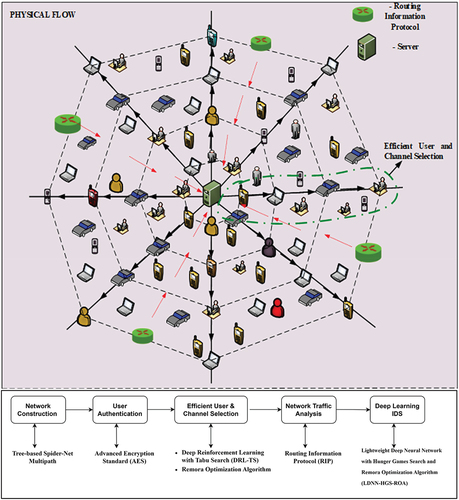
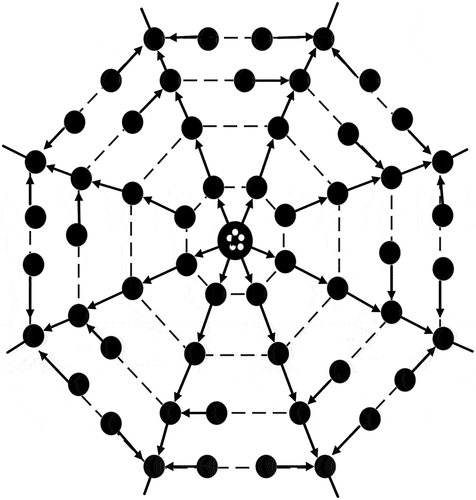
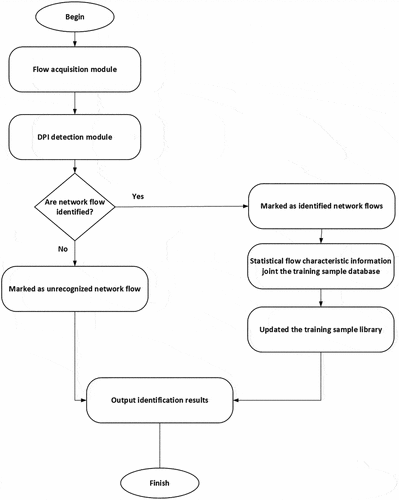
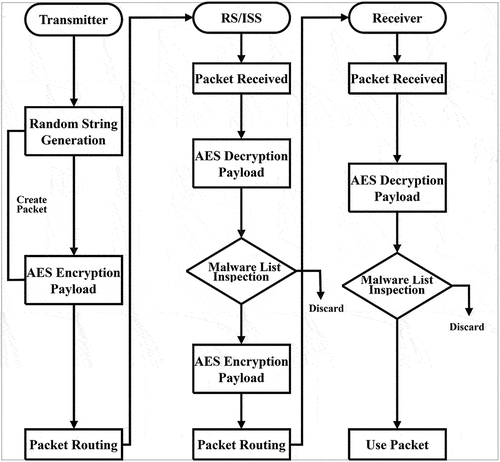
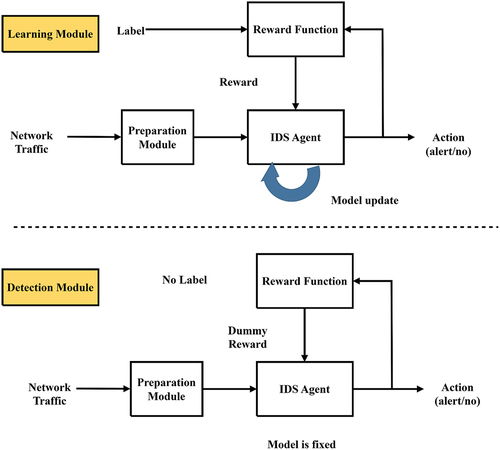
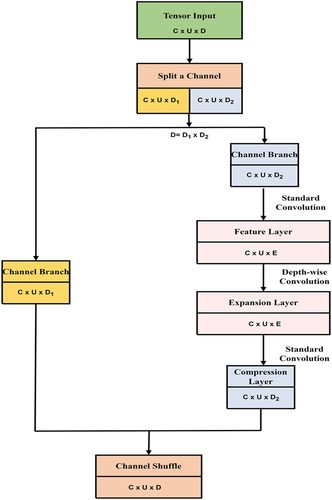
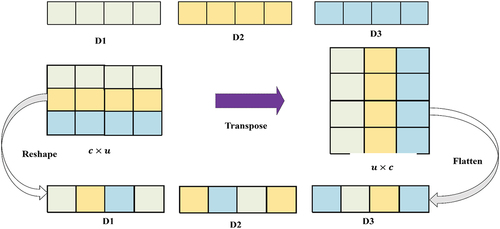
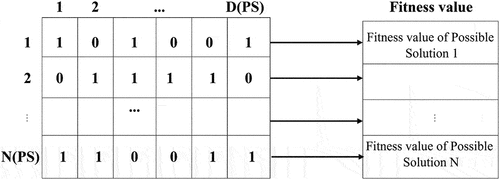
Figures & data
Table 1. Tabu search algorithm parameters.
Table
Table
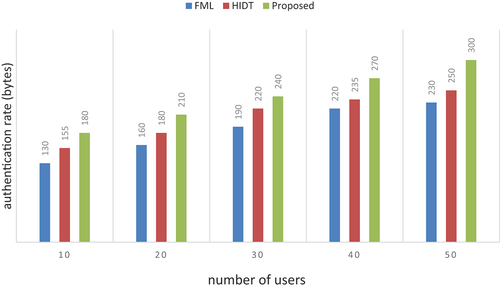
Table 2. Numerical outcomes of authentication rate.
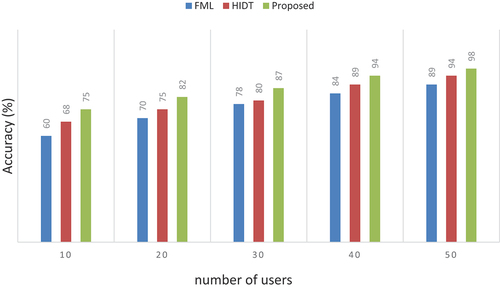
Table 3. Numerical outcomes of accuracy.
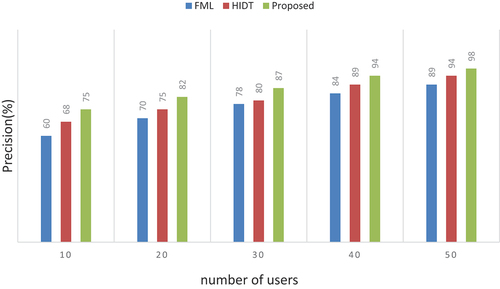
Table 4. Numerical outcomes of precision.
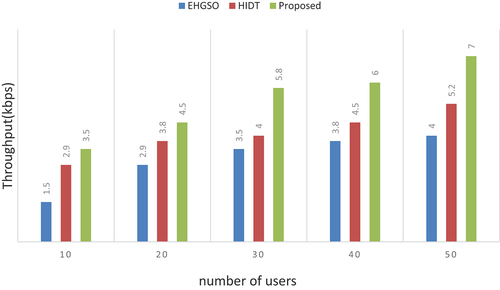
Table 5. Numerical outcomes of throughput.
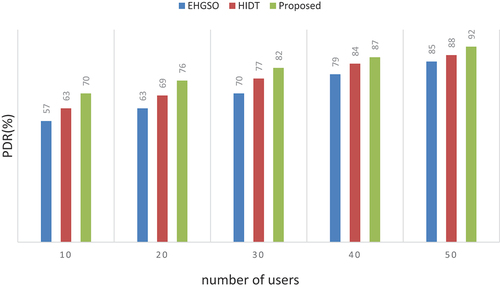
Table 6. Numerical outcomes of packet delivery ratio.
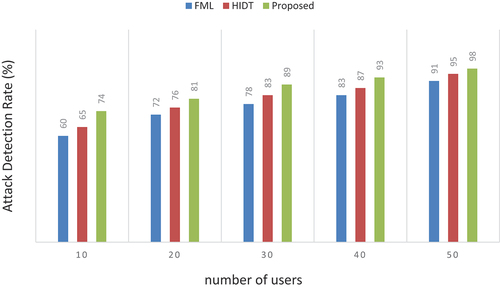
Table 7. Numerical outcomes of attack detection rate.
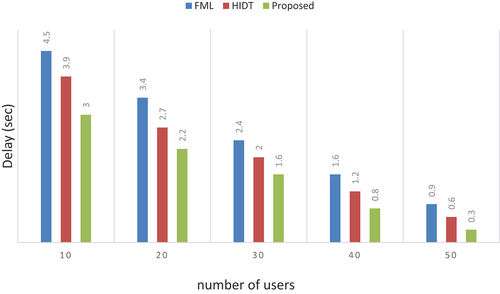
Table 8. Numerical outcomes of delay.
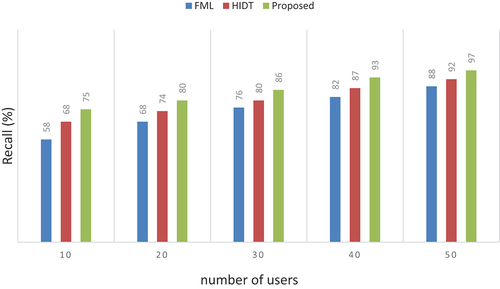
Table 9. Numerical outcomes of recall.
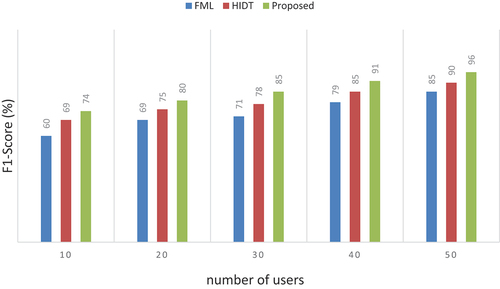
Table 10. Numerical outcomes of F1-score.