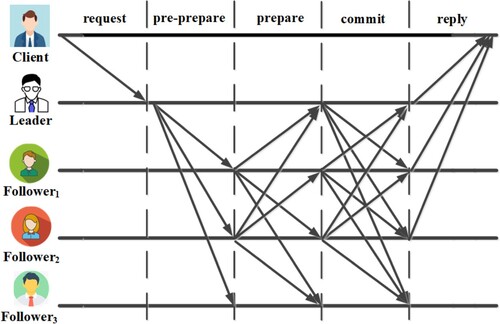
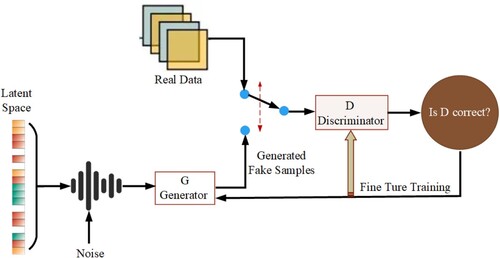
Figures & data
Table 1. Summary of existing poisoning attack defense schemes in FL.
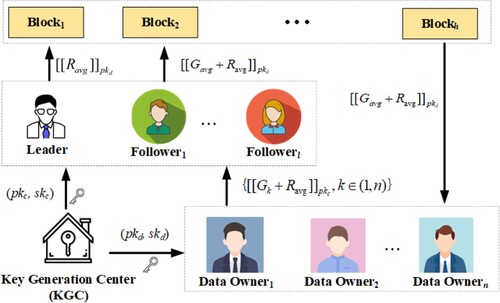
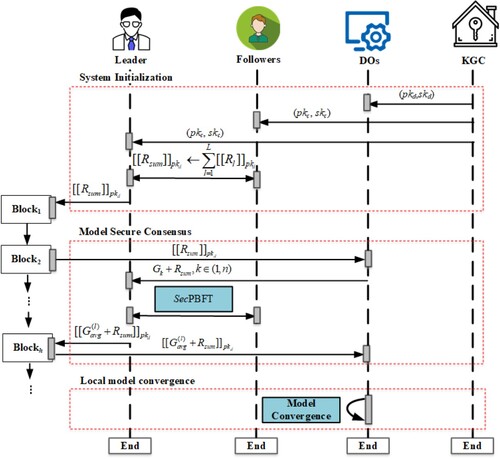
Table 2. Notations.
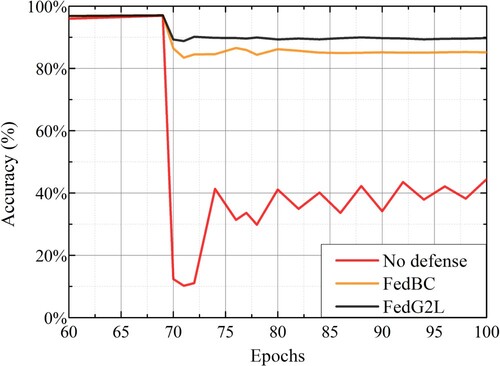
Figure 6. Comparison of accuracy with different epochs and byzantine percentage. (a) Epochs. (b) Byzantine percentage.
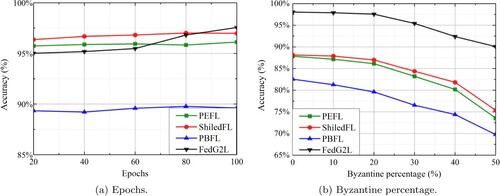
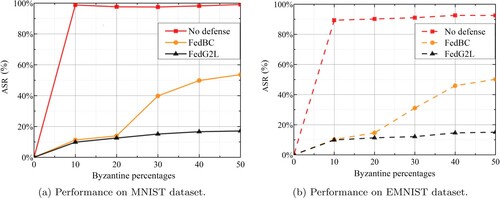
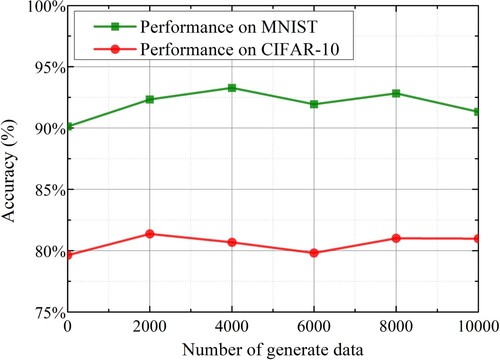
Figure 7. The ASR with different Byzantine percentages on 2 datasets. (a) Performance on MNIST dataset. (b) Performance on EMNIST dataset.