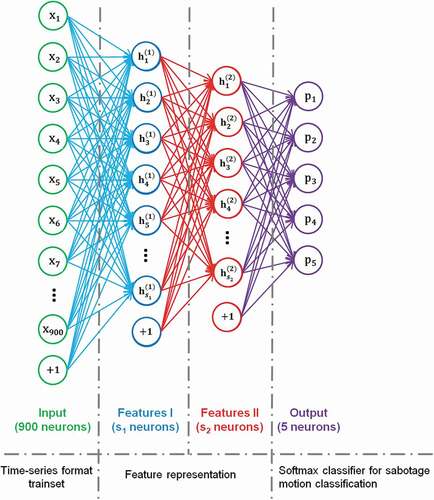
Figures & data
Table 1. Four proposed network architectures
Figure 6. Motion recognition output. Different colored lines represent the probability of different motions (red line: probability of pushing motion; blue line: probability of grasping motion; green line: probability of cutting motion; yellow line: probability of patting motion; pink line: probability of turning motion).
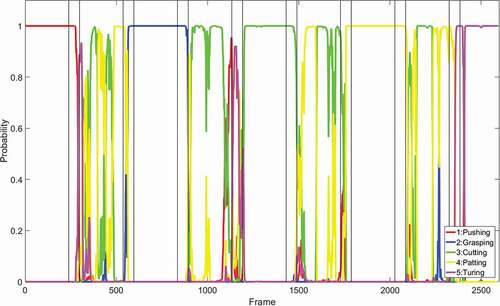
Table 2. Motion recognition accuracy
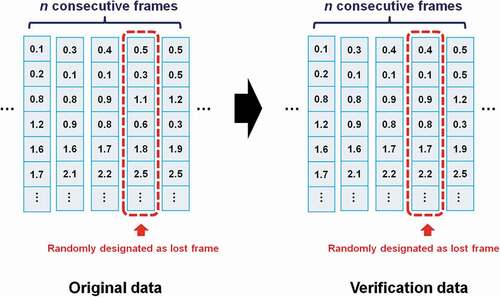
Table 3. Verification results for nonconsecutive frame loss
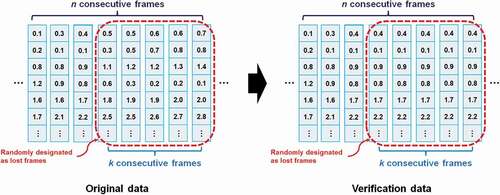
Table 4. Verification results for consecutive frame loss