?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.Abstract
Since the existing tropical cryptographic protocols are either susceptible to the Kotov-Ushakov attack and its generalization, or to attacks based on tropical matrix periodicity and predictive behavior, several attempts have been made to propose protocols that resist such attacks. Despite these attempts, many of the proposed protocols remain vulnerable to attacks targeting the underlying hidden problems, one of which we call the tropical two-sided discrete logarithm with shift. An illustrative case is the tropical Stickel protocol, which, when formulated with a single monomial instead of a polynomial, becomes susceptible to attacks based on solutions of the above mentioned tropical version of discrete logarithm. In this paper we will formally introduce the tropical two-sided discrete logarithm with shift, discuss how it is solved, and subsequently demonstrate an attack on a key exchange protocol based on the tropical semiring of pairs. This particular protocol is compromised due to the existence of efficient (albeit heuristic) solution of the tropical two-sided logarithm problem, and this highlights the ongoing challenges in search of a “good” key exchange protocol in tropical cryptography.
1 Introduction
Tropical cryptography is a new and promising area that seeks to transform the traditional public key exchange methods in cryptography using tropical mathematics. Grigoriev and Shpilrain [Citation5] pioneered the use of tropical algebra as an alternative framework for cryptographic protocols. In particular, they developed a tropical version of Stickel’s key exchange protocol [Citation18], the original version of which had been previously compromised by Shpilrain [Citation16] using a linear algebra attack. We also note here that Stickel’s protocol appears to be a special case of a more general protocol studied by Sidel’nikov, Cherepnev, and Yashchenko [Citation17] in early 1990s.
One of the motivations for the development of tropical cryptography came from the non-invertible nature of matrices in tropical algebra. The scarcity of invertible matrices makes the tropical implementation resistant to attacks resembling the ones faced by the original Stickel protocol (such as described in [Citation16]). However, the tropical implementation of Stickel’s protocol has been attacked by Kotov and Ushakov [Citation8]. The Kotov-Ushakov attack was further generalized in [Citation11] where it was shown how to apply the same idea to other implementations of Stickel protocol based on matrix commutativity. This has prompted the exploration of alternative ideas beyond matrix commutativity in Stickel protocols to implement tropical cryptographic protocols.
In response, Grigoriev and Shpilrain [Citation6] proposed two protocols based on tropical semi-direct product, but one of them was shown to be invalid by Isaac and Kahrobaei [Citation7] and the other was successfully attacked by the same authors as well as by [Citation14] and [Citation12]. The underlying problem that was solved and led to compromising the protocol was the tropical one-sided discrete logarithm. Subsequently, several alternative tropical protocols have been proposed that do not rely on this problem or matrix commutativity. Notably, one such protocol is based on the tropical algebra of pairs, as presented by Ahmed, Pal, and Mohan [Citation1].
The main ideas of the present paper are to formulate the problem which we call the “tropical two-sided discrete logarithm with shift” and present some heuristic methods of solving it, and then, based on a reduction of the matrix algebra over the tropical semiring of pairs to the usual tropical matrix algebra, develop some attacks on the above mentioned protocol of Ahmed, Pal, and Mohan [Citation1] and demonstrate their efficiency and success rate. More specifically, the paper is organized as follows. In Section 2 we start with some preliminaries and basic definitions, particularly those related to tropical matrix periodicity. In Section 3 we present the tropical two-sided discrete log with shift problem and two heuristic algorithms to solve it, showing their efficiency and success rate. In Section 4 we recall the tropical semiring of pairs and the implementation of Stickel protocol suggested in [Citation1]. In Section 5 we cryptanalyze this implementation using the solution of the tropical two-sided discrete log with shift problem, and present some numerical experiments showing the efficiency and performance of the attacks. Our codes have been uploaded to GitHub.Footnote1
2 Preliminaries
In this section, we present some of the standard definitions in tropical matrix algebra, for most of this part closely following Butkovič [Citation3]. Note that we use the standard notation and
for most common index sets.
Definition 2.1
(Tropical Semiring and Tropical Matrix Algebra). We define the tropical/max-plus semiring as where traditional addition + and multiplication × are replaced by tropical addition ⊕ and tropical multiplication ⊗, respectively. These new arithmetical operations are defined by
and
for all
.
The tropical arithmetic operations are naturally extended to include matrices and vectors. In particular, the operation where
and
for
and
, is defined by
The tropical addition of two matrices
and
, where
and
for
and
, is defined by
The tropical multiplication of two matrices is also similar to the “traditional” algebra. Namely, we define for two matrices, where
and
, as follows:
Note that, despite introducing this tropical arithmetic, we will also quite often utilize the usual arithmetical operations to introduce concepts and explain arguments.
Definition 2.2
(Tropical Matrix Powers). For , the n-th tropical power of M is denoted by
, and is equal to
We now introduce elements of graph theory to define the upcoming concepts. We begin by defining the directed graph (or digraph) associated with A and recalling the definitions of cycles, strongly connected components and other related concepts.
Definition 2.3
(Digraphs, Walks and Cycles). The digraph associated with , where
for
, is the pair
, where
is called the set of nodes of G(A) and
is called the set of arcs of G(A).
A walk on GA can be defined as a sequence of nodes where each
for
is an arc. A closed walk is a walk that starts and finishes at the same node, and a cycle is any closed walk that does not contain any repeated nodes, except for the beginning node and the end node.
The tropical analogue of irreducible matrix can be now defined (closely following its classical prototype).
Definition 2.4
(Irreducibility). A matrix is called irreducible if GA is strongly connected, i.e., if for each
there exists a walk on GA whose starting node is i and end node is j. A is called reducible if it is not irreducible.
We now introduce the concept of a maximum cycle mean, which is the value of the cycle that has the greatest average weight. We then also introduce a special subgraph of G(A) called the critical digraph of A. Formal definitions are given below.
Definition 2.5
(Maximum Cycle Mean and Critical Digraph). For , the maximum cycle mean
is defined in the usual notation as
which is the same as
in the tropical notation.
By definition, a cycle that attains the maximum cycle mean is a critical cycle. The critical graph of A, denoted by is the subgraph of GA which consists of all nodes and arcs of GA that belong to the critical cycles. The nodes belonging to
and the arcs belonging to
are also called critical.
The matrix inverses in tropical algebra can be defined only for a limited class of matrices, but the analogue of is more convenient to define.
Definition 2.6
(Kleene Star and Tropical Identity Matrix). Let have
. The Kleene star of M is defined by
where I is the tropical identity matrix, whose all diagonal entries are equal to 0 and all off-diagonal entries are equal to
.
One of the key ideas of solving the discrete logarithm problems (or, more specifically, Problems 1–4 formulated below) is to use the ultimate periodicity properties of tropical matrix powers. Strictly speaking, 1) the ultimate periodicity (in the sense of Theorem 2.1) occurs with a certain shift, that is, instead of repeating themselves the powers get multiplied in the tropical sense by some scalar, 2) the ultimate periodicity does not occur for general square matrix A, but is guaranteed only under certain conditions which (at their best) only slightly generalize the irreducibility property. For simplicity, the ultimate periodicity theorem is stated below only for the irreducible case, close to the original formulation in Cohen et al. [Citation4].
Theorem 2.1
(Ultimate Periodicity of Tropical Matrix Powers [Citation4]). Let be irreducible and let
be the maximum cycle mean of A. Then for some natural numbers TA and γ we have
(1)
(1)
Below we will also use the more particular ultimate periodicity of the ith columns and the ith rows:
(2)
(2)
(3)
(3)
The ultimate periodicity gives rise to a number of important concepts, of which we will define the following one.
Definition 2.7
(Periodicity Transients). The smallest integer TA for which (1) holds or, respectively, the smallest integers and
for which (2) and (3) hold, is called the periodicity transient of (the tropical matrix powers of) A or, respectively, the periodicity transient of the ith column and the ith row of those powers.
Obviously, the periodicity transients of ith row and ith column can be much smaller than the periodicity transient of A, and this is particularly relevant in the case where (i.e., when i is a critical node of A). It is also known that, for
, the properties (2) and (3) take place also for general reducible matrices A. Below we will recall a particularly useful result due to Nachtigall [Citation13].
Theorem 2.2
(Ultimate Periodicity of Critical Rows and Columns [Citation13]). Let and k be a critical node on a critical cycle Z of length lZ. Then
and
.
To explain how to compute the critical rows and columns in the ultimately periodic regime, let us also present the following result, which is a variation of the weak CSR theorems of [Citation9] and can be seen as a slight simplification of [Citation12], Proposition 2.5.
Theorem 2.3
(Weak CSR Expansion [Citation9]). Let have
, and let Z be a critical cycle of A with length lZ. Then for some integer Tweak we have
where
is the remainder when t is divided by lZ and
, and BZ are defined by
where
(i.e., the Kleene star of
).
Combining Theorem 2.2 with Theorem 2.3 as well as with [Citation15] Corollary 3.7, we obtain the following result, which we will be using below in some algorithms:
Theorem 2.4
(CSR Formula for Critical Rows and Columns). Let have
, and let Z be a critical cycle of A with length lZ. Then for any
we have
This theorem can be utilized to solve the different forms of tropical discrete logarithm problems, which are summarized below.
Problem 1.
Given such that
for some
, find this t.
Problem 2.
Given , such that
for some
and
, find τ and
such that
.
Solution to Problem 1 was discussed in [Citation12] and further in [Citation10], and Problem 2 can be solved by similar methods. However, since it involves a scalar, Problem 2 typically has an infinite number of solutions, unlike Problem 1, whose solution is typically unique. Also note that one can pose a version of Problem 1, respectively Problem 2, with instead of
, which can be regarded as a transposition of Problem 1, respectively Problem 2, and can be solved similarly.
Let us now pose two other problems, which will be referred to as tropical two-sided discrete logarithm problems.
Problem 3.
Given such that
for some
. Find
such that
.
Problem 4.
Given such that
for some
and
. Find
such that
, where
.
An attempt to solve Problem 3 can be found in [Citation10], where it is observed, in particular, that the solution to this problem is in general non-unique. However, the number of solutions to this problem (unlike the number of solutions to Problem 4 is typically finite).
It is natural to solve the problems listed above by exploiting the ultimate periodicity properties of the tropical matrix powers or, in particular, by using the more precise information about those powers in the ultimate periodic regime as given, e.g., by the CSR decomposition. Let us note, however, that this approach has some limitations. Firstly, tropical matrix powers are not ultimately periodic in general (see, e.g., [Citation3]), and both Alice and Bob can opt to use matrices whose powers are not ultimately periodic, which offers them some protection against attacks based on ultimate periodicity of entire tropical matrix powers. Secondly, the periodicity transient of tropical matrix powers depends on the matrix entries and it can be quite high.
In view of the above observations it looks more reasonable to exploit the ultimate periodicity of those columns and rows of tropical matrix powers whose indices correspond to the critical nodes. These columns and rows are ultimately periodic for any matrix and some of the known bounds on their periodicity transients are quadratic or even linear, if such columns and rows belong to a critical cycle of a known length.
This was the approach adopted in [Citation12] and [Citation10] and the same approach will be developed in the next section, see Algorithms 2, and 4. The more “naive” approach, based on the assumption that the tropical matrix powers are ultimately periodic, is more relevant to Algorithms 1 and 3.
3 Heuristic attacks on the tropical two-sided discrete logarithm with shift
In this section, we will discuss two approaches to how Problem 4 can be solved. Let us first note that this problem differs from the tropical two-sided discrete logarithm problem (Problem 3) since it includes a coefficient. The introduction of this coefficient enhances the solvability of the problem since it becomes sufficient to find a pair of exponents that makes U a shifted version of
. For this reason, if there is a pair
satisfying this equation, where
, respectively
, are above the ultimate periodicity thresholds for D1, respectively D2, then there are infinitely many such pairs. The first algorithm, which we are going to propose, will utilize this property, since we are relying on the intuition that the smallest pair of exponents
and
satisfying the equation is small enough, which is true if the sequences of matrix powers of D1 and D2 are ultimately periodic in the sense of Theorem 2.1 and if the threshold of their ultimate periodicity is small enough.
Algorithm 1
Solving the tropical two-sided discrete logarithm with shift using the non-uniqueness of exponents
Input:
Output:
1: for do
2: for do
3: if for some
then
4: ,
.
5: end if
6: end for
7: end for
Algorithm 1 has a perfect success rate in solving Problem 4 when is equal to the maximum exponent that could be used in the problem, but it is also expected to have a high success rate for lower values of
for the reasons outlined above.
For the second algorithm, we apply Theorem 2.4 for the powers of D1 and D2 to solve Problem 4. Note that here we can find by only searching in a search space of a size equal to the product of the two critical cycle lengths of the two matrices D1 and D2, while the previous algorithm has a maximum search space equal to the product of the maximum exponents that could be used in the problem (or, to be more precise, our estimates of such maximum exponents).
Note that this algorithm is heuristic in nature in particular since the CSR formulas of Theorem 2.4 are only guaranteed to hold when the exponent is larger than where lZ and, respectively, lW are the lengths of the critical cycle Z of D1 and, respectively, the critical cycle W of D2. The algorithm might not solve the problem if the original exponents t1, t2 are lower than this bound. One might add to the algorithm some parts where the exponents lower than this bound are also checked, similarly to the algorithms in [Citation12] and [Citation10].
To justify and explain the second algorithm we observe that we can use the CSR formulas of Theorem 2.4 for the rows of powers of D1 with indices in Z and for the columns of powers of D2 with indices in W, and then focus on the submatrix of U extracted from the rows with indices in Z and columns with indices in W. We then obtain the following equation
where λ1,λ2 denote the maximum cycle means of the two matrices.
Then we want to solve the problem of finding for some
and
such that
and this is achieved by firstly finding a pair of exponents
among
possibilities such that it will make the above described submatrix of U and the same submatrix of
“in phase”.
We will denote by
respectively. In particular, we begin by finding
and
that makes the submatrix of U extracted from the rows with indices in Z and the columns with indices in W a shifted version of the same submatrix of
. Then we try to find
by solving the following equation
(4)
(4)
As it follows from numerical experiments, it is also reasonable to impose some lower bounds on and
which guarantee that the submatrix of U with rows in Z and columns in W is in the ultimately periodic regime.
We now formulate (4) (with the above mentioned lower bounds on and
) in a more precise way as a mixed-integer linear programming problem. Recall that
and
denote the remainders when
, respectively
are divided by lZ and, respectively, lW. Thus
and
where
. We obtain
which can be rearranged to give
We also impose the lower bounds since we are counting on the critical rows and columns reaching the ultimate periodic regime, which may not be the case if these inequalities do not hold. We then have
which we can rearrange to obtain
Then we can find solutions by solving
(5)
(5) for
and
. Note that this is a mixed integer linear programming problem with unknowns
. We are now ready to formulate the solution method, see Algorithm 2.
Algorithm 2
Solving the tropical two-sided discrete logarithm with shift using CSR
Input:
Output:
1: Calculate
2: Find a critical cycle Z from D1, and W from D2, let their lengths be lZ and lW, respectively.
3: Calculate SZ, RZ, CW and SW as in Theorem 2.3
4: for do
5: for do
6: if for some
and for all i, j where
and
then
7: Check if (5) is solvable. If it is, then return where
and
.
8: end if
9: end for
10: end for
The following numerical experiments show the success rate and time consumption for Algorithm 1 and Algorithm 2 as a function of matrix dimension. For all experiments, the entries of the matrices are random integers in , and 100 trials were performed for each dimension. All numerical experiments are implemented on MATLAB R2023b running on Windows 11 64-bit, equipped with an Intel(R) Core(TM) i7-9750H CPU @ 2.60GHz and 16.0 GB RAM.
Success rate for Algorithm 1 is shown in . The exponents t1, t2 in Problem 4 are randomly chosen among integers in , and the scalar value α is in
. Algorithm 1 parameter
is n5 for the left hand side of the figure and n3 for the right hand side of the figure.
We notice that Algorithm 1 never fails when the maximum searchable exponent is the same as the one used in Problem 4 since the algorithm searches for all possible matrix exponents that make U in phase or equal to
. The guaranteed success results from testing all potential exponent combinations. The efficiency and quickness of the algorithm in finding appropriate exponents depends on the cyclicity pattern of the matrices D1 and D2. When we limit
to a lower exponent, we lose the guaranteed success rate, but we still achieve a high success rate with a faster time.
Success rate for Algorithm 2 is shown in . The exponents t1, t2 in Problem 4 are allowed to be less than and
for the left hand side, and are required to be larger than
and
for the right hand side, and the scalar value α is in the interval
.
We notice that Algorithm 2 has a high success rate when the exponents used in Problem 4 are larger than and
for t1 and t2 respectively since the critical entries are guaranteed to enter the ultimately periodic regime after such bounds. The attack however does not perform so well when the used exponents are lower than this threshold which is expected since the CSR formulas do not necessarily hold for such exponent values (i.e., entries in the critical rows or columns have not necessarily entered the ultimate periodicity).
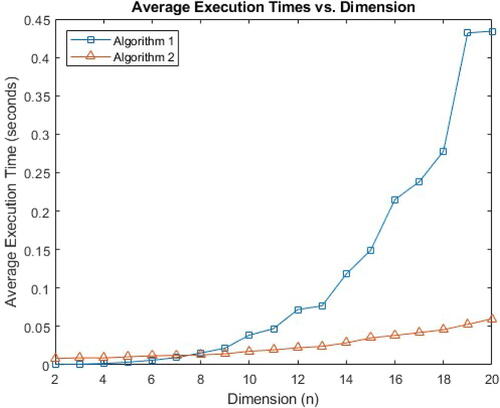
The time consumption for the two algorithms is quite different, as shown in . Here, the exponents t1, t2 in Problem 4 are random integers larger than and
, respectively, and the scalar value α is in the interval
.
We notice that Algorithm 2 is faster than Algorithm 1 since it limits its search to a finite set of values equal to the product of the critical cycle sizes of the two matrices D1, D2. However, for lower values of n, we note that Algorithm 1 is faster since the search space is small and Algorithm 2 requires more steps such as computing the CSR terms and maximum cycle means.
Note that one can combine the two algorithms to get better overall performance in terms of success rate and execution time. One possible combination is to apply Algorithm 1 for t1 until and t2 until a big enough number, then for t2 until
and for t1 until a big enough number, and then to perform Algorithm 2 for larger exponents.
4 The tropical semiring of pairs and the key exchange protocol
In this section, we examine a key exchange protocol proposed in [Citation1]. The protocol employs a modified tropical structure and is claimed to resist the known attacks on conventional tropical key exchange protocols. We will begin by introducing the modified tropical structure, followed by presenting the associated protocol and outlining its construction.
4.1 The tropical semiring of pairs
Let be the tropical semiring defined in 2.1, then we have the following definition.
Definition 4.1.
(Tropical Algebra of Pairs [Citation1, Citation2]). We define the tropical algebra of pairs as
with elements of the shape
such that
for
denotes the first and second element of a two-dimensional vector in
with the operations
defined as
The following example illustrates these operations.
Example 4.1.
Let then
The operations of this semiring can also be extended to include matrices following the same manner as the conventional tropical matrix operations in Definition 2.1 but with replacing the elements of by the elements of
and
by
. Thus, we will denote the semiring of matrices over
by
.
4.2 Key exchange protocol based on the semiring of pairs
We now present the key exchange protocol proposed by the authors in [Citation1] which is based on the tropical algebra of pairs . Note that the authors in this protocol altered the second operation of
to be
where
. This modification constructs a new semiring
with multiplicative identity
.
Protocol 1 (Key Exchange Protocol based on the Semiring of Pairs).
Alice and Bob agree upon two public matrices
.
Alice chooses a semiring
where
Here,
is her fixed private parameter. Bob also picks
where
and
is his fixed private parameter.
Alice picks two private natural numbers k, l and calculates
. She then chooses another private integer p and sends
to Bob, where
is
.
Bob also picks his private natural numbers r, s, calculates
and sends
to Alice, where
is
and
is Bob’s private parameter.
Alice computes her key
and Bob’s key is
.
The two parties end up with the same key KAlice = KBob as proved in [Citation1].
The following example illustrates the above key exchange protocol.
Example 4.2.
Alice and Bob agree on the public matrices X and Y:
and they choose the private parameters
for Alice, and
for Bob.
Alice calculates and sends
to Bob.
Bob calculates and sends
to Alice.
Then Alice and Bob compute their keys using those received transmissions:
Thus they end up with the same shared key.
5 Cryptanalysis of the protocol
In this section, we introduce our attacks on the proposed protocol. It is claimed that it is more resilient than its conventional tropical counterparts since it doesn’t reveal a cyclicity pattern for high powers, but we will show otherwise. We begin by presenting an alternative representation of matrices in , providing a foundation for constructing our attacks which are based on solving Problem 4. Subsequently, we implement our attacks showing their efficiency and success rate.
5.1 Representing matrices in 
 as matrices in
as matrices in 

Observe that a matrix with entries in the tropical semiring of pairs can be associated with a conventional tropical matrix in by replacing each entry of the matrix over that semiring with a 2 × 2 square matrix. More formally this representation is defined as follows.
Definition 5.1.
Suppose is given by
then we define
as follows:
We now observe that this representation gives rise to an injective homomorphism from the matrix algebra to the matrix algebra
. In other words, each matrix in
is uniquely represented by a matrix in
and this representation respects the matrix addition (obviously), and also the matrix multiplication, due to the following proposition.
Proposition 5.1.
Let , then
where
.
Proof.
We infer from the definition of the multiplication over (Definition 4.1) that if
and
Then we have
where
and
. Using Definition 5.1 to obtain matrices
and
, we have that
Then it is clear that we have a 2 × 2 sub-matrix in for each pair
, which has
and
Therefore
□
Example 5.1.
Suppose we have
Then
The above operation can be equivalently calculated using the conventional tropical matrix algebra, as we have
Notice that the odd numbered rows of are identical to the rows of
. We will exploit this observation to attack Protocol 1.
5.2 Attacks on Protocol 1 based on solving the tropical two-sided discrete logarithm
After the suggested matrix transformation, we observe that the problem of attacking the proposed protocol is essentially reduced to solving Problem 4. Thus, to attack the protocol, it is sufficient to find a pair of exponents that makes the tropical product of the public matrices
in phase with the transmitted matrix
, and not necessarily the exact exponents that generated the instance. In particular, we know from the definition of the proposed protocol that
Then when the two sides are multiplied by p, we get
This can be intercepted by the attacker, and he can transform it to
using Definition 5.1. Similarly, the attacker also transforms public matrices X and Y to
and
. The attacker can then utilize the following equality, which holds by Proposition 5.1
(6)
(6)
This equation resembles Problem 4 which can be solved by finding a pair of exponents such that
is a shifted version of
by a fixed integer τ which equals to the scalar part of the above equation (
). In other words, all entries of
differ by the same amount from the corresponding entry of
. There are highly likely infinite number of solutions due to the ultimate periodicity of tropical matrices. Note that the attacker can find the private parameters
by solving the equation
for
. However, these parameters are not required to construct the shared key as it suffices to use τ.
The shared key can then be computed using the found exponents and τ and the other intercepted massage
as
(7)
(7)
The attack is described in Algorithm 3. We also present an example illustrating this attack.
Algorithm 3
Attacking Protocol 1 by using Algorithm 1
Input:
Output: Key
1: Transform to
using Definition 5.1
2: Perform Algorithm 1 with Input:, then we get the output
3:
Example 5.2.
Suppose that Alice and Bob agree on the public matrices X and Y that are shown in Example 4.2, with the private parameters being for Alice and
for Bob. The attacker intercepts
and transforms it to a conventional tropical matrix
in
. He also transforms the public matrices X and Y to
and
, respectively. Let the results of this transformation be
The attacker then searches for a pair of exponents and
that satisfies the following equation
The attacker notices that any pair from and
satisfies the above equality. Suppose the attacker picks k = 2 and l = 10
Then, the shared key can be computed as:
which represents
We notice that the attacker successfully recovered the secret key using smaller exponents than those that generated the protocol instance.
We now describe the attack based on the CSR solution to the two-sided discrete logarithm problem. Starting from (6) we focus on the submatrix extracted from the rows with indices in a critical cycle Z of and the columns with indices in a critical cycle W of
, for which we obtain
Here lZ, lW denote the lengths of Z and W, and . Then, we want to find a pair of exponents
such that
is a shifted version of
by a fixed integer β which equals to the scalar part (
). To achieve that, we firstly need to find
and
that satisfies this shift requirement, and then find
by solving the following mixed integer linear programming problem
(8)
(8) with unknowns
and y. Then we obtain
and
. If it happens that (6) holds for the pair of exponents thus found, then this method also yields a common key, by applying the same argument as in (7). The attack is formally written as Algorithm 4.
Algorithm 4
Attacking Protocol 1 by Using Algorithm 2
Input:
Output: Key
1: Transform to
using Definition 5.1
2: Calculate
3: Find a critical cycle Z from , and W from
, let their lengths be lZ and lW, respectively.
4: Calculate SZ, RZ, CW and SW as in Theorem 2.3
5: Perform Algorithm 2 with Input:, then we get the output
6:
5.3 Numerical experiments
Both of the suggested attacks on Protocol 1 have been tested numerically. Specifically, we looked at the success rate for each attack as a function of matrix dimension. Additionally, we analyzed the time required for the attacker to construct the secret shared key. This analysis serves as a basis for comparison with the process of original secret key generation. For all experiments, the protocol parameters and the matrix entries are random integers in
, and 100 trials are performed for each dimension.
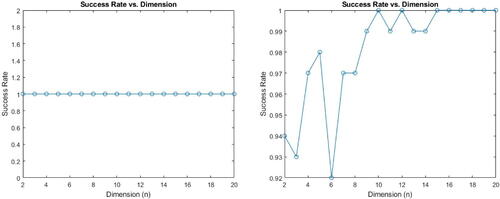
Success rate for Algorithm 3 is presented on . Here, the private exponents in the protocol are random integers in
, where n is the dimension of the matrices, and the parameter
is n5 (on the left) and n3 (on the right).
Since Algorithm 3 uses Algorithm 1, it never fails when the maximum searchable exponent is the same as the one used in the protocol since the algorithm searches for all possible matrix exponents that make
in phase or equal to
. The guaranteed success results from testing all potential exponent combinations. The efficiency and quickness of the algorithm in finding appropriate exponents depends on the ultimate periodicity threshold of the public matrices X and Y.
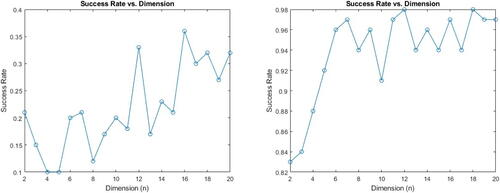
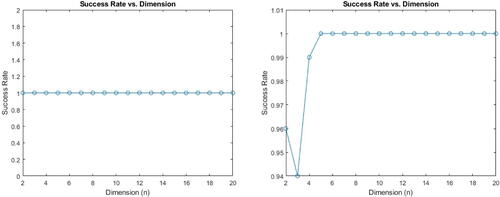
Success Rate for Algorithm 4 is shown in . The private exponents k, r are random integers less that , in
, larger than
for the left, middle and right figure, respectively. The same follows for l, s but with lW as the critical cycle length. For easier notations, we will denote both lZ, lW as lZ in what follows.
We notice that it is sufficient for Attack 4 to perform almost optimally when the original protocol’s exponents are larger than and not necessarily larger than
, which is the guaranteed threshold for the CSR formulas of Theorem 2.4 to hold. This might indicate that after transforming the matrices from
to
, the periodicity behavior is still maintained. The small number of failures are probably due the critical graph of 1 or more of the public matrices having multiple strongly connected components. We also notice that Algorithm 4 does not perform as well when the used exponents are lower than
which is expected since the CSR decomposition does not necessarily hold for such exponent values (i.e., entries in the critical rows or columns haven’t necessarily converged yet to ultimate periodicity).
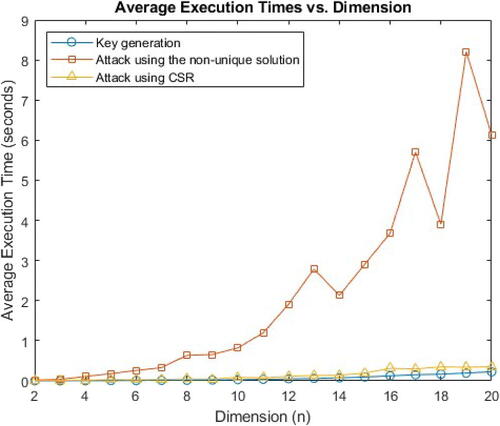
The time consumption comparison between the protocol and the two attacks is presented on . The private exponents in the protocol are random integers larger than
.
We notice that recovering the key with Algorithm 4 is faster than Algorithm 3 since it limits its search to a finite set of values equal to the product of the critical cycle sizes of the two public matrices. We see that there is no significant difference between the attacker’s time and the users’ time in generating the secret key.
5.4 An attack based on absolute values of tropical pairs
In this section, we describe another attack that does not require the attacker to double the matrices sizes, which makes it more efficient than the previous ones. However, while performing this attack we lose some information and this worsens the success rate. We firstly present the following definition, inspired by the symmetrized semiring introduced in [Citation2].
Definition 5.2
(Absolute Value). Let . Then the absolute value of this pair is defined by
.
For two pairs the following properties hold:
and
The first of them is rather unusual, since we only have in the usual algebra.
These properties can be also extended to matrices over tropical pairs, as we have
which directly follows from the above definition, and
Here A, and
.
We can use the above operations to perform the matrix addition and multiplication, and we will get a half sized conventional
matrix. These operations with half sized result are often sufficient to attack the proposed protocol. The attack is very similar to Attack 4, but they only differ in the type of matrix transformation. It is formally presented below as Algorithm 5.
Algorithm 5
Attacking Protocol 1 using the absolute values
Input:
Output: Key
1: Transform to
using Definition 5.2
2: Calculate
3: Find a critical cycle Z from , and W from
, let their lengths be lZ and lW, respectively.
4: Calculate SZ, RZ, CW, and SW as in Theorem 2.3
5: Perform Algorithm 2 with Input:, then we get the output
6:
We expect this attack to have a lower success rate than the previous ones due to the observation that does not always imply that
. Hence, the attack in this case will not successfully recover the secret key since the found exponents do not really solve the original tropical two-sided discrete log with shift problem over the tropical pairs. However, it is going to be faster since it does not require doubling the matrix size which expedites the process of computing the CSR terms and finding the exponents through solving the tropical two-sided discrete logarithm with shift. We performed a numerical experiment in which we observed that the algorithm had approximately 50–60% success rate but roughly twice the speed of Algorithm 4.
6 Conclusion
In this paper, we presented the tropical two-sided discrete logarithm with shift problem and its solution. We showed that two algorithms solve the problem with a high success rate. The first algorithm relies on the non-uniqueness of the exponents that can satisfy the problem’s equation, and it showed a perfect success rate but potentially slower convergence. The other algorithm heuristically solves the problem using the CSR decomposition, demonstrating a high success rate and a much faster execution time. We then presented a key exchange protocol that is based on the tropical semiring of pairs. We firstly showed that the matrix operations over the tropical semiring of pairs can be equivalently calculated using the conventional tropical semiring by doubling the matrices’ size. After the transformation to the conventional tropical semiring, the problem was reduced to the tropical two-sided discrete logarithm with shift, which can be solved using the two proposed algorithms. Lastly, we introduced an even faster approach that does not require the attacker to double the matrix size, showing roughly twice the speed of the previous heuristic attack, but it has a lower success rate.
We also note that the proposed protocol remains vulnerable to the known tropical cryptographic attacks even if the parties use matrix polynomials over the semiring of pairs. If Alice and Bob use matrix polynomials over the semiring of pairs, then the problem will not reduce to the tropical two-sided logarithm with shift, but in this case it may be possible to apply a modified version of the Kotov-Ushakov attack [Citation8] (which, however, shows an exponential blow up in the number of operations as the maximal degree of the polynomials increases). The main reason for insecurity of the protocols using the matrix algebra over the tropical semiring of pairs is the existence of injective homomorphism from this matrix algebra to the ordinary tropical matrix algebra.
Acknowledgments
The authors are grateful to Sergeĭ’s M.Sci. student Sarah Elt who gave them the idea to try using also the absolute value of pairs and its extension to matrices. We are also grateful to our anonymous referee for careful reading and comments which helped to improve our paper.
Notes
References
- Ahmed, K., Pal, S., Mohan, R. (2023). Key exchange protocol based upon a modified tropical structure. Commun. Algebra 51(1):214–223. DOI: 10.1080/00927872.2022.2095566.
- Baccelli, F. L., Cohen, G., Olsder, G. J., Quadrat, J. P. (1994). Synchronization and linearity - an algebra for discrete event systems. John Wiley and Sons.
- Butkovič, P. (2010). Max-Linear Systems: Theory and Algorithms. London: Springer.
- Cohen, G., Dubois, D., Quadrat, J. P., and Viot, M. (1983). Analyse du compartement périodique de systémes de production par la théorie des dioïdes. Research Report RR-0191, INRIA.
- Grigoriev, D., Shpilrain, V. (2013). Tropical cryptography. Commun. Algebra 42:2624–2632. DOI: 10.1080/00927872.2013.766827.
- Grigoriev, D., Shpilrain, V. (2019). Tropical cryptography II: extensions by homomorphisms. Commun. Algebra 47(10):4224–4229. DOI: 10.1080/00927872.2019.1581213.
- Isaac, S., Kahrobaei, D. (2021). A closer look at the tropical cryptography. Int. J. Comput. Math. Comput. Syst. Theory 6(2):137–142. DOI: 10.1080/23799927.2020.1862303.
- Kotov, M., Ushakov, A. (2018). Analysis of a key exchange protocol based on tropical matrix algebra. J. Math. Cryptol. 12(3):137–141. DOI: 10.1515/jmc-2016-0064.
- Merlet, G., Nowak, T., Sergeev, S. (2014). Weak CSR expansions and transience bounds in max-plus algebra. Linear Algebra Appl. 461:163–199. DOI: 10.1016/j.laa.2014.07.027.
- Muanalifah, A. (2023). Public key cryptography based on tropical algebra. PhD thesis, University of Birmingham.
- Muanalifah, A., Sergeev, S. (2020). Modifying the tropical version of Stickel’s key exchange protocol. Appl. Math. 65:727–753. DOI: 10.21136/AM.2020.0325-19.
- Muanalifah, A., Sergeev, S. (2022). On the tropical discrete logarithm problem and security of a protocol based on tropical semidirect product. Commun. Algebra 50(2):861–879. DOI: 10.1080/00927872.2021.1975125.
- Nachtigall, K. (1997). Powers of matrices over an extremal algebra with applications to periodic graphs. Math. Methods Oper. Res. 46:87–102. DOI: 10.1007/BF01199464.
- Rudy, D., Monico, C. (2020). Remarks on a tropical key exchange system. J. Math. Cryptol. 15(1):280–283. DOI: 10.1515/jmc-2019-0061.
- Sergeev, S., Schneider, H. (2012). CSR expansions of matrix powers in max algebra. Trans. Amer. Math. Soc. 364(11):5969–5994. DOI: 10.1090/S0002-9947-2012-05605-4.
- Shpilrain, V. (2008). Cryptanalysis of Stickel’s key exchange scheme. In: Hirsch, E. A., Razborov, A. A., Semenov, A., Slissenko, A., eds. Computer Science – Theory and Applications. Berlin, Heidelberg: Springer, pp. 283–288.
- Sidel’nikov, V. M., Cherepnev, M. A., Yashchenko, V. V. (1994). Public key distribution systems based on noncommutative semigroups [Doklady Akademii Nauk]. 332(5):566–567, 1993 (in Russian). Translated in: Russian Acad. Sci. Dokl. Math. 48(2):384-386.
- Stickel, E. (2005). A new method for exchanging secret keys. In: Third International Conference on Information Technology and Applications (ICITA’05), vol. 2, pp. 426–430.

![Fig. 5 Attack 4 success rate with protocol’s exponents less than (n−1)lZ, in [(n−1)lZ,(2n−1)lZ] and larger than (2n−1)lZ respectively.](/cms/asset/607b07a5-0a35-4d52-99b0-c9fc14c6efee/lagb_a_2341814_f0005_c.jpg)