Abstract
In this article the author revisits the oldest attack on GOST known, the Kara Reflection attack, and another totally unrelated truncated differential attack by Courtois and Misztal. It is hard to imagine that there could be any relationship between two so remote attacks which have nothing in common. However, there is one: Very surprisingly, both properties can be combined and lead the fastest attack on GOST ever found, which is nearly feasible to execute in practice.
1. Background
The Russian encryption standard GOST 28147–89 is a former top secret encryption algorithm. In 1989, it became an official standard for confidential information, but the specification of the cipher remained confidential [Citation23]. In 1994, shortly after the dissolution of the Soviet Union, the standard was declassified, published, and also translated to English [Citation23]. GOST is a block cipher with a simple Feistel structure, 64-bit block size, 256-bit keys, and 32 rounds. Each round contains a key addition modulo 232, a set of eight bijective S-boxes on four bits, and a simple rotation by 11 positions. It is widely known that the structure of GOST is in itself quite weak, and in particular the diffusion is quite poor; however, this is expected to be compensated by a large number of rounds. Thus, until 2011, there was no significant attack on this algorithm from the point of view of communications confidentiality: an attack which would allow decryption or key recovery in a realistic scenario where GOST is used for encryption with various random keys. This is in the sense of pure mathematical attacks. In real life, GOST would be broken routinely by a side channel attack (see for example [Citation18]).
The turning point in the security of GOST was the discovery of the so-called “reflection” property [Citation14]. Initially, at Indocrypt 2008, only a weak-key attack with time complexity of 2192 was proposed, with large proportion of 2−32 of weak keys. In 2011, several attacks on regular GOST keys were discovered, and more than half of these new attacks use this reflection property [Citation12], sometimes two, three, or four times [Citation5]. Most of these attacks can be described as attacks with a “complexity reduction” [Citation5, Citation6], where from some data for the full 32 rounds GOST, we obtain a certain number of pairs for eight or less rounds of GOST. The quantity of data available after reduction is very small, for example, two, three, or four pairs for a reduced cipher. In this aritcle, we will look at some of the simplest of these attacks and avoid the highly complex ones.
A basic assessment of the security of GOST against linear and differential cryptanalysis was conducted in 2000 by Shorin, Jelezniakov, and Gabidulin see [Citation25]. The results were quite impressive: At the prescribed security of level of 2256, five rounds are sufficient to protect GOST against linear cryptanalysis. Differential cryptanalysis [Citation1] of GOST seems comparatively easier and has attracted more attention. In [Citation25] the authors also estimated that seven rounds should be sufficient to protect GOST against differential cryptanalysis. The authors also claimed that “breaking the GOST with five or more rounds is very hard” [p. 5]. In addition, two Japanese researchers [Citation24], explained that the straightforward classical differential attack with one single differential characteristic is unlikely to work at all for a large number of rounds. In the same article [Citation24], more advanced differential attacks on GOST were described. They are advanced truncated differential attacks, cf. [Citation16]. The first advanced multiple differential attack proposed in [Citation24] allows to break about 13 rounds of GOST. Numerous recent works have tried to understand, evaluate, and improve the resistance of GOST against differential cryptanalysis, in view of the standardization of GOST [Citation1, Citation17, Citation22]. At the same time, in 2011–2012, many improved differential attacks on GOST were found, allowing finally to break full 32-round GOST faster than by brute force, see [Citation7, Citation9Citation10Citation11]. We also exploit these properties in this article.
In this article we do not study GOST in much depth. We just revisit the oldest attack on GOST known, the Kara Reflection attack, and ask ourselves a simple question: Do multiple symmetric fixed points exist? We can safely consider that eight rounds of GOST are a black box and that it has a simple truncated differential property, which has been discovered recently. These two properties seem totally unrelated. However, their combination leads to an extremely simple and powerful attack on GOST.
2. The Reflection Property of GOST
We write GOST as the following functional decomposition (to be read from right to left), which has been proposed at Indocrypt 2008 [Citation14]:
Fact 1 (Internal Reflection Property). Consider the last 16 rounds of GOST 𝒟○𝒮○ℰ for one fixed GOST key. This function has an exceptionally large number of fixed points: applied to X gives the same value X with probability 2−32 over the choice of X, instead of 2−64 for a random permutation.
Justification: Our permutation 𝒟 ○ 𝒮 ○ ℰ has a well-known “conjugated” structure of type Q−1 ○ P ○ Q. Consequently, it has the same cycle structure as the swap function S and 232 fixed points. The state of the cipher after the first eight rounds ℰ is symmetric with probability 2−32, and 𝒟 ○ ℰ = Id.
Note: This theorem about Q−1○P ○ Q and P has played a very important role in the cryptanalysis of important government and military ciphers, in particular many rotor machines. It was first used by Marian Rejewski in the cryptanalysis of Enigma in the early 1930s, and it is sometimes called “the theorem which won World War 2,” see [Citation13, Citation20, Citation21].
3. Attacks with Symmetric Fixed Points
At Indocrypt 2008, Kara described a weak-key attack on full 32-round GOST. It has time complexity of 2192 and works for a large proportion of 2−32 of weak keys. It uses a very interesting new “reflection” property [Citation14]. At first sight, this attack has only limited interest. However, a large number of very good attacks have been discovered, and more than half of them use this reflection property [Citation12], sometimes two, three, or four times [Citation7].
In late 2012, another weak key attack was proposd by Kara and Karakoç, cf. [Citation15]. The paper was presented at CANS 2012, in Darmstadt, Germany, on 12–14 December 2012. This attack is quite interesting because it uses pairs of symmetric fixed points. This article is about showing that such pairs exist with a probability which is larger than expected and that triple and quadruple symmetric fixed points also exist with surprisingly high probabilities. In one sense, we revisit this attack from [Citation15], and propose very important variants which are based on highly non-trivial facts that are somewhat impossible to expect from [Citation15]. We are going to deduce them from other major results on GOST [Citation7, Citation9Citation10Citation11, Citation24], even though it is safe to say that nobody would expect that these attacks could be related in any way.
3.1. Recent Weak Key Attacks from CANS 2012
The new weak key attack on GOST [Citation15] is based on the assumption that there are two symmetric fixed points in the first 16 rounds of GOST. Such symmetric fixed points happen only for weak keys and can happen for two distinct reasons. It is possible to see that the attack from [Citation15] can be split into two independent weak key attacks, which the authors describe as one single attack with a distinction of two distinct events (Event1 and Event2, see [Citation15]). We recall briefly the attack from [Citation15]. Let ℰ be the first eight rounds of GOST. In Event1, the assumption is that there exists two symmetric A ≠ B such that ℰ(A) = B and ℰ(B) = A, which is a swap. In Event2, we assume that there exists two symmetric fixed points A ≠ B (i.e., ℰ(A) = A and ℰ(B) = B). Both events lead to two symmetric fixed points for the full 32-round GOST. Each of these events occurs only for a proportion of d = 2−65 of keys, or at least it seemed so to the authors. In fact, the main point in this article is that such a probability can be much higher than expected, especially for multiple symmetric fixed points.
In this article, we only look at Event2; however, similar observations could also be made about Event1, and this can also lead to some non-trivial attacks and their generalizations and special cases, see [Citation5]. We can observe that Event2 is particularly simple: It is just twice the event which is used in the oldest reflection attack on GOST [Citation16]. This gives the following very simple attack from [Citation15]:
Fact 2 (Event2 Attack From [15]). For every key such that Event2 happens (i.e., there are at least two symmetric fixed points for the first eight rounds of GOST), given 232 CP (chosen plaintexts), we can obtain two P/C pairs for eight rounds of GOST correct with probability close to 1. Then, in time of about 2127 GOST encryptions, one can enumerate and check 2128 candidates for the GOST key and identify the correct key.
Remark
The original paper [Citation15] used the final step presented by Dinur, Dunkelman, and Shamir at FSE 2012 with time complexity of 2128 GOST encryptions [Citation12]. However, this can be reduced to an expected average of 2127 GOST encryptions and still 2128 in the worst case, at the price of more memory, see [Citation5].
3.2. Technical Analysis of CANS 2012 Attack
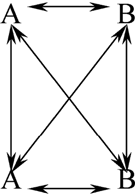
In this attack, the attacker observes that IF we have two symmetric fixed points, THEN we have the whole situation depicted in Figure , then the two symmetric fixed points also work for the whole GOST, and therefore they are visible to the attacker. However, symmetric fixed points of Enck() are not very likely to ever occur by accident, and in this attack we already study a property which occurs for a proportion of 2−65 of all GOST keys. With the same probability, two symmetric fixed could have occurred also for the whole GOST, purely by accident, as they would occur for a random permutation. For this reason, the authors of [Citation15] analyse the success probability of their attack in a very detailed way, though they are assuming that eight rounds of GOST behave as a random permutation, even though the present article will show that it does not behave as a random permutation. With this assumption, they arrive at a conclusion that if the whole 32-round GOST has two symmetric points, the Event 2 would occur with probability about 1/5 (and the other event which we ignore in this article with another 1/5).
Figure 1 Two symmetric fixed points, a.k.a. Event2 in [Citation15].
![Figure 1 Two symmetric fixed points, a.k.a. Event2 in [Citation15].](/cms/asset/0ff3c9cd-da04-445c-9979-01d2ecbd720e/ucry_a_988362_f0001_b.png)
In this article, we will show that most likely, and at least for the default sets of GOST S-boxes [Citation23], the basic event occurs with higher probability than expected for both eight and 32 rounds of GOST. Therefore, the analysis of [Citation15] is not at all what happens when their attack is implemented. Moreover, the nature of many events such as Event2 is to occur with two points A, B which are closely correlated in the sense that they have many shared bits. This is a very serious problem: Actually, it is trivial to see that if we have 2KP for eight rounds of GOST, neither the FSE 2012 attack [Citation12] will work, nor any of numerous weaker and stronger variants known from [Citation6] can work at all. Each key bit is only used once in the first eight rounds of GOST, and the diffusion is very poor. If the two data points share many bits, then in the first few rounds, states of many S-boxes will be identical, and we just do not have enough information about these key bits from the information theoretical point of view. Substantially larger number of solutions means that the overall time complexity is going to be substantially larger.
It may seem that our observations totally “ruin” the attack from [Citation15], and it should be possible to show that the attack from [Citation15] does not work at all with probability close to 1 (i.e., it almost never works as described). However, our observations do not ruin the attack; it is still expected to work as predicted for roughly the same number of weak GOST keys. There will be many additional cases for which the attack fails or is much slower than expected which have not been anticipated by the authors.
More importantly, we are going to present a way to turn to our advantage these internal correlations inside GOST and high frequency of pairs and larger sets of points, as well as the fact that data in these points are strongly correlated.
It remains to study the frequency of double symmetric fixed points in GOST and then analyse all the consequences of these quite unexpected facts. Before that, we recall a seemingly unrelated differential property of GOST.
4. Truncated Differential Cryptanalysis of GOST
We consider the following standard situation that has been introduced [Citation11] and further studied in [Citation7, Citation9Citation10Citation11]. Let Δ = 0x80700700 which mask has seven active bits out of 32. We denote by (Δ, Δ) a set of 214 − 1 non-zero differences on 64 bits with up to 14 active bits. Then, following [Citation9, Citation10], we have the following fact (Fact 3). We should note that in this article, it does matter a lot that this event is symmetric.
Fact 3. For a random permutation, there are 277 pairs with the input difference (Δ, Δ), and for a proportion of 2−50 or an average of 277−50 = 227 pairs, the output difference is also in the set (Δ, Δ). For eight rounds of GOST, we have about 252 pairs which satisfy these differences (Δ, Δ) at both ends, cf. Figure 2.
5. On Frequency of Symmetric Fixed Points in GOST
Fact 4 (Symmetric Fixed Points in GOST). For eight rounds of GOST and a random key, the probability that there is a symmetric fixed point is about 2−33 and is expected to be the same for a random permutation. However, for the default set of GOST S-boxes, the probability that there are two symmetric fixed points sharing as many as 50 bits which will be the inactive bits in mask (Δ, Δ) (such events are depicted in Figure ) is at least 2−60 instead of about 2−2−64−50 for a random permutation. Consequently, at least for the default set of GOST S-boxes, Event2 of Figure occurs with key density of at least approximately d ≥ 2−60 over GOST keys.
Justification: We provide a method to estimate this probability. Let A′ = ℰ(A) and B′ = ℰ(B). Following [Citation10], eight rounds of GOST, there are 277 pairs with the input difference of type (Δ, Δ), and for a proportion of 2−25 of them, which is 252 pairs A, B on average, the output difference is also in (Δ, Δ). This for the default set of GOST S-boxes.
Our computer simulations show that when the propagation occurs, the entropy of A ⊕ B is low, and the probability that A ⊕ B = A′ ⊕ B′ is only about 2−9. Furthermore, A = A′ with probability 2−64, which also implies B = B′. Furthermore, A is symmetric with probability 2−32. Since their difference lies within (Δ, Δ), which is symmetric, B is symmetric with probability at most 2−7. Overall, for a proportion of d = 252−9−64−32−7 = 2−60 of GOST keys, we have two symmetric fixed points A, B sharing the same 50 bits.
Remark 1
This is higher than what we would get for having just two symmetric fixed points without any extra condition, which is roughly about 2−2−64 for a random permutation. This is because two fixed points would occur with probability of (1 − 2/e) ≈ 0.26, and each would be symmetric with probability 2−32. We refer to [Citation2, Citation19] for related research and fundamental facts on fixed points in random permutations.
Remark 2
So far, this reduction in probability was only demonstrated for the default set of GOST S-boxes. However, this is a conservative estimate with just one mask (Δ, Δ). These probabilities must be added for different masks, and in real life, this probability should be even higher (!). We also expect very similar results for other sets of S-boxes.
6. CANS 2012 Attack in the Multiple Key Scenario
In order to grasp all the implications of Fact 4, we must consider not only the attack from [Citation15], but also a particular adaptation of this attack which we have personally suggested to the authors, and which is already described very briefly inside the paper [Citation15]. However, it is safe to say that nobody has realized all the implications of this variant and its extensions.
Fact 5 (Event2 Attack in the Multiple Key Scenario). If we have a diverse population of at least 265 different 256-bit GOST keys generated at random, with access to 232 CP per key, one can recover one of these 256-bit keys in total overall time of at least 2131 GOST encryptions for the default set of GOST S-boxes. For other S-boxes, the complexity is expected to be lower, about 2129 GOST encryptions.
Justification: This attack requires that some 265 devices with random keys exist. It is possible to see that for a proportion of about 2−65 keys, the first eight rounds are expected to have two symmetric fixed points in the same way a random permutation would have one. This is strictly following the calculations of [Citation15], and because this event occurs at random, A, B are not expected to share many bits. Therefore, the final step on 2 KP is likely to work as predicted with the running time of 2128 or maybe even 2127 GOST computations [Citation5, Citation12].
However, a truly remarkable thing happens with keys which are not weak. Such cases are basically “visible” to the attacker. He can reject them at a very low cost. There is no need to run the whole attack in 2127 for a majority of the keys. This is true because for a random permutation, the probability that Enck() has two symmetric fixed points A, B is low, even though it is not as low as we initially thought. There is no need to run the attack 264 times. We only must to run the attack about 264−60 times, only for the 2−60 of cases predicted by Fact 5.
For all except a proportion of about 264−60 GOST keys, we can reject them right away. We have 264 different keys, and we check them for two symmetric fixed points in time of about 232 each, which will be very small compared to the dominant term in the attack. With 264 different keys, two symmetric fixed points will occur only a few times (264−60 is expected). Therefore, the complexity of the whole attack is at least 2127+64−60 = 2131 GOST computations to recover one key, and possibly more (this is if the probability in Fact 4 is even higher). Later in this article, we will show how to benefit from the fact that GOST has more symmetric fixed points than expected, which is a problem in this attack.
For other sets than the default set of GOST S-boxes, we are not aware of a similar reduction in probability of having two symmetric fixed points; it is expected to be the same as for a random permutation. Then, the analysis of [Citation15] applies. We expect that Enck() has two symmetric fixed points with frequency about five times bigger than the frequency that Event2 occurs, and we expect to run our attack maybe five times and get the complexity of at least 2127+2 = 2129 GOST computations.
7. Approximate Fixed Point Bicliques
In this section, we introduce a new concept which is essentially an invariant affine space common for many encryptions at both sides and also an approximate invariant property:
Definition 7.0.1. (An approximate fixed point biclique)
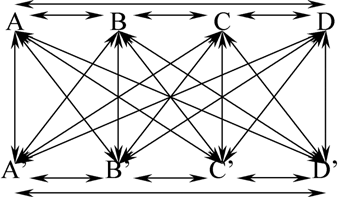
An approximate fixed point biclique with k points and dimension D and for r = 8 rounds of GOST is defined as a set of k + k values A, B,… and A′, B′, … , such that A′ is the encryption of A after eight rounds and so on (Figure ), and such that all these k + k values lie in the same affine space of dimension D.
This is different from bicliques studied in cryptanalysis of AES [Citation4], as our bicliques occur for one single key, and multiple connections on the graph mean that each pair is similar in the sense it shares a common substring of 50 bits.
We have discovered a new form of approximate self-similarity of GOST which happens to occur in the real life. For example, for one set, we can have four input points (k = 4) and four output points which share some fixed set of 50 bits, so that D = 14, and that for every arrow in Figure , the 50 bits in question are the same. This can be seen as a higher order truncated differential property. Surprisingly, this occurs for GOST and 256-bit keys generated at random with a non-negligible probability. The key observation is that (as we will see later) the number of such events with three or four points is not much lower than the number of events with two points.
7.1. Approximate Fixed Point Bicliques for Eight Rounds
We can remark that we are looking at a relatively strong property, and sets of points which satisfy it are unlikely to exist for many more rounds of GOST or for a random permutation. However, the internal structure and poor diffusion inside GOST allows many sets which satisfy the Definition 7.0.1 for some k.
Fact 6 (A 2/3/4-point approximate fixed point biclique for eight rounds of GOST and D = 14). For a typical GOST key, we have on average 22 possibilities for the set of four points A, B, A′, B′, such that A′, B′ are the encryption of A, B after eight rounds, AND which have differences with up to 14 bits and all the points A, B, A′, B′ share the same set of 50 bits, following the pattern using the mask (Δ, Δ). For the default set of GOST S-boxes [Citation23], for a proportion of at least 2−8 of GOST keys, there exists a set of 50 bits and a set of six points A, B, C and A′, B′, C′, such that A′ is the encryption of A after eight rounds and so on, and which have differences with up to 14 bits and share the same set of 50 bits. For another proportion of at least about 2−9 of GOST keys, there exists a set of 50 bits and a suitable set of eight points A, B, C, D and A′, B′, C′, D′, which again pairwise correspond to each other and after 8 rounds all share 50 bits as depicted in Figure .
Justification: We consider the affine space of D = 14 defined by the popular mask (Δ, Δ), cf. [Citation7, Citation9Citation10Citation11]. It is possible to observe that for one encryption A, A′ for eight rounds of GOST, if A ⊕ B ∈ (Δ, Δ), then if A′ ⊕ B′ ∈ (Δ, Δ) with probability 2−25.0, cf [Citation7, Citation9, Citation10]. There is about 264+14/2! ≈ 277 couples A, B with suitable input differences, then with probability 2−25 for one pair we have the correct output difference A′ ⊕ B′. Furthermore, then common 50 bits are the same for the input and for the output with probability 2−50. Thus, we expect that there are on average about 277−25−50 ≈ 22 pairs which share a fixed 50 common bits.
For k > 2, the existence of such configurations can be seen as a simultaneous higher-order truncated differential attack with three or four points, respectively. As above, if A ⊕ B ∈ (Δ, Δ), then if A′ ⊕ B′ ∈ (Δ, Δ) with probability 2−25.0, cf. [Citation7, Citation9, Citation10]. Then if A, A′ and B, B′ are the suitable pairs for eight rounds, it is easier to find more such pairs C, C′. Our computer simulation shows that now if C ⊕ A ∈ (Δ, Δ), then C′ ⊕ A′ ∈ (Δ, Δ) with probability of only about 2−22 instead of 2−25.0. In the same way, there will be a fourth pair D, D′ with even better probability of about 2−13.
There are about 264+14+14/3! ≈ 289.4 triples A, B, C with suitable input differences, then with probability 2−25 for one pair we have the correct output difference A′ ⊕ B′, and then the third point also has the same 50 bits with probability of only about 2−22. Thus, we expect that there are on average about 289−25−22−50 ≈ 2−8 triple points which share a fixed 50 common bits.
In the same way, there are about 264+14+14+14/4! ≈ 2101.4 quadruples A, B, C, D with suitable input differences, with probability 2−25 for one pair we have the correct output difference A′ ⊕ B′, and then the third point is correct with probability of only about 2−22, this multiplied by 2−13 for the fourth point and finally by 2−50 for the 50 bits on both sides being equal. Thus, we expect on average about 2101−25−22−13−50 ≈ 2−9 quadruple points which share a fixed 50 common bits and have differences with up to 14 bits as depicted in Figure .
7.2. Real Life Events
It is difficult to guarantee that the events which we study really happen as predicted. For example, it is very surprising to see that events with four points will occur more or less as frequently as events with three points. To validate this, we have tried 239 encryptions for eight rounds with random keys an initial random difference with 14 active key bits within (Δ, Δ), and if after the eight rounds the final difference was also within (Δ, Δ), then we count how many other plaintexts with the same 50 bits also produce the same 50 bits as the two cases. In our simulation, we have seen exactly 21 events with four points and also exactly 21 events with four points with random keys and random 50 bits.
Example: We exhibit one event with four points from our simulation. This event was generated strictly at random and has no special properties other than those which might occur naturally at random for such events. The data are self-explanatory.
8 rounds 4 points 50 inactive bits 8070070080700700key = C4EEEC4D9FC4A3C55DB81B7BEE470567396682007AE8D9B59E3FD9A3225BC7B4 P = 6492F05231436EBF E4D2F152317368BF 64D2F452B14368BF E492F552B1736EBF C = 89C3449606C28E22 09C3409606C28F22 89C3409686A28822 09C3449686A28922
8. On Triple and Quadruple Symmetric Fixed Points in GOST
We have established that multiple approximate fixed points occur with probabilities higher than expected. In this section, we look at a special case: triple and quadruple symmetric fixed points.
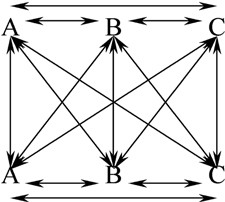
Fact 7 (Frequency of Triple and Quadruple Symmetric Fixed Points). For the default set of GOST S-boxes [26] the probability that for eight rounds there are two symmetric fixed points sharing as many as 50 bits, as shown in Figure 5, is at least 2−60 instead of about 2−2−64−50 for a random permutation.
The probability that there are three symmetric fixed points sharing the same set of 50 bits is at least 2−70 instead of roughly about 2−4−96−50 for a random permutation. For four symmetric fixed points sharing the same set of 50 bits, it is at least 2−79 instead of roughly about 2−6−128−50 for a random permutation.
Justification: Let A′ = ℰ(A) and B′ = ℰ(B) and C′ = ℰ(C) for eight rounds of GOST. Following Fact 6 for a proportion of at least 2−8 of GOST keys, there exists A, B, C such that all the six points share the same set of 50 bits following the mask 0x8070070080700700. The probability that A is symmetric is 2−32. Then, the probability that A = A′ is 2−14. Then, the probability that A ⊕ B = A′ ⊕ B′ and simultaneously A ⊕ C = A′ ⊕ C′ is maybe about 2−16 due to low entropy of these differences, which we have experimentally tested. Overall, for a proportion of at least d = 2−8−32−14−16 = 2−70 of GOST keys, we have three symmetric fixed points A, B, C sharing the same 50 bits.
In the same way, for a proportion of maybe d = 2−9−32−14−24 = 2−79 of GOST keys, we have four symmetric fixed points A, B, C, D sharing the same 50 bits. These are rough estimations, and they require further research.
Remark 1
This is much higher than what would get for having just 3/4 symmetric fixed points without any extra condition, which is roughly about 2−4−96 or respectively 2−6−128 for a random permutation.
Remark 2
Again, this reduction in probability was only demonstrated for the default set of GOST S-boxes. However, this is a conservative estimate with just one mask 0x8070070080700700, and these probabilities get higher if we take into account other masks. We expect similar results for other sets of S-boxes.
Remark 3
Again, symmetric fixed points for eight rounds also symmetric fixed points for the full 32-round GOST [Citation14, Citation15], and in what follows, we will use them to propose a remarkably efficient attack on full GOST. We skip a triple symmetric fixed point attack and go directly for the quadruple point attack.
8.1. Quadruple Symmetric Fixed Point Attack
We call this attack Family 8.4 attack in order to honor the numbering of various weak key classes from [Citation5].
Fact 8 (Weak Keys Family 8.4 Attack). We define the Weak Keys Family 8.4 by keys such that there exists four symmetric fixed points A, B, C, D for the eight rounds ℰ(). With the default GOST S-boxes, this occurs with probability of at least d = 2−79 over the GOST keys. For every such key given 232 CP, we can obtain four P/C pairs for eight rounds of GOST, correct with probability close to 1, and we can recover the key given 232 CP, with running time of 299 GOST encryptions and with negligible memory.
Justification: We get d = 2−79 by applying Fact 7. The four pairs are then ℰ(A) = A, ℰ(B) = B, ℰ(C) = C, and ℰ(D) = D. We cannot just apply one of the attacks from the recent Cryptologia 2013 article [Citation8] in 294 GOST computations. This is due to the fact that our four points are closely related, and the attacks from [Citation9] are not expected to work. However, it is possible to show that a variant of this attack in 299 GOST computations will work and that the system does NOT have too many solutions which would prevent the attack from working as in Section 3.2. The detailed description of the dedicated attack in 299 can be found in the Appendix of [Citation5].
Again, we have a conversion step with early rejection of non-weak keys:
Fact 9 (Family 8.4 Attack for a Population of 279 Random Keys). If we have a diverse population of at least 279 different 256-bit GOST keys generated at random, with access to 232 CP per key, one can recover one of these 256-bit keys in total overall time of about 2101 GOST encryptions.
Justification: We have an attack where given 232 CP per device, namely the encryption of all symmetric plaintexts, the weak key becomes immediately “visible” for the attacker. The probability that a random 64-bit permutation has four symmetric fixed points is about 2−134. Thus, for all except the correct device out of 279, we can reject this device right away after checking 232 plaintexts in time of 279+32 CPU clocks, which is about 2101 GOST encryptions.
For the remaining one case, which we expect to be really our weak key with correct additional differences, we apply Fact 8 above, which gives about 299 GOST encryptions and negligible memory. Overall, we expect to recover one key in time of about 2101 GOST encryptions.
9. Conclusion
Symmetric fixed points for GOST and advanced differential attacks on GOST have been invented independently for very different purposes. One recent attack presented at CANS 2012 does not work as exactly predicted. This is due to the fact that pairs of fixed points in GOST exist with a probability lower than anybody would have imagined, and this is a problem in this attack.
In this article, We show that something even more remarkable happens with multiple symmetric fixed points: They exist for eight rounds of GOST with probability not slightly but very substantially bigger than for a random permutation. We get a very strong property and very robust internal correlations between these points, which are “visible” to the attacker. This leads to a remarkable new attack on GOST, which requires a totally unrealistic quantity of encrypted data. However, it would be feasible for an intelligence agency to execute such an attack in the near future if not today. Further analysis of this attack should show that the complexity can be even lower.
Additional information
Notes on contributors
Nicolas Courtois
Nicolas T. Courtois is a cryptologist and a Senior Lecturer at University College London. He was born in Poland, received his PhD from the Paris 6 University, and then he worked as a cryptographic engineer for the French smart card industry. He is a highly influential code-breaker with more than 100 regular publications and more than 6000 citations. He has pioneered and/or achieved significant results in all of the following areas of cryptography: Design and analysis of new public key cryptosystems (Sflash, Quartz, HFE), generalized linear cryptanalysis of block ciphers (Crypto 2004), cryptanalysis of LFSR-based stream ciphers with and without additional memory (Eurocrypt 2003, Crypto 2004, ICISC 2004), efficient algorithms for solving systems of multivariate equations (Eurocrypt 2000), innovative attacks on block ciphers (Asiacrypt 2001, AES'4), alternatives to Grobner bases algorithms (Asiacrypt 2001, FSE 2012), low-data complexity cryptanalysis of block ciphers with SAT Solvers (IMA 2007), self-similarity attacks on block ciphers with black-box reductions (FSE 2008, Cryptologia 2012), advanced differential attacks (SECRYPT 2009), and importantly, in security analysis of major industrial standards and real life cryptographic algorithms used by hundreds of millions of people every day (E0 cipher in Bluetooth, automobile cipher KeeLoq, MiFare Classic Crypto-1 in contactless smart cards).
References
- Alekseychuk, A. N. and L. V. Kovalchuk. 2011. Towards a Theory of Security Evaluation for GOST-like Ciphers against Differential and Linear Cryptanalysis, Preprint http://eprint.iacr.org/2011/489 (9 Sep).
- Bard, G. V., S. V. Ault, and N. T. Courtois. 2012. “Statistics of Random Permutations and the Cryptanalysis Of Periodic Block Ciphers,” Cryptologia, 36(03):240–262.
- Biham, E. and A. Shamir. 1991. “Differential Cryptanalysis of DES-like Cryptosystems,” Journal of Cryptology, 4:3–72. IACR.
- Bogdanov, A., D. Khovratovich, and C. Rechberger. 2011. Biclique Cryptanalysis of the Full AES. In Asiacrypt 2011, LNCS 7073, pp. 344–371.
- Courtois, N. 2011. Algebraic Complexity Reduction and Cryptanalysis of GOST, Preprint, http://eprint.iacr.org/2011/626, (12 November).
- Courtois, N. 2012. “Security Evaluation of GOST 28147–89 in View of International Standardisation,” Cryptologia, 36(1):2–13.
- Courtois, N. 2012. An Improved Differential Attack on Full GOST. Cryptology ePrint Archive, Report 2012/138. http://eprint.iacr.org/2012/138 (15 March).
- Courtois, N. 2013. “Low-Complexity Key Recovery Attacks on GOST Block Cipher,” Cryptologia, 37(1):2–11.
- Courtois, N. and M. Misztal. 2011. First Differential Attack on Full 32-Round GOST, ICICS'11, pp. 216–227. Springer LNCS 7043.
- Courtois, N. and M. Misztal. 2011. Differential Cryptanalysis of GOST. Cryptology ePrint Archive, Report 2011/312. http://eprint.iacr.org/2011/312 (14 June).
- Courtois, N. and M. Misztal. 2012. “Aggregated Differentials and Cryptanalysis of PP-1 and GOST. In CECC 2011, 11th Central European Conference on Cryptology,”. Periodica Mathematica Hungarica, 65(2):1126, doi:10.1007/s10998-012-2983-8.
- Dinur, I., O. Dunkelman, and A. Shamir. 2012. Improved Attacks on Full GOST, FSE 2012, LNCS 7549, pp. 9–28. Early version available at http://eprint.iacr.org/2011/558/.
- Good, I. J. and C. A. Deavours. 1981. Afterword to Marian Rejewski, “How Polish Mathematicians Deciphered the Enigma,” Annals of the History of Computing, 3(3):229–232.
- Kara, O. 2008. “Reflection Cryptanalysis of Some Ciphers,” Indocrypt 2008, LNCS, 5365:294–307.
- Kara, O. and F. Karakoç. 2012. Fixed Points of Special Type and Cryptanalysis of Full GOST. Proceedings CANS 2012, Darmstadt, Germany, December 12-14, Springer LNCS.
- Knudsen, L. R. 1994. Truncated and Higher Order Differentials, FSE, pp. 196–211, LNCS 1008, Springer.
- Kovalchuk, L. V. 2010. “Upper-Bound Estimation of the Average Probabilities of Integer-Valued Differentials in the Composition of Key Adder, Substitution Block, and Shift Operator,” Cybernetics and Systems Analysis, 46(6):936–944.
- Moldovyan, N. A. 2007. Innovative Cryptography, 2nd ed. Boston: Charles River Media.
- Random Permutation Statistics. 2008. Wikipedia, http://en.wikipedia.org/wiki/Random~ permutation statistics. (22 January).
- Rejewski, M. 1981. “How Polish Mathematicians Deciphered the Enigma,” Annals of the History of Computing, 3(3):213–234.
- Rejewski, M. 1982. “Mathematical Solution of the Enigma Cipher,” Cryptologia, 6(1):1–37.
- Rudskoy, V. and A. Dmukh. 2012. Algebraic and Differential Cryptanalysis of GOST: Fact or Fiction. In CTCrypt 2012, Workshop on Current Trends in Cryptology, affiliated with 7th International Computer Science Symposium in Russia (CSR-2012), 2 July Nizhny Novgorod, Russia. An extended abstract is available at https://www.tc26.ru/invite/spisokdoc/CTCrypt_rudskoy.pdf. Slides are available at https://www.tc26.ru/documentary%20materials/CTCrypt%202012/slides/CTCrypt_rudskoy_slides_final.pdf.
- Schneier, B. 1996. Section 14.1 GOST, In Applied Cryptography, 2nd ed., New York: John Wiley and Sons, ISBN 0-471-11709–9.
- Seki, H. and T. Kaneko. 2000. Differential Cryptanalysis of Reduced Rounds of GOST. In SAC 2000, LNCS 2012, pp. 315–323, Springer.
- Shorin, V. V., V. V. Jelezniakov, and E. M. Gabidulin. 2001. Linear and Differential Cryptanalysis of Russian GOST. Preprint submitted to Elsevier Preprint, 4 April.
- Zabotin, I. A., G. P. Glazkov, and V. B. Isaeva. 1989. Cryptographic Protection for Information Processing Systems, Government Standard of the USSR, GOST 28147–89, Government Committee of the USSR for Standards.