social networking sites (Mohamed & Ahmad, Citation2012). In a later study, Wang et al. (Citation2016) found that perceived severity influences perceived risk, and this last one, at the same time, determines the intention to disclose information via mobile applications.
Disclosing our location is, in a sense, a way of revealing our private information. If a potential user of an LBMA perceives there is a threat in downloading, installing, or using the app, and he/she perceives the consequences might be severe, it should negatively affect the intention to adopt it.
H8: Perceived severity negatively influences users’ intention toward adopting the LBMA.
2.3. Behavioural intention and usage of LBMA
A vast body of literature on behaviour has focused on predicting intention rather than behaviour itself (Cheon et al., Citation2012; Kang et al., Citation2015; Natarajan et al., Citation2017; Zhou, Citation2012). However, the relationship between intention and behaviour is well established in the scientific community. Beginning with the development of the TPB conducted by Ajzen (Citation1991), which states that behavioural intention shapes actual behaviour. Later on, in one of the TAM extensions, Venkatesh et al. (Citation2003) also proved that behavioural intention has a positive significant influence on technology usage. Regarding location-based services, Keith et al. (Citation2013) found that the intention to disclose information determines behaviour in the context of mobile applications. Specifically, intention positively influences the behaviour of providing information during the registration process, using location services, storing credits cards and sharing their profile. In another study, the authors found a positive relationship between the intention and the behaviour of using tourism mobile apps (Xu et al., Citation2019). Therefore, we propose that individuals who have the intention to adopt LBMA will finally perform this behaviour.
H9: Behavioural intention positively influences users’ behaviour of adopting the LBMA.
3. Methodology
3.1. Data collection
In this study, we have opted for the collection of primary data using an online questionnaire that was administered in Spain amongst smartphone or tablet users. A market research company recruited the sample in October 2019 through an email-invitation-only process. In order to be eligible, the target population of the study needed to be over 18 years old and smartphone or tablet users, as location-mobile apps had to be installed in these types of mobile devices. Moreover, the market research company had to follow some instructions to ensure the representativeness of the sample. In this regard, based on the The App Date report (Statista, Citation2014), which is to the best of our knowledge the most recent report analysing the age of the users of smartphones in Spain, we asked the market research company to collect the data according to the following distribution in terms of percentage for each age range: 15% for the 18–24, 39% for the 25–34, 26% for the 35–44, 12% for the 45–55 years and 8% for the over 56 years old users. Furthermore, to check the quality of the data, the market research company deleted all the questionnaires completed in less than 8 minutes, which was calculated by the company as the minimum amount of time needed to respond to the posed questions. Regarding the data collection procedures, the market research company randomly distributed invitations to the members of the panel that met the requirements to participate in the study and a link to the survey. It must be acknowledged that the participants recruited by the market research company were rewarded for their participation in the study, earning points they could redeem for gift cards to purchase products or services provided by different brands. Finally, a total of 820 valid and fully completed responses were received. shows the descriptive statistics of the sample.
Table 1. Descriptive statistics.
3.2. Measures
The study aimed to measure the relationship between attitude, subjective norms, self-efficacy, perceived response efficacy, perceived vulnerability, perceived severity, and the intention to adopt LBMA, as well as whether intention determines the behaviour of adopting LBMA. It also measures the relationship between perceived usefulness, perceived ease of use, and attitude.
As shown in Annex 1 (Supplementary material), the reliable measurement items were drawn from the literature review and some of them were adapted to the LBMA context by specifying the LBMA as the object taken under consideration. For example, the item SN1 to measure subjective norms reads as follows: ‘My family or friends recommend me to use a LBMA to track my location’. More specifically, the scale for perceived usefulness and perceived ease of use is based on Davis (Citation1989), Venkatesh et al. (Citation2003), and Chang and Chen (Citation2014). To measure attitude, we used three of the items used in Armitage and Conner (Citation2001), Venkatesh et al. (Citation2003), Chang and Chen (Citation2014), and Wottrich et al. (Citation2019). Subjective norm is measured using the scale proposed by Ajzen (Citation2002) and Venkatesh et al. (Citation2003). Perceived severity measurement is adapted from Woon et al. (Citation2005), Crossler (Citation2010), and Mohamed and Ahmad (Citation2012). The scale for perceived vulnerability is adapted from Youn (Citation2009). To assess self-efficacy we opted for a scale based on Woon et al. (Citation2005), LaRose and Rifon (Citation2007) and Crossler (Citation2010). The perceived response efficacy scale is adapted from Wottrich et al. (Citation2019). Finally, the scale for behavioural intention is based on Ajzen (Citation2002), and the measure used by Chang and Chen (Citation2014) served to measure the behaviour of using LBMA.
3.3. Data analysis
The Structural Equation Modelling (SEM) method has been adopted to validate the proposed research model and test the hypotheses. In this regard, there are two alternative approaches, namely covariance- and variance-based SEM, the latter being recently improved and is now considered a very robust analytical method. More specifically, Partial Least Squares (PLS; Chin, Citation1998; Lohmöller, Citation1989) path modelling is the most prominent variance-based SEM method and considered a ‘silver bullet’ by Hair et al. (Citation2011). It must be acknowledged that analysts have traditionally criticised the use of PLS for its lack of consistency. To cope with this, Dijkstra and Henseler (Citation2015) have provided key improvements via the introduction of consistent PLS (PLSc), which enables the PLS to be ‘a full-fledged structural equation modeling approach’ (Henseler et al., Citation2016). In fact, by applying the PLSc estimates approach, true values asymptotically, non-recursive models can be estimated, and a global assessment of goodness-of-fit is obtained.
With these premises in mind, in this study, we have opted for the application of the PLS SEM using SmartPLS (Ringle et al., Citation2015) using the PLSc approach. All the variables included in the model were specified as first-order reflective constructs. The bootstrap technique has been used to estimate the significance of weights, loadings, and path coefficients. In this regard, a consistent bootstrap analysis has been performed with 5000 subsamples. Moreover, the blindfolding procedure has been used to assess the predictive relevance of the analysis. First, the measurement model (see ) was evaluated to analyse the psychometric properties of the measurement scales; second, the research hypotheses were tested by estimating the structural model (see ).
Table 2. Results of the measurement (outer) model.
4. Results
4.1. Measurement model assessment and scale validation
The results of the measurement model (see ) showed that all standardised coefficients were statistically significant (p < .01) and exceeded the more conservative .707 cut-off (Chin, Citation2010), except for PVUL3 (β PVUL3 = .66), SELF2 (β SELF2 = .65), REFF3 (β REFF3 = .68) and BEHAV3 (β BEHAV3 = .56), which were above the less conservative threshold of .5. Moreover, Cronbach’s α scores and Composite Reliability (CR) exceed the recommended cut-off of .8 and .7, respectively, in all cases. These findings provide evidence for the reliability of the measures. To assess convergent validity, the Average Variance Extracted (AVE) was calculated for all the constructs and exceeded the recommended cut-off of .5 for all cases, thus proving adequate convergence validity. The criterion proposed by Fornell and Larcker (Citation1981) was applied to test the discriminant validity. The results (see ) show that the square root of AVE was greater than the correlation shared among the constructs, except for one pair of constructs, namely perceived usefulness and perceived ease of use. Thus, to further evaluate discriminant validity, the Heterotrait-Monotrait (HTMT) ratio (Henseler et al., Citation2015) has been computed (see ) for each pair of constructs on the basis of the item correlations. The computation yielded values meeting the most conservative requirement (HTMT < .85) in all cases, except for the pair ‘perceived usefulness, perceived ease of use’ (HTMT = .871), which met the less conservative criterion (HTMT< .90). Therefore, statistical proof for discriminant validity of the measurement scales has been provided.
Table 3. Square root of AVE and correlations between constructs (Fornell & Larcker, Citation1981).
Table 4. Heterotrait-Monotrait (HTMT) ratios.
4.2. Structural (inner) model assessment and hypotheses testing
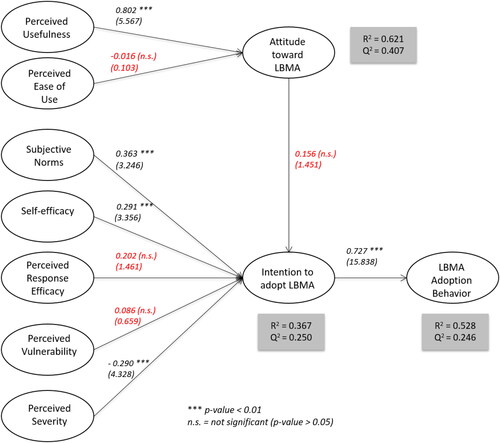
Once the psychometric properties of the scales were assessed, the structural (inner) model has been estimated with PLSc to test the research hypotheses. The findings (see ) showed that the model had an adequate goodness-of-fit (SRMR= .070) and suggested that perceived usefulness was positively and significantly related to the attitude toward the adoption of LBMA (βpuseful→att = .80; t = 5.57, p < .01), thus H1 gathered statistical support. On the contrary, the relationship between perceived ease of use and attitude (βpeasy→att = −.02; t = .103, p > .05) and between attitude and intention to adopt LBMA (βatt→int = .0.2; t = 1.451, p > .05) were found to be insignificant, thus H2 and H3 are not statistically supported and were rejected.
In regard to the drivers of the intention to adopt LBMA, subjective norms (βsn→int = .36; t = 3.246, p < .01) and self-efficacy (βself→int = .29; t = 3.356, p < .01) were found to be positively and strongly related to the intention to adopt LBMA, providing empirical evidence to support H4 and H5. On the contrary, the findings suggest that the relationship between perceived response efficacy and intention is positive but lacks statistical significance (βreff→int = .20; t = 1.461, p > .05), hence H6 has to be rejected.
Among the barriers that hinder the intention to adopt LBMA, perceived severity was found to be negatively and significantly related to intention (βpsev→int= −.29; t = 4.328, p < .01), while the link between perceived vulnerability and intention appeared to be insignificant (βpeasy→att = .09; t = .659, p > .05). Based on these findings, H8 gathered statistical support, while H7 had to be rejected.
Moreover, the intention to adopt LBMA was found to be strongly, positively and significantly related to the behaviour of adopting LBMA (βpeasy→att = .73; t = 15.838, p < 0.01), thus H9 gathered empirical support.
Following Chin (Citation2010), the magnitude of the R2 was assessed as a criterion of explanatory power, R2 values of .67, .33 and .19 indicating substantial, moderate and weak explanatory power, respectively. The results show moderate explanatory power, with the R2 values ranging between .36 and .62. Finally, to determine the predictive relevance of the analysis, the Stone-Geisser’s Q2 test has been executed. The blindfolding procedures enabled to obtain the Q2 values, which were all greater than zero, thus suggesting a good explanatory power for the model assessed (see ).
5. Discussion and implications
The objective of this study was to examine the drivers and barriers of the decision to install and use LBMA. For this purpose, we developed and tested a conceptual model based on the TAM, the TPB, and the PMT. The results partially demonstrate the TAM, as perceived usefulness had a positive influence on attitude toward adopting LBMA, but perceived ease of use didn’t show a significant effect. Previous TAM-related studies have found similar results, as the correlations and path coefficients are usually higher for relationships with perceived usefulness than with perceived ease of use. This might be related to the reduced perceived ease of use post-implementation effects, which happens when users have more experience with the system (Venkatesh et al., Citation2003, Schepers & Wetzels, Citation2007). In contrast, Chang and Chen (Citation2014) only tested the effect of perceived usefulness on intention, leaving perceived ease of use outside the model. In any case, the effect of perceived usefulness on attitude gets blurred in the model we present here, as attitude was not a significant determinant of the intention to adopt LBMA.
Second, regarding the drivers to adopt this type of apps, we found that subjective norms have a positive influence on intention. These results support the findings by Zhou (Citation2012), and Chang and Chen (Citation2014), which indicate that people will be more likely to download and install LBMA if their family and friends do so. Consequently, if the potential user thinks that an important person or group of people for him/her would approve the behaviour of adopting LBMA, he/she would be more likely to adopt it. Likewise, self-efficacy seems to play a role in the intention to adopt LBMA. It means that subjects who believe in their abilities to control and execute the applications and its features, will have a higher probability to adopt them. This result goes in line with previous research findings revealing that this construct is a determinant of the intention to adopt safe behaviours when online or while using mobile apps, such as privacy protection (Korzaan & Boswell, Citation2008; LaRose et al., Citation2005; Lee et al., Citation2008; Mohamed & Ahmad, Citation2012; Wottrich et al., Citation2019).
Third, we found perceived severity to be a barrier for the intention to adopt this type of mobile apps that trace location. This means that the subjects who perceived a greater threat from LBMA will be more reluctant to disclose their location through them. Previous research has found perceived severity to have an effect on users intending to protect themselves from potential threats (Chenoweth et al., Citation2009; Crossler, Citation2010; LaRose et al., Citation2005; Mohamed & Ahmad, Citation2012). Thus, our results provide support by extending the influence of this construct to the context of LBMA. Since self-efficacy and perceived severity have an effect on intention, both threat and the coping appraisal of PMT are partially corroborated. This result follows previous research where threat and cope increase secure online behaviour (van Bavel et al., Citation2019).
Finally, intention had a positive influence on LBMA adoption behaviour. This result was as expected and it is relevant, as most of the previous studies related with mobile applications and services adoption do not measure the relationship between intention and behaviour (Fodor & Brem, Citation2015; Kang et al., Citation2015; Wottrich et al., Citation2019).
Our findings have some implications for LBMA developers that aim to implement these types of apps and governments interested in promoting them to combat the spread of COVID-19, or any other types of applications whether private or public (e.g., applications that can be used to provide information to citizens or to public and private institutions on traffic density or mobility). However, we must be cautious when interpreting the results, as the data were collected before the pandemic and are not specific for COVID-related apps.
Regarding the potential implications, first, to fight the barriers that prevent potential users from downloading and installing LBMA, developers should pay attention to private information stealing concerns by increasing the level of protection that can be ensured. In addition, knowing that users’ perception of this protection has an important role, the applications could provide an initial message confirming the codification and encrypting of the information that is delivered through the apps.
On the other hand, companies and governments interested in promoting LBMA, should focus on the effect that friends and family may have on users, redirecting the efforts on advertising and marketing in this way. With the same purpose, app developers should contemplate the design of a user-friendly environment in which it would be easy to install and remove the applications, turn the location tracker on and off, as well as reduce the number of clicks to access features and change defaults.
6. Limitations and suggestions for future research
This study has some limitations. First, the purpose or use of each mobile application may have an effect on its acceptance; however, the questions included in the survey do not make a differentiation that could provide further information on this matter. Mobile applications that trace location with the objective of entertaining the user could have different barriers and drivers for adoption compared to health-related LBMA, such as COVID-19 apps.
Second, we measured the reported behaviour instead of the behaviour itself, which is usual when conducting surveys, but it does not always ensure that individuals will behave in this way when they have to make a decision.
Third, the data were collected before the COVID-19 outbreak, thus the results might not reflect the relevance that LBMA have during the pandemic for Spanish users. In this regard, future research is called for to look into the current pandemic context and analyse whether consumers’ attitudes and behaviours have changed due to this health emergency.
Hence, considering these limitations, future research should make a distinction focusing on the objective of the mobile app under study. In addition, we encourage future research to conduct behavioural experiments about this issue, as this type of method allowed the researcher to recruit information on actual instead of reported behaviour, which is an advantage.
Supplemental Material
Download MS Word (16.3 KB)Disclosure statement
No potential conflict of interest was reported by the authors.
Additional information
Funding
References
- Abdullah, F., & Ward, R. (2016). Developing a General Extended Technology Acceptance Model for E-Learning (GETAMEL) by analysing commonly used external factors. Computers in Human Behavior, 56, 238–256. https://doi.org/10.1016/j.chb.2015.11.036
- Ajzen, I. (1991). The theory of planned behavior. Organizational Behavior and Human Decision Processes, 50(2), 179–211. https://doi.org/10.1016/0749-5978(91)90020-T
- Ajzen, I. (2002). Constructing a TPB questionnaire: Conceptual and methodological considerations. https://bit.ly/2pErhPf
- Alalwan, A. A., Baabdullah, A. M., Rana, N. P., Tamilmani, K., & Dwivedi, Y. K. (2018). Examining adoption of mobile internet in Saudi Arabia: Extending TAM with perceived enjoyment, innovativeness and trust. Technology in Society, 55, 100–110. https://doi.org/10.1016/j.techsoc.2018.06.007
- Amnesty International. (2020). Joint statement: States use of digital surveillance technologies to fight pandemic must respect human rights. Retrieved May 10, 2020, from https://www.amnesty.org/en/documents/pol30/2081/2020/en/
- Armitage, C. J., & Conner, M. (2001). Efficacy of the theory of planned behaviour: A meta‐analytic review. British Journal of Social Psychology, 40(4), 471–499. https://doi.org/10.1348/014466601164939
- Bandura, A. (1982). Self-efficacy mechanism in human agency. American Psychologist, 37(2), 122–147. https://doi.org/10.1037/0003-066X.37.2.122
- Bandura, A. (1997). Self-efficacy: The exercise of Control. W.H. Freeman.
- Chang, C. W., & Chen, G. M. (2014). College students’ disclosure of location-related information on Facebook. Computers in Human Behavior, 35, 33–38. https://doi.org/10.1016/j.chb.2014.02.028
- Chenoweth, T., Minch, R., & Gattiker, T. (2009, January). 2009 42nd Hawaii International Conference on System Sciences, Application of protection motivation theory to adoption of protective technologies (pp. 1–10). IEEE.
- Cheon, J., Lee, S., Crooks, S. M., & Song, J. (2012). An investigation of mobile learning readiness in higher education based on the theory of planned behavior. Computers & Education, 59(3), 1054–1064. https://doi.org/10.1016/j.compedu.2012.04.015
- Cheung, R., & Vogel, D. (2013). Predicting user acceptance of collaborative technologies: An extension of the technology acceptance model for e-learning. Computers & Education, 63, 160–175. https://doi.org/10.1016/j.compedu.2012.12.003
- Chin, W. W. (1998). The partial least squares approach to structural equation modeling. Modern Methods for Business Research, 295(2), 295–336.
- Chin, W. W. (2010). How to write up and report PLS analyses. In V. Esposito Vinzi, W. W. Chin, J. Henseler, & H. Wang (Eds.), Handbook of partial least squares: Concepts, methods and applications (pp. 655–690). Springer Handbooks of Computational Statistics.
- Chiu, C. M., & Wang, E. T. (2008). Understanding Web-based learning continuance intention: The role of subjective task value. Information & Management, 45(3), 194–201. https://doi.org/10.1016/j.im.2008.02.003
- Crossler, R. E. (2010, January). Protection motivation theory: Understanding determinants to backing up personal data [Paper presentation]. 2010 43rd Hawaii International Conference on System Sciences (pp. 1–10). IEEE. https://doi.org/10.1109/HICSS.2010.311
- Davis, F. D. (1989). Perceived usefulness, perceived ease of use, and user acceptance of information technology. MIS Quarterly, 13(3), 319–340. https://doi.org/10.2307/249008
- Dijkstra, T. K., & Henseler, J. (2015). Consistent partial least squares path modeling. MIS Quarterly, 3(2), 297–316.
- Dinev, T., & Hart, P. (2004). Internet privacy concerns and their antecedents-measurement validity and a regression model. Behaviour & Information Technology, 23(6), 413–422. https://doi.org/10.1080/01449290410001715723
- Fishbein, M., & Ajzen, I. (1975). Belief, attitude, intention and behavior: An introduction to theory and research. Addison-Wesley.
- Fodor, M., & Brem, A. (2015). Do privacy concerns matter for Millennials? Results from an empirical analysis of location-based services adoption in Germany. Computers in Human Behavior, 53, 344–353. https://doi.org/10.1016/j.chb.2015.06.048
- Fornell, C., & Larcker, D. F. (1981). Evaluating structural equation models with unobservable variables and measurement error. Journal of Marketing Research, 18(1), 39–50. https://doi.org/10.1177/002224378101800104
- Ha, S., & Stoel, L. (2009). Consumer e-shopping acceptance: Antecedents in a technology acceptance model. Journal of Business Research, 62(5), 565–571. https://doi.org/10.1016/j.jbusres.2008.06.016
- Hair, J. F., Ringle, C. M., & Sarstedt, M. (2011). PLS-SEM: Indeed a silver bullet. Journal of Marketing Theory and Practice, 18 (2), 139–152.
- Henseler, J., Hubona, G., & Ray, P. A. (2016). Using PLS path modeling in new technology research: Updated guidelines. Industrial Management & Data Systems, 116 (1), 2–20. https://doi.org/10.1108/IMDS-09-2015-0382
- Henseler, J., Ringle, C. M., & Sarstedt, M. (2015). A new criterion for assessing discriminant validity in variance-based structural equation modeling. Journal of the Academy of Marketing Science, 43 (1), 115–135. https://doi.org/10.1007/s11747-014-0403-8
- Hsu, M. H., & Chiu, C. M. (2004). Internet self-efficacy and electronic service acceptance. Decision Support Systems, 38(3), 369–381. https://doi.org/10.1016/j.dss.2003.08.001
- Kang, J. Y. M., Mun, J. M., & Johnson, K. K. (2015). In-store mobile usage: Downloading and usage intention toward mobile location-based retail apps. Computers in Human Behavior, 46, 210–217. https://doi.org/10.1016/j.chb.2015.01.012
- Keith, M. J., Babb, J. S., Jr., Furner, C. P., & Abdullat, A. (2011, January). The role of mobile self-efficacy in the adoption of location-based applications: An iPhone experiment. In 2011 44th Hawaii International Conference on System Sciences (pp. 1–10). IEEE.
- Keith, M. J., Thompson, S. C., Hale, J., Lowry, P. B., & Greer, C. (2013). Information disclosure on mobile devices: Re-examining privacy calculus with actual user behavior. International Journal of Human-Computer Studies, 71(12), 1163–1173. https://doi.org/10.1016/j.ijhcs.2013.08.016
- Koohikamali, M., Gerhart, N., & Mousavizadeh, M. (2015). Location disclosure on LB-SNAs: The role of incentives on sharing behavior. Decision Support Systems, 71, 78–87. https://doi.org/10.1016/j.dss.2015.01.008
- Korzaan, M. L., & Boswell, K. T. (2008). The influence of personality traits and information privacy concerns on behavioral intentions. Journal of Computer Information Systems, 48(4), 15–24.
- LaRose, R., & Rifon, N. J. (2007). Promoting i‐safety: Effects of privacy warnings and privacy seals on risk assessment and online privacy behavior. Journal of Consumer Affairs, 41(1), 127–149. https://doi.org/10.1111/j.1745-6606.2006.00071.x
- LaRose, R., Rifon, N., Liu, S., & Lee, D. (2005, May). Understanding online safety behavior: A multivariate model. In the 55th Annual Conference of the International Communication Association, New York city.
- Lee, D., Larose, R., & Rifon, N. (2008). Keeping our network safe: A model of online protection behaviour. Behaviour & Information Technology, 27(5), 445–454. https://doi.org/10.1080/01449290600879344
- Liébana-Cabanillas, F., Ramos de Luna, I., & Montoro-Ríos, F. (2017). Intention to use new mobile payment systems: A comparative analysis of SMS and NFC payments. Economic research-Ekonomska Istraživanja, 30(1), 892–910. https://doi.org/10.1080/1331677X.2017.1305784
- Lohmöller, J. B. (1989). Latent variable path modeling with partial least squares. Physica-Verlag.
- Lu, Y., Zhou, T., & Wang, B. (2009). Exploring Chinese users’ acceptance of instant messaging using the theory of planned behavior, the technology acceptance model, and the flow theory. Computers in Human Behavior, 25(1), 29–39. https://doi.org/10.1016/j.chb.2008.06.002
- Maddux, J. E., & Rogers, R. W. (1983). Protection motivation and self-efficacy: A revised theory of fear appeals and attitude change. Journal of Experimental Social Psychology, 19(5), 469–479. https://doi.org/10.1016/0022-1031(83)90023-9
- Malhotra, Y., & Galletta, D. (2005). A multidimensional commitment model of volitional systems adoption and usage behavior. Journal of Management Information Systems, 22(1), 117–151. https://doi.org/10.1080/07421222.2003.11045840
- Marakas, G., Johnson, R., & Clay, P. F. (2007). The evolving nature of the computer self-efficacy construct: An empirical investigation of measurement construction, validity, reliability and stability over time. Journal of the Association for Information Systems, 8(1), 16–46. https://doi.org/10.17705/1jais.00112
- Min, S., So, K. K. F., & Jeong, M. (2019). Consumer adoption of the Uber mobile application: Insights from diffusion of innovation theory and technology acceptance model. Journal of Travel & Tourism Marketing, 36(7), 770–783. https://doi.org/10.1080/10548408.2018.1507866
- Mohamed, N., & Ahmad, I. H. (2012). Information privacy concerns, antecedents and privacy measure use in social networking sites: Evidence from Malaysia. Computers in Human Behavior, 28(6), 2366–2375. https://doi.org/10.1016/j.chb.2012.07.008
- Muñoz, F. L., Hernandez-Mendez, J., & Sanchez-Fernandez, J. (2012). Generalising user behavior in online travel sites through the travel 2.0 website acceptance model. Online Information Review, 36, 879–902.
- Natarajan, T., Balasubramanian, S. A., & Kasilingam, D. L. (2017). Understanding the intention to use mobile shopping applications and its influence on price sensitivity. Journal of Retailing and Consumer Services, 37, 8–22. https://doi.org/10.1016/j.jretconser.2017.02.010
- Pipitwanichakarn, T., & Wongtada, N. (2019). Leveraging the technology acceptance model for mobile commerce adoption under distinct stages of adoption. Asia Pacific Journal of Marketing and Logistics. https://doi.org/10.1108/APJML-10-2018-0448
- Rafique, H.,Almagrabi, A. O.,Shamim, A.,Anwar, F., &Bashir, A. K. (2020). Investigating the Acceptance of Mobile Library Applications with an Extended Technology Acceptance Model (TAM). Computers & Education, 145, 103732. https://doi.org/10.1016/j.compedu.2019.103732
- Ringle, C. M., Wende, S., & Becker, J.-M. (2015). SmartPLS 3. SmartPLS GmbH. http://www.smartpls.com
- Rogers, R. W. (1975). A protection motivation theory of fear appeals and attitude change1. The Journal of Psychology, 91(1), 93–114. https://doi.org/10.1080/00223980.1975.9915803
- Salimon, M., Bamgbade, J., Nathaniel, A., & Adekunle, T. (2017). Integrating technology acceptance model and organizational innovativeness in the adoption of mobile commerce. Management Science Letters, 7(10), 497–512.
- Schepers, J., & Wetzels, M. (2007). A meta-analysis of the technology acceptance model: Investigating subjective norm and moderation effects. Information & Management, 44(1), 90–103. https://doi.org/10.1016/j.im.2006.10.007
- Scherer, R., Siddiq, F., & Tondeur, J. (2019). The technology acceptance model (TAM): A meta-analytic structural equation modeling approach to explaining teachers’ adoption of digital technology in education. Computers & Education, 128, 13–35. https://doi.org/10.1016/j.compedu.2018.09.009
- Shen, G. C. C. (2015). Users' adoption of mobile applications: Product type and message framing's moderating effect. Journal of Business Research, 68(11), 2317–2321. https://doi.org/10.1016/j.jbusres.2015.06.018
- Shimonski, R. (2015). Cyber reconnaissance, surveillance and defense. Syngress.
- Shin, D. H. (2009). Towards an understanding of the consumer acceptance of mobile wallet. Computers in Human Behavior, 25(6), 1343–1354. https://doi.org/10.1016/j.chb.2009.06.001
- Statista. (2014). The App Date. Retrieved September 1, 2020, from https://es.statista.com/estadisticas/493850/edad-del-perfil-de-usuario-de-smartphone-en-espana-2014/
- Statista. (2020a). Global smartphone penetration rate as share of population from 2016 to 2020. Retrieved May 10, 2020, from https://www.statista.com/statistics/203734/global-smartphone-penetration-per-capita-since-2005/
- Statista. (2020b). Smartphone ownership rate by country 2018. Retrieved May 10, 2020, from https://www.statista.com/statistics/539395/smartphone-penetration-worldwide-by-country/
- Šumak, B., Heričko, M., & Pušnik, M. (2011). A meta-analysis of e-learning technology acceptance: The role of user types and e-learning technology types. Computers in Human Behavior, 27(6), 2067–2077. https://doi.org/10.1016/j.chb.2011.08.005
- Tsai, J., Kelley, P. G., Cranor, L. F., & Sadeh, N. (2009). Location-sharing technologies: Privacy risks and controls. In Proceedings of the 37th Research Conference on Communication, Information, and Internet, Arlington, VA.
- van Bavel, R., Rodríguez-Priego, N., Vila, J., & Briggs, P. (2019). Using protection motivation theory in the design of nudges to improve online security behavior. International Journal of Human-Computer Studies, 123, 29–39. https://doi.org/10.1016/j.ijhcs.2018.11.003
- Venkatesh, V., & Davis, F. D. (2000). A theoretical extension of the technology acceptance model: Four longitudinal field studies. Management Science, 46(2), 186–204. https://doi.org/10.1287/mnsc.46.2.186.11926
- Venkatesh, V., Morris, M. G., Davis, G. B., & Davis, F. D. (2003). User acceptance of information technology: Toward a unified view. MIS Quarterly, 27(3), 425–478.
- Wang, T., Duong, T. D., & Chen, C. C. (2016). Intention to disclose personal information via mobile applications: A privacy calculus perspective. International Journal of Information Management, 36(4), 531–542. https://doi.org/10.1016/j.ijinfomgt.2016.03.003
- Witte, K., & Allen, M. (2000). A meta-analysis of fear appeals: Implications for effective public health campaigns. Health Education & Behavior, 27(5), 591–615. https://doi.org/10.1177/109019810002700506
- Wottrich, V. M., van Reijmersdal, E. A., & Smit, E. G. (2019). App users unwittingly in the spotlight: A model of privacy protection in mobile apps. Journal of Consumer Affairs, 53(3), 1056–1083. https://doi.org/10.1111/joca.12218
- Woon, I., Tan, G. W., Low, R. (2005). A protection motivation theory approach to home wireless security. ICIS 2005 Proceedings, 31.
- Wu, B., & Chen, X. (2017). Continuance intention to use MOOCs: Integrating the technology acceptance model (TAM) and task technology fit (TTF) model. Computers in Human Behavior, 67, 221–232. https://doi.org/10.1016/j.chb.2016.10.028
- Xiong, J., Qureshi, S., Najjar, L. (2013). Factors that affect information and communication technology adoption by small businesses in China. Information Systems and Quantitative Analysis Faculty Proceedings & Presentations, 46.
- Xu, F., Huang, S. S., & Li, S. (2019). Time, money, or convenience: What determines Chinese consumers’ continuance usage intention and behavior of using tourism mobile apps? International Journal of Culture, Tourism and Hospitality Research, 13(3), 288–302. https://doi.org/10.1108/IJCTHR-04-2018-0052
- Xu, H., Teo, H. H., Tan, B. C., & Agarwal, R. (2009). The role of push-pull technology in privacy calculus: The case of location-based services. Journal of Management Information Systems, 26(3), 135–174. https://doi.org/10.2753/MIS0742-1222260305
- Yiu, C. S., Grant, K., & Edgar, D. (2007). Factors affecting the adoption of Internet Banking in Hong Kong – Implications for the banking sector. International Journal of Information Management, 27(5), 336–351. https://doi.org/10.1016/j.ijinfomgt.2007.03.002
- Youn, S. (2005). Teenagers' Perceptions of Online Privacy and Coping Behaviors: A Risk–Benefit Appraisal Approach. Journal of Broadcasting & Electronic Media, 49(1), 86–110. https://doi.org/10.1207/s15506878jobem4901_6
- Youn, S. (2009). Determinants of online privacy concern and its influence on privacy protection behaviors among young adolescents. Journal of Consumer Affairs, 43(3), 389–418. https://doi.org/10.1111/j.1745-6606.2009.01146.x
- Zhang, L., & McDowell, W. C. (2009). Am I really at risk? Determinants of online users' intentions to use strong passwords. Journal of Internet Commerce, 8(3-4), 180–197. https://doi.org/10.1080/15332860903467508
- Zhou, T. (2012). Examining location-based services usage from the perspectives of unified theory of acceptance and use of technology and privacy risk. Journal of Electronic Commerce Research, 13(2), 135.