?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.ABSTRACT
The nuclear security has been considered for the industrial terrorism preventions. In the fourth industrial revolution era, our life related systems are connected each other, which means the internet based networking is spread anywhere. It is suggested to make the modeling for the nuclear security in cyber information where the computer hacking is one of major incidents. The data and information could be transferred by the intruder or terrorist in which the intentional data changes could be happened. In the modeling, the system dynamics method is used for the verifications of protocol. The simulations for Implement and Maintain are performed where the cyber security is stabilized after 40th month considering the slope of the Maintain graph, which reflects the lowest point in Implement graph. The protocol for the for modified digital nuclear power plant data network (MNPPDN) is constructed.
1. Introduction
For the extensive security of nuclear facilities, the nuclear security has been considered as the aspect of the industrial terrorism preventions. There have been several cyber cases in the nuclear sites, which are in [Citation1]. Considering the fourth industrial revolution era, our life related systems are connected each other, which means the internet based networking is spread anywhere. For example, in the case of the cyber terrorism on South Korean nuclear power plant (NPP), the internet protocol (IP) address was a city in China where there were some espionages of North Korea [Citation2]. So, it has been doubtful that the attack was committed by the nation. The civilian internetworking could be used for the attacking to the industrial facilities, especially the nuclear energy stuffs. This is different from the conventional terrorism in which the direct bombing or intentional suicide assault could be happened. The cyber terrorism is not seen easily. However, the consequences have been gradually displayed to the public and wide ranged area. In the results, the effects are much severer than the physical attacks.
Table 1. Selected list of cyber nuclear incident
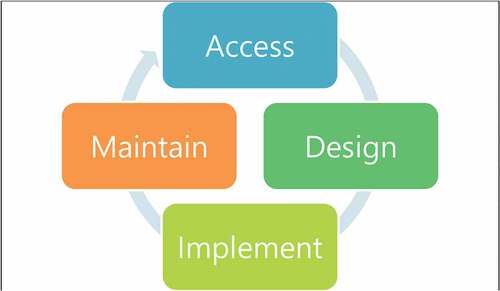
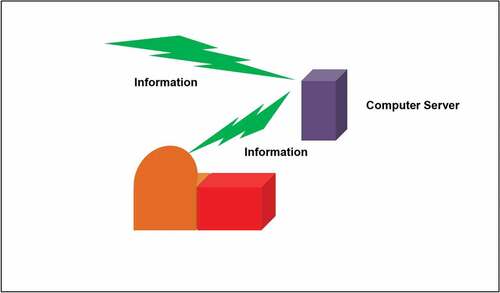
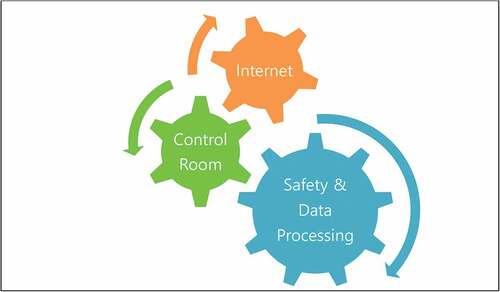
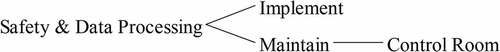
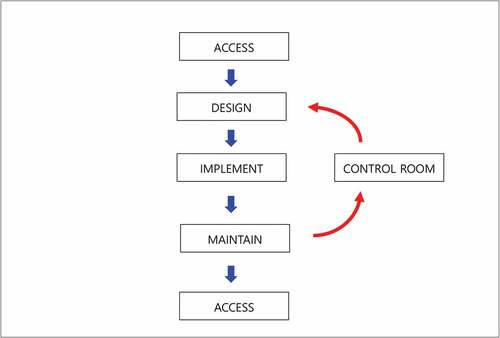
It is important that the dynamical investigation of the cyber world could be the solution of the cyber terrorism. shows the lifecycle of cyber security [Citation3] where the general cyber sequences are shown. As it is seen, the assess is the first step and it is done until the maintaining of the internetworking systems. Using this algorithm, the applications to NPP should be performed. The simplified configurations could be constructed. describes for the relations for the information networking systems on NPP site where the onsite computer server is connected to the reactor building. So, the information traffic should be considered in the nuclear cyber security matters. For the real system application, shows the modified digital nuclear power plant data network (NPPDN) [Citation4] in which there are three critical factors as Internet, Control Room, and Safety & Data Processing. The control room of the plant is a central factor which combines the internetworking system and Safety & Data Processing such as the several safety injection systems and coolant-based systems. Although the reactor building and the steam supply system could be disconnected in the normal time for the security reasons, it is needed to connect for a while to find out the data for the nucleonic processes in the reactor and its related nuclear fuel systems.
There have been several nuclear cyber security studies until now. Two things of security of cyber-physical assets were done as the access to control and to mask inputs [Citation5]. Lee et al. worked for the Intrusion Tolerance-based Cyber Security Index (InTo-CSI) which means a reduction ratio of probability of cyber-attack damages [Citation6]. In addition, the general analysis of the nuclear terrorism was done where the eight possible cases were introduced in the NPPs [Citation7]. In addition, there were some analyses and studies for the nuclear security works [Citation7–17].
2. Method
It is suggested to make the modeling for the nuclear security in cyber information where the computer hacking is one of major incidents. The data and information could be transferred by the intruder or terrorist in which the intentional data changes could be happened. In the modeling, the system dynamics (SD) method is used for the verifications of protocol, which is a kind of nonlinear algorithm.
2.1. Cyber security
It is constructed by combining of the lifecycle of cyber security [Citation3] and NPPDN [Citation4]. This means that the nuclear system should consider the general cyber characteristics such as the assessing to the networking as well as the safety data and processing. This reflects the South Korean case happened by the civilian internet networking. Hence, the nuclear facility can be reflected to the general industrial environment.
2.2. System dynamics method
The SD is used for he modeling where the loop typed configurations are constructed, which was created by Dr. J. Forrester [Citation18] for the analysis of the nonlinear complex systems in the social humanities as well as technological matters. This includes several methods with time step, feedback, and level algorithm which means calculation interval, backward event flow, and data accumulation, respectively.
2.3. Modeling
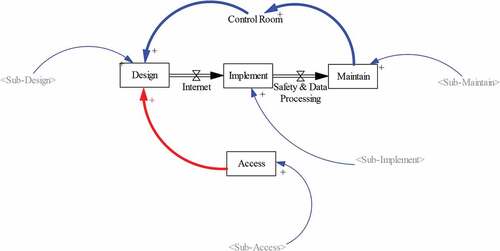
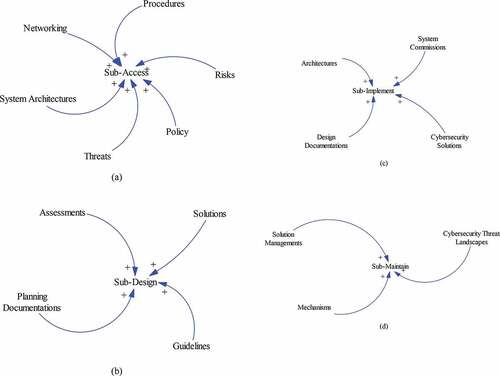
The modeling is done by the SD method with designed variables. shows the modeling for the modified digital nuclear power plant data network (MNPPDN), which is constructed by Vensim code system [Citation19]. The major events of Control Room, Internet, and Safety & Data Processing are shown as the variables, which are embedded of the lifecycle of cyber security as the Access, Design, Implement, and Maintain. These four factors have subvariables that are in . There are described as the sub-elements of Sub-Access, Sub-design, Sub-Implement, and Sub-Maintain. For example, there are Procedures, Risks, Policy, Threats, System Architectures, and Networking in Sub-Access. The other elements are seen in . For the connectivity for each variable, describes the causal loop for the Safety & Data Processing where the connectivity of cyber security is seen for MNPPDN.
shows the numeric values in the events. In the case of Access, the random numbers produced between 0.0 and 1.0 are compared by the designed number of 0.5. If the generated random number is lower than 0.5, it is 0.0. Otherwise, it is 1.0. In Implement, the value is accumulated from 1.0. So, it is shown in ). Similarly, in ), the values are accumulated.
Table 2. List for events related to the cases
Therefore, it is possible to apply to this modeling using the SD method where the time step is variable following the operator’s idea. In addition, the feedback algorithm in SD is connected from third step to second step of lifecycle of cyber security in . In the loop, the control room of NPPDN is combined. So, using the feedback loop of the general cyber security and nuclear industry aspect of NPPDM, the modeling is constructed as follows,
In addition, the level logic of SD is applied as the accumulation in Implement and Maintain. In case of Implement,
In case of Maintain,
In , the Safety & Data Processing are connected to Implement and Maintain, which is called the causal loop. This means the cause and result are connected by the data flow for the designed algorithm. The SD methods are used by the designed scenarios in this study.
2.4. Multiple plants
For the parallel NPPs where the data are connected by the networking, this could be shown as follows,
For the summations of the data,
The values are notated for the Implement or Maintain. If there is another interested value, it is possible to be constructed.
3. Results
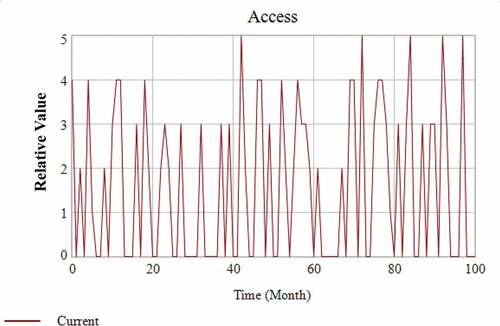
shows the results for simulations in Access where the Boolean value quantifications are performed. The plant operations are performed during 100 months when the cyber risk would be affected by the designed modeling in this study. As it is said above, the SD-based analysis is simulated for the quantification. So, the highest one is 5 as the dimensionless value in 42nd, 72nd, 84th, 92nd, and 97th months. This is the quantified values of the modeling and there is no specific physical meaning. So, the vertical axis shows the relative value without dimension. There is the related event as Sub-Access which includes Procedures, Risks, Policy, Threats, System Architectures, and Networking. This kind of method is done in Design, Implement, and Maintain which include Sub-design, Sub-Implement, and Sub-Maintain, respectively.
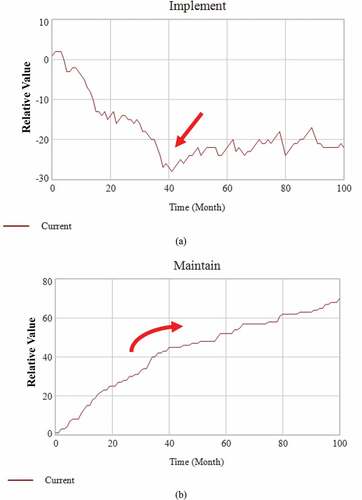
) has the simulations for Implement and Maintain where the minimum one is in 41st month of Implement. Otherwise, the slope of increasing is lower around 40th month of Maintain in ). In , the vertical axis shows the relative value without dimension. This means the cyber security is stabilized after 40th month during the plant operations considering the slope of the Maintain graph in ), which reflects the lowest point in Implement graph of ). shows the protoco 4l for the MNPPDN where the newly modified data networking for NPPs is constructed.
4. Conclusions
The protocol for the nuclear cyber security is investigated for the nuclear facilities where the NPP is one of major goals of the study. NPP is vary vulnerable to Internet networking, because the information is connected by the networking lines. Furthermore, in this fourth industrial revolution era, the cyber world has been considered as the other kind of community. So, the new sort of the method to manage the computer-based networking should be refined for blocking possible terrorism. It is shown of the importance of this study as follows:
The nuclear security is investigated.
Nonlinear algorithm is applied to the cyber security.
Dynamical modeling is quantified for the industrial systems.
Security is quantified by the SD method.
The first step of the protocol is to manage the information in this study. So, the SD used loop-type modeling is very effective to construct the system manuals. Although the government needs to make the protocol, it is necessary to revise the original protocol where the modeling study should be done, because the terrorism types could be changed by the circumstances around the potential terrorists. Hence, the IP address can give the information of the terrorist like the case of the South Korean incident where one city of China was discovered as the terrorist agitation point. This means the region of assessing to computer networking. The starting point of the modeling is to find out the IP location.
The protocol could be changed by the particular situation of the plant site. In the case of the political tension in a country, the potential possibility of the terrorism could be higher comparing to the other nations. The South Korean case can show the example of the regional instability that could make the attack with the quite and secret method such as the cyberspace based terrorism. The NPPs could be vulnerable to be invaded by internetworking strategies, because the data of the reactor should be transferred to the outside control facility. The reason the NPPDN includes the control room is that the data are connected to networking.
Using this study, a possible next terrorism to NPPs could be prohibited due to the dynamical simulations. The basic events could be changeable following several kinds of the specified cases. As it is said above, the international political status is one of the conditions to be managed by the modeling constructions. Furthermore, the natural state is another kind of the consideration, which can make the acceleration of terrorism, because a natural incident could effect on the plant stability. As it is known well, the NPPs around pacific rim region should be protected by the severe earthquake, volcanic movement, and some geological disasters. This needs to collect many data including the historic cases as the long-ranged cases. Usually, it is necessary to find a certain role to the natural events such as the cycle of the earthquake in a region.
For the future work, it is proposed to apply to the other industry such as the several plant sectors including oil or coal power plant. In addition, the traffic systems like the railroad and airplane could make use of the cyber security protocols. However, there the limitations for cyber terrorism control in wired system. For example, there was a case of attacking by the universal serial bus (USB) where a short-term employer used it carelessly when the computer virus invaded into the primary system in which the nuclear fuel and reactor core are equipped. Therefore, it is needed to investigated on maintenance situations of the cyber security much more.
Disclosure statement
No potential conflict of interest was reported by the authors.
References
- NTI. References for cyber incidents at nuclear facilities. Washington, DC (USA): Nuclear Threat Initiative (NTI); 2015. Available from https://www.nti.org/analysis/tools/table/133/
- Kwaak JS North Korea blamed for nuclear-power plant hack. The Wall Street Journal, New York (USA); 2015. Available from: https://www.wsj.com/articles/north-korea-blamed-for-nuclear-power-plant-hack-1426589324/
- Jadot F. Cyber security key to successful IIoT deployments, Industrial ethernet book. Schondorf (Germany): IEB Media GbR; 2018.
- USNRC. Cyber security assessment tools and methodologies for the evaluation of secure network design at nuclear power plants. Washington, DC (USA): U.S. Nuclear Regulatory Commission; 2012.
- Maccarone LT, D’Angelo CJ, Cole DG. Uncovering cyber-threats to nuclear system sensing and observability. Nucl Eng Des. 2018;331:204–210.
- Lee C, Yim HB, Seong PH. Development of a quantitative method for evaluating the efficacy of cyber security controls in NPPs based on intrusion tolerant concept. Ann Nucl Ener. 2018;112:646–654.
- Chen S, Demachi K. Proposal of an insider sabotage detection method for nuclear security using deep learning. J Nucl Sci Tech. 2019;56(7):599–607.
- Mitsutoshi S, Demachi K. Security by facility design for sabotage protection. J Nucl Sci Tech. 2018;55(5):559–567.
- Woo TH. Systems thinking safety analysis: nuclear security assessment of physical protection system in nuclear power plants. Sci Tech Nucl Instal. 2013; 473687.
- Woo TH. Nuclear safeguard protocol (NSP) construction of energy policy in nuclear power plants (NPPs) for secure power production. Energy Sources Part B Econ Plan Pol. 2015;10(1):91–102.
- Woo T, Kim T. Technological assessment of national nuclear fuel cycle using transmutations of high-level nuclear waste (HLW). Ener Environ. 2012;23(4):587–598.
- Woo TH. Nuclear safeguard assessment in nuclear power plants (NPPs) using loss function with modified random numbers. Ann Nucl Ener. 2012;43:1–7.
- Woo T-H. Dynamical nuclear safeguard investigations in nuclear materials using analytic pair values. Ann Nucl Ener. 2011;38(9):1916–1923.
- Woo T-H, Lee U-C. Safeguard assessment in nuclear power plants (NPPs) operations using analytic hierarchy process (AHP) and production function. Ener Explor Exploit. 2011;29(3):337–356.
- Woo T-H, Lee U-C. Safeguard assessment for life extension in nuclear power plants (NPPs) using a production function. Nucl Engin Des. 2011;241(3):826–831.
- Woo T-H, Lee U-C. Safeguard management for operation security in nuclear power plants (NPPs). Ann Nucl Ener. 2011;38(2–3):167–174.
- Woo T-H, Lee U-C. Modeling of operational safeguard for power productions in the nuclear power plants (NPPs). Ener Explor Exploit. 2010;28(6):433–449.
- SDS. Vision for the field, system dynamics society (SDS). Albany (NY); 2018. https://www.systemdynamics.org/vision-for-the-field
- Ventana. Vensim PLE, version 7.2. Harvard (USA): Ventana systems, Inc.; 2015.