?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.Abstract
Due to existing blockchain systems concentrate mainly on privacy protection but lack payment statistics and supervision, we propose a blockchain-based transaction system with payment statistics and supervision. In the system, a payer uses a homomorphic encryption scheme to protect payment amounts. After the transaction is recorded in the blockchain, not only the payee can decrypt the payment amounts and use for future payment, but also the payer can even decrypt it and use for payment statistics. Besides, two supervisors can independently decrypt all users' payment amounts to master the whole economic dynamism and detect illegal transactions. Comparing with existing schemes, our homomorphic scheme only increases a little length of ciphertext, but supports payment amounts decryption by the payer, an additional two receivers. Finally, analyses show that our system is extremely efficient.
1. Introduction
Blockchain (Nakamoto, Citation2019) has attracted great attention due to its characteristic of transparency, immutability and distribution, etc. It has a wide range of application prospects. In financial markets, the transparency of blockchain enables any user to conduct relatively fair transactions on the blockchain, which can reduce economic losses caused by the information asymmetry between buyers and sellers. In control and information systems, the immutability of blockchain permanently records data accesses or modifications by any user. Therefore the responsibility of each user is straightforward. In the military, the distributed blockchain can hide the command centre, and any damage to the partial system will not affect the stable operation of the whole systemThe Russian State Tretyakov Art Museum has established “My Triakov” as a fundraising initiative, utilising blockchain technology to allow “the entire globe” to get to be a supporter of the museum’s digital building and a collection of the gallery’s works. In September 2021, the State Hermitage Museum, one of the world’s four largest institutions, will organise an NFTs sale of five world-famous artworks, alongside the Louvre in Paris, the British Museums in London and the Museum of art in New York. This greatly improves the extent to which museums, especially digital collections, can make money from work of art (Wang, Li, et al., Citation2021). Blockchain is typically used to allow actual members of a certain group to share and trade sensitive information. Permissioned blockchains are referred to as such because exterior users can view or engage in private blockchains unless they have been given the authority. When users adopt a commercial blockchain network, they help to maintain the network’s decentralised nature by storing a shared ledger and collaborating to reach a consensus on modifications. Besides, blockchain technology has been widely applied to the Internet of Things, the medical, intellectual property, logistics, etc.
The Bitcoin (Nakamoto, Citation2019) and Ethereum (Wood, Citation2014) blockchain systems are the most successful application. In financial systems, privacy protection is very crucial. Plaintext transaction has many disadvantages. The difference among Ethereum and Bitcoin would be that Bitcoin is merely a currency, but Ethereum is a digital ledger that is being used by businesses to create new initiatives. Both Bitcoin and Ethereum are based on “blockchain” technologies, but Ethereum’s is significantly more reliable. For example, the disclosure of a user’s wealth will endanger his life and property safety; disclosure of the company’s economic status will lead to malicious competition; leakage of the country’s economic strength, will lead to a financial crisis. For museums, digital cultural relics exhibition lacks a complete authorisation verification mechanism, and these digital materials will be arbitrarily spread or even forged (Wang, Chen, et al., Citation2021; Zhaofeng et al., Citation2019). Therefore, it is necessary to protect transaction privacy. Monero (Noether, Citation2015; Noether & Mackenzie, Citation2016), Zerocoin (Miers et al., Citation2013) and Zerocash (Ben-Sasson et al., Citation2014) are typical blockchain systems with good privacy protection. The Monero system was originally built on CryptoNote, which hides the target and source of payment interactions via ring signatures and single-time keys. The strategy is dependent on confidential exchanges which are utilised on Bitcoin’s Elements side-chain, but it also enables their own use in ring signatures. Zerocoin is a Bitcoin-based cryptography option that allows for entirely anonymous monetary transactions. This approach is based on normal cryptography principles and therefore does not make any new providing valuable and otherwise alter Bitcoin’s security architecture. Zerocash is a derivative of Bitcoin that can be used at an equal scale. As a basis of its enhanced performance and efficiency, Zerocash allows for the complete replacement of standard Bitcoin transactions with untraceable equivalents.
However, privacy protection in financial transactions is not enough for economic development, as privacy protection creates a living space for corruption, illegal financing and illegal transfer abroad. Therefore, it is necessary to supervise each transaction under the premise of privacy protection. All transactions are recorded in the immutable blockchain, allowing regulators to check each transaction for discovering illegal transactions and other financial activities. In addition, the blockchain system can directly reject illegal transfers abroad, which is conducive to improving the stability of finances.
By embedding trapdoors to the Monero, Zerocoin and Zerocash systems, the purpose of supervisory can be fulfilled. For example, traceable ring signatures (Feng et al., Citation2020; Fujisaki & Suzuki, Citation2007) enabled the supervisor to trace the true signer. All payers need to count the payment amounts, which is a huge application demand in financial activities. For example, individuals, all companies, need to make periodical financial statistics of payment amounts and use them to plan their future payment activities; The state also needs to count every financial activity and plan its development direction. However, existing privacy-protected transaction systems, such as Monero, Zerocoin and Zerocash, only enabled the payee to decrypt his denomination, not the payer. As a result, neither individual users nor companies can decrypt payment amounts from the blockchain and conduct financial statistics, but only a plaintext backup of the transaction locally. However, this kind of plaintext backup has a high risk of data theft and tampering.
Therefore, according to existing blockchain systems only concentrate on privacy protection but lack payment statistics and supervision, we propose a transaction system with payment statistics and supervision based on blockchain.
Contributions: We first contribute a transaction system model. Then, we present efficient concrete construction. In the concrete construction, a special homomorphic encryption scheme is the main innovation of this paper. It enabled a payer, a payee and two supervisors to decrypt payment amounts independently. Finally, we prove strictly the security of the homomorphic encryption scheme and compare it with related schemes. The homomorphic encryption architecture reduces the computational cost, allowing it to function with smart appliances with limited processing capacity. It guarantees that information will never ever be relocated or exposed in cleartext. Analyses show that our transaction system and homomorphic encryption scheme are efficient.
2. Related work
Bitcoin (Nakamoto, Citation2019) is a peer-to-peer electronic cash that enables internet operations would be sent immediately between parties without the need of a bureaucratic commercial bank. By using the proof-of-work consensus mechanism and network timestamps, it prevents double-spending without using a trusted third party. Etherum (Wood, Citation2014) has demonstrated its strong practicality through a larger quantity of work. Each work can be seen as a simple application on a decentralised, but singleton, compute resource. However, Bitcoin and Ethereum use plaintext to transact, which reveal the private information of each user and lead hackers to conduct statistical analysis attacks on it.
Maxwell (Citation2013) introduced Coinjoin, a numerous input and multiple-output transaction mechanism, to handle the issue of anonymity. However, it requires interaction between the various participants, which increases the probability of information leakage. Besides, each user does not trust each other, and the interaction is extremely difficult. Coinjoin is a form of bitcoin exchange that improves anonymity by eliminating the presumption of common-input ownership. CoinShuffle is a distributed Bitcoin blending system described by Ruffing et al. (Citation2014), which enables payers and payees to conduct Bitcoin transactions in a fully anonymied fashion. CoinShuffle is based on the Dissent accountability anonymised group communication system and has numerous benefits over the Bitcoin blending techniques that came before it. It does not require any trusted third party and it is perfectly compatible with the current Bitcoin blockchain system. However, it is vulnerable to a variety of denial of service attacks as it needs all participants online all the time.
Bissias et al. (Citation2014) developed Xim, a two-party blending system that works with Bitcoin and other virtual payments. This can withstand a variety of assaults, including Sybil, DOS, man-in-the-middle and length of time inferences assaults. It’s the first decentralised network to combat several attacks and timing-based inferences assault all at the same time. It offers a decentralised method for discreetly locating mixing mates through blockchain marketing. Furthermore, it’s trying to obfuscate method of blending decreases the consequences of Sybil-based denial-of-service assaults, and it raises attackers expenses directly proportional to the number of participation. CoinParty is a distributed mixing system for Bitcoin suggested by Ziegeldorf et al. (Citation2015), which is built on a mixture of decryption mixnets and threshold cryptosystems. Monero (Noether, Citation2015; Noether & Mackenzie, Citation2016) uses ring signature scheme to hide the payer, and uses one-time keys to hide the payee in transactions. Besides, it uses the technique of a commitment scheme or homomorphic encryption scheme to rawhide the amount of a transaction. Zerocoin (Miers et al., Citation2013)/Zerocash (Ben-Sasson et al., Citation2014) are full-featured ledger-based cryptocurrencies that provide high privacy protections. It hides the sender, beneficiary and value in an online transaction using zero-knowledge Succinct Non-interactive ARguments of Knowledge (zk-SNARKs) (Ben-Sasson et al., Citation2014; Groth, Citation2016).
However, all the above schemes only consider privacy protection. The supervision of the blockchain system includes transaction traceability mechanisms (Koshy et al., Citation2014 Reid & Harrigan, Citation2013;), address clustering mechanisms (Meiklejohn et al., Citation2013; Zhao, Citation2014), certificate management mechanisms (Androulaki et al., Citation2018; Moser & Narayanan, Citation2019; Wust et al., Citation2018) and trapdoor technologies. We think that trapdoor is a good technology to achieve fine-grained supervision as it can trace each transaction in the system. Therefore, we will embed some trapdoors in our homomorphic encryption scheme to achieve fine-grained supervision. Besides, our homomorphic encryption scheme supports the sender/payer to decrypt his payment amounts, which is a main and special innovation of this paper.
3. Transaction system
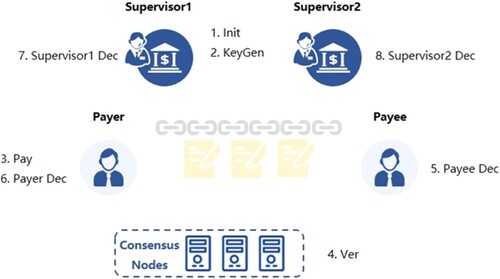
As shown in Figure , there are four kinds of participants, i.e. a payer, a payee, consensus nodes (or miners) and two independent supervisors, in the blockchain-based transaction system. In generic construction, we will employ a homomorphic encryption scheme, a non-interactive zero-knowledge proof protocol and a digital signature. The main innovation of our transaction system is a homomorphic encryption scheme, which enables the payer, the payee and two supervisors to decrypt the ciphertext payment amounts independently. The transaction system consists of eight procedures, Init, KeyGen, Pay, Ver, PayeeDec, PayerDec, Supervisor1Dec, Supervisor2Dec, for initialising the system, generating keys, paying, verifying, decrypting by the payee, payer and two supervisors, respectively. Private keys are often used to validate transactions and show that a blockchain address belongs to the owner. You can handle cryptocurrency transactions using a public key. It’s a private key that’s linked with a cryptography algorithm. While anybody can submit transaction to the public key, you’ll need to have the secret key to unlock them and show because you own the bitcoin that was acquired. Ciphertext is information that has been encoded using a data encryption. Moreover, a zero-knowledge proof, also known as a zero-knowledge protocol, is a methodology in cryptography through which one participant can establish to some other entity that a particular statement is accurate without providing any further information other than the premise that the argument is correct.
Formally, for a fixed security parameter, these procedures work as follows:
Init: The procedure is run by one of the supervisors. It takes as input a security parameter
. It returns the system parameters
.
KeyGen: The procedure is run by the payer, the payee and two supervisors. It takes as input the system parameters
. It returns a private key and a public key
Thus the key pairs of the payer, the payee and two supervisors are
,
,
,
, respectively.
Pay: The payment procedure includes three steps, i.e. the homomorphic encryption scheme , the non-interactive zero-knowledge proof
, and the digital signature
. This procedure is run by the payer.
HEnc: It takes as input the system parameters
, payment amounts
, his private key
, the public keys
of the payee and two supervisors. It outputs a homomorphic ciphertext
In the same way, it takes as input the system parameters , payment amounts
, his private key
, the public keys
of himself and two supervisors. It outputs a homomorphic ciphertext
The payment amount
is the change for the payer. Note that as the change
is the payer pay to himself, so both his private key
and public key
are embedded in the ciphertext.
Obviously, one can encrypt multiple payment amounts for other payees as follows
are public keys of other payees.
Similarly, the unspent amounts of the payer read from the blockchain has the following two kinds of expressions
The amount
spent by user 0 whose private key is
, and
is a change that the payer spends to himself. As
is in both ciphertexts
, the payer can spend
validly by using his corresponding private key
.
NIZK: The non-interactive zero-knowledge proof
includes two protocols, i.e. the Sigma protocol (Damgård, Citation2000) and the Bulletproofs (Bünz et al., Citation2018). The use of the customised dedicated hash algorithm and the sigma protocol to conceal the transactions by observing it from the public in the system tends to provide the rigid distance of deterministic public random value to determine the classified information transaction of this Non-Interactive Zero Knowledge (NIZK) confirmation. In the bulletproofs protocol, it was utilised to create a linear logarithmic trustless configuration with a small proofing dimension. Using the ZKP argument, it creates a proof that is monotonically continuous and has a rapid confirmation time period to speed up the process for different proof systems.
The Sigma protocol is used to prove that the sum of the unspent ciphertext amounts is equal to the sum of the ciphertext amounts
that need to be paid. The Sigma protocol takes as input
, and returns proof data,
This equation is a complete expression, which includes the following two subcases. If
or
, then the above equation can be reduced as follows
It means the payer only intends to spend the unspent amounts
or
.
The Bulletproofs protocol is used to prove that all ciphertext amounts that need to be paid are positive
Sign: It takes as input all the above data
and his private key
, and returns a signature
Ver: The verification procedure includes signature verification , Sigma verification
, and Bulletproofs verification
. This procedure is run by consensus nodes (or miners) of the blockchain system.
takes as input the system parameters
, all the above data
, the signature
, the corresponding public key
, and returns a judgment
and
take as input the proof data and returns a judgment respectively
If all output is True and no double-spending, then accept and record in the blockchain using a consensus mechanism, such as Byzantine fault-tolerant (Miller et al., Citation2016), etc. Deficiency of the Byzantine Tolerance refers to a decentralised channel’s potential to access consensus on the same quantity although some participating nodes refuse to reply or answer with inaccurate information.
PayeeDec: The procedure is run by the payee. It takes as input the system parameters
, his private key
, the public keys of the payee and two supervisors
,
,
, the homomorphic ciphertext
. It outputs an amount
Similarly, the payer can decrypt his change
PayerDec: The procedure is run by the payer. It takes as input the system parameters
, his private key
, the public keys of the payer and two supervisors
,
,
, the homomorphic ciphertext
. It outputs an amount
Similarly, the payer can decrypt the other amounts
We believe that the payer can decrypt his payment ciphertext is one of the main contributions of this paper. Payment statistics are one of the most important functions in financial activities, as each individual, our society and our country need to record payment amounts, summarise payment activities and use them for planning future payment activities.
Supervisor1Dec: The procedure is run by the first supervisor. It takes as input the system parameters
, his private key
, the public key of the other supervisor
, the homomorphic ciphertext
. It outputs an amount
Similarly, he can decrypt the other amounts
Supervisor2Dec: The procedure is run by the second supervisor. It takes as input the system parameters
, his private key
, the public key of the other supervisor
, the homomorphic ciphertext
. It outputs an amount
Similarly, he can decrypt the other amounts
Therefore, these two supervisors can independently decrypt all users’ payments to master the whole economic dynamism and detect illegal transactions.
4. Concrete construction
4.1. Preliminaries
In the concrete construction of the transaction system, we will use the Bulletproofs, and the digital signature scheme in the black-box model, and we omit their introduction. The employment of a black box approach in the cryptanalysis of homomorphic encryption algorithms might be beneficial. Bijective morphisms can indeed be expected to be isotropic instantly, which is a major feature of black box algebra. In computational theory, it’s an ideal context for randomised algorithms are used to solve permutations and matrices group problems. We briefly review some related important cryptography concepts including bilinear groups (Boneh & Boyen, Citation2008) and difficult problems. In recent times, bilinear groups of composite order have been employed to tackle a variety of cryptographic challenges. While the minority choice hypothesis is a valuable tool for creating secure protocols, it poses considerable challenges when it comes to putting them into reality.
4.1.1. Bilinear groups
The payer, the payee and two supervisors need to decrypt the payment amounts in the system, which can be implemented using a bilinear map. The discrete logarithm issue on that category of elliptic curve cryptography over a discrete space can be transported to the discrete logarithm on a narrower sample space, where a sub-exponential index math approach can be utilised. We briefly review the bilinear maps and groups, in the notation of (Boneh & Boyen, Citation2008):
Let
be a security parameter of our encryption system, and
is a large prime.
,
and
are three cyclic groups of prime order
.
is a generator of
and
is a generator of
;
is a bilinear pairing
, i.e. a map satisfying the following properties:
− Bilinearity:
,
,
,
− Non-degeneracy:
and is thus a generator of
.
All operations on groups and bilinear maps can be achieved in polynomial-time. Formally, one defines a bilinear group generation algorithm that takes as input a security parameter
and outputs the description of groups
and a bilinear map
. We then require the existence of probabilistic polynomial-time algorithms (in
) for computing the group operation in
and the bilinear map
. If
, we call the bilinear map is a symmetry bilinear map. If
, we call it asymmetric bilinear maps. In this paper, our scheme rely on the symmetrical bilinear group.
4.1.2. Difficult problems
The complexity of the Bilinear Diffie-Hellman Problem, that is an augmentation of the three challenges outlined below for a multiplicative group , provides the basis for our homomorphic encryption approach. To establish an effective cryptographic algorithm, a variety of Diffie-Hellman-type complexity considerations in bilinear groups were applied. The security of newer Weil-pairing-based crypto algorithms must be established.
Computational Diffie-Hellman (CDH) Problem: Given three group elements , where
, find an element
such that the following equation holds
Bilinear Diffie-Hellman (BDH) Problem: Given four group elements , where
, find an element
such that the following equation holds
Decision Bilinear Diffie-Hellman (DBDH) Problem: Given four group elements , where
, and an element
decide whether or not the following equation holds
If it holds, then the quintuple
is a valid DBDH tuple.
Gap Bilinear Diffie-Hellman (GBDH)Problem: Solve a given instance, , of the BDH problem with the help of a DBDH oracle that is able to decide whether or not a tuple
is a valid DBDH tuple. A DBDH group is one in which group elements are difficult to analyse but simple to confirm. It is clearly possible to create a group in which Decision Diffie-Hellman is manifestly simple, but really what evidence do we have indicating Computational Diffie-Hellman is difficult in these kinds of groups.
4.2. Concrete scheme
Formally, a concrete construction of the transaction system is as follows:
Init: Let be symmetric bilinear maps,
.
is a generator of
, and
is a generator of
. The prime order of
is
. A hash function
maps a data of any length to
,
. The system parameters are
KeyGen: The private keys and public keys of the payer, the payee and two supervisors are as follows,
Pay: The payment procedure includes three steps, i.e. the homomorphic encryption scheme , the non-interactive zero-knowledge proof
, and the digital signature
.
HEnc: It takes as input the system parameters
, a random element
, payment amounts
, his private key
, the public keys
of the payee and two supervisors, and computes as follows:
The unspent amounts of the payer read from the blockchain has the following two expressions
The unspent amounts
spent by user 0 whose private key is
, and the unspent amount
is a change that the payer spends to himself.
NIZK: The non-interactive zero-knowledge proof
includes two protocols, i.e. the Sigma protocol and the Bulletproofs.
The Sigma protocol is used to prove that the sum of the unspent ciphertext amounts is equal to the sum of the ciphertext amounts
that need to be paid. More specifically, the payer needs to prove that
so he needs to prove that he knows a witness
, where
The value
is equivalent to the following equation due to the Diffie-Hellman key exchange method
As the payer knows
,
,
,
,
,
,
,
,
,
,
, so he really knows the witness
. Therefore, the payer can prove the following discrete logarithm equation by using the Sigma protocol
The Bulletproofs protocol is used to prove that all ciphertext amounts
that need to be paid are positive.
Sign: The signature scheme can use any secure scheme such as ECDSA (Johnson et al., Citation2001), BLS scheme (Boneh et al., Citation2001), etc. It takes as input all the above data
and his private key
, and returns a signature
Ver: The verification procedure includes signature verification , Sigma verification
and Bulletproofs verification
. They are the same as in the system model and can be used in the black-box model. If all procedures, i.e. signature verification, Sigma verification and Bulletproofs verification, output valid and no double-spending, then accept and record in the blockchain, else reject.
PayeeDec: It takes as input the system parameters , his private key
, the public keys of the payer and two supervisors
, the homomorphic ciphertext
, and computes as follows:
As the payee knows the payment amounts
, he can verify
. If holds, then accept, else reject. Besides, as
is not a big random element in
, he can search a value
such that
to find it. In subsequent description, these two methods will be used frequently and we will omit them.
Similarly, the payer can decrypt his change
PayerDec: It takes as input the system parameters , his private key
, the public keys of the payee and two supervisors
, the homomorphic ciphertext
, and computes as follows:
Similarly, the payer can decrypt the other amounts
Therefore, the payer can decrypt his payment to summarise payment activities and use them for planning future payment activities.
Supervisor1Dec: It takes as input the system parameters , his private key
, the public key of the other supervisor
, the homomorphic ciphertext
, and computes as follows:
Similarly, he can decrypt the other amounts
Supervisor2Dec: It takes as input the system parameters , his private key
, the public key of the other supervisor
, the homomorphic ciphertext
, and computes as follows:
Similarly, he can decrypt the other amounts
Therefore, these two supervisors can independently decrypt all users’ payments to master the whole economic dynamism and detect illegal transactions.
Theorem 1.
In the PayeeDec procedure, the payee’s and the payer’s decryption is consistent.
The payee’s decryption is as follows
The payer’s decryption is as follows
Theorem 2.
The payer’s decryption is consistent.
Theorem 3.
The first supervisor’s decryption is consistent.
Theorem 4.
The second supervisor’s decryption is consistent.
5 Security
For the ciphertext where
an adversary can launch an attack from the angle of the payer, the payee and the two supervisors. However, the decryption operations of the payer and the payee are equivalent, and the decryption operations of the two supervisors are also equivalent. Therefore, we need to prove the following two theorems.
Theorem 5.
Suppose the hash function is a random oracle. From the angle of the payer or the payee, if the CDH problem is hard, then our homomorphic encryption scheme is provably secure in the classic IND-CPA security model with reduction loss
.
Theorem 6.
Suppose the hash function is a random oracle. From the angle of one of the two supervisors, if the DBDH problem is hard, then our homomorphic encryption scheme is provably secure in the classic IND-CPA security model with reduction loss
.
If the adversary attack from the angle of one of the two supervisors, then is useless, and the
is a random element in
. Therefore, the ciphertext can be reduced as follows
Therefore, theorem 6 is a bit easier than theorem 5, so we prove theorem 6 first in the classic security model, and prove theorem 5 s.
5.1. Security proof
Suppose there exists an algebra adversary who can break the above homomorphic encryption scheme from the angle of one of the two supervisors in the IND-CPA security model, in time
with non-negligible advantage
. We can construct a simulator
to solve the DBDH problem. Given as input a problem instance
, the simulator
controls the random oracle
, runs the algebra adversary
, and computes as follows.
Setup. Let system parameter be ,
and
be the random oracle controlled by the simulator
. The simulator
sets the public key as
The public key is available from the problem instance.
Challenge. The algebra adversary outputs two amounts
to be challenged. The simulator
chooses a random coin
, a random element
, and sets the challenge ciphertext
as
where
and
is from the problem instance. Let
. If
Then, the challenge ciphertext
is
Therefore, the challenge ciphertext
is a correct ciphertext from the point of view of the adversary.
Guess. The algebra adversary outputs a guess
of
. The simulator outputs true if
. Otherwise, false.
This completes the simulation and the solution. The advantage of solving the DBDH problem is
The reduction loss is 2. Let
denote the time cost of the simulation. We have
. Therefore, simulator
will solve the DBDH problem with
. This completes the proof of the theorem 6.
As shown in Table , Suppose there exists an algebra adversary who can break the above encryption scheme in the IND-CPA security model, in time
with non-negligible advantage
. We can construct a simulator
to solve the CDH problem. Given as input a problem instance
, the simulator
controls the random oracle
, runs the algebra adversary
, and works as follows.
Table 1. Theoretical comparison.
Setup. Let the system parameter be ,
and
be the random oracle controlled by the simulator
. The simulator
randomly chooses
and sets the public key as
where
and
. The public key can be computed from the problem instance
and the chosen parameters
.
Hash-Query. The simulator prepares a Hash-Query list to record all queries and responses. In the beginning, the Hash-Query list is empty. Let the
-th hash query be
If
is a new hash query, then the simulator
randomly chooses
and sets
. The simulator
responds to this query with
and adds
to the Hash-Query list. If
is already in the Hash-Query list, the simulator
responds to this query with the existed random value in the Hash-Query list.
Challenge. The algebra adversary outputs two amounts
to be challenged. The simulator
randomly chooses a random element
, five group elements
, and a random element
. He sets the challenge ciphertext
as
The challenge ciphertext can be seen as an encryption of the message
using the random coin
if
Then, the challenge ciphertext
is
Therefore, if there is no hash query on
to the random oracle
, then the challenge ciphertext
is a correct ciphertext from the point of view of the adversary.
Guess. The algebra adversary outputs a guess or
. In the above simulation, the challenge hash query is defined as.
As
are all in the Hash-Query list, where each query
. If
does not satisfy this structure, we can delete it. As the following equation holds
Then, the following equation holds
It is equivalent to the following equation
Therefore, the simulator
can find the query
from the Hash-Query list satisfying the above equation. He uses it as the solution to the CDH problem instance. Therefore, there is no reduction loss in the above security simulation. In other words, if the algebra adversary
can break the encryption scheme in polynomial-time
with non-negligible probability
, then we can construct a simulator
to break the CDH problem instance in polynomial-time
with the same probability
, where
is the time cost of the simulation. This completes the proof of the theorem 5.
6. Performance and comparison
Our homomorphic encryption scheme is extending from Diament et al.’s (Citation2004) dual receiver public encryption scheme, which has dual receivers. We add an extra receiver in their scheme and achieve the property of homomorphism. Besides, our scheme has a special characteristic that it supports both the payer and the sender to decrypt a message.
The Diament et al.’s (Citation2004) scheme can be converted to a homomorphic encryption scheme easily, and we can make a detailed comparison with it. In this paper, the payer corresponds to the sender, the payee corresponds to the receiver 1, the supervisor 1 corresponds to the receiver 2, and the supervisor 2 corresponds to the receiver 3.
In table 5.1, the second to the fourth columns show the size of the private key, the public key and the ciphertext. The fifth to the sixth columns show the computation complexity of encryption and decryption algorithms. The seventh to the eighth columns show the computational hard problems and reduction loss respectively.
The bilinear maps computational complexity denotes as , exponent operation and additive operation on group
denotes as
, respectively. We omitted the computation complexity of the hash function.
For the receiver 3,4 the length of the private key and public key, and decryption complexity is the same. Although the length of the private key and public key of the sender and receiver 1 in our scheme is twice over Diament’s scheme, the sender can decrypt it in our scheme. Besides, computational hard problems of our scheme are CDH and DBDH, where the DBDH problem is a bit harder than the BDH problem, and the CDH problem is a standard and is one of the most widely accepted hard problems. Furthermore, the reduction loss of Diament’s scheme is while the reduction loss of our scheme is only 1 and 2 respectively, which is very tight. More specially, with a fixed security level, the exponent of Diament’s scheme should
bits longer than our scheme. In other words, with a fixed exponent of the elliptic curve group, our scheme is more secure than Diament’s scheme for
-bits. Fully homomorphic encryption is also too leisure to be practicable. Fully homomorphic encryption is still a relatively new technology for data protection and usefulness. However, it’s an intriguing idea, and that we’re sure to see quicker variants that may be used in a number of scenarios.
Platform: Centos7.7 with kernel 3.10.0-1062.el7, @2.50 GHz, x86_64, 192GB RAM. We use SHA256 as the concrete construction of the hash function, and select the Type A elliptic curve in jpbc library. The exponent of the elliptic curve group in our encryption scheme is 160 bits, and the length of an elliptic curve group member is 512 bits. CentOS is a Linux distribution that offers a neighbourhood, open and free computing environment that is operationally consistent including its original source. Software archives contain latest version of the software than those included in the standard distribution.
As is shown in Table , the encryption time of the sender(payer) and the decryption time of the receiver 1 and 2 (payee and supervisor) are 30.61, 17.42 and 17.43 ms, respectively. The encryption time of the sender(payer) and the decryption time of the sender (payer), receiver 1,2,3 (payee, supervisor 1 and supervisor 2) is 57.05, 38.33, 38.34 ms, 24.85 and 24.83 ms, respectively. Although the encryption and decryption time of our scheme is a bit longer than Diament’s scheme, our scheme supports payment amounts decryption by the sender (payer), an additional receiver and tight security reduction loss.
Table 2. Performance comparison.
7. Conclusion
We propose a blockchain-based transaction system with payment statistics and supervision. We use a special homomorphic encryption scheme to protect the privacy of payment while the payer, the payee and two supervisors can decrypt it independently. We believe that the payer can decrypt it and use it for payment statistics is of great importance in financial statistics. Besides, the two supervisors can decrypt it independently so that they can master the whole economic dynamism and detect illegal transactions, which is also important in financial statistics.
We show that if the DBDH issue is difficult, our homomorphic encryption technique is secure and efficient in the conventional IND-CPA security framework with reduction loss L = 2 from the perspective of one of the two supervisors. If the CDH problem is difficult, our homomorphic encryption approach is highly robust in the conventional IND-CPA security model without even any reduction loss in the view of payer or payee’s perspective. Finally, by comparing with Diament’s scheme, our homomorphic scheme only increases a little length of ciphertext, but supports payment amounts decryption by the payer, an additional receiver and tight security reduction loss.
Disclosure statement
No potential conflict of interest was reported by the author(s).
References
- Androulaki, E., Barger, A., Bortnikov, V., Cachin, C., Christidis, K., De Caro, A., Enyeart, D., Ferris, C., Laventman, G., Manevich, Y., Muralidharan, S., Murthy, C., Nguyen, B., Sethi, M., Singh, G., Smith, K., Sorniotti, A., Stathakopoulou, C., Vukolic, M., Cocco, S. W., & Yellick, J. (2018). Hyperledger fabric: A distributed operating system for permissioned blockchains. EuroSys, 30, 1–30, 15.
- Ben-Sasson, E., Chiesa, A., Tromer, E., & Virza, M. (2014). Succinct non-Interactive zero Knowledge for a von Neumann Architecture. USENIX Security Symposium (pp. 781–796).
- Bissias, D. D., Ozisik, A. P., Levine, B. N., Liberatore, M. (2014). Sybil-resistant mixing for bitcoin. WPES (pp. 149–158).
- Boneh, D., & Boyen, X. (2008). Short signatures without random oracles and the SDH assumption in bilinear groups. Journal of Cryptology, 21(2), 149–177. https://doi.org/10.1007/s00145-007-9005-7
- Boneh, D., Lynn, B., & Shacham, H. (2001). Short signatures from the Weil pairing. ASIACRYPT (pp. 514–532).
- Bünz, B., Bootle, J., Boneh, D., Poelstra, A., Wuille, P., & Maxwell, G. (2018). Bulletproofs: Short proofs for confidential transactions and more. IEEE Symposium on Security and Privacy (pp. 315–334).
- Damgård, I. (2000). Efficient concurrent zero-knowledge in the auxiliary string model. EUROCRYPT (pp. 418–430).
- Diament, T., Lee, H. K., Keromytis, A. D., & Yung, M. (2004). The dual receiver cryptosystem and its applications. CCS (pp. 330–343).
- Feng, H., Liu, J., Wu, Q., & Li, Y. (2020). Traceable ring signatures with post-quantum Security. CT-RSA (pp. 442–468).
- Fujisaki, E., & Suzuki, K. (2007). Traceable ring signature. Public Key Cryptography (pp. 181–200).
- Groth, J. (2016). On the size of pairing-based non-interactive arguments. EUROCRYPT (2, pp. 305–326).
- Johnson, D., Menezes, A., & Vanstone, S. (2001). The elliptic curve digital signature algorithm (ecdsa). International Journal of Information Security, 1(1), 36–63. https://doi.org/10.1007/s102070100002
- Koshy, P., Koshy, D., & McDaniel, P. D. (2014). An analysis of anonymity in bitcoin using P2P network traffic. Financial Cryptography (pp. 469–485).
- Maxwell G. (2013). Coinjoin: Bitcoin privacy for the real world. https://bitcointalk.org/index.php
- Meiklejohn, S., Pomarole, M., Jordan, G., Levchenko, K., McCoy, D., Voelker, G. M., & Savage, S. (2013). A fistful of bitcoins: Characterizing payments among men with no names. Internet Measurement Conference (pp. 127–140).
- Miers, I., Garman, C., Green, M., & Rubin, A. D. (2013). Zerocoin: Anonymous distributed e-cash from bitcoin. IEEE Symposium on Security and Privacy (pp. 397–411).
- Miller, A., Xia, Y., Croman, K., Shi, E., & Song, D. (2016). The honey badger of BFT protocols. CCS (pp. 31–42).
- Moser, M., & Narayanan, A. (2019). Effective cryptocurrency regulation through blacklisting. Preprint.
- Nakamoto, S. (2019). “Bitcoin: A peer-to-peer electronic cash system”.
- Noether, S. (2015). Ring signature confidential transactions for monero. IACR Cryptol. EPrint Arch, 2015, 1098.
- Noether, S., & Mackenzie, A. (2016). Ring confidential transactions. Ledger, 1, 1–18. https://doi.org/10.5195/ledger.2016.34
- Reid, F., & Harrigan, M. (2011). An analysis of anonymity in the bitcoin system. SocialCom/PASSAT (pp. 1318–1326).
- Ruffing, T., Moreno-Sanchez, P., & Kate, A. (2014). CoinShuffle: Practical decentralized coin mixing for bitcoin. ESORICS (2, pp. 345–364).
- Wang, Q., Li, R., Wang, Q., & Chen, S. (2021). “Non-fungible token (NFT): Overview, evaluation, opportunities and challenges,” arXiv preprint arXiv:2105.07447.
- Wang, Y.-C., Chen, C.-L., & Deng, Y.-Y. (2021). Authorization mechanism based on blockchain technology for protecting museum-digital property rights. Applied Sciences, 11(3), 1085. https://doi.org/10.3390/app11031085
- Wood, G. (2014). Ethereum: A secure decentralised generalised transaction ledger. Ethereum Project Yellow Paper, 151(2014), 1–32.
- Wust, K., Kostiainen, K., Capkun, V., & Capkun, S. (2018). Prcash: Centrally-issued digital currency with privacy and regulation. IACR Cryptol. EPrint Arch, 2018, 412.
- Zhao, C. (2014). Graph-based forensic investigation of bitcoin transactions.
- Zhaofeng, M., Lingyun, W., Xiaochang, W., Zhen, W., & Weizhe, Z. (2019). Blockchain-enabled decentralized trust management and secure usage control of IoT big data. IEEE Internet of Things Journal, 7(5), 4000–4015. https://doi.org/10.1109/JIOT.2019.2960526
- Ziegeldorf, J. H., Grossmann, F., Henze, M., Inden, N., & Wehrle, K. (2015). CoinParty: Secure multi-party mixing of bitcoins. CODASPY (pp. 75–86).