?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.Abstract
One of the major challenges associated with applying Operations Research (OR) models to disrupting human trafficking networks is the limited amount of reliable data sources readily available for public use, since operations are intentionally hidden to prevent detection, and data from known operations are often incomplete. To help address this data gap, we propose a network generator for domestic sex trafficking networks by integrating OR concepts and qualitative research. Multiple sources regarding sex trafficking in the upper Midwest of the United States have been triangulated to ensure that networks produced by the generator are realistic, including law enforcement case file analysis, interviews with domain experts, and a survivor-centered advisory group with first-hand knowledge of sex trafficking. The output models the relationships between traffickers, so-called “bottoms”, and victims. This generator allows operations researchers to access realistic sex trafficking network structures in a responsible manner that does not disclose identifiable details of the people involved. We demonstrate the use of output networks in exploring policy recommendations from max flow network interdiction with restructuring. To do so, we propose a novel conceptualization of flow as the ability of a trafficker to control their victims. Our results show the importance of understanding how sex traffickers react to disruptions, especially in terms of recruiting new victims.
1. Introduction
Human trafficking is a human rights abuse that has been documented both in the United States and abroad. Although the magnitude of the problem is difficult to determine (Fedina, Citation2015; Farrell and de Vries, Citation2020), estimates from the International Labor Organization suggest that nearly 24,900,000 people were victims of human trafficking in 2016 (International Labour Organization, Citation2017). Human trafficking involves the use of force, fraud, or coercion in order to exploit a person for the purposes of labor or services (labor trafficking) or sexual exploitation (sex trafficking) (Martin and Lotspeich, Citation2014; Carpenter and Gates, Citation2016; Polaris Project, Citation2017; Preble, Citation2019). Despite the growing awareness of the problem, there has been limited research into the development of quantitative tools to address the problem of human trafficking (Konrad, Trapp, Palmbach and Blom, Citation2017; Caulkins et al., Citation2019; Dimas et al., Citation2022). This is partially due to a lack of readily-usable data to appropriately populate these tools. Since these networks are illicit in nature, their operations are hidden to avoid detection (Fedina, Citation2015; Konrad, Trapp and Maass, Citation2017; Konrad, Trapp, Palmbach and Blom, Citation2017; Farrell and de Vries, Citation2020). Current data for analytic approaches often comes from case files (Xie and Aros-Vera, Citation2022), scraped web data on sex advertisements (Keskin et al., Citation2021), or data pertaining to massage parlors (Mayorga et al., Citation2019; White et al., Citation2021). This data can be viewed as the “forward-facing” aspects of the operations of sex trafficking networks in terms of how they interact with the outside world, thus it is (somewhat) publicly accessible. However, there are data gaps around the more internal-facing operations and social connections between traffickers and victims. We seek to develop a way to generate data that can help fill some of these gaps to enable quantitative research on human trafficking networks. In order to highlight the importance of our data collection methods, we first survey the background on sex trafficking networks (Section 1.1) and Operations Research (OR) modeling of them (Section 1.2). We then position our data within the broader landscape of data on sex trafficking (Section 1.3) and highlight our contributions (Section 1.4).
1.1. Background on sex trafficking networks
Analytical tools that seek to understand and disrupt the operations of sex trafficking networks could be quite powerful, assuming their consequences are analyzed by domain experts. We can consider sex trafficking networks as mathematical networks. Networks consist of nodes, representing the entities, and arcs, representing the connections between nodes. A common example is a social network, where the nodes represent people and the arcs represent the different connections between people. Many models in OR involve networks, since they can be used to model the connections between entities and how people and goods can move between different locations or states. Operations researchers have begun to explore how network models can be used to disrupt sex trafficking networks, and have experienced difficulty in obtaining high-quality data (Mayorga et al., Citation2019; Tezcan and Maass, Citation2020; Dimas et al., Citation2022). The focus on describing sex trafficking networks tends to be on empirical studies that lack the type of data needed for OR modeling, as we discuss in the remainder of this subsection.
Cockbain (Citation2018) provides a comprehensive analysis of networks of victims and trafficking in case file records from six law enforcement investigations into domestic minor sex trafficking in the United Kingdom (UK). She analyzes police operational files, court records, prosecution case files, and interviews with convicted traffickers, police investigators and prosecutors to explore the demographics of the traffickers and victims in these cases and the tactics used by traffickers to recruit and retain victims. She produces the social networks of the victims and of the traffickers from these analyses. However, her work does not discuss how to generalize the structures of these networks to systematically create different, yet plausible and realistic, instances of a domestic sex trafficking network. In particular, there is no information on the connections between victims and traffickers.
Dank et al. (Citation2014) conducted a comprehensive analysis of the size and structure of the commercial sex economy in eight major cities in the United States of America (USA). As part of this study, they investigated the operations of sex trafficking, as well as how victims are recruited and managed. They also qualitatively describe how traffickers are socially connected to share information. They noted, from interviews with both traffickers and law enforcement, that traffickers are highly networked socially, but rarely form business partnerships. This work helps to set the foundation for creating realistic domestic sex trafficking networks.
Veldhuizen-Ochodničanová and Jeglic (Citation2021) explore sex trafficking networks with female traffickers by analysing publicly available federally prosecuted case files. Their work identifies operational characteristics, including the number of victims and traffickers, their ages, and whether or not victims are domestic or international, for 44 sex trafficking operations in the USA. They also explore the roles and duties that women performed in sex trafficking networks. Their work does not, however, include the social and operational connections between traffickers and victims.
Mancuso (Citation2014) investigated how a person’s role in a sex trafficking network impacted their centrality measures by analyzing one trafficking network obtained from one case file that spanned Italy to Nigeria. Campana (Citation2016) further explored the structure of that sex trafficking network, focusing on when multiple members of the network participated in the same trafficking events. We augment the social network perspective by incorporating the insights of domain experts and people with lived experiences in sex trafficking networks, elucidating hidden aspects of domestic sex trafficking networks that cannot be determined by advertisements or law enforcement investigations.
1.2. Background on OR modeling of sex trafficking networks
OR models for societal challenges can be supplemented with insights from domain experts from a wide array of disciplines, such as qualitative researchers. Transdisciplinary research is necessary to conduct appropriate research related to human trafficking networks and seeks to address complex societal challenges through the integration of knowledge and methods of different disciplines (Lotrecchiano and Misra, Citation2018). Because of the complexities of the lived experiences of survivors of sex trafficking, domain expertise and effective communication (Martin et al., Citation2022) is necessary to ensure that any analytical tools developed for the purpose of understanding and disrupting sex trafficking networks appropriately consider the human element of these networks. There are many challenges with building a transdisciplinary research team, but the time and effort expended to build such a team can result in scholarly works better grounded in the application area (Sharkey et al., Citation2021). We have applied a transdisciplinary approach in creating the proposed network generator by collaborating with domain experts, who have been investigating human trafficking for over 10 years (see Barrick et al. (Citation2014), Martin and Lotspeich (Citation2014), Martin et al. (Citation2014), Martin et al. (Citation2017), Barrick et al. (Citation2015), Barrick et al. (Citation2021), Barrick et al. (Citation2022)), and a survivor-centered advisory group.
Incorporating domain expertise in the application of OR is critical, since it allows the created models to focus on the true underlying problems faced in the application area. This is especially important when the system cannot be directly observed. Morris (Citation1967) discusses the types of tasks necessary to inform models, whereas Willemain (Citation1994, Citation1995) discusses the process by which experts create models when faced with a practical problem. However, less research has been done on how to integrate domain expertise, both within other academic disciplines and from practitioners, on socially-sensitive, hidden issues, such as human trafficking. Caulkins et al. (Citation2019) discuss the potential types of insights that can be obtained by using engineering models to understand human trafficking and discuss the need to partner with human trafficking domain experts. Sharkey et al. (Citation2021) present a high-level approach for how to integrate this expertise into the modeling process, where they observe that data is one of the key areas where experts need to inform the modeling process.
Dimas et al. (Citation2022) provide a comprehensive review of existing literature in applying operations research and analytics to the understanding and disruption of human trafficking. Researchers are currently considering investigating two different perspectives for sex trafficking networks. One perspective considers how sex trafficking networks interact with different locations. Mayorga et al. (Citation2019) used web scraping from an online escort service to populate a network interdiction model, where the victims in the trafficking network are considered the flow being moved from location to location. Keskin et al. (Citation2021) proposed a process of grouping online advertisements to predict the movement of sex trafficking networks based on where related advertisements appear. White et al. (Citation2021) used web scraping to gather data on illicit massage parlors, and determines potential contributing factors for where illicit massage parlors may be located. These works use a visible, forward-facing part of the sex trafficking networks, the advertisements, to perform their analysis. However, advertisements are not the same as number of victims or people in the network and it is unclear exactly how advertisements map to the underlying phenomena of trafficking itself. The other perspective considers the relationships of the individuals within the sex trafficking network. Cockbain (Citation2018) performs social network analysis of traffickers and victims in six sex trafficking operations in the UK that were disrupted by law enforcement.
Network interdiction has received considerable attention for its ability to assist in the disruption of illicit trafficking, including nuclear smuggling (Morton et al., Citation2007) and drug trafficking (Malaviya et al., Citation2012). As such, it has been suggested to be a tool that may prove useful in combating human trafficking (Smith and Song, Citation2020). There has been limited work in applying network interdiction to human trafficking networks. Mayorga et al. (Citation2019) discuss a robust max flow network interdiction model, where there is uncertainty about the capacities of arcs. Tezcan and Maass (Citation2020) consider a multi-period max flow network interdiction model where there is uncertainty about the success of the proposed interdictions, and the success of interdictions in each time period is dependent on the success of interdictions in the previous time periods. The model is unique in that they consider flow to be the desirability of a trafficker to travel along different routes. These models both model the movement of people across geographic areas. Xie and Aros-Vera (Citation2022) propose a network interdiction model on interdependent networks, building off of the work of Baycik et al. (Citation2018). Their model considers flow to be the victims in the network, being transported between people with different roles in the sex trafficking network. These models all focus on larger-scale operations, and all fail to consider the autonomy of the victims themselves in the trafficking networks. The conceptualization we propose treats victims as more than a product to be moved through the network and, importantly, directly captures the control that exists within trafficking networks.
1.3. Framing data sources on sex trafficking networks
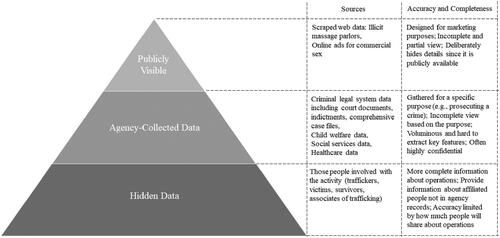
Data sources that can provide sex trafficking network details include (but are not limited to) publicly available data (e.g., web advertisements), secondary agency-collected data (e.g., law enforcement and service providers case files) and primary (hidden) data (e.g., interviews with those who have been a part of, or victimized by, these networks). However, each source has limitations, and no single source will have the full information necessary to perform a proper analysis of the network structure; we highlight the differences in these sources of data in . Although some data on sex trafficking is publicly available, it is limited to aggregate statistics, such as the number and characteristics of victims identified and perpetrators arrested, and does not provide detailed information about other actors in trafficking networks (Motivans and Snyder, Citation2018), or requires significant effort to extract the data for use in analysis.
In general, agency-collected data is used by agencies and organizations to achieve their internal needs. For example, in the case of law enforcement, the focus of information included in investigative and prosecutorial case files is on proving the elements of a specific crime. Details that do not help reach this goal, but would be relevant to construct the full extent of the trafficking network, may be viewed as irrelevant and thus not documented (e.g., information about associates who support trafficking operations without engaging in criminal behavior, such as providing transportation, housing, or childcare). Law enforcement data is further limited in that, by definition, it only includes sex trafficking cases that are known to and officially recorded by law enforcement (Cockbain et al., Citation2020). Those cases may systematically differ from those that do not come to the attention of law enforcement such that victims with certain demographic characteristics may be more likely to self-identify as a victim and law enforcement may be more proactive in identifying victimization in certain sectors (e.g., targeted stings at massage parlors). Because sex trafficking is known to be under-identified (US Department of Justice, Citation2019), the difference between reported and unreported cases could be even more substantial than other crime types. Additionally, extracting the relevant information from the case files to produce the network takes a significant amount of time. Agencies organize and store information in a manner that is most useful for their purposes, not for research. Case files may be incredibly large and include various types of documents, such as handwritten notes, evidence logs, transcripts from victim, suspect, or witness interviews, among others. Sorting, reviewing, and extracting the relevant pieces of information is cumbersome and time-consuming.
Primary data, or hidden data, collected from those involved in trafficking operations can help fill some of the gaps in secondary data. Traffickers and survivors of sex trafficking, as well as individuals who work with these populations, are valuable sources of information on sex trafficking networks, but there are numerous challenges associated with gathering data from them. For example, there are logistical difficulties in simply gaining access to traffickers and survivors and ethical issues around asking survivors to recount their exploitation, which can be retraumatizing. Although interviews provide an opportunity to gather complex and nuanced information about trafficking operations, they tend to rely on small, local convenience samples which may limit the generalizability of the data (Weitzer, Citation2014; Gerassi et al., Citation2017; Cockbain et al., Citation2020).
Prior research on trafficking networks has yielded foundational information on the social connections between victims and traffickers through the review of case files and/or interviews with individuals involved in trafficking operations (Dank et al., Citation2014; Mancuso, Citation2014; Campana, Citation2016; Cockbain, Citation2018; Xie and Aros-Vera, Citation2022) and on the locations and movement of sex trafficking operations through the web scraping of commercial sex advertisements (Mayorga et al., Citation2019; Keskin et al., Citation2021; White et al., Citation2021). This extant research includes both micro-level explorations of specific trafficking networks, with limitations on generalizing the findings to other networks, and higher-level descriptive information on operational characteristics (e.g., number of victims and traffickers and roles in the network), without producing network structures. We build on and bridge this prior work by incorporating the insights of domain experts and people with lived experience to better understand the full variation in how domestic sex trafficking networks realistically operate.
1.4. Our contributions
We propose a novel network generator that outputs network configurations that are representative of domestic USA sex trafficking networks in the real world and that account for realistic variation among operations. This generator takes the number of desired trafficking operations for use in analysis as an input, then produces the operational and social connections between the participants in the network. Our generator is the product of triangulating multiple data sources with the context of the upper Midwest USA, including case file analysis, interviews with people who have domain expertise, and validation with a survivor-centered advisory group. The networks produced by the generator can be used for various analytical models without the need for researchers to collect and validate their own data. Acquiring and cleaning data regarding sex trafficking networks is costly, so this generator will help reduce the barrier to entry for OR researchers to develop and test models to analyze and disrupt sex trafficking. We note that the development process for the network generator is iterative. This current iteration was developed in a specific context (domestic trafficking in the upper-Midwest USA) and will require additional collaboration to expand. The more the generator is used alongside domain experts, the more it can be refined, expanded and further validated for improved accuracy in more and varied contexts.
Additionally, we propose a novel conceptualization of flow for sex trafficking networks; we model flow as the ability of the traffickers to control their victims. Thus, the maximum flow through the network is the total number of victims the traffickers victimize at a particular moment in time. We demonstrate how max flow network interdiction can be applied to these networks and discuss policy recommendations for when the traffickers are able to restructure their operations after the interdiction decisions have been implemented.
This article is organized as follows. Section 2 outlines our objectives when developing the network generator and the process of triangulating data sources to develop the generator. Section 3 addresses the assumptions of the network generator and analyzes sample outputs. Section 4 focuses on a responsible use case study of the generator that applies a novel network interdiction model to disrupt the operations of generated sex trafficking networks. Section 5 discusses limitations of our network generator and proposes directions for future qualitative research to improve the applicability of the network generator. Section 6 concludes the article and discusses directions for future research.
2. Development of the network generator
The generator focuses on the social and operational connections of the people within domestic sex trafficking networks with specific operational characteristics. We recognize that these networks are abstractions of the true operations of sex trafficking; the proposed network generator cannot appropriately capture all of the complexities of the lived experiences of trafficking victims and survivors, nor can it account for the human rights abuses and violence that occur in sex trafficking networks. This is a limitation of any analytical approach to understanding the issue of sex trafficking.
The nodes represent the people in the network, and arcs represent the connections between them. The participants we consider are the traffickers, so-called “bottoms”, and victims. The term “bottom” is used in the literature and in some operations to refer to someone who is a victim, but has gained trust and responsibility from the trafficker and thus has additional responsibilities within the trafficking operation (Belles, Citation2018). They might be viewed as the highest ranking victim and function as a sort of right-hand person in the operation (Dank et al., Citation2014). However, there is a gray area in that bottoms may experience varying degrees of force and coercion, since there is always a chance they will lose this status and be forced to trade sex (Roe-Sepowitz et al., Citation2015). Likewise, a trafficker can expect or force some bottoms to exploit other victims (Belles, Citation2018; Roe-Sepowitz, Citation2019). For purposes of the generator, victims are split into two groups based on age, either minor or adult. Published research and insights from our survivor-centered advisory group suggest that there are operational differences in how traffickers interact with minors versus adults, due to developmental differences and harsher legal penalties for trafficking minors (Marcus et al., Citation2014).
In order to clarify the distinction between the activities of a specific trafficker and the activities of all traffickers, we additionally define the distinction between an operation and network. Henceforth, when we refer to an operation, we are referring to a single trafficker, their bottom (if they have one), and their victims. The network refers to all operations generated, where the number of operations is a user-specified input. We also want to provide a distinction to connections that are necessary for the function of trafficking operations, as opposed to connections that are purely social, although we recognize that social connections may help further the activities of a trafficking operation. We define an operational arc as an arc that is necessary for the functions of the trafficking operation. An example of this is an arc between a trafficker and a victim, as that connection represents that the trafficker is able to control the victim. We define a social arc as an arc that does not necessarily have any immediate operational function associated with it. An example of this is an arc between two victims. Such a connection may not be necessary for the act of sex trafficking. However, if one of those victim were to be promoted to be the bottom, that arc would gain an operational function.
2.1. Transdisciplinary research approach: Creation and validation
We apply a community-based participatory research approach in creating our network generator. Community-based participatory research approaches have been successfully applied to solve problems in health sciences and are especially impactful when the collaboration between researchers and community stakeholders is 4 years or longer (Brush et al., Citation2020; Haapanen and Christens, Citation2021). The survivor-centered advisory group brings together lived experience and deep social service and advocacy knowledge about sex trafficking, with many members possessing multiple forms of wisdom. The advisory group currently consists of five members, and two past members also contributed to this work. Together, advisory group members have over 90 years of combined experience in survivor-led social service, healing, and advocacy. For more details regarding the advisory group, their role, and transdisciplinary team building, see Martin et al. (Citation2022). Our survivor-centered advisory group was formed in 2018 and has helped co-create research assumptions, approaches, knowledge, and research directions. We then applied traditional, rigorous qualitative research methods, alongside OR mathematical modeling, to inform this co-creation process.
Our research methods helped to synthesize and triangulate multiple sources of data to create and validate the assumptions built into the network generator. According to Denzin (Citation2012), p. 82, “[t]he combination of multiple methodological practices, empirical materials, perspectives, and observers in a single study is best understood as a strategy that adds rigor, breadth, complexity, richness, and depth to any inquiry.” Our transdisciplinary method inserts qualitative data at key decision-points in the mathematical modeling procedures, similar to the approach discussed by Sharkey et al. (Citation2021). In particular, their approach discusses the importance of qualitative input into modeling decisions (which we have incorporated later in our novel conceptualization of flow in sex trafficking networks) and gathering data to populate resulting models.
For this first iteration of the network generator we used three sources of data: (i) documents from US federal prosecution of trafficking in Minnesota that were made publicly available (N = 13); (ii) targeted key informant interviews (N = 10); and (iii) secondary analysis of key informant interviews from previous studies (N = 246) (Martin et al., Citation2014; Martin et al., Citation2017). From these sources, (i) is an example of agency-collected data, and (ii) and (iii) are examples of hidden data. In addition, our survivor-centered advisory group provided initial drawings of sample networks based on their experiences, and iteratively reviewed and critiqued assumptions and parameters in the network generator to assess whether it reflected their experiences and knowledge of other trafficking operations. and in Appendix A present sample network drawings provided by the survivor-centered advisory group during one of our meetings with them. Data sources and analysis for this study focused on sex trafficking operations in the upper-Midwest region of the USA. For this first phase of development of the network generator, data analysis focused on smaller operations with only one trafficker. We used an analytic method called triangulation to identify and fill gaps within each data source, by comparing and contrasting content within and between sources.
2.1.1. Analysis of federal prosecutions of sex trafficking cases
Research staff obtained the court case docket and indictment for cases prosecuted in Minnesota between 2009 and 2015. To transform this data into usable information for mathematical modeling, we extracted nodes (people, places, and things) and arcs (connections between nodes) and entered them into an excel spreadsheet. These data were then converted into network structure outputs for visualization.
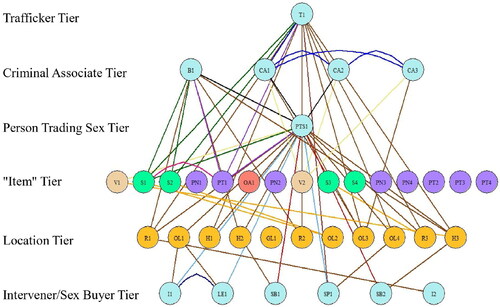
The research team, including the survivor-centered advisory group, visually inspected each output for verification and completeness. We wanted to know if these visualizations reflected what we would expect to see based on real-world experiences. , provides an example of an output, visualizing the connections between people, places and things described in one of the federal case files. For this case, the advisory group noted that many key players and connections they would have expected to see where not represented in this diagram. Most notably, there was no record in the case file connecting the trafficker (T1) with their bottom (B1), which would be an expected connection. This direct connection may not have been necessary to prove the elements of trafficking in this case. The team identified many such instances where key relationships for the functioning of a trafficking network were not reflected in the case file documents. Across cases, we noted a lack of documentation of similarly important relationships within networks. Moreover, these case files spanned a short duration of time, thus only capturing a small snapshot of the trafficker’s operation in that moment in time. For the network from , the recorded operations spanned a week.
2.1.2. Analysis of interview data
In semi-structured interviews with key informants, we asked 10 knowledgeable domain experts to provide details about the size and structure of relationship networks in trafficking operations, including number of victims and the social connections between victims. This data was thematically coded to extract typical ranges in size and organization structure of networks. Using this thematic framework, we systematically reviewed 260 stakeholder interview data from past projects to extract additional information to guide model parameters and assumptions. We found agreement and coherence between the information garnered from key informant interviews and the secondary analysis.
2.1.3. Data triangulation
The above sources all have strengths and missing information. By triangulating these sources, combined with validation from the survivor-center advisory group, we developed a basis for the rules and parameters for network generation. We devised rules from consistencies across these multiple data sources, such as the distribution of number of victims within an operation, and used statistics and qualitative descriptions to estimate parameters for these rules. Once all necessary parameters were determined, we generated a set of networks to review with the qualitative researchers and survivor-centered advisory group to bring domain expertise in conversation with rules contained in the network generator. The OR team prepared presentations for the qualitative research team and advisory group to discuss the merits and shortcomings of the current iteration of the generator. This iterative process sought to validate the model against real-world experience and expectation. Members of the qualitative research team produced detailed analytic memos and near verbatim transcriptions of survivor-centered advisory group meetings to capture critiques and missing information. These conversations resulted in adjustments to model parameters. Between meetings, questionnaires and surveys were prepared to help the OR team better implement the solicited feedback into the generator. This process of reviewing networks produced by the generator with the domain experts was repeated multiple times.
We made several important changes to the network generator during each iteration. For example, the probability distribution of the number of victims in a trafficking operation was substantially revised based on advisory group feedback. in Appendix A displays the distribution incorporated in the current iteration of the generator. Discussions with the advisory group, in combination with data surfaced in the secondary review, also led us to revise the procedure the generator used to determine social connections between victims. We included the option for a trafficking network to separate victims into separate clusters who reside together, but do not necessarily know each other. The domain experts were then able to further refine the choice of parameters for this method, such as average and maximum cluster size. To the best of our knowledge, very little literature explores social connections between victims (Cockbain, Citation2018). Conversations with the advisory group shed some light on these connections, such as smaller groups of victims being housed together and separated from the rest of the victims.
2.2. Details of the network generator
Our network generator produces a network of nT single trafficker operations, where nT is an input. Interested researchers may access the network generator from the authors upon reasonable request. For each operation i, we first generate the number of victims nvi a trafficker has in their operation. The distribution from which we sample is based on statistics gathered and validated by the domain experts. Based on the number of victims, we randomly determine if there is a bottom in the network. The probability of a bottom in the network grows significantly with respect to the number of victims, with a bottom almost surely present when there are at least six victims. If it is determined there is a bottom in the network, a new node is added to be the bottom, as the statistics collected for number of victims did not include a bottom as a victim. These observations were made based on our secondary analysis of previously collected interview data in (Martin et al., Citation2014; Martin et al., Citation2017).
We next determine how a trafficker is managing the victims within their operation. We do so by partitioning the victims into “clusters” (Melander et al., n.d.). Clusters can be thought of as groups of victims who were recruited roughly at the same time, or live in the same location. Each victim in a given cluster is connected to every other victim in the same cluster, i.e., a cluster forms a clique in the operational network. We first generate all feasible partitions of the number of victims, then remove partitions where any part is larger than six. This was determined to be the maximum size of a cluster based on our data sources and verified by our advisory group. For example, if there were seven victims in an operation, all partitions would be feasible except the case where all victims are in a single part. We then randomly select from the set of remaining partitions (Melander et al., n.d.). We estimated the sizes of clusters, and distribution of cluster sizes w, by triangulating our multiple data sources and verified these parameters with our expert survivor-centered advisory group through group discussions and member surveys. Let be the set of all feasible clusters. We say
is a set of clusters, where
and pi is the number of victims in the ith cluster. When there is more than one cluster, we randomly determine the age group of the victims for the entire cluster, where the probability of the cluster consisting of minors increases with cluster size. When a cluster consists of two victims, we additionally allow for one victim to be a minor and one victim to be an adult. This is representative of a situation where a pair of victims may be family members (e.g., mother and daughter) or where there is a parental-type relationship. These choices regarding ages and clusters were suggested by the advisory group.
We then determine how the trafficker (and bottom) interact with the clusters. If there is a bottom, we first determine how the victims are connected to the trafficker and bottom, as all victims are not necessarily connected to both the trafficker and the bottom. We randomly determine which clusters are connected to the trafficker, then which clusters are connected to the bottom. Similarly, if the trafficker (or bottom) is not randomly assigned any clusters, they will be assigned to the largest cluster. The probability of a cluster being assigned to the trafficker and bottom varies based on the age of the victims in the cluster and the size of the cluster. This is due to a trafficker potentially not wanting to have direct contact with a victim who is a minor, as prosecuting a sex trafficking case is easier if the victim is a minor, and the minimum punishments are more severe (Marcus et al., Citation2014). If there is no bottom, all victims are connected to the trafficker. If there is a single cluster, then age and connections to trafficker and bottom are determined individually, as if each victim were in their own cluster. We lastly refine upon the social network amongst victims within the operation by expanding upon the initial set of arcs provided by the clusters. We then determine any social connections between victims in different clusters. For each pair of victims in different clusters, we randomly determine if an arc between them should be added to the network. The probability of an arc being added between them is dependent on the age of the victims, since minor victims tend to be recruited into trafficking via their social network (Marcus et al., Citation2014). Algorithm 1 in Appendix B formalizes the procedure of generating a single trafficker operation.
Each choice in the development of the generator was carefully made based on information from previous literature, the data sources reported in Section 2.1, and meetings with the qualitative research team and the survivor-centered advisory group. reports the main data source used to refine the parameters used in the relevant steps in the generator. Although the main sources were used to inform the initial choices, other sources were used to verify and refine the choices.
Table 1. Main data sources that inform each step in the network generation procedure.
This procedure is repeated for the number of operations desired. After all operations are generated, we generate the social network amongst traffickers. From Dank et al. (Citation2014), we know that traffickers are connected to share information about profitable locations and law enforcement activity. Since little further is known about how traffickers are connected socially, we use the Watts–Strogatz model to generate the social network amongst traffickers (Watts and Strogatz, Citation1998). The Watts–Strogatz model is often used for social networks, as it produces networks with the “small world phenomena,” which indicates that the shortest paths between pairs of nodes include a small number of arcs and that nodes tend to be grouped into clusters, with a larger number of arcs between nodes in the same cluster than between nodes in different clusters. After the trafficker social network is generated, we then generate social connections between victims in different trafficking operations. Again, we impose a higher likelihood of two victims who are minors being connected over adult victims. Parameters regarding social connections were validated by the domain experts and advisory group. We formalize our generator in Algorithm 2 in Appendix B.
3. Outputs
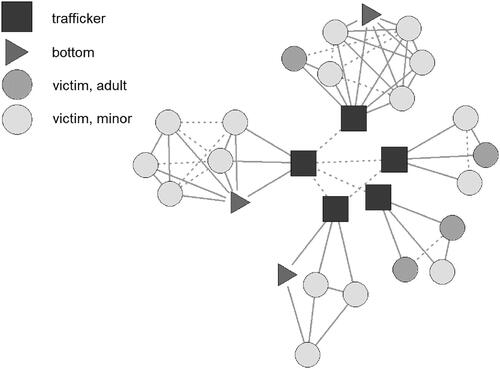
We now compare sample output operations from our domestic sex trafficking network generator to sex trafficking networks constructed in previous research. Trafficker nodes are squares, bottom nodes are triangles, and victims nodes are circles. Nodes representing victims who are adults are a darker shade of gray than nodes representing victims who are minors. Arcs are solid if they are representing an operational arc (e.g., trafficker to victim), or dashed if they are representing a social arc. We include arcs between victims in the same cluster as an operational arc because we expect that victims in the same cluster will be living and working together. displays a sex trafficking network with five operations. Each operation is displayed individually in Appendix C.
In these five operations, three operations have a bottom. In 25 generated outputs, 20 operations have bottoms, and every operation with more than five victims had a bottom. Of the eight operations with four victims, only one operation does not have a bottom. Of the four operations with three, half of them have a bottom. Both networks with two victims do not have a bottom. Additionally, of the 25 operations, five have one cluster, 16 have two clusters, two have three clusters, and one has four clusters. In the operation with four clusters, three of them are isolated victims. The median cluster size has two victims, with a maximum cluster size of five victims.
We compare centrality measures of the output operations in against those listed in Cockbain (Citation2018) and the sample operations provided by the advisory group in Appendix A (labeled AG). The advisory group provided two networks, a single trafficker operation, and a multiple trafficker operation with three traffickers. We consider each trafficker’s operation in the multiple trafficker operation separately, to provide a more accurate comparison. We exclude Operation Retriever, as the number of victims in that network is significantly higher than the other networks in the text. Note that this analysis is comparing operations from two different locations (Midwest USA versus UK), and so trafficking networks may be structured differently between the two locations.
As can be see in , the number of victims in operations produced by the network generator is similar to the number of victims in the operations investigated by Cockbain and in the operations described by the survivor-centered advisory group. Additionally, the arc densities and degree centralization scores of the synthetic operations all fall in the range of arc densities and degree centralization scores of the real operations. Excluding operation 4, operation AG1, operation Engage, and operation Central, which are all complete networks, the arc densities of the synthetic networks are higher than that of operations Span and Chalice, whereas the degree centralization scores of the synthetic networks are lower than the real networks investigated by Cockbain. However, the synthetic networks have degree centralization scores similar to that of the networks provided by the advisory group. This is likely due to the cluster structure in the synthetic networks, which was recommended by the advisory group. In operations with larger clusters, the arc density will be larger and the degree centralization will be smaller. The cluster structure also likely explains the significant difference in the betweenness centralization scores between the synthetic and real networks. Although operation 3 has a betweenness centralization score similar to operations Span and Chalice and AG2.3, operations 1 and 2 have betweenness centralization scores of one, matching AG2.2. This is because these three networks have the same structure: one cluster with two victims, and one isolated victim, with a single arc from the isolated victim to one victim in the cluster. These results suggest that although there is variation in the synthetic networks, they do share similarities with those produced through case file analysis on sex trafficking networks, as well as the networks provided by the advisory group. This is important, as the generator is able to create more synthetic networks that are reflective of multiple data sources, which can be used for OR analysis.
Table 2. Comparison of centrality measures on victim networks between operations produced by the generator, provided by the advisory group, and the operations studied in Cockbain (Citation2018).
We additionally provide an analysis of the spectrum of the Laplacian matrices of the networks to better understand the similarities in structures (Tantardini et al., Citation2019). Using spectral methods to compare networks was originally proposed by Wilson and Zhu (Citation2008), where they identify that the spectral distance between networks, i.e., the Euclidean distance between the eigenvalues of the Laplacian matrices, provides a strong measure of network similarity. For brevity, the tables of results appear in Appendix D. compares the spectral distances between our synthetic networks and both the networks provided by our advisory group and the networks described in Cockbain (Citation2018). additionally compares the spectral distances between advisory group and the networks described in Cockbain to provide an understanding of the deviation between real networks. In order to provide a comparison between networks of different sizes, we follow the procedure of Wilson and Zhu (Citation2008) of adding zeros to the spectrum of the smaller network until the number of eigenvalues is the same. Since the spectral distance is a symmetric measure, we only include the upper right triangle for repeated entries in the table. We note that the largest eigenvalue from all networks is 10.207 and the smallest eigenvalue is zero.
demonstrates that there can be a significant deviance in the victim networks in sex trafficking operations. In particular, Operation Retriever is significantly different from both the networks provided by the advisory group and the synthetic operations. This is likely due to the size differences between this network and other networks. We note that each data source seems to be more consistent with other networks from the same data source than the other data source. demonstrates that our generator is able to produce networks similar to both data sources. In particular, Operations 1, 2 and 4 are more similar to the networks provided by the advisory group, whereas Operations 3 and 5 are more similar to the networks shown in Cockbain (Citation2018).
4. Responsible use case study: Network interdiction
We now present a case study on how an output of the network generator can be used as data for OR tools. We consider interdiction prescriptions via the max flow network interdiction problem (MFNIP) (Wood, Citation1993). In a network with source node
and sink node
and capacities on the arcs
the max flow problem seeks to find the total amount of flow from s to t such that the flow on each arc is at most the capacity of that arc, and the amount of flow into a node is the same as the amount of flow leaving that node. The MFNIP converts that problem to a two-player game, where one player, known as the attacker, seeks to minimize the maximum flow through the network by choosing a subset of arcs to reduce their capacity to zero, subject to a budget and other constraints. The other player, the defender, then operates the network as per the max flow problem. Max flow network interdiction has successfully been applied to disrupting illicit drug trafficking networks (Malaviya et al., Citation2012; Baycik et al., Citation2018, Shen et al., Citation2021; Kosmas et al., Citation2022), and has been identified as an analytical tool to help address sex trafficking (Smith and Song, Citation2020). Some max flow network interdiction models have been proposed for disrupting human trafficking (Mayorga et al., Citation2019; Tezcan and Maass, Citation2020). We apply the model of Kosmas et al. (Citation2022), max flow network interdiction with restructuring (MFNIP-R), to networks outputted by our network generator. Their model accounts for how drug traffickers will respond to disruption efforts. This response is also a key aspect for disrupting sex trafficking, not merely displacing it. Accounting for responses from traffickers is vital to responsible policy recommendations, as research suggests that removing individual victims from a trafficking situation, while clearly necessary, might paradoxically result in more victims being recruited into trafficking after an interdiction (Martin and Lotspeich, Citation2014; Caulkins et al., Citation2019). This paradox aligns with the theoretical analysis in Kosmas et al. (Citation2022), where they observed that current law enforcement policy typically recommended interdicting participants in drug smuggling networks that would trigger restructuring arcs that would cross the minimum cut. We find that a similar situation occurs for our conceptualizations of sex trafficking networks, indicating that both disrupting current operations and their ability to restructure (especially recruit) is critical.
Kosmas et al. (Citation2022) defines MFNIP-R as the following. Given a network with source node s, sink node t, set of restructurable arcs A
and node and arc capacities
let Y be the set of feasible interdiction plans and let Z(y) be the set of feasible restructurings dependent on the chosen interdiction plan. First, the attacker chooses an interdiction plan
setting the capacity of the interdicted nodes to zero. Next, the defender chooses a restructuring plan
to add arcs to the network, increasing their capacity from zero to pre-specified values uz. Lastly, the defender operates the network to maximize flow through the network. We note that, contrary to standard max flow network interdiction models, the model of Kosmas et al. (Citation2022) interdicts nodes instead of arcs, representing the removal of a participant in the network, rather than the connections between participants. An equivalency between node interdiction and arc interdiction has previously been demonstrated in Malaviya et al. (Citation2012).
4.1. Modeling domestic sex trafficking with max flow
Compared with drug trafficking, it is less clear in sex trafficking networks of traffickers and victims what an interdiction might seek to restrict in terms of flow. The “product” being sold in sex trafficking is people and a sexual experience (Martin et al., Citation2014; Martin et al., Citation2017). The commercialization and sale of sex to a sex buyer may in some ways be analogous to the sale of drugs since both are commodities. However, the flow within the network is not the same because people (and their labor) are not equivalent to drugs. Much more work is needed to conceptualize how this concept of “flow” should best be applied to sex trafficking networks. Thus, we posit a novel interpretation of the maximum flow problem as it pertains to traffickers and victims of trafficking within a sex trafficking operation. Flow could represent the ways traffickers exhibit control over victims and the sex acts that victims are forced to perform. Thus, flow is exerted through control over trafficking victims in order to make them (and their labor) a product to sell (Martin et al., Citation2014). This conceptualization was developed in collaboration with the domain experts to reflect that the network flows in our approach are of different nature compared with traditional supply chain models.
In a network framework, we let the capacities of trafficker and bottom nodes represent the number of victims they are able to manage, and the capacities of victims represent that they are able to be controlled. Interdicting a node represents that node can no longer control or be controlled, and restructuring an arc represents establishing a connection that allows for a trafficker or bottom to control a victim. We note that, in our model, an interdicted node has its capacity set to zero, representing the participant being fully removed from the network. An interdiction can be practically interpreted as any action that removes a participant from the network, such as law enforcement arresting a trafficker. Another example would be an agency providing a victim access to resources (e.g., safe and secure housing, money) that would allow them to be able to leave their trafficker. It must be noted that the flow that is being modeled is exerted through violence, manipulation, and harm. For this discussion, we will focus on control within the network and on situations in which a trafficker needs to maintain control over a certain number of victims. For the sake of the model, we postulate that a trafficker has a specific number of victims they wish to have under their control at any given time. This is a preliminary exploration; more empirical research is needed to verify and extend modeling to understand the specificity and nuances of sex trafficking.
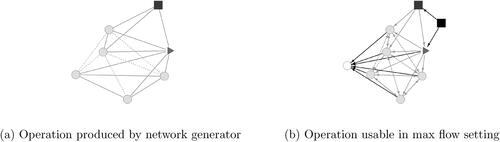
To convert an output of the network generator to a network usable in max flow network interdiction, we need to add in a source node and sink node. We add arcs from the source node to each trafficker and bottom node with infinite capacity, and arcs from each bottom and victim node to the sink with capacity one. All arcs incident to the trafficker are directed out of the trafficker, and all arcs incident to the bottom and a victim are directed out of the bottom and into the victim. Arcs between victims are replaced with a pair of arcs between the victims, one in each direction. The capacity of each trafficker node is the number of victims they can control, the capacity of each victim node is one, and the capacity of each bottom node is the number of victims they can control plus one. This is to recognize that bottoms are victims too, and that their role in sex trafficking networks does not make them any less of a victim than the other victims. Note that, with our modeling choices, it is not necessary to directly model the control of a bottom with an arc from the trafficker to them as the arc from the source can model this control, even though this arc will always be included in operations produced by the network generator. For ease of notation, we define T to be the set of traffickers, B to be the set of bottoms, and V to be the set of victims. Capacities for the traffickers and bottoms are chosen in such a way that the maximum flow through the network is the total number of victims currently in the network (including bottoms). The arcs between traffickers are only used to determine restructurable arcs, and are assigned capacity 0. demonstrates this conversion on a sample operation, where the black square node is the source node, the white circle node is the sink node, and the black arcs are the newly added arcs.
We now define the set of restructurable arcs. The types of restructurable arcs were determined by analyzing transcripts from previous meetings with the qualitative research team and survivor-centered advisory group. For the types of restructurable arcs, we allow for traffickers to recruit each other’s victims (or likewise, a victim choosing to join a different trafficker’s operation), traffickers to give or take victims from their bottom, the recruitment of new victims, back-up traffickers to take over an interdicted trafficker’s operation, the promotion of a new bottom, and traffickers to give victims to their newly promoted bottom. As in Kosmas et al. (Citation2022), we define sets of restructurable arcs based on whether a restructurable arc can be initiated by a trafficker or by a victim. An “out” restructuring (arcs belonging to
) represents a trafficker restructuring to a new victim after having one of their victims interdicted. An “in” restructuring (arcs belonging to
) represents a victim being recruited into a new operation after their trafficker has been interdicted. We start with
and
consisting of the set of arcs between traffickers and the victims of traffickers they know. For
and
and
if there exists a
such that
and
To allow for a trafficker i to assign a new victim k to their bottom j, we include
if
Likewise, we allow for a trafficker i to take a victim k from their bottom j by including
if
and
To model the recruitment of new victims, we introduce an additional set of nodes V We include an arc from each of these nodes to the sink node in the arc set A. We then randomly determine a subset of traffickers that can restructure to each recruitable victim node, and add arcs between the traffickers and the recruitable victim to
This results in these nodes having no arcs into them in the initial network, meaning no flow can pass through them, but flow can pass through them if an arc ending at the recruitable victim is restructured by a trafficker. To model an operation having a back-up trafficker, we introduce an additional set of nodes T
to be the set of back-up traffickers for certain operations, which is represented by ordered pairs (i, h), where trafficker i can be replaced by back-up trafficker h if trafficker i is interdicted. We add arcs from the back-up trafficker h to all of trafficker i’s victims to the arc set, and include an arc (s, h) in the set of restructurable arcs. As with recruitable victims, there are no arcs into back-up trafficker h in the initial network, so no flow can pass through the node, but restructuring the arc (s, h) allows for flow to pass through the node. To model the promotion of new bottoms, we define the set B
as the set of victims which may be eligible to be promoted to the role of bottom, which is represented by ordered pairs (j, k), where victim k may be promoted if bottom j was interdicted. If victim k is promoted to the role of bottom, their capacity is increased by
allowing flow to pass from victim k to the victims to which they are adjacent. We include arc (s, k) in the set of restructurable arcs
indicating that if this arc is restructured, the newly promoted bottom is able to receive flow from the source as did the original bottom. We also allow for a trafficker i to assign a victim l to the newly promoted bottom k by including arc
if
that can only be restructured if (s, k) has been restructured. The capacities of back-up traffickers are chosen to be 75% of the capacity of the initial trafficker (minimum one), and the capacity increase of promoting a victim to be a bottom is chosen to be 66% of the capacity of the initial bottom (minimum one). These choices were made to reflect a decrease in network functionality, due to a new person taking over the act of trafficking.
Restructurable arcs between an existing trafficker and existing victim are included in whereas all restructurable arcs are included in
Note that
in our model. This is because the only arcs belonging to
are between a victim currently in the network and a trafficker, which can also be restructured by the trafficker. Thus, these arcs also belong to
For brevity, we define the formal mathematical model in Appendix E. We apply the method of Kosmas et al. (Citation2022) to solve this model. Their method is a column-and-constraint generation (C&CG) method, where, when a previously visited restructuring plan is infeasible with respect to the current interdiction plan, the only feasible components in that restructuring plan are used to determine a lower bound on the true objective value. This method has been shown to be effective in solving their model faster than standard C&CG methods, particularly when recruitment is modeled.
4.2. Computational results
We implement this interdiction model on five generated networks, each with five operations, as well as a five operation network provided by the advisory group. The advisory group network was created by merging two copies of the single trafficker operation and the multiple trafficker operation to create a network with the same number of traffickers as the synthetic networks. reports the number of nodes, and number of bottoms and victims, in each network.
Table 3. Sizes of generated networks.
We set the cost of interdicting a trafficker to be eight, the cost to interdict a bottom to be four, and the cost to interdict a victim to be two. Interdicting a bottom reduces the cost of interdicting their trafficker by three, and interdicting a victim reduces the cost of interdicting their trafficker by one. Each trafficker has a budget of eight to restructure their operation. The cost to restructure to a victim currently in the network is one, as is the cost to take a victim from their bottom or give a victim to their bottom. The cost to recruit a new victim not currently in the network is two. The cost for a back-up trafficker to come into the operation is four. The cost to promote a new bottom is five, and the cost for the trafficker to give them a victim is two. We set the number of recruitable victims to be 40% of the number of victims in the network. A trafficker will have a back-up trafficker if they have at least four victims (including a bottom). If a trafficker has a bottom, the number of victims that can be promoted to become a bottom is half of the number of victims to which the trafficker is connected (minimum one). We note that parameters were chosen to demonstrate how a network interdiction model would be applied to these networks, and that future work in applying network interdiction to sex trafficking networks would require further collaboration and validation with domain experts.
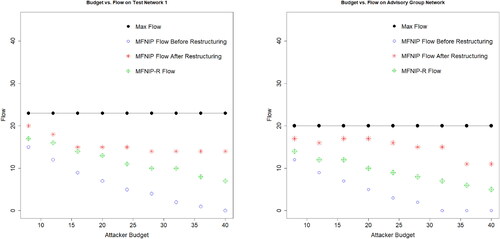
All instances were solved within 2 hours. Experiments were conducted on a laptop with an Intel® CoreTM i5-8250 CPU @ 1.6 GHz - 1.8 GHz and 16 GB RAM running Windows 10 using AMPL with Gurobi 9.0.2 as the solver. demonstrates the flow through the network over different attacker budgets. Results on other networks can be found in Appendix F. In this figure, the dotted black line represents the total number of victims (including bottoms) in the network. The hollow circles represent the interdicted flow determined by MFNIP. The stars represent the flow after optimally restructuring the network in response to MFNIP’s interdictions. The diamonds represent the interdicted flow determined by MFNIP-R. Network 1 is the network in .
In each network and across all budget levels, the traffickers are able to recover a significant amount of flow after restructuring in response to the MFNIP recommended interdictions. This is primarily due to being able to recruit new victims when victims are primarily interdicted, and being able to replace interdicted traffickers with back-up traffickers when traffickers are primarily interdicted. However, when we are able to account for how the traffickers will restructure in response to interdiction, we are often able to reduce the flow. demonstrates the interdiction recommendations for the network in . Columns 2 - 4 display the number of traffickers, bottoms, and victims that MFNIP recommends to interdict, and columns 5 - 7 display the number of traffickers, bottoms, and victims that MFNIP-R recommends to interdict.
Table 4. Interdiction recommendations from MFNIP and MFNIP-R for Network 1.
A clear distinction between the two recommended plans is the number of bottoms that each model recommends to interdict. Consistently across all attacker budgets, MFNIP recommends interdicting at least as many bottoms as does MFNIP-R. This observation is consistent across all tested networks. This is likely due to MFNIP-R identifying that bottoms have limited ability to restructure the network, as the only way they can acquire new victims is if their trafficker assigns them new victims. This finding is also consistent with the network provided by the advisory group, see , where MFNIP recommends interdicting all bottoms as soon as the budget allows for it, and continues this recommendation for every larger budget level. This seems to highlight that limiting the ability of the trafficker to restructure after disruptions may be just as important as disrupting the current operations, which is similar to the findings of Kosmas et al. (Citation2022). Additionally, network 3, where every operation has a bottom, had the smallest gap in flows projected by MFNIP and MFNIP-R. These observations suggest that better understanding how bottoms help operate the network both before and after disruptions may be critical to understanding how to more effectively dismantle sex trafficking networks. The advisory group confirmed the importance of these findings in implementing effective disruptions.
Table 5. Interdiction recommendations from MFNIP and MFNIP-R for network provided by the survivor-centered advisory group.
5. Limitations and directions for future qualitative research
As the lack of data is the challenge we wish to address, our network generator has many limitations about which a responsible user needs to be aware. First and foremost, our network generator is built on sources about domestic sex trafficking cases within the Midwest of the USA, since the case file analysis focused on the cases in the Midwest and the advisory group’s experiences involve operations within the Midwest. As such, their experience is not necessarily representative of sex trafficking as a whole. It may be that biases based on their experience are built into the network generator. However, the more the network generator is used and feedback is provided regarding operations in more locations and contexts, the more accurate we will be able to make it over time. Users should collaborate with domain experts in their geographical location to understand how sex trafficking networks in their location may operate differently from that of the Midwest.
Another limitation is regarding the social connections between traffickers. It is known that some traffickers are connected socially with other traffickers, but there has been little research on what these social networks look like. This gap prevents us from developing more authentic trafficker social networks. Further research focused on how traffickers are connected, both socially and professionally, will allow for more accurate trafficker social networks to be produced.
How bottoms interact with the network is also an area where further research is needed. Although the role of bottoms in their own trafficking operation has been previously studied, little is known on how they are connected to other traffickers and victims outside of their operation. It is also not well known what causes a trafficker to want or need to have a bottom in their network. Here, we base the likelihood of there being a bottom on the number of victims in the trafficker’s operations. Future qualitative research can ascertain why a trafficker chooses to promote a victim to the role of the bottom and how having a bottom allows a trafficker to grow their business.
6. Conclusions
We presented our network generator for producing synthetic domestic sex trafficking networks. The networks produced include the operational and social connections between traffickers, bottoms, and victims. Data sources including publicly available federal case files and interviews with domain experts were triangulated to determine the basis and parameters in the generator. The generator was further validated by domain experts, including a survivor-centered advisory group. As qualitative research furthers our understanding of sex trafficking networks, we can refine and advance the functionality of the generator in future iterations. An example of this is on how traffickers collaborate, which would allow us to build multiple-trafficker operations. The network generator and generated networks in this study are available from the corresponding author upon reasonable request.
This generator allows for the OR community to engage in human trafficking research without needing to go through the time-intensive process of collecting and cleaning their own data. We demonstrate how network interdiction can be applied to networks produced by this generator. In particular, we proposed a novel conceptualization of flow which considers the ability of the traffickers to control their victims. Our results suggest that better understanding the roles of bottoms in maintaining operations after disruptions occur may be key to more impactful disruptions.
The advisory group has suggested three avenues of future research to improve the applicability of the network generator. The first avenue is to include a temporal component. From their insights, the victims in an operation can change rapidly (in some cases daily) depending on many different factors. Being able to account for a temporal component can allow for a better understanding of how long term disruption decisions can be made. The second avenue of future research is to include a spatial component. Trafficking operations may move to different locations based on profit and law enforcement activity. Understanding how trafficking operations move between different locations will be essential to effective disruption prescriptions. The third avenue of future research is to produce networks where multiple traffickers are collaborating in larger trafficking operations.
Reproducibility Report
Download MS Word (33.5 KB)ST_Network_Generator_Online_Supplement.pdf
Download PDF (630.4 KB)Acknowledgments
We recognize that our research cannot capture all the complexities of the lived experiences of trafficking victims and survivors. We acknowledge the significant contributions of our survivor-centered advisory group including: Tonique Ayler, Breaking Free, Housing Advocate, Survivor Leader; Terry Forliti, Independent Consultant, Survivor Leader; Joy Friedman, Independent Consultant, Survivor Leader; Mikki Mariotti, Director, The PRIDE Program of the Family Partnership; Christine Nelson, Independent Consultant, Fellow of Survivor Alliance, Survivor Leader; Lorena Nevile, Vice President of Programs, The Family Partnership; and Drea Sortillon, Witness-Victim Division, Hennepin County Attorney’s Office. They have provided critical expertise in understanding the complexities of trafficking networks. We appreciate the recommendations of the reviewers, which have helped to better present the qualitative approaches used to determine parameters of the network generator.
Additional information
Funding
Notes on contributors
Daniel Kosmas
Daniel Kosmas is a postdoctoral research associate in the Department of Mechanical and Industrial Engineering at Northeastern University. His research interests include developing operations research models to address societal problems, such as disrupting human trafficking. His work has been supported by the National Institute of Justice.
Christina Melander
Christina Melander, MSW, is a researcher in RTI International’s Justice Practice Area. Coming from a background in community practice social work, her work focuses on using participatory and community-engaged research methodologies with vulnerable populations to critically examine and improve systems response to violence and marginalization. Her research areas include human trafficking, sex trading, sexual violence, intimate partner violence, gender equality, and labor protections.
Emily Singerhouse
Emily Singerhouse, BA, is a researcher at Strategic Prevention Solutions. With a background in community-based action research, her work focuses on using mixed methodologies and partnering with transdisciplinary teams to examine and improve the societal, community, relationship, and individual factors that contribute to harmful outcomes. Ms. Singerhouse specializes in translating and disseminating complex data for community wellness enhancement. Her research areas include human trafficking, sex trading, sexual violence, intimate partner violence, youth violence, health equity, and prevention science. Ms. Singerhouse earned her Political Science and Global Studies degrees from the University of Minnesota.
Thomas C. Sharkey
Thomas C. Sharkey is a professor in the Industrial Engineering Department at Clemson University. His research interests are in creating operations research models and algorithms for problems in public policy and social good. His research has been funded through multiple NSF awards, including a CAREER award. His teaching interests are in creating effective blended environments that emphasize active learning to build student intuition. He has received several teaching awards for these efforts, including the IISE OR Division Teaching Excellence award.
Kayse Lee Maass
Kayse Lee Maass is an assistant professor of Industrial Engineering and Director of the Operations Research and Social Justice Lab at Northeastern University. Her research focuses on advancing operations research methodology to address social justice, access, and equity issues within human trafficking, mental health, and housing contexts using a community-based participatory action approach.
Kelle Barrick
Kelle Barrick is a Senior Research Criminologist in the Justice Practice Area at RTI International with 20 years of experience conducting mixed methods research on crime, victimization, and the criminal legal response. Her current work focuses primarily on human trafficking, including efforts to estimate the prevalence of sex and labor trafficking and improve efforts to prevent, intervene, and respond to human trafficking. Her research has been funded through awards from various federal agencies, including the National Institute of Justice and NSF.
Lauren Martin
Lauren Martin, PhD, is an associate professor in the School of Nursing at the University of Minnesota. Trained in Anthropology, she uses participatory and action research approaches to conduct qualitative, mixed-methods, and collaborative research rooted in strengths, meaning-making, and experience to explore sex trading, trafficking, sexual violence and community health. As part of her research process, she works with partners to design research and shape anti-oppressive practices, programs and policy in service of justice and equity. Dr. Martin is affiliated faculty at the Humphrey School of Public Affairs and the University of Minnesota’s Urban Research and Outreach-Engagement Center (UROC), where she was director of research for almost ten years. In 2016, she was the recipient of the University of Minnesota, President’s Engaged Scholar award.
References
- Barrick, K., Lattimore, P.K., Pitts, W.J. and Zhang, S.X. (2014) When farmworkers and advocates see trafficking but law enforcement does not: Challenges in identifying labor trafficking in North Carolina. Crime, Law and Social Change, 61(2), 205–214.
- Barrick, K., Panichelli, M., Lambdin, B., Dang, M. and Lutnick, A. (2021) Law enforcement identification of potential trafficking victims. Journal of Crime and Justice, 44(5), 579–594.
- Barrick, K., Pfeffer, R., Tueller, S., Tibaduiza, E. and Melander, C. (2022) Estimating sex trafficking in Sacramento County: Final report. Retrieved from https://www.rti.org/sites/default/files/cash-est-sextrf-sacramento-final-report-7-15-22-rev2_sm.pdf (accessed 1 August 2022).
- Barrick, K., Pitts, W.J., McMichael, J.P., Wheaton, W.D. and Evans, B.M. (2015) Developing a sampling frame of potential trafficking victims using geo-mapping techniques. Forum on Crime and Society, 8, 95–108.
- Baycik, N.O., Sharkey, T.C. and Rainwater, C.E. (2018) Interdicting layered physical and information flow networks. IISE Transactions, 50(4), 316–331.
- Belles, N. (2018) Defining sex trafficking, in Handbook of Sex Trafficking, Springer, Cham, Switzerland, pp. 3–8.
- Brush, B.L., Mentz, G., Jensen, M., Jacobs, B., Saylor, K.M., Rowe, Z., Israel, B.A. and Lachance, L. (2020) Success in long-standing community-based participatory research (cbpr) partnerships: A scoping literature review. Health Education & Behavior, 47(4), 556–568.
- Campana, P. (2016) The structure of human trafficking: Lifting the bonnet on a Nigerian transnational network. British Journal of Criminology, 56(1), 68–86.
- Carpenter, A. and Gates, J. (2016) The nature and extent of gang involvement in sex trafficking in San Diego County, United States Department of Justice.
- Caulkins, J.P., Kammer-Kerwick, M., Konrad, R., Maass, K.L., Martin, L. and Sharkey, T. (2019) A call to the engineering community to address human trafficking. The Bridge, National Academy of Engineering, 49(3), 67–73.
- Cockbain, E. (2018) Offender and Victim Networks in Human Trafficking, Routledge, London, UK.
- Cockbain, E., Bowers, K. and Vernon, L. (2020) Using law enforcement data in trafficking research, in The Palgrave International Handbook of Human Trafficking, Palgrave Macmillan, London, UK, pp. 1709–1732.
- Dank, M., Khan, B., Downey, P., Kotonias, C., Mayer, D., Owens, C. and Yu, L. (2014) Estimating the size and structure of the underground commercial sex economy in eight major US cities. The Urban Institute.
- Denzin, N. (2012) Triangulation 2.0. Journal of Mixed Methods Research, 6(2), 80–88.
- Dimas, G.L., Konrad, R.A., Lee Maass, K. and Trapp, A.C. (2022) Operations research and analytics to combat human trafficking: A systematic review of academic literature. PLoS one, 17(8), 1–24.
- Farrell, A. and de Vries, I. (2020) Measuring the nature and prevalence of human trafficking, in The Palgrave International Handbook of Human Trafficking, Palgrave Macmillan, London, England, UK, pp. 147–162.
- Fedina, L. (2015) Use and misuse of research in books on sex trafficking: Implications for interdisciplinary researchers, practitioners, and advocates. Trauma, Violence, & Abuse, 16(2), 188–198.
- Gerassi, L., Edmond, T. and Nichols, A. (2017) Design strategies from sexual exploitation and sex work studies among women and girls: Methodological considerations in a hidden and vulnerable population. Action Research, 15(2), 161–176.
- Haapanen, K.A. and Christens, B.D. (2021) Community-engaged research approaches: Multiple pathways to health equity. American Journal of Community Psychology, 67, 1–7.
- International Labour Organization (2017) Global estimates of modern slavery: forced labour and forced marriage. International Labour Organization, Geneva, Switzerland.
- Keskin, B.B., Bott, G.J. and Freeman, N.K. (2021) Cracking sex trafficking: Data analysis, pattern recognition, and path prediction. Production and Operations Management, 30(4), 1110–1135.
- Konrad, R.A., Trapp, A.C., Palmbach, T.M. and Blom, J.S. (2017) Overcoming human trafficking via operations research and analytics: Opportunities for methods, models, and applications. European Journal of Operational Research, 259(2), 733–745.
- Konrad, R., Trapp, A. and Maass, K.L. (2017) Human trafficking analysis. OR/MS Today, 44(2), 30–33.
- Kosmas, D., Sharkey, T.C., Mitchell, J.E., Maass, K.L. and Martin, L. (2022) Interdicting restructuring networks with applications in illicit trafficking. Forthcoming in European Journal of Operational Research. https://doi.org/10.1016/j.ejor.2022.11.048
- Lotrecchiano, G.R. and Misra, S. (2018) Transdisciplinary knowledge producing teams: Toward a complex systems perspective, Informing Science: the International Journal of an Emerging Transdiscipline, 21, 51–74.
- Malaviya, A., Rainwater, C. and Sharkey, T. (2012) Multi-period network interdiction problems with applications to city-level drug enforcement. IISE Transactions, 44(5), 368–380.
- Mancuso, M. (2014) Not all madams have a central role: Analysis of a Nigerian sex trafficking network. Trends in Organized Crime, 17(1), 66–88.
- Marcus, A., Horning, A., Curtis, R., Sanson, J. and Thompson, E. (2014) Conflict and agency among sex workers and pimps: A closer look at domestic minor sex trafficking. The Annals of the American Academy of Political and Social Science, 653(1), 225–246.
- Martin, L.E., Pierce, A., Peyton, S., Gabilondo, A.I. and Tulpule, G. (2014) Mapping the market for sex with minor trafficked girls in Minneapolis: Structures functions, and patterns, Community Report. University of Minnesota Urban Research Outreach-Engagement Center, Minneapolis, MN.
- Martin, L., Gupta, M., Maass, K., Melander, C., Singerhouse, E., Barrick, K., Samad, T., Sharkey, T., Ayler, T., Forliti, T., Friedman, J., Nelson, C. and Sortillon, D. (2022) Learning each other’s language and building trust: Community-engaged transdisciplinary team building for research on human trafficking operations and disruption. International Journal of Qualitative Methods, 21, 1–15.
- Martin, L. and Lotspeich, R. (2014) A benefit-cost framework for early intervention to prevent sex trading. Journal of Benefit-Cost Analysis, 5(1), 43–87.
- Martin, L., Melander, C., Karnik, H. and Nakamura, C. (2017) Mapping the demand: Sex buyers in the State of Minnesota, University of Minnesota, Robert J. Jones Urban Research and Outreach.
- Mayorga, M., Tateosian, L., Velasquez, G., Amindarbari, R. and Caltagirone, S. (2019) Countering human trafficking using ISE/OR techniques, Emerging Frontiers in Industrial and Systems Engineering, CRC Press, Boca Raton, FL, pp. 237–257.
- Melander, C., Martin, L. and Maass, K.L. (n.d.) Conceptualizing operations that traffic people for sexual exploitation within the United States: Relationship networks within the broader socioecological context. Working paper, in progress.
- Morris, W.T. (1967) On the art of modelling. Management Science, 13(12), B–707.
- Morton, D.P., Pan, F. and Saeger, K.J. (2007) Models for nuclear smuggling interdiction. IIE Transactions, 39(1), 3–14.
- Motivans, M. and Snyder, H. (2018) Federal prosecution of human trafficking cases, 2015. Special Report NCJ 251390. U.S. Department of Justice, Office of Justice Programs, Bureau of Justice Statistics. Retrieved from: https://bjs.ojp.gov/content/pub/pdf/fphtc15.pdf (accessed 1 June 2022).
- Polaris Project (2017) The typology of modern slavery: Defining sex and labor trafficking in the United States. Polaris Project, Washington, DC.
- Preble, K.M. (2019) Under their “control”: Perceptions of traffickers’ power and coercion among international female trafficking survivors during exploitation. Victims & Offenders, 14(2), 199–221.
- Roe-Sepowitz, D. (2019) A six-year analysis of sex traffickers of minors: Exploring characteristics and sex trafficking patterns. Journal of Human Behavior in the Social Environment, 29(5), 608–629.
- Roe-Sepowitz, D.E., Gallagher, J., Risinger, M. and Hickle, K. (2015) The sexual exploitation of girls in the United States: The role of female pimps. Journal of Interpersonal Violence, 30(16), 2814–2830.
- Sharkey, T.C., Barrick, K., Farrell, A., Maass, K.L., Martin, L. and Song, Y. (2021) Better together: A transdisciplinary approach to disrupt human trafficking. ISE Magazine, 51(11), 34–39.
- Shen, Y., Sharkey, T.C., Szymanski, B.K. and Wallace, W.A. (2021) Interdicting interdependent contraband smuggling, money and money laundering networks. Socio-Economic Planning Sciences, 78, 101068.
- Smith, J.C. and Song, Y. (2020) A survey of network interdiction models and algorithms. European Journal of Operational Research, 283(3), 797–811.
- Tantardini, M., Ieva, F., Tajoli, L. and Piccardi, C. (2019) Comparing methods for comparing networks. Scientific Reports, 9(1), 1–19.
- Tezcan, B. and Maass, K.L. (2020) Human trafficking interdiction with decision dependent success. engrXiv preprint 1068.
- US Department of Justice (2019) Capturing human trafficking victimization through crime reporting. NCJ No. 252520. U.S. Department of Justice, National Institute of Justice, Washington, DC.
- Veldhuizen-Ochodničanová, E. and Jeglic, E.L. (2021) Of madams, mentors and mistresses: Conceptualising the female sex trafficker in the United States. International Journal of Law, Crime and Justice, 64, 100455.
- Watts, D.J. and Strogatz, S.H. (1998) Collective dynamics of ‘small-world’ networks. Nature, 393(6684), 440–442.
- Weitzer, R. (2014) New directions in research on human trafficking. The Annals of the American Academy of Political and Social Science, 653(1), 6–24.
- White, A., Guikema, S. and Carr, B. (2021) Why are you here? Modeling illicit massage business location characteristics with machine learning, Forthcoming in Journal of Human Trafficking. https://doi.org/10.1080/23322705.2021.1982238
- Willemain, T.R. (1994) Insights on modeling from a dozen experts. Operations Research, 42(2), 213–222.
- Willemain, T.R. (1995) Model formulation: What experts think about and when. Operations Research, 43(6), 916–932.
- Wilson, R.C. and Zhu, P. (2008) A study of graph spectra for comparing graphs and trees. Pattern Recognition, 41(9), 2833–2841.
- Wood, R.K. (1993) Deterministic network interdiction. Mathematical and Computer Modelling, 17(2), 1–18.
- Xie, X. and Aros-Vera, F. (2022) An interdependent network interdiction model for disrupting sex trafficking networks. Production and Operations Management, 31(6), 2695–2713.