?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.Abstract
The Internet of Vehicles is deployed in an open environment, and protecting its security and data privacy is the challenge. Carrying out the Internet of Vehicles secure authentication before interaction of information is an important part of ensuring the security foundation. Therefore, this article designs a safe and reliable Internet of Vehicles authentication and key agreement schemeassisted by blockchain. This article uses a multi-TA network model to improve the efficiency of authentication. Because of the rapid movement of vehicles, it will continue to appear cross-RSU and TA certification. Considering the disadvantages of most centralised authentication protocols using a single TA, this paper uses the multi-TA model to improve the efficiency of authentication. By usingblockchain technology to store the authentication information of vehicles, the cross-domain authentication of vehicles and the protection of user privacy information can be well realised. At the same time, in order to reduce the time of vehicle authentication, this scheme uses a lightweight calculation operation to complete the whole process of authentication. Through security analysis and results of Proverif simulation, the security of the solution is well proved, our scheme can resist various common attacks. Compared with some existing Internet of Vehicles security authentication protocols, the proposed scheme has a lower cost of computation, communication, and storage.
1. Introduction
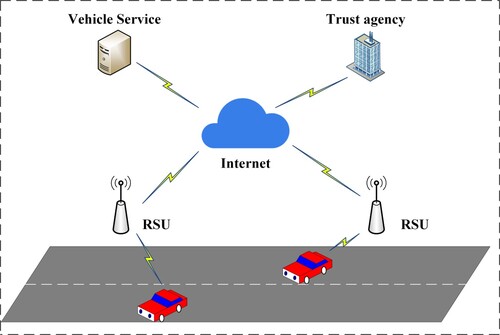
With the development of data processing (Liu et al., Citation2019) and communication technology, vehicles begin to be intelligent (Zhao et al., Citation2021). The vehicle integrates sensor computing, network communication, and other technologies, which enables it to interact with different units. It is the intelligent development of vehicles that led to the emergence of the Internet of Vehicles. It is not only an important part of the intelligent transportation system (Zheng et al., Citation2021), but also an important innovation in the Internet of Things technology (Xiao & Zhu, Citation2017). In the Internet of Vehicles, vehicles can realise V2X communication through their own communication components. X can be any entity, which includes communication between vehicle and vehicle(V2V), communication between vehicle and infrastructure (V2I), communication between vehicle and RSU (vehicle and roadside unit), etc (Machardy et al., Citation2018). The structure of the traditional internet of vehicles is shown in Figure . Internet of vehicles can provide users with a lot of basic services, such as vehicles can get traffic information, allowing users to make traffic decisions, vehicles can collect road information through sensors, GPS, and other equipment and share it with other vehicles in real time (Zhang et al., Citation2021). More and more smart cars are joining, which has led to a massive increase in traffic data to the Internet of Vehicles, and because of its open environment, the security problems of the Internet of Vehicles are getting worse (Jiang et al., Citation2019). It is not only necessary to safely and reliably protect the data privacy of vehicle users, but also prevent attacks from malicious users, such as data tampering, data replay, denial of service, man-in-the-middle attacks, and other malicious behaviours (Aman et al., Citation2020). These malicious behaviours will make users unable to use the Internet of Vehicles service normally, and cause serious traffic accidents due to the use of wrong traffic information data. The first step to improve the reliability and security of the Internet of Vehicles is to verify the security of users. It can ensure that legitimate vehicles enter the Internet of Vehicles and refuse the participation of illegal users. This is also the focus of experts' research on the Internet of Vehicles in recent years.
Authentication of identity and data processing efficiency are important factors to realise the real-time response of the Internet of Vehicles (Huang et al., Citation2021). Reducing the time delay can provide users with fast traffic decisions and ensure good service quality (Qiu et al., Citation2018). During the fast driving process of the vehicle, it will pass through different areas and conduct multiple authentications, which will also increase the computational and communication costs of vehicles, thereby affecting the service quality of the Internet of Vehicles. The German Federal Highway Research Institute (BASt) reports that the risk of traffic accidents caused by the traffic decision made by the owner under the condition of reaction delay is eight times higher than that in the normal situation, and the risk of fatal traffic accidents is four times higher (Huang et al., Citation2010). Therefore, it is necessary to ensure that the Internet of Vehicles has a low-latency authentication scheme, which can enable users to quickly obtain traffic information services and make correct decisions in time (Jiang et al., Citation2016; Vasudev & Das, Citation2018). In the current Internet of Vehicles authentication, the PKI method is still the most adopted. Because of the fast-moving characteristics of vehicles, TA must complete the trust relationship and key agreement with the vehicle in a short time. As the number of vehicles increases, many vehicles carry out authentication at the same time, which will cause heavy tasks on central node and privacy leakage of user (Wu et al., Citation2021). TA requires multiple information interactions with vehicles, which leads to increased delays in authentication and communication and makes it more unsuitable for fast-moving vehicles to access the Internet of Vehicles (Xiong et al., Citation2012). Therefore, the efficiency in the traditional PKI scheme is easily affected by the computational performance of TA. In our smart city, the independent development of regions has become more and more mature. Each region should have its own TA for vehicle management. Therefore, the Internet of Vehicles can no longer use a single TA for authentication and should use a multi-TA model. Given the ability of vehicles to move quickly and the limits of RSU communication range, vehicles will certainly encounter many RSUs or enter different areas during driving, and the number of authentication will increase (Yao et al., Citation2019). Therefore, shortening the time of authentication and communication is the main goal of authentication scheme for Internet of vehicle, and it also needs to meet the security characteristics such as authenticity, integrity, and anonymity. In order to ensure these security features, the blockchain (Li et al., Citation2021) can well meet these needs. As a distributed ledger, blockchain has the characteristics of tamper-proofing, integrity, and decentralisation (Liang et al., Citation2020). It is suitable for distributed application scenarios and provides great help to solve the problem of cross-domain authentication of vehicles. Blockchain has become a reliable technology to solve the security problem of vehicles. It solves the problem of message leakage caused by centralisation, and also makes attackers unable to tamper with vehicle-related data. Based on the above scenarios, this article proposes a blockchain-based lightweight authentication and key agreement scheme for Internet of vehicles. The main contributions of this article are summarised as follows:
This article uses a multi-TA network authentication model to establish a trust relationship with the vehicle. All TAs serve as nodes of the blockchain to maintain vehicle-related information to achieve cross-domain authentication.
To reduce the security risks caused by information leakage through distributed storage, We store the vehicle's auxiliary authentication information and the vehicle's real identity information separately. The former is stored in the alliance chain, and the latter is stored in the private chain of TA and RSU nodes in each region.
Each entity performs mutual authentication and reaches a key agreement to enhance security.
In order to realise the lightweight authentication, we only use XOR, connection, hash, and other related operations in the whole scheme, which reduces the calculation and storage cost of vehicle identity authentication and ensures the security characteristics required by the system.
Through security analysis and using the ProVerif tool, we prove the security of the authentication and key exchange mechanism designed in this scheme.
2. Related work
The design of the Internet of Vehicles is mainly to provide driving services for vehicle users, de Cock Buning and de Bruin (Citation2017) information security and privacy issues are very important. The first step to solve the problem of security and privacy in VANETs is authentication, which has attracted more and more scholars' attention and research. Raya and Hubaux (Citation2007) proposed an authentication scheme based on public-key infrastructure (PKI), which can complete identity authentication and ensure message integrity, but the process of authentication is complicated, the communication volume of RSU is huge, and the vehicle needs to store a large number of certificates. Vasudev et al. (Citation2020) proposed Internet of Vehicle identity authentication protocol, which uses physical unclonable functions to implement anonymous identity authentication, but it has not been proven that it can prevent man-in-the-middle attacks. Yahiatene and Rachedi (Citation2018) use anonymous identity for authentication, which can well protect the user's private information and protect against identity relocation attacks, but this scheme has a long delay and requires a lot of storage space. Lei (Citation2016) proposed an efficient and anonymous authentication scheme, which uses the roadside unit RSU for batch authentication, but the authentication of RSUs is very frequent and the workload of RSUs is considerable. Wang et al. (Citation2021) designed a novel authentication protocol for emergency vehicles. Although the subsequent process of authentication is simplified and the interaction of identity information is reduced, its overall authentication delay is still high. At the same time, the workload of RSU is relatively large, which has a great impact on efficiency. Fromknecht et al. (Citation2014) proposed a blockchain-based decentralised PKI authentication system to provide key querying and identity binding service, but it may leak user's privacy because the user's identity and public key are stored in the blockchain directly. Vasudev et al. (Citation2020) proposed a lightweight authentication scheme that simplifies the authentication process to respond to vehicles in real time. In terms of safety performance, malicious vehicles cannot be effectively traced. Basudan et al. (Citation2017) also designed a privacy protection protocol in order to improve the security of the Internet of Vehicles. Wang et al. (Citation2018) proposed a scheme based on Paillier encryption. However, these authentication schemes are too centralised and require multiple communication, which leads to increased consumption of computing and communication. Obviously, the traditional centralised authentication method can no longer meet the growing demand for cross-domain communication. As a distributed ledger, blockchain has become a good solution for the Internet of Vehicles authentication scheme. It can not only provide anonymity, authenticity, and integrity for information but also play an important role in the cross-domain authentication of vehicles (Liang et al., Citation2021). Wang et al. (Citation2019) developed an effective blockchain-based decentralised authentication mechanism for the Internet of Vehicles, which solved the centralisation problem caused by the traditional centralised authentication, but did not protect the private information of the vehicle and did not conduct a comprehensive security analysis. Vehicles are vulnerable to security attacks such as identity relocation. Wang et al. (Citation2020) proposed a scheme that uses blockchain assistance to calculate the credibility of vehicles and implement cross-domain authentication. Although the consumption of calculation and communication of vehicles in the subsequent authentication is reduced, the calculation overhead in the initial authentication stage is still relatively big. Lei et al. (Citation2017) used the blockchain to construct an identity authentication and key agreement protocol and designed a new network topology to simplify the management of distributed keys in the Internet of Vehicles, but it did not implement a key update. Xu et al. (Citation2021) also proposed a blockchain-assisted authentication protocol for Internet of Vehicle. With the help of blockchain, only some lightweight calculational methods are used to complete the authentication, which greatly reduces the calculation of the authentication process. But it still has the problem of data centring, and the efficiency of authentication is easily affected by the data centre. Yao et al. (Citation2019) proposed a lightweight anonymous authentication for distributed vehicle fog services assisted by blockchain, but the computational cost and time consumption will continue to increase as the number of vehicles increases. Eddine et al. (Citation2021) proposed a blockchain authentication scheme based on fog computing, which has an efficient authentication efficiency but cannot adapt to large-scale authentication of vehicles, and there is still a high delay when the number of vehicles is large. Kang et al. (Citation2018) used mobile edge computing and blockchain to realise data sharing and information security in the Internet of Vehicles. The authentication scheme designed does not support the mutual authentication, and the security is lower than that of the mutual authentication scheme. Therefore, in view of the security features and real-time requirements of the Internet of Vehicles, we designed a lightweight blockchain-based identity authentication and key agreement scheme for the Internet of Vehicles.
3. Background and system structure
3.1. Elliptic curve cryptography
Elliptic Curve Encryption Algorithm (ECC) is an asymmetric encryption algorithm based on the mathematical theory of elliptic curve (Xiao et al., Citation2021). In general, the elliptic curve can be represented by the following equation, where A, B are coefficients.
(1)
(1) Choose two non-negative integers A and B that are less than P meet the following constraints:
(2)
(2)
Definition 3.1
Elliptic curve discrete logarithm problem (ECDLP): Given a prime number p and an elliptic curve E, for
(3)
(3) that find a positive integer X less than p, given P, Q. The advantage of an adversary to calculate during polynomial time is as given:
,
, is the ECDLP assumption concluded, where
, is very small (Chaudhry et al., Citation2017).
3.2. One-way hash function
One-way hash function (Liu et al., Citation2021) can calculate quickly a fixed-length hash value based on information of any length, and the hash value is different for different messages, It has a one-way nature, which means that the hash value cannot be used to inversely calculate the message.
Definition 3.2
Hash function has the feature of resisting collision that predefined security anti-collision hash function Hf(). The opponent wants to find a label in order to get
which is marked as
, where A is permitted to choose
arbitrarily in polynomial time t, the collision resistance deduce that
(Chaudhry et al., Citation2017)
3.3. Blockchain
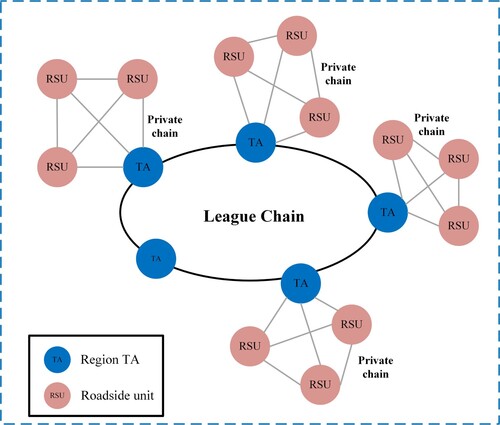
Blockchain is a distributed peer-to-peer network (Liang et al., Citation2019). It is also a specific data structure that combines data blocks in chronological order in a chain, and is cryptographically guaranteed to be non-tamperable, non-forgeable, and shared general ledger. There are three types of blockchains: public chains, private chains, and alliance chains. Faced with different types of application scenarios, different types of blockchains can be selected. The security requirements of the Internet of Vehicles coincide with the technical characteristics of the blockchain (Yang et al., Citation2019). In order to solve the problem that leakage of privacy information, and tampering caused by the traditional centralised authentication system, and to solve the problem of rapid cross-domain authentication, blockchain can be used technically to store the relevant authentication information of the vehicle. If an attacker wants to modify the data on the blockchain, it must not only modify the hash value of the current blockchain but also modify the hash value of all blocks on the chain. The cost is extremely high. In our proposed security scheme, we use blockchain to store vehicle auxiliary information for cross-domain authentication. The structure of the blockchain in this article is shown in Figure . In order to protect the privacy of users, the registered nodes TA in each region form an alliance blockchain and are responsible for initiating a consensus on the auxiliary authentication message obtained after vehicle registration. Because the private chain has a built-in access control layer in the protocol, it can manage access rights and ensure the privacy and security of data. In order not to expose the real identity of the user to the alliance chain with more participating nodes, We form a private chain of registered nodes (TA) in each region and all RSUs in the region, which is responsible for storing and updating the mapping relationship between anonymity and the real identity of registered vehicles in the region. In the blockchain structure, each block contains the previous block's hash value, timestamp, markle tree, block transaction, etc. As far as the consensus algorithm is concerned, PoW (Javaid et al., Citation2020) needs to consume a lot of computing resources and cannot meet real-time performance. PoS (Ayaz et al., Citation2020) and DpoS (Liang et al., Citation2020) are also not suitable for the application scenarios of the Internet of Vehicles, so the alliance chain and Private chains all use the PBFT consensus algorithm, which has a low consensus response and meets the real-time requirements of the Internet of Vehicles.
3.4. System structure
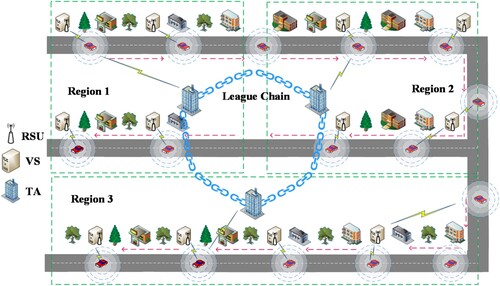
The Internet of Vehicle System is composed of the following parts: authoritative department (AD), vehicle, trust agency (TA), roadside unit (RSU), vehicle server (VS). In smart city management, a city has only one AD, the city consists of several regions. Each region will have its own TA, RSU, and VS. When the vehicle enters the region managed by a TA, it will pass through multiple RSU communication ranges in the region. After the vehicle is authenticated by RSU, the key to communicate with VS can be obtained. VS provides corresponding services for the vehicle through the key. The Internet of Vehicle model framework of this article is shown in Figure .
AD (authoritative department): It manages the TA of the entire CITY system and initialises and publishes system security parameters
TA (trust agency): Each region is managed by a TA, TA is responsible for vehicle registration tasks. TAs in this region and TAs in other regions act as alliance chain nodes that store vehicle authentication information
, In addition, TA in each region and RSU belonging to the region together form a private chain, which maintains the real identity and anonymous identity
of registered vehicles in the region.
RSU (roadside unit): It is responsible for mutual authentication with vehicles entering the communication range, and assists VS to complete key agreements with the vehicle. RSU, as a private chain node, maintains
together with TA in the region. It can also access the alliance chain.
VS (vehicle server): As an information platform for providing services for vehicles, it is deployed around each RSU. With the help of RSU, complete the key agreement with the vehicle, and finally provide service for the vehicle through the key. The services VS can provide are road traffic information, route planning, entertainment applications, etc.
3.5. Adversary threat model
The threat models used in this article are as follows:
All TAs are semi-trusted nodes, they may produce malicious behaviour, but their malicious behaviour will not affect other TA nodes.
The adversary has the ability to intercept all data transmitted through non-secure channels, he can inject new data, and replace or replay previously sent data.
The adversary can simulate the communication between entities. For example, the adversary can simulate a trusted node and perform authentication.
The adversary can perform password guessing through offline attacks of password guessing.
The shared key between RSU and TA is stored in the tamper-proof device. Even if the adversary compromises the RSU or TA, it still cannot obtain the session key.
The adversary can capture the vehicle's session information to retrieve the parameters.
4. Proposed scheme
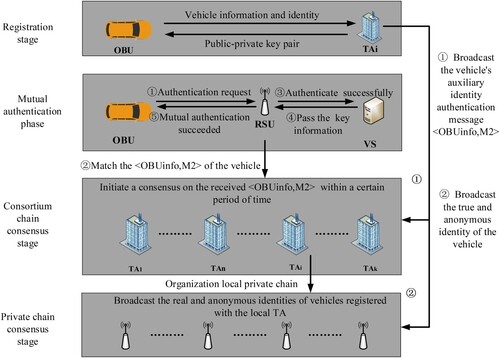
In this section, we will describe in detail the proposed scheme, which consists of five stages: (1) system initialisation stage, (2) registration stage, (3) consensus stage, (4) mutual authentication and key agreement stage. (5) Vehicle real identity retrospective and anonymous identity change Its workflow is shown in Figure . We will explain each stage in the following sections. Table shows the label descriptions used in the certification process.
4.1. Description of our scheme
4.1.1. System initialisation phase
When the system is being established, AD loads the parameters into TA and RSU through offline mode.
Table 1. Label description.
AD chooses a large prime number P and a finite field
.
AD generates a session key
shared by each regional TA.
AD chooses a secure one-way encryption hash function
.
Each TA will get the parameters
shared by AD when it is arranged.
4.1.2. Registration stage
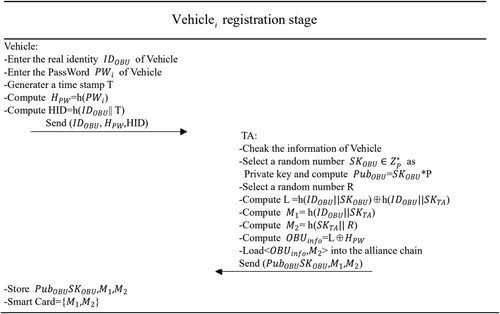
Each vehicle needs to register with the local TA before obtaining the relevant services provided by the Internet of Vehicles. TA will check the identity information of the registered vehicle, assign it a public–private key pair, and store the relevant information of the vehicle in the blockchain. The specific steps are shown in Figure .
The user submits the real message of his related vehicle and unique identity
, vehicle password
. It generate a timestamp T, and creating anonymous identity
. User sends
to TA through a secure channel (offline transmission).
TA checks the vehicle information and
, and then TA selects a random number
, as vehicle's private key, and computes the public key that
. TA assigned
to vehicle. In addition,
. The TA choose a random number R, then calculates
.TA broadcasts
to the alliance chain, broadcasts the mapping
of the vehicle to the local private chain and stores TK locally. TA sends smart card
and TK to the vehicle.
The vehicle user saves , HID, T, TK, Smart Card
for future communication.
4.1.3. Consensus stage
In our scheme, there are alliance chains and private chains. TAs of all regions form an alliance chain, and TAs and RSUs of each region form a private chain. In order to reduce the consumption of consensus time, they choose to use the PBFT algorithm to form a public ledger. To solve problems caused by centralised management, we use the tamper-proof modification of the blockchain to write the relevant auxiliary authentication information ,
of the vehicle into the alliance chain composed of TA. Because of the openness and transparency of the blockchain, if all TAs can obtain the relevant identity information of the vehicle, it is easy to cause the leakage of the vehicle information. Therefore, We introduce a private chain to store identity information
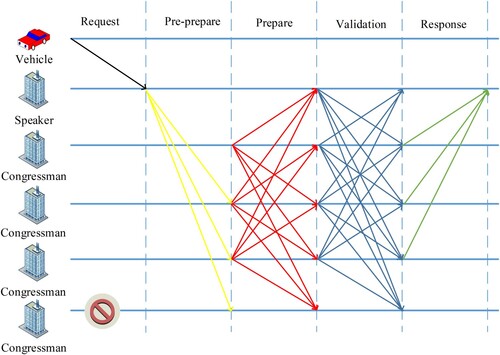
for vehicles registered in the area. If there is a TA seeking the true identity of a malicious vehicle on the consortium chain, each TA can quickly search on its own private chain to see whether there is the real identity of the anonymous vehicle. In the consensus process, we take the alliance chain as an example, and the consensus process is shown in Figure .
We assume that there are n registered nodes
, in a certain city, and they are all responsible for creating blocks as consensus nodes of the blockchain. In each round of consensus, one node is selected as the speaker. The remaining nodes serve as slave nodes to respond or vote and the speaker cannot vote. In order to save consensus time, each speaker is responsible for k rounds of consensus. The rule for the election of speakers is
Where heigh is the height of the current block.
After the vehicle has passed the TA registration, the TA will publish the vehicle's auxiliary information
to the alliance chain, so as to facilitate the subsequent cross-RSU or TA certification of the vehicle. At the same time, the TA announces the relationship
to the private chain of its own group for consensus. After a certain fixed time interval, ▵t, the vehicle auxiliary authentication information
set within the interval is constructed into a block, and the speaker will send
to other TAs,
represents the speaker's vote request.
After the TA node receives the speaker's voting request, it will check the block content and make a voting response and broadcast that
.
Each TA node will reach a consensus only if it receives voting responses from N-F nodes, otherwise, it will enter the next round of consensus. Among them, F stands for
, which means that at most F nodes are tolerated during the consensus process, such as offline caused by network failure.
4.1.4. Mutual authentication and key agreement stage
After registered vehicles want to obtain services from VS, they must first perform mutual authentication with RSU and a key agreement with VS. The specific process is as follows.
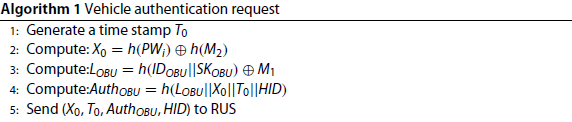
The vehicle generates a timestamp
and calculate
,
, these parameters are used for authentication.
,
, Vehicle sends
to RSU, as shown in Algorithm 1.
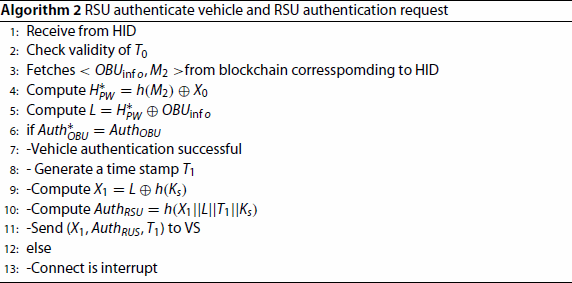
RSU verifies the timestamp and matches the
according to HID from the blockchain. First, RSU obtains the password information of the vehicle and calculates
. RSU calculates vehicle identity information
, computes
. RSU verifies whether
and
are equal and completes the validation, otherwise disconnecting the connection. Next, RSU computes
. and generating a timestamp
, Computes
, Finally, RSU sends
to VS. The specific steps are shown in Algorithm 2.
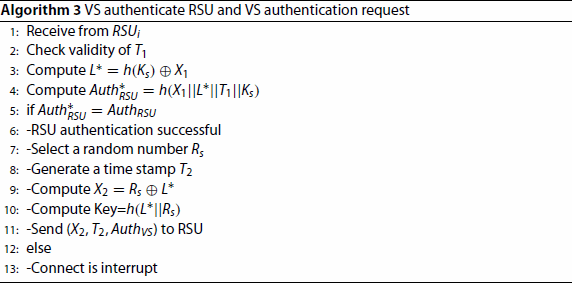
VS first verifies the timestamp
sent by RSU, Computes
,
. Check if
is equal to
, if it is equal, the authentication of the RSU is completed. Otherwise, disconnect the connection. VS generates a timestamp
and random number
. VS calculates the
,
. Finally, VS sends
to RSU. The specific steps are shown in Algorithm 2.
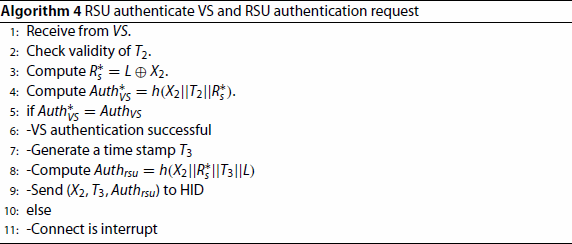
RSU verifies the timestamp
, and calculates
. RSU checks if
is equal to
if they are equal, its integrity is valid and authentication is successful. RSU generates a timestamp
and computes
. Finally RSU sends
to vehicle.

Vehicle checks timestamp
, computes
If
equals
, the validation completes. Finally, vehicle calculates the
. The specific steps are shown in Algorithm 3.
4.1.5. Vehicle real identity retrospective and anonymous identity change
The private chain composed of TAs and RSUs in each region maintains a public ledger with the label of the real and anonymous identity of the vehicle user. When a node on the alliance chain looks for the real identity of the malicious vehicle, a request broadcasting Request-HID is sent, each TA node will start a smart contract to forward the message to the private chain maintained by itself, and look for the identity information of the anonymous vehicle on the private chain. If it exists, TA broadcasts the real identity information
to the alliance chain. On the private chain and the alliance chain, the Speaker on the respective chains will set the status of the vehicle's different information
to be invalid and add them to the public ledger maintained by the blockchain. If the authenticated vehicle wants to change HID, the vehicle sends a change request
to the new TA. New TA stores the
on its private chain and tells other TAs that HID identity information has changed.
5. Security analysis
This part shows the security analysis of our proposed solution. First, we analyse the security characteristics of the solution and compare the security performance with other solutions, and then use Random Oracle Model and Proverif software to provide formal verification security certification for the solution.
5.1. Security feature analysis
Simulated attack: The enemy can pretend to be a participant in the entire conversation, such as vehicles, RSU, and VS.
Resist simulation attacks of vehicle: If the adversary wants to simulate a legal vehicle for authentication, it needs to calculate authentication message that
. The adversary needs to guess the real identity of the legal vehicle
, the vehicle password
and also need to obtain the Smart Card of the vehicle
. If the authentication information is calculated and sent to the RSU without knowing these identity information parameters, the authentication will fail at the RSU and RSU will consider the authentication request as invalid and connect the terminal. Therefore, this solution is a good defense against simulation attacks of vehicles.
Resist simulation attacks of RSU: The adversary can intercept the information transmitted on the non-secure channel between the RSU and the vehicle/VS server, and pretend to be the RSU to communicate with them. When the adversary sends a message to the VS, it needs to guess the session key
between the RSU and the VS, which will cause the verification to fail due to the wrong value of
. That will cause the verification to fail due to the wrong value of
when the VS server performs verification. Similarly, when the opponent sends a message to the vehicle, it needs to guess a random number
generated by the VS server and L. These guessed values will cause the verification at the vehicle to fail.
Resist simulation attacks of VS: When the adversary simulates the VS to send a message to the RSU, it needs to guess the shared key
between the RSU and the VS and the L sent by the RSU to the VS, so that the VS cannot calculate the correct
and the verification at the RSU also leads to failure.
Smart card theft attack: When the Smart Card
of the vehicle is obtained by the opponent, the adversary can use it to calculate the authentication information, but the adversary cannot know
and the password
, and still cannot calculate the correct
and
. The first step of RSU verification is to get the correct password of the vehicle and calculate the correct L with
for the next step of verification.
Key security: When a vehicle wants to negotiate a session key with the VS, both the RSU and VS verify the vehicle's information
to ensure that it is valid. Vehicle at the same time will also check L and
sent by RSU, and finally,
and L will be used for the session Key, the session
. This ensures the security of the session key.
Replay attack: The proposed protocol uses timestamp
to resist replay attacks. When the session entity receives the message, it first verifies the validity of the timestamp. In addition, it can ensure that the received timestamp is not tampered with, because the timestamp is also protected by h() function as part of the authentication parameter. Because the opponent cannot get some relevant parameters such as
, and L to calculate the correct messages such as
So the validity of the timestamp can be guaranteed to resist replay attacks.
Man-in-the-middle attack: In order to avoid man-in-the-middle attack, each part of the session will verify each other. For example, RSU will authenticate the vehicle through
and
. VS and RSU are also authenticated by the session key
, and the vehicle authenticates the L from the RSU to ensure there is no man-in-the-middle attack.
Non-interactivity: The vehicle only needs to send the authentication request message once. Even in the service transport phase, the vehicles only need to submit the service access request, and they are non-interactive throughout the process.
Traceability and non-repudiation: The goal of the private chain of TA and RSU is to store the identity information
to achieve traceability. When malicious behaviour is discovered and broadcast in the alliance chain, each TA will search for the vehicle's true identity
on its own private chain according to HID. After finding the public key, TA will revoke its public key, broadcast the result on the alliance chain, and add its real identity and auxiliary authentication message
to the blacklist maintained by the alliance chain. When the true identity of the vehicle is revealed, its malicious behaviour cannot be denied, so the proposed scheme is traceable and uncertain. Finally we compare our security performance with other schemes, as shown in Table .
Table 2. Safety analysis and comparison.
5.2. Formal security verification using Random Oracle Model (ROM)
The following theorems are used to formally prove the security of our scheme against an adversary (Mishra et al., Citation2014), we define the following Oracle:
Reveal: This oracle will unconditionally return the input m from the associated hash value
Extract: This oracle will return the scalar X out of a specified point Q = XP and P
Theorem 5.1
Based on the assumption that the secure one-way hash function acts like a random oracle and the hardness hypothesis of the ECDLP, the proposed authentication scheme is secure against an adversary A for resolution: It prevents an adversary from getting the identity of the vehicle
the vehicle key
and the TA key
.
Proof.
If Adversary A wants to get the identity of the vehicle , private key
and the TA key
, Reveal and Extract are needed to perform some operation
to counter the security of the proposed certification scheme. A has a success rate of
. The advantage of A is defined as
[27], in which is allowed to make the maximum number of Reveal
and Extract
queries. In EXPR1, A calculates the information it needs by eavesdropping on the message sent by OBU to TA and using Reveal and Rxtract. Based on the above behaviour of A, if A can reverse the security one-way hash function Hf() and solve ECDLP, So A can Compute
. However, according to Definitions 3.1 and 3.2, this is not feasible in the calculation. As a result
. Therefore, the proposed authentication scheme is secure against an adversary A to derive the
.
Theorem 5.2
Based on the assumption that the secure one-way hash function acts like a random oracle and the hardness hypothesis of the ECDLP, the proposed authentication scheme is secure against an adversary A for resolution: It prevents an adversary from getting the Shared key
of the RSU and VS, Authentication message
and Session Key.
Proof.
Adversary A wants to get the Shared key of the RSU and VS,
. In order to calculate these, A must use Reveal and Extract in
to against the security of the proposed scheme. Its success rate is
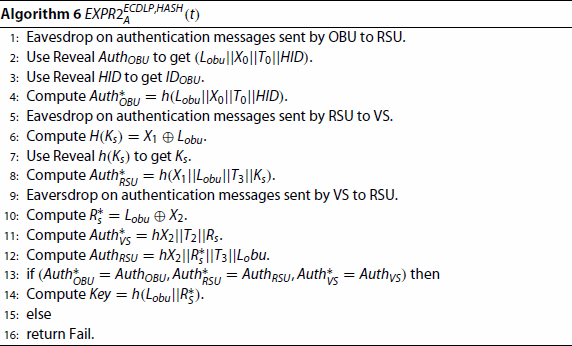
, the experimental EXPR2 algorithm is shown in Figure . The advantage of A is defined as
,in which is allowed to make the maximum number of Reveal (
) and Extract (
) queries. Based on EXPR2, If A can reverse the secure one-way hash function Hf() and solve the ECDLP, then A can calculate the shared key
of the RSU and VS,
and Session Key. However, according to Definitions 3.1 and 3.2, this is not feasible in the calculation. As a result
. Therefore, the proposed authentication scheme is secure against an adversary A to derive the
.
5.3. Proverif security verification
ProVerif is a formal automatic verification cryptographic protocol tool based on the Dolev–Yao model developed by Bruno Blanchet. It is implemented in Prolog language. It is able to describe a variety of cryptographic primifiers, including: shared key cryptography, public key cryptography (encryption and digital signature), Hash functions, the Deffie–Hellman key exchange protocol, specify rewrite rules and equations for the input language as applied PI calculus or Horn words. In order to verify the scheme proposed in this paper, we coded and tested the protocol with HLPSL. Figures and are the verification result of the Proverif. Proverif software verifies the experimental results of our scheme. It can be concluded that our scheme can guarantee the security of parameters such as vehicle password ,
,
, and negotiated Key between vehicle and VS server, which cannot be captured by the opponent. All the authentication processes defined are also performed sequentially.
6. Performance analysis
In this part, we analyse the performance of the proposed scheme. We will analyse the consumption of computation, communication and storage from the three aspects. We also compare our scheme with some existing schemes. We implemented the entire authentication scheme on a single desktop device running Windows 7 Professional 64-bit version having an Intel Core i7-3537U processor with a 2.00 GHz clock and 3.7 GB memory. we evaluate the performance of our scheme with C++ under Visual Studio 2019 using the Crypto++ library.
6.1. Computaional cost
In this article, we make represents cost of a multiplication,
representative for a hash operation cost,
represents the cost of XOR operation,
represents the cost of a symmetric encryption,
represent the cost of a symmetric decryption,
represents the cost of a public key encryption,
represents the cost of a public key decrypt,
is the cost of a private key signature and
is the cost of a signature verification. Assuming that the cost is the time required to perform the calculation, then a single operation needs this time, according to (Vasudev et al., Citation2020) we can know,
,
. In the mutual authentication phase of our scheme, OBU used 6h(.), RSU used 6h(.), VS used 4h(.). Because the time required for concatenation and XOR calculations was short, these operations could no longer be considered. Since the initialisation phase and the registration phase can take place earlier than the authentication phase, we also do not consider their overhead. So the total computational time cost in the whole process is:16
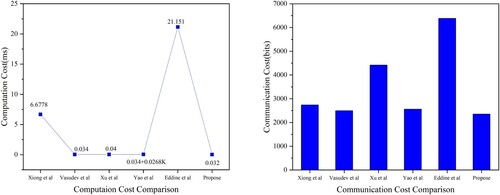
. In short, our scheme is suitable for practical applications because of its low computational overhead. We can see the differences in the calculated costs of the various scenarios in Table . From Figure (a), we can see that our scheme has lower computational consumption than existing schemes and is more suitable for real-time requirements of Internet of vehicle. Although our scheme is similar to that of xu and Vasuade, our security is better than theirs.
Table 3. Comparison of safety performance.
6.2. Communication cost
The hash used by the proposed scheme is the SHA-256 algorithm, with 256 bits, timestamp is 64 bits, and HID is 64 bits, public/private key pair is 256 bits, symmetric encryption or decrypt is 256 bits, Throughout the mutual authentication process, we sent
. The total number of bits is 2357. The communication cost of our agreement is shown in Table . It can be seen from Figure (b) that our scheme has obvious advantages in communication consumption, which is lower than that of the existing scheme.
Table 4. Communication costs in different stage.
6.3. Storage cost
In this part, we will calculate the storage consumption of each vehicle node in the scheme. To determine the overall consumption of each related scheme, we still adopt the following assumptions: the size of identity and random number is 64 bits, the output size of One-way hash function is 256 bits, and Elliptic points are 40 bytes.
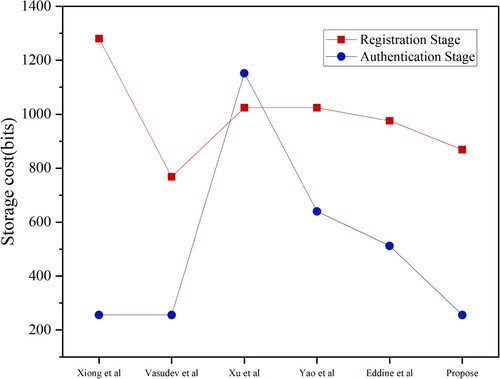
During the registration phase of this scheme, vehicle nodes require 896 bits of storage space, because it needs to store their own public–private key ( 320 bits),
( 64 bits) and smart card
( 512 bits). In the vehicle authentication and key agreement phase, the vehicle node needs to store the session key( 256 bits) negotiated with the VS node. In comparison with other related solutions, this scheme is relatively small in terms of storage consumption, and vehicle nodes do not need to consume too much storage space. We can see the comparison results from Figure .
7. Conclusions and future directions
In this paper, we use the multi-TA model of the Internet of Vehicles and use blockchain to propose a mutual authentication and key agreement scheme, which can be used for the communication between the vehicle and VS to provide better and more timely service for the vehicle. We use these lightweight operations Xor, hash to implement mutual authentication between entities, this allows our scheme to have lower consumption, but also easier to meet the real-time requirements of the Internet of Vehicles. The blockchain composed of TA nodes can not only facilitate the cross-TA authentication of vehicles but also improve the authentication efficiency. In order to ensure the security of vehicle identity information, that is distributed stored in the private chain composed of TA and RSU nodes in each region. It reduces the threat of information leakage brought by centralised storage and the openness of the blockchain itself. Through security analysis and simulation results of Proverif, we show that our authentication scheme is secure, and the consumption of time and communication cost of our protocol is very low. In short, our scheme can meet the real-time requirements of the Internet of Vehicles, and enable fast-moving vehicles to obtain Internet of Vehicles services, which has more practical industrial significance. In the future, we will start from two perspectives of analysing network attacks of Internet of Vehicles and authentication consumption, solving the problem of massive consumption of computation and communication after vehicle passing the first authentication.
Disclosure statement
No potential conflict of interest was reported by the author(s).
References
- Aman, M. N., Javaid, U., & Sikdar, B. (2020). A privacy-preserving and scalable authentication protocol for the internet of vehicles. IEEE Internet of Things Journal, 8(2), 1123–1139. https://doi.org/10.1109/JIoT.6488907
- Ayaz, F., Sheng, Z., Tian, D., & Guan, Y. L. (2020). A Proof-of-Quality-Factor (PoQF)-based blockchain and edge computing for vehicular message dissemination. IEEE Internet of Things Journal, 8(4), 2468–2482. https://doi.org/10.1109/JIoT.6488907
- Basudan, S., Lin, X., & Sankaranarayanan, K. (2017). A privacy-preserving vehicular crowdsensing-based road surface condition monitoring system using fog computing. IEEE Internet of Things Journal, 4(3), 772–782. https://doi.org/10.1109/JIOT.2017.2666783
- Chaudhry, S. A., Naqvi, H., Mahmood, K., Ahmad, H. F., & Khan, M. K. (2017). An improved remote user authentication scheme using elliptic curve cryptography. Wireless Personal Communications, 96(4), 5355–5373. https://doi.org/10.1007/s11277-016-3745-3
- de Cock Buning, M., & de Bruin, R. (2017). Autonomous intelligent cars: Proof that the EPSRC Principles are future-proof. Connection Science, 29(3), 189–199. https://doi.org/10.1080/09540091.2017.1310181
- Eddine, M. S., Ferrag, M. A., Friha, O., & Maglaras, L. (2021). EASBF: An efficient authentication scheme over blockchain for fog computing-enabled internet of vehicles. Journal of Information Security and Applications, 59(3), 102802. https://doi.org/10.1016/j.jisa.2021.102802
- Fromknecht, C., Velicanu, D., & Yakoubov, S. (2014). Certcoin: A namecoin based decentralized authentication system (Tech. Rep. No. 6) (pp. 46–56). Massachusetts Institute of Technology.
- Huang, C. M., Tu, L., & Chou, C. H. (2010). ReWarn: An opportunistic relay scheme for cooperative collision warning in VANET. IEEE International Symposium on Personal.
- Huang, X., Leng, S., Maharjan, S., & Zhang, Y. (2021). Multi-agent deep reinforcement learning for computation offloading and interference coordination in small cell networks. IEEE Transactions on Vehicular Technology, 70(9), 9282–9293. https://doi.org/10.1109/TVT.2021.3096928
- Javaid, U., Aman, M. N., & Sikdar, B. (2020). A scalable protocol for driving trust management in internet of vehicles with blockchain. IEEE Internet of Things Journal, 7(12), 11815–11829. https://doi.org/10.1109/JIoT.6488907
- Jiang, S., Zhu, X., & Wang, L. (2016). An efficient anonymous batch authentication scheme based on HMAC for VANETs. IEEE Transactions on Intelligent Transportation Systems, 17(8), 2193–2204. https://doi.org/10.1109/TITS.2016.2517603
- Jiang, T., Fang, H., & Wang, H. (2019). Blockchain-Based Internet of Vehicles: Distributed Network Architecture and Performance Analysis. IEEE Internet of Things Journal, 6(3), 4640–4649. https://doi.org/10.1109/JIoT.6488907
- Kang, J., Yu, R., Huang, X., Wu, M., Maharjan, S., Xie, S., & Zhang, Y. (2018). Blockchain for secure and efficient data sharing in vehicular edge computing and networks. IEEE Internet of Things Journal, 6(3), 4660–4670. https://doi.org/10.1109/JIoT.6488907
- Lei, A., Cruickshank, H., Cao, Y., Asuquo, P., Ogah, C. P. A., & Sun, Z. (2017). Blockchain-based dynamic key management for heterogeneous intelligent transportation systems. IEEE Internet of Things Journal, 4(6), 1832–1843. https://doi.org/10.1109/JIOT.2017.2740569
- Lei, Z. (2016). Research and implementation of VANETs secure authentication and privacy protection. Anhui University.
- Li, A., Tian, G., Miao, M., & Gong, J. (2021). Blockchain-based cross-user data shared auditing. Connection Science, 5(2021), 1–21. https://doi.org/10.1080/09540091.2021.1956879
- Liang, W., Fan, Y., Li, K. C., Zhang, D., & Gaudiot, J. L. (2020). Secure data storage and recovery in industrial blockchain network environments. IEEE Transactions on Industrial Informatics, 16(10), 6543–6552. https://doi.org/10.1109/TII.9424
- Liang, W., Tang, M., Long, J., Peng, X., Xu, J., & Li, K. C. (2019). A secure fabric blockchain-based data transmission technique for industrial Internet-of-Things. IEEE Transactions on Industrial Informatics, 15(6), 3582–3592. https://doi.org/10.1109/TII.9424
- Liang, W., Xiao, L., Zhang, K., Tang, M., He, D., & Li, K. C. (2021). Data fusion approach for collaborative anomaly intrusion detection in blockchain-based systems. IEEE Internet of Things Journal, PP(99), 1–1. https://doi.org/10.1109/JIOT.2021.3053842
- Liang, W., Zhang, D., Lei, X., Tang, M., Li, K. C., & Zomaya, A. (2020). Circuit copyright blockchain: Blockchain-based homomorphic encryption for IP circuit protection. IEEE Transactions on Emerging Topics in Computing, PP(99), 1–1. https://doi.org/10.1109/TETC.2020.2993032
- Liu, T., Liu, X., Li, X., Amin, R., Liang, W., & Hsieh, M. Y. (2021). RETRACTED ARTICLE: Cloud enabled robust authenticated key agreement scheme for telecare medical information system. Connection Science, 33(4), I–XX. https://doi.org/10.1080/09540091.2021.1901072
- Liu, Z., Japkowicz, N., Wang, R., & Tang, D. (2019). Adaptive learning on mobile network traffic data. Connection Science, 31(2), 185–214. https://doi.org/10.1080/09540091.2018.1512557
- Machardy, Z., Khan, A., Obana, K., & Iwashina, S. (2018). V2X access technologies: Regulation, research, and remaining challenges. IEEE Communications Surveys & Tutorials. https://doi.org/10.1109/COMST.2018.2808444
- Mishra, D., Das, A. K., & Mukhopadhyay, S. (2014). A secure user anonymity-preserving biometric-based multi-server authenticated key agreement scheme using smart cards. Expert Systems with Applications, 41(18), 8129–8143. https://doi.org/10.1016/j.eswa.2014.07.004
- Qiu, T., Liu, X., Li, K., Hu, Q., Sangaiah, A. K., & Chen, N. (2018). Community-aware data propagation with small world feature for internet of vehicles. IEEE Communications Magazine, 56(1), 86–91. https://doi.org/10.1109/MCOM.2018.1700511
- Raya, M., & Hubaux, J. P. (2007). Securing vehicular ad hoc networks. Journal of Computer Security, 15(1), 39–68. https://doi.org/10.3233/JCS-2007-15103
- Vasudev, H., & Das, D. (2018). Secure lightweight data transmission scheme for vehicular Ad Hoc networks. In 2018 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS) (pp. 1–6). IEEE.
- Vasudev, H., Das, D., & Vasilakos, A. V. (2020). Secure message propagation protocols for IoVs communication components. Computers & Electrical Engineering, 82(1), 106555. https://doi.org/10.1016/j.compeleceng.2020.106555
- Vasudev, H., Deshpande, V., Das, D., & Das, S. K. (2020). A lightweight mutual authentication protocol for V2V communication in internet of vehicles. IEEE Transactions on Vehicular Technology, 69(6), 6709–6717. https://doi.org/10.1109/TVT.25
- Wang, B., Chang, Z., Zhou, Z., & Ristaniemi, T. (2018). Reliable and privacy-preserving task recomposition for crowdsensing in vehicular fog computing. In 2018 IEEE 87th vehicular technology conference (VTC Spring) (pp. 1–6). IEEE.
- Wang, C., Huang, R., Shen, J., Liu, J., Vijayakumar, P., & Kumar, N. (2021). A novel lightweight authentication protocol for emergency vehicle avoidance in VANETs. IEEE Internet of Things Journal, PP(99), 1–1. https://doi.org/10.1109/JIOT.2021.3068268
- Wang, C., Shen, J., Lai, J. F., & Liu, J. (2020). B-TSCA: Blockchain assisted trustworthiness scalable computation for V2I authentication in VANETs. IEEE Transactions on Emerging Topics in Computing, PP(99), 1–1. https://doi.org/10.1109/TETC.2020.2978866
- Wang, X., Zeng, P., Patterson, N., Jiang, F., & Doss, R. (2019). An improved authentication scheme for internet of vehicles based on blockchain technology. IEEE Access, 7, 45061–45072. https://doi.org/10.1109/Access.6287639
- Wu, L., Wei, X., Meng, L., Zhao, S., & Wang, H. (2021). Privacy-preserving location-based traffic density monitoring. Connection Science. https://doi.org/10.1080/09540091.2021.1993137
- Xiao, L., Xie, S., Han, D., Liang, W., Guo, J., & Chou, W. K. (2021). A lightweight authentication scheme for telecare medical information system. Connection Science, 2021(8), 1–17. https://doi.org/10.1080/09540091.2021.2017853
- Xiao, Y., & Zhu, C. (2017). Vehicular fog computing: Vision and challenges. In 2017 IEEE International Conference on Pervasive Computing and Communications Workshops (Percom Workshops) (pp. 6–9). IEEE.
- Xiong, L., Xiong, Y., Jian, M., & Wang, W. (2012). An efficient and security dynamic identity based authentication protocol for multi-server architecture using smart cards. Journal of Network & Computer Applications, 35(2), 763–769. https://doi.org/10.1016/j.jnca.2011.11.009
- Xu, Z., Liang, W., Li, K. C., Xu, J., & Jin, H. (2021). A blockchain-based roadside unit-assisted authentication and key agreement protocol for internet of vehicles. Journal of Parallel and Distributed Computing, 149(6), 29–39. https://doi.org/10.1016/j.jpdc.2020.11.003
- Yahiatene, Y., & Rachedi, A. (2018). Towards a blockchain and software-defined vehicular networks approaches to secure vehicular social network. In 2018 IEEE Conference on Standards for Communications and Networking (CSCN) (pp. 1–7). IEEE.
- Yang, M., Zhu, T., Liang, K., Zhou, W., & Deng, R. H. (2019). A blockchain-based location privacy-preserving crowdsensing system. Future Generation Computer Systems, 94(1), 408–418. https://doi.org/10.1016/j.future.2018.11.046
- Yao, Y., Chang, X., Misc, J., Misc, V. B., & Li, L. (2019). BLA: Blockchain-assisted lightweight anonymous authentication for distributed vehicular fog services. IEEE Internet of Things Journal, 1–1. https://doi.org/10.1109/JIOT.2019.2892009
- Zhang, K., Cao, J., & Zhang, Y. (2021). Adaptive digital twin and multi-agent deep reinforcement learning for vehicular edge computing and networks. IEEE Transactions on Industrial Informatics, PP(99), 1–1. https://doi.org/10.1109/TII.2021.3088407
- Zhao, H., Yao, L., Zeng, Z., Li, D., Xie, J., Zhu, W., & Tang, J. (2021). An edge streaming data processing framework for autonomous driving. Connection Science, 33(2), 173–200. https://doi.org/10.1080/09540091.2020.1782840
- Zheng, Z., Zhou, Y., Sun, Y., Wang, Z., Liu, B., & Li, K. (2021). Applications of federated learning in smart cities: Recent advances, taxonomy, and open challenges. Connection Science, 12(1), 1–28. https://doi.org/10.1080/09540091.2021.1936455