ABSTRACT
The theory of convenience suggests that characteristics of white-collar offenders include motive, opportunity, and willingness for deviant behavior. This article discusses the case of offenders developing and supporting the software platform Popcorn Time. The motive seems to be sensation seeking with a deviant identity. The opportunity seems to be unknown and anonymous identity of offenders based on the lack of oversight and guardianship on the Internet. The willingness seems to be lack of self-control as well as disclaim of responsibility for violations of intellectual property rights. A structural model of convenience theory is applied to the case study.
Introduction
Popcorn Time is a software platform to access and view video streaming without paying for it (Stone Citation2015). The legality of the software depends on the jurisdiction. A website was created in Norway to explain and access Popcorn Time. Both the software and the website are illegal violations of intellectual property laws in Norway (NTB Citation2018). The domain name for the website was revoked to the Norwegian state by court order after hearings in the court of appeals (Borgarting Citation2019) and the Supreme Court (Høyesterett Citation2019).
The Norwegian National Authority for Investigation and Prosecution of Economic and Environmental Crime (Økokrim) prosecuted the case in court. Both courts defined the perpetrator as unknown (Borgarting Citation2019; Høyesterett Citation2019). Therefore, no individual was convicted of crime. The organization behind the website in Norway was making money on advertising and was organized as an association. The chairperson of the association witnessed in court, but he was never prosecuted (NTB Citation2018). Similarly, the developers of Popcorn Time remained anonymous and unknown (Stone Citation2015).
The case study in this article analyzes the court verdicts in Norway based on convenience theory. The theory of convenience suggests that white-collar crime occurs when there is a financial motive, an organizational opportunity, and a personal willingness for deviant behavior (Chan and Gibbs Citation2020; Gottschalk Citation2017, Citation2019; Hansen Citation2020; Nolasco and Vaughn Citation2019; Vasiu and Podgor Citation2019).
White-collar convenience
Convenience is the state of being able to proceed with something with little effort or difficulty, avoiding pain and strain (Mai and Olsen Citation2016). Convenience is savings in time and effort (Farquhar and Rowley Citation2009), as well as avoidance of pain and obstacles (Higgins Citation1997). Convenience is a relative concept concerned with the efficiency in time and effort as well as reduction in pain and solution to problems (Engdahl Citation2015). Convenience is an advantage in favor of a specific action to the detriment of alternative actions. White-collar offenders choose the most convenient path to reach their goals (Wikstrom, Mann, and Hardie Citation2018).
White-collar crime is nonviolent crime committed by individuals in competent positions (Piquero Citation2018; Piquero et al. Citation2019; Schoultz and Flyghed Citation2016, Citation2019). White-collar offenders commit and conceal their crime in a professional setting where they have legitimate access to premises, resources and systems (Gottschalk and Tcherni-Buzzeo Citation2016; Logan et al. Citation2019). The benefit from white-collar crime might be financial gain, personal adventure or some other desired outcome (Craig Citation2019; Craig and Piquero Citation2016, Citation2017; Dhami Citation2007; Onna and Denkers 201; Sutherland Citation1983).
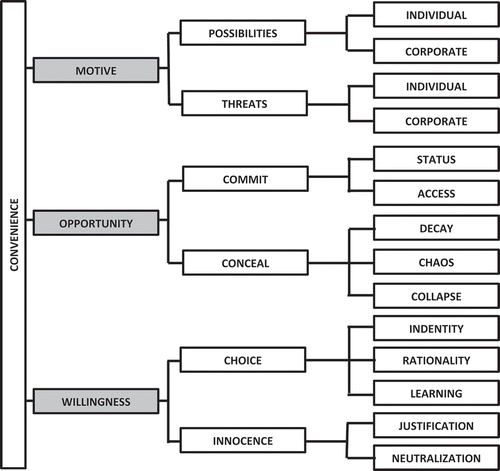
The theory of convenience suggests that white-collar misconduct and crime occurs when there is a motive benefitting an individual or n organization, professional opportunity to commit and conceal crime, and personal willingness for deviant behavior (Chan and Gibbs Citation2020; Gottschalk Citation2017, Citation2019; Hansen Citation2020; Nolasco and Vaughn Citation2019; Vasiu and Podgor Citation2019). The theory of convenience is an umbrella term for many well-known perspectives from criminology, strategy, psychology, and other schools of thought. Motive, opportunity and willingness are the three dimensions in convenience theory. Since convenience is a relative concept, convenience theory is a crime-as-choice theory. Shover, Hochstetler, and Alalehto (Citation2012) suggest that it is a conscious choice among alternatives that leads to law violation.
illustrates the structure of white-collar convenience. The extent of white-collar crime convenience manifests itself by motive, opportunity and willingness.
The personal willingness for deviant behavior manifests itself by offender choice and perceived innocence. The choice of crime can be caused by deviant identity, rational consideration, or learning from others. The perceived innocence at crime manifests itself by justification and neutralization. Identity, rationality, learning, justification, and neutralization all contribute to making white-collar crime action a convenient behavior for offenders (Craig and Piquero Citation2017; Engdahl Citation2015; Sutherland Citation1983; Sykes and Matza Citation1957).
Popcorn time case
“Too Good to Be Legal” was the heading of an article in Blomberg Businessweek, where Stone (Citation2015: 31) described Popcorn Time as making piracy easier than ever:
In the past year, a program called Popcorn Time has become the kinder, gentler face of piracy online, taming BitTorrent to make it far more user-friendly and less obviously sketchy. Free incarnations for PCs, phones, and tablets look pretty much like Netflix, Hulu, or Amazon Instant Video.
The daily Norwegian newspaper “Aftenposten” told the story under the article heading, “Norwegians violated the law by watching movies through Popcorn Time” (NTB Citation2018):
Hundreds of thousands of Norwegians have broken the law after watching movies and TV shows through the free service Popcorn Time, Follo district court states in a recent verdict.
Popcorn Time is a free service that offers streaming of movies and TV shows in the same manner as other suppliers on the market, such as Netflix. The difference is that Popcorn Time neither pays the licensees nor has obtained permission to show the contents.
A recent sentence from Follo district court states that the individual user violates the intellectual property law by watching films and series through the streaming service.
-The verdict is clear and clarifying that even those who watch movies and TV shows through Popcorn Time, violate the intellectual property law, says police lawyer Maria Bache Dahl at Økokrim.
-A special feature of this technology is that parts of the file are retrieved from an infinitely large number of users. Users who watch movies and TV shows through Popcorn Time will usually contribute to this file sharing by allowing others to retrieve parts of the file from them while watching movies. It is this kind of availability by the users that Follo district court says is undoubtedly in violation of the intellectual property law says Dahl.
Licensees in Norway may have lost as much as NOK 500 million, Willy Johansen said in court. He is the head of the Rights Alliance and secretary general of the Norwegian Videogram Association. It was also referred to an article in Aftenposten in May 2015, where a survey by TNS Gallup showed that 315,000 Norwegians used Popcorn Time weekly.
Økokrim hopes and believes that the verdict will be preventive against copyright infringements on the Internet. However, it is unclear whether Norwegian users of Popcorn Time risk being prosecuted.
-Users of illegal file sharing services cannot subsequently claim that they were unaware of the actions being illegal and will hopefully result in more users abstaining from such offenses. Generally, Økokrim does not comment on the cases that we will investigate, but it is clear that users of Popcorn Time can, in principle, be prosecuted, says Dahl.
She makes a point that the licensees have other tools that they can use, and refers to a ruling from Oslo district court in November last year. Telenor and 12 other network providers were required to block customers’ access to various domain names related to the streaming service. The plaintiffs were American film companies Disney Entertainment, Paramount Pictures, Columbia Pictures, Twentieth Century Fox Film, Universal City Studios and Warner Bros. Entertainment.
The case in Follo district court was about whether the right to use the domain popcorn-time.no should be revoked, which the district court now has determined that it should be. Økokrim seized the domain in March last year.
While Popcorn Time has provided a quick and easy way to download and view movies and TV shows that are copyrighted material, the Norwegian domain has reinforced the opportunity of illegal use, the court states.
The domain popcorn-time.no is owned by Imcasreg8, an association created by the company Internet Marketing Consult. The company has created this and a number of associations with similar names to register domain names for their customers.
-The verdict is very clear that the participation actions on the Norwegian domain, which were the topic of the court case, constitute intentional and very clandestine complicity. It is stated in the verdict about Popcorn Time, among other things, that the service cannot be considered to have any function or purpose other than providing access to protected films and TV shows, without the licensees’ consent, says police lawyer Dahl.
The verdict in Norwegian courts (Borgarting Citation2019; Høyesterett Citation2019) is in line with the statement that “if you are seen as encouraging people to infringe, then you have a copyright problem” (Stone Citation2015: 32).
Defense attorney Ola Tellesbø had argued in the court for dismissal of the case (Borgarting Citation2019: 5):
Popcorn Time is software that integrates several features including a browser, a BitTorrent client and a player. The software and technology behind it is not in itself illegal, as the prosecution has acknowledged. Nor is the BitTorrent technology, which enables efficient file sharing, illegal. The fact that the software can be used to share copyrighted material cannot lead to criminal liability for those behind the Norwegian domain. Based on the content of popcorn-time.no, it is most natural to compare the website with a technology blog. This cannot be confused with the software Popcorn Time and possible copyright infringements when using it.
The main purpose of the domain has been to sell advertisements and VPN solutions, not to facilitate or contribute to copyright infringement. This is substantiated by the fact that there was a disclaimer on the website, as well as information that use and downloading might be illegal and is done at the user’s own risk.
The contents of the Norwegian domain also have protection under the Norwegian Constitution (§ 100) and the European Convention on Human Rights (Article 10), which protect the freedom of expression and information.
The prosecuting authority has not established a causal link between the content of the Norwegian domain and alleged copyright infringements. There is a clear weakness in the investigation that it has not been investigated how many users (if any) have visited the Norwegian domain, possibly clicked further on from the Norwegian site and downloaded the software, and then used the software for copyright infringements. The fraction of legal material in the directories that the software’s search features are linked to is also not examined.
There is no basis for concluding that physical or mental involvement has taken place. The decisive factor in the scope of the responsibility is the relevance of penalty for the actions. The Napster sentence and Filmspeler case from the European Court of Justice do not apply as comparable cases and are irrelevant to determine the extent of participation.
Napster was a piracy site hosting infringing files. Pirate Bay did not host such files, nor link to them (Wikhamn and Knights Citation2016). Instead, Pirate Bay hosted trackers, that is, files which tell users of individual BitTorrent apps which other BitTorrent users to link to in order to download large files. Nevertheless, the European Court of Justice ruled that Pirate Bay was infringing copyright (Hern Citation2017).
The reference to Filmspeler at the European Court of Justice was a case where the Dutch citizen Jack Wullens sold a multimedia device online called the Filmspeler. The device acts as a medium between an audiovisual data source and a TV. Wullems’ player made it possible for users to watch free programming on their TVs regardless of copyright protection. The court noted that the sole purpose of the device was intentionally to access copyrighted work, where Wullens made money on sale of his device while depriving the rights holders of their economic benefit (Dotinga Citation2017).
Convenience case study
The unknown perpetrator referred to in the Norwegian court documents (Borgarting Citation2019; Høyesterett Citation2019) is the team of anonymous developers of Popcorn Time (Stone Citation2015: 32):
Creating a less cumbersome wrapper for BitTorrent was the primary objective of Popcorn Time’s anonymous developers, a group of friends in Argentina, ways a Dutch blogger who goes by Ernesto van der Sar and runs TorrentFreak, a news site that covers file sharing. The creators abandoned Popcorn Time just a few weeks after its launch, writing on their website that they needed to ‘move on with our lives’ (…)
Popcorn Time survived. Its code is open-source, so several other groups of coders quickly released versions after the site shut down. ‘We were users of the original and were sad to watch it go’, wrote a developer of one of the spinoff versions, who answered an e-mail sent through his group’s website and insisted on communicating through anonymous Internet chat software to protect his identity. ‘The amount of attention this project has been receiving is HUGE, ground breaking and way above anything we expected when we first picked it up’.
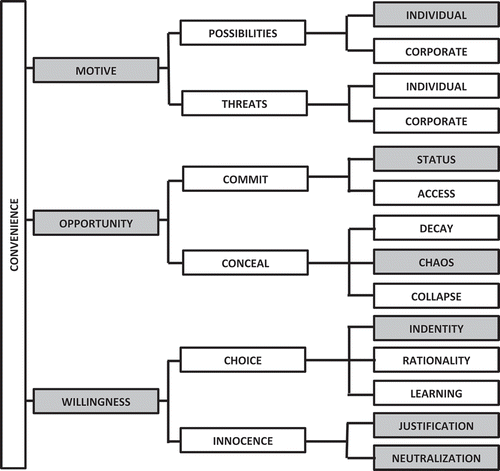
In the motive dimension of convenience theory, sensation seeking seems to be an important driving force for anonymous and unknown developers of piracy software such as Popcorn Time. Sensation seeking to experience adventure is a common characteristic of some white-collar offenses (Craig and Piquero Citation2017). Sensation seeking is a psychological trait where the offender seeks excitement. The offender seeks variation, novelty, complexity and intensity. The offender may be willing to take physical, social, legal and financial risks for the sake of such experiences. Even when the sensation seeking is not particularly strong, many white-collar crime acts may involve sensations that some find exciting.
Sensation seeking does not necessarily represent anti-social behavior. For example, bribing a potential customer during contract negotiations can be both social and exciting. When executives from the German bus manufacturer MAN bribed public officials from a Norwegian transportation agency, they went for a walk in a German forest where the Germans handed over envelopes containing euros to the Norwegians (Solem and Kleppe Citation2014). For both briber and bribed, the forest tour in itself might have been exciting. The memory of the Black Forest (Schwarzwald) at night will probably remain with the participants. Long and boring meetings, reading volumes of documents, and writing minutes of meetings, on the other hand, might be activities that participants soon forget.
Craig and Piquero (Citation2017: 1367) mention other examples where individuals can be sensation seeking:
Those qualities could fit a business man adding false charges to his expense account to make some extra money just to see if he can get away with it. These factors may also describe a retail employee stealing money from the cash drawer, or an individual committing an elaborate Ponzi scheme that requires complex planning and intense pressure.
Sensation seekers such as hackers and pirates attempt to avoid boredom by replacing repetitive activities such as status meetings in software projects, computer operations monitoring and documentation of applications with thrill and adventures. They search out risky and exciting activities and have distaste for monotonous situations.
illustrates the convenience theme of sensation seeking as a possibility for the individual piracy developer.
In their empirical study involving students, Craig and Piquero (Citation2017) included embezzlement and credit card fraud. Stealing money from an employer by embezzlement is risky not only because of legal implications but also because of the probable job loss. Abusing a roommate’s credit card can not only result in legal punishment but also an interpersonal cost if caught. At the same time, the offender can perceive both embezzlement and credit card abuse as thrilling adventures in a situation characterized by boredom. These offenses can also represent acts involving new and intense experiences. To claim to be the roommate is a fraudulent behavior that the offender may perceive as a high-pressure event.
In their empirical study involving students, Craig and Piquero (Citation2017) made a distinction between socialized sensation seeking and un-socialized sensation seeking. While thrill and adventure seeking represents social experience, disinhibition and boredom avoidance represent unsocial experience. The researchers found that unsocial – but not social – sensation seeking was a positive predictor of intentions to engage in shoplifting, embezzlement and credit card fraud.
In the opportunity dimension of convenience theory, being an anonymous and unknown perpetrator makes it possible to rescue software and avoid detection (Stone Citation2015: 32):
The anonymous Popcorn Time developer says the added pressure is motivating him and his colleagues to finish a version of the software that operates entirely by connecting viewers’ computers and doesn’t rely at all on central servers. “When we release this, there will be nothing to be taken down again,” he says.
indicates the high social status among insiders when committing piracy crime as white-collar crime (Slyke and Bales Citation2012). Status-relate factors such as influential positions in the technological underworld make offenders untouchable (Hausman Citation2018).
indicates that lack of oversight and guardianship against pirates on the Internet is another element of the opportunity structure characterized by chaos when it comes to policing the Internet. The climate encourages deviant behavior as normal and acceptable among hackers and pirates (Murphy and Dacin Citation2011). Offenders can play the blame game to avoid attention (Eberly et al. Citation2011; Lee and Robinson Citation2000).
In the willingness dimension of convenience theory, lack of self-control (Gottfredson and Hirschi Citation1990) seems related to sensation seeking in that willingness for sensation seeking increases with deterioration of self-control. Low self-control individuals give in more easily to their impulsive desires.
Lack of self-control is a frequent explanation for executive deviance and crime in general (Gottfredson and Hirschi Citation1990). While many might be tempted, only those lacking self-control will actually do it. Self-regulation monitors self-control, where self-regulation represents a process of using self-regulatory resources to control undesirable impulses and override subsequent behavioral responses. As argued by Mawritz et al. (Citation2017), individuals possess varying and limited self-regulatory resources that inhibit responses that may arise from physiological processes, habit, learning, or the strain of the situation. When resources that regulate self-control are depleted, individuals struggle to constrain their urges and engage in behavior almost unwittingly, using quick, thoughtless responses. They move down the slippery slope from the right side of the law to the wrong side of the law (Arjoon Citation2008). Self-control processes deplete self-regulatory resources and impair one’s ability to control subsequent inappropriate responses.
Kroneberg and Schulz (Citation2018: 59) link lack of self-control (Gottfredson and Hirschi Citation1990) to the situational action perspective, when they find that “personal moral rules play a crucial role in the process of perception of action alternatives, whereas self-control matters only in the subsequent process of choice should actors start to deliberate on whether or not to break the law”. While the perception of action alternatives belongs to the organizational opportunity dimension of white-collar offending, the subsequent lack of self-control belongs to the personal willingness dimension of white-collar offending. When the situational action perspective by Wikstrom, Mann, and Hardie (Citation2018) distinguishes between three stages, (1) perception of action alternatives (legal alternatives, illegal alternatives), (2) process of choice (habit, rational deliberation), and (3) action, then Kroneberg and Schultz (Citation2018) conceptualize lack of self-control as well as lack of deterrence on the axis from (2) to (3).
Lack of self-control as described by Gottfredson and Hirschi (Citation1990), combined with sensation seeking as described by Craig and Piquero (Citation2017), can substantially increase the level of willingness among potential white-collar offenders. The researchers also found that unsocial as well as social sensation seeking correlates positively with low self-control.
In addition to lack of self-control, justification of action and neutralization of guilt are typical sources of willingness in deviant behavior. The developers of Popcorn Time thought they did nothing wrong (Stone Citation2015: 32):
The developers don’t call themselves pirates. Asked about consequences of making illicit file sharing easier, the anonymous developer claims Popcorn Time doesn’t break any laws because it’s just an index of other BitTorrent sites and doesn’t host any pirated material. ‘The torrent world was here with millions of users way before us and will be here BILLIONS of users way after us’, he wrote.
The neutralization technique of disclaiming responsibility for crime is relevant here (Sykes and Matza Citation1957), where piracy developers claim not being responsible for what happens. They argue that the responsibility for obeying copyright laws should fall to users. Generally when applying this neutralization technique, the offender claims that one or more of the conditions of responsible agency did not occur. The person committing a deviant act defines himself or herself as lacking responsibility for his or her actions. In this technique, the person rationalizes that the action in question is beyond his or her control. The offender views himself as a billiard ball, helplessly propelled through different situations. He denies responsibility for the event or sequence of events (Jordanoska Citation2018; Kaptein and Helvoort Citation2019; Siponen and Vance Citation2010).
Robert Red English, a developer of a separate Popcorn Time spinoff who communicated over Skype Instant Messenger from Ontario with Stone (Citation2015: 32), also argued that the responsibility for obeying copyright laws should fall to users:
‘I’m not going to justify it’, he wrote. ‘If it’s stealing or not varies by country and each user is given the choice to use the program, and warned we use torrents. It’s up to them to choose if they wish to continue’.
That’s common defense among people who collect links to pirated videos, but judicial precedent doesn’t back it up. The founders of Pirate Bay, a popular BitTorrent hub, made similar arguments in Swedish court and received prison sentences. Older file-sharing networks such as Napster and Grokster shut down, because U.S. courts ruled that they were emboldening users to break laws.
indicates that deviant identity might also be a cause of willingness among piracy developers. Some white-collar offenders take on a professional deviant identity (Obodaru Citation2017). The identity perspective suggests that individuals develop professional identities where they commit to a chosen identity. It is a process of generating possible selves, selecting one, and discarding the others. Professional identity is how an individual sees himself or herself in relation to work. The self-concept is a complex cognitive structure containing all of a person’s self-representations. According to the identity perspective, roles and identities are interdependent concepts. Identity enactment refers to acting out an identity, or claiming the identity by engaging in behaviors that conform to role expectations and that allow the identity to become manifest. Deviant behavior finds an anchor in a person’s professional identity, where the deviant leader must claim and assume a leader identity by their followers.
Labeling can influence the deviant personality offender mind. The labeling perspective suggests that individuals adapt to the reputation created by others. The labeling perspective argues that the deviant reputation stigmatizes a person into a stereotype. Formal societal reaction to the individual can be a stepping-stone in the development of a criminal career. The deviant label is over time embedded in the individual. The labeled person is increasingly likely to become involved in social groups that consist of social deviants and unconventional others without feeling any doubt or regret since the behavior is in accordance with the label glued to the person by others (Bernburg, Krohn, and Rivera Citation2006).
Discussion
The theory of convenience is an emerging approach to cross-level deductive integration of numerous perspectives on white-collar crime (Chan and Gibbs Citation2020; Gottschalk Citation2017, Citation2019; Hansen Citation2020; Nolasco and Vaughn Citation2019; Vasiu and Podgor Citation2019). It is a combination of many preexisting perspectives, which are relevant for selection based on their perceived commonalities. To integrate is to form, coordinate, or blend into a functioning or unified whole. Integration is to add perspectives and propositions that improve the validity, generalizability, and utility of a theory to explain a phenomenon and to predict potential outcomes (Fried and Slowik Citation2004; Hambrick and Lovelace Citation2018).
The theory of convenience integrates various perspectives on convenience into a single theory with greater comprehensiveness and explanatory value than any one of its component perspectives. As such, convenience theory attempts to explain white-collar crime by bringing together several different theories and invoking multiple levels of analysis at the individual, organizational, as well as societal levels as suggested by Friedrichs (Citation2010: 479):
The number of different theories or levels, and the formality, with which the relationship between the theories or variables on different levels of analysis is posited, varies.
Deductive reasoning is the process of reasoning from one or more statements (premises) to reach a logically certain conclusion. A conclusion results reductively by applying general rules, which hold over the entirety of a closed domain of discourse. Pratt, Kaplan and Whittington (Citation2019) argue that most management scholars employ deductive and quantitative methods in positivistic testing of hypotheses.
Krohn and Eassey (Citation2014) argue that up-and-down integration – also referred to as deductive integration – might be considered the classic form of theoretical integration (Liska, Krohn, and Messner Citation1989: 5):
Up-and-down integration refers to identifying a level of abstraction or generality that encompasses much of the conceptualization of the constituent theories.
There are two types of up-and-down integration. In one type, integrated propositions in an up-and-down manner use the premise of one theory to derive the propositions of constituent theories. In particular, if theory A contains a more abstract or more general proposition from which theory B can be specified, then it is possible to integrate B with theory A, resulting in a single theory. Alternatively, if both theories A and B are able to be elaborated using assumptions more general than either theory individually, then it could be possible to synthesize the theories together in order to create a new theory C, which contains parts of both constituent theories. The former approach often involves theoretical reduction, while the latter involves theoretical synthesis.
The theory of convenience is a result of deductive integration by theoretical synthesis where a large number of theoretical perspectives blend into a unified whole to explain the main dimensions of motive, opportunity, and willingness. Some scholars argue that deductive integration is the only true type of theoretical integration. It is also the most difficult to do (Krohn and Eassey Citation2014).
The theory of convenience also applies another kind of up-and-down integration by including different units of analysis. Some perspectives are at the individual level of the offender (e.g., personal neutralization and personal strain). Some perspectives are at the group level of the organization (e.g., lack of guardianship and institutional deterioration), while some perspectives are at the level of society (e.g., criminogenic market structures and resource scarcity).
Conclusion
This article has illustrated how the convenience theory applies to hackers and pirates on the Internet. The theory of convenience suggests that characteristics of white-collar offenders include motive, opportunity, and willingness for deviant behavior. This article discussed the case offenders developing and supporting the software platform Popcorn Time. The motive seems to be sensation seeking with a deviant identity. The opportunity seems to be unknown and anonymous identity of offenders based on the lack of oversight and guardianship on the Internet. The willingness seems to be lack of self-control as well as disclaim of responsibility for violations of intellectual property rights.
Additional information
Notes on contributors
Petter Gottschalk
Petter Gottschalk is professor in the Department of Leadership and Organizational Behavior at BI Norwegian Business School in Oslo, Norway. After completing his education at Technische Universität Berlin, Dartmouth College, Massachusetts Institute of Technology, and Henley Management College, he took on executive positions in technology enterprises for twenty years before joining academics. Dr. Gottschalk has published extensively on knowledge management, intelligence strategy, police investigations, white-collar crime, convenience theory, and fraud examinations. He has lectured at universities in the United States, China, Singapore, and Egypt.
References
- Arjoon, Surendra. 2008. “Slippery When Wet: The Real Risk in Business.” Journal of Markets & Morality 11 (1):77–91.
- Bernburg, Jon G., Marvin D. Krohn, and Craig J. Rivera. 2006. “Official Labeling, Criminal Embeddedness, and Subsequent Delinquency.” Journal of Research in Crime and Delinquency 43 (1):67–88. doi: 10.1177/0022427805280068
- Borgarting. 2019. “Case Number 18-027486AST-BORG/02.” Borgarting lagmannsrett (Borgarting court of appeals), Oslo, Norway, Retrieved January 22, 24.
- Chan, Fiona and Carole Gibbs. 2020. “Integrated Theories of White-Collar and Corporate Crime.” Pp. 191–208. The Handbook of White-Collar Crime chapter 13 edited by Melissa L. Rorie. Hoboken, NJ: Wiley & Sons.
- Craig, Jessica M. 2019. “Extending Situational Action Theory to White-Collar Crime.” Deviant Behavior 40 (2):171–86. doi: 10.1080/01639625.2017.1420444
- Craig, Jessica M. and Nicole L. Piquero. 2016. “The Effects of Low Self-Control and Desire-for-Control on White-Collar Offending: A Replication.” Deviant Behavior 37 (11):1308–24.
- Craig, Jessica M. and Nicole L. Piquero. 2017. “Sensational Offending: An Application of Sensation Seeking to White-Collar and Conventional Crimes.” Crime and Delinquency 63 (11):1363–82. doi: 10.1177/0011128716674707
- David .O, Friedrichs. 2010 “Integrated Theories of White-Collar Crime.” Pp. 479–86 in Encyclopedia of Criminological Theory, Vol. 1, edited by Francis T. Cullen and Pamela Wilcox. Los Angeles, CA: Sage Publications.
- Dhami, Mandeep K. 2007. “White-Collar Prisoners’ Perceptions of Audience Reaction.” Deviant Behavior 28 (1):57–77. doi: 10.1080/01639620600987475
- Dotinga, William. 2017. “EU Court Finds Copyright Issues with Streaming Player.” Courthouse News Service, Retrieved April 26 (www.courthousenews.com).
- Eberly, Marion B., Erica C. Holley, Michael D. Johnson, and Terence R. Mitchell. 2011. “Beyond Internal and External: A Dyadic Theory of Relational Attributions.” Academy of Management Review 36 (4):731–53.
- Engdahl, Oskar. 2015. “White-Collar Crime and First-Time Adult-Onset Offending: Explorations in the Concept of Negative Life Events as Turning Points.” International Journal of Law, Crime and Justice 43 (1):1–16. doi: 10.1016/j.ijlcj.2014.06.001
- Farquhar, Jillian D. and Jennifer Rowley. 2009. “Convenience: A Services Perspective.” Marketing Theory 9 (4):425–38. doi: 10.1177/1470593109346894
- Fried, Yitzhak and Linda H. Slowik. 2004. “Enriching Goal-Setting Theory with Time: An Integrated Approach.” Academy of Management Review 29 (3):404–22. doi: 10.5465/amr.2004.13670973
- Gottfredson, Michael R. and Travis Hirschi. 1990. A General Theory of Crime. Palo Alto, CA: Stanford University Press.
- Gottschalk, Petter. 2017. “Convenience in White-Collar Crime: Introducing a Core Concept.” Deviant Behavior 38 (5):605–19. doi: 10.1080/01639625.2016.1197585
- Gottschalk, Petter. 2019. Convenience Triangle in White-Collar Crime – Case Studies of Fraud Examinations. Cheltenham, UK: Edward Elgar Publishing.
- Gottschalk, Petter and Maria Tcherni-Buzzeo. 2016. “Reasons for Gaps in Crime Reporting: The Case of White-Collar Criminals Investigated by Private Fraud Examiners in Norway.” Deviant Behavior 38 (3):267–81. doi: 10.1080/01639625.2016.1196993
- Hambrick, Donald C. and Jeffrey Lovelace. 2018. “The Role of Executive Symbolism in Advancing New Strategic Themes in Organization: A Social Influence Perspective.” Academy of Management Review 43 (1):110–31. doi: 10.5465/amr.2015.0190
- Hansen, Laura L. 2020. “Review of the Book ‘Convenience Triangle in White-Collar Crime: Case Studies of Fraud Examinations’.” Pp. 5. in ChoiceConnect, Vol. 57. Middletown, CT: Association of College and Research Libraries.
- Hausman, Wim J. 2018. “Howard Hopson’s Billion Dollar Fraud: The Rise and Fall of Associated Gas & Electric Company.” Business History 60 (3):381–98. doi: 10.1080/00076791.2017.1339690
- Hern, Alex. 2017. “European Court of Justice Rules Pirate Bay Is Infringing Copyright.” The Guardian, www.theguardian.com, published June 15.
- Higgins, E .Tory. 1997. “Beyond Pleasure and Pain.” American Psychologist 52 (12):1280–300. doi: 10.1037/0003-066X.52.12.1280
- Høyesterett. 2019. “Case Number HR-2019-1743-A, 19-057105STR-HRET.” Norges høyesterett (Norwegian supreme court), Oslo, Norway, September 17, 12.
- Jordanoska, Alexandra. 2018. “The Social Ecology of White-Collar Crime: Applying Situational Action Theory to White-Collar Offending.” Deviant Behavior 39 (11):1427–49. doi: 10.1080/01639625.2018.1479919
- Kaptein, Muel and Martien van Helvoort. 2019. “A Model of Neutralization Techniques.” Deviant Behavior 40 (10):1260–85. doi: 10.1080/01639625.2018.1491696
- Krohn, Marvin D. and John M. Eassey. 2014. “Integrated Theories of Crime.” Pp. 458–63 in The Encyclopedia of Theoretical Criminology, edited by J. Mitchell Miller. Chichester, UK: John Wiley & Sons,
- Kroneberg, Clemens and Sonja Schulz. 2018. “Revisiting the Role of Self-Control in Situational Action Theory.” European Journal of Criminology 15 (1):56–76. doi: 10.1177/1477370817732189
- Lee, Fiona, and Robert J. Robinson. 2000. “An Attributional Analysis of Social Accounts: Implications of Playing the Blame Game.” Journal of Applied Social Psychology 30 (9):1853–79. doi:10.1111/jasp.2000.30.issue-9.
- Liska, Allen E., Marvin D. Krohn, and Steven F. Messner. 1989. “Strategies and Requisites for Theoretical Integration in the Study of Crime and Deviance.” Pp. 1–20 in Theoretical Integration in the Study of Deviance and Crime, edited by Steven F. Messner, Marvin D. Krohn, and Allen E. Liska. Albany, NY: State University of New York Press.
- Logan, Matthew W., Mark A. Morgan, Michael L. Benson, and Francis T. Cullen. 2019. “Coping with Imprisonment: Testing the Special Sensitivity Hypothesis for White-Collar Offenders.” Justice Quarterly 36 (2):225–54. doi: 10.1080/07418825.2017.1396488
- Mai, Huynh T. X and Svein O. Olsen. 2016. “Consumer Participation in Self-Production: The Role of Control Mechanisms, Convenience Orientation, and Moral Obligation.” Journal of Marketing Theory and Practice 24 (2):209–23. doi: 10.1080/10696679.2016.1130554
- Mawritz, Mary B., Rebecca L. Greenbaum, Marcus M. Butts, and Katrina A. Graham. 2017. “I Just Can’t Control Myself: A Self-Regulation Perspective on the Abuse of Deviant Employees.” Academy of Management Journal 60 (4):1482–503. doi: 10.5465/amj.2014.0409
- Murphy, Pamela R. and M. Tina Dacin. 2011. “Psychological Pathways to Fraud: Understanding and Preventing Fraud in Organizations.” Journal of Business Ethics 101 (4):601–18. doi: 10.1007/s10551-011-0741-0
- Nolasco, Claire A. and Michael S. Vaughn. 2019. “Convenience Theory of Cryptocurrency Crime: A Content Analysis of U.S. Federal Court Decisions.” Deviant Behavior 10.1080/01639625.2019.1706706.
- NTB. 2018. “Nordmenn Brøt Loven Ved Å Se Filmer Gjennom Popcorn Time (Norwegians Violated the Law by Watching Movies through Popcorn Time).” Daily Norwegian newspaper Aftenposten, www.aftenposten.no, Retrieved January 19.
- Obodaru, Otilia. 2017. “Forgone, but Not Forgotten: Toward a Theory of Forgone Professional Identities.” Academy of Management Journal 60 (2):523–53. doi: 10.5465/amj.2013.0432
- Pratt, Michael G., Sarah Kaplan and Richard Whittington 2019. “Editorial Essay: The Tumult over Transparency: Decoupling Transparency from Replication in Establishing Trustworthy Qualitative Research.” Administrative Science Quarterly, 1–19. doi: 10.1177/0001839219887663
- Piquero, Nicole L. 2018. “White-Collar Crime Is Crime: Victims Hurt Just the Same.” Criminology & Public Policy 17 (3):595–600. doi: 10.1111/1745-9133.12384
- Piquero, Nicole L., Alex R. Piquero, Chelsey Narvey, Brian Boutwell, and David P. Farrington. 2019. “Are There Psychopaths in White-Collar Jobs?” Deviant Behavior. doi:10.1080/01639625.2019.1708537.
- Schoultz, Isabel and Janne Flyghed. 2016. “Doing Business for a ‘Higher Loyalty’? How Swedish Transnational Corporations Neutralize Allegations of Crime.” Crime, Law, and Social Change 66 (2):183–98. doi: 10.1007/s10611-016-9619-5
- Schoultz, Isabel and Janne Flyghed. 2019. “From ‘We Didn’t Do It’ to ‘We’ve Learned Our Lesson’: Development of a Typology of Neutralizations of Corporate Crime.” Critical Criminology 1–19 Retrieved December 16 10.1007/s10612-019-09483-3.
- Shover, Neal, Andy Hochstetler, and Tage Alalehto. 2012. “Choosing White-Collar Crime.” Pp. 475–93 in The Oxford Handbook of Criminological Theory, edited by Francis T. Cullen and Pamela Wilcox. UK: Oxford: Oxford University Press,
- Siponen, Mikko and Anthony Vance. 2010. “Neutralization: New Insights into the Problem of Employee Information Security Policy Violations.” MIS Quarterly 34 (3):487–502. doi: 10.2307/25750688
- Slyke, Shanna van and William D. Bales. 2012. “A Contemporary Study of the Decision to Incarcerate White-Collar and Street Property Offenders.” Punishment & Society 14 (2):217–46. doi: 10.1177/1462474511434437
- Solem, Lars K. and Mads K. Kleppe. 2014. “Seks Dømt for Korrupsjon I Unibuss-Saken (Six Convicted in the Unibuss Case).” Daily Norwegian business newspaper Dagens Næringsliv, Rretrieved December 3 (https://www.dn.no/korrupsjon/unibuss/kriminalitet/seks-domt-for-korrupsjon-i-unibuss-saken/1-1-5245586)
- Stone, Brad. 2015. “Too Good to Be Legal.” Bloomberg Businessweek March 2 – March 8, 31–33.
- Sutherland, Edvin H. 1983. White Collar Crime – The Uncut Version. New Haven, CT: Yale University Press.
- Sykes, Gresham and David Matza. 1957. “Techniques of Neutralization: A Theory of Delinquency.” American Sociological Review 22 (6):664–70. doi: 10.2307/2089195
- Vasiu, Viviani I. and Ellen S. Podgor. 2019. “Organizational Opportunity and Deviant Behavior: Convenience in White-Collar Crime.” in Criminal Law and Criminal Justice Books, Rutgers, the State University of New Jersey. July. www.clcjbooks.rutgers.edu.
- Wikhamn, Bjorn R. and David Knights. 2016. “Associations for Disruptiveness – The Pirate Bay Vs. Spotify.” Journal of Technology Management & Innovation 11 (3):40–50. doi: 10.4067/S0718-27242016000300005
- Wikstrom, Per-Olof H., Richard P. Mann, and Beth Hardie. 2018. “Young People’s Differential Vulnerability to Criminogenic Exposure: Bridging the Gap between People- and Place-Oriented Approaches in the Study of Crime Causation.” European Journal of Criminology 15 (1):10–31. doi: 10.1177/1477370817732477