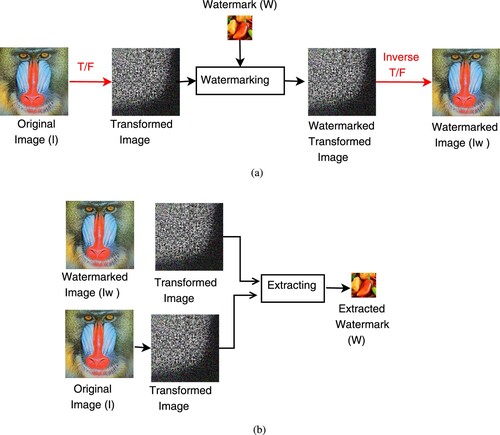
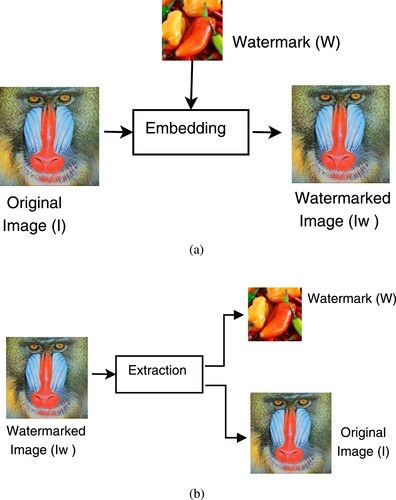
Figures & data
Table 1. Full form of the abbreviations used in the paper.
Table 2. Data hiding techniques and their goals in the research.
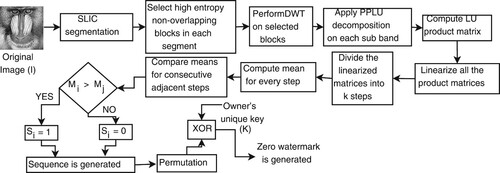
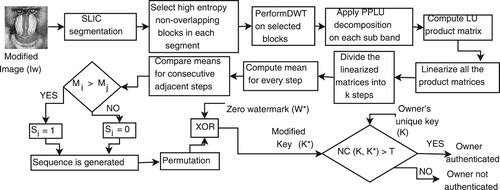
Figure 2. Zero-watermarking scheme: (a) zero-watermark construction and (b) zero-watermark extraction.
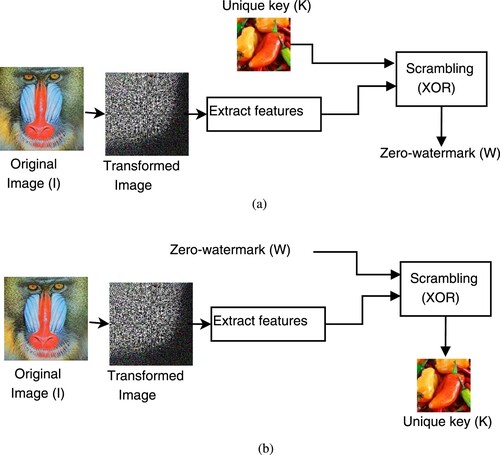
Table 3. Correlation and BER values between the generated and received watermark against listed attacks for the proposed method and the existing method for general images.
Table 4. Correlation and BER values between the generated and received watermark against listed attacks for the proposed method and the existing method.
Table 5. Extracted watermarks against listed attacks for the proposed method and the existing method for general images.
Table 6. Correlation and BER values between the generated and received watermark against MF attack for different window sizes for MRI images, where Lo = 0, Hi = 1.
Table 7. Correlation and BER values between the generated and received watermark against MF attack for different window sizes for CT images, where Lo = 0, Hi = 1.
Table 8. Correlation and BER values between the generated and received watermark against AF attack for different window sizes for MRI images, where Lo = 0, Hi = 1.
Table 9. Correlation and BER values between the generated and received watermark against AF attack for different window sizes for CT images, where Lo = 0, Hi = 1.
Table 10. Correlation and BER values between the generated and received watermark against SPN attack for CT images, where Lo = 0, Hi = 1.
Table 11. Correlation and BER values between the generated and received watermark against SPN attack for CT images, where Lo = 0, Hi = 1.
Table 12. Correlation and BER values between the generated and received watermark against GN attack for MRI images, where Lo = 0, Hi = 1.
Table 13. Correlation and BER values between the generated and received watermark against GN attack for CT images, where Lo = 0, Hi = 1.
Table 14. Processing time for sample images.
Table 15. Correlation and BER values between the generated and received watermark against CE, quantization and JPEG compression attack for MRI and CT images, where Lo = 0, Hi = 1.