?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.Abstract
Traffic has increased significantly over the past few years as a result of an increase in the number of vehicles using the common routes. It has been noted that manually operating signals has grown to be difficult. The difficulties encountered during an accident are the backed-up ambulances during emergencies caused by vehicle congestion and poor weather conditions like fog and haze. Considering this, the study focuses on the outcomes of an intelligent accident detection system using Vehicular Fog Computing (VFC). Automatic identification of crash spots and free flow of ambulances on roadways at peak hours of traffic. VFC has recently gained popularity as a useful tool for assisting vehicles in computing and storing service demands. Using the built-in sensors on a smartphone to monitor vehicular collisions and report them to the closest accessible first responder, as well as providing real-time location monitoring for paramedics and emergency victims would greatly improve the odds of recovery for emergency victims while saving time and money. This computing model guarantees the optimization of traffic congestion and energy consumption in the accident and foggy environment. This method also relies on delivering medical records to the closest hospital before the ambulance arrives, so pre-treatment can begin in the hospital.
1. Introduction
To improve the efficiency of the traffic system, a complex algorithm that must be automated and several sensors from which data will be gathered and communicated via the Internet of Things are required to improve the effectiveness of the traffic system. To be effective, the automated traffic control system must differ from the current approach [Citation1]. For each light, three colour patterns are fixed to a specific interval in this method. Using vehicular fog computing and taking into account the volume of traffic on the road, this needs to be made more adaptable. When heavy traffic is present in one direction, the system must be automated so that the green light remains on until the obstruction is cleared [Citation2]. When an ambulance needs to cross a traffic signal in an emergency, this method of signal maintenance might be more helpful. The traffic control system automatically stops all signals when it detects an ambulance, allowing the patient to reach the hospital in time to save a life. The limitations of the current traffic control techniques are overcome by this system.
Lack of emergency care results in a patient's death even after they have survived a car accident because emergency responders do not get timely reports about the accident. In accidents like car crashes, the emergency response time is crucial. According to studies, cutting crash reaction time by just one minute raises a person's chance of living up to 6%. According to a global survey conducted in 2017, 55% of the world's population lives in cities. It is predicted that the population will grow by 2 to 2.5% per year until 2025, resulting in more traffic on the roads. One thing to consider is that employees who live in cities may have to relocate to a location far from their workplace as the cost of living in cities rises [Citation3]. Naturally, this results in heavy traffic on the roads during rush hours, which causes congestion and makes it challenging for ambulance drivers to get through and reach the traffic signal. Additionally, officials use temporary fixes like adding lanes, raising the road level, constructing flyovers, and setting up detours during peak hours rather than coming up with a more cost-effective solution. The suggested approach gets around the aforementioned drawbacks by using vehicular fog computing to make traffic signals and the ambulance system smarter [Citation4].
The major contribution of this paper is, (i) Directly notifies the closest available responder in an emergency, (ii) A Smartphone application for emergency responders that gets immediate updates of emergencies that occur near them and provides real-time location of the victim as well as information about the patient such as name, blood type, and address, (iii) Image defogging methodology based on wavelet decomposition and the Dragonfly Optimized Gamm algorithm, (iv) In the event of a medical emergency, gives instruction to the closest hospital.
The remaining paper is presented as follows: the Section II discusses the literature survey works and the proposed algorithm is presented in Section III. Results and simulation are presented in Section IV. Finally, the paper concludes in Section V.
2. Literature survey
In this paper, the general survey is taken from Coimbatore, Tamilnadu where the road traffic and the inefficiency of the convolutional method have been studied. Coimbatore cCty is southern part of Tamilnadu. After independence, the city had great growth due to an increase in industries. The city has been crowded in the past few years as rural migrants come seeking jobs in the city.
2.1. Population
From the Table , the surveys on the population of Coimbatore city in particular years are calculated [Citation5]. Coimbatore city has increased in population by around 0.0323 million. From the analysis, in 2022 it is expected around 2.08 million.
Table 1. Survey on population of Coimbatore city.
Figure depicts the most common causes of car crashes involving a passenger vehicle. Furthermore, the driver and corresponding travellers in a car must obey some additional laws.
All inhabitants inside a vehicle should wear safety belts, remembering those for the secondary lounge.
All kids who are 160 cm or less in stature should be set in a kid seat.
No calls or visit applications ought to be taken/utilized while driving.
All speed limits on different sections of the road should be respected.
It is illegal to drive when under the influence of alcohol.
Figure 1. The most common causes of passenger car crashes demonstrated with an example of pie diagram (1991–2021).
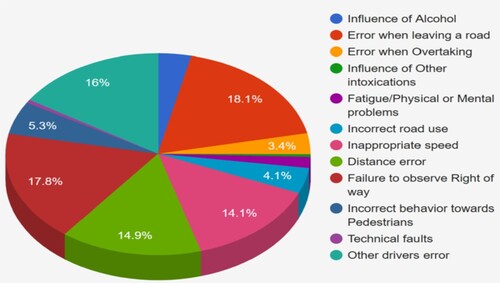
The most common cause of passenger car crashes is “the mistake when exiting the lane”. When exiting the main road to enter a side street or passage, it often involves shifting into reverse or heading backwards. In the past ten years, it has been involved in almost 440,000 traffic collisions, accounting for 18.1 percent of all accidents. Inside any designated crosswalk, drivers of motor vehicles must always concede the right-of-way to a nearby pedestrian. Failure to do so is risky and can lead to serious injuries. Other causes of road crashes affecting 4-wheel vehicles include driver error, distance error, and inappropriate speed [Citation6].
Figure shows the survey on a number of accidents which occur in Coimbatore. According to the survey by the Hindu newspaper, Coimbatore ranks 23rd in fatal accidents in India. On average, 180 accidents occur in peak hours. According to the survey done by Times of India, an average of 1 person dies in road accidents every 30 h. It is the greatest challenge for ambulance drivers to take the deceased to hospitals in traffic. So not only Coimbatore, but the entire nation is in need of an efficient smart automated system which controls the traffic signal as well as an ambulance which is connected to IoT to send information of patients to the nearby hospital [Citation7].
Figure 2. Survey number of accidents demonstrated with an example using image of road traffic of Coimbatore city in 2021.

Table shows the survey on the composition of vehicles in India from 2014–2021. It is very clear that we have a gradual increase in population and transportation by road which will be increasing in the upcoming years. Ultimately it leads to huge traffic in cities like Coimbatore which further leads to increase in road accidents in mere future.
Table 2. Composition of vehicles in India from 2014–2021.
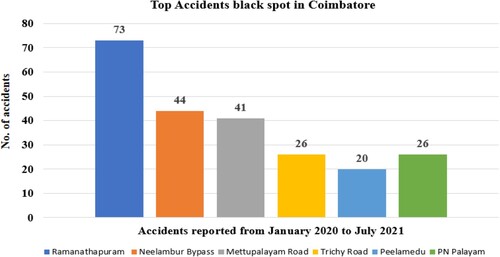
In Figure , the survey on number of accidents in Coimbatore from January 2020 to July 2021 is shown. From Figure itself, it is clearly shown that the Ramanathapuram area in the city with the highest number of accidents from January to July.
2.2. Fog environment
Climate has a significant impact on human life. However, the extraordinary growth in automobile traffic and industry has impacted the freshness of fresh air and the ecosystem. The satellite weather report offers the present status of a certain location but not its exact status. Due to weather changes occurring many accidents. The majority of road accidents occur when vision is poor or the motorist is unable to apply the brakes in time. This problem occurs during the winter and rainy seasons when visibility is reduced to zero owing to fog and severe rains, respectively.
Poor weather conditions like fog and haze. The fog is known by people as a “mobile killer” . A haze is a little obscuration of the lower atmosphere that is created by aerosol, which is made up of suspended droplets and particles in the atmosphere. It occurs as a result of smoke, droplets, and dust in the atmosphere. Fog has the ability to drastically limit visibility, it is vital that drivers remain focused on the road in order to stay safe. Driving in poor weather appears to be an impossible undertaking because it impairs visibility. As a result, the number of traffic accidents has grown. It produces poor lighting, which has a negative impact on the quality of the supplied images.
Fog is one of the major problems we face in winter conditions that driver many people face. Driving in a foggy atmosphere may lead to dangerous accidents. Statistics show the average number of deaths in a single accident. Major traffic accidents occur from time to time caused by foggy days. On a sunny day is about 1.86 times increase than a single accident happening on a foggy day.
Fog has the greatest impact on transportation, primarily airport operations and highway travel, but also on seaborne and rail public transportation. The consequences might range from aggravation due to delayed travel to fatal multi-vehicle highway accidents. Persistent, dense fog has the potential to ground or severely impede air transport. Fog can impair your sight on the road, preventing you from spotting automobiles or other landmarks directly ahead of you.
2.3. Simulation and prototype requirements
The below Table shows the basic requirements for the prototype model which includes both hardware and software components for the design. Also, the specification of the components is detailed below.
Table 3. Simulation and prototype requirements.
Cloud-based accident prevention and disaster recovery systems can experience latency and bandwidth issues due to the infrastructure's centralized nature. Fog computing, an evolving concept that promises lower latency, accessibility assistance, improved resilience, and scalability, will help solve these concerns [Citation8]. Furthermore, by using mobile sensors, the emergency warning and management systems in legacy vehicles can be made more inexpensive and simpler to install [Citation9].
3. Proposed methodology
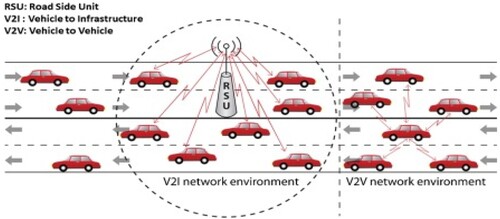
This segment describes the technique of fog-based application which uses the benefits of fog computing to diminish the general framework delays [Citation10]. The solution relies on the sensors found in modern smartphones to gather and process data, eliminating the need for an internal processing unit and extra sensors while also reducing the price of the device. The typical model of VANETs introduced in the literature includes two important components, which are On Board Units (OBUs), fixed on vehicles, and Road Side Units (RSUs) deployed on the roadside to help in establishing the infrastructure required for deploying VANETs [Citation11]. Every vehicle is presumed to be fixed with a bunch of sensors to gather the parameters around the vehicle; the OBU performs processing of the information that the sensors gather and transmits/receives them to/from other associated vehicles either directly or via RSUs that are close. The RSUs may also be connected to the Internet to yield the services required by the vehicles. Two main types of communication, as shown in Figure , can enable a wide range of applications: (i) infrastructure-based communication Vehicle to Infrastructure (V2I) communication; and (ii) direct communication between vehicles, Vehicle to Vehicle (V2V) communication.
Even though there has been a growth in the fascination around the probable advantages of VANETs, the dynamic characteristic of VANETs (vehicles can attach and detach as and when they wish) in addition to various system and application-based needs render it a huge challenge to develop effective techniques to ensure the privacy of vehicles. Privacy indicates the privacy of the vehicles (drivers) and the position of the vehicles [Citation12]. If a vehicle transmits a message, no one (with the corresponding management as an exception) must have the capability of deciding the identity or position of the vehicle from the messages that are transmitted by a vehicle. Simultaneously, the messages that a vehicle sends must be authenticated prior to its processing. Till these issues are resolved and the users are satisfied, the broad-level implementation of VANETs is not possible. Authentication has to be attained at two levels – first at the node level, known as node authentication and the second one at the message level, called message authentication. The fundamental concept of message authentication can be simply said to be the sender signing a message and later the verification of the authenticity and integrity of the message when the receiver gets it. A few authentications like reduced computational overhead, powerful and flexible authentication, and effective and scalable certificate revocation have to be dealt with and resolved to guarantee that the communication is secured in VANETs.
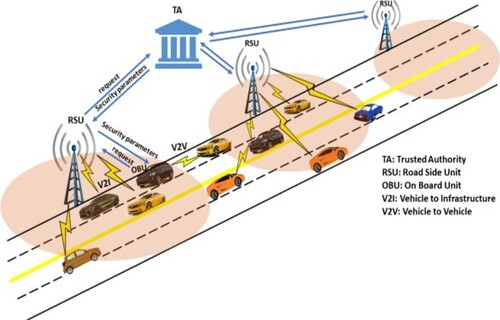
One of the primary challenges is guaranteeing the privacy of vehicles (drivers) and it needs an effective solution to be devised due to the fact that a malicious user could snoop on the travelling paths of a vehicle by acquiring and evaluating its messages and finding the vehicle (driver) leading to harmful incidents over the drivers. To deal with this problem, a few protocols in which vehicles make use of pseudonyms rather than their original IDs during communication are used when simultaneously facilitating the authorities to obtain the actual IDs from pseudonyms so that tracking and penalizing malicious vehicles is made possible [Citation13]. These protocols are known as conditional privacy-preserving protocols. Assignment of pseudonyms to vehicles and varying them often is one of the mechanisms utilized for guaranteeing the privacy of vehicles. To improve privacy, vehicles should alter the pseudonyms more often even though the number of times these alterations are done stays a question. Aspects including availability and storage size have a significant part to play in deciding the rate at which the change in pseudonyms must be done. A large number of the research in the literature dealing with security, authentication, and privacy employ a TA to obtain and load the OBUs and RSUs using security parameters like keys, certificates, and pseudonyms as shown in Figure .
It is also a huge challenge to provide security to VANETs against attacks due to intrusive vehicles owing to the dynamic characteristics of the network. Few of these attacks may be launched by nodes present in the network (i.e. nodes, which have been earlier authenticated to become a member of the VANET) [Citation14] few other attacks may be initiated by vehicles not from the VANET group. Besides this, the data redundancy model is studied in the section that follows.
3.1. Detecting accident
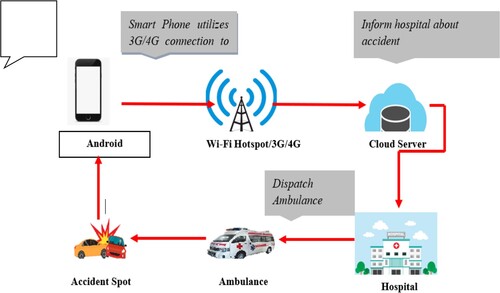
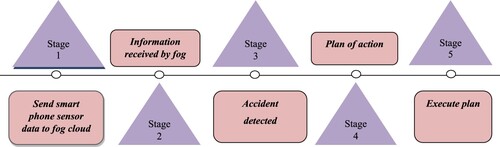
The identification process is concerned with deciding whether or not a casualty (accident) has happened. In this methodology, three in-built sensors have been used in the smartphone such as accelerometer, GPS sensor and microphone. Figure shows the block diagram of the proposed methodology for automated detection of casualty [Citation15,Citation16].
With the aid of IoT, details about the occurrence of any fatal crash on the roadways can be sent to the closest hospital, police department and fire station [Citation17,Citation18]. The ambulance driver will be given the shortest and safest route to take in order to get to the casualty location as quickly as possible once the information is shared. In the meantime, after picking up the patient, the patient's health condition is referred to the nearest medical clinic, so that pre-treatment plans can be made earlier.
The following is the protocol for the detection phase: Before beginning a journey, the car owner must open the application and a specific identification (ID) code is assigned to each car. The sensor data is constantly tracked by the programme. If the accident detection value is greater than or equal to 1, it identifies an accident has occurred, and a warning is generated and shown to the user for 10 s. A false alert is registered and stored in the archives if the warning is cancelled. The warning process continues if the alarm is not cancelled. For this, a system known as Emergency Response and Disaster Management System has been initiated [Citation19]. This system is based on fog computing which has less access time since it can access the data using smartphone sensors and communicate. As the sensors in the system need not be manipulated separately, it is a cost-effective method that can replace all conventional methods. Figure shows the system flow of ERDMS and also Table depicts ERDMS's advantage over the conventional method.
Table 4. ERDMS advantages over conventional method.
Each sensor's threshold is defined in order to determine whether or not a calamity has occurred. The force of gravity is measured using an accelerometer and Positioning System (GPS). If the value is greater than 4, crash the scene. Subsequently, by means of this value alone generates a large number of false positives. This also includes the speed of the vehicle and the sudden variation of the speed along with sensors values such as accelerometer sensor; microphone as well as GPS are used for precise calculation of the spot. If the vehicle speed variation is more than 2.07, then the vehicle is considered as a crashed state. Equation (1) is used to determine the detection of a casualty (accident) situation.
(1)
(1)
3.2. Android APP and WEB server design
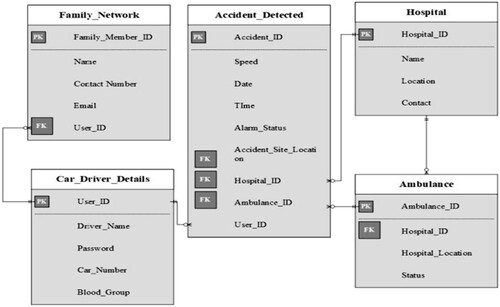
Since the fog-based system is based on smartphones, it is important to build an application to enhance the system's efficacy. All users will be directed to a login tab, where they must enter all of their personal information during the sign-up process. As seen in Figure , your mobile gets tracked after the login process. When the smartphone detects a casualty (accident), it sets a timer for 25 s. This functionality is used to prevent crash fault detection. If there is no crash, the user may manually stop the timer, or the device can transmit the accident reports to the closest police department, fire station, and ambulance using IoT. On arriving at the casualty spot, the ambulance would transfer the patient's details to a local hospital. The hospital can access the information through a website created with Angular JavaScript. The patient's name, phone number, email ID, crash venue, blood group, car number, date, and time will be listed on the website dashboard as shown in Figure .
When an error is discovered, the next step is to formulate a suitable course of action. This includes using the Google Maps Application Software Interface to assess the site of the crash and the closest hospital. If the victim's place is determined, a nearby ambulance is notified by a message sent from the victim's smartphone, along with the necessary details. Furthermore, when a person uses the app, they are asked to provide details about any two of their friends or family members who might be called in the event of an emergency [Citation20–22]. As a result, anytime an injury occurs, a Short Messaging Service is launched, and information about the injured patient and hospital is communicated to the family members or friends. When the whole course of action has been carried out, the evidence is saved in a single archive.
3.3. Automated traffic signal
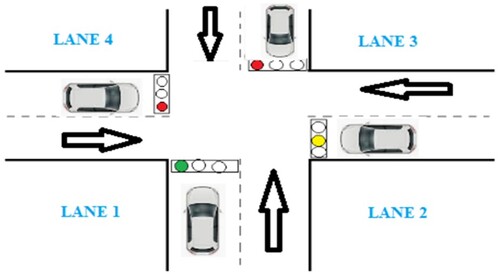
The proposed method uses Vehicular Fog Computing to effectively manage the traffic during peak hours. LEDs are used to denote traffic light and ultrasonic sensors are used for sensing the vehicles in the signal. This system is managed by automatically reducing the congestion in the signal. The timing of traffic light signals is determined by real-time traffic data. If one lane is heavily congested, the signal length will be prolonged before the traffic is cleared. The cloud would receive all of the data obtained from the signal. This can shorten the time it takes an ambulance to arrive at the hospital, saving a lot of lives. Figure represents a traffic signal automation scheme. In the event of an emergency, if lane 1 is open, lane(s) 2, 3, and 4 will be blocked before the ambulance reaches the signal.
3.4. Algoritham for counting vehicles
Assume that the IR sensor is detecting only vehicles
3.5. Algorithm to control traffic light
3.5. Accident prevention technique in FOG environment
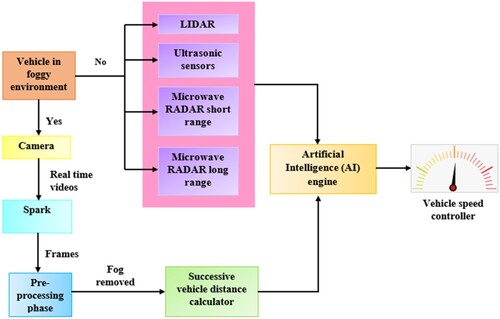
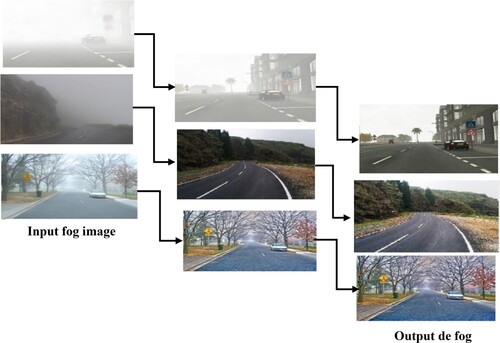
Outdoor pictures suffer from poor visibility due to light diffraction and absorption of airflow in fog. Images taken outside are affected by a variety of variables, including lower contrast and colours caused by fog, rain, haze, and so on. Because of bad weather conditions over the winter, drivers have found it difficult to distinguish barriers and other vehicles, resulting in road accidents. This scientific initiative has the potential to tackle this problem and save many lives. In this section, the suggested system has been described in detail. In foggy conditions during a car, while driving, a car front camera gathers real-time videos. The camera sends the real-time videos to the big data processor Spark. In the Spark separate the videos into small – small frames. Then the Spark send the frame to the image processor, which processes the image in foggy image to de foggy image [Citation23,Citation24]. Accident Prevention Technique (APT) in foggy conditions is proposed for efficaciously retrieving the fog-free image and preventing accidents. The foggy image is divided into high and low-frequency sub-images using DWT (Discrete Wavelet Transform), which has the advantage of preserving temporal features so that information loss can be stopped. Then the low-frequency and high-frequency images are processed with defogging and denoising modules to remove fog and noise respectively. The DOG (Dragonfly optimal Gamma) algorithm and Bilateral Filter defogging module dynamically enhanced the colour detail information without human intervention so that observed scene contrast and visibility are well preserved. Lastly, a fog-free image is reconstructed from sub-enhanced images [Citation25,Citation26]. After completing all the processes images are sent to Artificial Intelligence (AI) engine, which will control the vehicle's speed. Figure shows the schematic representation of the accident prevention technique in a fog environment.
3.6. Successive vehicle distance calculation in defogging
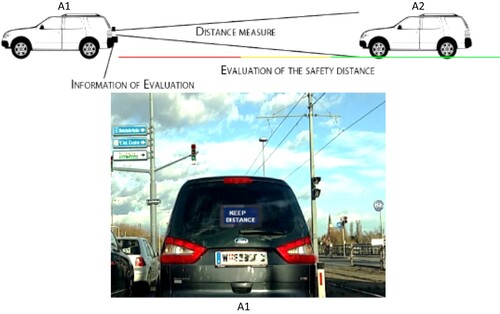
Every vehicle on the highway can receive the GPS information of the other vehicles, and the distance (D) between its vehicle and the other vehicles calculates the distance using the below formula. Consider two vehicles A1 and A2, where A1 is the vehicle in front and A2 is the vehicle behind travelling at a higher velocity than A1 shown in Figure .
Where,lat1, lon1 – latitude and longitude of A1 vehicle,
lat2, lon2 – latitude and longitude of A2 vehicle,
R – Earth radius in kilometre,
D – Distance obtained in kilometre.
After calculate the vehicle distance, which gives the AI engine it decides to control the vehicle. This process is very useful in bad weather condition, which avoids accidents.
4. Result and discussion
The built-in sensor will repeatedly detect the traffic accident and send an emergency message to the nearby emergency responder, giving the possibility of saving the victim's life in situations where victims are unable to call an ambulance on their own during fatal collisions. Sending an emergency message is much easier and more secure now that all crucial features are housed in one place. The tool aids in faxing a request to the appropriate ambulance department in the event of any emergencies. From the standpoint of an emergency responder, the programme can provide them with information about nearby emergencies, enabling them to quickly identify patients and evacuate them, making better use of the resources available for emergency response. We carried out some experiments by falling a smartphone from heights 15, 25, 35 and 45 cm, recording the g-force values, which are seen in Table .
Table 5. Gravitational force during dropping the smart phone.
We dropped and checked a smartphone up to ten times and reported the findings. We discovered that accidentally dropping a smartphone would not allow the device to trigger an alarm. In our research, the highest g-force value obtained by a falling smartphone from a height of 45 cm was 2.528542508. If the g-force value exceeds 4 g, our system will generate an alert.
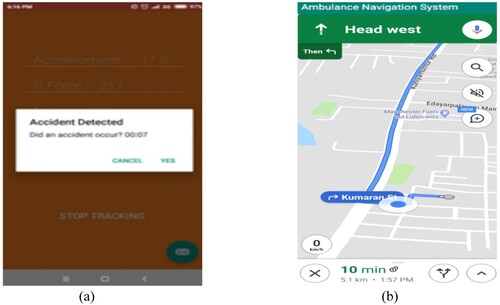
The proposed approach is examined in a cloud-based setting where the smartphone sends data to the cloud for processing. The above Figure (a,b) shows the stepwise function of accident detection.
Table expresses the device configuration for fog, smartphone and proxy based on testing in the environment with the appropriate devices.
Table 6. Device configuration for fog.
Table signifies the comprehensive system configuration predicated on the smartphone and user count.
Table 7. Detailed configuration of the system.
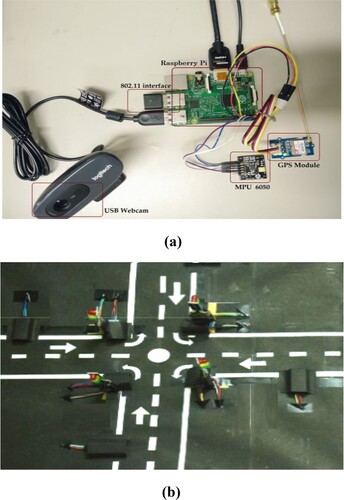
Where, Figure (a) represent an Experimental setup for the detection of an accident automatically, Figure (b) represent a Model of Automated traffic control. As seen in Figure , the device is made up of on-board sensors. The in-vehicle onboard unit (OBUs) constantly monitors the vehicle's acceleration and orientation in order to detect collisions. When a collision occurs, the most important details are sent to a local Edge node, including geographical location (latitude and longitude), the date and time, vehicle interior temperature and chassis number.
Figure 13. (a) Illustrates with an example for the detection of accident automatically and (b) Illustrates with an example of automated traffic control.
The proposed model defogging performance on the road is shown in Figure . Here to analyse the performance some images is collected from publicly available dataset. The results reveal that the APT model is suitable for various scenario defogging. Most of the existing techniques were developed only to process the homogeneous fog, but the proposed model DOG can adaptively clear all fog, and enhance and brighten the color in the image.
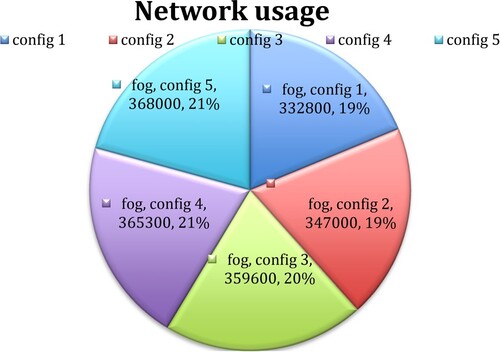
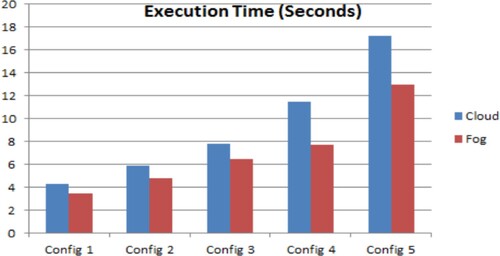
Figure shows the network usage of fog and Figure shows the comparison of cloud and execution time. It compares the execution time of a fog node to that of a cloud server. It's worth remembering that the assistances of fog-based ERDMS become additionally apparent as the number of devices grows, so transmission occurs with lower average latency and bandwidth utilization. It is obvious that fog computing saves power, while cloud computing uses more network data while transmitting them. Both tasks are diverted to the cloud data centres by using the cloud for computing and storage. These employees travel the whole network from point origin to point endpoint. Thus, fog computing increased the performance by up to 21% compared with other existing techniques.
5. Conclusion
Fog computing enables localized, reliable data processing, which is particularly advantageous in applications that require quick response times. Low delay, regional distribution, and mobility assistance are the advantages of the proposed system. Lower response times are regarded as an especially significant requirement in calamity prevention and emergency warning systems, as delays can result in fatalities. In contrast to cloud-based systems, the fog-based ERDMS optimized the latency, network utilization, and execution time, according to the test results. The assessment of the planned scheme in a virtual world is one of our study's weaknesses. Traffic delays that block ambulances during emergencies put patients’ lives in danger and are a threat to ambulances in accidents. This research concept (ERDMS) will reduce the traffic issue and death rate using Vehicular Fog Computing by automatically detecting the accident spot and passing information to nearby hospitals for prior arrangements based on the health condition of the patient. This method also focuses on the free movement of vehicles during peak hours without getting stuck in traffic.
Disclosure statement
No potential conflict of interest was reported by the author(s).
References
- Peng X, Ota K, Dong M. Multi attribute based double auction toward resource allocation in vehicular fog computing. IEEE Internet Things J. 2020;7(4):3094–3103. doi:10.1109/JIOT.2020.2965009
- Ning Z, Huang J, Wang X. Vehicular fog computing: enabling real time traffic management for smart cities. IEEE Wirel Commun. 2019;26(1):87–93. doi:10.1109/MWC.2019.1700441
- Cretu DRBA, Yi J, Avram C, et al. Flying ad hoc network for emergency applications connected to a fog system. Lect Notes Data Eng Commun Technol. 2018;17(1):675–686. doi:10.1007/978-3-319-75928-9_60
- Chaurasia N, Kumar P. A comprehensive study on issues and challenges related to privacy and security in IoT. e-Prime – Adv Electr Eng Electron Energy. 2023;4:100158. doi:10.1016/j.prime.2023.100158
- Khan A, Bibi F, Dilshad M, et al. Accident detection and smart rescue system using Android smart phone with real time location tracking. Int J Adv Comput Sci App. 2018;9(6):341–355. doi:10.14569/IJACSA.2018.090648
- Aydin C, Tarhan C, Ozgur AS, et al. Improving disaster resilience using mobile based disaster management system. Procedia Technol. 2016;22(1):382–390. doi:10.1016/j.protcy.2016.01.027
- Muzakkir Hussain M, Alam MS, Sufyan Beg MM. Vehicular fog computing-planning and design. Procedia Comput Sci. 2020;167:2570–2580. doi:10.1016/j.procs.2020.03.313
- Khaliq KA, Chughtai O, Shahwani A, et al. Road accidents detection data collection and data analysis using V2X communication and edge or cloud computing. Electron (Basel). 2019;8(8):896. doi:10.3390/electronics8080896
- Sami H, Mourad A, ElHajj W. Vehicular OBUs as on demand fogs: resource and context aware deployment of containerized micro services. ACM Trans Network. 2020;28(2):778–790. doi:10.1109/TNET.2020.2973800
- Lin C, Han G, Qi X, et al. A distributed mobile fog computing scheme for mobile delay sensitive applications in SDN enabled vehicular network. IEEE Trans Veh Technol. 2020;69(5):5481–5493. doi:10.1109/TVT.2020.2980934
- Osanaiye O, Chen S, Yan Z, et al. From cloud to fog computing: a review and a conceptual live VM migration frame work. IEEE Access. 2017;5(1):8284–8300. doi:10.1109/ACCESS.2017.2692960
- Salma RN, Balaji NA, Sukumar R. A framework for authentication in vehicular ad-hoc network using identity based approach. IOSR J Eng. 2013;3(7):15–19. doi:10.9790/3021-03731519
- Park Y, Rhee KH, Sur C. A Secure and Location Assurance Protocol for Location-Aware Services in VANETs’. 2011 Fifth International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing. 2011;2(11):456–461. 10.1109IMIS.2011.40
- Kamat P, Baliga A, Trappe W. Secure, pseudonymous, and auditable communication in vehicular ad hoc networks. Secur Commun Networks. 2008;l(3):233–244. doi:10.1002/sec.27
- Xie Y, Zhang S, Li X, et al. An efficient cooperative message authentication based on reputation mechanism in vehicular ad hoc networks. Int J Distrib Sens Netw. 2019;15(6):1–13. doi:10.1177/1550147719854910.
- Zhang X, Wang W, Mu L, et al. Efficient privacy-preserving anonymous authentication protocol for vehicular ad-hoc networks. Wireless Pers Commun. 2021;120:3171–3187. doi:10.1007/s11277-021-08605-x
- Lakshmi Narayanan K, Robinson YH, Krishnan R, et al. Internet of things based smart accident recognition and rescue system using deep forests ML algorithm. In: Balas VE, Solanki VK, Kumar R, editors. Recent advances in internet of things and machine learning. intelligent systems reference library. Cham: Springer; 2022. p. 215. doi:10.1007/978-3-030-90119-6_4
- Kumar A, Khusru Akhtar MA, Pandey A, et al. Smart city vehicle accident monitoring and detection system using (MEMS, GSM, GPS) Raspberry Pi 4. IETE Journal of Research. 2022. doi:10.1080/03772063.2022.2043787
- Pant B, Sharma H, Chawla R, et al. An IoT-based intelligent traffic engagement system with emergency vehicles pre-emption. Int J Sens Netw. 2022;40(1):10–19. doi:10.1504/IJSNET.2022.125271
- Rathod GS, Tipale RC, Jajulwar K. Intelligent accident detection and alerting system based on machine learning over the IoT Network. 2022 International Conference on Futuristic Technologies (INCOFT), Belgaum, India, 2022. pp. 1–6. doi:10.1109/INCOFT55651.2022.10094513
- Josephin Shermila P, Sharon Priya S, Malarvizhi K, et al. Accident detection using automotive smart black-box based monitoring system. Meas Sens. 2023;27:100721. doi:10.1016/j.measen.2023.100721
- Uma N, Saktheeswari R, Indumathi A, et al. Smart accident detection and alert system. Int J Eng Res Technol. 2023;11(3):1–7. doi:10.17577/IJERTCONV11IS03004.
- Saxena P, Sonwani S. Primary criteria air pollutants: environmental health effects. In: Saxena P, Sonwani S, editors. Criteria air pollutants and their impact on environmental health. Singapore: Springer; 2019. pp. 49–82. doi:10.1007/978-981-13-9992-3_3
- Choudhary M, Kumari S, Chaulya SK, et al. Perceptive driving assistant system for opencast mines during foggy weather. Mining Metall Explor. 2022;39(7):1–17. 10.1007s42461-022-00678-x
- Jalew EA. Fog computing based traffic safety for connected vulnerable road users. Mobile Computing. Université Bourgogne Franche-Comté, 2019. English. 〈NNT: 2019UBFCK057〉. https://theses.hal.science/tel-02459792.
- Emambocus BAS, Jasser MB, Mustapha A, et al. Dragonfly algorithm and its hybrids: a survey on performance, objectives and applications. Sensors. 2021;21:7542. doi:10.3390/s21227542