?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.Abstract
Since sensor nodes in wireless sensor networks or Internet of things have limited resources, achieving secure data transmissions among nodes is a challenge. Hence, efficient key management schemes with lightweight ciphers are essential. Many asymmetric keys or public key mechanisms have been developed. However, they are unsuitable for secure group communications in wireless sensor networks, because sensor nodes are usually devoid of sufficient memory, CPU and bandwidth to deal with complex operations. In addition, only a few group key agreements are integrated into secure data transmissions. Therefore, a key agreement using the hierarchy-based cluster elliptic curve key agreement named HCECKA is proposed in this study to deal with secure data transmissions in wireless sensor networks. The presented security mechanism relies on elliptic curves instead of logarithmic curves, and utilises a lesser key length to accomplish similar security classification than Diffie-Hellman and Rivest Shamir Adleman cryptosystems. Simultaneously, the proposed scheme provides a rapid, efficient and dynamic group key synchronisation technique in plenty of sensor nodes with no need for reorganising the whole system key if members join or leave wireless sensor networks.
1. Introduction
So far, the key management in Wireless Sensor Networks (WSNs) are an important issue. The wireless communications operate in an open environment (Diffie et al., Citation1976), therefore WSNs are vulnerable (Nicolas & Xin, Citation2007, p. 3). Many related research papers have been presented. The proposals can be sorted out the listed below classifications: (1) pre-distribution mechanism with random keys, (2) single master key, (3) full pairwise key, and (4) group-based key.
The pre-distribution mechanism with random keys is based on the possibility of a common key shared between two sensors (Du et al., Citation2005). Every sensor stores a key ring, which casually selects x keys from the common key pool y. When two sensors have an identical key, then they have a secure path. The bigger key ring size improves the probability of owning identical keys and linkages between two nodes, meanwhile improving the storage space required for every sensor node. However, the key ring size increases vulnerabilities on a communication path existed between uncompromised nodes. Moreover, several nodes possibly own a common key, making them unable to identify which node is connected with.
In the single master key system, each node owns the same master key. During data transmissions, this method adopts the master key to secure the transmitted message between sensor nodes, and is plain to perform with a few memory spaces. However, if an enemy steals anyone’s master key, the whole system discloses the secret.
Every two sensors, the full pairwise key method utilises a distinct pair key between them to secure the delivered message. Therefore, each sensor needs pre-assigning and storing n-1 keys. Thus, every sensor owns n(n-1)/2 keys (Dong & Peng, Citation2003). Namely, every node has to reserve a huge amount of keys for securing data transmissions. Moreover, when increasing or decreasing the amount of sensors, each sensor needs to update pairwise keys (Haowen et al., Citation2003). Even though this mechanism is flexible and secure, a compromised sensor only impacts on the secure connection between other sensors linking with it. Therefore, the unsecure sensor does not influence the secure connection between uncompromised sensors. However, the heavy memory and storage overload render it inappropriate for a WSN on a wide scale. Additionally, the node addition and deletion complicates the system re-keying.
The mechanism of the group-based key management allocates sensors into separate groups. Every sensor has the same intra-group key for securing transmissions with its nearby nodes (Donggang et al., Citation2005; Zhou et al., Citation2005). The method of the group-based key management exceeds other methods regarding scalability, efficiency and storage overhead. Recently, several ID-based or certificateless authenticated group key agreements for dynamic groups are proposed. They investigate how to manage the intra-group key. However, the research results indicate that a dynamic topology is a complex issue to implement the intra-group key (Lin et al., Citation2016).
As we know, the mentioned methods concentrate on key managements in WSNs, and are short of the mechanism of secure data transmission, which should be combined with key management protocols. This study presents a HCECKA mechanism to perform quick and effective key synchronisation for hierarchy-based WSNs, in spite of nodes dynamically taking part in or leaving from WSNs. Additionally, to improve the WSNs security, this study integrates the proposed key agreement with transferring data. In other words, we would like to offer an elliptic curve key agreement based on hierarchy with several secure data transfer modes for WSNs.
The remaining sections of this document are structured as follows. Section 2 presents the key agreement of Elliptic Curve Diffie-Hellman (ECDH) and compares Rivest Shamir Adleman (RSA) with elliptic curve cryptography under similar security levels. In Section 3, this study details the proposed HCECKA protocols and operational procedures of HCECKA. Section 4 discusses the multiple modes of secure data transfer of HCECKA. Section 5 includes computing evaluations and depicts the security analyses. Afterwards, in Section 6, we discuss the state of this study, describe future avenues of research, and conclude this study.
2. ECDH, the key agreement of elliptic curve Diffie-Hellman
In general, the asymmetric key system is more secure than a symmetric key system. Therefore, Public Key Infrastructure (PKI) provides higher security level functions, but PKI consumes lots of computing resources. However, WSNs have insufficient computing resources. Thus, sensors could not properly execute security operations very well through the above methods. So far, many studies intended to enhance security for sensor nodes through ECDH security mechanisms. Nicolas et al. (2007) designed and implemented Elliptic Curve Cryptography (ECC) on a hardware architecture. Piotr et al. (Citation2008) surveyed the limit value of ECC, and confirmed that implementation of the public key cryptography on WSNs was achievable. An et al. (2008) developed an executable software and a function library for ECC.
Elliptic Curve Diffie-Hellman (ECDH) is a native of the renowned Diffie-Hellman (DH). The main difference is that ECDH employs the elliptic curve cryptography to create a common secret key known as a session key, which is responsible for secure transmitted data in open environments between two parties. Subsequently, they adopt the session key to cipher or decipher succeeding transmissions through a symmetric key mechanism. However, ECDH uses only 160-bit keys to achieve the same level of security as the DH secret sharing system. But, the raw DH agreement reaches an appropriate security level at least needing a 1024-bit key length, and hence consumes more memory capabilities and computing resources to execute exponential operations. Regrettably, sensors only have limited resources and a few computing power to deal with extra overheads. This study compares the key length of ECC with RSA under the same security levels. Table indicates that the ECC has a key size of less than 160 bits to reach secure levels, which is equivalent to 1024 bits RSA. Besides, in ECC operations, there are only use addition and multiplication and thus can reduce the operational complexity and increase the operational performance. On the contrary, RSA, DH and DSA all need exponential operations. That is why ECC outperforms RSA, DH and DSA algorithms. This study adopts ECC as the cryptosystem is certainly workable for WSNs without sufficient computing sources. Consequently, ECDH is well adequate for WSNs.
Table 1. Under the same security level, different needed length (bits) of key on ECC and RSA.
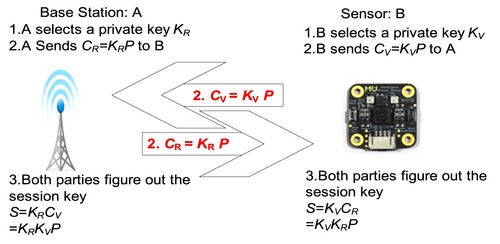
Figure represents the sensor A which wishes to connect with the sensor B using a session key within ECDH. Initially, the well-known parameters must first be set, including an elliptic curve y2 = x3+ax + b, coefficients a and b, and a generator P with prime and base point in Diffie-Hellman. Moreover, each node owns a proper key pair to perform elliptic curve cryptography, comprising a randomly selected integer as ECC private key K and a well-known C (where C = KP) as the public key. Then the sensor A’s key pair represents (KR, CR), and the sensor B’s key pair represents (KV, CV). Every node has each other’s public key. Subsequently, the node A figures out CR = KRP, and the node B figures out CV=KVP. Then the node A delivers CR to the node B, and the node B delivers CV to the node A. After receiving, each node computes the common session key S = KRCV = KRKVP = KVKRP = KVCR. This agreement is secure since two nodes disclose nothing besides public keys, and there is no one who knows the other’s private key unless the Discrete Logarithm Problem (An & Peng, Citation2008) of Diffie-Hellman can be worked out. Additionally, we assume that there is a secure CA (Certification Authority) server on this system. CA is a trusted digital signature server, and provides both nodes with a digital signature to sign the sent message before transmitting them. Therefore, both nodes ensure each other’s identity, and prevent attacking from malicious nodes (Zhongyuan et al., Citation2014).
3. The proposed key agreement using the hierarchy-based cluster elliptic curve, HCECKA
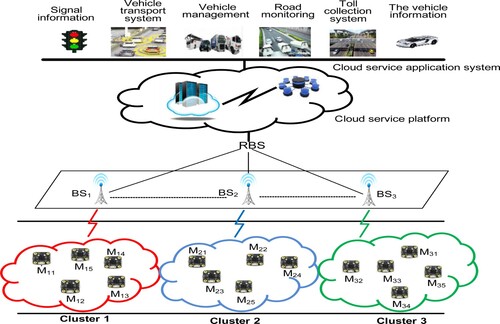
This section presents our proposed key agreement using a hierarchy-based cluster elliptic curve. Considering numerous sensor nodes, clustering forms a resilient and scalable architecture in which the entire WSNs are separated into many clusters with gateway sensors managing inter-cluster communications. The proposed hierarchy-based cluster key agreement (HCECKA) is inspired by cluster architecture.
We assume that HCECKA splits the whole sensor network into several groups named clusters through an appropriate cluster algorithm. Besides, each cluster has a cluster head named base station, and the whole network only has a root base station with sufficient computing power, huge memory and constant power. Generally, the base station and root base station comprise a powerful computer and differ from sensor nodes, and they never collapse. For simplicity, this study assumes that the base stations and the root base station provide constant power and are secure. At the same time, the base stations are elected and deployed before arranging the sensor nodes according to secure operations. Simultaneously, the base stations can straightly reach to each sensor node of the intra-cluster, and periodically broadcasts a hello message that includes the cluster identity and the member information to each node of the intra-cluster for determining other node geographic coordinates.
The proposed above architecture quickly synchronises the inner cluster key of plenty of members, intelligently executes key exchange among cluster heads, and ensures secure data transmissions. Our proposed hierarchy-based cluster infrastructure consists of three entities and is scalable for group key managements as below.
Member node (Mxi): a regular sensor node i acquires authentication from a base station (BSx), and joins the cluster x and protects data transmissions using the obtained descendent cluster key. RBS denotes the controller of the entire system cluster key and is also known as the root base station, and BS is responsible for the controller of the descendent cluster key. Prior to whole sensor nodes being arranged, this study deployed RBS and BS in advance. The detailed HCECKA hierarchical model is illustrated in Figure .
Base station (BS): it is responsible for the controller of the descendent cluster key in a cluster, managing the descendent cluster operation for a cluster. When a cluster achieves the key synchronisation. In this cluster, every node obtains the same descendent cluster key for future secure data transmissions.
Root base station (RBS): RBS is in charge of controlling the system cluster key, managing operations for the whole WSNs. When the entire system achieves the key synchronisation, every node obtains the same system cluster key for future security communications. RBS is the ancestor of base stations, figures out the system cluster key of the whole system, also assigns a descendent cluster key to every base station.
Necessary settings reduce the quantity of key agreement operations executed in every cluster. Especially, in a quite huge cluster, the computing overload increases if members of a cluster grow. Our proposed mechanism comprises the following stages. Figure depicts the detailed operations in each stage.
Stage 1. The controller of a descendent cluster key is the base station BSx, which is deployed for the members Mxi in the cluster, where i represents the quantity of sensors in this cluster, i and n ∈integer, and x represents the identity of the cluster, 1 ≦ x ≦ n.
Stage 2. In this system, the most secure and powerful base station is selected as RBS, responsible for key control for the whole network. The other base stations BSx, 1≦x≦n, work with RBS to figure out the system cluster key for WSNs.
Stage 3. Every BSx (BS1, BS2, BS3, … , BSn-1) executes the agreement of the descendent cluster key as depicted in Figure (such as BS1) and determines a descendent cluster key KCxP, where x ∈ [1, n-1] through the ECDH agreement. This study presents the specific descendent cluster key agreement as the following steps.
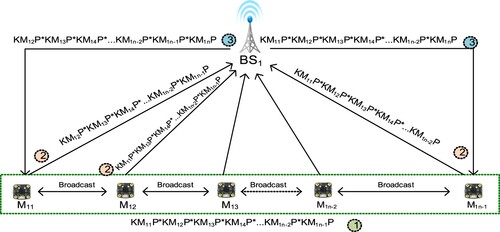
Step 1. Initially, every node M1i in the BS1 cluster creates a private key KM1i and figures out the public key KM1iP, where P is a generator in ECDH. M1i subsequently broadcasts KM1iP to the rest of member nodes in cluster 1. After receiving KM1iP, M1x (x≠i) calculates KM1xP and multiplies KM1xP with KM1iP. Finally, every node obtains the common result KM11P*KM12P*K … M1n-1P, as shown in Figure .
Step 2. After receiving KM11P*KM12P* … *KM1n-1P, M11 takes out its own factor KM11P, and then unicasts KM12P*KM13P* … *KM1n-1P to BS1. Meanwhile, the reset of node M1i, i ∈ [2, n-1] executes the same processes. Under a secure channel, the M1i securely unicasts (Janies et al., Citation2007) the taken out result to BS1. Figure depicts the processes.
Step 3. After receiving KM12P*KM13P* … *KM1n-1P from M11, BS1 computes its own key KM1nP. Then BS1 figures out KM12P*KM13P* … *KM1n-1P*KM1nP, and enciphers the message to securely unicast it back to M11, as shown in Figure . Simultaneously, BS1 executes the same processes to figure out the keys for M1i, where i ∈ [2, n-1]. Then, BS1 transmits the outcome to M1i. After receiving, M11 multiplies the transmitted key with its own KM11P. Subsequently, M11 acquires the descendent cluster key KM11P*KM12P* … *KM1n-1P*KM1nP. Likewise, every node finally obtains the same descendent cluster key KM11P*KM12P* … *KM1n-1P*KM1nP, and then we can simplify to represent the above descendent cluster key as the mathematical representation, where (i = 1 to n), and the symbol
denotes a multiplication of multiple elements, such as KM11P multiplies KM12P multiplies KM13P, which can be represented as
1iP. Briefly, in BS1, the descendent cluster key
is defined as KC1P. Finally, every BSx executes the similar process and obtains a descendent cluster key KCxP, where x ∈ [1, n-1].
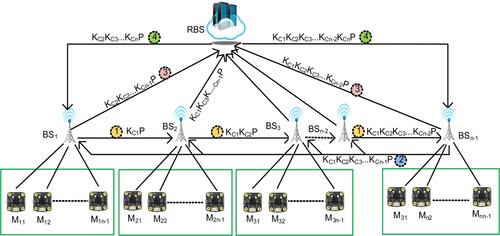
Stage 4. Meanwhile, this entire network gathers every cluster head BSx’s descendent cluster keys. Subsequently, each BSx figures out KC1PKC2P … KCxP by multiplying its own KCxP with the received KC1PKC2P … KCx-1P, and forwards its own descendent cluster key to the next BSx+1, as shown in Figure . For instance, BS4 receives the forwarding descendent key KC1PKC2PKC3P from BS3, then multiplies KC1PKC2PKC3P with its descendent key KC4P, and then delivers KC1PKC2PKC3PKC4P to the next BS5. Consequently, the forwarding key from BSn-2 is obtained, and BSn-1 then can derive KC1PKC2PKC3P … KCn-2PKCn-1P=, where (i=1 to n-1), and the symbol
denotes a multiplication of multiple elements.
Stage 5. Subsequently, as shown in Figure , BSn-1 declare KC1PKC2PKC3P … KCn-1PKCn-1P to all other cluster heads (BS1, BS2, BS3, … , BSn-2).
Stage 6. Every BSi (i ∈ [1, n-1]) obtains the declared key , then takes out its own factor KCiP, and sends the outcome to RBS. Figure depicts the detailed process.
Stage 7. At the last stage, after receiving all descendent cluster keys from every BSx, RBS subsequently multiplies its own KCnP with every descendent cluster key, and enciphers the message to securely unicast back to BSx. Figure depicts the detailed process. After receiving the unicasted key, BSx multiplies the received key with its own descendent key KCxP. Consequently, every cluster head obtains the same KP =
as the system cluster key for the entire network.
The above-mentioned stages introduce the complete synchronisation process to construct the system cluster key for the whole system. In a practical environment, the root cluster head could be replaced or may collapse down, also ordinary sensors or cluster heads may join or leave the network. This study only explores multiplication and addition operations, and thus the proposed scheme can rapidly achieve synchronisation of the system key.
3.1. The system cluster key synchronisation for clusters participating in or departing from networks
3.1.1. Mobile nodes participate in or leave a cluster
When a node M1i participates in (or leaves) cluster 1, M1i only needs to broadcast its public key KM1iP to each node in the cluster once. Other nodes multiply (or remove) the received key with their own key KM1xP (x≠i). Subsequently, each node repeats steps 2 and 3 in stage 3, and then the cluster obtains the new descendent cluster key KC1P. Eventually, the system performs the stages 4–7, and obtains the system cluster key.
3.1.2. Cluster participation
A system must reconstruct the system cluster key for the entire network when a new cluster head BS (nominated during system deployment) joins a WSN. The key exchange processes are categorised into three cases as presented in detail below.
(1) In the general case
The joining cluster head BSx is between BS1 and BSn. Then the BSx-1 system forwards KC1PKC2PKC3P … KCx-1P to BSx, and BSx generates a private key KCx using ECC. Subsequently, BSx multiplies KCxP with KC1PKC2PKC3P … KCx-1P to obtain KC1PKC2PKC3P … KCx-1PKCxP, and forwards the result to BSx+1. Eventually, the system performs the stages 5–7 in section 3. The performance of recalculating the system cluster key depends on the joining position of a new cluster head.
(2) In the worst case
The joining cluster head is BS0 allocated at the leftmost position, the system has to completely perform the stages 4–7 in section 3.
(3) In the best case
The joining cluster head is BSn allocated at the rightmost position. Achieving the system cluster key for the whole network, this system only performs several computations. The detailed procedures are as follows.
Phase 1
The last cluster head BSn-1 forwards KC1PKC2PKC3P … KCn-1P to BSn, and then BSn generates a private key KCn using ECC. Subsequently, BSn multiplies KCnP with KC1PKC2PKC3P … KCn-1P to obtain KC1PKC2PKC3P … KCn-1PKCnP, and then unicasts the result to RBS.
Phase 2
Upon receiving KC1PKC2PKC3P … KCn-1PKCnP, RBS generates a new ECC private key KCn+1, and replaces its own old public key KCnP with KCn+1P. Subsequently, RBS calculates a new system cluster key value as below.
KC1PKC2PKC3P … KCn-1PKCnPKCn+1P=, and the symbol
denotes a multiplication of multiple elements, such as KC1P multiplies KC2P multiplies KC2P.
Phase 3
RBS extracts the key KCxP of the target base station BSx, and calculates the n descendent cluster keys for the other clusters as below, and securely unicasts it to BSx.
Phase 4
Each base station BSx receives the descendent cluster key from RBS, and multiplies the received key by its own key KCxP. Thus, each BSx can derive the new system cluster key K n+1P.
The HCECKA rapidly and efficiently calculates the new system cluster key Kn+1P, and requires only a few operations to calculate n descendent cluster keys if a new cluster is added. Additionally, all former clusters recalculate the new system cluster key by Kn+1P with a single multiplication. Only an RBS needs to generate a new private key and perform n multiplications for n descendent cluster keys. RBS inevitably requires additional operational loads.
3.1.3. Cluster departure
The procedure in HCECKA for a cluster head departing from a network is similar to a cluster head joining a network. Let BSx denote a cluster removed from the network. In the general case, assume that x ∈ [1, n-1] and x ≠ n. Thus, BSx-1 forwards KC1PKC2PKC3P … KCx-1P to BSx+1, and the subsequent key generation procedure is performed with BSx+1 replacing BSx. Subsequently, the system performs stages 4–7 in section 3, and obtains the system cluster key.
In the worst case, if the leftmost node BS1 leaves the network, the system has to completely perform the stages 4–7 in section 3. However, each BSx (x≠1) only needs to extract KC1P from its previous KC1PKC2PKC3P … KCx-1PKCxP, and thus can reduce operational time in stage 4.
In the best case, the leaving cluster head is BSn-1 allocated at the rightmost position. RBS generates a new private key KC* replacing KCn, and calculates a new system cluster key KP = KC1PKC2P … .KCn-2PKC*P for the entire network. RBS then securely unicasts a new set of n-2 partial system cluster keys to the base station BSx. Additionally, if RBS leaves the system, then BSn-1 substitutes the role of RBS, and performs the system cluster key procedures. Consequently, the system generally regains the system cluster key in a few operations.
From the above presentation, we propose an elliptic curve key agreement based on a hierarchy cluster infrastructure to improve the efficiency of a group key synchronisation when nodes or clusters dynamically join or leave. Besides, we integrate the proposed key agreement into communications and then secure the data transmission. The detailed description is as follows.
4. The mechanism of secure data transmissions
This section introduces how to deal with secure data transmissions for inter-cluster and intra-cluster, and applies the descendent cluster key, system cluster key and ECDH session key on various scenarios to enhance secure data transmission efficiency.
This study adopts the descendent cluster key to protect and confirm the data security of intra-cluster, exploits the system cluster key performing security operations of inter-cluster, and utilises the ECDH session key to provide flexible modes of secure data transmissions for intra-cluster, inter-cluster and gateway. The detailed description is as follows.
4.1. Transmission mode of data security using the descendent or system cluster key
Considering the key synchronisation of the descendent cluster key or the system cluster key in WSNs, this proposed mode gives the best efficient secure data transmissions. Since, the whole network utilises the same key to secure data transmissions. This operational process is just like a single master key mechanism. We present the transmission mode of data security using the descendent or system cluster key for inter-cluster and intra-cluster as below.
4.1.1. Transmission mode of data security for intra-cluster
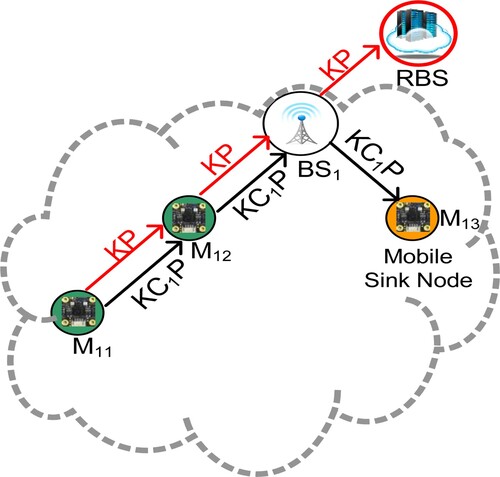
As shown in Figure , when a sink node (a data collector) named M13 dynamically enters the cluster to collect information, the cluster head BS1 first performs the descendent key operations to calculate the descendent key. Subsequently, in the same cluster, M11, M12 and BS1 deliver their collected data to M13. This operational mode utilises the same descendent cluster key to encipher and decipher the transmitted data, and performs operational processes of data security from M11 sending data to M13 as below.
Sensor node M11 exploits the descendent cluster key KC1P to encipher the path of routing nodes, the sensed message DM11 of node M11 and HMAC (DM11). Then, this study inputs the sensed message DM11 and the KC1P descendent cluster key, and figures out the Hash Message Authenticated Code HMAC (DM11). After that, M11 puts the above data into the relevant fields, and subsequently sends the encoded message to the following M12.
When the transmitted message is received, M12 enciphers them utilising the descendent cluster key KC1P. After that, M12 inspects the integrity of HMAC (DM11) by KC1P, accumulates sensed data DM12 with DM11, appends self M12 identity into the route, generates HMAC (DM12||DM11), and enciphers them using KC1P. Subsequently, M12 sends the enciphered result to the next BS1.
When BS1 accepts the enciphered message, and then deciphers the received message utilising KC1P. Subsequently, BS1 executes the similar processes as the above procedures. Eventually, BS1 delivers the enciphered result to the end sensor M13.
As M13 receives the enciphered message, M13 deciphers the received message and inspects the HMAC (DBS1||DM12||DM11) integrity by KC1P to identify if these original messages have been modified.
The proposed scheme for secure data transmissions of intra-cluster is straightforward and clear. The early single master key mechanism is a particular instance in our proposed cluster architecture.
4.1.2. Transmission mode of data security for inter-cluster
When two nodes in different clusters would like to communicate with each other, this study secures the data transmissions utilising the system cluster key. During transmission, nodes employ the system cluster key KP to encipher and decipher messages, exploit KP to generate the HMAC code through hash functions, and inspect the transmitted message integrity by KP. The whole processes are similar to the transmission mode of data security for intra-cluster.
4.1.3. Urgent transmission mode of data security
If sensor nodes are deployed in critical environments for detecting urgent accidents, this mode provides a rapid and secure data transmission method. Figure depicts that M11 detects an urgent message and needs to notify RBS immediately. Since RBS serves as the urgent operation centre, in this mode, M11 adopts the system cluster key KP to encipher the urgent message, and then dispatches the enciphered result to the next sensor along the routing path toward RBS. Consequently, RBS obtains the enciphered message and deciphers them utilising KP to enhance the efficiency of data transmissions. The detailed transmission procedure from M11 to RBS is as follows.
First, M11 exploits the system key KP to encipher its identity and an urgent message EM11 sensed from M11, and then attaches the routing path and HMAC on the tail of the enciphered message. Subsequently, M11 sends the enciphered message to the following M12.
As M12 receives the transmitted data, M12 only needs to inspect the integrity of the attached HMAC by KP instead of deciphering the message. Subsequently, M12 appends its own ID into the route, meanwhile and calculates a new HMAC code containing the enciphered urgent data and the updated routing path. Then, M12 delivers the new enciphered message to its cluster head BS1.
After receiving the transmitted message, BS1 executes the similar processes as the above procedures, and transmits the enciphered message to its cluster head RBS.
After receiving the message, RBS calculates HMAC for (EKKP[M11|EM11],BS1M12M11), and compares the result with the received HMACKP(EKKP[M11|EM11], BS1M12M11). If both HMACs are equal, RBS adopts the system cluster key KP to decipher the enciphered message, and obtains the emergency message EM11.
4.2. Transmission mode of data security using the ECDH session key
As known to all, ECDH stems from the key agreement protocol of Diffie-Hellman. The variation is that ECDH utilises elliptic curve cryptography to create a session key for securing the communication between two parties over unshielded channels. Here, for simplicity, we assume that a secure and trusted server named CA takes charge of certificate authority in this system. The CA server issues digital certificates for both parties to ensure the identity of each other for communications. As a result, this system prevents identity theft and the attack of the man-in-the-middle. Subsequently, we perform secure data transmissions between two nodes directly connected utilising the session key from ECDH.
4.2.1. Transmission mode of data security for intra-cluster
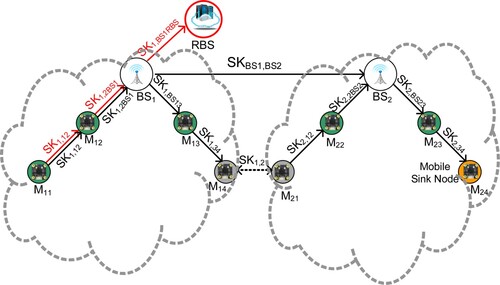
Within an intra-cluster, sensor nodes employ the common ECDH session key to protect and securely transmit data. Our designed scheme is both straightforward and efficient, and offers secure data transmissions of peer-to-peer. Figure indicates that M11 is located in the left cluster and would like to forward the sensed data to M14. The following is the procedure of secure data transmissions.
Initially, the sensor node M11 adds its sensed message DM11 and its own ID to the routing path. Subsequently, we use the descendent cluster key KC1P (not session key SK1,12 of two nodes, where 1 denotes the cluster ID and 12 denotes node 1 and node 2) for later secure verification of inter-cluster. Then, M11 takes DM11 as an input and executes a hash function to generate HMAC (DM11). Eventually, M11 puts the above data into the relevant fields, uses session key SK1,12 to encipher them, and then forwards the enciphered result to the next M12.
Upon receipt of the transmitted data, M12 utilises the SK1,12 session key to decipher it and inspects the HMAC(DM11) integrity through the descendent cluster key KC1P. After that, M12 aggregates sensed data DM12 with DM11 as (DM12||DM11), calculates HMAC (DM12||DM11) using KC1P, and puts its own ID in the routing path. Finally, M12 uses the SK1,2BS1 session key to encipher the above fields, thereafter and sends the enciphered result to the subsequent BS1 base station.
Upon receipt of the transmitted data, BS1 utilises the SK1,2BS1 session key to decipher it. Then, BS1 checks the integrity of HMAC, combines sensed data DBS1 with DM12||DM11, generates HMAC(DBS1||DM12||DM11), and puts its own ID into the routing path. Eventually, BS1 enciphers these fields using session key SK1,BS13, thereafter and sends the enciphered result to the subsequent M13. This system duplicates the above procedures until the transmitted data arrives at the target M14.
Upon receipt of the transmitted data, M14 utilises the SK1,34 session key to decipher the incoming data, employs descendent cluster key KC1P to examine the integrity of the aggregated data HMAC (DM13||BS1||DM12||DM11), and then identifies if the original data were modified during communication. As such, this system can accomplish secure data transmissions for Intra-cluster.
4.2.2. Transmission mode of data security for inter-cluster
Figure depicts when M11 would like to send a message to M24. Because two nodes are situated in separate clusters, the procedures for securely transmitting data are similar to those described above steps in session 4.2 (1) (a)-(b) until the delivered message reaches BS1. Subsequently, BS1 executes a hash function for the accumulated message DBS1||DM12||DM11, and utilises the system cluster key KP to product HMAC (DBS1||DM12||DM11) for the later inspecting the HMAC integrity. Finally, BS1 utilises the session key SKBS1,BS2 to decipher the received message, and performs the following steps (c)-(e) to secure data transmission until the transmitted message arrives in BS2, which is located in a different cluster.
After receiving the enciphered messages, BS2 utilises the SKBS1,BS2 session key to decipher them, and inspects the HMAC integrity through the system cluster key KP. After that, BS2 accumulates the sensed message DBS2 with DBS1||DM12||DM11, utilises the descendent cluster key KC2P to compute HMAC (DBS2||DBS1||DM12||DM11) for the internal cluster security, appends self-identification to the routing path, puts them into the relevant fields, and enciphers all fields using the session key SK2,BS23. Eventually, BS2 sends the enciphered result to the next M23.
After receiving the enciphered messages, M23 utilises the SK2,BS23 session key to decipher them, and adopts KC2P to inspect the HMAC(DBS2||DBS1||DM12||DM11) integrity. Subsequently, M23 accumulates the sensed message DM23 with DBS2||DBS1||DM12||DM11, uses the descendent cluster key KC2P to generate HMAC (DM23||DBS2||DBS1||DM12||DM11), puts its own ID M23 into the routing path, enciphers all fields using the session key SK2,34, and subsequently forwards the enciphered result to the following M24.
After receiving the enciphered messages, the target node M24 utilises the SK2,34 session key for deciphering the enciphered message and inspecting the HMAC (DM23||DBS2||DBS1||DM12||DM11) integrity by the descendent cluster key KC2P to verify if the data has been modified during data transmissions.
In this secure inter-cluster data transmission, the transmitted message goes through various clusters, and therefore BS1 and BS2 take charge of the secure data transmission for inter-cluster, and inspect the integrity of the HMAC during the passage of the various clusters. Thus, BS1 and BS2 can utilise the system cluster key KP to compute HMAC and inspect the received HMAC integrity.
4.2.3. Transmission mode of data security via gateway nodes
In this mode, Figure depicts if two different clusters have common gateway nodes, the source node can pass through gateway nodes to reach the target node. Under this situation, the secure transmission procedure is similar to the secure data transmission mode of inter-cluster. When the transmitted message passes through the gateway (M14→M21), this mode utilises the system cluster key KP to generate and inspect HMAC, and employs the session key SK1,2 of gateway nodes to en/deciphered the transmitted messages. Since the other nodes do not have the session key SK1,2 of gateway nodes, then cannot decipher the enciphered message. Eventually, the target node receives the transmitted message and inspects the HMAC integrity by the system cluster key KP, and identifies if the original data has been modified during transmissions.
4.2.4. Urgent transmission mode of data security
Between clusters, delivering urgent data enciphered by the system key is efficient, but probably not secure, since each member equipped with the system key can reveal the urgent data. Therefore, this study exploits session keys to achieve advanced protection. Suppose that M11 delivers urgent data to RBS using session keys belonging to participants in the routing path. The following is the detailed procedure.
Sensor node M11 adds emergency message EM11, adopts the system cluster key KP for later confirmation and EM11 as inputs to execute hash functions and generates HMACKP (EM11), and then places its own ID to the routing path. After that, M11 puts those data into the relevant fields, subsequently utilises the session key SK1,12 to encipher all fields, and then transmits the enciphered result to the next M12.
Once M12 obtains the transmitted message, it utilises the SK1,12 session key to decipher the received message, and then adopts the system cluster key KP to inspect the integrity of the received HMAC. After that, M12 calculates HMACKP (EM11) and appends its own ID to the router. Eventually, M12 employs SK1,2BS1 for encryption of the whole message, subsequently and forwards the enciphered result to BS1.
When BS1 receives the transmitted message, BS1 utilises the session key SK1,2BS1 to decipher them, and verifies the HMAC integrity. Subsequently, BS1 puts its own ID to the routing path, and generates HMAC of the emergency message. Eventually, BS1 enciphers all fields using the session key SKSK1,BS1RBS, and then forwards the result to RBS. When RBS receives the enciphered message, subsequently deciphers them and inspects the integrity of the transmitted emergency message EM11 sent from M11.
5. Secure data transmission analyses and computing evaluations
This research investigates the effectiveness evaluation of the above models of secure data transmissions, and performs several security analyses. Additionally, we also demonstrate that the proposed methods indeed decrease key resynchronisation time when nodes are leaving or joining, enhance the performance of secure data transmissions, and decrease key resynchronisation time when nodes are leaving or joining. Additionally, we also provides the decentralised key management with a scalable and flexible infrastructure. The detailed security analysis is as below.
(1) Authentication and confidentiality
During the transmission, this study secures transmitted messages using a session key. Upon receipt of the enciphered message, it can only be deciphered by the owner of the same session key. However, since the other nodes have different session keys, they cannot decipher the enciphered message.
(2) Failure tolerance of the transmission path
In the proposed mechanism, there are multiple routing paths that exist among sensors. If the original selected path is interrupted, the gateway mode will be the alternative route to execute information security transmissions, and therefore the entire system reverts to regularity. In addition, when transmitting data securely between peers, this mechanism makes it possible to carry out fast and efficient fault-tolerant routing protocols without a single point of failure.
(3) Correctness and integrity of data transmitted
While transmitting, the present study examines the correctness and integrity of the transmission of the message by HMAC. Where two nodes are situated in separate clusters, the sender utilises the descendent or system cluster key to generate HMAC for later verification. As a result, the system prevents malware nodes from utilising the session keys to pass HMAC inspection. After reception of the enciphered message, the recipient deciphers the enciphered message, subsequently adopts the related cluster key and plain messages as inputs to compute and inspects the HMAC integrity. As we know, the hash function H is a non-reversible operation to generate HMAC. Where i ≠ j is H(i) ≠ H(j). A random number i and j cannot be taken into consideration in such a way that H(i) = H(j). Consequently, while transmitting, there is a sensor node which changes the delivered message, and the recipient immediately inspects the unequal HMAC and determines the altered data.
(4) Operations of data encryption and decryption
As we know, PKI and asymmetric key schemes need lots of computing power. However, sensor nodes have no sufficient computing resources, and thus asymmetric key infrastructures are unsuitable for WSNs. In the proposed design, every sensor retains only one system group key, one descending group key and one session key for securing the delivered message, subsequently and adopts like MD5, SHA-3 or RIPEMD-160 hash functions to inspect the delivered message correctness and integrity. Additionally, session key operations and hash functions only consume few resources. As a result, the proposed schemes are plain, straightforward and quite appropriate for WSNs.
Moreover, this study simulates performance evaluation and analyses of various public key cryptosystems, and compares key operating costs and key communication costs. Here we assume that RBS and BS are absolutely secure and have constant power. The study performs a few ECDH processes on the sensor node, which utilises the prime field to establish an ECDH session key, subsequently and figures out a point multiplication on a SECP-160 curve.
Regarding the simulation scenarios of intra-cluster and inter-cluster infrastructures, this study evaluates the data transmission time and the key synchronisation time, and adopts the descendent cluster key and the system cluster key to achieve secure data transmissions of intra-cluster and inter-cluster. Moreover, we employ an ECDH session key for securely transmitting messages, which is similar to estimate the efficiency of gateway, inter-clusters and intra-clusters modes. For simplicity, this study utilises <x, y> pair to denote the length of the key of a security level, where x corresponds to the length of one HCECKA private key, and y corresponds to the length of one Diffie-Hellman (DH) private key. The mechanism of the DH key agreement is for both parties to find a shared private key to securely exchange and transmit the message in non-secure connections. Additionally, both the receiver and the sender own key pairs in the DH key protocol. Two parties combine one's private key with the other's public key to identify the shared common session key (Zhong et al., Citation2014). GDH extends the renowned two-party DH key protocol to n parties. The several versions of GDH, including GDH.2 and GDH.3, are considered to be particular group protocols. GDH places all members of a group into a binary tree or a logic ring. When increasing the quantity of group members, the quantity of communication rounds and the computing cost seriously influence the efficiency of the GDH key agreement.
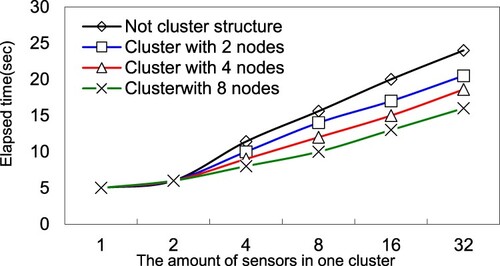
To evaluate the efficiency and scalability of our proposed schemes in WSNs, this scenario adopts different cluster member nodes (1, 2, 4, and 8) to simulate various numbers of sensor nodes in WSNs (1, 4, 8, 16, 32, and 64), and compares various scenarios of the system cluster key convergence time for 1–64 members in WSNs. When the number of a cluster member node is 1, which means that each node is similar to a cluster head (BS); this is a special case. Simulation results in Figure indicate that when member nodes of a cluster increase, the system cluster key synchronisation time for the cluster scheme outperforms that of the non-cluster schemes. The non-cluster scheme performs more operations in stages 1–7 to achieve key synchronisation.
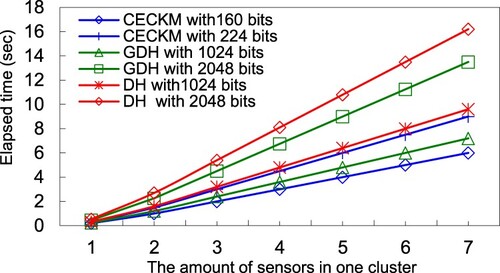
Figure 8. A cluster with different members, the convergence time for computing the descendent cluster key.
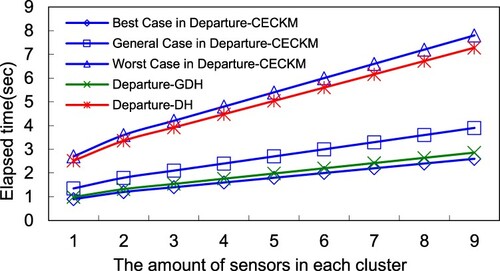
In the same cluster, the simulated network of nodes (5, 10, 15, 20, 25, and 30) is used to build the descendent cluster key, and determines the synchronisation time. This study compares our proposed HCECKA with DH and GDH schemes on different key lengths. Simulation results indicate that GDH and DH must execute exponent operations. However, HCECKA needs only multiplication operations. Consequently, GDH requires significantly more computing time than HCECKA. Figure illustrates the results of the simulation and shows the synchronisation time for constructing the descendant cluster key on HCECKA is less than GDH for <224, 2048 bits> and <160, 1024 bits>. Therefore, HCECKA exceeds DH in computing the descendent key on the synchronisation time.
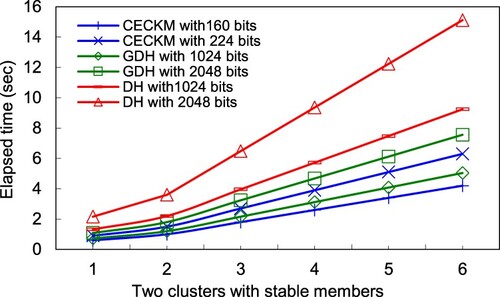
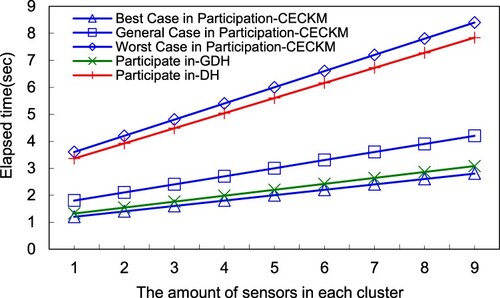
In Figure , this study evaluates the time to synchronise the system cluster key construction for HCECKA and GDH. Initially, this study divides a network into two clusters containing member nodes (1, 2, 3, 4, 5, and 6). For two clusters, simulation results reveal that GDH takes more time than HCECKA to converge the system cluster key. The main reason is that every cluster head (BS) is the controller of the descendent cluster key. Consequently, in HCECKA, the entire system can rapidly synchronise the system cluster key, and only need both cluster heads to interchange their descendent cluster keys. However, in this GDH mechanism, each pair of nodes must exchange their keys, and therefore GDH takes more time than HCECKA.
Figures and demonstrate that when a node is added or removed, the system must resynchronise the system cluster key. The simulation result shows that HCECKA spends less time than GDH to resynchronise the new system cluster key. The main factor is because multiplications spend significantly less time than exponential operations. Moreover, in the HCECKA scheme, only a cluster with nodes leaving must recalculate the descendent cluster key, and the main loading focuses on three steps in stage 3 of section 3 for the purpose of recalculating the descendent cluster key. Subsequently, the system can determine the system cluster key within a few operations. However, in the non-cluster scheme for GDH, each node must perform all stages; thus the system requires many operations to calculate the system cluster key.
Figure 11. When one node participates in the system, the time to resynchronise the generation of the system cluster key.
In different key management schemes, Figure demonstrates the elapsed time of secure data transmission for gateway, inter-cluster, intra-cluster modes. Initially, HCECKA takes more time than ECDH to derive the system cluster key. After synchronisation, each node performs secure data transmission using the system cluster key. However, the ECDH scheme must perform session key operations during each secure data transmission phase. Comparison results demonstrate that the intra-cluster equipped with the mechanism using the system cluster key is more efficient than other mechanisms.
Figure 13. Compare secure data transmission time for gateway, inter-cluster and intra-cluster modes.
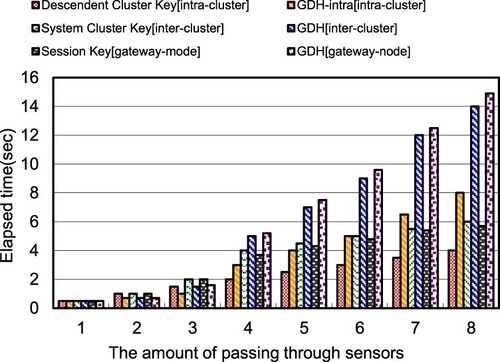
Figure illustrates the consuming time of intra-cluster secure data transmissions. This investigation compares ECDH with the system cluster key scheme of HCECKA, and finds that the transmission time of ECDH is almost 3.5 times that of the system cluster key scheme. These simulation results demonstrate that members of an intra-cluster exploit the descendent cluster key to secure transmitted messages without maintaining the session key for each transmission and take a lower time than ECDH. Additionally, our proposed scheme contains the single master key agreement, which is a particular case of HCECKA. Therefore, the Elliptic Curve Cryptography indeed reduces the key operation time.
Figure depicts the inter-cluster secure data transmission time. After the system cluster key synchronisation, each node enciphers the transmitted message, and adopts the same system cluster key (KP) between distinct clusters to generate HMAC. However, ECDH exchanges a session key between two linked sensors within the routing path, causing the system cluster key scheme to outperform ECDH.
Figure 15. The time required to securely transmit data between two clusters within the inter-cluster.
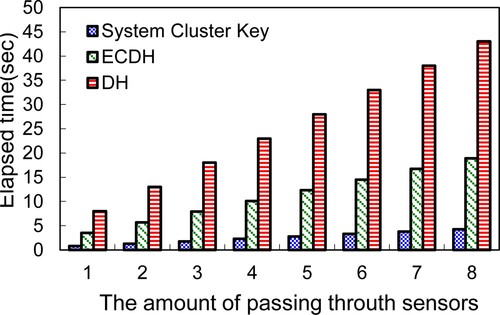
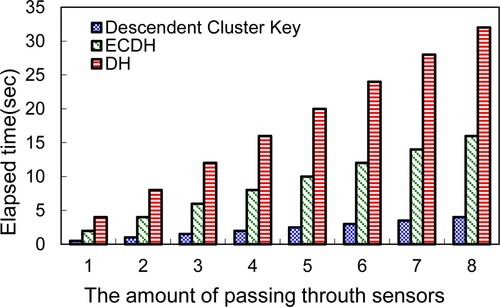
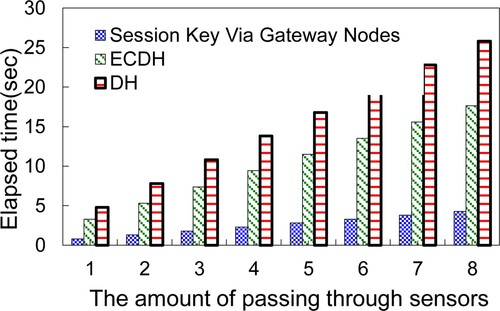
Figure illustrates the time to securely transmit inter-cluster data through the gateway approach. That is this mode. The proposed approach exploits the shortest routing path to secure data transmissions between two distinct clusters using the ECDH session key. Meanwhile, this investigation provides a system cluster key option to improve the secure data transmission efficiency. As the results of these simulations demonstrate that the system cluster key scheme using the gateway mode outperforms ECDH. The transmission time of using ECDH is nearly 4.2 times that of the system cluster key scheme with the gateway mode.
Figure 16. Pass through the gateway nodes, the time required to securely transmit data within an inter-cluster.
Based on the proposed scheme, this study demonstrates that the main computing load of each base station (BS) performs n-1 times multiplication operations to determine the descendent cluster key (for nodes 1∼n-1), and two multiplication operations in order to determine the system cluster key. Additionally, during transmissions, a routing path includes the cluster head that requires the cluster head to encipher and decipher transmitted data and calculate the HMAC code. Moreover, the sensor nodes are responsible for two multiplication operations to assist in determining the descendent cluster key, encipher and decipher transmitted data, and estimate HMAC. The root base station (RBS) performs n-1 times multiplication operations to determine the system cluster key (for base stations 1∼n-1). Consequently, the computing overhead of cluster heads is larger than that of others.
This study surveys various ID-Based Cryptography (IBC) schemes (Sumalatha & Sathyanarayana, Citation2015). M. Arifi et al. utilised a ternary tree to come up with an authenticated group key agreement based on identification (ID-AGKA) (Bala et al., Citation2016; Mandal et al., Citation2020), which was also considered when a member takes part in or departs from the group, and this system needed to reconstruct the group key. Contrary to conventional public key cryptosystems, non-certified public key cryptographic systems assure the authenticity of non-certified public keys. A similar protocol “Certificateless Authenticated Group Key Agreement protocol for dynamic groups” (CAGKA) was considered. Sungchul et al. (Citation2007; Yong et al., Citation2013) proposed CAGKA to overcome the shortcomings of CL-PKC and to support changing group membership (joining or leaving). Debabrat et al. (Citation2014) implemented the ElGamal Elliptic Curve Cryptography over prime field using C. The Distributed Local Key Hierarchy (DLKH) such as the Group Tree-based Diffie-Hellman (TGDH) (Ranjani et al., Citation2011; Lin et al., Citation2011) agreement and the Distributed One-way Function Trees (DOFT) (Hajyvahabzadeh et al., Citation2012; Liang et al., Citation2020) were also considered.
Since HCECKA is enhanced DH and GDH version, they use a key exchange protocol. So we use DH and GDH as evaluated standards to prove that our proposed scheme outperforms DH and GDH. Here, we survey the additional ECC EIgama scheme that is approximate to our proposed scheme, and ECC EIgama uses additions, minuses and multiplications without exponentiations to achieve the entire operations. This study adds the comparison of key operating costs and communication costs between HCECKA and ECC EIgama, and proves that our proposed architecture is better than traditional DH and GDH as well as ECC EIgama. Table compares key operating costs and communication costs of these schemes.
Table 2. Comparison of computing costs.
6. Conclusions
This study employs the elliptic curve cryptography to integrate a key management scheme, and furthermore propose a hierarchy-based key agreement named HCECKA to deal with secure group data transmission. The mechanism that we propose utilises shorter keys to reach the same security level as RSA and Diffe-Hellman (Wei et al., Citation2021; Li et al., Citation2017). Furthermore, this study implements HCECKA on large-scale WSNs to perform key management very well suited. The simulation result shows that HCECKA is quite appropriate for resource-constrained environments such as Internet of Things (IoT) (Dezhi et al., Citation2020; Liang et al., Citation2020), Ad Hoc networks and WSNs. Moreover, during the secure data transmission, HCECKA indeed consumes less resynchronisation time of constructing the system key than GDH and DH key agreement.
Moreover, we also propose a distributed group key agreement protocol with scalable and flexible capabilities. This mechanism utilises multiplications instead of exponential operations when performing ECDH (Jiang et al., Citation2021; Xiao et al., Citation2018), and therefore effectively lowers the CPU overhead (Alessandro et al., Citation2020; Tingting et al., Citation2020). The mechanism we offer is very well suited to implement on a large scale WSNs carrying out dynamic key operations.
This research offers multiple communication modes to increase the performance for securely transmitting data. Within the same cluster, this study provides the intra-cluster mode to secure transmitted data among nodes. When the source node and the target node are located in different clusters, the proposed inter-cluster mode or gateway mode also can accomplish secure data transmissions. Our method employs an efficient hash function and simple key operations to inspect the integrity of transmitted data and secure the transmitted data, respectively, and therefore reduce the requirement of complicated operations in WSNs.
Eventually, the analyses of simulation results demonstrate that HCECKA exceeds other mechanisms on rekeying efficiency and communication overhead. Therefore, HCECKA is quite suited for the large scale of IoT or WSNs without sufficient resources. Especially, in industry, IoT is a tendency. However, IoT is exposed to an open environment. Our proposed approach could be applied to many industrial fields, and significantly improve the security issues.
Disclosure statement
No potential conflict of interest was reported by the author.
Data availability statement
The data that support the findings of this study are available on request.
References
- Alessandro P., Marc O. P., & Lars W. (2020). Group key management in constrained IoT settings. IEEE Symposium on Computers and Communications. https://doi.org/10.1109/ISCC50000.2020.9219619
- An, L., & Peng, N. (2008). TinyECC: A configurable library for elliptic curve cryptography in wireless sensor networks. In Proceedings of the 2008 International Conference on Information Processing in Sensor Networks (pp. 245–256). https://doi.org/10.1109/IPSN.2008.47
- Bala, S., Sharma, G., & Verma, A. K. (2016). PF-ID-2PAKA: Pairing free identity-based two-party authenticated key agreement protocol for wireless sensor networks. Wireless Personal Communications, 87(3), 995–1012. https://doi.org/10.1007/s11277-015-2626-5
- Debabrat B., & Monjul S. (2014). Implementation of ElGamal elliptic curve cryptography over prime field using C. International Conference on Information Communication and Embedded Systems. https://doi.org/10.1109/ICICES.2014.7033751
- Dezhi, H., Nannan, P., & Kuan, C. L. (2020). A traceable and revocable ciphertext-policy attribute-based encryption scheme based on privacy protection. IEEE Transactions on Dependable and Secure Computing. https://doi.org/10.1109/TDSC.2020.2977646
- Diffie, W., & Hellman, M. (1976). New directions in cryptography. IEEE Transactions on Information Theory, 22(6), 644–654. https://doi.org/10.1109/TIT.1976.1055638
- Dong G. L., & Peng N. (2003). Establishing pair-wise key establishments for static sensor networks. In Proceedings of 10th ACM Conference on Computer and Communications Security (pp. 52–61). https://doi.org/10.1145/986858.986869
- Donggang, L., Peng, N., & Wenliang, D. (2005). Group-based key pre-distribution in wireless sensor networks. In Proceedings of ACM Workshop on Wireless Security (pp. 11–20). https://doi.org/10.1145/1080793.1080798
- Du, W., Deng, J., Han, Y. S., Varshney, P. K., Katz, J., & Khalili, A. (2005). A pairwise key pre-distribution scheme for wireless sensor networks. ACM Transactions on Information and System Security, 8(2), 228–258. https://doi.org/10.1145/1065545.1065548
- Hajyvahabzadeh, M., Eidkhani, E., Mortazavi, S. A., & Nemaney Pour, A. (2012). An efficient group key management protocol using code for key calculation: CKC. Telecommunication Systems, 51(2-3), 115–123. https://doi.org/10.1007/s11235-011-9421-8
- Haowen, C., Adrian, P., & Dawn, S. (2003). Random key pre-distribution schemes for sensor network. In Proceedings of IEEE Symposium on Research in Security and Privacy (pp. 197–213). https://doi.org/10.1109/SECPRI.2003.1199337
- Janies, J., Huang, C. T., Johnson, N. L., & Richardson, T. (2007). SUMP: A secure unicast messaging protocol for wireless ad hoc sensor networks. International Journal of Sensor Networks, 2(5/6), 358–367. https://doi.org/10.1504/IJSNET.2007.014359
- Jiang, Y., Liang, W., Tang, J., Zhou, H., Li, K.-C., & Gaudiot, J.-L. (2021). A novel data representation framework based on nonnegative manifold regularization. Connection Science, 33(2), 136–152. https://doi.org/10.1080/09540091.2020.1772722
- Li, Z., Wang, H., & Fang, H. (2017). Group-based cooperation on symmetric key generation for wireless body area networks. IEEE Internet of Things Journal, 4(6), 1955–1963. https://doi.org/10.1109/JIOT.2017.2761700
- Liang, W., Fan, Y., Li, K.-C., Zhang, D., Gaudiot, J.-L. (2020). Secure data storage and recovery in industrial blockchain network environments. IEEE Transactions on Industrial Informatics, 16(10), 6543–6552. https://doi.org/10.1109/TII.2020.2966069
- Liang, W., Huang, W., Long, J., Zhang, K., Li, K.-C., & Zhang, D. (2020). Deep reinforcement learning for resource protection and real-time detection in IoT environment. IEEE Internet of Things Journal, 7(7), 6392–6401. https://doi.org/10.1109/JIOT.2020.2974281
- Liang, W., Li, K.-C., Long, J., Kui, X., Zomaya, A. Y. (2020). An industrial network intrusion detection algorithm based on multi-feature data clustering optimization model. IEEE Transactions on Industrial Informatics, 16(3), 2063–2071. https://doi.org/10.1109/TII.2019.2946791
- Lin, H. Y., Hsieh, M. Y., & Li, K. C. (2016). Flexible group key management and secure data transmission in mobile device communications using elliptic curve Diffie-Hellman cryptographic system. International Journal of Computational Science and Engineering, 12(1), 47–52. https://doi.org/10.1504/IJCSE.2016.074558
- Lin, Y., Bing, L., Feng, X., Guowei, W., & Qiang, L. (2011). A group key management protocol based on weight-balanced 2-3 tree for wireless sensor networks. Information, 14(10), 3261–3278. https://arxiv.org/abs/1205.1465
- Mandal, S., Mohanty, S., & Majhi, B. (2020). CL-AGKA: Certificateless authenticated group key agreement protocol for mobile networks. Wireless Networks, 26(4), 3011–3031. https://doi.org/10.1007/s11276-020-02252-z
- Nicolas, S., & Xin, M. Z. (2007). Wireless security and cryptography: Specifications and implementations. CRC-Press. https://doi.org/10.1201/9780849387692
- Piotr S., Leonardo B. O., Michael S., Martin C., & Ricardo D. (2008). NanoECC: Testing the limits of elliptic curve cryptography in sensor networks. European Conference on Wireless Sensor Networks, LNCS, 4913 (pp. 305–320). https://doi.org/10.1007/978-3-540-77690-1_19
- Ranjani, R. S., Lalitha, B., & Avadhani, P. S. (2011). Current trends in group key management. International Journal of Advanced Computer Science and Applications, 2, 82–86. https://doi.org/10.14569/IJACSA.2011.021114
- Sumalatha, P., & Sathyanarayana, B. (2015). Enhanced identity based cryptography for efficient group key management in WSN. International Journal of Application or Innovation in Engineering & Management, 4, 116–128. https://doi.org/10.1007/s11276-020-02252-z
- Sungchul H., Zeen K., & Kwangjo K. (2007). Certificateless authenticated group key agreement protocol for dynamic groups. IEEE global Telecommunications Conference. https://doi.org/10.1109/GLOCOM.2007.93
- Tingting, X., Dezhi, H., Junhui, H., Kuan, C. L., & Rodrigo, F. M. (2020). Multi-Keyword ranked search based on mapping set matching in cloud ciphertext storage system. Connection Science, 33(1), 95–112. https://doi.org/10.1080/09540091.2020.1753175
- Wei, L., Lijun, X., Ke, Z., Mingdong, T., He, D., & Kuan, C. L. (2021). Data fusion approach for collaborative anomaly intrusion detection in blockchain-based systems. IEEE Internet of Things Journal. https://doi.org/10.1109/JIOT.2021.3053842
- Xiao, S., Guo, Y., Huang, K., & Jin, L.(2018). Cooperative group secret key generation based on secure network coding. IEEE Communications Letters, 22(7), 1466–1469. https://doi.org/10.1109/LCOMM.2018.2831703
- Yong, J. K., Yong, M. K., Yong, J. C., & Hyong, C. O. (2013). An efficient bilinear pairing-free certificateless two-party authenticated key agreement protocol in the eCK model. Journal of Theoretical Physics and Cryptography, 3, 1–10. https://arxiv.org/abs/1304.0383
- Zhong, Y. Q., Xin, S. Z., Kerong, F., Qun, F. Z., & Jie, H. (2014). An efficient identity-based key management scheme for wireless sensor networks using the bloom filter. Sensors Journal, 14(8), 17931–17951. https://doi.org/10.3390/s141017937
- Zhongyuan, Q., Xinshuai, Z., Kerong, F., Qunfang, Z., & Jie, H. (2014). An efficient identity-based key management scheme for wireless sensor networks using the bloom filter. Sensors Journal, 14, 17931–17951. https://doi.org/10.3390/s141017937
- Zhou, L., Ni, J., & Chinya, V. R. (2005). Efficient key establishment for group-based wireless sensor deployments. In Proceedings of the 4th ACM Workshop on Wireless Security (pp. 1–10). https://doi.org/10.1145/1080793.1080797