Figures & data
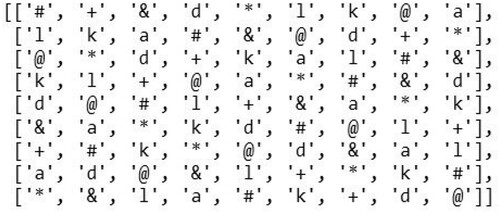
Algorithm 1 Read Image, Store Keys
Algorithm 2 Generate Pseudo Random & Perform Thresholding
Algorithm 3 Image Padding
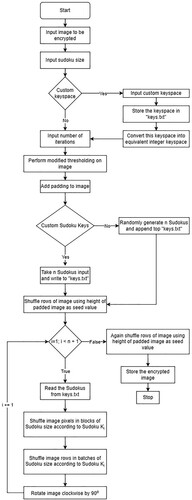
Algorithm 4 Sudoku Based Encryption
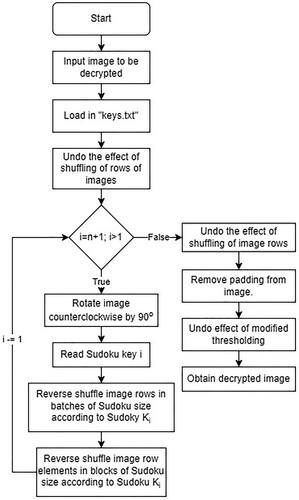
Algorithm 5 Sudoku Based Decryption of Encrypted Image
Algorithm 6 Remove Image Padding
Algorithm 7 Restore original image by reversing thresholding
Table 1. Comparison of iterations for Lena.
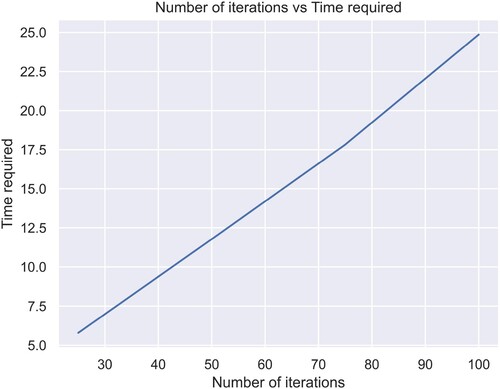
Table 2. Time required for key generation.
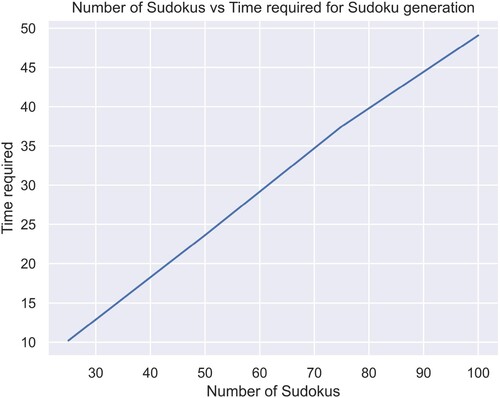
Table 3. Total time per set of iterations for Lena for a Sudoku of size in seconds.
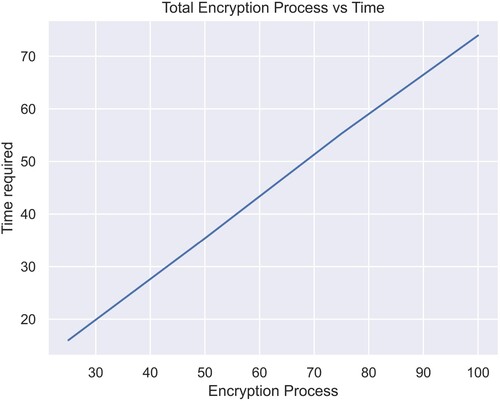
Table 4. Total time required for 100 iterations of all images using Sudoku and
Sudoku.
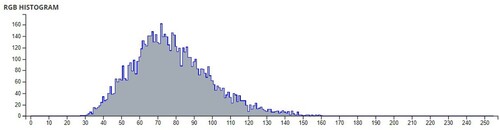
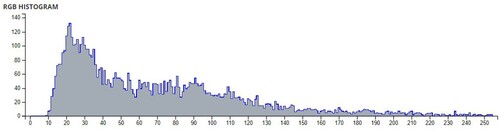
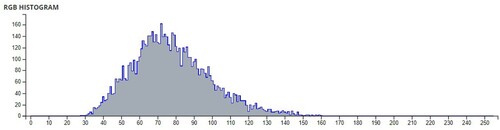
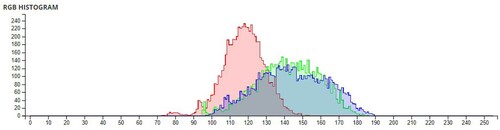
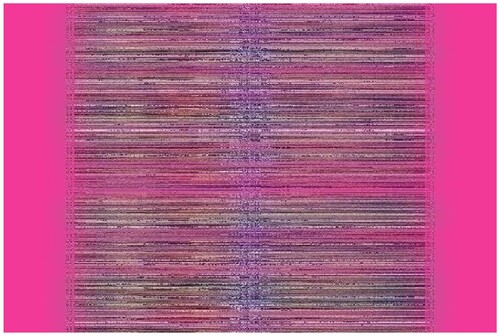
Table 5. Average pixel intensities of Images before and after encryption using Sudoku and
Sudoku.
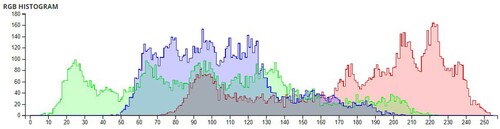
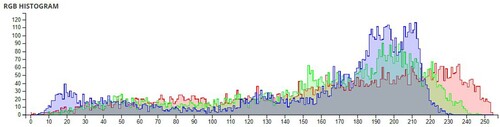
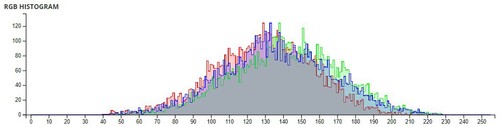
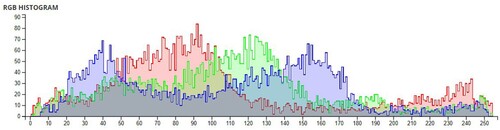
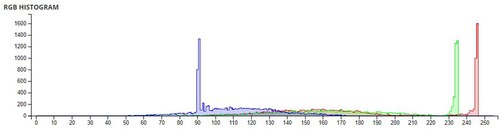
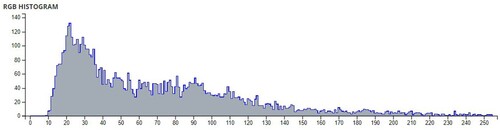
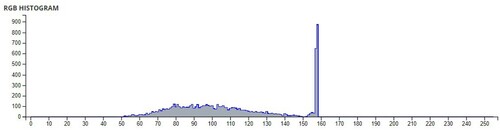
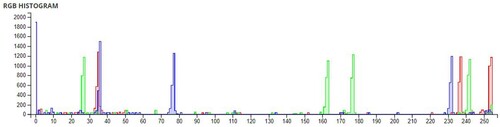
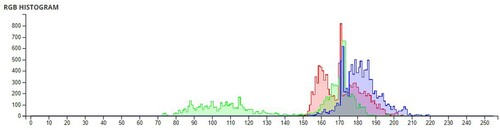
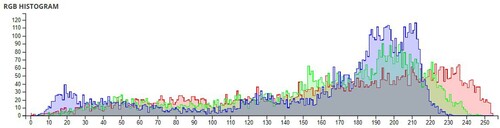
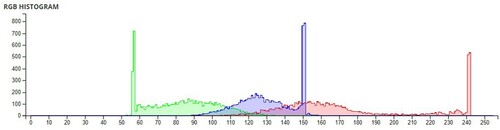
Table 6. Comparison of Shannon entropies of original images and encrypted Images.
Table 7. Information Entropies comparison for different algorithms on Lena.
Table 8. Obtained NPCR and UACI values for encrypted images using different Sudokus.
Table 9. Comparison of NPCR and UACI values between different algorithms on Lena.