?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.ABSTRACT
It is well known that private key generation is a computing bottleneck in an identity-based encryption scheme when a large number of users exist. Outsourcing computation can greatly reduce the users’ computational cost, but the existing schemes are all based on two servers, which are not feasible in the real cloud environment. In this paper, we first propose a scheme where the PKG outsources the task of private key generation to a single server, and the results can be verified effectively. Moreover, PKG only needs to execute 1 modular exponentiation, so it is more efficient when compared with previous schemes. Meanwhile, we prove the indistinguishability of the ciphertext and verifiability of the outsourcing results in the security model. Finally, the proposed algorithm is realized in a simulation environment. Theoretical analysis and experimental results show that total computing time of PKG and the server in the outsourced algorithm is far less than that of direct computation.
1. INTRODUCTION
With the rapid development of cloud computing, the safety and efficiency of outsourcing computation have attracted widespread attention. By outsourcing computation, outsourcers with limited ability can outsource complex computing tasks to powerful servers, which will greatly reduce users’ computational costs. However, outsourcing computing tasks to servers also presents some security risks because the servers are not completely trusted. Verifiable outsourcing schemes can keep the information of users confidential and verify computational results returned from the server. At present, verifiable outsourcing schemes have involved in many aspects in cryptography, such as modular exponentiation [Citation1,Citation2], polynomial operations [Citation3], attribute-based encryption operations [Citation4,Citation5], image feature extraction [Citation6], and so on.
Modular exponentiation is one of the most time-consuming and commonly used operations in cryptography, and many outsourcing schemes for modular exponentiations have been proposed. Hohenbergerd et al. [Citation7] first proposed an outsourcing scheme for single modular exponentiation with two non-colluding servers, where the outsourcer could check the fault that the servers might make with a probability of 1/2, and they also defined the security model of outsourcing calculation. Then Wang et al. [Citation8] presented an outsourcing solution for batch modular exponentiations based on a single untrusted server with increased security, but the checkability was only 1/(s + 1)(where s is the number of modular exponentiations), which means it was not efficient and the checkability was only 1/2 for outsourcing single modular exponentiation. Different from the previous schemes, Liu et al. [Citation9] did the work for outsourcing composite modular exponentiations. Ye et al. [Citation10] proposed a new secure outsourcing algorithm based on a single server, and the verifiable probability is close to 1 while the outsourcer appended much computation cost. Chen et al. [Citation11] firstly presented an efficient outsourcing algorithm for bilinear pairing based on two untrusted servers and the outsourcer need not any expensive operations in their algorithm. Then another outsourcing algorithm was proposed with improved checkability based on two servers for bilinear pairing [Citation12]. Recently, Ren et al. [Citation13] presented a new outsourcing algorithm of bilinear pairing with a verifiability of close to 1 if one of the servers misbehaved, which improved the checkability without an interactive operation between the server and the outsourcer.
In identity-based cryptography, the user’s identity is directly used as a public key, and the private key generator needs to generate a private key or perform key update for each user. The identity-based cryptography was firstly proposed in 1984 by Shamir [Citation14], but the first scheme was constructed by Boneh and Franklin in 2001 [Citation15]. In order to reduce the risk of key leakage, Ren et al. [Citation16] proposed an identity-based parallel key encryption scheme, then Yu et al. [Citation17] presented a securer solution because this algorithm supports frequent key updates without increasing the risk of key leakage. With the increase of users, the calculation burden of PKG will be heavy and it may cause the bottleneck of the system. In order to solve this problem effectively, Li et al. [Citation18] proposed an outsourced deletion algorithm based on identity encryption scheme, which transfers the calculation burden of deleting users from PKG to cloud server. Recently, Ren et al. [Citation19] firstly proposed a verifiable algorithm for outsourcing private key generation in the IBE scheme. Based on the
scheme [Citation20], PKG can outsource the tasks of generating private keys and verify the correctness of returned results. This scheme can verify the results with a probability of 1 if one of the servers returned fault results, but it is based on two untrusted servers. So far, there is no relevant algorithm proposed based on a single server.
Our contributions: In this paper, we introduce the concept of verifiable computation into the identity-based encryption scheme, and then propose an IBE scheme that includes an outsourcing private key generation algorithm. In the proposed scheme, PKG outsources the tasks of generating the private key and verifies the returned results effectively. The outsourcing algorithm is based on a single server and it can greatly reduce the computational cost of PKG, meanwhile, the server cannot obtain PKG or the private key of any user during the outsourcing process. The PKG can detect the failure with a probability of about 1 if the server misbehaves, the experiment shows the time cost for PKG is much smaller than that of generating the private keys directly and the server in the outsourcing algorithm.
2. DEFINITION AND SECURITY MODEL
In this section, we introduce some definitions including bilinear groups with the order of composite number, the identity-based encryption scheme and the security model of .
2.1 Bilinear Groups with Order of Composite Number
People first presented bilinear groups with the order of composite number in [Citation20], the algorithm takes security parameter as input and then outputs (
), where
are distinct primes,
and
are cyclic groups with order
, if it has following conditions, then
:
is a bilinear map:
(Bilinear):
,
,
.
(Non-degenerate):
, which makes
is a generator of
.
(Computable): There is an efficient algorithm to compute
for all
.
Let represent the subgroups of
with order
respectively.
,
,
represent the subgroups of
with order
, respectively. So
,
. Assume
is a generator of
, and then
,
,
are generators of
,
,
respectively,
,
and
, we have
. If
,
, since that
, then, for some
and
,
, and
.
2.2 Identity-Based Encryption Scheme
An IBE scheme is usually composed of four aspects, including Setup, KeyGen, Encrypt, and Decrypt algorithms [Citation20], which typically involves two entities, PKG, and users (including sender and receiver). If PKG sends the task of outsourcing private key generation to the server, the algorithm will be added and the scheme consists of the following algorithms.
Setup (): The setup algorithm takes a security parameter
as input, and outputs the master key
and the public key
. The key
is public and the master key is kept secret.
KeyGen (,
): The private key generation algorithm takes the public key
, an identity
and the master key
as input, and outputs a private key
corresponding to the identity
.
Encrypt (,
): The encryption algorithm takes an identity
, a public key
and a message
as input, and outputs the ciphertext
.
Decrypt (): The decryption algorithm takes the ciphertext
, a private key
and the public key
as input, and it returns a message
or an error
.
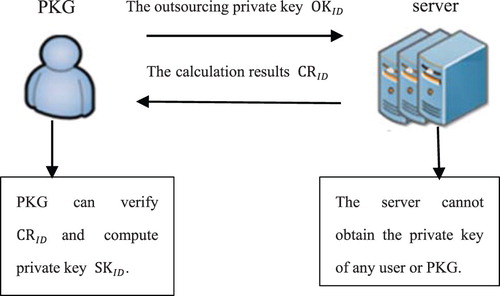
If PKG outsources the task of generating private keys to the server, then the following algorithm is appended. The computation model of the scheme is shown in Figure .
(
): The algorithm takes the identity
as input, PKG generates outsourcing private key
and sends it to the server. When the server returns the calculation results
, we verify the results correct or not, if correct, then calculate the user’s private key
, otherwise return an error
.
2.3 Security Model of an 
 Scheme
Scheme
We first introduce the full security model against the chosen-plaintext attack (CPA) in an scheme, and then introduce the security model of an IBE scheme which adds the outsourcing private key generation algorithm. A game between a challenger and an adversary
can describe them.
In the following games, we define the advantage of and the scheme is secure if the advantage is negligible.
Definition 1:
(IND-ID-CPA) Through the following games, the definition of indistinguishability of an scheme under the chosen-plaintext attack is given [Citation20]. The game contains 2 participants: challenger and adversary
.
Setup: The challenger executes the Setup algorithm to get the public key and the master key
, which then sends the public key
to attacker
while ensuring that
is secret.
Phase 1: The attacker adaptively issues.
Private key query: the attacker sends an identity
to the challenger, then the challenger runs the KeyGen algorithm, and sends the private key of identity to the attacker
.
Challenge: sends an identity
and two same length messages
to the challenger, in Phase 1,
has not been executed the private key query. The challenger randomly chooses a bit
and forms the ciphertext
, and then returns
to
.
Phase 2: The adversary continues to issue private key queries and the challenger responds queries adaptively. However,
will not been executed the private key query.
Guess: outputs guess
.
Definition 2:
(IND-OID-CPA) Through the following games, the definition of indistinguishability of an scheme under the chosen-plaintext attack is given after adding private key generation algorithm [Citation19]. The game contains two participants: challenger and adversary
.
Setup: The challenger executes the Setup algorithm to get the public key and the master key
, which then sends the public key
to attacker
while ensuring that
is secret.
Phase 1: First the challenger initializes an empty outsourcing list and the adversary
adaptively issues queries.
Private key query: the adversary sends an identity
to the challenger, then the challenger runs the KeyGen algorithm, and sends the private key of identity to the adversary
.
Outsourcing key query: The adversary sends
to the challenger and then the challenger search
in
. If it exists, then returns
to
, Otherwise, generates
and returns it to
.
Challenge: sends an identity
and two same length messages
to the challenger, in Phase 1,
has not been executed the private key query or outsourcing key query. The challenger randomly chooses a bit
and forms the ciphertext
, then returns
to the adversary.
Phase 2: The adversary continues to issue private key queries and the challenger responds queries adaptively. However,
will not been executed the private key query or outsourcing key query.
Guess: outputs guess
.
In the above two games, we define the advantage of as
.
Different from Definition 1, Definition 2 adds the outsourcing private key generation algorithm, and it mainly adds the outsourcing key query in Phase 1. Moreover, in the above two security models, will not been executed the private key query or outsourcing key query.
3. IDENTITY-BASED ENCRYPTION WITH OUTSOURCED PRIVATE KEY GENERATION
This section proposes an algorithm with verifiable outsourced private key generation based on the scheme [Citation20], PKG can verify the correctness of the returned results effectively, but the server cannot obtain the PKG or the private key of any user.
3.1 
 Scheme
Scheme
In this section, we first review the scheme [Citation20].
Setup(): PKG runs the Setup algorithm, which selects a bilinear group
of order
, where
are three large primes. Let
be a subgroup of order
in
, where
. Then PKG randomly chooses
,
, and generates a public key
, and the master key is
and a generator of
.
KeyGen (): PKG randomly selects
,
based on identity
, and computes:
Then PKG outputs
corresponding to
.
Encrypt (): For an identity
and a message
, we randomly choose
and computes:
Then creates the ciphertext
.
Decrypt (): Take as input an identity
, a private
and a ciphertext
, then it decrypts the ciphertext as below:
Since
,
,
, then
Thus, the ciphertext can be decrypted successfully.
3.2 The 
 Scheme with Verifiable Outsourced Key Generation
Scheme with Verifiable Outsourced Key Generation
In this section, we propose an scheme with verifiable outsourced key generation. The Setup, KeyGen, Encrypt, and Decrypt algorithms are run as the
scheme, and then we only introduce the identity-based encryption with verifiable outsourced key generation. In [Citation7], a subroutine
is used to generate random tuple with the form of
, where
, so that the computations of the outsourcer can be speeded, and
represents the server.
(
): (1) Firstly PKG computes
and stores it in the system, then running
sixth to create six blinding pairs:
We denote
,
, so that we get the first logical divisions:
where
,
.
Then we get the second logical divisions:
where
(2) PKG first selects
random numbers
then randomly chooses
is a small integer [from 1 to 10] and computes:
(3) Then PKG selects
random numbers
then randomly chooses
is a small integer [from 1 to 10] and computes:
Then we set .
(4) PKG makes queries to
in random order:
(5) PKG verifies that the calculation is correct or not:
If
where
and
initial value are
.
If
where
and
initial value are
.
The verification calculation is as follows:
If not, PKG outputs “error”; otherwise, PKG randomly chooses
,
, and computes:
The private key corresponding to the
is
.
In the above outsourcing algorithm, the server need not know the relationship between and
, and users only need to perform modular exponentiation operations once in the outsourcing process, which greatly reduces the computational cost of PKG, and the server cannot obtain the PKG or the private key of any user.
4. ANALYSIS OF THE SCHEME
This section analyzes the scheme, including the indistinguishability of the ciphertext and verifiability of the outsourcing results. Then, we show the computation cost comparison of PKG for generating private keys directly and outsourcing the task to a single server, and an efficiency comparison for different schemes with outsourced key generation. Finally, the simulation of the scheme is implemented.
4.1 Security Analysis
When the proposed scheme is under the choice of plaintext attack , Theorem 1 and Theorem 2 prove the indistinguishability of the ciphertext and verifiability of the outsourcing results, respectively.
Theorem 1
(indistinguishability of ciphertext): Assuming that the scheme [Citation20] is completely secure under CPA attack, then the
scheme is also completely secure under CPA attack.
Proof:
Suppose that an adversary can distinguish two different plaintexts with a probability of
under the
security model of the
scheme, then the algorithm B can be constructed to distinguish two different plaintexts with the same probability of
under the
security model of the
scheme.
Let represent the challenger who answered
in the
scheme,
and
perform the following steps:
Setup: sends
to
as a public parameter of the
scheme, and
returns
to
as a public parameter of the
scheme.
Phase1: Firstly, creates an empty outsourced list
and then performs the following inquiries.
Private key query: sends identity
to
, then
sends the
to
for private key query in the
scheme and
generates
, where
,
, which is returned to
and
returns
to
.
Outsourcing key query: sends identity
to
,
searches
in
and returns
to
if it exists, otherwise randomly selects
, and calculates
, then adds the
to the outsourced list
and returns
to
.
Challenge: sends two plaintexts
of the same length and an identity
to
, where
does not perform the outsourcing key query or private key query. Then
sends
to
to complete the challenge phase of the
scheme.
randomly chooses
, then generates ciphertext
of
, and returns
to
. At last,
sends
to
as the challenge ciphertext.
Phase2: continues to ask, and
runs the same operation as Phase1. However,
can not been executed the outsourcing key query or private key query.
Guess: outputs
,
also outputs
as a guess for
.
Then we analyze ’s success probability. When
runs the outsourcing key query about identity
, the value of
can be obtained by
and
. If
continues to ask
for private key query and it can obtain
. Therefore, if
can break the
scheme with a probability of
, then
can also break the
scheme with the same probability of
.
In the above game, successfully simulates the full security model under the
attack of the
scheme. As in [Citation20], the
scheme is completely secure under
attack, similarly, the
scheme is also completely secure under
attack according to theorem 1.Then the verifiability of the
scheme is proved as below.
Theorem 2
(verifiability of outsourcing results): In a malicious model, PKG can detect the error with a probability of if the server returns incorrect results in the veryfiable
scheme, (
represents the number of random numbers).
Proof:
Assume is a malicious server, at the end of the algorithm, the PKG verifies the result as below:
(1)
(1)
(2)
(2)
Since the PKG sends
to the server, and
must return true values of
. Otherwise, the Equations (1) and (2) cannot pass the verification successfully.
Therefore, if returns the error result, the PKG will surely detect this error with a probability of
in the proposed
scheme, (
is the number of random numbers).
4.2 Efficiency Comparison
Suppose the system has a total of users. PKG can precompute
and store it in the system. The following is a computational comparison of PKG between generating private keys directly and outsourcing the task to a single server, as shown in Table .
Table 1: Computation cost comparison of PKG for generating keys directly and outsourcing the task to a single server
In Tables and , represents the total number of system users and
is the bit length of
. Note that
and
are cyclic groups of order
, where
are all 512-bit primes. MExp, MM denote the computation of modular exponentiation and modular multiplication,
is the number of random numbers.
Table 2: Computation cost comparison for different schemes with outsourced key generation
As we know, using the table-lookup method to invoke the Rand subroutine takes MM, and using the square-and-multiply method to execute the modular exponentiation operation takes
MM. In the outsourcing algorithms, we omit other operations such as modular addition.
It can be seen from Table , if PKG directly generates the private keys for the users and need to perform MExp,
MM operations and the total computation cost is roughly
MM. Then if PKG outsources the task of generating private keys to a single server, it only needs to execute 1 MExp,
MM and
Rand operations for
users, the total computation cost is roughly
MM. The server
runs
MExp operations. Therefore, the cost of the PKG is much smaller than that of generating private keys directly.
As shown in Table , the proposed scheme is based on a single server compared with [Citation19], and PKG only needs to perform modular exponentiation operations once during the outsourcing process. Moreover, with the increasing number of users in the system, the computation of PKG remains basically unchanged, and the total computation cost is roughly MM in this paper. However, in scheme [Citation19], the total computation cost is roughly
MM and it is much more expensive than this scheme, so the scheme of this paper has more practical advantages.
4.3 Simulation Result
In this section, we provide the experiment evaluation to show the efficiency of the proposed algorithm based on one untrusted server. The PKG and the cloud server are simulated by Intel Core i5 Processor running at 3.2 GHz with 8G memory and Intel Xeon Processor running at 2.2, 2.19 GHz (two processors) with 128G memory, respectively. Note that and
are cyclic groups of order
, where
are all 512-bit primes. The programing language is Java.
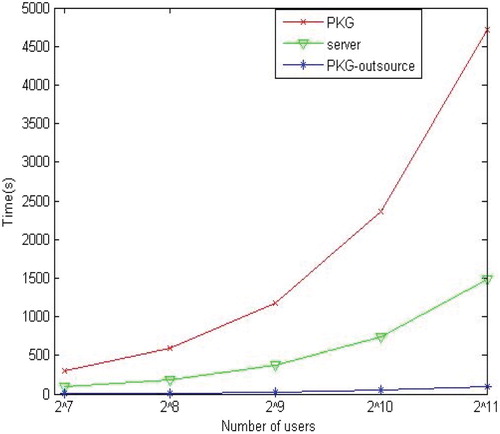
In Figure , we give the time cost of PKG for generating private keys directly and outsourcing the task to the server of the IBE scheme respectively. In the figure, the abscissa represents the total number of users in the system and the ordinate represents the total time cost. It is obvious that the time cost for PKG and the server are less than half of generating private keys directly, with the increasing number of users in the system, the total calculation of the server and PKG is also less than generating private keys directly. For example, when the number of system users is , the PKG calculation time is about 1100 s and the server is about 1400 s, however, the time cost of direct computation is about 4700 s, obviously, it is far higher than the sum of PKG and the server. Therefore, the algorithm of this paper will become more practical when the number of users is continuously increasing.
5. Conclusion
In this paper, we use combinatorial bilinear groups to propose a verifiable outsourcing algorithm for private key generation based on identity-based encryption. The scheme greatly reduces the time cost of PKG, and the server cannot obtain PKG or the private keys of any user during the outsourcing process. PKG outsources the tasks to a single server, and it can improve security and verify the correctness of outsourced results. Finally, the experimental results show that the total calculation of the server and PKG is far less than generating private keys directly.
Additional information
Funding
Notes on contributors

Ting Xue
Ting Xue received the BS degree on electrical and information engineering from Changshu Institute of Technology, China, in 2016. Currently, she is a graduate student at the School of Communication and Information Engineering in Shanghai University, Shanghai, China. Her research interests include applied cryptography and secure outsourcing computing. Email: [email protected]

Yanli Ren
Yanli Ren is an associate professor in School of Communication and Information Engineering at Shanghai University, China. She was awarded an MS degree in applied mathematics in 2005 from Shaanxi Normal University, China, and a PhD degree in computer science and technology in 2009 from Shanghai Jiao Tong University, China. Her research interests include applied cryptography, secure outsourcing computing, and network security.

Guorui Feng
Guorui Feng received the BS and MS degree in computational mathematic from Jilin University, China, in 1998 and 2001 respectively. He received PhD degree in electronic engineering from Shanghai Jiaotong University, China, 2005. From January 2006 to December 2006, he was an assistant professor in East China Normal University, China. During 2007, he was a research fellow in Nanyang Technological University, Singapore. Now, he is with the School of Communication and Information Engineering, Shanghai University, China. His current research interests include image processing, image analysis, and computational intelligence. Email: [email protected]
References
- J. Ye, X. Chen, and J. Ma, “An improved algorithm for secure outsourcing of modular exponentiations,” in IEEE International Conference on Advanced Information Networking and Applications Workshops, 2015, pp. 73–76.
- Y. Ren, M. Dong, Z. Qian, X. Zhang, and G. Feng, “Efficient algorithm for secure outsourcing of modular exponentiation with single server,” IEEE Trans-actions on Cloud Computing. doi: 10.1109/TCC.2018.2851245
- L. Zhang, and S. R. Naini, “Private outsourcing of polynomial evaluation and matrix multiplication using multilinear maps,” in Cryptology and Network and Security [C], 2013, pp. 329–48. doi: 10.1007/978-3-319-02937-5_18
- H. Ma, R. Zhang, Z. Wan, Y. Lu, and S. Lin, “Verifiable and exculpable outsourced attribute-based encryption for access control in cloud computing,” IEEE Transactions on Dependable and Secure Computing, Vol. 14, pp. 461–62, 2017. doi: 10.1109/TDSC.2015.2499755
- J. Li, Y. Wang, Y. Zhang, and J. Han. “Full verifiability for outsourced decryption in attribute based encryption,” in IEEE Transactions on Services Computing, 2017, pp. 1–1.
- Y. Ren, X. Zhang, G. Feng, Z. Qian, and F. Li, “How to extract image features based on co-occurrence matrix securely and efficiently in cloud computing,” IEEE Transactions on Cloud Computing. doi:10.1109/%TCC.%2017.2737980
- S. Hohenberger, and A. Lysyanskaya. “How to securely outsource cryptographic computations,” in TCC. LNCS, Vol. 3378, J. Kilian, Ed. Heidelberg: Springer, 2005, pp. 264–82.
- Y. Wang, Q. Wu, and D. Wong. “Securely outsourcing exponentiations with single untrusted program for cloud storage,” ESORICS, Part I, LNCS 8712, Springer Switzerland, pp. 326–43, 2014.
- J. Liu, and B. Yang. “A new algorithm for secure outsourcing composite modular exponentiation,” in: IEEE 2nd International Conference on Information Science and Control Engineering, 2015, pp. 461–65.
- J. Ye, and J. Wang. “Secure outsourcing of modular exponentiation with single untrusted server,” in: 18th International Conference on Network-Based Information Systems, 2015, pp. 643–45.
- X. Chen, W. Susilo, J. Li, D. S. Wong, J. Ma, S. Tang, and Q. Tang, “Efficient algorithms for secure outsourcing of bilinear pairing,” Theoretical Computer Science, Vol. 562, pp. 112–21, 2015. doi: 10.1016/j.tcs.2014.09.038
- H. Tian, F. Zhang, and K. Ren, “Secure bilinear pairing outsourcing made more efficient and flexible,” in: Proceedings of ASIA CCS, Singapore, April 14-17, ACM Press, New York, 2015, pp. 417–26.
- Y. Ren, M. Dong, Z. Niu, and X. Du, “Noninteractive verifiable outsourcing algorithm for bilinear pairing with improved checkability,” Security and Communication Networks, 2017, pp. 1–9, 2017. doi: 10.1155/2017/4892814
- A. Shamir, “Identity-based cryptosystems and signature schemes,” In Proc. CRYPTO 84, California, USA, Aug. 19–22. Springer, Berlin, 1984, pp. 47–53.
- D. Boneh, and M. Franklin, “Identity-based encryption from the weil pairing,” Proc, CRYPTO 01, Califomia, USA, Aug. 19-23. Springer, Berlin, 2001, pp. 213–29.
- Y. Ren, and D. Gu, “Cca2 secure (hierarchical) identity-based parallel key-insulated encryption without random oracles,” Journal of Systems and Software, Vol. 83, pp. 153–62, 2010. doi: 10.1016/j.jss.2009.07.046
- J. Yu, R. Hao, H. Zhao, M. Shu, and J. Fan, “Iribe: intrusion-resilient identity-based encryption,” Information Sciences, Vol. 329, pp. 90–104, 2016. doi: 10.1016/j.ins.2015.09.020
- J. Li, X. Chen, C. Jia, and W. Lou, “Identity-based encryption with outsourced revocation in cloud computing,” IEEE Transactions on Computers, 64, pp. 425–37, 2015. doi: 10.1109/TC.2013.208
- Y. Ren, and J. Cai, “Verifiable outsourcing private key generation algorithm in an identity-based encryption scheme,” Journal of Communication (in Chinese), Vol. 36, pp. 1–6, 2015.
- A. Lewko, and B. Waters, “New techniques for dual system encryption and fully secure HIBE with short ciphertexts,” Theory of Cryptography Conference [C], pp. 455–79, 2010.