?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.Abstract
In this article we study the quality of permutations in historical cipher machines from Germany, Spain, Italy, Norway, Switzerland, Japan, Hungary, Croatia, Poland, Czechoslovakia, Russia and the United States. We show that numerous real-life rotors have been made in order to imitate or tend to a certain ideal property related to latin squares. Rotors from the same source and the same period have consistent properties deeply rooted in classical cryptography of polyalphabetical ciphers. We demonstrate this based on probabilities: random occurrence of permutations having such features is unlikely, or would amount to winning in a lottery several times in row. We put all this in the context of known historical sources on how cipher machines and cryptanalysis have developed on both German and Allied sides. We also exhibit strong linear and differential properties. The same occurs in Fialka cipher machines. Finally, a stronger property holds for the historical block cipher T-310.
1. Introduction
All works on cryptanalysis of Enigma known to the authors, from the 1930s until now, have assumed that rotors are just permutations and do not exhibit any particular weakness or internal structure. This was also what Hebern recommended explicitly in the 1920s. However, very clearly most rotors are NOT random permutations as we are going to show in this article. The main question we study here, is a form of reverse engineering of Enigma, which was previously studied very carefully by Rejewski in the 1930s and by Turing, cf. page 16 in Turing (Citation1940). However we are asking questions deeper than recovering the connections of the rotors. We would like to know how a permutation inside a rotor was made or decided. A broader question is the design criteria for cryptographic components: how a long term cryptographic setup is generated, selected and approved for official use. In contemporary cryptology considerable attention is paid to the design criteria for block cipher functional components. Permutations implemented by the Enigma rotors represent a natural equivalent of these blocks, however we are not aware of any contemporary study of their selection process and security.
For block ciphers, this problem was carefully studied ever since the 1970s. For the Cold War T-310 block cipher there was a question of a “long-term key” cf. (Courtois, Drobick, and Schmeh Citation2018) and (Courtois et al. Citation2017) for more details. Likewise the question was studied for DES (cf. Courtois et al. Citation2003; Meyer and Vaudenay Citation2017) and later for AES etc. This question is however inevitably older. In this article we will show that many historical cipher machines already had carefully chosen components which do satisfy some properties, which make them systematically, substantially different than a random permutation. What is more, the difference is actually visible and detectable.
It is important to see that our problem is not quite the same as with block ciphers. We have abundant literature about how permutations in block ciphers (S-boxes) can be weak or strong. For example, some well chosen permutations such as the inverse S-box (Courtois Citation2005) were chosen to resist basic attacks on block ciphers, which is how the AES S-box has been chosen and standardised. More recently, a topic of non-linear invariant attacks have been popular among researchers, and the corresponding notion of anti-invariant resistance for bijective S-boxes was proposed by Calderini (Citation2015, Citation2018). However the invariant resistance notions for permutations is natural and relative to the vector space structure of and the key in the block ciphers is about transforming affine spaces into other affine spaces. In rotor machines the key is applied by rotation of the rotor, which corresponds to +1 mod 26 without a rich multi-dimensional vector space structure. We therefore need to work in a different way.
The main research question, already studied in classical cryptanalysis literature in the first half of 20th century, was about encryption with multiple “permuted alphabets” cf. Section 7.1 in Bauer (Citation2006). The main question we study here is what happens when you derive several encryption alphabets for different encryption keys. Then an ideal situation, is when different keys lead to totally distinct encryption letter, and we have a latin square. In this article we show that most Enigma rotors, for an unknown reason which almost certainly lies in classical cryptanalysis, were chosen to approximate this ideal situation (which itself is hard to achieve cf. Section 8.3). In addition, we show that some rotors have substantially stronger properties and rotors which come from the same source and the same period are similar.
This article is organised as follows. In Section 2, we study how engineering and later code breaking have shaped the devleopement of cipher machines in the early XXth century. In Section 3, we look in more detail at the development of cipher machines in Germany. In Section 4, we examine the history of various rotors used in known Enigma cipher machines. In Section 5 rodding attack, and in Section 6 we study how it works. In Section 7 we study one extremely strange old historical rotor. Then in Section 8 we show that most Enigma rotors ever made are concerned by a broader question of latin squares, and we discuss how we can measure the distance from the ideal situation and report some statistics computed for random permutations. In Section 9 we look at another famous rotor machine, Fialka. Finally, in Section 10, we will show that quite strangely a similar property was mandated, again, for a block cipher machine T-310, which was in widespread use in Eastern Germany in the 1980s.
2. Historical background on development of rotor machines
The history of electro-mechanical cipher machines starts towards the end of World War One. Earliest rotor ciphering machines have been proposed during and immediately after the end of WWI by several inventors working independently from each other. The first known attempt to construct a ciphering machine was undertaken in or around 1915, by two officers of the Royal Dutch Navy, Hengelo and Spengler (cf. Leeuw Citation2003). Although their nominal experience was focussed around the construction of the naval mines and torpedoes, their engineering skills proved to be sufficient for the construction of the ciphering machine. Initially, constructors cared primarily about reliable operation: speeding up the encryption tasks and making them less error prone, rather than about security. In parallel to their efforts, an American, Edward Hebern, started patenting a series of ciphering machines of growing complexity. Hebern’s initial idea back in 1912–1914 with US patent US1912682933A, was connecting two electrical typewrites with the mesh of reconfigurable wires. This yielded a simple monoalphabetic substitution, a cipher whose methods of breaking was known for about a thousand years (AlKindi frequency analysis). His next step - a single moving rotor between the keyboard and the printhead – improved the situation only slightly in 1921, with US Patent 1510441A. His machine was generating a polyalphabetic substitution cipher with a constant period equal to the length of the alphabet. The ultimate design of Hebern was US Patent 1683072A of 1923 granted in 1928. A machine with five rotors moving regularly in an odometer fashion. It increased the length of the period drastically. Compared to Enigma in Hebern cipher machines, the current was flowing just once and in one direction through all the rotors. Inside this patent, Hebern makes numerous claims about randomness and security of his machine. It allows complex movement with levers moving other wheel after full revolution, and several wheels could move simultaneously. Moreover he explicitly states that “each code wheel is wired at random and differently,” which is not quite what actually happened later when cipher machines achieved wider adoption, as we will discover in this article.
2.1. Engineering meets cryptography - United States
Hebern’s professional background was rather distant from cryptology: he was basically a carpenter who became a construction contractor. Hebern attempted to sell his machine both to the US Army and the US Navy, succeeding only marginally and in an indirect way. In 1922 Hebern built for his company a monumental two-storey Gothic building in Oakland, California. Yet for a few more years the company didn’t sell a single cipher machine. Hebern’s commercial offer was rejected by the US Army when its chief cryptologist, William Friedman, unknowingly to Hebern, cryptanalysed his cipher machine around 1922, (Simpson Citation2020), and this without knowing the wiring of the rotors. Maybe Hebern started too early: extremely few customers ever bought his cipher machines. Eventually the building was repossessed due to unpaid debt, and his glorious pioneering Electric Code Company business collapsed.
In parallel with business and engineering development of the rotor ciphering machines, these cryptographic innovations have attracted the attention of professional cryptographers of the time. Experts started to study the initial designs concentrating on security, rather than on commercial or engineering questions. Hebern did not know that the US military had decided, starting 1926, to re-develop his inventions (cf. Mucklow Citation2015). The goal was strengthening their security, however without his participation, and without paying him any royalties. It was only in the 1950s that his family managed to obtain, as a compensation for obvious violations of Hebern’s patent rights, a rather ridiculous or simply inadequate sum of 30 thousand US dollars.
2.2. Engineering meets code breakers
We see that cipher machines were developed by engineers and business people, and initially none of them had any direct or earlier contact with cryptology. Therefore, it is not surprising that some of their ideas were a bit naive, from the contemporary perspective. The commercial offer by Hebern was also rejected by the US Navy. Here again the (same) cipher was broken by Agnes Meyer Driscoll, one of the Navy’s leading code breakers of this era (Johnson Citation2015). Her success resulted in Hebern’s decision to employ Driscoll as a cryptologic consultant at his company, cf. Friedman Citation1973.
We should not under-estimate the importance of these early years of machine crypto history in 1920-1939. This is a period before designers have managed to complicate machines’ construction, or before the market would allow more complex and more costly machines to be developed, introducing complex irregular rotor movement (e.g. SIGABA) and additional wired substitutions in a form of a plugboard etc. We claim that only in this period certain fine questions about cipher design would be studied because code breakers had specific historical attacks in mind, and worked initially with ciphers which were not too complex and were breakable by manual methods. According to Driscoll (Citation1889), for an extensive period of time from 1924 until approximately 1940 Agnes Driscoll worked on various Japanese codes and ciphers which were very important for the U.S. Navy. In October 1940, Agnes Driscoll was transferred to a team working on German naval Enigma. Here, according to Encyclopedia Britannica, she worked for two years in old fashioned ways, without mathematics, without machine support and without any success. Reportedly she refused help on Enigma from Bletchley Park code breakers, who travelled to US to advise her. It would be, in these early days of Hebern and Friedman, where ciphers were not yet very complex, an important line of defense, would a very careful selection of the permutations defining rotor’s wiring. That question represented a problem well known among the cryptologists of this period, as it appeared in a very similar form in the design of the classical (manual) polyalphabetic ciphers. A well known reference is the French de Viaris Attack cf. Section 14 in Bauer (Citation2006) which was later studied and improved by Friedman. Marquis Gaëtan Henri Léon de Viaris was, after Babbage, the first scholar to use mathematics in cryptology as early as 1888 (cf. Bauer Citation2006).
2.3. Not random rotors after all
In this article we will discover that designers of German Enigma started to pay attention to the proper selection of the rotors’ substitutions also very early. Conscious of the existence of the letter frequency attack on the monoalphabetic substitution cipher, designers of the polyalphabetic ciphers attempted to achieve the possibly uniform letter frequency distribution in the ciphertext. One of the ways leading to that goal, was ensuring that the table of different encryption alphabets (corresponding to a polyalphabetic substitution) would represent a Latin square. This approach is directly applicable to the design of the rotor wiring. However a perfect latin square can hardly be achieved, as we will see later in Section 8.3. What remains is to approximate a latin square. In this article we will see that numerous historical Enigma rotors have such properties. We will also see that this is closely related to the so called “rodding” attack, which is how “everybody” has broken early rotor machines according to Batey (Citation2008). We will see that Germany had serious crypto expertise, they were also breaking Enigma of other nations, and were well aware of its weak points. This is why they made their military Enigma a lot more complex than other countries (with a stecker) as early as 1930.
3. Machine cipher and crypto engineering in Germany
In 1918, a German engineer, Arthur Scherbius, filed a patent application for the device which was later to turn into the most famous cipher machine in history - the Enigma. Scherbius specialised in several disciplines of mechanical and electrical engineering, such as technical ceramics or control of water and steam turbines, and before patenting his invention he had no direct contact with cryptology. His apprentice and successor was Willi Korn. Initially Scherbius and Korn they worked at Gewerkschaft Securitas of Berlin, the original company of Arthur Scherbius. In some countries, patents were filed by the German Securitas, (later Chiffriermaschinen AG 1) whilst the same patent was filed in other countries by the Dutch Securitas branch. This was probably done to avoid claims that, after WWI, Germany wasn’t allowed to develop and produce certain high-tech equipment as part of the Treaty of Versailles. After the unexplained death of Scherbius in 1929, cf. page 114 in Bauer (Citation2006), this company was officially dissolved and was taken over by another company known as Chiffriermaschinen Gessellschaft Heimsoeth und Rinke.
The development of Enigma rotor machines started with Hebern and commercial Enigma in the 1920s. Our brief review of known information about the inventors of the earliest rotor machines suggests that we should look at their creations primarily from an engineering point of view. They were concentrating on speed, reliability, portability and ease of use. Their complexity was not very high. We then see that the systematic study of these machines by cryptologists went a long away, with progressive development of powerful attacks. At no moment in the history of cryptology it is business as usual, and we have rarely run out of new disturbing discoveries. Even today, we are discovering new, weak points of Enigma cipher machines, as we will see below.
3.1. Engineering meets cryptanalysis again in Germany
In Germany, the development of Enigma cipher machines is attributed to Willi Korn, cf. page 114 in Bauer (Citation2006). His name is very rarely mentioned by other German cryptologists, and the main source of information about his work and ideas are the numerous patents on cipher machines he filed in his name in 1926-1930. We also have the final product: numerous versions of Enigma machines themselves, see Section 4 below. Numerous documents state very clearly that Korn had for a very long time collaborated with Wilhelm Fenner cf. (Alvarez Citation2007) and (“Further interrogation of” Citation2017). Fenner had worked in decryption of foreign communications since 1922 and was later director of cryptanalysis section of the Signal Intelligence Agency of the Supreme Command German Armed forces, commonly known as OKW/Chi (Alvarez Citation2007). He reported to Rudolph Schmidt, major of the general staff.
Willi Korn was the chief engineer at Heimsoeth&Rinke, based in Berlin, and continued working there until at least 1942. Design decisions made by Korn in early periods of Enigma development have had serious adverse consequences. Korn is responsible for the invention and introduction into Enigma construction of the reflector (Umkehrwalze). A reflector is a brilliant way to use the permutations of the rotors twice and therefore we could (very naively) believe that Korn’s Engima with one reflector and three rotors has as much (apparent) complexity as a Hebern-type machine with seven rotors. Reciprocity between encryption and decryption also somewhat simplified the machine’s use. However this comes at the price of two fundamental cryptographic weaknesses: permutations generated belong to a substantially smaller set of self-reciprocal permutations (a.k.a. involutions), and the fact that a letter does not encrypt to itself. Thus, every single of multiple alphabets generated by an Enigma machine is an involution without fixed points. For some years prior to 1939, Fenner operated a small section with Fritz Menzer, where the security of their own Enigmas was studied (Army Security Agency Citation1946). Fenner said that Menzer indicated the possibility of a solution and made suggestions for the necessary improvement on Engima cipher machines (Armed Forces Security Agency Citation1950).
3.2. Short history of German Enigma with a stecker
A crucial question is one of adoption of Enigma with a stecker for military use. Starting from 1925 the German Reichsmarine started experimenting with Enigma C, without a stecker (). Then it seems that Germany decided to make these machines more complex and more secure. In the Reichswehr, another model, Enigma G, was introduced in July 1928 by Major Rudolf Shmidt. It had a relatively complex rotor movement for that time (with multiple rotor turn-overs) but it did not have a stecker. Even though according to cryptomuseum.com there existed historically one version of Enigma G with a stecker, there is no evidence that such machines were actually used. One version of Enigma G, also without a stecker, is now commonly known as the Abwehr Enigma.
On 1 June 1930, the German army introduced another different Enigma machine, with simpler odometer-like rotor movement (a.k.a. cyclometric method) and with a stecker. This machine is known under the name of Enigma I of the Heer, Wehrmacht Enigma, German military Enigma or Service Enigma. It is also known under later names of M1, M2 and M3 which were in fact successive compatible versions produced in large quantities. In 1934 the Reichswehr also finally agreed to accept this same Enigma as a common version, as it was necessary for different armed forces to communicate with each other. In August 1935, the same Enigma was also adopted by the Luftwaffe (Bauer Citation2006).
4. Short history of enigma rotors
From available sources, we assume that work on the exact wiring of Enigma rotors was done by the main historical Enigma developer and serial inventor Willi Korn, known from numerous patents on Enigma cryptography from 1926 to 1930. Some important information can be found in post-war TICOM interrogations of two German cryptologists Dr. Huettenhein and Dr. Fricke which occurred on 25 August 1945 and declassified in 2017 (cf. “Further interrogation of” Citation2017). The crucial question of who made the wiring of various Enigma rotors, was then asked explicitly, on behalf of Mr. Friedman of the NSA himself, who as we know was involved in development of rotor machines since the very beginning. Dr. Huettenhein responded that Willi Korn was the principal person who developed the machines, in collaboration with Fenner, and that they were based in Berlin in Uhlanstrasse. The wheels for the army and air were made by Konsky&Krüger, in Chausseestrasse, Berlin, a small firm which probably made only Enigma machines. The naval machines were made by Ertel in Munich. Some other non-specified machines were also made by Olympia typewriter company in Erfurt, which later also made variable-notch rotors (Lueckenfuellerwalze).
In early 1930s the army released for use by Enigma operators only three rotors I, II, and III. On 15 December 1938, two more rotors were added, IV and V. In 1938, the Heer (German navy) added three more rotors, VI, VII and VIII. The British recovered rotors VI and VII from the crew of U-33 in February 1940, while rotor VIII was captured in August 1940 (cf. Erskine and Enigma Citation1988). Two more new wheels known as Beta and Gamma, were introduced for the naval Enigma M4 model only, on 1 July 1943, see page 4 in Bletchley Park (Citation1944). Then, maybe surprisingly, all these rotors remained in active use until 1945: probably because it would have been too costly to replace them, and also because the machine was overall considered to be very secure. In fact, Germany was very careful as to make Enigma substantially stronger with a stecker, which most other countries did not have, not even in 1945. The complexity of a stecker is very high, equivalent to as many as 47 bits of entropy. This led to a high cost of decrypting Enigma communications by Britain during WW2, which was without any doubt enormous.
4.1. Recovering the Enigma rotor wiring by code breakers
One rotor in Enigma could be a permutation chosen uniformly at random. There are 26! possible wirings for one rotor, therefore the entropy of one rotor is about 88 bits. For this reason recovering the unknown rotors was a big challenge. These rotors could have been obtained from some sort of “pinch” on German military equipment, or provided by a spy or a traitor. However, as far as we know, this did not happen. We know that the French had a spy in the German Armed Forces’ Cipher Office, Hans Thilo-Schmidt, and who was the brother of Rudolf Schmidt mentioned earlier. This spy provided operation manuals, genuine examples of plaintext, ciphertext, and some keys used in realistic circumstances. He also provided countless other documents not directly relevant here, including documents about 14 French diplomatic codes broken by German code breakers. A total of 285 or maybe 303 documents depending on the source (Dumas Citation1997). Out of these, exactly 10 are technical documents on Enigma cipher machines (cf. Bouchaudy Citation2021). However, he NEVER transmitted to any allied intelligence service, the actual connections of any of the Enigma rotors. It is therefore logical to believe that Hans Thilo-Schmidt was a spy trying to do only limited harm, and it is difficult to agree with the title of Kahn (Citation2009) if we limit ourselves to Enigma. The information transmitted (sold for large sums of money) was without doubt valuable and had serious short term benefits (learning about the machine such as decryption with known keys). However he did not do everything which was in his power to help the foreign intelligence services to defeat Enigma (which are supposed to be strong even it falls into enemy hands according to famous Kerckhoffs’ principle). From this information, a Polish mathematician Marian Rejewski was able to reverse engineer Enigma rotors by mathematical techniques (Lawrence Citation2005) in the early 1930s. It is also possible that the fact that only 10 documents were about Enigma, simply means that the French intelligence have under-estimated the importance of Enigma cipher machines back in early 1930s, and simply did not ask their agent to provide more information about them.
The methodology to recover unknown rotors was through study of mathematical theory of permutations, and specifically, through solving the set of so called Rejewski equations which have later been studied by Lawrence (Citation2005). The fact that this task was actually possible to do, was much later called by David Kahn “the greatest breakthrough in cryptanalysis in a thousand years.” In Kahn (Citation2009), David Kahn wrote: “Poland had greater cryptanalytic ability […] only one of the three to employ mathematicians […] and only mathematics could make it possible to reconstruct the Enigma rotor’s internal wirings.” This information and some actual rotors and actual complete working clones of military Enigma cipher machines produced by a secret factory at a company known as AVA in Poland, was then shared with the French and the British intelligence services. It is worth noticing that Alan Turing has also studied in depth the question of recovering the rotors of Enigma. This precise question occupies very substantial space in his book (Turing Citation1940) starting from page 16. Alan Turing worked with the so called “boxes” formed by showing the cyclical structure when composing two involutions without cycles. In page 17, Turing says that both involutions can be recovered from “boxes,” or in effect that such permutations can be uniquely factored. Turing does not say where this fact comes from. In fact it is a well-known theorem of Rejewski, cf. Section 13.8 in (Courtois Citation2011), Section 3 in (Rejewski Citation1940), and pages 9–10 in (Pommerening Citation2008). A recent paper shows that it is an imperfect method with some difficulties (Kuhl Citation2007).
4.2. Rewiring and peripheral smaller scale or late adoption
Copies of commercial Enigma were sold or donated to a number of countries such as Switzerland, Hungary and Japan, many of which made a seemingly reasonable decision to rewire their rotors before use. Intelligence service of Norway, which have been using seised military Enigmas for some time after the end of WWII, made a similar decision. we discovered, however; that cryptologists of these countries typically understood their security at a lower level than their original designers. Our research below shows that these rewired machines such as in Norway Enigma represent lower quality substitutions than the rotors selected for German military use, see our later . German cryptographer Buggisch testified that Germany equipped Hungary, Finland, Romania, Italy and Japan with a more secure military Enigma (cf. TICOM/I-9292 Citation1945). He also clearly says that they deliberately supplied less secure machines without a stecker to Croatia, fearing they would be selling information to the British. Rotors for the Croatian Enigma were made by Konsky& Krueger in Berlin. From here German code breakers were able to know their connections from the start, and they decrypted Croatian army communications extremely easily (cf. Christos Citation2017). Buggisch said very clearly that breaking Croat Enigma was “not an outstanding cryptanalytic achievement.”
Table 1. Collisions and entropy of one column for selected historical rotors.
4.3. Weak German rotors and mystery questions
In addition, it is impossible to claim that all German Enigma rotors are OK. The first three from early 1930s are clearly not OK. In this article we show that the old rotor III in the original, military Enigma model I (common with the Kriegsmarine’s models M-3 and later M-4) is very special and clearly weak. Isolated nature of this phenomenon prevents us from drawing solid conclusions from our findings. It seems unlikely that the particular structure of this rotor’s wiring alone translates directly into a serious weakness. All our findings are simply and primarily a reflection of the cryptographic expertise which existed at the time. It seems that almost nobody (except for Swiss and Norwegian Enigma and U.S. Sigaba cipher machines) followed the recommendation of Hebern about using rotors chosen at random.
This question remains very important until today in modern cryptography: for example when AES/Rijndael was designed in late 1990s, many authors suggested using a random permutation on 8 bits, which is not at all what the designers did. There exist numerous contemporary works which examine the choice of cipher components à posteriori, looking for hidden properties (cf. Courtois et al. Citation2003; Courtois et al. Citation2015). We discover that there exist, permanently and since the 1920s, two schools of thought in cipher design: random permutations and relying on complexity of the cipher, since Hebern, or a more refined study of properties of small components (rotors, S-boxes, Boolean functions) and specific (strong) choices which are very far from being random. This dichotomy was very clearly visible in the AES cipher competition in 1997–2000. In many cases, no one can say if some weakness can or can not be compensated by more rounds in a block cipher, or by more rotors in a rotor machine. For example the Russian Fialka machine has as many as 10 rotors, yet the rotors are certainly not random permutations, see Section 9. Can a combination of 2,3,…10 such special rotors be distinguished from a random permutation? Can such a combination be factored in order to recover individual rotors? New attacks are found in cryptography on a regular basis and these questions need yet to be studied.
4.4. A permutation impossible to recover unless… it is trivial
A major difficulty is to simply obtain some secret permutation used inside an enemy encryption system. We need to realise how difficult this question can be, well in theory. One famous permutation which code breakers at Bletchley Park did not have was the famous QUERTZU question, which Turing called the diagonal and the question of recovering it is also studied in Turing (Citation1940). Initially, not knowing how keyboard was connected to the machine, Dilly Knox was effectively discouraged to ever try to break German military Enigma, and initially has studied this question as a theoretical one. Until 1937, Britain was essentially not trying to intercept and collect encrypted messages actually transmitted by the German army (Batey Citation2008). A serious obstacle, which was completely impossible to just guess, there are 26! possibilities, which is an extremely large number, about 2 Dilly was shocked when Polish code breakers told him in Pyry in 1939 that this initial super secret permutation was actually that A was connected to A, B to B etc.
If we study this question from the point of view of one rotor, the question of the initial permutation does not seem very interesting, it amounts to renaming a metallic contact called Q to be now called A, etc. In this article we show some surprising facts: Enigma rotors have NOT been generated at random and they are NOT agnostic w.r.t. the order in which contacts are named. One old German military Enigma rotor reveals a hidden property when we name contacts in the alphabetic order, a property which could be overlooked if we name the contacts differently, and was probably overlooked, as we are the first to show this property. First however, we need to study a well known old attack on Enigma.
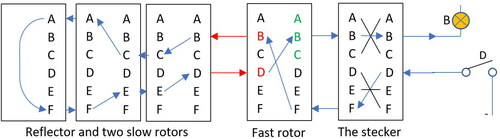
5. Rodding attack or undoing the effect of the fast rotor
Officially, the rodding attack was known and studied in Bletchley Park around 1935, and is typically and attributed to Dilly Knox. However, this attack is almost certainly older. According to Batey (Citation2008) who worked for and under direction of Dilly, “everybody who tried cryptanalysis of the commercial Enigma machine arrived at the rod solution.” This attack was basically known to many other intelligence services worldwide, including France and probably the US. It actually had a French name, Les Bâtons and few other names such as Strips or Isomorphs. Since 1935 French and British intelligence services had collaborated very closely on monitoring and decryption of Italian Enigma traffic in the Spanish Civil War. Another name for this attack is the Method of Isomorphs and it was made public in 1946 by a New York-based cryptography lecturer Rosario Candela (cf. Bauer Citation2006). However, strangely the attack was not known to Rejewski in Poland in 1939, Good & Deavours Citation1981. We are also nearly certain that this attack was known in Germany. According to page 281 in Bauer (Citation2006) knowledge of this attack was the MAIN reason for the introduction as early as 1930, of the stecker in military Enigma machines.
An interesting question is that the rodding attack is relatively simple and it can be implemented in many different ways, with sticks, paper strips, or 26 × 26 squares known as rod square and inverse rod square in Alan Turing Prof’s Book (Turing Citation1940). From available sources (Foss Citation2001), we learn that even though Dilly Knox purchased a commercial Enigma in 1925, and Foss had in 1929 already understood that it was breakable with a crib, Foss has later admitted that his earlier methods were “cumbersome” and Foss attributes the invention of a more practical method, the rodding method, to Dilly (Batey Citation2008). Here, the date of this invention is very far from being clear: it could be at any moment between Foss’ report from 1929 and April 1937 when Knox was already able to break into Italian-Spanish Enigma traffic (Batey Citation2008). This was not without an additional difficulty: the rotor connections were also to be recovered in the process. Overall, reading Batey we are inclined to believe that the date when Dilly Knox would discover the rodding attack is closer to 1935 than to 1929. Some sources claim that Foss invented this attack as early as 1927 (Bauer Citation2006), maybe in some early form. Trying to reconcile these conflicting sources with what we discover in this article, we are in fact inclined to believe that this attack could be known in Germany as early as 1930, and possibly before it was known in England or in France. If Germany did not study this very major weakness in Enigma, why would they have made the stecker mandatory as early as 1930? The answer could be because the attack was known, which is also claimed in page 281 of Bauer (Citation2006).
5.1. Germany against Engima type K without a stecker
Another serious argument to support this claim is that according to various sources, both Germany and the United States were able to break into Swiss WW2 Enigma traffic, reading it, pretty much throughout the war and until 1945. Swiss Enigma was of type K without a stecker and operating procedures were not very strong (cf. Jennings Citation2018). The same applied to Germany reading the messages encrypted with the CroatianFootnote1 Enigma which was also of type K without a stecker cf. Section 4.3. This was reportedly extremely simple and done by hand, with “wiring charts” and with short cribs (TICOM/I-9292 Citation1945; Christos Citation2017).
Initially, at Bletchley Park, colonel Tiltman was able to read Swiss diplomatic traffic starting from September 1939 (cf. Hamer, Sullivan, and Weierud Citation1998). One source of information on solving Swiss Enigma in Germany is Army Security Agency (Citation1946) where we read that a certain Lt. Kunze was Chief of Swiss substection at OKW/Chi in charge of decrypting Swiss traffic which “was regularly read” in Germany. Then, in 1942, machine was modified and later the Swiss traffic remained unsolved (cf. TICOM/I-200200 Citation1946), at least at OKW/Chi. In fact, following a recent book by Jennings there was another specialist of Swiss Enigma traffic, Dr. Bruno Kröger, expert at Forschungsamt, a rival agency, who “worked hard to break the secrets of the Swiss Enigma” (Jennings Citation2018) apparently without any coordination with OKW/Chi. It is clear the Swiss did not use the machine correctly: initially large numbers of messages were encrypted with the same key (cf. Jennings Citation2018). According to Jennings, Swiss trafic was read longer, until early 1944 by Kröger and his team at Forschungsamt. They gave up on it after Swiss Enigma operators have updated their operational procedures to use a random key and change the order of wheels for each message, which made decryption too costly.
All the attacks mentioned above are expected to be close cousins of the rodding attack and took place in the 1940s. In this article however we hypothesise that this type of attack was studied already in early 1930s. We will argue that, while historical documents are scarce, certain claims are highly plausible based on probabilities, with a reference being a random permutation. This will be reinforced by observing that rotors which come from the same source behave in the same consistent way.
6. Rodding – various variants of the same attack
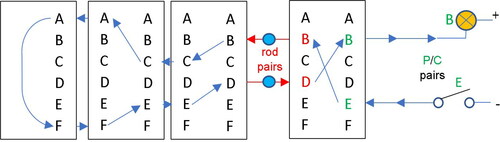
An important question is one of how the rodding attack can exist in many different conceptual forms with incompatible implementations (). A certain pattern which will be visible in our implementation of the rodding attack, cf. , will not be apparent in another implementation.
Figure 3. A strange order of letters with old wartime rotor III, see Courtois Citation2020.

Our implementation of the rodding attack is simplified, and the same as the Method of Isomorphs using the so called “rotated Enigma alphabets,” cf. page 253 in Bauer (Citation2006). It was initially designed as a student exercise during and after our annual Bletchley Park trip (Courtois, Citation2020) and our table is actually the same as displayed in page 126 in Bauer (Citation2006), except that we do it for a different rotor. Rodding is about pairs of letters which occur at the border between the fast rotor and two slow rotors inside an Enigma machine, which following Dilly Knox and Alan Turing, we call “Rod Pairs.” cf. Def. 6.2 below.
We also work with “Rod Pairs,” however our version of the attack is actually greatly simplified and different from how this attack was traditionallyFootnote2 studied and implemented in Britain, which may seem more complicated. We will stick to the basic “mathematical” versionFootnote3 of how the rodding attack works. It consists of creating some fixed tables, which allows us to then decrypt the plaintext and ciphertext letters one round backwards, to obtain possible rod letters. This partial decryption is attempted several times for each position of the fast rotor. In order to implement this we use a 26 × 26 tableFootnote4 to represent all the possible ways in which the fast rotor can be decrypted 1 step forward from a plaintext letter or one step in the backwards direction after a ciphertext letter.
In each case, the attacker produces an ephemeral table of rod pairs for this encryption. In this table, assuming that the fast rotor is not moving, the same letters should give consistent answers. This process is further enhanced by using the fact this transformation is expected to be an involution. From here the attacker will typically obtain a contradiction very quickly after examining just a few letters and without recovering the whole mapping. A contradiction indicates that his initial guess about the position of the fast and rightmost rotor was incorrect. One short example of how this can be done can be found in Section 14.5.2 in Bauer (Citation2006), another in Exercise 2 in Courtois (Citation2020).
6.1. Rod letters, letter, number and rotor encoding conventions
We define, for the purpose of this paper:
Definition 6.2
(Rod Letter). We call a “Rod Letter” a letter corresponding to a wire active at the border between the fast rotor and 2 slow rotors inside an Enigma machine.
Remark.
This letter corresponds to a set 26 physical contacts inside a machine, where the current leaves one rotor and goes into another rotor. The same rod letter can have different names, for example the rotor contact we call A would be called Q in Prof’s book by Turing (Citation1940). The situation is a bit simpler with numbers. Alan Turing has a convention to code letter Q with 1, the same letter which we call A will be denoted 0 in this paper: this is because we make extensive use of arithmetic modulo 26. In general if Alan Turing uses number k we should use k – 1 modulo 26. In reality however we end up using the same number, k, as Turing starts numbering relative to a different starting column, as explained below. Therefore at the end many numbers we use would be entirely compatible with work of Turing, except that we will not use number 26, it is replaced by 0 as we work modulo 26.
For rotor specification, we do in this paper use the same conventions as in 100% of modern works on Enigma known to us, cf. cryptomuseum.com, (Fuensanta, López-Brea Espiau, and Weierud Citation2010), etc. An interesting observation is that the original position where a wheel is assumed to start or not move (a base position or neutral position with i = 0 in this paper) is then bound to differ by 1 step compared with the work of Turing. In page 6 of Turing (Citation1940) the description of the actual wiring of rotor start with a mapping of Q to Z or 1 to 6 for a Railway rotor. We recall the Enigma simulators such as https://cryptii.com/pipes/enigma-machine take into account the fact that in a real-life Enigma machine, the fast rotor rotates by one position and only then the first ciphertext letter is produced. This means that if an Enigma simulator shows AAZ in the window, and if the ringstellung is in a neutral position which is AAA, then the actual position of rotors used in encryption is AAA. If we compare how the Enigma rotor is typically described in modern sources, the Railway rotor is described by:
Which in our coding is 9,6,3,16 corresponding to output letters JGDQ, for input letters ABCD and in Turing coding the same rotor is encoded by 6,3,16, where the first number 9 will be shifted to the very end and this corresponds to output letters ZEJ for input letters QWE.
6.3. Notation and rotated alphabets
In this paper we denote by ρ a function which rotates the letters by one position, A becomes B etc. We identify 26 letters with numbers A = 0, B = 1, C = 2, etc. Then we also have ρ a function which adds 1 modulo 26. Now let R be a permutation of one rotor:
then at step i the transformation of this rotor will be (which needs to be read form right to left):
6.4. A first glimpse at rotor III
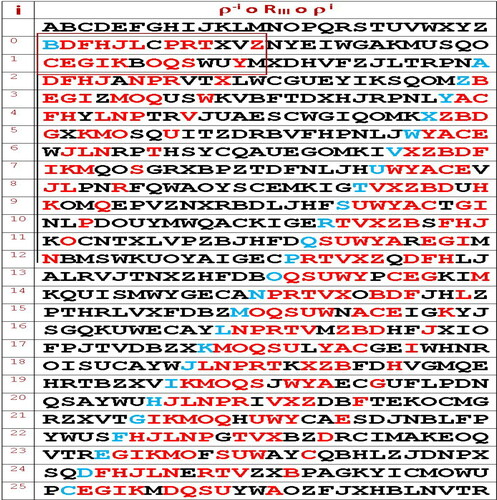
In this article, we show that a very strange order governs the connections of wartime Rotor III. A peculiar order seems to dominate in one corner of our table, and in particular for the first half of inputs A to M, i.e.
There is certainly something not right here. This is an extremely strong property. The full pattern will be shown here below in .
6.5. Permuted letter variants
An interesting question is why this property was not discovered before. A plausible explanation on why this property would not be by discovered by Turing, is that in his book, letters in an Enigma rotor were named not ABC like in the present article, but using an older QWERTZU ordering. The exact same Enigma metallic contact will the have a different name, Q not A, W not B etc. This is what Alan Turing advocates explicitly, as naming contacts the “Cryptographer’s” way. In addition, our table is very different than the “Rod Square” and the “Inverse Rod Square” tables studied by Turing and presumably defined earlier by Knox. Our table is more basic: all it does is to represent a list of rotated alphabets: effectively each line simply represents the wiring of our rotor, when it is moved to a different position. Therefore, it is possible that this extremely strong pattern we see here was simply not noticed at Bletchley Park during the war, because the columns would be permuted, or that rodding was primarily studied for a different set of rotors (e.g. Spanish/Italian rotors).
7. The full table of permuted alphabets for the original rotor III
In the table below, we write, in the first line the permutation of the military Enigma Rotor III. Then, below we write the permutation obtained where this rotor moves one step forward (which is anti-clockwise if we look at an Enigma machine from the right hind side). Likewise, for any we display the same permutation when our rotor moves by one position. This is the same table as in page 185 in Ulbricht (Citation2005) which computed the table for many different rotors, and in page 126 in Bauer (Citation2006) where it was done only for Rotor I.
We recall that ρ is a function which rotates the letters by one position, with A = 0 mapped to B = 1 etc. We observe that the following affine approximation holds for all entries in colour:
Fact 7.1 (Linear Approximation).
7.2. On linear cryptanalysis of Enigma
This is nothing else than a linear approximation, which is linear modulo 26, of an old Enigma rotor, presumably from 1930. Who says that linear cryptanalysis was invented in 1990s and was not known to the designers of DES? In fact linear approximations of non-linear cipher components were already studied in 1970s for the block ciphers SKS V/1 and T-310 (cf. Courtois, Oprisanu, and Schmeh Citation2018) and possibly it is even older. However we do not think that the way this property could or should be used in cryptanalysis will have a lot to do with linear cryptanalysis of block ciphers. This is because other components of our cipher do not have good linear approximations.
7.3. An important observation
It is easy to see linear approximation for our table will behave in a way which is a bit counter-intuitive. Indeed it holds for a large proportion of 26 values not 26, for any i, j. How is this possible? Should not the probability be negligible for so many values? We have the following result:
Theorem 7.4
(Conjugation Property). Let a, b be two fixed integers. We fix i and we consider the probability (over all ) that we have:
This probability is the same for every i, and for every j. Consequently, the number of coloured letters is the same in every line in our square, and also in every column, cf. . This probability is also the same for every letter y where is the letter displayed. Consequently, the number of coloured letters is the same for every letter.
Proof.
We prove the first result by induction on i, modulo 26 we can start from any point. We assume that for some i. We apply ρ on both sides and we replace x by
modulo 26, which is a bijective transformation:
which gives us the same probability over
for i − 1:
We see that if we have k solutions x for one i, we can produce also k solutions z for i − 1. Moreover after 26 steps we can back to the same place so the number of solutions in this process cannot increase, it must stay constant for every i.
For the second column-wise invariance result we fix i and vary x. It is easy to see that is equivalent to
In each case where
we have also
which is exactly what we expect. Finally the last result, is due y rotating though all possible values in 2nd result, letter y being in coloured in column x was transformed into y + 1 also in colour in column x + 1. □
8. On ideal encryption alphabets or latin squares
8.1. Theory of permuted alphabets in classical cryptography
The classical cryptographic theory of encryption in the first half of 20th century was about multiple “permuted alphabets” cf. Section 7.1 in Bauer (Citation2006) and (Eyraud Citation1953). It was about how multiple variations of one alphabet could be systematically derived from basic building blocks such as iterating certain permutations and transforming them by cyclical shifts. In Section 7.2.5 in Bauer (Citation2006) the cardinality of the set of different rotated versions of the same rotors is discussed, and it is observed that in small sizes, such as with
elements, there are many events where some of these permutations could be identical. However, this type of event coincidences occur with a negligible probability for permutations with N = 26 letters.
8.2. Latin squares
We would like to propose a plausible explanation why the Rotor III has letters in order ABCDEFG in the first column. There is a very famous requirement in classical cryptography (Bauer Citation2006), which is that if we have a collection of 26 encryption alphabets, no character should repeat twice in each column. This property is also known as a latin square, or under the French name of “alphabets réellement non-parallèles.” In mathematics it is equivalent to the notion of a quasi-group, a topic which is studied extensively until this day.
According to Bauer (Citation2006) latin squares were studied in cryptography since the 18th century (Bauer Citation2006). A definition of a latin square appears in the official Bletchley Park dictionary of cryptographic terms from 1944 (cf. Cryptographic Co-ordination and Records Section G.C. & C.S Citation1944). It also appears in page 51 in East german crypto dictionnary of 1971 (cf. Zentrales Chiffrierorgan der DDR Citation1971). They play an important role in optimising the diffusion P-box in DES, cf. page 58 in Brown (Citation1991), and it has been a popular recreational mathematics topic ever since Euler. A few years ago during an international congress of mathematics the community discovered that in fact latin squares are yet older. A confucian scholar and Korean mathematician, Seok-Jeong Choi, published in year 1700 a work known as Gusuryak where he studied magic squares, and presents the first known orthogonal latin square of order 9 (cf. Sangwook Citation2014). This was at least 67 years before Euler has made this topic popular with European mathematicians.
It is easy to see that Enigma Rotor III does not satisfy this requirement, for example in the first column the letter K occurs three times for i = 9, i = 11 and i = 14. Moreover we also have an equivalent of Thm: 7.4 if we shift our values by 1, the probability distribution obtained is the same in each column in , and if one column was a latin square, another would be. Given the state of cryptographic knowledge at the beginning of the 20th century, and the popularity of latin squares over the centuries, this fact alone should also be considered as a weakness in the spirit of classical poly-alphabetic cryptanalysis methods, cf. de Viaris Attack in Section 14 in Bauer (Citation2006) later improved by Friedman.
Therefore cryptologists should in principle design a rotor such that this table is a latin square.
8.3. Can for rotor III be a latin square?
This question is not obvious at all. In fact the requirement of obtaining a latin square for all permuted alphabets for a given rotor, seems an extremely difficult one. We have examined some 70 different historical rotors and also vast numbers of their combinations. We have never obtained a latin square in our table, not even in one case. This fact was already observed for Rotor I in page 138 of Bauer (Citation2006) and the author also says clearly that we should not expect this to happen for other rotors either. Latin squares are hard to make, and there is a famous example of an almost perfect latin square by Mauborgne cf. page 137 in Bauer (Citation2006) which has three exceptions only and can be fixed by permuting three letters.
Table 3. Results for selected historical rotors.
Table 4. Selected values in probability distribution of Imk for random permutations.
Latin squares are very hard to make if all lines in our table need to be obtained from one single rotor. We estimate the probability that we obtain a latin square for a rotor chosen at random to be approximately equal to the probability that there is no repeated characters in the first column, then we compute the first line, and again if we are lucky, there should be no repeated characters. Assuming that both events are approximately independent, this probability will be about:
This argument does not explain how to find a suitable rotor. Until recently it was not clear if there exist efficient algorithm for generating a rotor for Enigma, and in a way such that we obtain a latin square for the set of rotated alphabets.
We have built a software tool based on formal coding and a SAT solver and our software returned UNSAT. Therefore we claim that this problem has no solution for n = 26. An ideal rotor does not exist for N = 26 contacts. More generally, in a companion paper (Courtois, Grajek and Rams Citation2020) we settle this problem once and for all with a mathematical theorem: it turns out that our problem has a solution if and only if N is odd. For example a solution exists for N = 13, one example is LAIFHBKEJDCGM. In fact for odd N, a working solution can be obtained generated in a prescriptive way, with a simple closed formula using modular arithmetic see our Thm. 8.7 below. However such prescriptive solutions would not satisfy the secrecy requirements in cryptography: the attacker should not be able to guess what the rotor connections are.
8.4. On invariance of collisions
In the same way as in Thm. 7.4, we have a property which occurs in the same way for every input of a given rotor, or in every column of our table:
Theorem 8.5
(Rotor Collision Invariance). We consider a rotor such that a collision occurs in one column in our table of rotated alphabets, i.e. there exist two integers (or two lines) and one input letter (column) x such that
Then for each column in our table x we obtain the same number of collisions.
Proof.
We can simply translate our property by c steps for every c, and these translations are one to one:
Example.
For example in , in each column we have four letters concerned by events of this type, with K repeated 3 times at i = 9, 11, 14, N repeated twice for i = 10, 12, P repeated twice with i = 15, 25 and S repeated twice for i = 16, 24. Then in fact in each column we also have four letters concerned by events of this type which are L,O,Q,T in the next column and so on.
8.6. A feasibility result
Theorem 8.7
(On Existence of Quasi-groups Derived From one Single Permutation). For every odd N there exists a rotor with N contacts so that the corresponding table of permutated alphabets (expanding it in the same way as we did in ) generates a quasi group and we get a perfect latin square.
Proof.
For an odd N it is easy to check that the rotor mod N always works for any odd
In line i we have then
mod N which is always a permutation, and each column x we have
mod N which is also always a permutation.
Remark 1.
With our rotor RIII we also had albeit with probability
This strongly suggests that the designers of Enigma in 1930 have studied latin squares and knew how to solve our problem for an odd N. The formula was still somewhat applied.
Remark 2.
Simple prescriptive solutions of this type are not recommended in cryptography. They do not satisfy the secrecy requirements in cryptography: the attacker should not be able to guess what the rotor connections are and it should be possible to keep them secret.
8.8. Historical rotors vs. random permutations
We denote by Ims the size of the image in one column. This corresponds to the number of possible encryptions of one fixed input letter, for example A, by this rotor R, for any rotor position i. This number Ims is the same for every input letter and we have a latin square if and only if Ims = 26. We denote by Ent(R) the entropy of this output which would be a maximum of bits if we had a uniform distribution which is only possible if we had a latin square which is impossible and is never the case in practice, cf. Thm 8.7. In table below we compare our Rotor III to some other rotors. Some further results are also displayed in .
We observe that rotors from the same source are very similar. We have examined some 63 different real-life historical Enigma rotors. On average, the entropy is 4.39 while it is 3.87 for a rotor chosen as a random permutation. We are almost always far from what Hebern would recommend. We also examined 6 different original rotors by Hebern and found that Ims is between 13 and 18 as we would expect for random rotors. Only Swiss and Norwegian Enigma rotors have Ims being close to 16 and were possibly generated at random, except for one Norwegian rotor. We omitted Norwegian rotor IV, which was not rewired towards the end of the war like others, instead the same exact original German rotor IV was kept. Almost all other rotors from all known sources are clearly not random as their Ims is very high.
We also examined 10 rotors from the US cipher machine SIGABA from Wing On Chan (Citation2007) and the results seem to perfectly confirm the idea that these rotors were generated at random.
8.9. More details and comparison to random permutations
Random permutation statistics play an important role in cryptanalysis of block ciphers (cf. Bard, Ault, and Courtois Citation2012). For smaller permutations results can be obtained more easily by computer simulations. We observe that middle values such as Ims = 12 can happen for a random permutation with probability of about What is not likely to happen accidentally is when Ims is very low or very high.
We recall that when Ims = 26 we would have a latin square. It seems that German army rotors behave very much as approximating a latin square with high Ims close to 26, rather than behaving like random permutations. The probability that we have Ims = 23 of 24 for a random permutation is about and
respectively. It is even more exceptional to have Ims = 25, like with one of Japanese Enigma rotors. Here the probability is less than
The case with Ims = 26 and obtaining actual latin square was never observed so far, and we estimated this probability of it to be less than
However we frequently observe values close to 26. Small numbers
are quite rare as shown in , and potentially these rotors and only those were actually generated at random. In fact our table contains all known rotors such that
We do not list rotors with
because most of known rotors are such and accordingly most rotors are such that they could very hardly be generated at random ().
Table 2. Probability distribution of Ims for random permutations.
For all real-life historical Enigma rotors known to us, we found that on average Ims is 22.2 which is a very high value. In contrast if a rotor chosen as a random permutation the average value is 16 and values higher than 22 occur with low probability of less than
High values of Ims in the range 23–25 show that German army and many other Enigma rotors were certainly not chosen at random and this already in 1938, before the war started. Rather, they were chosen with some specific properties or design criteria in mind. These original criteria are currently unknown to researchers.
This is a repeated game and the chances of what we see in happening accidentally are extremely small. For example with all 8 Japanese Tirpitz rotors, the probability that they all have is less than
For the five German military rotors IV-VIII we get
This is like winning in a lottery four or five times in a row.
8.10. Combination of rotors
An important question is, if we combine just two rotors with high Ims, does the combination behave as a random permutation? In other words, is there a long-term effect for Enigma when we combine several rotors? Unhappily the value of Ims will not be abnormal anymore. We observed that a combination of just two rotors with Ims = 25 gives a rotor with Ims close to 16 which is also what we expect for a random permutation.
8.11. Related research: impossible invariant differentials
In a companion paper we study another very closely related question of the existence of invariant differentials of type
where differences are taken modulo 26. The study of Imk is another metric which allows one to show that most known rotors are far from being random permutations (and allows to distinguish them from such). We have the following definition:
Definition 8.12
(Imk). We call Imk the number of horizontal offsets k which are impossible in any column of our table or rotated alphabets (such as in ) when we have a collision in this column. In other terms we look at values of such that for no value x we have:
It also easy to see that the number Imk is equal to the number of impossible invariant differentials for this rotor R of type where
It is also easy to see that this set of impossible offsets k is in fact the same in every column in and in general. We observe that for most Enigma rotors not only Ims is large but Imk is also typically quite large and both are closely related. The maximum value of Imk is 25 because
is always possible and we have 25 if and only if we have a latin square.
Examples of Imk values for different rotors are shown in .
8.13. On relationship of Imk and Ims
We observe that for most Enigma rotors not only Ims is large but Imk is also typically quite large and both are closely related. If one is close to maximum, the other is also close to maximum. We note that Ims is always bigger typically and in line with the maximum allowed values: we have and
A strong relationship between Ims and Imk values does not hold anymore for smaller values.
The resistance of real-life Enigma rotors to invariant differentials of type is frequently unusually high and very few k are possible. We have Imk equal to 17.97 when averaged over all real-life Enigma rotors known to us. For example for German Army Rotor V we have Imk = 23 and only
is at all possible. Yes, the set of invariant differentials has exactly one element, this is quite incredible. In fact this happens frequently for many different real-life rotors, some examples are given in .
For rotors chosen uniformly at random, the average value of Imk is substantially lower, about 9.1, and we obtain numerous invariant differentials which are possible. For example for Norway Rotor V which seems to be generated at random and has no special properties known to us, the following k are possible:
and also
etc. We observe that there is a huge, roughly between 5x and tenfold difference, between what happens with random rotors and most real-life Enigma rotors. This is shown in .
8.14. On anti-latin squares
An important observation is that on the other side of the spectrum, low values of Imk are not forbidden and can occur for random rotors.
Definition 8.15
(Anti-Latin Square Property). We call a rotor an anti-latin square if for every the differential
has a non-zero probability. This is equivalent to Imk = 0.
The probability that Imk = 0 is about for a random permutation on 26 letters. We do not know any real-life rotors with Imk = 0.
Interesting Observation: In all known cases where Imk = 0 the very special differential for the basic rotor itself propagates with a quite high probability at least 8/26 and typically rather 12/26. Therefore potentially the cases of Imk = 0 could be cryptographically significant.
8.16. On Imk in random permutations ()
9. Comparison to Fialka
Fialka is a very complex Russian cipher machine with as many 10 rotors. Known rotors are listed in CryptoMuseum.com (Citation2020). Each rotor has 30 contacts instead of 26 which makes that the numbers we obtain are a bit higher than for Enigma but it is overall very similar. In , we compare the average parameters obtained for each known set of ten Fialka rotors, compared to what we obtain on average for a random permutation.
Table 5. Parameters of totors in Fialka cipher machines.
A quick computer simulation shows that the probability that for a random permutation is as low as about
and such events have occurred for about half of 40 rotors we examined. This cannot happen by accident and we see that all rotors without exception ever used in Fialka cipher machines have been very carefully chosen to approximate a latin square as with Enigma rotors, and they never behave like random permutations. The reason for this is again the lessons learned from classical cryptography about making the distribution of letters as uniform as possible when the key varies and this already for one single rotor.
10. Comparison to T-310 block cipher and local injectivity
It might come as a surprise, but similar properties exist for other ciphers, for example in modern block ciphers, which tend to behave rather like latin squares and not at all like random permutations. This is when the number of iterations (rounds) is limited. For a larger number of rounds we expect to obtain a random permutation.
10.1. Local injectivity in T-310
For example in the 1970s a substantial effort went into the design of the T-310 cipher which later was the main government encryption system used in Eastern Germany with some 3,800 cipher machines in active service in the 1980s (cf. Courtois, Drobick, and Schmeh Citation2018). Our property says that if we fix the input letter of one rotor and vary the key [which is accomplished by rotating the rotor] then the number of possible encryptions Ims is surprisingly large (e.g. 24) for the majority of historical rotors without ever reaching the maximum of 26. We can do the same in a block cipher and keep the input constant and vary the key.
It turns out that a similar and stricter property of this type was mandated in the 1970s for any “good quality” long term keys in T-310, cf. page 49 in Referat 11 (Citation1980) and Section 11 in Courtois et al. (Citation2017). This old historical result proves that this sort of questions have been studied also in Germany after the war. This makes our interpretation that this property is intentional, and a product of careful cryptographic engineering, also with Enigma cipher machines, more plausible. More precisely, the designers of T-310 have mandated in the 1970s the following very strict property:
Fact 10.2 (Local injectivity result for T-310). For 1,2,3 and 4 rounds of T-310, if we fix the block round input u on 36 bits, and vary the 12 bits of the key and IV bits, we obtain 2 pairwise distinct
values on 36 bits.
In contrast for 5 rounds, and for some weaker keys, this property is in rare cases violated, leading to the so called “related key collision attacks.” Specific examples of such attacks can be found in Section 5 of Courtois, Scarlata, and Georgiou (Citation2019) and these events remain extremely rare for just 5 rounds. Now we are going to show that, very much like the majority of Enigma rotors, T-310 also imitates a latin square in a substantial way. We need a more detailed quantitative assessment: how large is the analogue of Ims for T-310 when the number of rounds grows. We call the analogue of Ims when the key space is no longer the same as the input space. It is defined as the size of the output space when key varies and the input is fixed.
A direct estimation of for T-310 requires about 8 Gbytes of memory and substantial running time. A practical and reportedly accurate method to estimate
from the frequency of collisions was described in Section 18.4 of Courtois et al. (Citation2017). It is using the inverted Ramanujan formula and we expect that:
where Eck is the average expected number of keys which need to be tried in order to find a collision for a randomly chosen fixed cipher input. We can now answer the question whether real-life government keys for T-310 behave like latin squares also for more than four rounds.
The answer is yes, and we observe that for all real-life keys, such as those used to encrypt government communications during the Cold War, and for 12 rounds of T-310 we get results of type different images. We have not observed in practice any significant deviation from 2
The injectivity holds far beyond what is expected (from 4 to 12 rounds!). In contrast some other keys are substantially weaker. A nice proof of concept is the KT1 key 716 specified in Section 5 of Courtois, Scarlata, and Geougiou (Citation2019). Here the size of the output space is only
We conjecture that testing if
for 12 rounds could be considered as a practical method to evaluate the quality of long-term keys in T-310 which follows closely to the actual ideasFootnote5 and intentions of the designers of T-310. Our key 716 is the weakest KT1 key currently known and in Section 5.6 of Courtois, Scarlata, and Geougiou (Citation2019) we read that this sort of collisions with two different keys are rare for say 5 or 12 rounds but eventually become almost inevitable at 16 rounds approximately, this including real-life historical keys. We conclude that the designers of T-310 have avoided this type of collisions with different keys as hard as they could, leading to T-310 imitating a latin square through partial injectivityFootnote6 for up to 16 rounds.
10.3. Other block ciphers – local injectivity vs. birthday bound
We would like to compare different ciphers, those like T-310 which in 8 rounds use a very short key, and most other with very long keys. Let n be the block size in bits. It is easy to see that all results with Eck above the birthday bound of are representative of local injectivity we study. We tested this property for GOST block cipher, where key size is 256 bits (cf. Courtois Citation2012). For 2 rounds of GOST we obtain
far above the birthday bound. We see that GOST also satisfies a property similar to Fact 10.2 and therefore it also somewhat vaguely imitates a latin square. This reveals the fact that most Feistel ciphers have properties which go beyond what happens with one key, yet great majority of researchers only study what happens in one single key scenario. In specialist terms, they are expected to be not only good permutations but also good permutation generators (the attacker is allowed to compare different permutations for different keys). For 3 rounds GOST behaves already more like a random function with
11. Conclusion
All known attacks on Enigma, for more than 90 years, have worked under assumption that the permutations of the rotors do not have special properties. In this paper we show that most Enigma rotors ever made have not been chosen at random. Instead, they have been chosen to imitate a certain ideal property about permuted encryption alphabets. There are only a handful of exceptions with the Swiss and Norwegian rotors and in US rotor machines such as original Hebern rotors and also with US Army SIGABA rotors.
Our property is closely related to latin squares and it also translates into having an unusually large number of impossible invariant differentials. In addition certain rotors have unusually strong linear approximations. It is clear that in some cases rotors can be implemented in software cheaper than random rotors. This can be used to speed up (modern) implementations of the Turing-Welchman bombe attack and modern ciphertext-only attacks on Enigma (cf. Gillogly Citation1995; Ostwald and Weierud Citation2017). In general we observe that the differential properties of most Enigma rotors are quite peculiar. From here, an open question is, if it would be possible to reject a certain rotor order, through a sophisticated statistical distinguisher, without running the attack in full and without cribs. This could possibly save precious bombe time. After 90 years of study of Enigma we are just discovering that some rotors are special and not all rotor orders are the same.
The question of latin squares goes back to the 17th century and was studied in Korea long before it became a topic of interest among European mathematicians and cryptologists. Our discovery is simply an indirect proof that designers of various cipher machines in the XXth century have studied earlier classical cryptanalytic attacks. This opens a major research question about what is a balanced set of design criteria for rotors leading to an optimal resistance against known attacks. A satisfactory answer is unlikely to be determined from old sources alone. We need in fact be sceptical, and question the idea that individual rotors need to be as strong as observed. It is clear that our property affects the security of early Hebern cipher machines combining very few rotors without a reflector. For later cipher machines with a reflector and with a larger number of active rotors, there is no evidence that such properties will make the full ciphers weaker overall. For example we show that 100% of known Fialka rotors have been carefully chosen. However, Fialka combines as many as 10 such permutations and the chances of distinguishing such complex permutations from random are probably quite slim. Future research will show how many rotors are actually needed to obtain a decent level of security.
A natural extension of our property is to study local injectivity: we fix the input and vary the key for some part of the cipher and see if collisions are possible. This can apply potentially to any cipher ever made from 1920s until today, including all modern block ciphers. We expect that to some extent, injectivity is strong in any reduced-round cipher. We show that a very strong property of this type has been mandated in the 1970s for four rounds of the T-310 block cipher and it remains true in approximation for up to 16 rounds. Long term keys in T-310 need to be tested for this property and even inside the very narrow KT1 class of keys which was mandated for official use, there exist some substantially weaker keys in this respect.
About the Authors
Nicolas Courtois is a Crypto Research Engineer at Qualcomm, Sophia Antipolis, France. In 2006–2021 he was a lecturer at University College London, UK where he taught about applied cryptography and cryptanalysis. Prior to 2006, he worked a crypto research engineer at Thales/Gemalto, the worlds largest manufacturer of secure hardware. He has filed more than ten patents on practical applications of cryptography. His research focuses on cryptographic engineering with particular focus on cryptographic primitives used by millions of people every day in government, military, telecommunication and financial sectors, inside mobile phones, smart cards, crypto currency, etc. His Google Scholar profile lists more than 200 papers with 10,200 citations in cryptography. He is well known for his research on algebraic cryptanalysis using Boolean polynomials. He has contributed 20 research papers in the post-quantum cryptography spectrum with digital signature schemes such as HFE, Quartz, Sflash or CFS variant of McEliece. More recently he has co-authored several research papers on cryptocurrency with particular focus on questions of bitcoin mining, key management, password cracking, payment anonymity and cryptocurrency crime. His H-index is 42. A university team lead by Nicolas Courtois was given the UK University Cipher Champion in March 2013. He is a founding member of the group Code-Breakers at LinkedIn and a member of the editorial board of Cryptologia. His blog is blog.bettercrypto.com.
Marek Grajek – consultant, journalist, and historian. Spent a major part of his professional career in the IT, the other part in the financial services, combining finally both in his portfolio of consulting projects (digital identity, trust services). Author or editor of more than 10 books on the history of cryptology. His book “Enigma. Bliżej prawdy” was nominated the “History Book of the Year 2008” in Poland. An English translation is expected to appear soon. His book “Not Only Enigma. The Fish That Talked” was nominated the “Popular Science Book of the Year 2014” in Poland. One of the initiators of the monument in memory of Marian Rejewski, Jerzy Różycki and Henryk Zygalski in Poznań and more recently author and contributor at Enigma Cipher Center interactive museum in Poznań.
Correction Statement
This article has been republished with minor changes. These changes do not impact the academic content of the article.
Notes
1 Later below we study the so called Zagreb Enigma which also comes from TICOM and was used German military attaché in Zagreb. We expect however that it is not the same as Croatian army Enigma decrypted by Germany (cf. Christos Citation2017).
2 We refer to Turing (Citation1940) and to “Dermot Turing” (Citation2018) for a very brief summary and the definitions of Rod Square and the Inverse Rod Square which are actually not needed in this article.
3 In a basic version of this attack we assume that the crib is fixed. More generally it can be enriched with a “linguistic” or crib guessing dimension, if the attacker is not sure what the crib is, or for example he wants to deduce a longer crib from a shorter one.
4 An example of this is our later .
5 Reportedly the original software used for testing T-310 long-term keys for faults was lost.
6 This also means that roughly up to 16 rounds of T-310 can be distinguished from a random permutation generator by simply studying the frequency of collisions with the same input and different key.
References
- Alvarez, D. 2007. Wilhelm Fenner and the development of the German Cipher Bureau, 1922–1939. Cryptologia 31 (2):152–63.
- Armed Forces Security Agency. 1950. Replies by Ministerialrat Fenner to questions regarding cryptologic matters. English translation report from TICOM interrogation of Wilhelm Fenner, DF-187-G, October 1950.
- Army Security Agency. 1946. European axis signal intelligence in World War II. Vol. 3. Washington, DC, May. https://www.cryptomuseum.com/intel/nsa/files/volume_3.pdf
- Bard, G. V., S. V. Ault, and N. T. Courtois. 2012. Statistics of random permutations and the cryptanalysis of periodic block ciphers. Cryptologia 36 (3):240–62. doi: 10.1080/01611194.2011.632806.
- Batey, M. 2008. Dilly Knox - A reminiscence of this pioneer enigma cryptanalyst. Cryptologia 32 (2):104–30. In doi: 10.1080/01611190801914290.
- Bauer, F. L. 2006. Decrypted secrets: Methods and maxims of cryptology, 525. Berlin Heidelberg: Springer-Verlag.
- Bletchley Park: German signals security improvements since the battle of El Alamein (October/November 1942). 1944. Report ULTRA/ZIP C.C.R. 22, 7 p, 27 February.
- Bouchaudy, J.-F. 2021. Enigma: The spoils of Gustave Bertrand, or “par où tout a commencé.” Cryptologia 45 (4):309–41. doi: 10.1080/01611194.2020.1736205.
- Brown, L. P. 1991. Analysis of the DES and the design of the LOKI encryption scheme. PhD thesis, Dept. Computer Science, UC UNSW, ADFA.
- Calderini, M. 2015. On Boolean functions, symmetric cryptography and algebraic coding theory. Ph.D. in Mathematics, University of Trento.
- Calderini, M. 2018. A note on some algebraic trapdoors for block ciphers. https://arxiv.org/abs/1705.08151
- Christos, T. 2017. The compromise of the Croat Enigma K cipher machine by the German Army’s codebreakers, blog article at Christos military and intelligence corner, February 1. http://chris-intel-corner.blogspot.com/2017/02/the-compromise-of-croat-enigma-k-cipher.html
- Courtois, N. 2005. The inverse S-box, non-linear polynomial relations and cryptanalysis of block ciphers. In AES 4 Conference, Bonn, May 10–12 2004, LNCS 3373, 170–188. Springer. https://www.researchgate.net/publication/221005723/_The/_Inverse/_S-Box/_Non-linear/_Polynomial/_Relations/_and/_Cryptanalysis/_of/_Block/_Ciphers.
- Courtois, N. 2011. Algebraic complexity reduction and cryptanalysis of GOST. Monograph study on GOST cipher, 224. https://ia.cr/2011/626.
- Courtois, N. 2012. Security evaluation of GOST 28147-89 in view of international standardisation. Cryptologia 36 (1):2–13. doi: 10.1080/01611194.2011.632807.
- Courtois, N., G. Castagnos, and L. Goubin. 2003. What do DES S-boxes say to each other? https://ia.cr/2003/184/.
- Courtois, N., J. Drobick, and K. Schmeh. 2018. Feistel ciphers in East Germany in the communist era. Cryptologia 42 (5):427–44. doi: 10.1080/01611194.2018.1428835.
- Courtois, N., M.-B. Oprisanu, and K. Schmeh. 2018. Linear cryptanalysis and block cipher design in East Germany in the 1970s. In Cryptologia, December 5. https://www.tandfonline.com/doi/abs/. doi: 10.1080/01611194.2018.1483981.
- Courtois, N. T. 2020. Student exercises about breaking Enigma, updated March 2020, taught at University College London in 2020 as a part of COMP0058 Allied Cryptography and Cryptanalysis course. http://www.nicolascourtois.com/teach/Exos_Engima_0058.pdf
- Courtois, N. T., M. Grajek, and M. Rams. 2020. On weak rotors, latin squares, linear algebraic representations. Invariant Differentials and Cryptanalysis of Enigma, in Post-Proceedings of CECC, Rad HAZU, Matematiĉke znanosti. ISSN 1845-4100 (Print), ISSN 1849-2215 (Online), DOI: 10.21857/94kl4cw3zm.
- Courtois, N. T., T. Mourouzis, M. Misztal, J.-J. Quisquater, and G. Song. 2015. Guangyan song: Can GOST be made secure against differential cryptanalysis? Cryptologia 39 (2):145–56. doi: 10.1080/01611194.2014.915266.
- Courtois, N. T., M. Scarlata, and M. Georgiou. 2019. How many weak-keys exist in T-310?. In Number theory, algebra and cryptology’18, Vol. 73, 61–82. Tatra Mountains Mathematical Publications. https://content.sciendo.com/view/journals/tmmp/73/1/article-p61.xml.
- Courtois, N. T., K. Schmeh, J. Drobick, J. Patarin, M.-B. Oprisanu, M. Scarlata, and O. Bhallamudi. 2017. Cryptographic security analysis of T-310, Monography study on the T-310 block cipher, 132. https://ia.cr/2017/440.pdf
- Cryptographic Co-ordination and Records Section G.C. & C.S. 1944. Cryptographic dictionnary, July 20.
- CryptoMuseum.com. 2020. Fialka wiring. https://www.cryptomuseum.com/crypto/fialka/wiring.htm
- Dermot Turing with help of David Kenyon: The Bombe breakthrough, blue guide book. 2018. Bletchley Park Trust, 96 p.
- Driscoll, A. M. 1889–1971. Encyclopedia Britannica article. https://www.britannica.com/biography/Agnes-Meyer-Driscoll
- Dumas, L. R. 1997. Documents remis par ASCHE au SR français, Bulletin de l’ARCSI, Nr. 24, Paris, France, December.
- Erskine, R., and N. Enigma. 1988. The breaking of Heimisch and Triton, intelligence and national security. [Frank Cass] 3 (1):162–83.
- Eyraud, C. 1953. Précis de Cryptographie Moderne, 1st ed. Paris: Editions Raoul Tari, 2nd ed., 1959.
- Foss, H. 2001. Chapter 3: Reminiscences on the Enigma. In The Bletchley Park codebreakers, ed. R. Erskine and M. Smith, 35–39. Biteback Publishing.
- Fuensanta, J. R. S., F. J. López-Brea Espiau, and F. Weierud. 2010. Spanish enigma: A history of the enigma in Spain. Cryptologia 34 (4):301–28. doi: 10.1080/01611194.2010.485414.
- Further interrogation of R. R. Dr. Huettanheim and Sdf. Dr. Fricke of OKW/Chi, TICOM/I-84, 4 September 1945, released by NSA FOIA on 25 July 2017.
- Gillogly, J. J. 1995. Ciphertext-only cryptanalysis of enigma. Cryptologia 4 (19):405–13.
- Good, I. J., and C. A. Deavours. 1981. Afterword to: Marian Rejewski, “How Polish mathematicians deciphered the enigma.” Annals of the History of Computing 3 (3):229–32.
- Hamer, D., G. Sullivan, and F. Weierud. 1998. Enigma variations: An extended family of machines. Cryptologia XXII (3).
- Interview with Mrs. William F. Friedman Conducted by Dr. Forrest C. Pogue at the Marshall Research Library, Lexington, Virginia, 16 May 1973, In Friedman’s declassified documents, NSA. https://www.nsa.gov/news-features/declassified-documents/friedman-documents/
- Jennings, C. 2018. The Third Reich is listening: Inside German codebreaking 1939–45, 352. Oxford: Osprey Publishing.
- Johnson, K. W. 2015. The neglected giant, ed. Agnes Meyer Driscoll. National Security Agency, Center for Cryptologic History.
- Kahn, D. 2009. How i discovered World War II’s greatest spy. Cryptologia 34 (1):12–21. doi: 10.1080/01611190903385019.
- Kuhl, A. 2007. Rejewski’s catalog. Cryptologia 31 (4):326–31. doi: 10.1080/01611190701299487.
- Lawrence, J. 2005. A study of Rejewski’s equations. Cryptologia 29 (3):233–47. doi: 10.1080/01611190508951300.
- Leeuw, K. d. 2003. The Dutch invention of the rotor machine, 1915–1923. Cryptologia 27 (1):73–94. doi: 10.1080/0161-110391891775.
- Meyer, L. D., and S. Vaudenay. 2017. DES S-box generator. Cryptologia 41 (2):153–71. doi: 10.1080/01611194.2016.1169456.
- Mucklow, T. J. 2015. The SIGABA/ECM II cipher machine, a beutiful idea. NSA CCH. https://www.nsa.gov/Portals/70/documents/about/cryptologic-heritage/historical-figures-publications/publications/technology/The_SIGABA_ECM_Cipher_Machine_A_Beautiful_Idea3.pdf
- Nicolas, T. 2020. Courtois: Si seulement Enigma tournait moins vite, ou cryptanalyse d’Enigma avec un rotor faible. Bulletin de l’ARCSI, Nr 46 Paris, France.
- Ostwald, O., and F. Weierud. 2017. Modern breaking of enigma ciphertexts. Cryptologia 41 (5):395–421. doi: 10.1080/01611194.2016.1238423.
- Pommerening, K. 2008. Permutations and Rejewski’s theorem. http://www.staff.uni-mainz.de/pommeren/MathMisc/Permut.pdf
- Referat 11. 1980. Kryptologische Analyse des Chiffriergerätes T-310/50. Central Cipher Organ, Ministry of State Security of the GDR, document referenced as ‘ZCO 402/80’, a.k.a. MfS-Abt-XI-594, 123, Berlin.
- Rejewski, M. 1940. Henryk Zygalski and other undisclosed authors: Kurzgefasste Darstellung der Auflösungsmethoden. Bertrand archives, Service Historique de la Défense, Vincennes, France, DE 2016 ZB 25/6, Dossiers Nos. 281 and 282, ca.
- Sangwook, R. 2014. Choi Seokjeong and traditional Asian mathematics, Confucian scholar’s discovery predates the work of Euler. In page 3 of Math & Presso, Daily News of the Congress, No 3, Friday 15 August printed and edited by Korea JoongAng Daily newspaper, publication commissioned by the International Congress of Mathematicians, ICM 2014, Seoul, Korea. http://www.icm2014.org/download/MP0815.pdf.
- Simpson, R. 2020. Before ENIGMA: Breaking the Hebern rotor machine. Computer History Museum website. http://www.computerhistory.org/atchm/before-enigma-breaking-the-hebern-rotor-machine/.
- TICOM/I-200. 1946. Interrogation of Min. Rat. Wilhelm Fenner of OKW/Chi, November 22.
- TICOM/I-92. 1945. Final interrogation of Wachtmeister Otto Buggisch, OKW/IN. and OKW/Chi, September 11.
- Turing, A. 1940. Mathematical theory of ENIGMA machine A.k.a. Prof’s book, ed. UK national archives. https://archive.org/download/TuringMathTheoryEnigma/Turing
- Ulbricht, H. 2005. Die Chiffriermaschine ENIGMA, Trügerische Sicherheit, Ein Beitrag zur Geschichte der Nachrichtendienste. PhD thesis, Technische Universität Braunschweig.
- Wing On Chan. 2007. Cryptanalysis of SIGABA, a project report, Computer Science, San Jose State University, May. http://www.cs.sjsu.edu/faculty/stamp/students/Sigaba298report.pdf.
- Zentrales Chiffrierorgan der DDR. 1971. Fachbegriffe des Chiffrierwesens. VVS – ZCO 407/71, Berlin, 122 p.