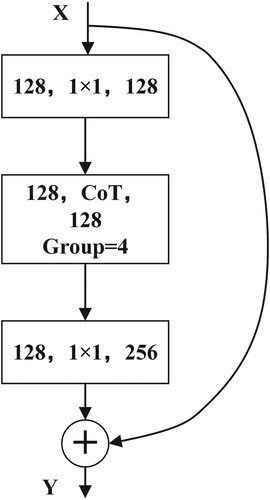
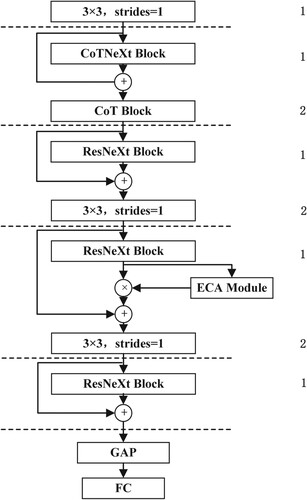
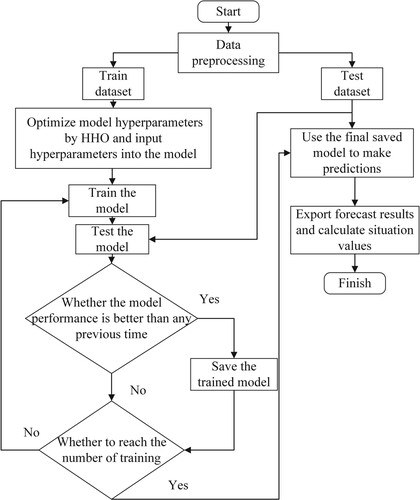
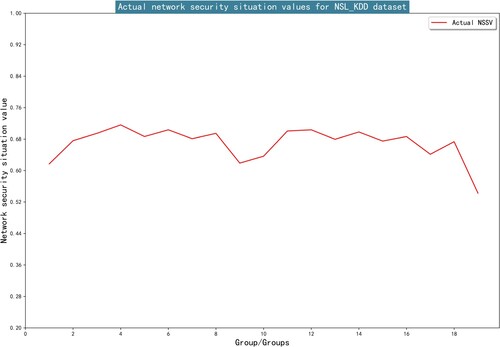
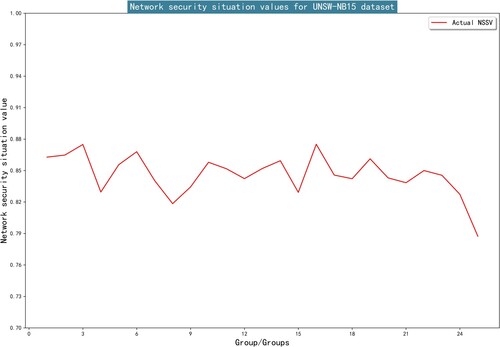
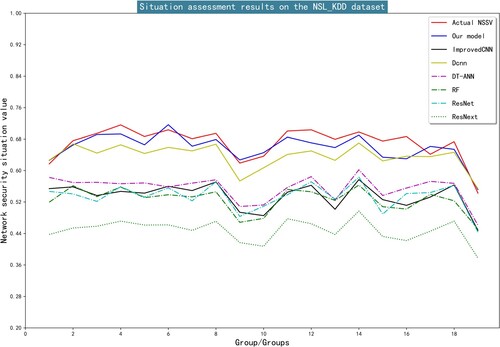
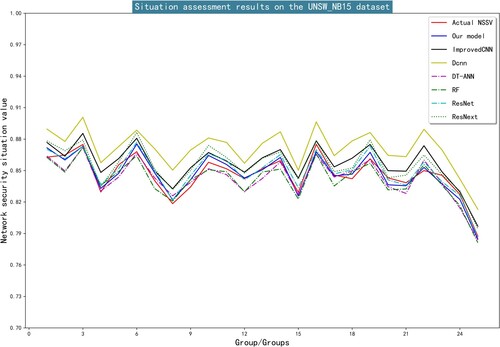
Figures & data
Table 1. Details of this model.
Table 2. Impact of attacks in the NSL-KDD dataset.
Table 3. Impact of attacks in the UNSW-NB15 dataset.
Table 4. Experiment results of different models.
Table 5. Network security situation assessment results of each model.