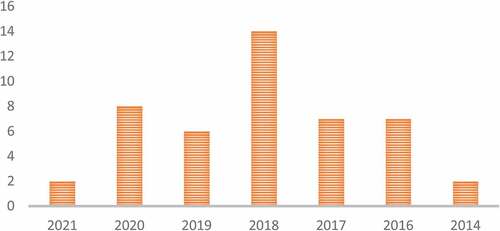
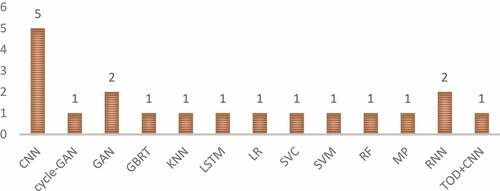
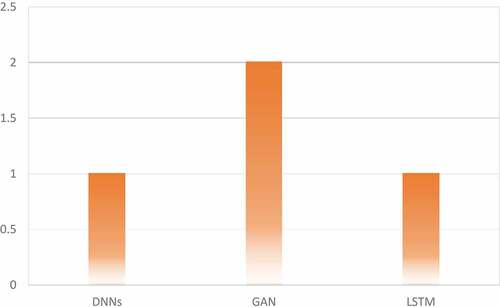
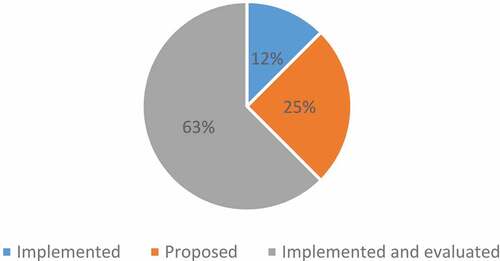
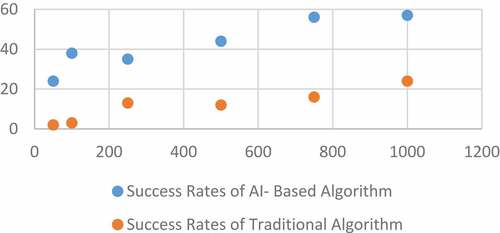
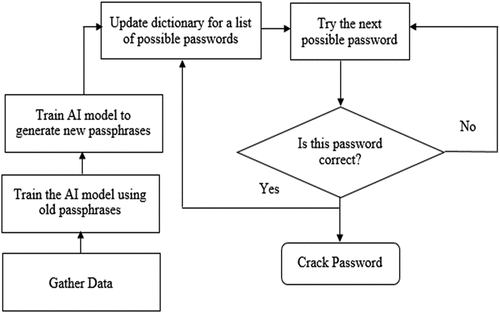
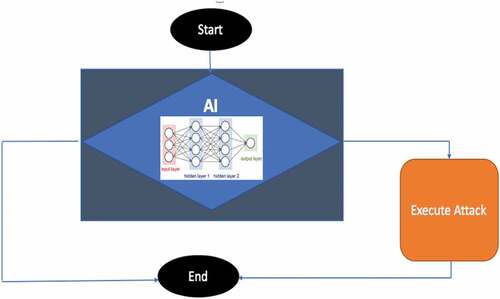
Figures & data
Table 1. Research Questions.
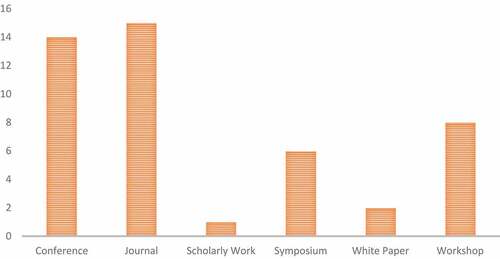
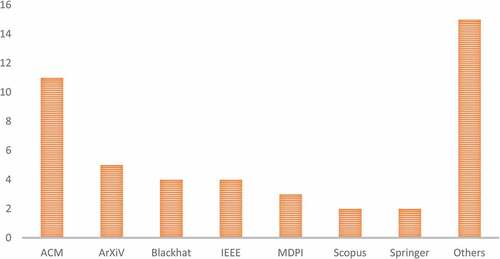
Table 2. The number of publications found in online databases.
Figure 1. PRISMA flowchart illustrating the systematic review process and article selection at various stages.
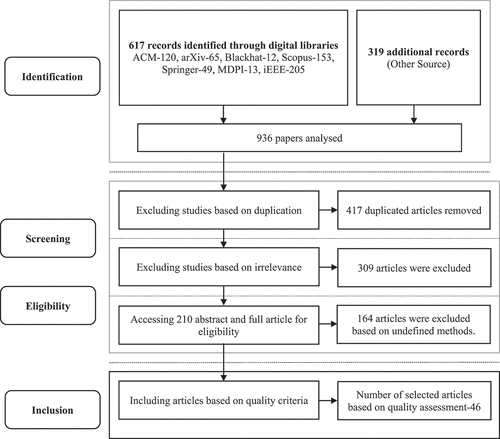
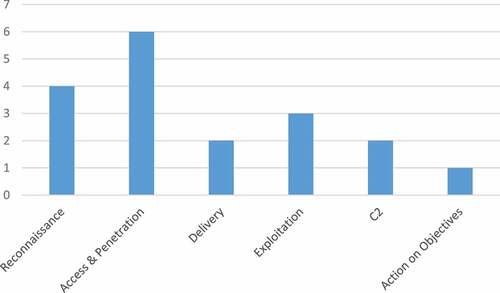
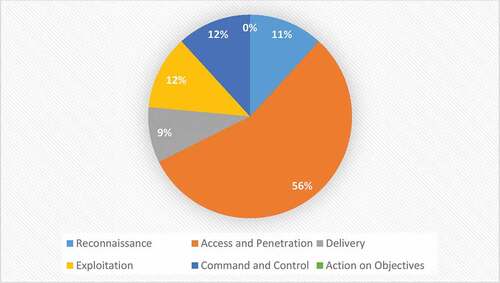
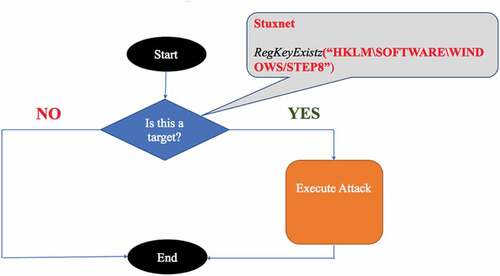
Figure 3. Modified Cybersecurity Kill Chain for AI-Driven Attack (Kaloudi and Li Citation2020).
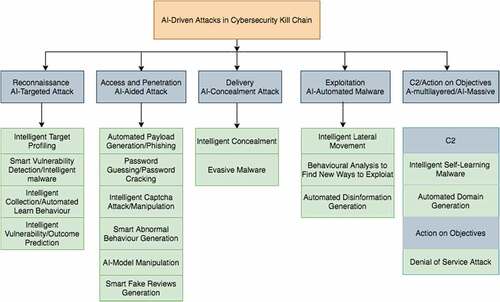
Table 3. Status of existing literature with respective narration.
Table 4. Offensive Utilization of AI Techniques in the Reconnaissance Stage of Cybersecurity Kill Chain.
Table 5. Offensive Utilization of AI Techniques in the Access and Penetration Stage of Cybersecurity Kill Chain.
Table 6. Offensive Utilization of AI Techniques in the Delivery Stage of Cybersecurity Kill Chain.
Table 7. Offensive Utilization of AI Techniques in the Exploitation Stage of Cybersecurity Kill Chain.
Table 8. Offensive Utilization of AI Techniques in the C2 of Cybersecurity Kill Chain.