Abstract
This paper assesses the evolution of last 43 years in counterfeit research with respect to sources of knowledge (i.e. journals, authors, institutions, countries) and research themes. The oldest paper on this subject discovered in the Scopus database was published 43 years ago, yet a time frame was not specified. Sources of knowledge are assessed on research productivity (quantitative) as well as impact (qualitative). Research themes, key areas of focus within the counterfeit research landscape, are identified and discussed to conceptualize our understanding of the field. Via a systematic literature review, 713 peer-reviewed academic articles published in 282 journals from 1978 to 2021 were selected as the sample for this study. The systematic review technique was chosen as compared with narrative reviews of the literature it focuses on open, extensive, and detailed approaches to literature searches, in addition to conforming to the scientific criteria utilised in primary research, namely transparency, rigour, comprehensiveness, and reproducibility. A database of references and citations was created for analysis. The data was analyzed to prepare comparative tables. Further, the Leximancer software was used to generate lexical conceptual trends. This data was further analyzed to identify emerging themes. The Journal of Business Ethics had the highest number of articles and citations, followed by the Journal of Business Research and Business Horizons. Ian Phau (14 articles) and Michael D. Smith, (9 articles) were the most prolific authors. Joseph Nunes and Ian Phau attained the highest number of citations, cited 658 and 577 times respectively. Eight major research themes were identified: products, piracy, model, price, firms, digital, supply, and ethical. Each theme was analyzed over time. The major research areas analyzed across the articles over time were Technology (particularly “Technology” and “Software” topics) and Ethics (particularly “IP” and “Legislation”). The identification of these research area captures the essence of the paper’s uniqueness and contribution to this field of research. This is the first systematic literature review in counterfeit literature that captures multi-decade sources of knowledge in business journals.
1. Introduction
Counterfeiting is defined as the act of copying the features and characteristics of an existing product to create a new product with the intention of making it indistinguishable from the original (Eisend & Schuchert-Güler, Citation2006). This phrase, which denotes a high degree of precision or likeness, is frequently used in a variety of contexts, such as when assessing the quality of a replica, a copy, or a counterfeit. Products that are purposefully designed to resemble real products from a well-known brand are known as counterfeit goods in the world of trademarks and brands. These fake products are frequently created with the goal of being “indistinguishable from the original” in terms of design, branding, and packaging. In order to trick customers into thinking they are buying authentic products when they are actually buying fraudulent and unlicensed replicas. Owners of copyrights and trademarks are legally entitled to prevent unlawful copies, sales, or distribution of their intellectual property. Intellectual property rights are intended to shield brand owners and content creators from unauthorized copies and imitations that can hurt their interests or mislead customers. Counterfeit products are generally sold for a lower price than the original product (Eisend & Schuchert-Güler, Citation2006). More simply, counterfeiting, also commonly referred to as piracy, “involves the unauthorized replication of copyrighted intellectual assets for commercial purposes” (van Wijk, Citation2002, p. 689). It can further be divided into deceptive (e.g., commodities falsely acting as luxury products) and non-deceptive channels (i.e., consumers are aware that the goods they are purchasing are counterfeit; Khan et al., Citation2020). Piracy, specifically, is the illegal reproduction, distribution, or use of intellectual property, such as software, music, movies, books, or other works, that are protected by copyrights without the owner’s consent. It is a type of intellectual property violation that is prohibited in the majority of nations.
Globally, according to current forecasts on counterfeiting and international trade, the magnitude of counterfeiting is estimated to exceed USD 3 trillion in 2022 (Organisation for Economic Co-operation and Development, 2021). According to a survey by the Organization for Economic Co-operation and Development (OECD), the value of global commerce in fake and pirated goods is estimated to be 3.3% of all trade, or about USD 509 billion. This represents a huge drain on the revenue of genuine enterprises and tax revenue for governments (EUIPO, Citation2019). In legitimate industries, counterfeiting results in employment losses. Over 468,000 jobs have been lost due to piracy and counterfeiting in the European Union, according to a study by the European Union Intellectual Property Office (EUIPO, Citation2019). Counterfeiting threatens intellectual property (IP) and causes a loss of revenue because it limits the ability of a manufacturer or brand to charge fair prices and diminishes product image because consumers are unable to distinguish between genuine and counterfeit products (Çekirdekci & Baruonu Latif, Citation2019; Chaudhry & Stumpf, Citation2011). In addition to revenue losses, legitimate producers have cited declines in brand reputation and equity (Phau et al., Citation2009). Consumers may be at risk for safety issues as a result of counterfeit products, particularly in sectors like electronics and pharmaceuticals.
In the case of luxury products, where counterfeiting is rampant, the exclusiveness of an original, authentic product is vastly reduced (Çekirdekci & Baruonu Latif, Citation2019; Phau et al., Citation2009). Inconsistent or absent punishment for those engaging in counterfeit activities has resulted in further incentives for pirates to continue producing counterfeit products (Chaudhry & Stumpf, Citation2011). As a result, consumers risk being subjected to low-quality and imitation products which may cause harm to their well-being, particularly in the case of counterfeit medicine and drugs. Although counterfeiting can increase brand awareness and create additional demand (Braun & Eklund, Citation2019), the overall damage caused by counterfeiting is outweighs the benefits gained from exposure.
A quick search of “counterfeit” or “piracy” in the title, abstract, or keywords in an online journal database resulted in about 14,000 academic peer-reviewed English language articles. Counterfeit or piracy is a multi-disciplinary concept; amongst 14,000 articles, the concept was found in diverse disciplines such as law, social science, political science, agriculture, business, engineering, economics, biology, geography, earth sciences, economics, transportation, and anthropology. Since counterfeiting is a complex issue with wide-ranging effects, it is connected to many different academic fields. Legal frameworks are essential for pursuing counterfeiters and defending the rights of those who possess intellectual property. Political science and counterfeiting can interact through issues of global trade agreements, intellectual property laws, and the responsibility of governments in stopping the trade in counterfeit goods. Social scientists research the effects of counterfeit goods on people. False pesticides, fertilizers, and seeds in agriculture can reduce crop yields and food output. Businesses are directly impacted by counterfeiting since it impacts their sales, market share, and brand integrity. Economic losses result from counterfeiting, including those from lower sales of real goods, higher expenditures associated with law enforcement, and effects on trade balances. Economists research these outcomes. Medical devices and drugs that are fake can seriously affect your health. Intricate transportation networks, including air, sea, and land routes, are frequently used to convey counterfeit goods. The ways that counterfeiters abuse these systems are examined by transportation experts. A global and multidisciplinary problem, counterfeiting has an impact on many facets of society and the economy. Since this issue is so complicated, it requires the participation of several academic disciplines in order to be successfully understood, addressed, and mitigated. To handle various aspects of the issue, each field offers special knowledge and perspectives.
Academic research on counterfeiting has been conducted on various topics such as Counterfeit goods with products, including software, books, medicine, drugs, luxury products, software, anti-counterfeits, among others (e.g., Alghannam et al., Citation2014; Almuzaini et al., Citation2013; Barnor et al., Citation2020; Baruönü Latif et al., Citation2018; Chavarria et al., Citation2016; Eisend et al., Citation2017; Fadlallah et al., Citation2016; Hoecht & Trott, Citation2014; Karunamoorthi, Citation2014; Khan et al., Citation2021; Koczwara & Dressman, Citation2017; Lima de et al., Citation2018; Samaddar & Menon, Citation2020; Staake et al., Citation2009).
Despite considerable importance and multi-dimensional nature of this topic, there is a dearth of literature reviews that has synthesized this area of research. Therefore, in order to comprehend the state of knowledge about counterfeiting and its ramifications, the main goal of this study is to identify the knowledge sources and their noteworthy contributions to the literature. To achieve this objective, this study presents a systematic review of the counterfeit literature using citation analysis. It further presents conceptual trends observed in the literature using Leximancer, a visual text analysis tool. We mainly focus on articles published in business and management journals. Specifically, we posit the following research questions:
RQ1: What are the sources of knowledge depicted in terms of the most prolific and highly influential journals, authors, institutions, and countries?
RQ2: What are the major research themes relevant to this topic and how do they vary over time?
RQ3: What are the mature and emerging research topics and how do they relate to one another?
This paper makes four major contributions. First, we argue that this is the most comprehensive review of the counterfeit literature to date that encompasses all relevant counterfeit topics within the field of business and management addressing the lack of an integrative literature review on this topic. Second, we identify the most prolific and influential sources of knowledge to provide credibility to research findings; it acknowledges the contribution of different authors, journals, institutions, and countries and makes it easier for aspiring researchers to identify co-researchers and potential collaborators. Third, the categorization of research into different themes allows researchers and policymakers to better identify and understand sub-topics relevant to counterfeiting. Additionally, it provides a conceptual map of areas and shows how different topics are linked to one another leading to interdisciplinary research. Fourth, the identification of emerging research topics offers direction for future research on this timely topic encouraging relevance and exploration of research in most needed areas.
The remainder of this paper is organized into five sections: Section 2 provides an overview of the existing literature on this topic. Section 3 elaborates on article selection and methodological procedures. It also describes the process of deriving conceptual themes using Leximancer. Section 4 presents findings of citation and Leximancer analyses, and further explores the research questions posited. Section 5 concludes and discusses the results in terms of a broader research perspective.
2. Prior literature reviews
Table lists the previous literature reviews related to counterfeiting. However, only three literature reviews—Staake et al. (Citation2009), Latif et al. (Citation2018), and Samaddar and Menon (Citation2021)—are considered relevant to the current study and are discussed below (see Table ). The review’s overall focus on counterfeiting in general as opposed to a focus on a particular product was how the relevance was determined. The studies with research on a specific product covered medicine (e.g., Koczwara & Dressman, Citation2017; Lima de et al., Citation2018), luxury brands (e.g., Eisend et al., Citation2017; Khan et al., Citation2021), digital (e.g., Barnor et al., Citation2020), and software (e.g., Chavarria et al., Citation2016). Hoecht and Trott (Citation2014) examined anti-counterfeit strategies. Thus, because a general overview of the topic cannot be attained from those articles, they have been excluded from discussion in the current study.
Table 1. Systematic literature reviews in the field of counterfeit
Table 2. Characteristics of comparable literature reviews
Staake et al. (Citation2009) is the only review published in a top-tiered journal. The authors organize their review around six categories: 1) general description and overview of the phenomenon, 2) qualitative impact analysis, specifically the effect of counterfeit on various indicators such as brand value, turnover, and liability claims, on the manufacturers of genuine products, 3) supply-side investigations, including the motive of illegal parties, production aspects, and supply chain implications, 4) demand-side investigations, which represent consumer attitudes toward counterfeit products, 5) managerial guidelines to avert counterfeits, which includes strategies and tactics to tackle counterfeiting activities, and 6) legal issues and legislative, such as the enforcement of intellectual property rights. Staake et al (Citation2009) identify research gaps and further propose managerial implications for both demand and supply side. They suggest evaluation of counterfeit market to estimate the impact on brand loyalty, brand awareness, and quality perception while educating consumers about it. They also encourage examination of strategies and production locations of actors involved in counterfeiting.
Latif et al. (Citation2018) focus on the demand side (i.e., consumers) of counterfeit goods. In this review, they “illuminate the existing body of research on counterfeiting through a content analysis and identify theoretical gaps and opportunities for further research from a marketing perspective” (Latif et al, Citation2018, p. 458). The authors provide a comprehensive background on the history of history before delving into their main findings. Based on a review of 65 articles published over a 37-year period, Latif et al. (Citation2018) identify four themes related to counterfeiting: 1) product and brand-specific motivations, 2) social influence motivations, 3) consumer trait-specific motivations, and 4) proliferated motivations.
Samaddar and Menon (Citation2020) review literature related to non-deceptive counterfeit products. Non-deceptive counterfeit is a subsection of the counterfeit literature in which the user is aware that the product is not authentic. In this review, they “develop a morphological analysis (MA) framework and to identify the major research gaps that offer potential for future research” using 120 research papers published over 25 years (Samaddar & Menon, Citation2020, p. 1). MA is a qualitative method widely used in social sciences for examining and analyzing a set of structured interactions in a multidimensional setting. The authors derived five key themes from the literature focusing on non-deceptive counterfeit: 1) market characteristics, 2) influencing factors, 3) self-regulating factors, 4) research methodology, and lastly 5) theoretical model. By building a cross-comparison matrix, Samaddar and Menon (Citation2020) determine that future research directions for counterfeiting should focus on the societal role of intention, consumer traits, mindful consumption, and social media in anti-counterfeit.
Relative to other related works, Table demonstrates that the current study is the most comprehensive account of extant research on counterfeit literature to date for three reasons. First, it has the largest sample size (713) of any systematic review on this topic. The next highest is 120 studies by Samaddar and Menon (Citation2020). It also covers the largest timeframe (43 years. Latif et al. (Citation2018) examine the literature over 37 years. It also includes the largest number of journals (282) as compared to 50 journals by Samaddar and Menon (Citation2020), the next highest. To date, this is the only study which examines sources of knowledge, research productivity and impact.
3. Methodology
Large-scale scientific data can be explored and analyzed using the popular bibliometric analysis technique such as citation analysis. Bibliometric techniques use a quantitative approach to describe, assess, and track published research. Only with the emergence of easily accessible internet databases with citation data such as Scopus and Web of Science, bibliometric methods began to draw wide attention (Zupic & Čater, Citation2015). Citation analysis is considered a measurement of influence in academia (Liu et al., Citation2013). As a bibliometric technique, it has been used by researchers as a performance metric of authors, articles, journals, and universities (Chatha et al., Citation2015). Publications that are cited more than others are presumed to have been more relevant and influential for research (Jeung et al., Citation2011).
The first step in citation analysis is article selection. Based on the prior literature reviews (Baruönü Latif et al., Citation2018; Samaddar & Menon, Citation2020; Staake et al., Citation2009), four keywords – counterfeit, pirated, piracy, and fake – were searched in the Scopus database. The articles were restricted to peer-reviewed, published in academic journals, and the English language only, and published within the last 43 years (i.e., 1978–2021). Since the objective of this study is to examine counterfeit literature relevant to the field of business, only journals in the following areas were searched: business, management, and accounting.
The initial search resulted in 1,527 journal articles. After removing 814 irrelevant articles, 713 unique articles were retained for further analyses (Table ). The analysis was performed in the form of a frequency distribution of articles and citations, and the percentage of articles and citations. To better analyze the various research topics explored in this field, we developed a matrix that cross references each topic. This matrix was developed by first identifying most frequently keywords then filtering most frequently occurring keywords in the title, abstract, and KWs of each article in our database. A number of research topic were further categories into broad research areas such as a) intangible products (books, clothes, drugs, food, and luxury, b) intangible products (movie, music, software), c) technology (technology, blockchain, and RFID), d) IP rights (legislation, legal, IP, and copyright). Anti-counterfeit and ethics were treated as a standalone research topic. The matrix, similar to correlation matrix, captures cross-reference of each topic against one another. The matrix shows how different topics are interrelated.
Table 3. Article selection process
The field can be divided into three timeframes across the examined papers (Table ). 47 articles were gathered between 1978 and 2001, 238 articles between 2002 and 2011, a considerable increase, and 428 papers between 2012 and 2021, a twofold increase. In terms of percentage, it comes out to be 6.6% of the total sample from 1978 to 2001, 33.5% between 2002 and 2011, 60.0% of the entire sample from 2012 to 2021. Thus, research in the field of counterfeiting has increased over time. Notably, the volume of articles published doubled between the second and final timeframes following a considerable spike in activity in the early 2000s. The significant increase in counterfeit research since can be attributed to greater focus on this area due to several factors such as globalization leading to higher trade across borders, technological advancement making it easier to produce and distribute counterfeit products, particularly digital products. The international multilateral agencies such as World Trade Organization has realized the negative economic impact of counterfeit on countries and encouraged legislation to curb counterfeit.
Table 4. Articles by timeframe
Next, via a visual text analysis software (Leximancer), we extracted conceptual themes from the data in each of the three timeframes (i.e., 1978–2001, 2002–2011, and 2012–2021). Leximancer uses a combination of machine learning processes, such as Bayesian statistics, to generate concepts and then further relates these identified concepts with other co-occurring concepts (Angus et al., Citation2013). Specifically, for extracting and displaying concepts, themes, and patterns from enormous amounts of text data, Leximancer is a text analysis software program. Here is a detailed explanation of how Leximancer operates (Smith et al., Citation2016):
All 713 papers (PDFs) that comprise the entire sample were uploaded to the software.
Leximancer use an algorithm to recognize concepts or keywords in text and automatically extract them. In the dataset, these ideas represent the most important and frequent phrases.
The program looks at the co-occurrence patterns of concepts to find themes or subjects. In order to determine the main themes or topics present in the data, it evaluates which concepts commonly appear together in the text.
The extracted concepts and topics are turned into graphic representations called concept maps that make it simpler to understand and explain the findings.
Leximancer’s visualizations and insights are used by researchers and to analyse the data, comprehend the content more thoroughly, and spot trends, patterns, or anomalies.
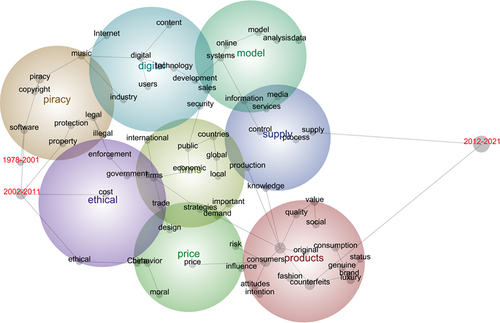
Leximancer provides emerging themes present in the dataset analyzed through a map visualization (Ward et al., Citation2014). Themes are visualized by bubbles; the bubble size directly referring the content density of a specific theme. The size of the bubble relates to the frequency in which the theme is represented in the dataset. The proximity of the bubbles indicates their likelihood to appear together in similar contexts (Ward et al., Citation2014). For instance, a bubble labelled “consumer” overlaps with a bubble labelled “affinity”, then the two themes are strongly related to each other. Via this process, researchers can identify relationships among terms and present it in a network visualization format (Ward et al., Citation2014). In short, the size of a bubble denotes the significance or prominence of that concept within the dataset. Larger bubbles often represent themes that are more prominent or frequently appear in the text under analysis. The closeness of bubbles on a map denotes the strength of the relationships between certain concepts. The text in the bubbles is more closely related to the ones that are closer together.
Content analysis is an important research methodology, for it quantitates social science research. As a result, Leximancer has become a strategic tool for researchers looking to improve their rigour. It has also provided a method to analyze conceptual trends and sentiments over time, as leveraged in this research paper. Leximancer is preferred over manual content analysis for several reasons. First, large amounts of text can be processed by Leximancer quickly, whereas doing so manually (713 articles) would take a lot of time and effort. Second, Leximancer provides consistent results which would be difficult to maintain in manual coding due to subjectivity of coder. Third, coder’s interpretations may contain intentional or unconscious bias with manual coding. The automated process used by Leximancer removes any prejudice and provides a neutral analysis.
4. Results
4.1. RQ1: What are the sources of knowledge depicted in terms of the most prolific and highly influential journals, authors, institutions, and countries?
Across the 713 articles published in 282 journals, the majority of articles came from 33 journals. The top five journals by total publications are the Journal of Business Ethics (51), Journal of Business Research (29), Business Horizons (22), Journal of Brand Management (16), and Journal of Consumer Marketing (10). Almost 60% articles published in the Journal of Business Ethics focus on software piracy. In additional to ethical issues related to piracy, these studies discuss intellectual property rights. Journal of Business Research, on the other hand, mainly examines counterfeit luxury and fashion. The major focus of Business Horizons is on anti-counterfeit measures.
The Journal of Business Ethics has the highest number of citations (3323, 24% of total citations). The Journal of Consumer Marketing and Journal of Business Research are both with more than one thousand citations at 1566 citations and 1137 citations respectively. The Journal of Marketing has 980 citations and the Journal of Management Information Systems has 962 citations. Of the five most influential journals, none had published articles relevant to counterfeiting in the 1978–2001 timeframe. The Journal of Business Ethics, Journal of Business Research, and Journal of Consumer Marketing appeared multiple times from 2002–2011, and again from 2012–2021. Journal of Marketing and Journal of Management Information Systems appeared in the 2002–2011 timeframe. Notably, at this time, research began to emerge more prolifically across many journals. See Table for details.
Table 5. Most prolific and influential journals
Ian Phau, Michael D. Smith, Peggy E. Chaudhry, and Deli Yang are the most prolific authors with 14, 9, 9, and 8 articles, respectively. Ian Phau’s research focuses on luxury branding, brand counterfeiting and piracy, and consumer animosity. Michael D. Smith’s research focuses on piracy and technology, specifically information systems, security, and other retail technology-related topics. Peggy E. Chaudhry studies management and operations concerning piracy. Deli Yang conducts research on business intellectual property and brand counterfeiting and specializes in information related to patent uncertainties. With respect to citations, Joseph Nunes (658 citations), Ian Phau (577 citations), and Lawrence G. Sanders (469 citations) have been cited the most in order.
Joseph Nunes’ research specializes in status and luxury goods, anti-counterfeiting, and pricing. Specifically, his highly cited study titled “Signaling Status with Luxury Goods: The Role of Brand Prominence” examines the reasons for consumer use of luxury counterfeit brands. Lawrence G. Sanders’ research focuses on information technology and piracy. Sanders’s research examines key issues and impact of software piracy and propose preventive and deterrence mechanisms in addition to deliberating ethical considerations in decision making and software piracy. Of these noteworthy authors, Sanders is the only author to have exclusively published between the 1978 to 2001 timeframe. Ian Phau has consistently published across all three timeframes. Particularly, his study titled, “Devil wears (counterfeit) Prada: a study of antecedents and outcomes of attitudes towards counterfeits of luxury brands” is considered influential even in the most recent times. It examine how social and personality factors affect Chinese customers’ perceptions of luxury brand knockoffs and how these two sets of criteria affect consumers’ intentions to make a purchase. It gives a profile of those who buy and don’t buy luxury brand knockoffs. Michael D. Smith has published frequently across all three timeframes. However, he has mainly focused on movie and music piracy. His study titled, “The effect of graduated response anti-piracy laws on music sales: Evidence from an event study in France” examines the effectiveness of government anti-piracy policies. The research found that increased awareness of anti-piracy law had a positive impact on sales of digital music sales. Other authors, such as Peggy E. Chaudhry, joined the field of research in the 2002–2011 timeframe and have remained active in the field to date. On the other hand, Joseph Nunes and Deli Yang also joined in 2002–2011 but exited (per their publication count) in 2012–2021. See Table for details.
Table 6. Most prolific and influential authors
The most prolific institutions in this field by total publications are Curtin University in Australia with 12 articles, Carnegie Mellon University in the USA with 11 articles, Hong Kong Polytechnic University in Hong Kong with 11 articles, the University of British Columbia in Canada with 9 articles, and the University of Minnesota in the USA with 8 articles. The most prolific author Ian Phau is based at Curtin University while M.D. Smith, another prolific author is affiliated with Carnegie Mellon University. There are multiple researchers associated with the University of British Columbia and the University of Minnesota. Hong Kong Polytechnic University in Hong Kong with 11 articles is home to 34 authors this making it truly a source of knowledge for counterfeit research. Both Curtin University and Carnegie Mellon University are present throughout all three timeframes, specifically a denser number of articles from Curtin University in 2012–2021 and Carnegie Mellon University in 2002–2011. See Table for details.
Table 7. Most prolific and influential universities
Although certain institutions produce more research than others, this is certainly not indicative of the most prolific countries in research areas. Unsurprisingly, the North American region produced the most research, specifically the USA at 285 articles. The second most prolific country in this field is the United Kingdom, with 76 articles published. From there, China occupies the third-most prolific country in this field at 47 articles, Australia as fourth-most at 43, and Hong Kong fifth at 39 articles. At the time this research first started being explored (1978–2001), most publications came from the USA. As interest in this area developed, more research from notably the UK and Australia came to be published across 2002–2011, with some prominence from China and Hong Kong. In recent years, more countries have published occasional research on counterfeiting, such as Canada, Italy, Spain, and Taiwan. Malaysia has emerged as a recurring publisher for counterfeit research from 2012–2021, even as the USA and UK remain present throughout all three timeframes. See Table for details.
Table 8. Most prolific and influential countries
4.2. RQ2: What are the major research themes relevant to this topic and how do they vary over time?
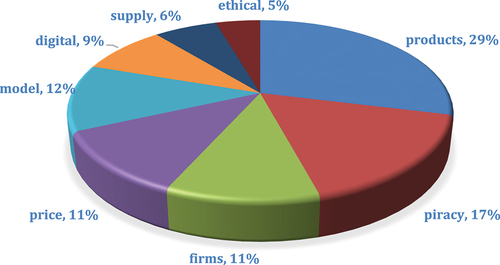
The major research themes across the articles over time provide insight into the areas of interest but also steers future research directions based on areas that currently have less attention. Across this systematic literature review, eight main themes emerged. The densest theme discussed in the literature is “products” at 29% of all lexical occurrences. As the literature is divided amongst various commodities, technologies, and other related product offerings, this concept sets the framework for the other following concepts: “piracy” (17%), “firms” (11%), “price” (12%), “model” (12%), “digital” (9%), “supply” (6%), and “ethical” (5%). Taken together, these themes indicate that most research focuses on product and organizational counterfeiting and piracy and aims to maximize current tools in anti-counterfeiting methods through cost-effectiveness and digitally efficient means. See Figure for details.
Leximancer also provides an opportunity to further analyze concepts correlated to the major themes identified in its lexical analyses. Regarding “products”, concepts associated included counterfeits, consumers, brands, luxury, and value. “Piracy” was related to software, music, legal, property, and protection. “Model” yielded connections to information, data, analysis, online, and systems. “Price” correlated to behaviour, risk, influence, and demand. “Firms” related to countries, economics, public, strategy, and trade. Concerning “Digital”, this term correlated to industry, technology, content, users, development, and security. “Supply” related to control, services, processes, media, and production. Lastly, “Ethical” correlated to cost, enforcement, and government. See Figure .
Of interest is also the timeframes for when each of the identified themes was discussed. Across the three timeframes, “Products” were discussed the most, increasing in frequency from 1978 to 2001 from 27% to just under half (44%) from 2012–2021. In terms of specific product categories, clothing and pharmaceuticals lead the pack followed by cosmetic and personal care, watches and jewellery, handbags and luggage, toys and games, and sports goods (Sabanoglu, Citation2022). The total number of counterfeit incidents related to pharmaceuticals increased worldwide from 196 in 2002 to 6,615 in 2022, showing a phenomenal rise by 3275% (Mikulic, Citation2023). The countries most hit by counterfeit clothing and footwear in Europe include Italy, Spain, United Kingdom, Germany, and France (Statista, Citation2015). The probable reasons for increasing trend of counterfeit clothing could be several including high prices of luxury brands beyond the reach of ordinary persons, ubiquitous use of social media which promotes the use of counterfeit products. A recent study estimates that 22% of consumers aged 16–60 years and active on social media purchase counterfeits because the illicit goods were recommended by influencers; 31% of males and 13% of females (Shepherd et al., Citation2023). Supply chains have become increasingly complicated as a result of globalization, with apparel production frequently taking place across numerous nations. Because of this complexity, there are opportunities for counterfeiters to enter the supply chain and create fake apparel. The expansion of online marketplaces and e-commerce has made it simpler for counterfeiters to reach a global clientele. Online marketplaces can have trouble efficiently policing fake listings.
On the other hand, the second-most discussed theme, “Piracy,” decreased over the timeframes in frequency, from 33% between 1978 and 2001 to 24% between 2002 and 2011 to 13% from 2012 to 2021. The term piracy is generally associated with software and digital products. The share of unlicensed software has gradually decreased overtime across all regions in the world (Vailshery, Citation2022). Some probable reasons for this trend is stricter enforcement and legal actions by the government and software companies, availability of free and open-source software, improve accessibility of legitimate software, increased awareness, introduction of cloud-based software and subscription models. Other themes that increased in frequency over the 43 years include “Model”, “Digital”, and “Supply”. On the contrary, themes such as “Firms” and “Ethical” decreased over the years. “Price” is the only theme to have fluctuated throughout the years, from 8% from 1978 to 2001 to 10% from 2002 to 2011 and then down a percentage point to 9% from 2012 to 2021.
4.3. RQ3: What are the mature and emerging areas of research and how do they relate to one another?
To better analyze the various research topics explored in these journals, we developed a matrix that cross references each of these topics. Upon this exercise, we identified that research topics can be categorized into three distinct and broad areas such as commodities, technology, and ethics, etc. Across numerous journals, there emerged some areas of research that deserve specific attention. Over the past decade, technology has made incredible advancements from the 3 G to 4 G and 5 G, AI, cloud computing, and big data (Palandrani, Citation2020). Not surprisingly, technology emerged as one of the most mature areas of focus in this field of research (i.e., “Software” at 136 counts in the Commodities segment and “Technology” at 84 counts in the Technology segment). Similarly, results coincide with recent technological advancements, as research is still emerging for topics such as “Blockchain” at 14 counts and “RFID” at 11 counts. Interestingly, in the Ethics segment, many journals discussed legality (i.e., “Legality” at 87 counts) and specifically mentioned IP at 140 counts and Legislation at 136 counts. Ethics itself appeared 125 times in the dataset. Other mature areas in the research included “Luxury”, “Music” and “Software”, all from the Commodities segment. See matrix A for details.
The least-dense segment was Commodities. On average, across ten different topics, Commodities averaged 55.2 citations. Specifically, the topics “Books” and “Clothes” garnered little interest across the journals. Therefore, it may be concluded that research in these areas has lost its traction, perhaps due to longevity and prior breadth of literature, to other progressive areas such as technological advancements (e.g., Chavarria et al., Citation2016), as noted earlier.
Concerning the topic of anti-counterfeit, the topic with highest correlation was “IP” at 15 counts and “Luxury” and “Technology” both at 7 counts. On the opposite end, topics such as “Books” and “Food” and “Clothes” had correlation with anti-counterfeit, ranging from 1 to 3 counts. This further suggests that current research is less concerned with commodity-based topics through the lens of anti-counterfeit and is instead focusing on topics such as high-profile items and technology as they relate to anti-counterfeit.
The findings from Leximancer analysis were corroborated by matrix analysis. Overtime, the research shows increasing trend in the area of fashion and luxury items, which are mainly related to clothing and accessories. Similarly, as piracy, a concept primarily related to software, showed a decreasing trend, captured by matrix as well where research on software has declined significantly in the most recent times. Another notable trend is lower emphasis on ethics research. A deeper introspection reveals that a big component of ethics research was focused on software. Thus, a decline in software research caused a slow down on ethics research. In Table , research conducted in last five years (2017–2021) was further bifurcated and compared with research conducted overall to identify emerging areas of research. The research areas showing increasing trend in last five years include food, luxury, blockchain technology, and anti-counterfeiting. The research on software, intellectual property, and RFID has declined in the most recent timeframe.
Table 9. Research topics by timeline
Interestingly, the research demonstrated that overlapping keywords included system, development, and sales across the themes of “model” and “digital”. This may indicate that digitization is becoming a prominent feature of information technology, particularly related to the ways that it can aid sales tactics. Similarly, the overlap between the themes of “model” and “supply” yielded topics related to information, media, and services. This finding may point to a potential benefit in using digital media to optimize supply chain management (SCM) strategies. In relation to the themes “ethical” and “firms”, the topic of trade appeared, perhaps signalling that trade is a shadowy channel of counterfeit and piracy that requires more attention. See Table for details.
5. Discussion, conclusion, limitations, and future research directions
This paper uses citation analysis to conduct a bibliometric analysis of the literature in the field of counterfeiting. The main motivation for the current study is to determine the sources of knowledge (specifically the articles, authors, and journals) that are making significant contributions to the field of counterfeiting. The identification of the relevant quality of these parameters will help us to identify the notable contributions to the literature. This paper identifies the most prolific and highly cited journals and authors, and thus it provides a broad overview of the field and guidance to potential researchers in the same. It was also found that teamwork and collaboration are needed in order to publish in high-quality journals. Potential researchers can select appropriate journals to disseminate their work and can identify opportunities to pursue collaborative work. Further, potential graduate students can approach established scholars for supervision of their research. The scope of this study was limited to only 11 journals. Future studies can pursue articles published in other journals as well. To date, there have been limited integrative systematic literature reviews that have identified the most influential authors, journals, and articles, and research themes in the counterfeit literature (including piracy). Of those that exist, they are narrow in focus or have small number of studies as part of their review. The results of the current review are expected to fill this gap by providing a more comprehensive overview of the counterfeit literature.
We contend that this is the most thorough assessment of the counterfeit literature to date in the fields of business and management. We acknowledge the contributions of various authors, journals, institutions, and countries and making it easier for aspiring researchers to find co-researchers and potential collaborators. We also offers a conceptual map of the various topics and illustrates the connections between various subjects that encourage interdisciplinary research. By identifying emerging research areas, we encourage exploration of the most pressing issues for research and provide direction for future study on this topical topic.
This study performs citation and lexical concept analysis of 713 articles published in business journals over a 43-year period. The objective of this research is to identify sources of knowledge, the most prolific and highly influential authors, and journals. The Journal of Business Ethics, Journal of Business Research, Business Horizons, Journal of Brand Management, and Journal of Consumer Marketing are the most prolific journals. Journal of Business Ethics, Journal of Consumer Marketing, Journal of Business Research, Journal of Marketing, and Journal of Management Information Systems attained the highest overall citations. Although many of the same journals were both highly prolific and cited, the data shows that they can be mutually exclusive and that despite being non-prolific, journals can be highly cited (see Journal of Marketing, Journal of Management Information Systems). The most prolific journal, the Journal of Business Ethics, has become less dominant in recent times while the Journal of Business Research and Business Horizons are more active. Overall, this paper has identified the most prolific and highly cited journals and authors, thus providing a broad overview of the field of counterfeiting and piracy, as well as offering guidance to potential researchers.
This research also sought to identify research themes among the collected articles. Specifically, eight lexical concepts (i.e., themes) were identified: products, piracy, firms, price, model, digital, supply, and ethical. The research articles were further categorized into three topics: commodities, technology, and ethics. In conjunction with the major themes, most research tends to focus on improving organizational efficiency and product offerings through digitization and security. Specifically, the theme “Products” relates to commodity-based research and the value placed upon them by consumers. For example, consumers who knowingly purchase counterfeit luxury goods value the status that they incur from the physical appearance of the good, as opposed to the good’s functional qualities, such as durability (Phau et al., Citation2009). “Piracy” focused on specific intellectual commodities, such as music and software, with a focus on how to protect them against piracy. For example, Jeong et al. (Citation2012) address the challenges of assessing a product’s piracy risk. “Model” provided a substantial overview on how best to achieve efficiency in anti-counterfeit measures, commonly referring to systems and data to analyze. “Price” as a theme focused on ethical pricing tactics and how prices and price-based demand impacted consumer behaviour. “Firms”, “Digital”, and “Supply” refers to topics related to increasing organizational efficiency through digital systems and other methods of lean supply-chain management. Lastly, the theme “Ethical” referenced policies, such as government enforcement. Thus, this research provides a frame of reference, based on prior studies, about the interests previously examined and the themes present within this area of research.
For tangible products, there are a number of areas which show a significant increase in number of studies such as fashion, luxury, food, and books. Incidentally, there is a dearth of research on pharmaceutical which is one of highest counterfeit categories as mentioned earlier. It is important to educate consumers and develop public health campaigns about the importance of obtaining food and medications from reputable sources. It is important to encourage, possibly through legislation and regulations, the pharmaceutical and food industries to develop supply chain traceability and transparency procedures. Demand-side solutions are required for counterfeit luxury and fashion products. It is integral to investigate how consumers behave when purchasing fake designer goods to learn why certain people do so and how this behaviour may be modified. The effectiveness of intellectual property laws in preventing counterfeiting should be studied, and if necessary, improvements should be suggested. To assist buyers in determining the authenticity of luxury goods, manufacturers and retailers should use cutting-edge authentication technology like QR codes and NFC tags.
Anti-counterfeit studies mainly concentrate on Intellectual Property Rights with a major focus on luxury, fashion, and clothing. Interestingly, there is lack of anti-counterfeiting research on blockchain, an emerging research area within this field. In the context of blockchain technology, counterfeit goods provide unique difficulties and challenges. There is a need for practitioners to design and implement technologies such as smart contracts and product authentication systems and academics can conduct research to study the effectiveness of those technologies. Policymakers and regulations need to enhance regulatory frameworks to facilitate the use of blockchain or similar technologies in specific industries to thwart counterfeiting. There is a need to set up sector-specific standards for blockchain-based anti-counterfeiting systems. Programs that certify adherence to these requirements should be supported.
The current study is not without limitations. First, the scope of this study was limited only to business/management-related journals. That is, the dataset for the current study only included counterfeit and piracy-related articles published in business and management journals. Future studies should analyze articles published in other disciplines, such as law and economics. It is also encouraged, as a future research direction, to explore the areas where counterfeit-related research is currently dwindling in popularity to determine the reasons for the decline in research. As well, further examination of areas lacking substantial research is necessary to provide a more thorough wealth of information to society at large. A content analysis with precise, focused, and pointed inquiries to gather and analyze data from each study was not possible due to the large sample size of 713 studies. By performing an interrogative analysis on a sample of studies that have been classified according to research topics, future researchers can gain a deeper comprehension of the goals and findings of the studies. The future studies can consider smaller sample size with TCCM framework (Theory, Context, Characteristics, Method). Business literature is useful for understanding the business-related aspects of counterfeiting, but it falls short of fully addressing the subject given its complexity. To effectively combat counterfeiting and lessen its negative impacts on society, a holistic and multidisciplinary approach that incorporates knowledge from numerous sectors is needed. However, give the vast nature of studies on this topic, future research should focus on narrow areas such as law and intellectual property, technology and forensics, public policy, etc. and examine it within overall literature.
Overall, this research provides future researchers insights for identifying appropriate journals that best align with their research topic to disseminate their work. As well, this research will help future researchers determine novel and burgeoning areas of study to differentiate their work within the field of counterfeit and piracy. As mentioned earlier, future researchers should expand current literature to include emerging research areas (i.e., “Blockchain” and “RFID” as it relates to counterfeiting). For instance, Blockchain technologies are increasingly being discussed as a solution to counterfeiting as it adds traceability to a product or service. In fact, it has been explored as an anti-counterfeiting measure for various industries, from drugs to cryptocurrencies (e.g., Haq & Esuka, Citation2018; Ma et al., Citation2020). Thus, blockchain-based applications may be a viable anti-counterfeiting solution for most industries. Other sparsely populated areas of research to further explore include miscellaneous laymen commodities, such as “Books” or “Clothes”. Demonstrating the difference between anti-counterfeit and piracy for commonplace goods, in comparison to luxury goods, may help retailers to further understand the impulses, tactics, and outcomes of counterfeiting more holistically.
Due to cultural, economic, legal, and historical differences, the characteristics of counterfeit goods might differ between Eastern and Western nations. Counterfeit goods may be more socially acceptable or seen as more cost-effective premium brand alternatives in some Eastern nations. Western societies, on the other hand, frequently place a premium on a product’s authenticity and uniqueness. Economic differences between Eastern and Western nations might affect the market for counterfeit goods. Due of price, it’s possible that counterfeit goods are more common in lower-income Eastern nations. Western nations often have more effective laws protecting and enforcing intellectual property, especially those in Europe and North America. The dedication to and efficiency of eastern nations in protecting intellectual property rights may vary. Consumers’ knowledge of fakes and the risks they pose can vary. Western buyers may actively seek out genuine goods since they are frequently better aware of the risks associated with counterfeit products. Given this backdrop, Eastern countries should continue the trajectory of publishing more prolifically within this field, as each timeframe shows that Western countries dominate this research space. Thus, because most research related to counterfeiting has been conducted by Western countries (predominantly the USA and the UK), the research and subsequent themes are likely to be influenced by a Western-centric lens. Thus, findings may not be globally generalized. Having more prolific and influential papers from the East may ameliorate this incongruency, should it at all exist.
Most of the research conducted in western cultures follows emic approach. The emic approach is concerned with evaluating a cultural construct and comprehending it from the perspective of those who belong to that culture (Gudykunst, Citation1997). This kind of research frequently adapts conceptions, hypotheses, or measurements created in one culture—typically the United States—for use in another society. The etic technique uses broader comparative assessments encompassing two or more cultures, whereas the emic approach concentrates on key elements of the specific culture being studied. In order to better comprehend a construct, etic cross-cultural study specifically compares it across cultures (Schaffer & Riordan, Citation2003). It is important for researchers in eastern countries to use etic approach for conducting counterfeit research.
Additionally, a more diverse research design should contribute to the advancement of bibliometric research. It should be noted that publication trends and citation analyses are limited to research papers using quantitative research methods. Indeed, very few articles utilized qualitative or mixed methods research designs. Since counterfeit is more of a demand than a supply concern in eastern countries due to consumers receptiveness, it is crucial that academics in the east conduct qualitative research to build contextual and in-depth understanding of issues. If utilized more, these methodologies could be a new path for research directions in this area.
Counterfeit products frequently fall short in terms of safety and quality. Businesses and government can collaborate to ensure the security and welfare of customers by comprehending these concerns in the framework of consumer protection. Preventing consumers from unintentionally purchasing inferior or potentially dangerous products is crucial. Businesses have an ethical duty to combat piracy and counterfeiting. These actions can harm a company’s brand, violate moral standards, and erode consumer and partner trust. Businesses can be helped to make ethical decisions by being aware of the ethical implications of piracy and counterfeiting. The intellectual property rights of inventors, innovators, and lawful businesses are violated by counterfeiting and piracy. It is essential to comprehend these concerns in relation to intellectual property rights in order to safeguard innovation, foster creativity, and advance fair competition. Research on piracy and counterfeiting can offer crucial insights that motivate constructive modifications to corporate procedures, governmental policies, and consumer behaviour. This in turn helps to create a company atmosphere that is more moral and sustainable and that values creativity, customer confidence, and fair competition.
Disclosure statement
No potential conflict of interest was reported by the author(s).
Data availability statement
The authors consent to providing, upon reasonable request, all data and materials necessary to substantiate the findings and conclusions in this research.
Additional information
Funding
References
- Alghannam, A., Evans, S., Schifano, F., & Aslanpour, Z. (2014). A systematic review of counterfeit and substandard medicines in field quality surveys. Integrated Pharmacy Research and Practice, 71, 71. https://doi.org/10.2147/IPRP.S63690
- Almuzaini, T., Choonara, I., & Sammons, H. (2013). Substandard and counterfeit medicines: A systematic review of the literature. British Medical Journal Open, 3(8), e002923. https://doi.org/10.1136/bmjopen-2013-002923
- Angus, D., Rintel, S., & Wiles, J. (2013). Making sense of big text: A visual-first approach for analysing text data using leximancer and discursis. International Journal of Social Research Methodology, 16(3), 261–20. https://doi.org/10.1080/13645579.2013.774186
- Barnor, J., Boateng, R., Kolog, E., Afful-Dadzie, A., Entee, E., & Patterson, A. (2020). A Systematic Literature Review of Digital Piracy Research in Information Systems Journals (2010 -2020): Preliminary Insights.
- Baruönü Latif, Ö., Kaytaz Yiğit, M., & Kirezli, Ö. (2018). A review of counterfeiting research on demand side: Analyzing prior progress and identifying future directions. The Journal of World Intellectual Property, 21(5–6), 458–480.
- Braun, J. A., & Eklund, J. L. (2019). Fake news, real money: Ad tech platforms, profit-driven hoaxes, and the business of journalism. Digital Journalism, 7(1), 1–21. https://doi.org/10.1080/21670811.2018.1556314
- Çekirdekci, Ş., & Baruonu Latif, F. O. (2019). Users and non-users of counterfeits: Motivations, emotional outcomes and neutralization processes. Journal of Product & Brand Management, 28(6), 733–746. https://doi.org/10.1108/JPBM-06-2018-1926
- Chatha, K. A., Butt, I., & Tariq, A. (2015). Research methodologies and publication trends in manufacturing strategy: A content analysis based literature review. International Journal of Operations & Production Management, 35(4), 487–546. https://doi.org/10.1108/IJOPM-07-2012-0285
- Chaudhry, P. E., & Stumpf, S. A. (2011). Consumer complicity with counterfeit products. Journal of Consumer Marketing, 28(2), 139–151. https://doi.org/10.1108/07363761111115980
- Chavarria, J. A., Andoh-Baidoo, F. K., Midha, V., & Hughes, J. (2016). Software piracy research: A cross-disciplinary systematic review. Communications of the Association for Information Systems, 38, 31. https://doi.org/10.17705/1CAIS.03831
- Eisend, M., Hartmann, P., & Apaolaza, V. (2017). Who buys counterfeit luxury brands? A meta-analytic synthesis of consumers in developing and developed markets. Journal of International Marketing, 25(4), 89–111. https://doi.org/10.1509/jim.16.0133
- Eisend, M., & Schuchert-Güler, P. (2006). Explaining counterfeit purchases: A review and preview. Academy of Marketing Science Review, 12.
- EUIPO, (2019). Status report on IPR Infringement, why IP rights are important, IPR infringement and the fight against counterfeiting and piracy.
- Fadlallah, R., El-Jardali, F., Annan, F., Azzam, H., & Akl, E. A. (2016). Strategies and systems-level interventions to combat or prevent drug counterfeiting: A systematic review of evidence beyond effectiveness. Pharmaceutical Medicine, 30(5), 263–276. https://doi.org/10.1007/s40290-016-0156-4
- Gudykunst, W. B. (1997). Cultural variability in communication. Communication Research, 24(4), 327–348. https://doi.org/10.1177/009365097024004001
- Haq, I., & Esuka, O. M. (2018). Blockchain technology in pharmaceutical industry to prevent counterfeit drugs. International Journal of Computer Applications, 180(25), 8–12. https://doi.org/10.5120/ijca2018916579
- Hoecht, A., & Trott, P. (2014). How should firms deal with counterfeiting?: A review of the success conditions of anti-counterfeiting strategies. International Journal of Emerging Markets, 9(1), 98–119. https://doi.org/10.1108/IJOEM-02-2011-0014
- Jeong, B. K., Zhao, K., & Khouja, M. (2012). Consumer piracy risk: Conceptualization and measurement in music sharing. International Journal of Electronic Commerce, 16(3), 89–118. https://doi.org/10.2753/JEC1086-4415160304
- Jeung, C. W., Yoon, H. J., Park, S., & Jo, S. J. (2011). The contributions of human resource development research across disciplines: A citation and content analysis. Human Resource Development Quarterly, 22(1), 87–109.
- Karunamoorthi, K. (2014). The counterfeit anti-malarial is a crime against humanity: A systematic review of the scientific evidence. Malaria Journal, 13(1), 209. https://doi.org/10.1186/1475-2875-13-209
- Khan, S., Fazili, A. I., & Bashir, I. (2021). Counterfeit luxury consumption: A review and research agenda. Journal of Consumer Behaviour, 20(2), 337–367. https://doi.org/10.1002/cb.1868
- Koczwara, A., & Dressman, J. (2017). Poor-quality and counterfeit drugs: A systematic assessment of prevalence and risks based on data published from 2007 to 2016. Journal of Pharmaceutical Sciences, 106(10), 2921–2929. https://doi.org/10.1016/j.xphs.2017.05.018
- Lima de, F. R. P., Da Silva, A. L., Godinho Filho, M., & Dias, E. M. (2018). Systematic review: Resilience enablers to combat counterfeit medicines. Supply Chain Management: An International Journal, 12(3), 117–135. https://doi.org/10.1108/SCM-04-2017-0155
- Liu, X., Zhang, J., & Guo, C. (2013). Full-text citation analysis: A new method to enhance scholarly networks. Journal of the American Society for Information Science and Technology, 64(9), 1852–1863. https://doi.org/10.1002/asi.22883
- Ma, J., Lin, S. Y., Chen, X., Sun, H. M., Chen, Y. C., & Wang, H. (2020). A blockchain-based application system for product anti-counterfeiting. Institute of Electrical and Electronics Engineers Access, 8, 77642–77652. https://doi.org/10.1109/ACCESS.2020.2972026
- Mikulic, M. (2023). Total number of counterfeit incidents concerning pharmaceuticals worldwide 2002-2022; Retrieved October 10, 2023 from https://www-statista-com/.
- Palandrani, P. (2020, February 10). A Decade of Change: How Tech Evolved in the 2010s and What’s in Store for the 2020s. Global X ETFs. https://www.globalxetfs.com/a-decade-of-change-how-tech-evolved-in-the-2010s-and-whats-in-store-for-the-2020s/
- Phau, I., Sequeira, M., & Dix, S. (2009). Consumers’ willingness to knowingly purchase counterfeit products. Direct Marketing: An International Journal, 3(4), 262–281. https://doi.org/10.1108/17505930911000865
- Sabanoglu, T. (2022). Global sales loss from counterfeit and pirated goods 2020, Retrieved October 10, 2023, from https://www-statista-com//.
- Samaddar, K., & Menon, P. (2020). Non-deceptive counterfeit products: A morphological analysis of literature and future research agenda. Journal of Strategic Marketing, 1–24. https://doi.org/10.1080/0965254X.2020.1772348
- Schaffer, B. S., & Riordan, C. M. (2003). A review of cross-cultural methodologies for organizational research: A best-practices approach. Organizational Research Methods, 6(2), 169–215. https://doi.org/10.1177/1094428103251542
- Shepherd, D., Whitman, K., Button, M., & Wilson, J. M. (2023). The impact of deviant social media influencers and consumer characteristics on purchasing counterfeit goods. Deviant Behavior, 1–15. https://doi.org/10.1080/01639625.2023.2233041
- Smith, A., McFadden, T., & McFadden, K. (2016). Leximancer User Guide (Manual) (p. 132). Brisbane.
- Staake, T., Thiesse, F., & Fleisch, E. (2009). The emergence of counterfeit trade: A literature review. European Journal of Marketing, 43(3/4), 320–349.
- Statista. (2015). Sales lost due to counterfeit clothing and footwear in Europe 2015, by country; Retrieved October 10, 2023, from https://www-statista-com///.
- Vailshery, L. S. (2022). Share of pirated software in global regions 2009-2017; Retrieved October 10, 2023 from https://www-statista-com.
- van Wijk, J. (2002). Dealing with piracy: Intellectual Asset Management in music and software. European Management Journal, 20(6), 689–698. https://doi.org/10.1016/S0263-2373(02)00118-4
- Ward, V., West, R., Smith, S., McDermott, S., Keen, J., Pawson, R., & House, A. (2014). The role of informal networks in creating knowledge among health-care managers: A prospective case study. Health Services and Delivery Research, 2(12), 1–132. https://doi.org/10.3310/hsdr02120
- Zupic, I., & Čater, T. (2015). Bibliometric methods in management and organization. Organizational Research Methods, 18(3), 429–472. https://doi.org/10.1177/1094428114562629