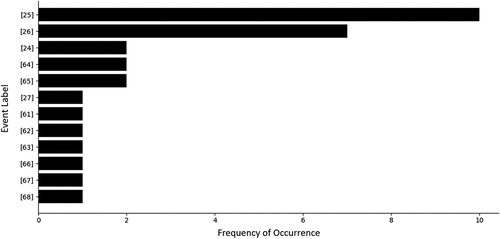
Figures & data
Table 1. Notable ICS cyberattacks (2000 – 2023).
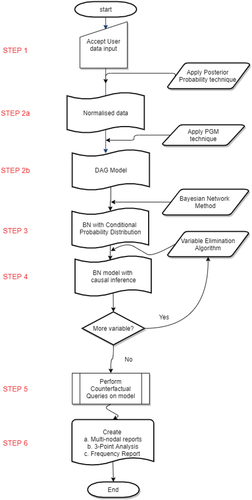
Algorithm 1. RiskED Process Flow
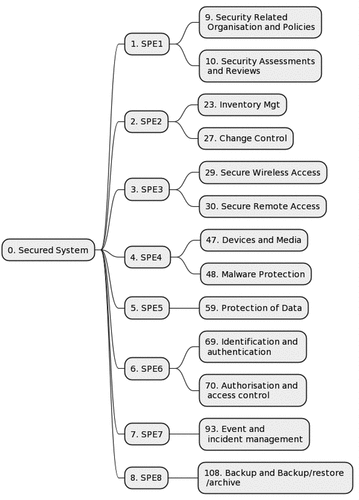
Table 2. Risk assessment data based on IEC 62,443 method.
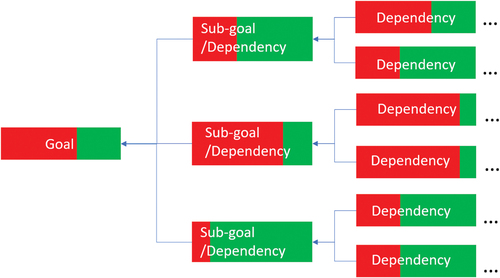
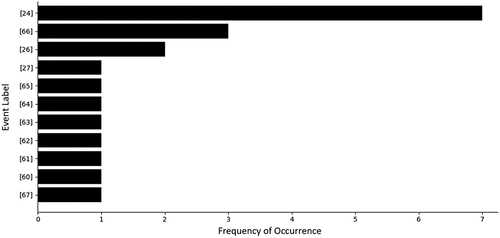
Table 3. Case study: dependency model.
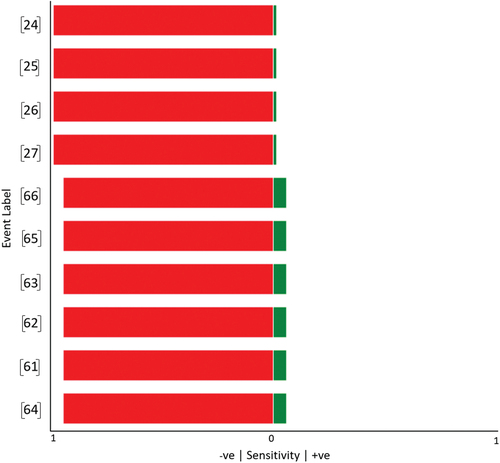
Table 4. Causal inference with single node.
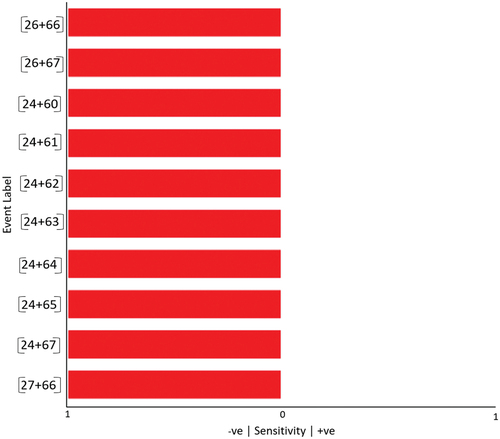
Table 5. Causal inference with two nodes.
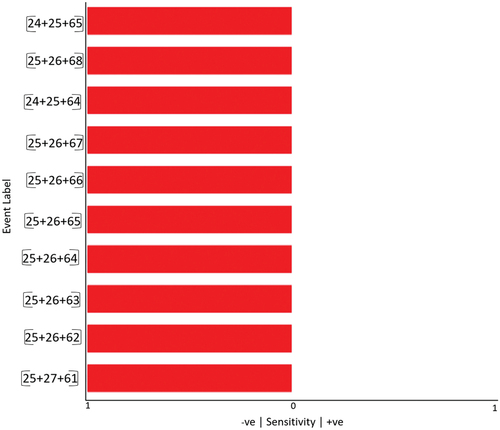
Table 6. Causal inference with three nodes.
Data availability statement
All data is provided in full in the results section of this paper. No new data was created during this study.