Abstract
This paper focuses on the emergence factors and themes that surfaced as result of cyberbullying activities among adolescents in Malaysia that have never been reported before this one. The actual research attempted to fill the knowledge gap in cyberbullying phenomenon by focusing on factors that contribute to its activities among adolescents in Malaysia. In addition, the research seeks to understand the antecedents and the contexts and prevailing conditions that influence it, as well as the phenomenon, the coping strategies and the consequences resulting from the coping strategies. Using a grounded theory methodology, in-depth interviews were conducted on adolescents aged between 12 and 18 years from different schools in the state of Perlis. The data were analysed using NVivo 10 by methodically coding and categorising the data in open, axial and selective coding to arrive at a model development. A paradigm model will be obtained based on informants' individual comments and experiences that uniquely contribute to the body of knowledge on cyberbullying phenomenon in Malaysia. The involved elements derived from the model are; the antecedents of cyberbullying; the phenomenon; the coping strategies by informants and the consequences resulting from these strategies. The significance of this study lies in its attempt to provide a working framework for reducing adolescents' technology abuse that will eventually lead to cyberbullying and to find solutions for adolescents to tackle cyberbullying problems if it ever happened. This study is hoped to benefit all the parties: adolescents, parents, teachers and other stakeholders to minimise adolescents' cyberbullying phenomenon. At a time when most adolescents are exposed to cyber bullying around the world, this research is both timely and necessary.
Introduction
The intention of current research was to construct a grounded theory of cyberbullying phenomenon on the basis of adolescents' reports about their own cyberbullying incident. Second, most of existing researches were based on traditional bullying occurrence; therefore, it is hoped that this study can provide a more in-depth descriptive account of cyberbullying phenomenon. The most fundamental ground to the researcher nevertheless is to come out with a working hypothesis or process model of cyberbullying. The researcher conducted the present study to examine the process by which cyberbullying occurs and to propose a preliminary paradigm model (Strauss & Corbin, Citation1998) that can be tested in future research. The researcher preferred grounded theory methodology as it is preferably suited to construct a data-based theory that can be utilised as a foundation for future study (Creswell, Citation1998; Strauss & Corbin, Citation1998). Given the prevalent nature of cyberbullying, the researcher questioned how adolescents perceive cyberbullying and whether their experiences are aligned to the existing views in the literature. The researcher believed that a grounded theory analysis would facilitate researchers to ascertain other characteristics of cyberbullying that might justify its widespread unremitting incident.
Definitions of cyberbullying
Descriptions of cyberbullying are consistent from author to author. Shariff (Citation2009) in her book Confronting Cyberbullying stated that definitions of cyberbullying by experts in this field share some similarities in defining it. Other experts such as Hinduja and Patchin (Citation2009) developed cyberbullying definitions to be straightforward, brief and practically comprehensive and encapsulates the most significant elements such as: (1) Wilful: the behaviour has to be purposeful, not accidental; (2) Recurring: bullying displays a pattern of manners, not just one isolated occurrence; (3) Harm: the objective must distinguish that harm was imposed and (4) The usage of computers, cell phones and other electronic devices differentiates cyberbullying from traditional bullying. Therefore, cyberbullying in a sentence is wilful and repeated harm inflicted through the use of computers, cell phones and other electronic devices (Hinduja & Patchin, Citation2009).
Method
Informants
One hundred and five adolescents (n = 105) from four secondary school and three from a primary school participated in this research. Data were collected over a period of 7 months, and these were done after major examinations as not to disrupt their academic activities. All respondents were enrolled in various educational backgrounds and ranged between the ages of 12 and 18. Most of the respondents were chosen through the school counsellors but many of the informants were picked up by snow-balling technique as the adolescents will inform about others who have engaged in the cyberbullying activities as a perpetrators or victims. The researcher also went online for a period of 6 months in order to experience the real situation of cyberbullying phenomenon and to collect the examples related to themes of study. This was done particularly via one of the most prominence social networking sites among adolescents – Facebook.
Procedure
Data were collected using grounded theory procedures described in Strauss and Corbin (Citation1990, Citation1998). Creswell (Citation1998) suggested that a standard grounded theory research will comprise 20–30 interviews that collectively saturate the categories that emerge during analysis. Data are accumulated in four phases that differ with regard to purpose and data collection strategies (Harry, Sturges, & Klingner, Citation2005) is summarised in Table . Analysis of data of current study were completed by using NVivo Version 8 Software as to meet the terms of ‘trustworthiness’, ‘rigorousness’ or ‘quality’ of the data; therefore, it is important that these are carried out in a thorough and transparent manner (Crawford, Leybourne, & Arnott, Citation2000; Creswell, Citation1998; Kirk & Miller, Citation1986; Lincoln & Guba, Citation1985; Miles & Huberman, Citation1994; Seale, Citation1999). Therefore, using software in the data analysis process has been thought by some to add rigour to qualitative research (Richards & Richards, Citation1994).
Table 1 Four phase of data collection.
Phase 1 data collection incorporated individual interviews and focus group interviews that allowed the researcher to generate a list of codes within five categories in the paradigm model specifically antecedents, definitions of the phenomenon, context and conditions that affect the phenomenon, coping strategies and consequences of the coping strategies taken. The main reason of open coding is to distinguish significant topics creditable of closer analysis and explanation (Strauss & Corbin, Citation1998). In all, 30 adolescents were interviewed individually, and 11 informants who were divided into 3 groups with 3 individuals in 2 groups and 5 in a group. The interviews in this stage was to implore preliminary thoughts and impressions about cyberbullying in a setting in which informants could react to each other (Krueger, Citation1994). All interviews were based on both open-ended responses to the following questions:
How would you describe cyberbullying?
What do you do when you cyber bully? What others did to you when you are cyber bullied?
Are there any situations when you are most likely to cyber bully? Are there any situations when you are most likely to be cyber bullied?
How do you cope when you do cyberbullying? How do you cope when you being cyber bullied?
What are some positive and negative consequences of cyberbullying?
These questions are consistent to the major elements of the paradigm model described by Strauss and Corbin (Citation1998). Table shows 103 preliminary codes obtained from the interview sessions with each code represent a significant topic of discussion related to cyberbullying. Many adolescents for instant, mentioned characteristics of online technology such as social networking are facilitating factors to cyberbullying. The researcher thus concluded that the focus group and individual interviews saturated the codes that were necessary to understand the phenomenon of cyberbullying after similar codes emerged during the interviews.
Table 2 Initial categories and codes in Phase 1.
Phase 2 that exercised axial coding encompassed of nine individual interviews and four in a focus group, which aimed to elucidate codes in detail. Phase 2 clusters codes into themes and patterns related to cyberbullying. Axial coding allowed the researcher to structure an advance understanding of each of the five main components in the paradigm model (Strauss & Corbin, Citation1998). A structured interview was used in which each individual responded to nine questions and follow-up probes. Question 1 was intended to familiarise individuals to a typical cyberbullying situation. Questions 2 through 9 were based on the five questions presented in Phase 1 of data collection. Follow-up probe questions were added to focus in more detail on prominent categories mentioned during Phase 1.
Describe a typical situation in which you might cyber bully? Or being cyber bullied?
What causes you to cyber bully others or being cyber bullied by others? Probes: self, perpetrators (friends, strangers), online technology characteristics.
Please list as many reasons as you can why you bully cyber? Probes: constructive, destructive behaviour.
What do you do to cope with cyberbullying? Probes: Active, aggressive, avoidance, cognitive.
By means of what you would be cyber bullied? Probes: Internet, mobile phone.
Can you identify conditions or situations where you are most likely to cyber bully? Probes: issues specific to cyberbullying, characteristics of guardian.
How you been bullied or bullied online or via a mobile phone? Probes: word, sentences, image, voice, video (methods of cyberbullying).
What are the impacts of cyberbullying? Probes: emotional, behaviour, social, physical, academic.
What are the positive and negative consequences of cyberbullying? Probes: quality of life and quality of academic.
The researcher identified a range of preliminary themes on the foundation of five categories and codes as illustrated in Table . The researcher merged themes in a way in accordance with the interviews. Phase 2 provides the researcher with the possibility to organise and label themes that could be tested in Phase 3. Therefore, macrothemes and themes identified in Phase 2 were viewed as provisional, subject to revision and removal in Phase 3.
Selective coding was intended for Phase 3. According to Strauss and Corbin (Citation1998), selective coding is the process of assessing the macrothemes and themes identified in Phase 2, linking the categories to one another, and developing a plot that integrates the paradigm model. Thirty one informants participated in six focus groups interviews to serve several purposes such as one to duplicate crucial codes and themes that were identified in Phase 1 and 2 (Strauss & Corbin, Citation1998). Second selective coding was used to delve into detail the connection among macrothemes within each category (Strauss & Corbin, Citation1998). A third objective was to request informants to discuss the five categories in the paradigm model related to each other for example in order to understand the process of cyberbullying, informants discussed the relationship between antecedents and contextual conditions of cyberbullying (Strauss & Corbin, Citation1998). This information facilitated the researcher to construct a credible paradigm model that could be authenticated in Phase 4. Final objective was to create a story line, which consists of a descriptive story about central phenomenon of this research. This phase consists of two major outcomes. The first outcome distinguished range of themes that were considered within macrothemes in each of the five categories. Altogether as shown in Table 2, 105 themes were identified and were grouped into 5 macrothemes. The second outcome was a constructed preliminary paradigm model that has been validated in Phase 4 of data collection and illustrate in detail in a following section. The preliminary paradigm model consisted of the macrothemes and themes acknowledged so far.
Finally, Phase 4 was projected to validate and explain the paradigm model constructed in Phase 3. Twenty informants in four focus groups were interviewed and were asked to respond to a paradigm model based on responses in Phase 3. The central idea was to perform member checks on the preliminary paradigm model. Informants were asked whether the themes and macrothemes were conceivable to them. A second purpose was to ask for comments and reactions concerning the reliability of the paradigm model. Informants in Phase 4 were shown preliminary diagrams of the paradigm model and asked to comment on whether the model is sensible to them and in line with their own cyberbullying activities. A third purpose was to encourage adolescents to refine or add to any of the categories, macrothemes or themes in the paradigm model. According to Maxwell (Citation1996), this last stage facilitated to guarantee that the final paradigm model was fully saturated, reliable and credible.
Findings
A paradigm model of cyberbullying includes antecedents, the phenomenon, contexts and conditions, coping strategies and consequences of cyberbullying. However, for this paper, only one aspect of the phenomenon will be discussed – the emergence factors or themes of cyberbullying.
Emerging themes of cyberbullying
The researcher proposed that the principal theme that emerged from the open coding investigative process, which in-depth interviews provided, was that adolescents especially the bullies desired to gain ‘a sense of satisfaction’ over their lives and they found that this concept could be easily achieved by their use of online media applications. The imperative new categories that emerged from these interviews were (1) the significance of social network, in this case, Facebook for the informants, (2) the characteristics of the bullies or perpetrators, (3) the positive impacts of cyberbullying, (4) the role of supporters and the instigators in cyberbullying activities, (5) the lack of nonverbal communication in online communication that contributes to misunderstanding, (6) the types of online friends added by the victims, which provide the opportunity for cyberbullying to take place and (7) the hard to remove cyberbullying incidents in the cyberspace makes it remain for all to see even though it happens only once. The identification of these seven categories are the elements of the paradigm model of cyberbullying that was never discussed prior to this study and therefore should be useful to add to the existing literature and for adolescents and stakeholders to have a better grip on the phenomenon in the Malaysian context.
All factors emerged evidently are interpretive in nature and entail advance exploration; however, there was sound consistency among the informants in this research. After all, most informants illustrated these factors impulsively and when asked honestly to assess these factors in Phase 4 of this study using peer member checks, all informants (n = 20) strongly agreed with them.
Facebook – the permanence of expression
Online communication has a permanence and inseparability that are very difficult to erase. Mobile phones are generally carried all the time, making them difficult for victims to ignore, and computers are generally used everyday. Although, of course a mobile phone can be ignored, text messages and emails can be sent so that every time the phone or computer is turned on, the nasty messages are waiting. Moreover, emails and defamatory material or modified photographs about a person on the Internet are extremely difficult to remove once posted, as millions of people can download and save it immediately. These forms of expression can then be forwarded on to hundreds of other people and saved in their desktop or laptop computers. (Shariff, Citation2008, p. 34)
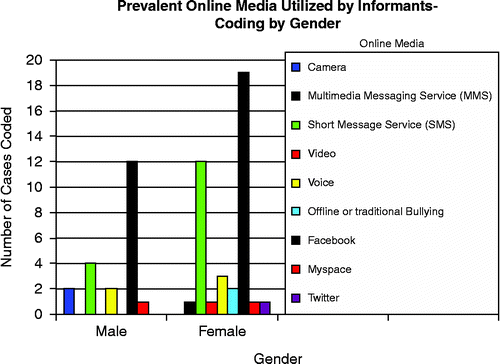
Developed in 2004 by then Harvard University student Mark Zuckerberg, Facebook is a social networking site used by more than 800 million active users around the world in 70 languages (Collier & Magid, Citation2012). Current research suggests that adolescents are exposed to the information and communication technologies in their daily life and this corresponded well with Shariff's (Citation2008) suggestions that online media have a permanence and inseparability that are very hard to remove. Figure summarises the prevalent of online media most popular among the informants while engaging themselves in cyberbullying activities.
In this case, the informants admitted that they cannot be separated from their mobile phones (M = 48%, F = 52%) and social networks (M = 35%, F = 65%) as means of communication media. Unfortunately, these informants also got themselves implicated in cyberbullying activities by means of communication media. Five informants (n = 5) revealed that they had been bullied right after they registered on Facebook. Figure fine points the detail of those media with short message service or SMS (M = 31%, F = 69%) and Facebook (M = 34%, F = 66%) as the uppermost medium used by the informants in cyberbullying activities while MySpace came second. Other than that 63% of the male informants and 37% of the female informants used voice facility to socialise.
Informants described the inevitability to avoid online communication to socialise. The researcher conceptualised this as the permanence of expression. The features of online media that attract the informants to continue using it include the ease of use, fun, free and interactivity. Therefore, the researcher's proposition is that the characteristics of online media, especially Facebook, have motivated adolescents to utilise it for socialising in the cyberspace. Adolescents use it mostly for socialising, day-to-day news about friends and families, school work, emotional support, self-expression, informal learning, discovering and exploring interests, and learning about the world borderlessly (Collier & Magid, Citation2012).
Researches show that adolescents and technologies cannot be separated. This inseparability, which is very difficult to erase, is exposing them to cyberbullying.
The characteristics of the perpetrators
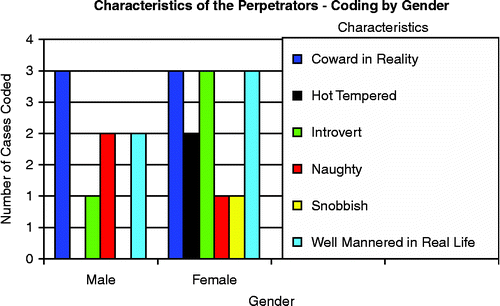
To perform traditional bullying, a bully logically must have a strong physique in order to harass his or her victim or the perpetrator comes in group so that they can perform the action of bullying. However, now everyone can harass others regardless of their conditions as long as they are online. According to the victims interviewed, they described six types of perpetrators; the one who is actually a coward in real life, introvert, hot-tempered, snobbish or arrogant, naughty and well-mannered. Responses from the victims enlightened the characteristics of bullies they know well enough. Figure outlines the characteristics of the perpetrators obtained from the informants' feedback. The researcher ascertained that the perpetrators can be categorised as two distinct personalities. One would be extrovert, which for the victims could somehow absorb the perpetrators' actions, as they in reality are mischievous and hot-tempered individuals.
Nevertheless, the second personality somehow caught the victim by surprise as the perpetrators were usually introverts (M = 25%, F = 75%) in real life. For the victims, they seemed shy, quiet and well-mannered (M = 30%, F = 70%) during face-to-face conversations, but when they were online they could turn out to be rather intimidating. Some informants described the perpetrators as cowards (M = 46%, F = 54%) in reality, but transformed into some kind of a fiend while using the Internet.
The researcher, therefore, concludes that online media has the opportunity to alter its users' behaviour due to its capabilities of being anonymous. Users can be anybody they want when online and remain hidden from others.
The positive impacts
To date, there is no literature that mentioned the positive impacts of cyberbullying. Breguet (Citation2007) found cyberbullying victims feel abandoned, lack self-confidence and dishonoured. As a result of these negative feelings, Patchin and Hinduja (Citation2006) and Strom and Strom (Citation2005) emphasised that victims may undergo lowered self-respect, despair, feelings of depression and alienation, which may also lead to psychological turmoil. Gati, Teyi, Tury, and Wildmann (Citation2002) in their qualitative research of a female adolescent identified with eating disorder, established that sexual harassment on the Internet acted as a significant part in the advancement of her disorder.
Patchin and Hinduja (Citation2006) in their research of habitual Internet users verified that frequent feelings stumbled upon by cyberbullying victims embrace disappointment and rage (Patchin & Hinduja, Citation2006). Beran and Li (Citation2005), in a study concerning 432 students, indicated that 57% of cyberbullying victims felt aggravated on countless occurrences, and about 36% felt miserable and affronted. Beran and Li (Citation2005) strongly recommended that these emotions of rage, misery and upset will manipulate students' skills to concentrate in school and thrive academically (Beran & Li, Citation2005). The effects of cyberbullying have actually exceeded the emotional level when there are suicides among children and youth in response to extreme cases of cyberbullying (Shariff, Citation2009).
However, the researcher managed to observe positive impacts for both the bully and the victim. According to the informants particularly the bullies, cyberbullying brings them satisfaction (M = 55%, F = 45%) and overconfidence (M = 31%, F = 69%) after the deed was accomplished. Therefore, the researcher ironically considers these as the positive impacts of cyberbullying.
However, cyberbullying also procreates positive impacts to the victims. The informants mentioned that they were relieved when cyberbullying was successfully overcome after the right coping strategy was implemented.
The supporting actors
In existing literature, two significant players most highlighted in cyberbullying are: the bully and the victim. Differ to conventional bullying; study on cyberbullying has constantly exposed an important correlation among cyberbullies and those who are victimised via online (Li, Citation2007; Raskauskas & Stoltz, Citation2007; Totten, Quigley, & Morgan, Citation2004; Ybarra & Mitchell, Citation2004a, Citation2004b). In other words, adolescents who bully their peers online are more likely to be victimised themselves, in contrast to those who do not engage in cyberbullying behaviours.
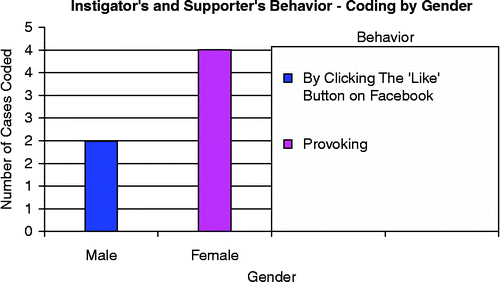
However, the researcher was enlightened by the informants in Phase 3 and confirmed in Phase 4 of data collection that apart from the perpetrators, victims and bystanders, there were two other ‘actors’ with connection in cyberbullying behaviour. The informants identified these as the instigators and the supporters of cyberbullying. Previous literature has been paying attention only to the perpetrators and victims of cyberbullying. Figure summarises these individuals and which of their actions were considered as instigating and supporting cyberbullying activities. According to the informants, there were individuals who liked to support the perpetrators' remarks by clicking the ‘like’ button on the Facebook wall, thus encouraging them. Another kind of individuals, according to the informants, were those who liked to provoke cyberbullying incidents by initiating the aggravation and let others do the actual harassment on the victim. The researcher found that these activities were performed solely via Facebook.
The researcher's proposition is that the instigators and supporters are those who want to witness the fight between the bully and the victim. They will have some kind of satisfaction when their actions have successfully triggered cyberbullying.
The lack of non-verbal communication
Furthermore, the researcher noticed that the near absent of non-verbal communication produced several impacts among adolescents. For instance, by using any online applications, the perpetrators will not know the extent of severity of their wrongdoings. Victims will not be able to express their depression, resentment, humiliation, etc. when facial or non-verbal expression is not present during cyberbullying. Emoticon alone is not enough to convey the exact emotion of the victims. Because of this criterion, for example, adolescents can be seen involving themselves in the act of sexting without any embarrassment whatsoever – which they may not be doing openly in reality. In addition, messages will often be misinterpreted when the receiver tries to construe the meaning via their own analysis that is frequently influenced by the receiver's present contexts and conditions. To add to this predicament, there will often be no immediate feedback to clarify matters (unless real-time video conferencing is used), not until the damage has already been done. Future studies should consider examining these deficiencies in cyberbullying contexts including the degree of sexual related matters, which adolescents engaged in during online activities.
The types of online ‘friends’ added on social networks
The researcher hypothesised that there are four types of individuals in the victim's friend's list: first, individuals with genuine information who are the victim's own friends; second, individuals who are strangers but with sincere intention to be friends with the victim and therefore provide real information in their social network accounts; third, strangers with fake identities with unhealthy intentions towards the victim; and finally, individuals who are familiar with the victim but provide fake identities in order to do harassment. The researcher, moreover, found that online media can facilitate in transforming adolescents into what they want to be which would not take place in reality. They can pretend to be younger when they are actually a grown-up, they be able to pretend as the opposite sex when they want to deceive others; they can transform into anyone other than themselves in cyberspace. It is impossible for the victims to be capable of knowing all individuals they have added, but the perpetrators will have lots of opportunities to study their victim in the comfort of their home before they strike. Future research should therefore investigate prevalence of cyberbullying behaviour among these four types of individuals and why do adolescents are keen to be anyone but themselves in cyberspace.
Recurring – the unending bullying
Many cyberbullying experts suggest that to meet the term bullying, the act of bully must be repetitive. However, the researcher put forward that although the act of bullying occur only once, sometimes the harassing material uploaded lingers forever for anyone to download or forward it to others. This is due to the difficulty to remove it as soon as it is online.
Conclusion
Previous researches have supported the view of cyberbullying negative impacts to adolescents. Breguet (Citation2007) found cyberbullying victims feel abandoned, unselfconfident and dishonoured. As a consequence of these negative feelings (Patchin & Hinduja, Citation2006; Strom & Strom, Citation2005) stressed that victims may undergo lowered self-respect, despair, feelings of depression and alienation, which may also lead to psychological turmoil. Gati et al. (Citation2002) in their qualitative research of a female adolescent identified with eating disorder established that sexual harassment on the Internet acted as a significant part in the advancement of her disorder. In addition, Patchin and Hinduja (Citation2006) in their latest research of habitual Internet users verified that frequent feelings stumbled upon by cyberbullying victims embrace of disappointment and rage. Beran and Li (Citation2005) in a study concerning 432 students implied that 57% of cyberbullying victims felt aggravated on countless occurrences, and about 36% felt miserable and affronted. Beran and Li (Citation2005) strongly recommended that these emotions of rage, misery, and upset will manipulate students' skills to concentrate in school and thrive academically. The effects of cyberbullying have actually exceeded the emotional level when there have suicides among children and youth in response to extreme cases of cyberbullying (Shariff, Citation2009).
Findings from current study support several claims from earlier research and produce several new findings. The researcher's finding confirms the claim that cyberbullying yields several harmful impacts on adolescents (Hinduja & Patchin, Citation2009; Shariff, Citation2008). Respondents equivalently reported higher levels of cyberbullying incidents happened to them when they registered to Facebook.
The current study should be considered as investigative study on two grounds. One is that qualitative methods are used intended to generate rather than validate a data-based theory. Second, adolescents were selected purposely because they involved in cyberbullying experience. These include the bystanders and supporters who do not directly involve in cyberbullying incidents.
The researcher observed three limitations of the current research. One is that data consisted of the judgments of respondents who admitted they had involved in cyberbullying incidents. It is potential, however, that these adolescents provided incorrect statements or that the bystanders would report different beliefs and behaviours. A second insufficiency is that the paradigm model is intended to disclose associations among diverse aspects of cyberbullying rather than to propose a fundamental connection among the five components. The third inadequacy was that only one particular ethnic group has been implicated in this study. The Malays may perhaps be bounded with beliefs and attitudes that might be totally different from other main ethnics in Malaysia, and this could results in dissimilar reactions regarding cyberbullying experience.
For future studies, the researcher proposes that a quantitative research to be taken in Malaysian context. This might generate a generalisation to a wider and diverse population as the current study only contemplates on a single ethnic group and perspectives of cyberbullying.
Disclosure statement
No potential conflict of interest was reported by the author.
Additional information
Notes on contributors
Hanif Suhairi Abu Bakar
Hanif Suhairi Abu Bakar is a senior lecturer in the Center for Communication Technology and Human Development at the Universiti Malaysia Perlis. His research interests focus on human communication, new media and information communication technology.
References
- Beran, T., & Li, Q. (2005). Cyberharassment: A study of a new method for an old behavior. Educational Computing Research, 32, 265–277.
- Breguet, T. (2007). Frequently asked questions about cyberbullying. New York, NY: The Rosen Publishing Group.
- Collier, A., & Magid, L. (2012). A parents' guide to Facebook. Retrieved from http://www.connectsafely.org/pdfs/fbparents.pdf.
- Crawford, K. H., Leybourne, M. L., & Arnott, A. (2000). How we ensured rigour in a multi-site, multi-discipline, multi-researcher study. Forum: Qualitative Social Research. 1, Art. 12. Retrieved from http://www.qualitative-research.net/fqs.
- Creswell, J. W. (1998). Qualitative inquiry and research design: Choosing among five traditions. Thousand Oaks, CA: Sage.
- Gati, A, Teyi, T., Tury, F., & Wildmann, M. (2002). Anorexia nervosa following sexual harassment on the Internet: A case report. International Journal of Eating Disorders, 31, 474–477.
- Harry, B., Sturges, K. M., & Klingner, J. K. (2005). Mapping the process: An exemplar of process and challenge in grounded theory analysis. Educational Researcher, 34, 3–13.
- Hinduja, S., & Patchin, J. W. (2009). Bullying beyond the schoolyard: Preventing and responding to cyberbullying. Thousand Oaks, CA: Sage.
- Kirk, J., & Miller, M. L. (1986). Reliability and validity in qualitative research. London: Sage.
- Krueger, R. A. (1994). Focus groups: A practical guide for applied research (2nd ed.). Thousand Oaks, CA: Sage.
- Li, Q. (2007). New bottle but old wine: A research of cyberbullying in schools. Computers in Human Behavior, 23, 1777–1791.
- Lincoln, Y. S., & Guba, E. G. (1985). Naturalistic inquiry. Newbury Park, CA: Sage.
- Maxwell, J. A. (1996). Qualitative research design: An interactive approach. Thousand Oaks, CA: Sage.
- Miles, M. B., & Huberman, M. A. (1994). Qualitative data analysis: An expanded sourcebook (2nd ed.). Beverly Hills, CA: Sage.
- Patchin, J. W., & Hinduja, S. (2006). Bullies move beyond the schoolyard a preliminary look at cyberbullying. Youth Violence and Juvenile Justice, 4, 148–169.
- Raskauskas, J., & Stoltz, A. (2007). Involvement in traditional and electronic bullying among adolescents. Developmental Psychology, 43, 564–575.
- Richards, L., & Richards, T. (1994). From filing cabinet to computer. In A. Bryman & R. G. Burgess (Eds.), Analysing qualitative data (pp. 146–172). London: Routledge.
- Seale, C. (1999). The quality of qualitative research. London: Sage.
- Shariff, S. (2008). Cyber-bullying: Issues and solutions for school, the classroom and the home. Abingdon, Oxfordshire: Routledge.
- Shariff, S. (2009). Confronting cyber-bullying: What schools need to know, to control misconduct and avoid legal consequences. New York, NY: Cambridge University Press.
- Strauss, A., & Corbin, J. (1990). Basics of qualitative research: Grounded theory procedures and techniques. Newbury Park, CA: Sage.
- Strauss, A., & Corbin, J. (1998). Basics of qualitative research: Techniques and procedures for developing grounded theory (2nd ed.). Thousand Oaks, CA: Sage.
- Strom, P. S., & Strom, R. D. (2005). When teens turn cyberbullies. The Educational Digest, 71, 35–41.
- Totten, M., Quigley, P., & Morgan, M. (2004). CPHA safe school study. Retrieved from http://www.cpha.ca/uploads/progs/_/safeschools/safe_school_study_e.pdf.
- Ybarra, M. L., & Mitchell, K. J. (2004a). Online aggressor/targets, aggressors, and targets: A comparison of associated youth characteristics. The Journal of Child Psychology and Psychiatry, 45, 1308–1316. Retrieved from http://www3.interscience.wiley.com/journal/118755439/abstract.
- Ybarra, M. L., & Mitchell, K. J. (2004b). Youth engaging in online harassment: Associations with caregiver–child relationships, Internet use. Journal of Adolescence, 27, 319–336.