Figures & data
Figure 1. Taxonomy of elliptic curves (Lara-Nino et al., Citation2018).
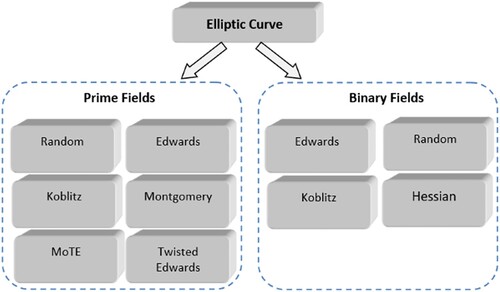
Table 1. ASCII-map table.
Table 2. Key size of RSA and ECC (Mahto & Yadav, Citation2017).
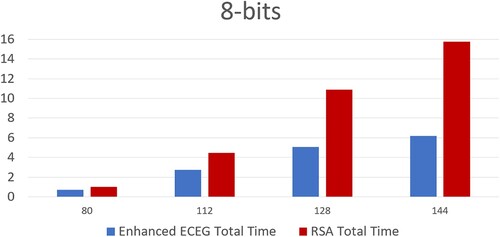
Table 3. Time complexity analysis of RSA and enhanced ECEG algorithms with 8-bit input (in seconds).
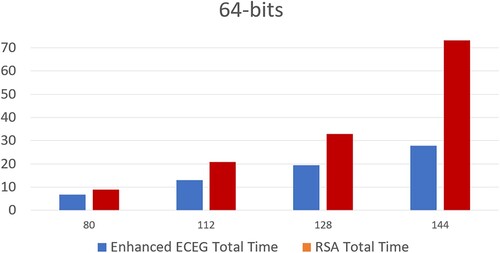
Table 4. Time complexity analysis of RSA and enhanced ECEG algorithms with 64-bit input (in seconds).
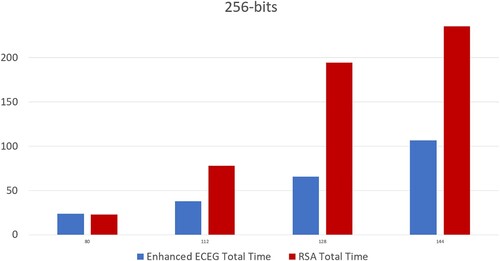
Table 5. Time complexity analysis of RSA and enhanced ECEG algorithms with 256-bit input (in seconds).
Figure 10. ECC (Mahto & Yadav, Citation2017) versus enhanced ECEG with 8 bit computation time.
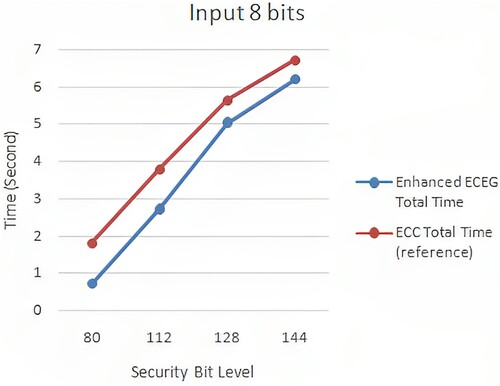
Figure 11. ECC (Mahto & Yadav, Citation2017) versus enhanced ECEG with 64-bit computation time.
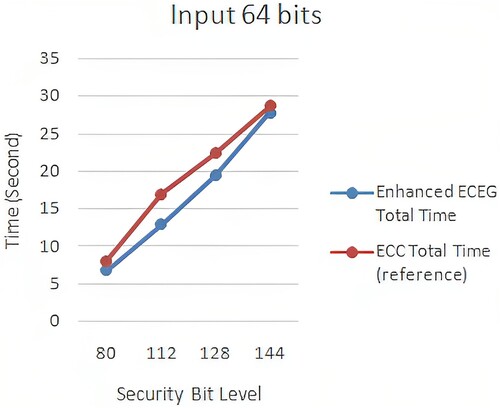
Figure 12. ECC (Mahto & Yadav, Citation2017) versus enhanced ECEG with 256-bit computation time.
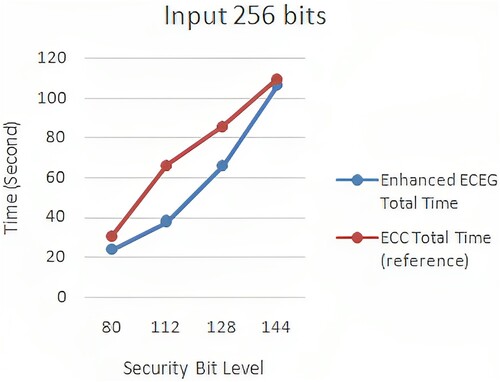
Table 6. Enhanced ECEG and ECC (Mahto & Yadav, Citation2017) with 8-, 64-, and 256-bit time complexity (in seconds).
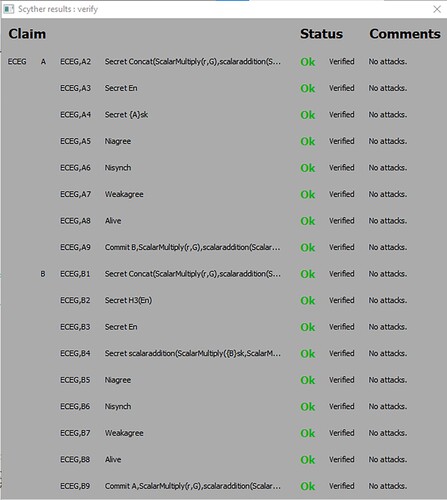
Table 7. Time and space complexity of authentication.
Table 8. Comparison of space and time complexity.