?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.ABSTRACT
Cabling, handoff, and switching costs play pivotal roles in the design and development of cellular mobile networks. The assignment pattern consisting of which cell is to be connected to which switch can have a significant impact on the individual cost. In the presence of the limitation on the number of cells that can be assigned to a switch, the problem of the cell to switch assignment (CSA) becomes nondeterministic polynomial time hard to solve with all effective solutions being based on metaheuristic optimization algorithms (MOA) approach. This article applies three recently evolved MOA, namely, flower pollination algorithm (FPA), hunting search (HuS), and wolf search algorithm (WSA) for solving CSA problem. Comprehensive computational experiments conducted to collate the performance of the three algorithms indicate that FPA is superior to both HuS and WSA with respect to attaining the global best value and faster convergence with desired CSA.
Introduction
The mobile station (MS) of a cellular network communicates through a stationary base station (BS) to the mobile switching center (hereafter called as the switch) which routes calls either to another BS or to a public switched telephone network. The cell is defined as the basic geographic unit of a cellular mobile network and is usually represented as hexagons, with the entire cellular mobile network being portrayed as a honeycomb structure. As the distance between a subscriber and the BS increases, the signals between the MS and the BS become weaker while interference from neighboring cells increases. Handoffs are used to avoid the problems associated with weak signals and interference while maintaining mobility. A handoff occurs when a call is transferred automatically by the mobile network from a radio channel in one BS to another radio channel in an adjacent BS as the subscriber crosses into the adjacent BS cell area. As the subscriber advances toward the boundary of the current cell, the call strength dips to a minimum threshold and the MS alerts the network (Pierr and Houéto Citation2002). The network finds an unused channel on the appropriate adjoining BS and provides the MS with all the information needed for the handoff. The MS then switches to the new channel, usually without the subscriber noticing the transition. The cells among which the handoff frequency is high should be assigned to the same switch as far as possible to reduce the cost of handoffs (Merchant and Sengupta Citation1995). The endeavor should be to assign cells to switches (determining which cell to be connected to which switch) such that the total cost comprising of cabling cost between cells and switches, handoff cost between adjacent cells and switching cost between two or more switches, is minimized subject to the constraints of the call handling capacities of switches (Menon and Gupta Citation2004).
The CSA problem was introduced by Merchant and Sengupta (Citation1995) whereby heuristic approach based upon a greedy strategy (denoted as H) was presented while making the observation that optimal approaches fail even with relatively small problem instances. Later, Bhattacharjee, Saha, and Mukherjee (Citation1999) proposed other versions of CSA heuristics (H-II through H-VI). It was found that there was no single heuristic that performed equally well in terms of cost and execution time. Bhattacharjee, Saha, and Mukherjee (Citation2000) solved the problem of balancing traffic (load) amongst switches when the cluster of cells to be connected to a switch is decided during the design of a personal communication service network. Saha, Mukherjee, and Bhattacharjee (Citation2000) proposed a heuristic which was simpler and faster than earlier published results. Mandal, Saha, and Mahanti (Citation2002) employed block depth first search (BDFS) algorithm in which an admissible heuristic was used in order to minimize the paging, updating, and physical infrastructure costs. The same authors in 2004 proposed another heuristic combining BDFS with iterative deepening A* (IDA*) which gave superior results compared to earlier published results in terms of quality of the solution obtained and the execution time to obtain the optimal solution. Approaches based upon metaheuristic optimization algorithms (MOA) (Chawla and Duhan Citation2014, Citation2015, Yang Citation2014) for resolving the CSA problem can also be found in the literature. Various MOA-based approaches to address the above problem include simulated annealing (Menon and Gupta Citation2004), tabu search (Pierr and Houéto Citation2002), memetic algorithm (Quintero and Pierre Citation2002), ant colony optimization (Shyu, Lin, and Hsiao Citation2004), and modified binary particle swarm optimization (Udgata et al. Citation2008). All these algorithms except the last one considered the cabling cost and the handoff cost as the cost for assigning cells to the switches. In our approach, switching cost is also added to the total cost in addition to the cabling cost and handoff cost. This paper experimentally demonstrates the application of three recently introduced MOA, namely, flower pollination algorithm (FPA), hunting search (HuS), and wolf search algorithm (WSA) to efficiently solve CSA problem in the cellular mobile network.
Mathematical Problem Formulation
Given a cartel of cells and switches whose positions are established, the CSA problem consists of determining a cell assignment pattern to minimize the cost function, while respecting certain constraints, particularly those related to the capacity of the switches (Menon and Gupta Citation2004; Udgata et al. Citation2008). The various notations used are as follows:
number of cells;
number of switches;
handoff cost occur between cell
and cell
;
cabling cost between cell
and switch
;
distance between cell
and switch (MSC)
;
call handling capacity of switch
;
number of communications per time unit in cell
.
1, if cells
and j are assigned to same switch.
0 if cells are assigned to different switches.
1, if cell
assigned to switch
0 otherwise.
For all cases, the range of ,
and
are defined as
Formulation of Cost Function
The cost function consists of the summation of cabling, handoff, and switching cost. Each one of them is described as follows.
Cabling Cost
Cabling cost depends upon the distance between the base station and switch and number of calls that a cell can handle per unit time. The total cabling cost is given by
where is the cost of cabling per kilometer.It is also modeled as a function of the number of calls that a cell can i handles which is given by
In Equation (4), A and B are constants whose values are 1 and 0.001, respectively, as reported in the literature (Udgata et al. Citation2008).
Handoff Cost
Total handoff cost is given by the relation
Two types of handoffs, one which involves only one switch and another which involves two switches, are considered in our approach. When the two cells are assigned to the same switch, the handoff cost is negligible, whereas if the two cells among which handoff takes place are connected to two different switches, handoff cost is quite significant and is calculated using Equation (3).
Switching Cost
The total switching cost involved is defined as
where is the total number of calls switch i can handle per unit time and
is the cost function of switching a call in switch i. Thus the load at switch i is given by
involves both the cost of switching and the cost of maintaining a call at switch. Thus,
can be represented as
where denote the call switching capacity of switch i and α is a constant whose value is set at 40 (Udgata et al. Citation2008).
Total Cost
Total cost is the summation of all three costs .The objective function or the cost function is thus given by
Constraints of the Problem
The first constraint that should be satisfied is that each cell must be assigned to exactly one switch. This can be expressed as
The second constraint is that optimization is to be carried out in such a way that the call handling capacity of the switch is not breached. It means that the total load of all the cells which are assigned to a particular switch is below the capacity of the switch. Mathematically it can be represented as
The aim is to minimize Equation (7) subject to the condition that constraints given by Equations (8) and (9) are satisfied.
Methodology
Many algorithms and procedures are available in the literature for finding the solution to Nondeterministic polynomial time (NP) hard problems (Roa Citation2009, Yang Citation2010). Some of them are exact methods that are guaranteed to find optimum solutions provided enough time is at hand, while the others are approximation techniques, usually called MOA which will give a good solution to problems within a reasonable amount of time, with no guarantee of achieving optimality (Yang Citation2014). Given the limitation of exact methods in solving large combinatorial optimization problems (Blum and Roli Citation2003), approaches based on MOA are often preferred in many practical situations. These emulate the biological, physical,or natural phenomena of the real world (Yang Citation2015). They usually perform well in most practical situations and have become increasingly popular among researchers in the optimization field (Sutcliffe and Neville Citation2014). Unlike the deterministic ones, they are derivative-free, competent in solving convex and non-convex problems (Yang Citation2010), independent of the initial solution, and have the inbuilt inheritance to avoid being trapped in local optimum solutions. However, they have some drawbacks, such as being problem-dependent when it comes to parameter tuning and global solution attainment being not guaranteed. Standard benchmark functions (Jamil and Yang Citation2013) are typically being employed to determine the overall efficiency of MOA. These algorithms are tested using at least a subset of these benchmark functions with diverse properties so as to make sure that the tested algorithm can solve certain types of optimization problems efficiently. In the present work, the three (FPA, HS, and WSA) MOA employed to solve CSA problem seem to be very promising and have been proven to have excellent convergence characteristics on different benchmark functions. A brief introduction to each of these three algorithms is given below.
Flower Pollination Algorithm (FPA)
FPA is inspired from the pollination process among flowering plants in which the reproduction between flowers takes place by transfer of pollen from one flower to another (Yang Citation2012). FPA is based on the following four rules (Yang, Karamanoglu, and He Citation2013).
Biotic and cross-pollination can be considered as a process of global pollination, and pollen-carrying pollinators move in a way which obeys Levy flights.
For local pollination, abiotic, and self-pollination are used.
Pollinators such as insects can develop flower constancy, which is equivalent to a reproduction probability that is proportional to the similarity of two flowers involved.
The interaction or switching of local pollination and global pollination can be controlled by a switch probability
∈ [0, 1], with a slight bias toward local pollination.
In the global pollination step, flower pollen gametes are carried by pollinators such as insects, and pollen can travel over a long distance because insects can often fly and move in a much longer range. This can be represented mathematically as
where is the pollen
or solution vector
at iteration
, and
is the current best solution found among all solutions at the current generation/iteration. Here
is a scaling factor to control the step size. In addition, L (λ) is the parameter that corresponds to the strength of the pollination, which essentially is also the step size. Since insects may move over a long distance with various distance steps, Levy flight can be used to mimic this characteristic efficiently. Levy distribution for L > 0 is given by
Here, Γ (λ) is the standard gamma function, and this distribution is valid for large steps s > 0.
Local pollination and flower constancy, can be mathematically represented as
where and
are pollen from different flowers of the same plant species. This essentially mimics the flower constancy in a limited neighborhood. If
and
comes from the same species or selected from the same population, this equivalently becomes a local random walk if
is drawn from a uniform distribution in [0, 1].
Though flower pollination activities (Yang Citation2014) can occur at all scales, both local and global, adjacent flower patches or flowers in the not-so-far-away neighborhood are more likely to be pollinated by local flower pollen than those far away. In order to copycat this, a switch probability is used to switch between common global pollination to intensive local pollination. The pseudocode of FPA can be summarized as
Objective min or max,
Initialize a population of n flowers/pollen gametes with random solutions
Find the best solution in the initial population
Define a switch probability p ∈ [0, 1]
Define a stopping criterion (either a fixed number of generations/iterations or accuracy)
while
for i = 1: n (all n flowers in the population)
if ,
Draw a (d-dimensional) step vector L which obeys a Levy distribution
Global pollination via
else
Draw from a uniform distribution in [0, 1]
Do local pollination via
end if
Evaluate new solutions
If new solutions are better, update them in the population
end for
Find the current best solution
end while
Output the best solution found
Hunting Search (Hus)
This MOA simulates the behavior of animals hunting in a group (lions, wolves, etc.). Group hunters encircle the prey and gradually tighten the ring of siege until they catch the prey. In addition, each member of the group corrects its position based on its own position and the position of other members. If the prey escapes from the ring, hunters reorganize the group to siege the prey again. In HuS algorithm, artificial hunters move toward the leader. The leader is the hunter which has the best position at the current stage (the optimum solution among current solutions at hand). It is assumed that the leader has found the optimum point and other members move toward it. If any of them finds a point better than the current leader, it becomes the leader in the next stage (Oftadeh and Mahjoob Citation2009).
The step by step procedure of the HuS is as follows (Oftadeh, Mahjoob, and Shariatpanahi Citation2010).
Step 1: Initialize the optimization problem and algorithm parameters.
Step 2: Based on the number of hunters in the group, the hunting group matrix is filled with feasible randomly generated solution vectors. The values of the objective function are computed and the leader (the hunter that has the best position in the group) is defined based on the values of objective functions of the hunters.
Step 3: The new hunters’ positions (new solution vectors) are generated by moving toward the leader and is given by
where is a uniform random number which varies between 0 and 1, parameter
is the maximum movement toward the leader, and
is the position value of the leader for the
variable. For each hunter, if the movement toward the leader is successful, the hunter stays in its new position. However, if the movement is not successful (its previous position is better than its new position), it comes back to the previous position.
Step 4: As the search process continues, there is a chance for the hunters to be trapped in a local minimum (or a local maximum once our goal is to find the maximum). If this happens, the hunters must reorganize themselves to get another opportunity to find the optimum point. The leader keeps its position and the other hunters randomly choose their positions in the design space by
where and
are the maximum and minimum possible values of variable
, respectively. EN counts the number of times that the group has been trapped until this step (i.e. number of epochs until this step). As the algorithm goes on, the solution gradually converges to the optimum point. Parameters α and β are positive real values. They determine the global convergence rate of the algorithm. As the algorithm proceeds, the solution gradually converges into the optimum point.
Step 5: Repeat steps 3–4 until the termination criterion is satisfied.
Wolf Search Algorithm (WSA)
WSA is inspired by the hunting behavior of the wolves. It imitates the way wolves search for food and survive by avoiding their enemies.
It is governed by the following three rules (Tang et al. Citation2012)
1. Each wolf has a fixed visual area defined by the radius of the visual range. In
, the coverage area will be a circle by the radius
. Each wolf can only sense companions who appear within its visual circle and the step size by which the wolf moves at a time is usually smaller than its visual distance.
2. The fitness of the objective function represents the quality of the wolf’s current position. The wolf always tries to move to better terrain but rather than choose the best terrain it opts to move to better terrain that already houses a companion. If there is more than one better position occupied by its peers, the wolf will choose the best terrain inhabited by another wolf from the given options. Otherwise, the wolf will continue to move randomly in Brownian motion.
3. At some point, it is possible that the wolf will sense an enemy. The wolf will then escape to a random position far from the threat and beyond its visual range.
Pseudocode of WSA as to how algorithm actually functions is described as below
Objective function
Initialize the population of wolves,
Define and initialize parameters:
radius of the visual range.
step size by which a wolf moves at a time.
velocity factor of wolf.
= a user-defined threshold [0, 1] that determines how frequently an enemy appears
while && stopping criteria not met)
for //for each wolf
Prey_new_food_initiatively ();
Generate_new_location ();
//check whether the next location suggested by the random number generator is new. If not, repeat generating random location.
if
moves toward
//
is a better than
else if
= Prey_new_food_passively ();
end if
Generate_new_location ();
if
//escape to a new position.
end if
end for
end while
For further detailed explanation on WSA readers, refer Fong, Deb, and Yang (Citation2015) and Tang et al. (Citation2012).
Procedure for CSA Problem
Step-by-step procedure for the assignment of cells to switches in an optimum manner using FPA, HuS, and WSA is as follows.
Step 1: Initialize the number of cells, switches, and population size (number of flowers in FPA, number of hunters in HuS, and number of wolves in WSA) in the solution space.
Step 2: Initialize position of cells and switches randomly in the search space and calculate the distance between each cell and switch.
Step 3: For each population member, generate an assigned matrix with cells along column and switches along rows.
Step 4: Obtain a solution matrix from the assigned matrix for each population member satisfying the two constraints as described in Equations (8) and (9).
Step 5: For each population member, calculate the total cost using Equation (7).
Step 6: Find the flower, hunter, and wolf with highest fitness value (He, Chen, and Yao Citation2015) and save its value and assignment.
Step7: Update the solution with minimum cost (highest fitness value) as obtained in step 6 corresponding to the pseudocode of the respective algorithm.
Step 8: Repeat steps 3–7 for the respective algorithm until the stopping criterion is met.
Step 9: Output minimum cost and the corresponding assignment.
Experimental Results
All the experiments were done on Intel (R) Core(TM) 2.50 GHz i5-2520M processor with 4 GB of RAM and 64-bit operating system. The experiments were implemented in MATLAB programming environment. In order to compare the performance of three algorithms (FPA, HuS, and WSA) in solving the CSA problem, the statistical parameters upon which the comparison have been carried out are global best value (GBV), average value (AV), average CPU time , coefficient of variation (CV), and percentage gap (Gap %).
Experiments were conducted with a number of cells varying between 25 and 250 and number of switches varying between 2 and 15.Thus, the search space size was between and
. Three main categories of data (Menon and Gupta Citation2004, Udgata et al. Citation2008) were generated, based on the number of cells in the set. The small category comprised of problems involving 25 cells and 50 cells, the medium category comprised of problems involving 100 cells and 150 cells, and the large category comprised of problems involving 250 cells. In each category, five values 2, 3, 5, 10, and 15 were used for the number of switches. Ten data sets each were generated for small and medium categories, while five data sets were generated for large categories. Thus, an overall 25 test cases were investigated.
Each algorithm was run 100 times using randomly generated population sets for each run. The numerical data obtained for GBV, AV, and CV for each of the algorithm has been recorded in , whereas and Gap (in %) has been enlisted in . In all experiments in this paper, the values of the common control parameters (Karafotias, Hoogendoorn, and Eiben Citation2015) of the mentioned algorithms such as the population size, number of iterations and the maximum objective function evaluation number were chosen to be the same. The population size has been fixed as 25, the number of iterations was kept at 500 and the maximum objective function evaluation number was set to 1,250,000. These common control parameter settings are sufficient to compare the performances of MOA for this data set. The values of algorithmic-specific (Sun, Garibaldi, and Hodgman Citation2012) control parameters of the mentioned algorithms are
Table 1. Comparison of the performances of the FPA, HuS, and WSA for the statistical parameters of GBV, AV, and CV.
Table 2. Comparison of the performances of the FPA, HuS, and WSA for the statistical parameters of average CPU time and gap.
For FPA, have been used.
For HuS, have been used.
For WSA, have been used.
All the three MOA under investigation always found feasible solutions with objective values close to the optimum solution. For all test cases, FPA yielded superior results with respect to attaining the minimum value of cost function (GBV) and in comparison with the other two algorithms. With exceptions, the time needed for solution tended to increase as the number of cells or the number of switches is increased. FPA converged to the optimum solution in the least amount of
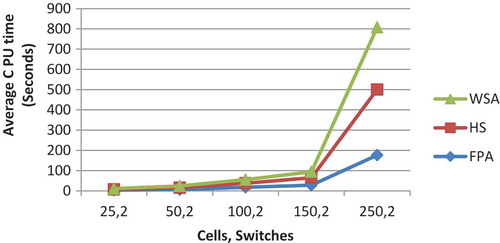
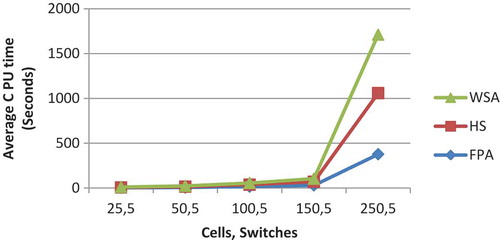
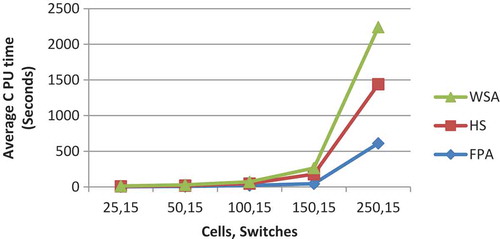
; WSA was intermediate of the other two whereas HuS was the slowest to arrive at the optimum solution. The comparative results of three algorithms while considering the
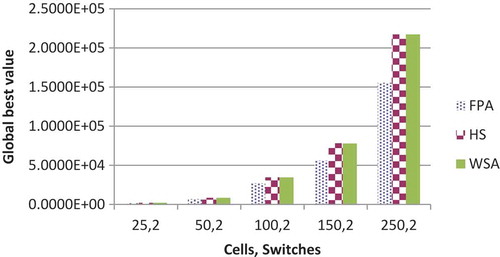
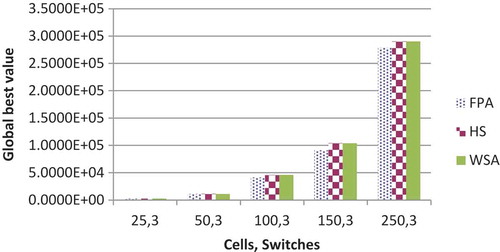
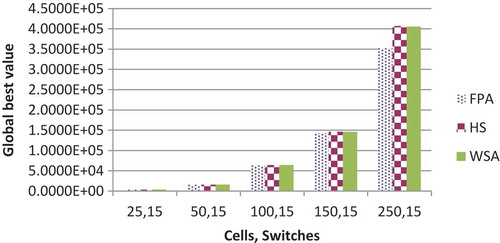
for 2, 5, and 15 switches are shown in respectively. GBV of HuS and WSA are nearly identical whereas FPA gives the superior performance of the three. It increases with the increase in the number of cell or switches with few exceptions. The comparative results of three algorithms with respect to the GBV for 2, 3, and 15 switches are shown in , respectively.
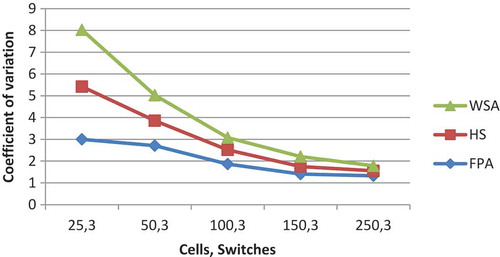
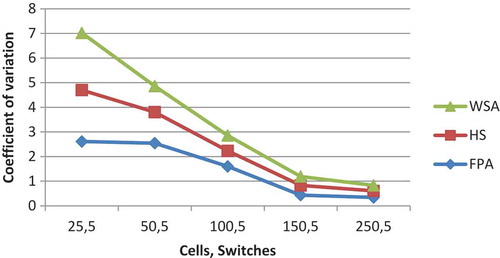
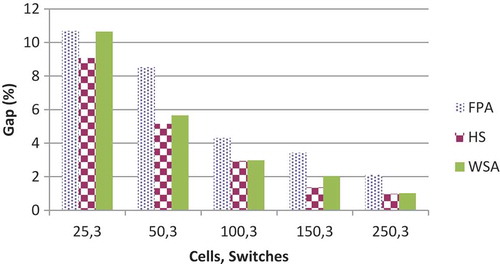
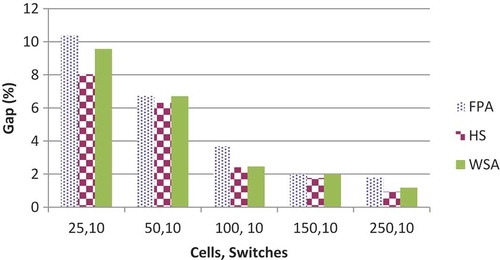
With few exceptions, for all the three algorithms, CV which is calculated as decreases with the increase in the number of cells or switches. It is a measure of spread that describes the amount of variability relative to the AV. Higher the value of CV, the greater is the dispersion in the variable. It has been found that CV is highest for FPA among all the three algorithms, while that of HuS and WSA are comparable and gives slightly better results than FPA. Comparative results of CV for 3 and 5 switches have been shown graphically in and respectively. For FPA, the value of CV varies from a maximum value of 6.5175 to a minimum value of 0.5120.For HuS, this range varies from 2.2335 to 0.1800, while for WSA, it varies from 2.6846 to 0.2413. Gap (%) is defined as the relative difference between the best and the worst solution. The general trend in all the three algorithms is that the gap reduces with the increase in the number of cells or switches with few exceptions. For all the combination of cells and switches, this gap is highest for FPA. The numerical value of the gap for FPA varies from 15.246% to 1.2127%. For HuS, this range is from 9.8039% to 0.8351% and for WSA it lies between 11.652% and 1.2070%. Comparative analysis of Gap for 3 and 10 switches is shown in and respectively.
Conclusions
In this paper, we have addressed one of the critical problems concerning how to assign cells to switches to minimize the total cost comprising of cabling, handoff, and switching costs that are usually considered by the designers of cellular mobile networks. We have investigated MOA approaches incorporating FPA, HuS, and WSA for solving the CSA problem. Experiments were performed in MATLAB programming environment whereby a set of experiments were conducted to evaluate the quality of the solutions with respect to the total minimum cost and another set to evaluate the performance in terms of average CPU time to arrive at the solution. All the three algorithms successfully converged to the optimal solution with a desired assignment in a reasonable time, which was practically not possible by traditional mathematical approach due to the huge size of CSA problem. FPA converged to the optimum solution in minimum time and at least cost and thus was superior to both HuS and WSA for the CSA problem under investigation. Empirical results obtained corroborate the proficiency and the effectiveness of MOA to provide good solutions for large-sized cellular mobile networks.
References
- Bhattacharjee, P., D. Saha, and A. Mukherjee. 1999. Heuristics for assignment of cells to switches in a PCSN: A comparative study. Proceedings of the IEEE international conference on personal wireless communications, 331–34. Jaipur, India.
- Bhattacharjee, P., D. Saha, and A. Mukherjee. 2000. CALB: A new cell to switch assignment algorithm with load balancing in the design of a personal communication services network (PCSN). Proceedings of the IEEE international conference on personal wireless communications, Hyderabad, India, 264–68.
- Blum, C., and A. Roli. 2003. Metaheuristics in combinatorial optimization: Overview and conceptual comparison. Journal of ACM Computing Surveys 35:268–308. doi:10.1145/937503.
- Chawla, M., and M. Duhan. 2014. Applications of recent metaheuristics optimization algorithms in biomedical engineering: A review. International Journal of Biomedical Engineering and Technology 16 (3):268–78. doi:10.1504/IJBET.2014.065807.
- Chawla, M., and M. Duhan. 2015. Bat algorithm: A survey of the state of the art. Applied Artificial Intelligence 29 (6):617–34. doi:10.1080/08839514.2015.1038434.
- Fong, S., S. Deb, and X. S. Yang. 2015. A heuristic optimization method inspired by wolf preying behaviour. Neural Computing and Applications 26:1725–38. doi:10.1007/s00521-015-1836-9.
- He, J., T. Chen, and X. Yao. 2015. On the easiest and hardest fitness functions. IEEE Transactions on Evolutionary Computation 19 (2):295–305. doi:10.1109/TEVC.2014.2318025.
- Jamil, M., and X. S. Yang. 2013. A literature survey of benchmark functions for global optimization problems. International Journal of Mathematical Modelling and Numerical Optimisation 4 (2):150–94. doi:10.1504/IJMMNO.2013.055204.
- Karafotias, G., M. Hoogendoorn, and A. E. Eiben. 2015. Parameter control in evolutionary algorithms: Trends and challenges. IEEE Transactions on Evolutionary Computation 19 (2):167–87. doi:10.1109/TEVC.2014.2308294.
- Mandal, S., D. Saha, and A. Mahanti. 2002. A heuristic search for generalized cellular network planning. Proceedings of the IEEE international conference on personal wireless communications, New Delhi, India, 105–09.
- Menon, S., and R. Gupta. 2004. Assigning cells to switches in cellular networks by incorporating a pricing mechanism into simulated annealing. IEEE Transactions on Systems, Man, and Cybernetics—Part B: Cybernetics 34 (1):558–65. doi:10.1109/TSMCB.2003.817081.
- Merchant, A., and B. Sengupta. 1995. Assignment of cells to switches in PCS networks. IEEE/ACM Transaction on Networking 3 (5):521–26. doi:10.1109/90.469954.
- Oftadeh, R., and M. J. Mahjoob. 2009. A new meta-heuristic optimization algorithm: Hunting search. Proceedings of the fifth IEEE international conference on soft computing, computing with words and perceptions in system analysis, decision and control, Famagusta - North Cyprus, 1–5.
- Oftadeh, R., M. J. Mahjoob, and M. Shariatpanahi. 2010. A novel meta-heuristic optimization algorithm inspired by group hunting of animals: Hunting search. International Journal on Computers and Mathematics with Applications 60:2087–98. doi:10.1016/j.camwa.2010.07.049.
- Pierr, S., and F. Houéto. 2002. Assigning cells to switches in cellular mobile networks using taboo search. IEEE Transactions on Systems, Man and Cybernetics—Part B: Cybernetics 32 (3):351–56. doi:10.1109/TSMCB.2002.999810.
- Quintero, A., and S. Pierre. 2002. A memetic algorithm for assigning cells to switches in cellular mobile networks. IEEE Communications Letters 6 (11):484–86. doi:10.1109/LCOMM.2002.805515.
- Roa, S. S. 2009. Engineering optimization theory and practice. 4th ed. Hoboken, New Jersey: John Wiley & Sons, Inc.
- Saha, D., A. Mukherjee, and P. Bhattacharjee. 2000. A simple heuristic for assignment of cells to switches in a PCS network. Wireless Personal Communications 12:209–24. doi:10.1023/A:1008850615965.
- Shyu, S. J., B. M. T. Lin, and T. S. Hsiao. 2004. An ant algorithm for cell assignment in PCS networks. Proceedings of the IEEE international conference on networking, sensing and control, 1081–86. Taipei, Taiwan.
- Sun, J., J. M. Garibaldi, and C. Hodgman. 2012. Parameter estimation using metaheuristics in systems biology: A comprehensive review. IEEE/ACM Transactions on Computational Biology and Bioinformatics 9 (1):185–202. doi:10.1109/TCBB.2011.63.
- Sutcliffe, A. W. C., and R. S. Neville. 2014. Applying evolutionary computing to complex systems design. IEEE Transactions on Systems, Man and Cybernetics—Part A: Systems and Humans 37 (5):770–79. doi:10.1109/TSMCA.2007.902653.
- Tang, R., S. Fong, X. S. Yang, and S. Deb. 2012. Wolf search algorithm with ephemeral memory. Proceedings of the seventh IEEE international conference on digital information management, Macau, China, 165–72.
- Udgata, S. K., U. Anuradha, G. P. Kumar, and G. K. Udgata. 2008. Assignment of cells to switches in a cellular mobile environment using swarm intelligence. Proceedings of the IEEE international conference on information technology, Bhubaneswar, India, 189–94. doi:10.1097/MPA.0b013e31816459b7.
- Yang, X. S. 2010. Engineering optimization: An introduction with metaheuristic applications. Hoboken, New Jersey: John Wiley and Sons, Inc.
- Yang, X. S. 2012. Flower pollination algorithm for global optimization. Unconventional Computation and Natural Computation 7445:240–49.
- Yang, X. S. 2014. Nature inspired optimization algorithms. London: Elsevier.
- Yang, X. S. 2015. Recent advances in swarm intelligence and evolutionary computation, studies in computational intelligence 585. Switzerland: Springer International Publishing.
- Yang, X. S., M. Karamanoglu, and X. He. 2013. Multiobjective flower algorithm for optimization. international conference on computational science, Procedia Computer Science 18, 861–68. Barcelona, Spain: Elsevier.