LIKE ANY DISRUPTIVE INNOVATION, the Internet of Things brings opportunities and risks alike. These are set to have a significant impact on individuals, industries and society as a whole. The insurance sector was only recently said to have adopted a “wait and see” attitude towards the potential challenges, but O.R. suggests that there is no more time to waste.
In 2006, in an operation codenamed Olympic Games, US intelligence experts created a computer virus that infiltrated and infected the systems controlling the centrifuges at Iran’s Natanz industrial plant. This cyber-attack – to use a term that was seldom heard at the time but has since entered everyday parlance – successfully derailed the Iranian regime’s alleged efforts to enrich uranium. Iran eventually realised what was happening only when IT firms captured and reverse-engineered the virus after a programming error allowed it to replicate elsewhere on the internet.
Olympic Games has since been described as the cyber-warfare equivalent of the dropping of the first atomic bomb. According to various high-level sources, it was only a minor component of a far bigger operation, Nitro Zeus, which, had it been carried out, would have devastated Iran’s air defences, power grid, communications and other vital infrastructure.
disruption has been made possible by the ever-increasing connectivity of internet-linked, data-driven devices – and O.R. can help to explain the myriad implications of this global, all-encompassing trend
What does any of this have to do with Operational Research? The story is relevant because such discreet, yet ultimately spectacular, disruption has been made possible by the ever-increasing connectivity of internet-linked, data-driven devices – and because O.R. can help to explain the myriad implications of this global, all-encompassing trend.
Levels of interconnectedness were still in their comparative infancy when Olympic Games was devised. Not so now. Today, with “smart” sensors becoming omnipresent, we have the Internet of Things (IoT) – a near-boundless, immensely intricate system of appliances and objects able to communicate and interact with each other.
It has been estimated that the IoT already consists of around 25 billion devices, many of them – including refrigerators, lightbulbs and other fixtures and fittings in “smart homes” – not necessarily immediately associated with the concept of “big data.” The figure is expected to reach 125 billion by 2030, by which time the transformation may have become truly ubiquitous. It therefore seems reasonable to infer that the IoT’s continued growth will affect almost every aspect of our lives, whether professional or personal.
The challenges for insurers are particularly notable. Thirteen years on from Olympic Games and Nitro Zeus, in an age when even a household fridge could fall victim to a cyber-attack, how might the sector adapt to the novel opportunities and – perhaps more importantly – the unfamiliar risks that the IoT era is likely to bring? This is where O.R. enters the picture in earnest.
USING THE FUTURE TO INFORM THE PRESENT
Dr Ine Steenmans, Lecturer in Futures, Analysis and Policy at UCL, recently worked with one of the industry’s foremost specialists, Lloyd’s, to reimagine insurance for a super-connected society. The collaboration – which also involved PETRAS, an IoT research consortium comprising 11 UK universities – resulted in a major report entitled Networked World: Risks and Opportunities in the Internet of Things.
The report clearly divides the insurance implications of the IoT into opportunities and risks. The former include improved data collection and management and the scope, thanks to innovations such as real-time monitoring, to enhance risk assessment and product flexibility. The latter include the emergence of new kinds of “harm” – for example, data loss, exploitation and information asymmetries – and their prospective effects, not least the threat of a single security breach spiralling into systemic failure.
As the authors observe: “The difficulties in securing very simple but connected devices like sensors can lead to a vastly expanded cyber-attack vector, with many weakened access points to critical systems.” This, they add, may be especially worrying when more and more data-driven decisions are likely to entail no direct human intervention whatsoever.
It was with such concerns in mind that Steenmans was asked to “unpack different risk trajectories” by using techniques from the field of technology foresight, which the United Nations Industrial Development Organisation (UNIDO) calls “the most upstream element of the technology development process.” The principal aim of technology foresight, according to UNIDO, is to provide “inputs for the formulation of policies and strategies that guide the development of technological infrastructure.”
The difficulties in securing very simple but connected devices like sensors can lead to a vastly expanded cyber-attack vector, with many weakened access points to critical systems
This form of “horizon scanning” is by no means an exact science, but it can still prove very useful if approached correctly. “Plausibility is essential,” says Steenmans. “Studies often invite only one question: ‘So what?’ This tends to happen when research generates future impact stories that are noticeably different from the status quo but which place only limited focus on the fundamental nature of change. That’s why we tried to outline situations that might actually come about and which could be realistically associated with the massive economic and societal shifts that the IoT is producing.”
Steenmans eventually assembled 10 scenarios, spreading them across four themes: critical water infrastructure, agriculture, marine and smart homes. The intention was to illustrate not only how the IoT is dramatically remoulding the landscape of risk but also, crucially, how the future might help to reshape the present.
CONFRONTING THE UNPRECEDENTED
The construction of “extreme but plausible” stress-testing scenarios is a well-known method of future risk management in the insurance sector. In this instance, given the scale and speed of disruption, a balance between the radical and the conceivable was especially desirable. “We expect to see profound changes between now and 2030,” says Steenmans, of UCL’s Department of Science, Technology, Engineering and Public Policy (STEaPP), “so we wanted insurers to take the leap and envision the immediate, mid-term and long-term effects of the IoT. It was a case of exploring the likely impacts with a view to preparing for fundamental changes before they happen.”
Steenmans and her fellow researchers, Dr Leonie Tanczer, Dr Irina Brass and Professor Madeline Carr, first reviewed the literature on IoT risk projections. They then surveyed dozens of experts – including PETRAS associates, IoT industry figures and specialists in cyber-security and technological disruption – to ensure that the scenarios chosen for the report would be suitably robust, representative and complex. There were also workshops with academics and practitioners, as well as interviews with Lloyd’s underwriters and actuaries.
The team used the same basic format for each scenario: a description of IoT devices and technologies that could be deployed by 2030 or beyond; a pathway explaining how events and risks might materialise; an appraisal of critical uncertainties; and an examination of the classes of insurance likely to be affected. A further constant was the severity of the possible outcomes, with the predicted consequences ranging from mass bankruptcies and collapsing infrastructure to street riots and food shortages.
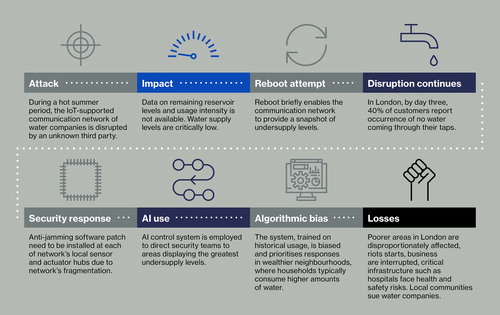
Consider, for example, the scenario detailed in . Here a cyber-attack on water companies’ communication networks sparks serious supply problems, dangerous miscalculations and, as the crisis escalates, public disorder. The initial security breach is exacerbated by an artificial intelligence system that has been trained on historical usage patterns and so prioritises wealthier neighbourhoods. Businesses fail. Hospitals are rendered unsafe. Entire communities take legal action.
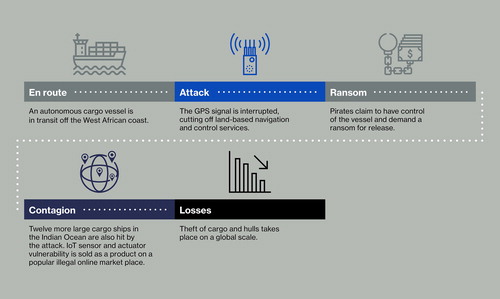
Consider, too, the scenario shown in . Here the world’s seas are the preserve of uncrewed, autonomous vessels that are loaded with containers whose perishable cargos are kept in optimum condition by temperature sensors. Using hacks illegally sold online, criminals block the ships’ GPS signals and swiftly usher in a new age of global piracy – prompting substantial losses for maritime businesses.
“These scenarios reveal numerous critical uncertainties for insurers,” says Steenmans. “There’s the issue of unclear attribution – how do we identify the intentional or unintentional nature of harm in an IoT setting? There’s the issue of cascading and aggregated risk, which is practically inevitable in light of the IoT’s interdependencies. There’s the issue of legislative and regulatory frameworks and how these need to evolve. There’s the ever-present, overarching issue of whether data can be trusted… It’s a lengthy list – and a thought-provoking one.”
ADAPTING TO A “NEW NORMAL”
The findings of Networked World echo Steenmans’ observations. The report concludes: “‘Cyber’ is a broad concept in insurance, and it will need to be broken down into much greater detail to be effective in modelling risk and exposure, shaping coverage and guiding capital reserve requirements… Much closer partnership with the tech sector is necessary. Expertise and cutting-edge developments in data science could be integrated into the insurance sector through collaborative relationships.”
TABLE 1 OPERATIONAL BENEFITS REQUIREMENTS FOR THE INSURANCE SECTOR

This message has already been welcomed within the industry. “We will know so much more with billions of additional pairs of ‘eyes’ on the world,” says Trevor Maynard, Head of Innovation at Lloyd’s, whose own Innovation Lab worked on the project. “The challenge is to be ready to make best use of what these eyes see. New forms of insurance may arise. Smart contracts with parametric, sensor-driven triggers may improve the claims process. Advanced data talent will be required to engage with this new world, and actuaries are well placed to play a key role – provided they upskill as necessary.”
Policymakers are also taking note. The Parliamentary Office of Science and Technology has referenced Networked World in a briefing entitled ‘Cyber Security of Consumer Devices’. Lord Clement-Jones, the Liberal Democrats’ House of Lords spokesperson for the digital economy, has commended the authors for drawing attention to “a technological advancement regrettably often overlooked,” adding: “UCL and Lloyd’s have championed the emerging leadership role of the insurance sector in the domain of ethical data usage… [Insurers] now need to take on the challenge of developing standards for businesses and consumers.” Praising Steenmans’ scenarios for “illustrating some of the fundamental changes likely to be encountered across multiple sectors,” Lord Fox, the Liberal-Democrats’ House of Lords spokesperson for business, energy and industrial strategy, has acknowledged the report’s “contribution to ongoing debates on future codes of practice and models of cyber-security governance.”
As shown in Table 1, Networked World offers a simple breakdown of what IoT is likely to allow insurers to do and what it is likely to require them to do. Steenmans believes that there is no more time to waste in responding to both.
the sector is going to have to move quickly to capitalise on this transformation – and we can help it to do so
“Ernst & Young referred to the IoT as a ‘futuristic concept’ as recently as 2016 and suggested that many insurers were adopting a wait-and-see attitude,” she says. “But things have progressed rapidly in the few years since then. Usage of the IoT has increased exponentially, compelling insurers to examine the risks and value propositions to which the IoT is giving rise. It’s no longer a matter of ‘wait and see’. It’s a matter of acting now.”
New forms of insurance may arise. Smart contracts with parametric, sensor-driven triggers may improve the claims process. Advanced data talent will be required to engage with this new world, and actuaries are well placed to play a key role
The O.R. community, too, should pay heed of what is happening, since technology foresight and horizon scanning will undoubtedly play a continued role in recognising and adapting to the “new normal” of unparalleled connectivity. “This was very much an O.R. project,” says Steenmans, Chair of the OR Society’s Special Interest Group on Policy Design. “Historically, O.R. has made great contributions to the development of scenario methodologies, and this work built on that tradition. Our scenarios to date have already highlighted significant considerations for new business models, the operational future of underwriting, insurance claims and modelling. Now the sector is going to have to move quickly to capitalise on this transformation – and we can help it to do so.”
The figures are taken from ‘Networked World: Risks and Opportunities in the Internet of Things’, published in November 2018. This can be downloaded at https://www.lloyds.com/news-and-risk-insight/risk-reports/library/technology/networked-world.
Additional information
Notes on contributors
Neil Robinson
Neil Robinson is the managing editor of Bulletin Academic, a communications consultancy that specialises in helping academic research have the greatest economic, cultural or social impact.