Figures & data
Table 1. The security evaluation requirements for each of the SOA functional layers (selection) (Kołaczek, Citation2013).
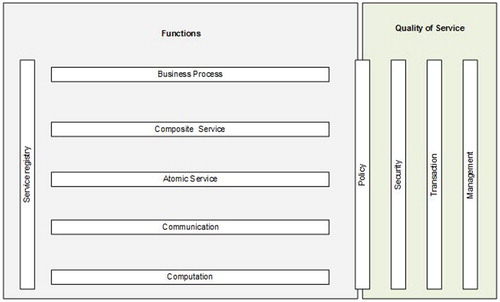
Figure 2. Architecture of multi-agent system for evaluation of the security level in service-oriented systems.
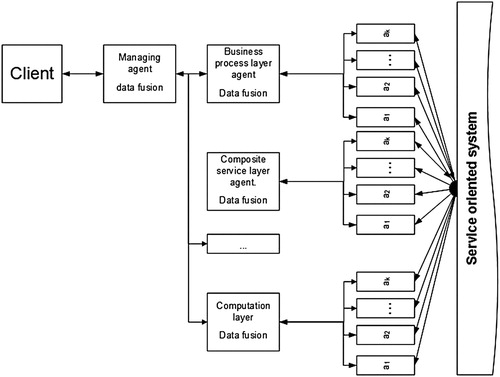
Figure 3. The opinion triangle (Josang, Citation1999).
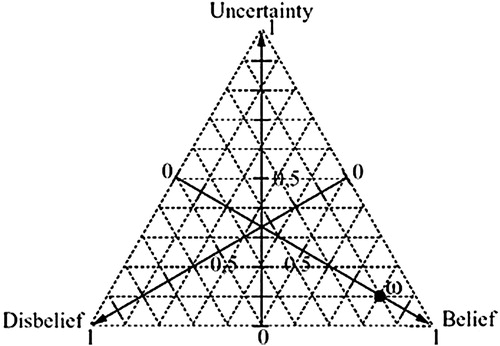
Figure 4. Structure of the composite services. (a) ring, (b) ring + additional connection, (c) ring + two additional connections and (d) random connections.
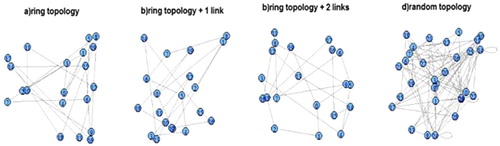
Table 2. Moran-I test results for examined topologies.
Table 3. Local Moran-I test results summary.
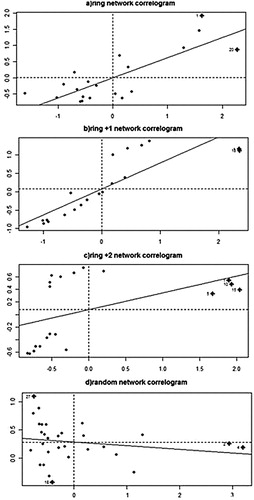
Figure 5. Correlation of spatial data communication traffic generated for the four selected structures of complex service. (a) ring network correlogram, (b) ring +1 network correlogram, (c) ring +2 network correlogram and (d) random network correlogram.