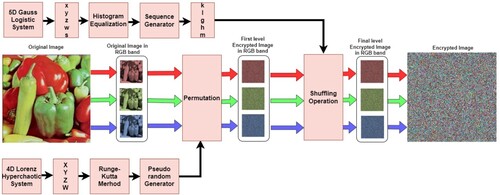
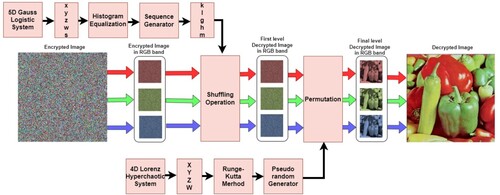
Figures & data
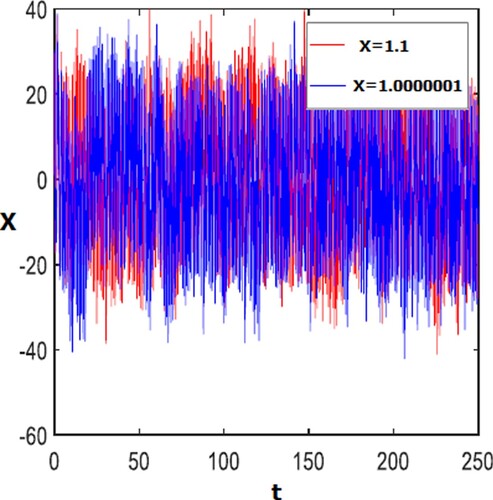
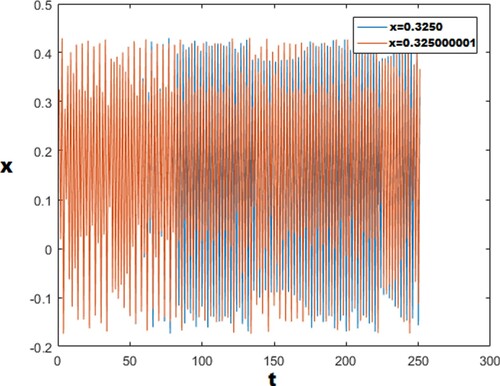
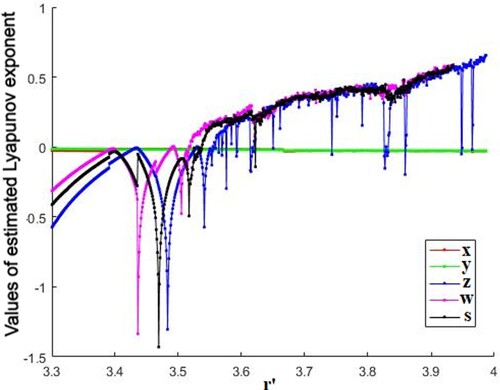
Figure 1. Lyapunov Exponent of proposed Gauss-logistic map. (With reference to Equation 5; The Gauss map is represented by the first two equations with the colors green and red, whereas the Logistic map is represented by the last three equations with the colors pink, black, and blue.)
Table
Table
Table
Table
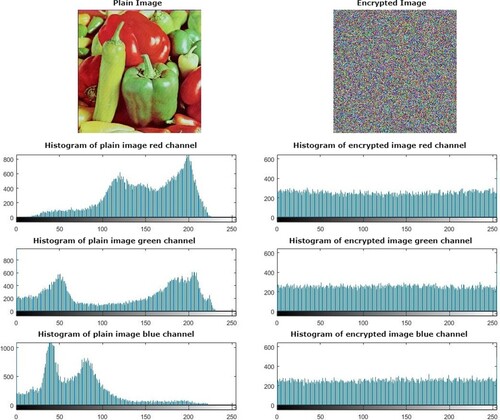
Table 1. Histogram uniformity evaluation by chi-square test.
Figure 8. The pixel distribution of different (RGB) components of pepper original and encrypted image in horizontal, vertical and diagonal directions.
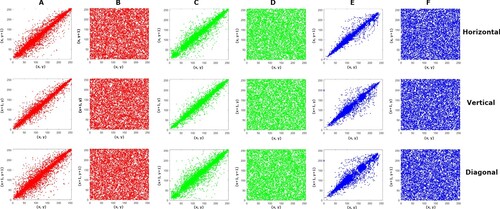
Table 2. Correlation coefficients of original and encrypted test images.
Table 3. Correlation coefficients of colored test images in the RGB components.
Table 4. Comparison of correlation coefficients of colored test images.
Table 5. Comparison of correlation coefficients of colored test images in the R G B components.
Table 6. Information entropy results for the proposed algorithm on different test images.
Table 7. Comparison of Information entropy with different literature.
Table 8. Local Entropy results for the proposed algorithm on different test images.
Table 9. NPCR AND UACI values of different size test images.
Table 10. Comparison among the suggested algorithm and the algorithms in literature based on NPCR and UACI.
Table 11. Comparison of keyspace in different literatures.
Figure 10. Key sensitivity analysis for encrypted pepper image with a slight change in one of the secret keys.
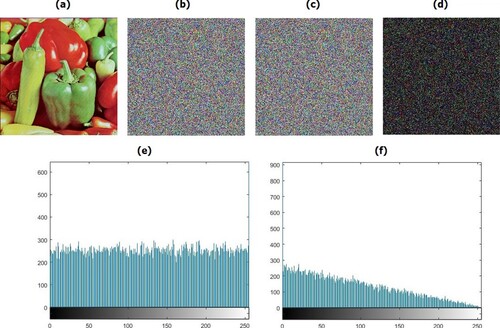
Table 12. CDRs estimation as a result of changing secret keys for encryptions.
Table 13. Randomness test for the 5D Gauss logistic hyperchaotic system's sequences.
Table 14. Test scores for the proposed algorithm such as PSNR, SSIM, MSE.
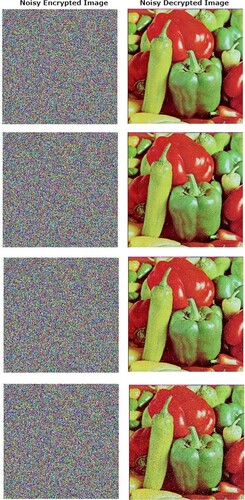
Table 15. Noise attacks with different intensities.
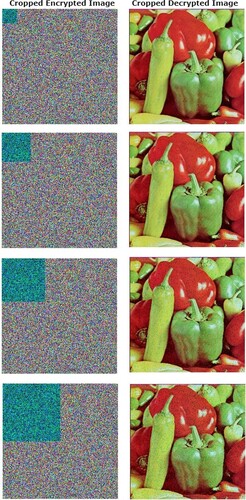
Table 16. Cropping attacks with different data loss pixel areas.
Table 17. Computational time for the proposed algorithm on different test images.
Table 18. Comparison of computational time and Speed analysis of encryption process in different literatures.