?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.Abstract
Mobile ad hoc networks (MANETs), which include vehicular ad hoc networks (VANETs), are a promising method for intelligent transportation systems. The major challenges of VANET protocols are symmetric links and changing topology of the networks and hence a proper routing method is necessary for VANET. A crucial issue with VANETs is the transmission of data from a starting point to the base station. To discover the least path with the lowest cost and fewest hops between the source and the destination, existing work uses a novel priority-based direction-aware collision avoidance (P-DVCA). To direct the ants to develop a shorter path with fewer hops for data transmission, the suggested method uses the prioritising and scheduling enhanced congestion control-based source ant colony optimization (ECC-ACO) for VANETs. Based on the message type and network situation, this technique provides precedence for privacy messages communications. Privacy messages can also be divided into beacon messages and occurrence messages. At that point, each message is routed into the appropriate queue predicated on its primary consideration, and each message in each queue is planned. When compared to renowned VANET communication architecture, simulation and analytical findings show that proposed ECC-ACO offers a respectable reduction in collisions.
1. Introduction
VANET is a distinct type of MANET with properties of high flexibility and frequent topology. VANET is a self-configuring identity network designed for the time-critical exchange of information and communication. VANET offers a variety of services, including crash, incident reporting, investigation prevention, traffic control and escapism [Citation1–3].
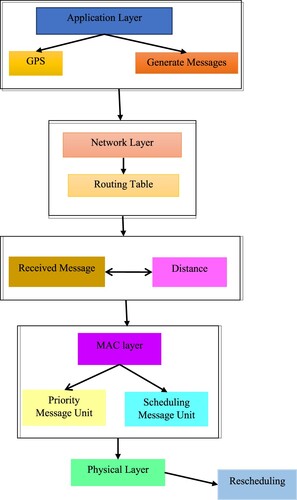
Vehicle-to-infrastructure (V2I) and vehicle-to-vehicle (V2V) communication modes are used by VANETs to achieve different levels of functioning (V2V). In a V2V model, nodes talk to one another directly, whereas in a V2I model, devices talk to each other while transferring data to other ground stations or a wireless device [Citation4,Citation5]. Compared to the V2V architecture, the infrastructural development and maintenance costs for the V2I architecture are higher [Citation6]. To efficiently manage the flow of information through cluster heads (CHs) and group comparable nodes, both connections typically use clustering [Citation8–10]. Wireless Access in Independent Escort (WAVE) is one example of a VANET heterogeneous network that uses a multi-layered protocol suite [Citation11,Citation12]. Among them are the layers of the physical, networking, Media Access Control (MAC), application, and security of the state.
However, a number of issues must be resolved at all VANET communication architectural tiers for effective collision detection in a CCA implementation. The orientation of nodes, which is critical for collision detection on input and output highways, is not taken into account by current VANET architectures [Citation13]. As a result, calculations of collision probabilities at the application layer become erroneousr effective collision detection in a CCA implementation. The orientation of nodes, which is critical for collision detection on input and output highways, is not taken into account by current VANET architectures [Citation13]. As a result, calculations of collision probabilities at the application layer become erroneous. Furthermore, the current application layer protocols’ performance is negatively impacted by the fixed decelerations they use as preventative measures [Citation14]. The existing security services layer architectures jeopardize the secrecy of these signals due to significant computational overheads and plaintext data acquisition for warning messages. Additionally, it has been discovered that the current VANET architectures are deficient in their ability to route warning messages while accommodating frequent topological changes on bi-directional roads [Citation15]. Another significant flaw in the current VANET systems is the unprioritized sending of warning messages at the MAC layer [Citation16].
This work's major contributions are as follows:
The Priority Message Unit (PMU), which considers the static factor, message size, and dynamic factor, assigns priorities to the messages. Clustering is used to compute the dynamic factor. The static factor divides messages into safe and unsafe categories.
The Scheduling Message Unit (SMU) changes the time for these texts to the media access a management line and the underlying infrastructure queue according to their priorities. Low-priority communications and service text are routed to service channel queues, whereas high-priority communications and security emails are routed to regulate connection queues.
We propose a new Enhanced Congestion Control source-based Ant Colony Optimization (ECC-ACO) routing protocol for trying to locate the least distance with the fewest hops possible for the routing algorithm.
The suggested model for providing route information to guide ants uses a source-based concept. The complete address from source to destination is included in the route information.
The ECC-ACO is used in combination with PMU, SMU, and a citation concept to evaluate the ideal shortest distance with the fewest hops while taking edge distance and heuristic information density into account.
Additionally, this paper compares the proposed ECC-ACO with currently used techniques, including F-ACO, AODV, and AntNet.
2. Related works
A VANET's technology and data have many layers, including application, security agencies, connection, MAC, and infrastructure layers. The application analyzes nodes, predicts possible future collisions, and defines prevention measures for cooperative collision avoidance. Warning messages are created at this layer and supplied to inform both of these nodes about potentially hazardous events with the help of the lower layers [Citation17]. Because malicious operations on warning messages can result in massive collisions, secure communication of danger signs remains critical. The trained security layer is in charge for upholding security. The internet protocol distributes advanced warning to receiver nodes on the most effective networks to reduce congestion problems and packet loss rates because timely and dependable delivery of this urgent signals is still essential. The MAC layer seeks to maximize shared channel utilization, whereas the core network sends bits using electronic technology. Effective collision avoidance cannot be limited to a single layer because each layer has its own relevance; as a result, it is a cross-layer problem [Citation18]. In the literature now available, this section discusses notable VANETs. Real-time data clients are given a priority value by the PR-CAI routing protocol for the SDN network [Citation19] based on the functions of deadline, vehicle social standing, and permission shortlisting. The rating is intended to select the best planning application. Details on vehicle status and network circumstances that are covered by RSUs are included in the function for traffic status. The priority-based scheduling algorithm (PSA) for SDVN's architectural style, which splits emails into security and non-security queues, was presented by the authors [Citation21].
Prioritizing safety messages and non-safety texts, including both, was done using the New Deadline and Size of Data (NDS) and First Come, First Serve (FCFS) techniques. By adaptively attempting to schedule beacon signals, location-based beacon scheduling (CABS) [Citation22] prevents beacon overloading in higher places. For dynamic scheduling, CABS adds information to beacon messages such as speed, guidance, and location. While low latency and minimal level jitter are both essential requirements for the algorithm for tabu search in MOTabu, minimal level delay is solely taken into account in UOTabu. To establish the best transmission rate and range, MOTabu uses short-, mid-, and selective memories. These techniques, more than others, lessen packet loss and delay. A congestion control technique assigns priorities based on the helpfulness and credibility of communications, as well as the speed of sending and receiving nodes. Then a prioritized message was planned. The performance results in a reduction in the latency of the safety challenges, but it is still higher than 40 ms, which is the one-time length of time for a host controller or a capacity to apply [Citation23].
To address the restriction satisfaction problem, the [Citation24] attempted to offer advanced ant colony optimization with an automated updating approach (AU-ACO) (CSP). Predetermined optimization of the CSP type is crucial. The researchers of this work improve ACO by resolving CSPs. To identify the ideal pairs in the chosen assignment, AU-ACO regularly reorganizes non-excellently varied pairs while keeping fantastically varied couples. The convergence rate of AU-ACO is accelerated by only adjusting variable-value pairings with less-than-ideal values. The vertices of the graph (G) used to describe the issue in AU-ACO are the variable-value pairings. The assignment's vertices do not violate. Based on signal values and other heuristic data, the ACO creates an assignment that is comprehensive and has great variable-value pairings. The longevity of ad hoc networks is influenced by the nodes’ lifespans (wireless sensor networks or VANETs). ACO is combined with the butterfly optimization algorithm (BOA) to increase network lifetime [Citation25]. In the proposed study, a fitness function is used to select a secure cluster head from the BOA. To determine the shortest path, the ACO takes into account spacing (distance measure), base station strength, and node extent levels. This study demonstrates the ACO's flexibility, efficiency, and suitability for the route request.
Analysis and comparisons of the ACO protocol with reactive and proactive protocols were done [Citation26]. The ACO protocol in this study mimics the fundamental behaviours of ants. The ants move in the direction of the target while leaving signals in their wake during the route-finding phase. Towards the route reaction phase, ants move in the direction of the source and lay down pheromone in accordance with the rate of evaporation. The packet is routed on the path of largest pheromone density. ACO outperforms reactive and proactive protocols in terms of performance thanks to its parallelism, fault tolerance, and flexibility properties. Ramamoorthy and Thangavelu [Citation27], and Sinwar et al. [Citation28] identifies the shortest route for transmitting protocols on VANETs using enhanced distance-based ant colony optimization routes (EDBACOR). This plan combines the distance-based approach (DBA) and the adjusted ACO to improve forwarding in VANETs. IDBACOR is used to find the shortest paths, which reduces operational costs, communication costs, and information sharing delays.
An overview of different enhanced congestion control source-based ant colony optimization (ECC-ACO) solutions is given above, along with a discussion of their shortcomings. Various issues are attempted to be minimized in this work in order to create a trustworthy and safe VANET system. Improvements in the present congestion control systems are assured by higher throughput, less delay, and fewer packet losses.
3. Proposed method
The goal of the planned ECC-ACO was to determine the path between the starting point and the end point with the fewest hops and lowest cost. The distance computation technique (DCM), which employs the distance formula, is now used to determine the separation between two moving vehicles. Until one-hop neighbours are gathered and a list of one-hop neighbours is updated in the vehicle routing tables, the vehicles will operate in promiscuous mode. Following the full-duplex mode, a list of a vehicle's acquaintances can be found in the vehicle routing protocol. The distance between the vehicle and its neighbours is then calculated using the neighbour list and the range formula. When the lengths are ascertained, each vehicle's route optimization database is refreshed with the premeditated distances.
The enhanced congestion control source-based ant colony optimization (ECC-ACO) method was employed in the proposed method to determine the fastest way with the fewest hops between these sources and destinations. The ACO uses a vehicle's routing database to discover its neighbours and the distance between them. The suggested ECC-ACO utilizes its methods to locate and maintain the shortest path based on neighbours with distances that have been identified.
The enhanced congestion control source-based ant colony optimization (ECC-ACO) was used in the suggested method to discover the path with the fewest hops between sources and destinations. The ACO uses a vehicle's routing database to discover its neighbours and the distance between them. The suggested ECC-ACO utilizes its methods to locate and maintain the shortest path based on neighbours with distances that have been identified. despite the proposed ECC-ACO diagram.
3.1 Priority message unit (PMU)
In the VANET, the vehicle sends the message, which is received by other featuring. The comparative transmitting times for each statement are then determined according to the priority assigned to each statement. Priorities are determined by the static component, dynamic component, and message size.
(1)
(1)
In order to offer channel access within the clusters and to reduce channel contention, clustering is implemented. Clustering increases network capacity because it enables the geographic reuse of resources. Cluster head (CH) selection in clustering is dependent on mobility. Because configuration is constantly changing, CH is chosen in order to maintain a stable cluster. Every base station in a cluster sends a status update every Control Channel (CCH) interval. The cluster's CH is chosen based on which vehicle has the highest Service Channel (SCH). Here, each node will communicate with the nodes in its own cluster, and CH will communicate with all nearby clusters. The CH of the neighbouring cluster will receive this information and broadcast it to that cluster as well as to all nearby clusters, and so on.
The equations are following as cluster head selection using each node in priority message unit.
3.1.1 Metric for average velocity (Vel)
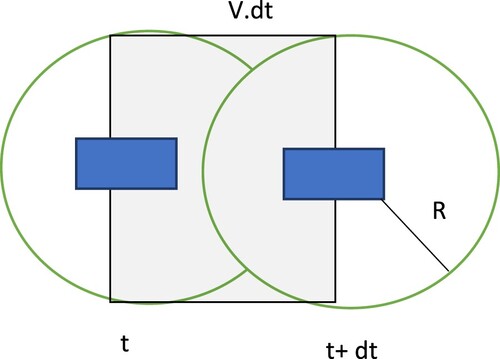
The relative occurrence of a cluster conversing with other k clusters within its radius R while flowing at a flow velocity of v in a period of time of dt is what is meant by this term. The provided velocity monitoring is
(2)
(2)
R = cluster communicate and interact (i.e. 100 m), v = average speed in time dt.
depicts the velocity metric of a CH. If the average velocity is very high, the constellation will cover a large amount of ground in a short period of time. As a result, the likelihood of lack of connection from near the area clusters rises, raising Vel. When the average speed is low, this cluster seems to have enough time to communicate with its neighbourhood, causing the Vel value to decrease.
3.1.2 Usability measure (Use)
The chance of communication retransmission by neighbouring CHs is how one might conceptualize it.
(3)
(3)
(4)
(4)
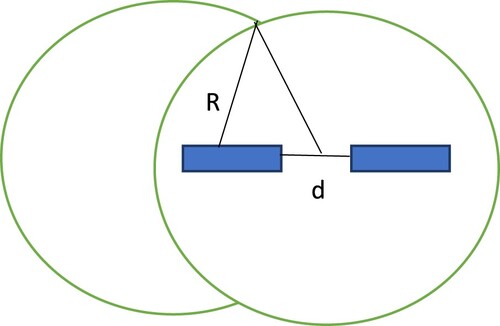
Communication area
Hence,
(5)
(5)
The overlapping area in can be used to calculate utilization. If the intersecting region is substantial, there is a decent possibility that the group will be within scope for some time and that notifications from neighbouring clusters will be s actually. As a result, use is low, whereas use value for less interpenetrating area is high.
3.1.3 Metric for validity (Val)
It is the ratio of time left to time left plus data transmission time. The looking to transfer time is the estimated time necessary to travel among both two CHs. If the deadline is close to reaching, the packet will almost certainly be lowered. As a result, avoiding congestion problems will be a top priority.
(6)
(6)
3.1.4 Distance measurement (Dis)
It entails the separation of CHs. The largest the distance between them as possibility of disassociation; as a direct consequence, more special attention is given. Low distance between them increases the likelihood that they will connect. Consequently, a lower priority is given.
3.1.5 Direction metric (Dir)
It has 2 choices: (1) Dir = 0 indicates that two clusters are starting to move toward one another, increasing the likelihood of them connecting and thus assigning a lower priority; and (2) Dir = 1 indicates that two segments are shifting away from one another, reducing the probability of them connecting and thus allocating a greater priority.
(7)
(7)
(8)
(8)
Eqs 2 through 7 are used to calculate Equation 8. According to Equation (8), Dynamic component or text priority, which is inversely proportional to dynamic factor, is inversely proportional to Vel, Use, and Val. Val is assigned a value of one because if Val had a value of zero, the dynamic component would be infinite. Because Dis cannot be zero, a value of 0 for Dis indicates that an accident has occurred. Dir = 0 indicates that two groupings are getting closer, reducing the spacing between them and increasing the probability that they'll link, resulting in a lower priority. This is the assumption because Dis is inversely related to the situation makes. Dir = 1 indicates that two clusters are shifting apart, raising the distance between them, increasing the likelihood of a disassociation and rising the priority.
GPS and the routing algorithm provide all of the data needed to calculate dynamic factor. Because we know the message size, static component, and dynamic component, special attention is determined and decided to add to the incoming packets.
3.2 Scheduling message unit (SMU)
Because of the network's unique features, message time management is a difficult task. Because of a deliver value dispatcher, the VANET system is reliable and secure. Messages are delayed and forwarded to the supervision and customer support channel people queuing of the text work schedules unit.
Using meta-heuristic techniques: The tabu algorithm based is used for dynamic scheduling in this work, hence the name TaSch. The tabu search algorithm is one of the most effective meta-heuristic methods. The TaSch algorithm is based on message priority, jitter, and delay. Based on these factors, TaSch quickly determines a nearly ideal network solution, lowering message delivery postponement and jitter. The following formula is used to calculate jitter and delay:
(9)
(9)
(10)
(10)
The ith packet's waiting time is denoted by Ri. Si is the time signature of the ith packet (when data was transmitted), and Ri-1 is the entrance time of the I (1)th packet. The utilizing of the (i-1)th packet is represented by Si-1. J(i) represents the ith packet jitter, J(i 1) represents the ith message jitter, and D(i 1, I) represents the difference between the ith and (I,1)th message delivery times.
3.3 Proposed source base routing (SBR) using ECC-ACO
To route packets of data among both source and destination, the proposed ECC-ACO employs the source-based routing (SBR) concept. The SBR can be used by the sender of a packet to specify the pathway that the datagram must take. In SBR, the source vehicle appears to contain the entire packet routing path. To reach its destination, the packet makes use of its header. The primary concept of SBR is the accumulation of path data in the incoming packets. The SBRACO is a meta-heuristic optimization influence on the implementation caused by ant behaviour in nature. Ants (special packets) are used in SBRACO to find the best solution to a problem.
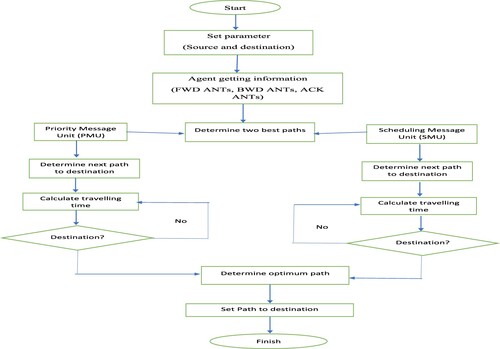
Every ant colony in each nest contains millions of ant colonies, which is the basic analogue of the ACO. The ants in the colony leave the nest in search of an ant source. Ants in the nest take different paths, and if they do, they leave behind pheromones, a type of hormone. Ants are attracted to heuristic information material left alone, and by having left their own pheromone behind, more ants may follow the same trail. The surviving ants are instructed to take a faster route. The compressive strength of the route decreased as the implantable cardiac number of particles began to diminish (evaporate) over time. The SBRACO algorithm employs heuristic information downpayment and continuously updates designs to improve the track with heuristic data deposits depending on outlet temperature. Starting point paths are used to instruct and facilitate the ants of ACO in trying to transfer network packets along the shortest path in the proposed model, which uses SBRACO to decide the fastest way between both the source and destination based on resonance and separation relative density. The flow diagram in Figure depicts the optimized path taken by the SBRACO heuristic.
Step involved in the proposed deals PMU and SMU.
Vehicles are randomly deployed in promiscuous mode before operating in forwarding state to generate their one-hop location information.
Using their Neighbour List (NL), vehicles in PMU and SMU determine how far apart they are from their neighbours.
The determined Ds are then saved by the vehicle in its routing tables. The SBACOA includes methods for planning on getting, route response, data transmission, and route maintenance.
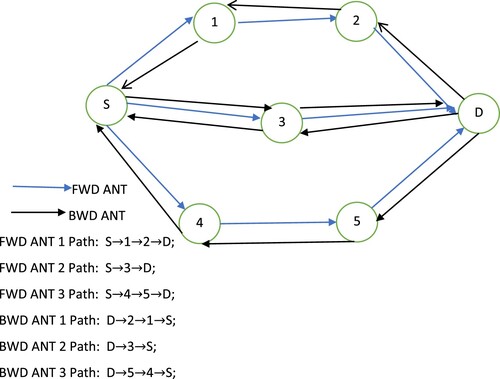
It stands for the discovery of the route. The goal of this procedure is to identify a reliable path to the desired location. The source requests that F-ACO create FWD ANTs using its NL. To begin their journey, FWD ANTs follow the NL of the source, and to get to their destination, they follow the NL of their neighbours. The route reply will be active if the neighbour is the destination. If not, it will forward FWD ANTs according to its NL. According to the pheromone deposit concept, FWD ANTs manage the route cache and scatter pheromones along their path as they move.
Destination makes it possible for this procedure to send BWDANTs to the source that include route data. The BWDANTs condense pheromone based on the signal summation model and update signal on pathways based on the signal update model as they get closer to the source.
In order to determine the least path, it applies the PSSV method based on BWDANTs data. In order to transmit and acknowledge data via the least path, D-ANTs and ACK-ANTs are developed throughout this procedure.
3.4 SBRANT optimization
The Agent Ant (A-ANT), Forward Ants (FWD-ANTs), Backward Ants (BWD-ANTs), Data Transfer Ants (D-ANTs), Acknowledgement Ants (ACK-ANTs), and Route Maintenance Ant are the main ants in the proposed scheme (R-ANT). The path discovery method employs A-ANT and FWD ANTs. The modifier employs BWD ANTs. The information transmission technique employs D-ANTs and ACK-ANTs. The construction method employs the R-ANT.
3.4.1 Route exploration
When an intermediate node has data to communicate and the previously used path is obstructed, the same vehicle employs A-ANT to generate a large number of FWD ANTs in order to locate a new path. FWD ANTs are initiated and produced by A-ANT, also recognized as Queen Ant (Q-ANT). All types of ants can be produced by any of the suggested system's vehicles. The Neighbour List (NL) of the generated vehicle influences how FWD ANTs are produced. Each vehicle in the receiving state has the NL imprinted on it. The network device of the vehicle contains NL, a list of its one-hop neighbour nodes.
In the route discovery method, shows how the FWD ANTs move between intermediate cars to get at their destination. Each intermediate vehicle completes the following objectives while receiving FWD ANT.
Table
3.4.2 Route response
BWD ANT is created to send the route data back to the starting point during in the routing path if the vehicle is at the region or has a viable path to the destination. The trail is transported from point B to point A by the BWD ANTs. The FWD ANTs’ journey is highly susceptible to evapotranspiration. Depending on the distance, old algorithmic knowledge value, and rate of evaporation, BWD ANTs can collect identical or distinguishable amounts of secretion while attempting to move in opposite order. The heuristic information automatic update model is used by BWD ANTs to deposit signal. The supercomputing equation used among BWD ANT to keep updating the substance is depicted in Equation 8.
(11)
(11)
where
BWD ANT has deposited a new signal amount.
represents the amount of old signal on the same periphery.
symbolizes the evaporation process. D refers to the distance among both vehicular X and Y in 1/D, and 1 is a continuous function.
Equation 12 depicts the computational formula used by BWD ANT to calculate the sum of heuristic information values.
(12)
(12)
where
represents the sum of signals from transmitting data.
indicates the amount of signal collected from beginning to end.
Until the data transmission is finished, all BWD ANTs that are received are held in the source. With the aid of the sequence number, the intermediate vehicle discards any BWD ANT that was received twice or in triplicate (SEQnum).
Table
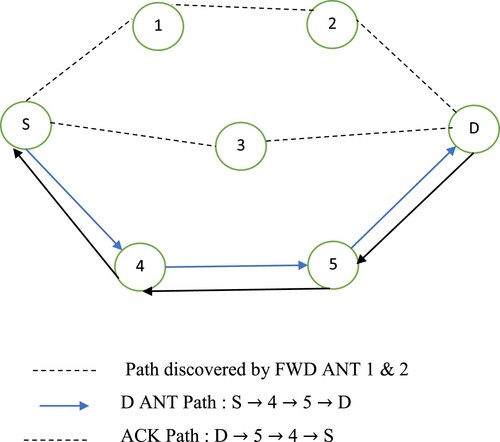
3.4.3 Data transmission
D-ANTs transmit information from source to destination in the data transfer method. To recognize successful data communication, ACK-ANT was used. The source needs to initiate the path selection method to begin transmission of data. The reference extracts passageways (RRec) from BWD ANTs in order to perform path selection. The route discovery algorithm determines the shortest route. When a transfer of data begins, the source makes a copy of the D-ANT header using the shortest route determined. The D-ANT header includes the selective route that must be followed to get from the source into the destination. The D-structure ANTs are depicted in Equation 13.
(13)
(13)
where ANTtype, ADDsrc, and ADDdest denote the identity of the ant type, source, and destination. The sequence produced for D-ANT is denoted by SEQnum. The route cache is RRec, and the statement reflects the material that needs be sent to a desired location. The location vehicle generates ACK-ANT to notify the source that the packet of data was successfully received. The framework of ACK-ANT is represented by Equation 14.
(14)
(14)
where ANTtype, ADDsrc, represents the ant type and the source individuality. The data packet generated for ACK-ANT is SEQnum. RRec is the route cache. The Orginal ADDsrc represents the location vehicle's contact information.
depicts transfer of data that use the shortest path, in which D ANT transports data as well as ACK-ANT recognizes effective data transmission.
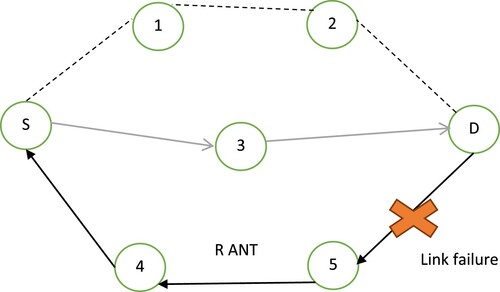
3.4.4 Route survival
The F-ACO effectively continues to maintain broken connections. Because of their high mobility, intermediate vehicles deviate from the established path, resulting in link failure. We consider vehicle-to-vehicle (V2 V) communication in the proposed scheme. Both the sources and destinations vehicles are starting to move forward in a V2 V transaction. As long as they are implicated in the discovery of the route (data transmission process) or the radio communications link with the intermediate cars is retained, the reference, popular tourist destination, and transition phase vehicles are all valid while trying to move forward. The citation, tourist attraction, and connections in a network lose their validity when they deviate from the predetermined route. As shown in , a new route is formed as a result of a failed link.
3.5 Path selection at source vehicle (PSSV)
PSSV's primary aim is to find the quickest distance with the least amount hops. The source vehicle initiates the PSSV after having received the BWD ANTs. The PSSV determines the required path, scent gland, and reactive routing's choice based on the hop count and secretion total sum. The PSSV reads the routing information and shortest path variables in addition to the hop count and heuristic information variables.
The Route maintenance of a link failure, the R-ANT can start in a nearby parking lot. R-ANT is destiny all along the current path in a downlink direction to notify the starting point vehicle of a link failure node. While towing R-ANT, the transitional vehicles simply remove their route cache memory of a previous route. The source vehicle instantly clears the failure route's route cache. The route selection procedure is then repeated by the source node to pick the backup and restore path.
Table
3.6 Evaluation parameters
we’re attempting to evaluate the very next performance measures in order to determine the impact of our suggested model. The following formula provides the performance metrics used to analyze the findings.
Packet Delivery Ratio (PDR):
The amount of receiving to send packet data is known as PDR. The system is more effective when the Delivery ratio is higher. The following equations can be used to determine PDR:
(15)
(15)
Throughput:
This is the average amount of data received packets by the destination per second. As a result, the following formula can be used to determine throughput:
(16)
(16)
End To End Delay:
The time it takes parcels to travel from sender and the receiver to transmitter and receiver on median wage. To determine the average delay, use the given equations:
(17)
(17)
4. Packet loss rate (PLR)
PLR is the total amount of packets sent from an origin but not did receive at their desired location. Eq. 18 is used to determine the PLR.
(18)
(18)
For all scenarios, PLR is determined by calculating using requirements such as data packets sent from the provider and results of research conducted at the preferred destination. In all scenarios, the sum of information conveyed from the starting place and packets received at the preferred destination is a mathematics measurement.
4. Experimental setup
The performance of the ECC-ACO is especially impressive in comparison to the F-ACO, AODV, and AntNet in the exploratory results table. To simulate the proposed and existing procedures, the MATLAB simulation tool has been used.
The F-ACO and AntNet procedures are based on a biology-based algorithm for ant colony optimization (ACO). The proposed protocol also employs the biological algorithm. In the proposed ECC-ACO, the enhanced SBRACO is used to determine the quickest distance using the starting point outbound notion and the range numerical model. The AODV protocol is used to forward demand. To guide packets, the proposed scheme employs starting point routing theory. Source-based forwarding is a subset of on-demand routing. Because of these considerations, the F-ACO, AntNet, and AODV procedures are good alternatives to our recommended ECC-ACO.
Throughput
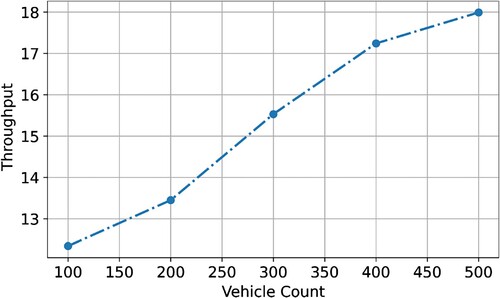
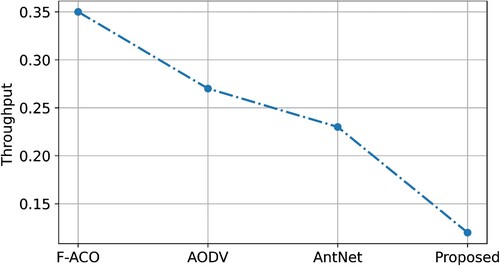
The proposed ECC-ACO protocol outdoes the other four procedures in terms of throughput. To avoid stagnation, ECC-ACO employs a modified heuristic information update model. It prevents stagnation by selecting a route based on a node parameter known as distance. Because of its high convergence rate, low ant time consumption, and use of the quickest route without relatively stable conditions, the proposed ECC-ACO improves high throughput in all three route circumstances (0.5–0.35 ms/s). In all three route scenarios, the average throughput was 17.99 kbps for ECC-ACO, 12.34 kbps for F-ACO, 15.53 kbps for AODV, and 17.24 kbps for AntNet. and depict the throughput for numerous vehicles under significantly variable road circumstances.
Routing Overhead (RO)
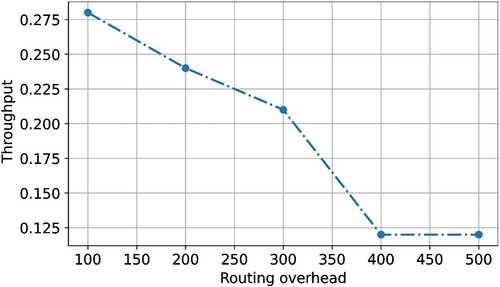
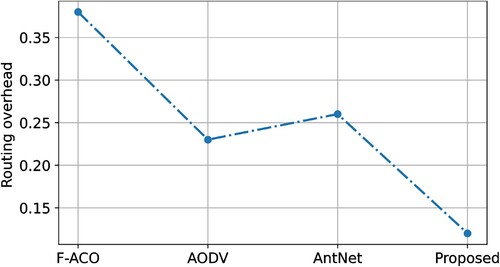
The comparison of FANT, AntNet, and AODV, the suggested methodology has lower latency. The proposed ECC-ACO forbids blind transmission of network congestion control messages, and the minimum distance is completed in a controllable environment. In the proposed ECC-ACO, routing protocol control packets rely on the node's NL to continue their journey. The allowed broadcast of data forwarding is purely tied to NL, which limits the ant's search time and improves the overhead efficiency of the proposed protocol. FANT's and ACO use a large number of control packets in the routing protocol to store information about the entire colony. Control messages were overused by participants who agreed. The control packet in the proposed scheme contains less information. Initiatives have been taken to create a single routing path, which can cause significant control overhead in AODV. In terms of overhead, the suggested ECC-ACO outperforms other protocols in all three road circumstances. The proposed ECC-ACO has 0.28%, the F-ACO has 0.12%, the AODV has 0.21%, and AntNet has 0.24%. and show the overhead routing for various vehicle types for road scenarios.
Packet Loss Rate
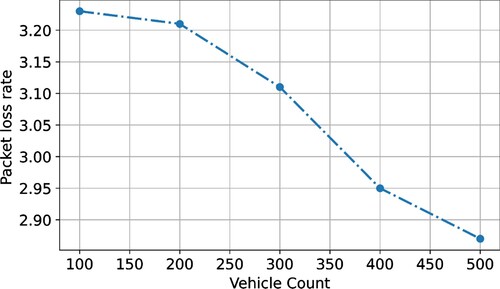
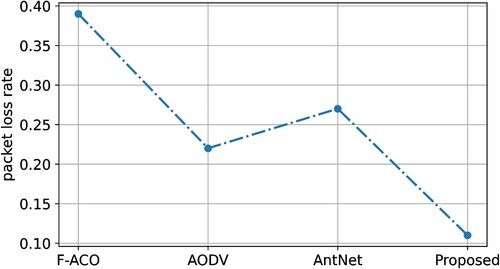
By using a constant transmission speed, the proposed ECC-ACO avoids link congestion. The ECC-ACO selects the shortest path with the fewest hops and the lowest data transfer cost. The proposed scheme is distinguished by its short communication range. Explanation routing is used in the proposed protocol to avoid network congestion. To reduce network congestion, the F-ACO maintains reliable paths. The F-ACO has a lower packet loss rate than AntNet and AODV. Interconnection and node-level specifications in F-ACO prevent packet loss. Inconsistent paths and AODV's relatively long delay cause network congestion. In ARA, ACO link stabilization is poor, and AntNet's ACO experiences packet loss when vehicle density is high. The proposed scheme establishes a constant route with a low hop count between source and destination. The route with the shortest interaction distance avoids packet delays. The use of PMU and SMU to select small distance edges improves the ECC-ACO organizational framework. The non-congested quickest route in all three road circumstances always is built using tiny length edges and a low number of hops (100–500 km). The proposed ECC-ACO had a PLR of 2.85%, the existing F-ACO had a PLR of 3.23%, AODV had a PLR of 0.321%, and AntNet had a PLR of 2.85%. and show that the packet loss ratio for various vehicle circumstances ranges from 100 to 500 kilometres.
Packet Delivery Rate
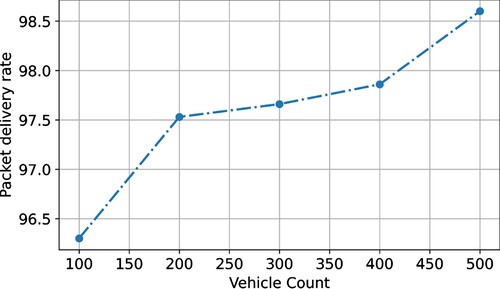
In comparison to F-ACO, AODV, and AntNet, the suggested ECC-ACO has a higher packet delivery rate. To achieve this improvement, the shortest distance in ECC-ACO with the fewest hops and the lowest actual cost is selected. ECC-PMU ACOs and SMU assist in choosing the lowest-cost option, and a citation-enhanced ACO directs packets to take the least path with the fewest hops. Path congestion reduces the delivered packet ratio. To address the issue of stagnant model growth, the proposed ECC-ACO uses a modified heuristic information order to update the recurrent parameter-based framework known as distance. The signal updating approach overcomes the immobility issue by selecting a path based on heuristic understanding and appreciation. The proposed approach continuously maintains the dependable least path in all three vehicle circumstances to increase the packet delivery ratio. The scheduled ECC-ACO, F-ACO, AODV, and AntNet road situations had average PDRs of 98.6%, 96.3%, 97.53%, and 97.86%, respectively. depicts the packet delivery rate for situations involving 100 and 500 kilometres of travel for different vehicle revisions.
End To End Delay
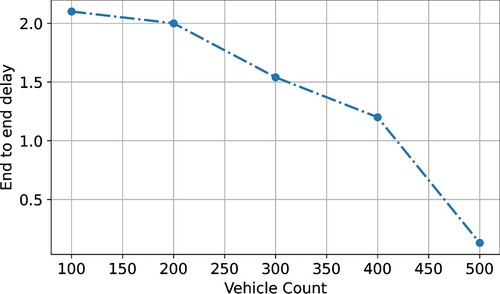
End-to-end delays grow in proportion to the total number of vehicles. The developed scheme completes tasks more quickly than just the earlier methods. The proposed ECC-ACO reduces packet delay by taking the least path with the fewest hops and no congestion. The PMU, SMU, and a source-based ACO in the proposed ECC-ACO direct packets to take the path with the least amount hops. Congestion is avoided by maintaining a constant transmission speed. In the proposed model, in the absence of an ACK, the packet forwarding ant shall notify the reference to use the path method of selecting rather than the packet forwarding technique. Without launching a destination node method, the path selection procedure acknowledges the next quickest route. The average end-to-end time delay measured for all three road circumstances is 2.1 s for suggested ECC-ACO, 0.13 s for F-ACO, 1.54 s for AODV, and 2 s for AntNet. depicts the end-to-end latency for 100–500 km vehicle scenarios with different vehicle different variants.
Comparison With Existing Techniques
For packet routing, the proposed ECC-ACO seeks the least path with the fewest hops. When particularly compared to the F-ACO, AODV, and AntNet protocols, the proposed ECC-ACO speeds up the ant's search time and accelerates convergence. Additionally, it prevents packet blind transmission, provides efficient formulating, and prevents packet stagnation. Congestion control's improved ACO avoids the global optimal problem. To handle route failures more successfully than existing protocols, ECC-ACO has implemented a new mechanism for route maintenance. ECC-ACO transmits data in the shortest possible path with the fewest hops, which improves all aspects of its achievement ().
Table 1. Comparison with existing techniques.
When a new message reaches the event-driven queue, rather than the entire waiting line, it is quickly rescheduled, improving VANET results. The modelling outcomes show that the proposed ECC-ACO outperforms FANT, AODV, and AntNet in terms of throughput, end-to-end delay, routing overhead, and packet delivery ratio (PLR).
5. Conclusion
To increase bandwidth in VANETs, this paper proposes ECC-ACO, a novel routing protocol. The proposed ECC-PMU, ACO's SMU, and SBACO combination speeds up convergence, reduces ant search time, prevents packet blind broadcasting, processes packets faster, and avoids stagnation issues. PDR and throughput are increased in ECC-ACO by using the shortest path with no economic decline, rapid packet sorting, and rapid fast convergence. The proposed model is made up of two components: the prioritization message unit (PMU) and the scheduling message unit (SMU). PMU assigns a priority to messages based on their type. Messages are classified into two types: security messages and non-secured messages. Messages are rescheduled in SMU based on their priority before being sent into the command and provider channels. When a new message arrives, the event-driven queue, rather than the entire queue, is quickly rescheduled, which improves VANET performance. According to the simulation results (PLR), the proposed ECC-ACO outperforms F-ACO, AODV, and AntNet in terms of throughput, end-to-end delay, routing overhead, and packet delivery ratio.
Disclosure statement
No potential conflict of interest was reported by the author(s).
References
- Ghafari A. Hybrid opportunistic and position-based routing protocol in vehicular ad hoc networks. J Ambient Intel Human Computer. 2020;11(4):1593–1160. doi:10.1007/s12652-019-01316-z
- Abassi R, Ben Chehida Douss A, Sauveron D. TSME: a trust-based security scheme for message exchange in vehicular Ad hoc networks. Hum Cent Computer Inf Sci. 2020;10(1):1–19. doi:10.1186/s13673-020-00248-4
- Kumar DNSR, Barani S. (2020). Epidemic and transmission priority-based data dissemination model in vehichular adhoc networks (VANETs). Peer-to-Peer Netw Appl.
- Taleb T, Benslimane A, Letaief KB. Toward an effective risk-conscious and collaborative vehicular collision avoidance system. IEEE Trans Veh Technol. 2010;59:1474–1486. doi:10.1109/TVT.2010.2040639
- Saraereh OA, Ali A, Khan I, et al. Interference Analysis for Vehicle-to-Vehicle Communications at 28 GHz. Electronics (Basel). 2020;9:262), doi:10.3390/electronics9020262
- Harding J, Powell G, Yoon R, et al. Vehicle-to-vehicle communications: readiness of V2 V technology for application; technical report; United States National Highway Traffic Safety Administration: Washington, DC, USA, 2014.
- Nyerges Á, Tihanyi V.. Trajectory planning for automated vehicles– A basic approach. In Proceedings of the vehicle and automotive engineering (VAE 2018), Miskolc, Hungary, 23–25 May 2018; pp. 403–412.
- Cooper C, Franklin D, Ros M, et al. A comparative survey of VANET clustering techniques. IEEE Commun Surv Tutor. 2016;19:657–681. doi:10.1109/COMST.2016.2611524
- Haider S, Abbas G, Abbas ZH. VLCS: A novel clock synchronization technique for TDMA-based MAC protocols in VANETs. In Proceedings of the 4th International Conference on Emerging Trends in Engineering, Sciences and Technology (ICEEST 2019), Karachi, Pakistan, 10–11 December 2019; pp. 1–6.
- Mohammad SA, Rasheed A, Qayyum A. VANET architectures and protocol stacks: A survey. In Proceedings of the International Workshop on Communication Technologies for Vehicles, Berlin, Germany, 23–24 March 2011; pp. 95–105.
- Group IW. IEEE guide for wireless access in vehicular environments (WAVE)-Architecture; 1609.0-2013; IEEE: Piscataway, NJ, USA, 2014.
- Haider S, Abbas G, Abbas ZH, et al. P-DACCA: A probabilistic direction-aware cooperative collision avoidance scheme for VANETs. Future Gener Comput Syst. 2020;103:1–17. doi:10.1016/j.future.2019.09.054
- Haider S, Abbas G, Abbas ZH, et al. LWE-CPPA: A scheme for secure delivery of warning messages in VANETs. Int J Ad Hoc Ubiquitous Comput. 2019;34:17–185.
- Haider S, Abbas G, Abbas ZH, et al. DABFS: A robust routing protocol for warning messages dissemination in VANETs. Comput Commun. 2019;147:21–34. doi:10.1016/j.comcom.2019.08.011
- Abbas G, Abbas ZH, Haider S, et al. PDMAC: A priority-based enhanced TDMA protocol for warning message dissemination in VANETs. Sensors. 2020;20:45), doi:10.3390/s20010045
- Khaliq KA, Chughtai O, Shahwani A, et al. Road accidents detection, data collection and data analysis using V2X communication and edge/cloud computing. Electronics (Basel). 2019;8:896), doi:10.3390/electronics8080896
- Farooq SM, Hussain S, Kiran S, et al. Certificate based security mechanisms in vehicular ad-hoc networks based on IEC 61850 and IEEE WAVE standards. Electronics (Basel). 2019;8(96):21), Khan, U.A.; Lee, S.S. Multi-Layer Problems and Solutions in VANETs: A Review. Electronics 2019, 8, 204.
- M. Adnan et al., “On the design of efficient hierarchic architecture for software defined vehicular networks,” Sensors 2021, 21, 1400, pp. 1–18, 2021, doi:10.3390/s21041400
- Bai S, Oh J, Jung J-I. Context awareness beacon scheduling scheme for congestion control in vehicle-to-vehicle safety communication. Ad Hoc Network. 2013;11:2049–2058. doi:10.1016/j.adhoc.2012.02.014
- Taherkhani, N., & Pierre, S. (2012). Congestion control in vehicular ad hoc networks using meta-heuristic techniques. In Proceedings of the Second ACM International Symposium on Design and Analysis of Intelligent Vehicular Networks and Applications (pp. 47–54). doi:10.1145/2386958.2386966
- Bouassida MS, Shawky M. (2008). On the congestion control within VANET. In 1st IFIP Wireless Days, WD’08 (pp. 1–5).
- Guan B, Zhao Y, Li Y. An improved ant colony optimization with an automatic updating mechanism for constraint satisfaction problems. Expert Syst Appl. 2021;164:114021), doi:10.1016/j.eswa.2020.114021
- Maheshwari P, Sharma AK, Verma K. Energy efficient cluster-based routing protocol for WSN using butterfly optimization algorithm and ant colony optimization. Ad Hoc Netw. 2021;110:102317), doi:10.1016/j.adhoc.2020.102317
- Sales Mendes A, Jiménez-Bravo DM, Navarro-Cáceres M, et al. Multiagent approach using lorawan devices: an airport case study. Electronics (Basel). 2020;9(9):1430), doi:10.3390/electronics9091430
- Ramamoorthy R, Thangavelu M. An improved distance-based ant colony optimization routing for vehicular ad hoc networks. Int J Commun Syst. 2020;33(14):e4502), doi:10.1002/dac.4502
- Sinwar D, Sharma N, Maakar SK, et al. Analysis and comparison of ant colony optimization algorithm with DSDV, AODV, and AOMDV based on shortest path in MANET. J Inf Optim Sci. 2020;41(2):621–632.