Figures & data
Figure 1. The figure shows the step-wise systematic literature review methodology we followed to develop the categorisation of social engineering and side-channel attacks on mobile phones.
Figure 2. The figure shows the categorisation of human centred social engineering and side channel attacks on mobile phones from the perspective of an attacker. We developed this categorization based on the resources extracted from the papers resulting from the systematic literature review.
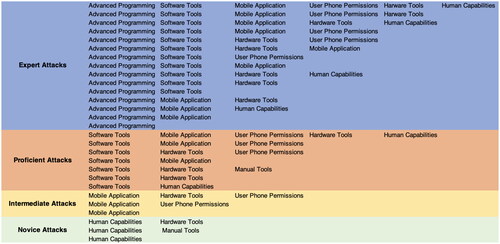
Figure 3. The figure shows the categorisation of attacks in four levels from an attacker’s perspective. The expertise required to perform an attacker increases as we progress in categorisation levels.
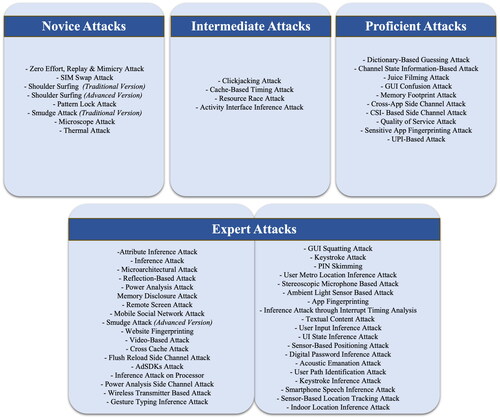
Figure 4. The figure shows a thermal image of smartphone authentication captured using a thermal camera, i.e., a flir camera. The authentication information can be easily observed by observing the heat traces. This is a typical scenario of thermal Attacks that belongs to the category of Novice Attacks.
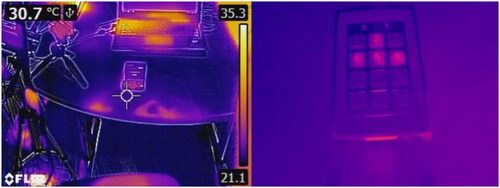
Figure 5. The figure showcases common occurrences of shoulder surfing - a type of novice attack - in the daily lives of users where the bystander uses direct observation to make observations of the screen and retrieve personal information about the user.

Table A1. The table shows the list of papers extracted from the selected publication venues which are included in the systematic literature review.
Table A2. The table shows the list of papers extracted by performing backward search which are included in the systematic literature review.
Table A3. The table shows the list of papers extracted by performing forward search which are included in the systematic literature review.
Table B1. The table shows the codebook for attack infrastructure requirement categories.
