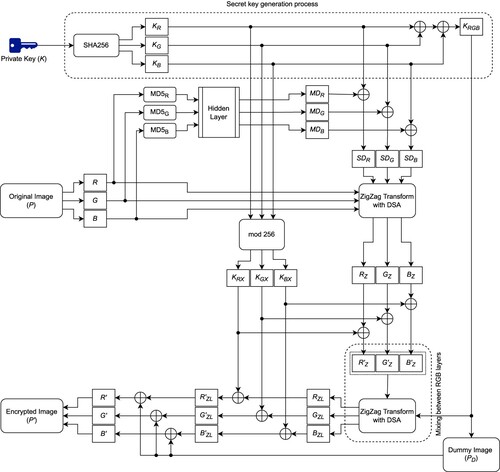
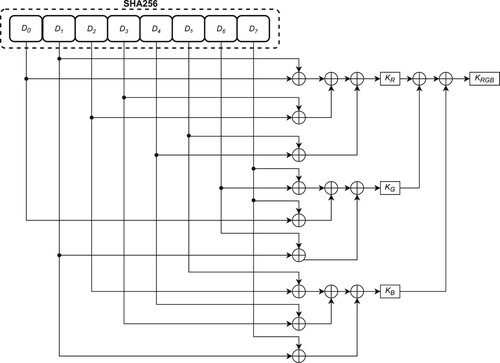
Figures & data
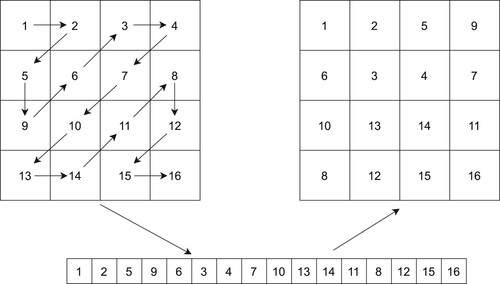
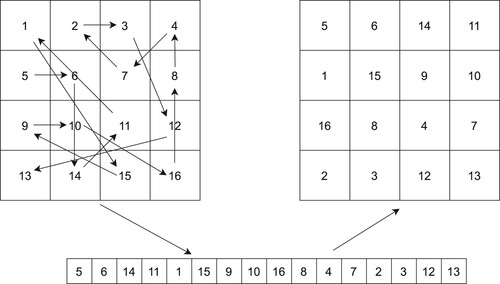
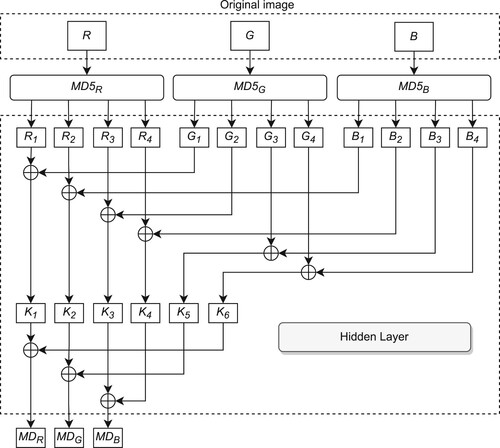
Table 1. Guiding information to select pairs of blocks to XOR.
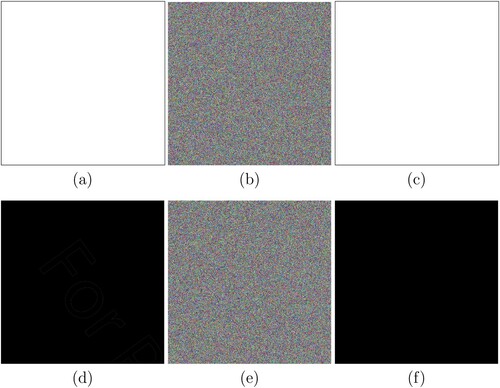
Figure 6. Experimental results for encryption and decryption, (a)–(d) plaintext images Lena, Pepper, Baboon and Barbara, (e)–(h) encrypted images Lena, Pepper, Baboon and Barbara, (i)–(l) decrypted images Lena, Pepper, Baboon and Barbara.

Figure 8. Decryption results with correct and incorrect keys: (a) decrypted image with the correct key maltepe@, (b)–(f) images decrypted with keys with little difference (Maltepe@, malTepe@, ma1ltepe, maltrpe_, maltePe).

Table 2. NPCR (%) values of decrypted images with different keys.
Figure 9. Histogram analysis: (a) histogram of the plaintext Lena in all channels, (b)–(d) histograms of the ciphertext image Lena in channels R, G and B, respectively, (e) histogram of the plaintext Pepper in all channels, (f)–(h) histograms of the ciphertext image Pepper in channels R, G and B, respectively, (i) histogram of the plaintext Baboon in all channels, (j)–(l) histograms of the ciphertext image Baboon in channels R, G and B, respectively, (m) histogram of the plaintext Barbara in all channels, (n)–(p) histograms of the ciphertext image Barbara in channels R, G and B, respectively.
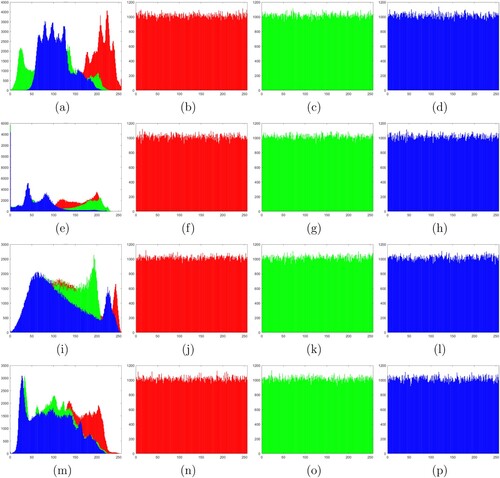
Figure 10. Correlation between adjacent pixels in channel R of Lena: (a)–(c) horizontal, vertical and diagonal correlations in plaintext, (d)–(f) horizontal, vertical, diagonal correlations in ciphertext.
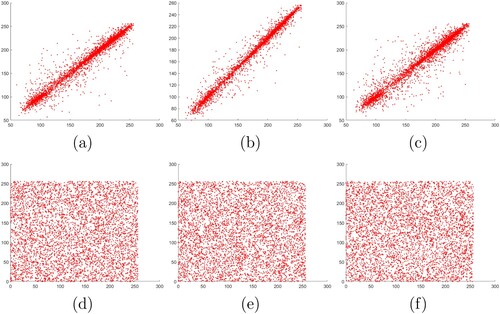
Figure 11. Correlation between adjacent pixels in channel G of Lena: (a)–(c) Horizontal, vertical, and diagonal correlations in plaintext, (d)–(f) horizontal, vertical, diagonal correlations in ciphertext.
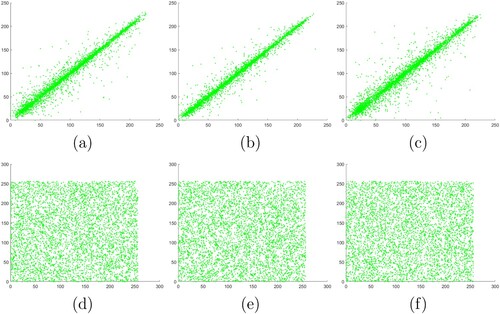
Figure 12. Correlation between adjacent pixels in channel B of Lena: (a)–(c) horizontal, vertical and diagonal correlations in plaintext, (d)–(f) horizontal, vertical, diagonal correlations in ciphertext.
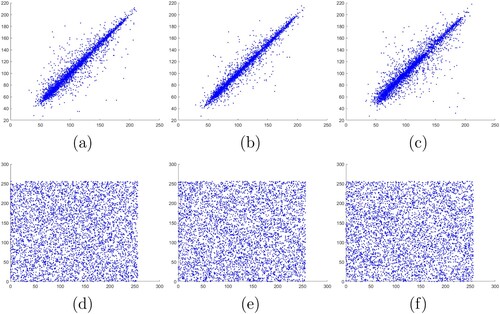
Table 3. Correlations between adjacent pixels of plaintext and ciphertext images of Lena.
Table 4. Entropy analysis results (in bits).
Table 5. NPCR and UACI values of ciphertext images of Lena for plaintext sensitivity analysis.
Figure 13. Experimental results for a noise attack. Gaussian noise decryption results with variance of (a) 0.01 and (b) 0.1. Salt-and-pepper noise decryption results with intensity of (c) 0.01 and (d) 0.05.

Figure 14. Experimental results for occlusion attacks. The encrypted images with (a) 1/16, (b) 1/4 and (c) 1/2 occlusion, (d) Plus occlusion, (e)–(h) are the corresponding decrypted images.

Table 6. Quantitative results of occlusion attack resistance.
Table 7. NIST test results.