Evolution is what happens when you are not watching. An example is the personal computer. Computing for many individual persons has evolved from the ‘standalone desktop PC’ to a ‘networked PC’ to a ‘network of a PC and a laptop’ to a ‘network of PCs, laptops, printers, smartphones, etc’. This single processor has evolved into a complex ‘individual information system’ architecture just beneath the noses of information systems (IS) researchers. But are such small scale systems and architectures a topic worthy of IS research?
Without a doubt, IS are evolving, and evolving rapidly. We often use technology as a substitute for the major evolutionary indicators in IS. In many places, ‘Computing’ has evolved to ‘Information Technology (IT)’, which has in turn evolved to ‘Information and Communications Technology (ICT)’. The exponential rise of available computing power is well recognized. This rise is frequently emphasized the comparable computing power of today's small devices, which will inevitably have faster and more powerful processors, more memory, more storage, more sophisticated applications, and more communications bandwidth, than the large computer rooms of earlier times. Such rooms were physically large, and included ‘large’ mainframes, ‘large’ minicomputers, etc. From an IS perspective, it was perhaps more important that these computer rooms had a ‘large’ staff. For such a facility, there would have been a staff of more than 20 operators, systems programmers, application programmers, systems analysts, engineers, and managers. This facility would have been the information heart of a substantial centralized organizational IS.
This kind of organizational computing and data communications power has grown, but it has also migrated down to fewer and fewer staff. It is the changing organizational size that should be of equal interest in IS to the changing ICT power. While such computer power has shrunk to a single small device, like a smartphone or a laptop, the staff size has dwindled to a single individual, who manages this ICT power part-time and with relatively little training. As time has passed, the relative levels of ICT power have migrated to medium sized organizations and further to smaller organizations and further still to a single individual. The research discipline of IS kept up well as long as there was an organization at hand. There are many studies of small-to-medium-enterprises that have illuminated how these organizations have interacted with the increasing availability of powerful information and communications technologies. Of course, such IS studies examined more than just technology. These took more holistic views of the social-technical systems based on such technology. As we would expect, these studies centered on the changing organizations as the business, social and organizational impacts of the technology unfolded.
However, once this technological power continued to march downward in terms of organizational scope finally reaching a single individual, IS interests waned. Families and individual persons now possess progressively more powerful ICT. From these technologies, these individuals and family units are building complex and (at least compared to the computer room described above) relatively large-scale individually owned-and-operated IS.
Have we failed to notice the individuation of IS? Do individual persons independently own and operate complex IS?
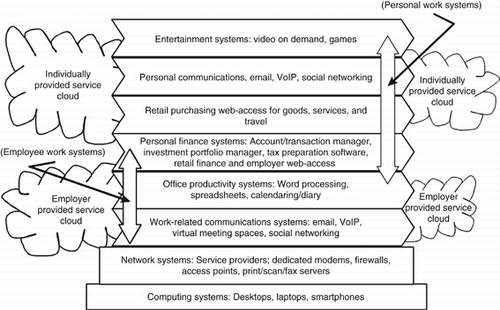
Consider one case of this phenomenon. The case of Jane Doe (a pseudonym) may seem familiar to many EJIS readers. Doe is a professional employee in a large government division. Doe has three dedicated computers, two desktop machines and one laptop. By dedicated, I mean used only by Doe and no others. One desktop is owned by her employer and is located in her office on her employer's premises. The remaining desktop belongs to Doe, and is located in her home office. Aside from Doe's dedicated laptop (provided by her employer), Doe owns two other laptops she shares with her family. Doe also owns a smartphone. Doe routinely uses three Internet providers, one provided to her office by her employer, one DSL connection she provides to her home and an Internet link to the smartphone via her mobile phone provider. Doe manages a LAN at her home that includes the DSL modem, a firewall, an Ethernet router, and a wireless access point. The home network also includes a printer, scanner, and fax machine.
While there are more than 50 separate software packages installed on Doe's computers, her main activities involve relatively few of these. The office productivity package is perhaps the mainstay of her work life, especially the word processing tool. The package is used to generate documents in all facets of her profession. She also frequently uses ancillary tools like a dictionary/thesaurus and language translation dictionaries. She also heavily uses an email package and diary/calendar application (both synchronized with the smartphone) as communications, planning, and record-keeping tools. She frequently uses a Voice over Internet Protocol (VoIP) package for low cost teleconferencing across the Internet.
From an individual perspective, she obtains many services from a ‘cloud’ provided by her employer. This cloud includes reference resources, such as publications and regulations, much of which is contracted for Doe's access by her employer. This employer cloud also includes various online access to customer data, vendor data, various online professional tools, and virtual meeting resources. Through the employer's personnel unit, Doe's personnel records, pay slips, employee-related benefits, etc. are also available in web-based form in this cloud. Doe also uses a few (usually free) services from outside her employer's cloud, including discussion groups, meeting planning tools, and shared file folder drop sites.
Doe's personal finance operates with tight links into the ‘retail’ banking, insurance, and financial services cloud available to Doe on an individual customer basis. Doe also uses a personal finance package to manage bank accounts and credit cards. She routinely uses this package to download and synchronize transactions for her banking accounts for review and reconciliation. She uses a separate package to manage a shares/stock investments portfolio. Doe also uses a tax package to prepare annual tax reports that synchronizes with the personal finance package, and draws information from both the banking and the employer clouds. The results are sent directly to the tax authorities across the Internet.
When she travels, even for professional purposes, Doe does most of her travel planning through airline and hotel booking web sites via the Internet. When she shops, most of her purchases are made online.
Doe's family also uses email heavily in communications. They are also engaged in a social networking service. The family has recently gained access to a web-based service from the local cable television provider, enabling Internet-based, on demand, high-definition access to the films, videos and television programs provided under Doe's personal cable subscription fees.
delineates the information system architecture of Jane Doe. Such individual IS architectures are unique at this time; many other examples would be more complex, and others simpler. This is a single example.
There are two elements in the architecture that might require slight elaboration. We note with vertical arrow two ‘work systems’ within this IS architecture. One is Doe's ‘profession’ work system as an employee. The other is the work system that serves Doe as a person. While Doe and her family might not regard their involvement with entertainment and personal communications systems as work, it is nevertheless work for the information system that Doe is operating. The other element is the representation of information services consumed and produced as arising from, and sinking into, clouds. The term cloud is used here in its loose, IS perspective because the ‘network’ is evolving to the ‘cloud’. This evolution is because of the increasing availability of not just low-level data services, but cloud-based business processes (CitationFingar, 2009).
This individuation of IS may go unnoticed in the IS research discipline, simply because we have traditionally defined the field in terms of social, organizational, and managerial relations. IS are more than computing and communications technologies (of course), but it is important to recognize that IS are more than just those technologies plus the information within them. Indeed, appending the human factors to this collection is also insufficient. IS have been understood as social-technical phenomena from the earliest years (CitationBostrom & Heinen, 1977; CitationMumford & Weir, 1979). But our understanding of the systems has grown. CitationAlter (2008) details more than 20 different authoritative definitions of IS. The definitions vary to extremes, but of these definitions, 12 include references to computers or technology, 12 refer to organizations, and four refer to society or social aspects (these counts overlap). Some refer to none of these. Alter himself goes on to define IS as a type of ‘work system’, ‘in which human participants and/or machines perform work (processes and activities) using information, technology, and other resources to produce informational products and/or services for internal or external customers’ (p 451). But even Alter's definition implies the exclusion of individuals with its reference to internal and external ‘customers’.
This centricity of the business-enterprise, the organization, or the society may reflect a prevailing attitude that research into individual IS is somehow ‘off our patch’. It may embody an assumption inherited from the days when individuals processed their personal information with uninteresting, very simple, paper-based systems. This assumption positioned individual IS only at the edge of the real, organizational IS. These individuals were more-or-less just customers of IS. For a business school, a meaningful business requires an organization. IS usage by organizations is, and should remain, one of the central foci of IS research. But does a meaningful IS always require an organization?
Such a viewpoint overlooks the essential human progress enabled by the ICT now available to individuals. It overlooks the way in which individual IS have evolved into rather a complete and legitimate form of IS. As technological evolution has enabled more-and-more complex individual IS, it seems that these could easily become the most prevalent of all kinds of such systems. Ignoring individual IS within our discipline is an evolutionary oversight that may simply reflect our own assumptions that personal, individual IS are uninteresting: simple; or mostly recreational systems used ‘after hours’ or outside of real organizational IS (CitationCrowston et al., 2010).
Why should IS researchers have any concern for individual IS? Perhaps we might begin with the recognition that we are fairly benighted about the phenomena. We might also recognize that these systems represent the most recent frontier for the design of computer based IS. These are complicated and unique systems that cross the boundaries between work and home. As such, individual systems still engage social aspects and organizational aspects. Certainly, these systems are socially constructed. It is not sufficient to regard individual IS as merely retail consumers of information, entertainment, and technologies. Very few individual systems are purely information sinks. People are not merely customers and game-players, but are actively collecting data and processing it into information for their various purposes, and feeding it outward.
Thus far, we have yet to seriously introduce our knowledge about complex IS into these individual versions. How has Doe designed her system above? Why has she made the choices, initiatives, and investments apparent in her individual information system? How does she plan and control this complicated architecture? How can our extant body of knowledge improve Doe's individual information system? What are the important relationships between Doe's system and other IS (e.g., individual or otherwise)? The list of possible research questions seems endless. Individual IS may well be an extremely large, undiscovered, arena for future IS research.
In this issue…
There are three regular papers in this issue of EJIS, followed by a special section on Transformational Government (t-gov).
How does the relationship between two different occupational communities (IT and business) influence the perceived performance of an IT department? In ‘Us and Them: A Social Capital Perspective on the Relationship between the Business and IT Departments’, Bart van den Hooff of VU University Amsterdam and Maarten de Winter of Accenture Netherlands offer a new insight on the social capital aspect of the relationship rather than the more commonly studied strategic IT-business alignment aspect. With findings from qualitative and quantitative data, the authors show that a lack of three elements of social capital (structural, relational, and cognitive) can lead to low perceived performance of IT department. Further, the findings suggest that social capital is particularly relevant for perceived IT performance in business functions. However, the effect of social capital is mediated through knowledge sharing in IT department. This study sheds light on the role that social capital can play in improving the IT relationship with business.
In ‘The Influence of the Informal Social Learning Environment on Information Privacy Policy Compliance Efficacy and Intention’, Merrill Warkentin of Mississippi State University, Allen C. Johnston of University of Alabama at Birmingham, and Jordan D. Shropshire of Georgia Southern University bring privacy policy compliance into focus with a social learning perspective. Prior studies have focused mostly on formal education and training to improve individual privacy policy compliance. Left unstudied is the important relation between informal social learning and an individual’s intent to comply with privacy policy. Drawing on social learning theory, the authors investigate the influence of three aspects of social learning (situational support, verbal persuasion, and vicarious experience) on privacy policy compliance. The findings from a survey of more than 200 health-care professionals suggest that social learning influences an individual’s intent to comply with privacy policy. This study underscores the importance of informal social learning activities to improve an individual’s policy compliance.
How can vendors of IT-enabled services achieve the scalability needed to respond to diverging needs of customers? In ‘Scalable Growth in IT-enabled Service Provisioning: A Sensemaking Perspective’, Mark Lewis of Bentley University, and Lars Mathiassen and Arun Rai of Georgia State University show that seven properties of sensemaking interfere with the efficacy of three scalability strategies (addressing equivocality through structural separation, reducing equivocality through market segmentation, responding to equivocality through service modularization). Based on an in-depth case study with a supply chain solution company (a subsidiary of a large package delivery company), the study reveals the role of socio-cognitive factors in scalable growth for IT services vendors. These are key factors for vendors who must deliver an increased variety of services to their customers.
Following these three regular articles, you will find the EJIS special section on t-gov, with a special editorial introduction to the four papers in this section by the special editors, Prof. Zahir Irani, Dr. Sofiane Sahraoui, and Dr. Ahmad Ghoneim. Together with these Special Editors, EJIS Associate Editors Eric Ngai of Hong Kong Polytechnic University and Sarah Spiekermann of the Vienna University of Economics and Business join Ray Paul, Frantz Rowe, and me in hoping you find this issue of EJIS rewarding and enjoyable.
References
- AlterSDefining information systems as work systems: implications for the IS fieldEuropean Journal of Information Systems200817544846910.1057/ejis.2008.37
- BostromRHeinenSMIS problems and failures: a socio-technical perspective, part i: the causesMIS Quarterly197711173210.2307/248710
- Crowston K, Fitzgerald B, Gloor P, Schultze U and Yoo Y (2010) Panel: IS after hours: how should IS researchers study non-organizational uses of ICT? International Conference on Information Systems, Saint Louis, Missouri.
- FingarPDot Cloud: The 21st Century Business Platform Built on Cloud Computing2009
- MumfordEWeirMComputer Systems Work Design: The ETHICS Method1979