?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.Abstract
Individuals use Vehicular Ad Hoc Networks (VANETs) to secure, reliable communication networks as a viable route of transmission. Platooning uses Inter-Vehicular Communication to supervise a group of vehicles (IVC). The information communicated, especially acceleration, location, and speed, can then be used to respond by longitudinal control legislation. Platoons require help between those vehicles to improve fuel efficiency, security, and various crises associated with driver errors. Despite these advances, the communication network must govern vehicles unprotected from adequate threat vectors, which malicious attacks might exploit. Considering that connected cars between trusts could increase security, whereas all active automobiles can develop and spread legitimate, accurate, and recognized information within the network. So, considering badmouth, this work proposes a unique node centric weight-based trust management algorithm (NC-WTM). By quickly recognising and deleting fraudulent vehicles and their generated messages, the NC-WTM (node-centric weighted trust management) technique improves aggregate platoon security. The NC-WTM beats the robust and privacy-preserving reputation management scheme (RPRep) and the attack resistant trust management scheme (ART) trust designs regarding accuracy, recall, and F-score. Metrics, such as precision results of 78%, recall of 69.3%, F-score of 60.4%, and accuracy of 89%, are achieved and optimised in this trust model.
Abbreviations: VANETs: vehicular ad hoc networks; IVC: inter-vehicular communication; NC-WTM: node-centric weight-based trust management algorithm; WTM: weight-based trust management algorithm; RPRep: robust and privacy-preserving reputation management scheme; ART: attack-resistant trust management scheme; MANET: mobile ad hoc network; DSRC: dedicated short-range communication; WAVE: wireless access in vehicular environment; IVC: inter-vehicular communication; I2V: infrastructure-to-vehicle; V2I: vehicle-to-infrastructure; V2V: vehicle-to-vehicle; TA: trust authority; RSU: road side unit; OBU: on-board unit; GPS: global positioning system; WSN: wireless sensor network; VASNETs: vehicular sensor networks; CCW: cooperative collision warning; BMA: bad mouth attack; TDMA: time division multiple access; GDVAN: greedy detection for VANETs; SMTS: spider monkey time synchronization; SVM: support vector machine; DST: Dempster-Shafer theory of evidence; TA: trust authority; PCA: puzzle-based co-authentication; VLC: visible light communication; NE: Nash equilibrium; RTB: request-to-broadcast; CTB: clear-to-broadcast; RREQ: route request message; RREP: route reply; DDR: data disseminate ratio; Dir: direct trust; IDir: indirect trust; TCE: trust computation error; PDR: packet delivery ratio
1. Introduction
Most of the autonomous nodes in mobile have been possessed by mobile ad hoc network (MANET). They are tranquil to transmit in many directions that can also be changed in their location continuously, which can be configured on their own (Matin & Islam, Citation2012). Since this network does not have the infrastructure, its nodes can connect to Wi-Fi and other mobile networks. The application for MANET is VANET. VANET is a wireless ad hoc network where the movable vehicles will act as mobile nodes. Also it can connect among them through dedicated short range communication (DSRC), and a protocol projected for wireless access in vehicular environment (WAVE) is IEEE 802.11p for inter vehicular communication (IVC). MANETs are networks made up of mobile devices linked together without the assistance of an existing internet infrastructure or any other permanent network station. It is a self-contained network of nodes linked together by wireless connections. Because there is no permanent infrastructure and the nodes are free to migrate, the network architecture in a MANET can vary dynamically and in an unforeseen manner. However, each node has limited transmitting power. In terms of data transfer, VANET is similar to MANET in that it does not require any infrastructure. VANETs are crucial in safe driving, intelligent navigation, and emergency and entertainment applications. This network can establish a connection among infrastructure-to-vehicle (I2V), vehicle-to-infrastructure (V2I), and vehicle-to-vehicle (V2V) communication schemes.
An infrastructure-to-vehicle (I2V) communication architecture allows autonomous and semi-autonomous cars to locate and recognise infrastructure markers, such as lane dividers, stop signs, and structural health information, which may be used to supplement the data acquired by cameras and LIDAR systems to improve the driving experience.
Vehicle-to-infrastructure communication (V2I) refers to the two-way exchange of information by a wireless link between vehicles, trucks, buses and traffic lights, lane markings, and other smart road equipment.
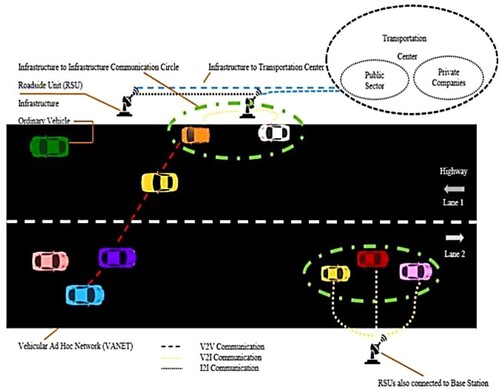
Generally, the architecture of VANET has three essential components, namely, trust authority (TA), road side unit (RSU) and on-board unit (OBU), (Arif et al., Citation2018) as depicted in . Vehicle-to-vehicle (V2V), inter-infrastructure (I2I), and vehicle-to-infrastructure (V2I) are the three communication modes comprised in VANETs.
There are three communication modes: Vehicle to vehicle, vehicle to infrastructure and infrastructure to infrastructure, with ordinary and malicious vehicles under the transportation centre. VANETs also enable vehicles to connect to roadside units (RSUs), which are then linked to the wired Internet and may be networked by a high capacity mesh network. The RSU wired and wireless backbone network may be used to connect the VANET’s network partitions. Here among the entire elements, TA acts as a third party where this is used by RSU and OBU; it is also capable of handling and controlling the entire network. A base station is represented by RSU (e.g. WiFi, WiMAX, and so forth).This operates on long roadway also; their node in between TA and the OBU operates in various authentication processes. An on-board unit is a DSRCS transceiver often placed in or on a vehicle but may also be a portable unit in specific cases. An OBU can function whether a vehicle or a person is moving or stopped. On one or more radio frequency (RF) channels, the OBUs receive and compete for time to transmit.
A wireless exchange for safety messages and their acknowledgement of Internet among vehicles and RSU have been carried out by V2I communication. To avoid collisions in vehicles, it is necessary to update frequently regarding the street situation, meteorological conditions, status of traffic jams, etc., in which VANET plays a major role. When vehicles come within the range of communication, it acquires connection automatically and initiates an ad hoc network (Altintas et al., Citation2015). They can share the location, speed and data direction, where GPS is linked with DSRC, where their outcome is a V2V communication system where a 360° view for vehicles has been offered within the range of communication. A wireless link and movement of the vehicles have been provided using VANETs where the vehicles possess types by promptly altering the structure, extraordinary calculation, expectable movement, and adjustable platoon compactness (Patel et al., Citation2016). Network collaboration among wireless sensor network (WSN) and VANET has been invented by the researchers and termed vehicular sensor networks (VASNETs). Mobile nodes present in automobiles are known VASNET; the essential application in vehicular systems are cooperative collision warning (CCW) message broadcastings, which use V2V communication also secure . The CCW concept was inspired by the widespread use of GPS and ad-hoc wireless technologies such as Wi-Fi (IEEE). They are inexpensive and approach learning about the area’s status. In the CCW idea, a vehicle that knows its GPS position and speed, as well as other crucial metrics such as turn signal status, transmits these data to others over Wi-Fi.
1.1. VANET
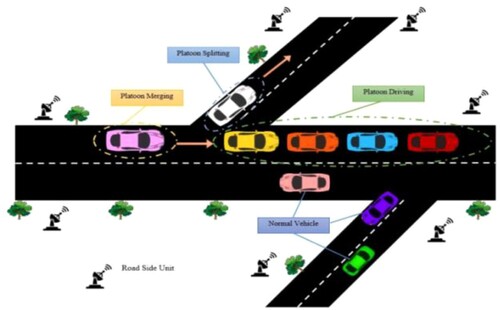
Vehicles in VANET that are automatic possess consistent generation in a wireless network used in the exchange of data in the vehicle domain, might cover the way in future systems, while computers acquire the art of driving. For transmitting encrypted messages, it needs the help of stable communication among the vehicles (Jia et al., Citation2015). Among the automatic driving function, the estimation of communication between vehicles is more essential; it is referred to as platooning. This method arranges the vehicles that travel far away in short (close) distances. The secured distance among the vehicles where the communication requires has been reduced, when the vehicle disseminates the information to generate autonomous emergency retardation steering (Segata et al., Citation2015). The stages in platooning are (i) merging process, (ii) transportable process, (iii) splitting process. VANET generally covers all vehicular network-based applications. In this paper, NC-WTM is proposed to reduce the consumption of fuel, security and risks that are related to driver mistakes platoons. Platooning or flocking is a way of moving a cluster of automobiles with each other in transport. It intends to boost road infrastructure using a computerised roadway. Platoons use electrical, and perhaps structural, connections to reduce the space among automobiles or tractors. Platooning for vehicles intends to maximise the capability of the road. The goal is attained by vehicles in closed sets, also called platoons, that work adjacent together. Finally, accommodation of many vehicles on the highway, while vehicles can operate in platoons that contrast with manual conditions. Their advantages are as follows:
Maximised road capability: This could be attained when the vehicles have functioned tightly more than driving manually.
Minimisation in impacts of surroundings: The vehicles that have been tightly functioned in a platoon are decreased through the mean resistance of air (Amoozadeh et al., Citation2015).
Enhancement of security: Using combined technologies, the system executes platooning of vehicles might not respond faster in harmful conditions. Wireless transmission technology has been expanded through the view of traffic vision below the eyesight of the driver. Here, early dangerous detection has been enabled; hence, security is enhanced. The advantages of wireless communication are that it is less expensive to create and sustain, repair. Maintenance costs are lower than other types of connections, it may be accessible at any location and at any time, and data are sent quicker and at a higher velocity.
Enhanced driver comfort: The amount of automatic operations has relied on the delegate of driver tasks. In particular, for long highway travel, acts as a stress reliever so that the driver concentrates on his shift (Jiang & Delgrossi, Citation2008).
Even though the arrangement aims to maximise their detection performance, inevitable false alarm and miss rates still limit the possibility of real-world deployment where hundreds of thousands of detections may be required per second.
Vehicle platooning is a synchronised mobility approach and an exciting technique for the transportation sector due to the possible effects of enhanced road safety, reduced energy, pollution consumption, and enhanced traffic flow. Platooning improves transportation of using highways, transporting cargo faster, and minimising traffic congestion. Trucks’ driving capacity can be expanded in specific circumstances. It can make future road transportation better, cheaper, and much more economical. Manufacturers are keen to get these platoons into real-world testing, which is already beginning. It allows drivers to do things like a secretarial burden or make and receive emergency calls. For platooning, the inter-vehicular spacing is often smaller, and the automated vehicle handles a different kind of experience of lateral and longitudinal control depending on its level of innovation. The longitudinal controllers, also known as Adaptive Cruise Govern, manage the vehicle’s cruising speed and braking systems, while the lateral controllers manage steering and route trackings, such as carriageway assist and lane change. Platooning can be adopted and integrated with developing solutions such as multimodal transportation and green logistics since it impacts the way trucks travel on the road. Platooning becomes more appealing and significant for the transportation business in the long run due to this. The transportation industry has been forced to explore reliable, cost-efficient, and accordance with change as the demand for inexpensive, fast, and effective transportation services has expanded. Although environmental regulations become more rigorous due to emissions, the transportation industry must embrace new methods to remain viable in commercial and societal well-being. With technology improving, research into the operationalisation of vehicle platooning is the best path forward as the technique to be widely adopted in the transportation business. While technology dictates viability, operationalisation to convey the expense assessment of platooning is critical for decision-makers and stakeholders to see platooning as a viable and appealing choice. We hope that now the framework will aid in the discovery of correct findings and analysis for platooning practice.
Based on behaviour evaluation, each node repeats to build, and its major reason for the management of trust has been estimated by various behaviours for other nodes. For determining the trust of other nodes, reputation has been used, where the nodes choose to provide cooperation. For the action of an untrustworthy node, punishment can be given if needed (Rajakumari et al., Citation2022). Generally, the trust management system depends upon two types of analysis for the estimation of node behaviours. There are two types of trust control methods: distributed authorization systems based on trust chains and networked credibility assessment techniques depending on node actions. This function could include record-keeping and invoice paying, asset allocation maintenance, management company, probate administrator, supplying for a relative individual’s requirements, or assisting an organisation. It is frequently a mix of each of these.
indicates the arrangement of a platoon in the network, whereas the platoons splitting, merging and driving are included in two directions. The first type of analysis is the first-hand analysis; it is also known as the direct analysis (Nait-Abdesselam et al., Citation2008). The analyses carried out by the node themselves are the first-hand analyses. This analysis can be gathered in an active phase or passive phase. The local information is observed when the node is gathered passively. It is compared with the management system that depends upon a few definite behaviours in the neighbouring has to evaluate, namely authentication packet during pathway findings. Another type of analysis is second-hand analysis, and it is also known as an indirect analysis. In general, acquiring interchanging this type of analysis with other nodes for second-hand analysis in the network. Second-hand analysis has the major disadvantages: it has been correlated with overhead, false reports and conspiracy (Buchegger & Le Boudec, Citation2005). Initially, confidence is considered by RSUs with feasible protection. Secondly, the clustered vehicles can undergo different attacks, and it is negotiated when VANET is formed. The attacks can be from outside is situated in the range of wireless network of the vehicles. Even the attacks can be negotiated initially where more than one vehicles behave with an insider. The attacker can overhear, congest, adapt, forge, or fall among any of wireless communication devices of its range (Yau & Mitchell, Citation2003). The attackers comprise major goals, namely regular data broadcast, falsifying or altering information, bordering the benign devices by intentionally yielding the false endorsements, etc. In this paper, bad mouth malicious attack is taken as an example.
Bad mouth attack (BMA): The bad mouthing attack (BMA) is targeted at destroying the reputation of other nodes; a malicious node will only provide misleading suggestions to reduce the likelihood of benign nodes being chosen as providers. The attackers purposefully extend the false trust opinions among the normal nodes, whereas the original malicious nodes are unable to detect. The message from one platoon member to another platoon member is altered due to this attack. This type of attack targets to interrupt the truthful trust assessment and mark it inflexible to efficaciously recognise the malicious invaders (Molina-Gil et al., Citation2014).
Platoons seek assistance between vehicles to decrease fuel consumption, security, and dangers associated with driver errors. The NC-WTM technique improves platoon security through rapid technological changes and eliminates fraudulent vehicles and messages. Platooning is a type of group motion control in which autonomous vehicles are linked together to enhance fuel economy. Automated vehicles navigate by establishing a flexible platoon over a few lanes with a small inter-vehicle distance while completing lane changes, merging, and exiting the platoon. Platooning has several advantages, including increased highway use, reduced fuel consumption, increased driver comfort, and increased security.
The main objective is as follows. In this investigation, we would like to begin a trust management algorithm to repel the badmouth attack inside vehicular platoons. Moreover, we want to enhance the security of platoon heads while resisting attacks.
The motivation of this work is as follows: security during information exchange has always been of the highest importance in vehicular platoons, especially during the attacks of external intruders. It develops unsuccessful patterns. Once the attackers become malicious drivers in platoons, they plan to disturb the entire network or deceive others for their profits. So, it is important to analyse, data should be appropriate and faithful, and vehicles should be able to (i) receive data assured to be correct, (ii) the sender has been verified whether it is authenticated and authorised, and therefore, can be trusted. These have to be considered in security measures which are more important.
The contributions of this work are as follows:
a novel node centric weight-based trust management algorithm (NC-WTM) by considering bad mouth attack.
To compute direct and indirect trust for each vehicle for identifying the malicious platoon member.
2. Literature review
This section deals with the existing techniques proposed and contributed by various researchers in the realm of VANET and vehicular platooning.
Jones (Citation2013) discussed the plausibility of more unfortunate human execution when directing robotised frameworks than driving physically and potential vestige impacts.
Segata et al. (Citation2014) designed the pioneer subsequent centred cooperative adaptive crusie control framework. Communicate power controller is used to let pioneer guide all vehicles inside the company, whereas additional vehicles interface with their nearest individual. Besides, guides are spread in a time division multiple access (TDMA) – style way: the pioneer directs its reference point first, trailed by others.
Jia et al. (Citation2014) examined the uplink execution of drive-through Internet in mistake inclined conditions. By making an allowance for traffic portability and remote correspondence, they proposed an innovative detachment-based agreeable retransmission plot in which a vehicle retransmits required information for its neighbours in the event of bombed broadcast. In addition, a 4-D Markov tier remained figured to show the helpful retransmission conduct in the projected plan.
Li and Song (Citation2015) discuss malicious attacks using an Attack-Resistant Trust management scheme (ART) in VANETs, which can identify and handle node behaviour and also estimate trust among mobile nodes and data. The ART system evaluates the trustworthiness of data and nodes using independent measures, namely data trust and node trust. Data trust is used to determine whether or not the provided traffic data are reliable and to what extent. On the other hand, node trust reflects how reliable the nodes in VANETs are. Furthermore, in VANETs, the ART technique may detect malicious nodes. Particularly, the sense of data has been estimated based on trust in data also, it has been gathered through various vehicles; the trust of node has two directions, one is trust based on function and the other is trust based on recommendation. These are known for functionality satisfaction of nodes and recommendation among the nodes based on trust, respectively. A trust-based recommendation approach differentiates consumers’ information based on their trust ratio. Trust is a degree of certainty in forecasting a node’s future behaviour based on past competency and action observation within a certain context and time frame. This proposed method has been evaluated for its effectiveness and efficiency simultaneously.
Li and Zhu (Citation2016) proposed a BAN-trust strategy. For wireless body area networks (BANs), an attack-resilient malicious node detection technique (BAN-Trust) is suggested to identify and respond to malicious assaults. Extensive tests are used to demonstrate usefulness and efficiency.
Mejri and Ben-Othman (Citation2016) determined a novel technique known as GDVAN (greedy detection for VANETs) for greedy performance outbreaks in VANETs. This technique has been conducted using two stages, namely the distrust stage and the resolution stage. On the basis of undeviating regression with its concept of an arithmetic operation is carried out in mistrust stage, and resolution stage based on decision technique in fuzzy logic. This proposed technique will not identify the greedy behaviour of the nodes; also, it demonstrated effective nodes through three newly defined metrics. A traffic trace of the network has been monitored using the projected algorithm by detecting the greedy nodes in a network. Positively it has to resolve for responsible nodes.
Wang et al. (Citation2016) investigated the robustness against these tactical attacks, and the preservation of privacy by integrating trust management with the pseudonym technique. To resist the tactical attacks in VANETs, we present a reputation model to builds service reputation and feedback reputation. Moreover, we apply the information entropy and the majority rule to the reputation accumulation algorithms to counter false feedback. To defend against the reputation link attack during pseudonym changes, they proposed a hidden-zone strategy and k-anonymity strategy. In data protection, the notion of k-anonymity was developed. It is based on the premise that by mixing data groups with common traits, identifiable details about all the other persons who contributed to the knowledge may be masked. The simulation results show that their scheme is robust to these tactical attacks and preserves privacy against the reputation link attack during the pseudonym changes.
Hu et al. (Citation2017) determined the platoon service system based on trust with query technique while opting for head vehicles in a platoon where it aims to validate among well-mannered and badly-reacted vehicles. The integration in this projected system shows separate characteristics and necessitates for vehicles of the user, such as their location, destination and calculated arrival time. This simulation results have been extensive, and it is indicated that this proposed TPSQ system might attain maximum accurateness related to dependable Platoon Head vehicles.
Iwendi et al. (Citation2018) describe the new spider monkey time synchronisation (SMTS), which is inspired biologically by a vast range of VANETs for decreasing the consumption of energy at the delivery time of data packet to boost. Spatial resolution was decreased using the spider monkey optimisation (SMO) technique, and the resulting information was put into a deep neural network (DNN). Spider monkey time synchronisation (SMTS) is a bio-inspired approach based on cooperative situations of CSMA/CA and TDMA detection time synchronisation techniques primarily used for large-scale VANETs. It is used in a packet-controlled mode, similar to ant colony optimisaation, and employs a pheromone tracking mechanism to detect malicious nodes, based on meta-heuristic prompted architecture through natural spider monkey behaviour, to analyse Sybil attack approaches for VANETs in identifying vehicular collision of challenge area employed with higher density. For the effectiveness of energy in time synchronisation for dual packet delivery of randomly distributed in the algorithm for assessing the offset of clock and delay in propagation for packet transmission from beacon message to the vehicles in destination exactly. The simulation analysis of this proposed technique has been compared to the existing techniques. It transmits for long distance in detecting Sybil attack in VANETs system, which is dynamic for precision measurement, the detection rate for intrusion and efficiency in energy.
Zhang et al. (Citation2018) explained the mechanism based on the Support Vector Machine (SVM) and Dempster-Shafer’s theory of evidence (DST) in identifying misbehaviour for false message resistance attack along with suppression attack in the message. The two phases that are comprised in the proposed technique are the trust model based on data and the trust model on the basis of vehicle. On the basis of the SVM classifier ,false messages based on the content of messages and constraints of the vehicle are identified by the data trust model. The trust model based on data in a vehicle comprises a trust model for a local vehicle and a TA (trust authority) vehicle trust module. The trust model of a local vehicle can be used by any other classifier based on SVM for estimating the vehicle’s credible based on the behaviour of a vehicle for message propagation terms. The performance analysis gives Gaussian kernel best fits while contrasted to an existing operation.
Liu et al. (Citation2018) determined a puzzle-based co-authentication (PCA) scheme. This method has been developed deliberately to minimise DoS attacks using the hash puzzle, and this can acknowledge against a pseudonymous process where it uses collaborative verification. The capability can be offered by the resistance of DoS attacks and enhancing effectiveness in verifying certificates of 5G-VANET. This proposed technique has been combined easily with mutual authentication with pseudonymous schemes. This proposed technique proves their simulation results to be effective and efficient based on both theory and experimental results.
Ucar et al. (Citation2018) determined security protocol visible light communication (VLC) for platoon communication, namely SP-VLC, for stable and secure platoon operation below injection of the data packet has been assured its aim along with channel eavesdropping, congestion and platoon operation occurrences. The detection in different sequences is based on platoon operation attacks, while false operation in packet transmission due to malicious nodes. The secret key initiate mechanisms comprise SP-VLC along with message acknowledgment, transmitting of data terminated in IEEE 802.11p and VLC, identification on congestion along with switching response to VLC for communicating the platoon operation based on the combined practice of IEEE 802.11p and VLC.
Chen et al. (Citation2019) provide a security mechanism that evaluates the credibility of data received from other peer nodes by combining evidence. It can withstand badmouthing, selective misbehaving, and time-dependent attacks.
Poongodi et al. (Citation2019) described a mechanism for a controller known to be reCAPTCHA controller mechanism that defends against automatic attacks similar to botnet zombies. This controller has been utilised for analysing and restricting frequent attacks that occur automatically in DDoS attacks. DDoS (distributed denial of service) assaults are a denial of service (DoS) attack. A DDoS assault comprises a network of linked internet connections, referred to as malware, that is employed to flood a targeted server with bogus data. DDoS may be exceedingly damaging to any digital firm due to this. The simulation of this technique is based on information theory metrics, which are utilised for requests in entropy. Regularity is the metric that is handled to the extent of the susceptibility of the attack. The proposed controller is based on a stochastic model that this can be a mechanism for defending against large botnet-based attackers. This is also used for identifying the distribution of information to the destination vehicle deprived of any interruption using the metrics of PDR.
Basiri et al. (Citation2019) discuss platoon security based on game theory. Under analysis, the architecture of the platoon has been directed or undirected through subjective graphs. The standard can be more particular in edge weights for connection of communication among surroundings in data transmission with vehicles in the unidirectional/bidirectional. The strategies in Nash equilibrium (NE) have been analysed in the game based on the detector that can opt for particular vehicles with these sensors operating and the level of security has been improved. Based on the results, the sensor placement strategy has been detected for the improvisation of certain security in the system.
Dhanasegaran and Soundrapandiyan (Citation2020) vehicular adhoc network (VANET) is one of the most current study fields. The purpose of this study is to provide a data-centric dispatcher selection (DCDS) method based on data offloading for safe information transmission in VANET.
Ruan et al. (Citation2020) discuss acknowledgement correlation in reputed game infinity of vehicle platoon to assist in examining the use of all nodes and to indicate weakness in the present collaborative acknowledgement protocol. This weakness has been handled with authentication protocol based on an enhanced cooperation mechanism that makes it simple for the vehicles to admit to the collaborative approach other than incline to self-centred performance. It can decrease the verification rate by resisting certain confidential attacks by security investigation.
Jin et al. (Citation2021), open multi-agent systems (OMAS) enable autonomous agents to work together in coalitions to complete complicated tasks. Measures to increase OMAS robustness face difficulties, reducing their usefulness. In this work, reliability refers to the likelihood to the actions of an AA will comply with the successful achievement of coalition goals.
Pu (Citation2021) proposed trust block MCDM can increase the detection rate of false messages and harmful vehicles. Vehicular networks (VANETs) are important for processing, computing, and distributing travel-related data. Each vehicle assesses the trustworthiness of the received road safety message and calculates the message originator's trust value.
Markus et al. describe a DLT-based system concept for data trading in VANETs. In data trading, distributed ledger technology (DLT) promises to lower transaction costs. However, DLT integration clashes with the limited communication time between fast-moving objects.
In the existing system, several methodologies have been utilised, such as TDMA, 4-D Markov tier, ART in VANET, etc. All these techniques have some drawbacks, such as decreasing energy consumption, identifying and handling node behaviour, trust between mobile nodes and data, identifying false message-resistance attacks, Sybil attacks, etc. In our proposed work, we utilise a novel node-centric weight-based trust management algorithm (NC-WTM) by considering bad mouth attacks for managing the nodes for the identification process of a malicious platoon, and it has been evaluated. Moreover, security issues are reduced by recognising the malicious platoon.
3. Proposed methodology
A novel node-centric weight-based trust management algorithm (NC-WTM) is proposed by considering bad mouth attack to compute direct and indirect trust for each vehicle for identifying the malicious platoon member. Trust is established in wired networks using indirect trust mechanisms. To establish indirect trust, some initial authentication methods, such as certifying authority, must first authorise all connecting nodes. The challenge of establishing confidence in ad hoc networks is difficult. It is centered on establishing trusting connections with neighbouring routers.
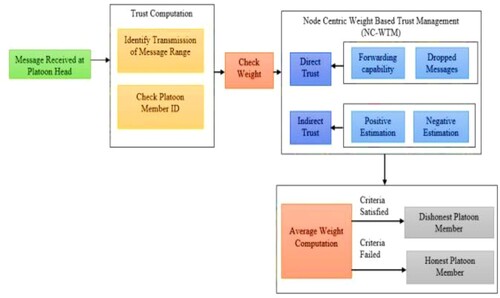
The proposed trust evaluation model known as node-centric weight-based trust management algorithm (NC-WTM) is used as an effective mechanism in VANET. There is no integration among information and approach offered through RSU, as depicted in . Firstly, the estimation for trustworthiness has been detected by the sender node. A sensor node in a sensor network may conduct some processing, acquire sensory data, and communicate with other network nodes. By previous interaction, it is carried out and vehicles that are nearby have been provided with the recommendation. When the trust has been calculated by the centre node, data received have been calculated in three phases, i.e. (1) data excellence, (2) the competency of each node to send message and (3) opinions from neighbours. The central node is the centre point of the net of controllers’ middle hierarchical level. The central node’s functions include collecting measured data from local nodes, processing it, and storing it in the central database. Evaluator nodes and centre nodes are the two types of nodes present in the network centre. When both the nodes in the centre have been computed, the data of the sender node are established. If not, the evaluator node will not accept the data. The evaluation node makes it simple to analyse and compare predictive models to select the optimal model for your application. Once the trust robustness is computed, it is significant to check the weight, and hence based on weight, the computed robustness can be splitted into direct and indirect trust. The direct trust coincides with forwarding capability and indirect trust coincides with positive and negative estimation. After the direct and negative trust calibration, the average weight has to be computed, which helps to differentiate the honest and dishonest platoon members.
3.1. Network model
The current transverse access control idea overcomes these challenges by integrating an adaptable classification system based on a prototype with a series of dynamical feed-forwards to modify the airplane activity in all conditions so for all navigation activities. As a group of vehicles is considered in a vehicle platoon which travels through a collective longitudinal control law, the vehicles custom inter-vehicular communication for correlation with data sharing regarding physical state, namely speed, acceleration and position. An array of vehicles in the network model comprises V = [v1, … , vn], in which lane of the given platoon the vehicle belongs to. The formation of V is not the part of vehicles, which is formed in platoons, even though it is not considered.
EntirePos: P → Q signifies the longitudinal location of each vehicle.
VehInForward-facing: P → P, signifies each vehicle facing the front direction. Assume that the rate of leader vehicle for this function is zero.
VehAtBehind: P → P, signifies each vehicle facing the backward direction. Assume that the rate of the last vehicle for this function is zero.
AttackVeh: P → {0, 1}, signifies the particular vehicle is attacker or not.
The platoon member has to be deployed only after the certification in the behaviours of vehicles. All the certificate credentials of vehicle registration have been handled by RSU. In deploying indirect relationships among two members in platoons are comprised of certification. In our case, the platoon members get their certificates from RSU and check them with platoon heads. Platooning is a useful strategy for increasing road capacity and driving efficiency. VANETs (vehicular ad hoc networks) can help platoons operate better. A platoon comprises a leader vehicle and one or more following vehicles that are all controlled by AHS. However, if a vehicle wants to communicate with another one, it must use RREQ and RREP between the platoon members. The RREQ package is routed through data packets, generating an inverse routing from the target. Whenever a demand hits a network with data to transmit, it generates a route reply (RREP) that includes the hop count taken to accomplish the endpoint. Thus, the certification process takes place each time, and two vehicles will communicate in unicast applications. Initially, the control message named as request-to-broadcast (RTB) is sent to all the vehicles in the lane by RSU. Once the RTB messages reach each vehicle, it starts to compute the overall distance between that particular vehicle to RSU. The calculated distance is subjugated by adjusting the waiting time from 10 ms to 1 ms. When the countdown of the vehicle is zero, their waiting time is correlated; at this time, the vehicle moves and sends the clear-to-broadcast (CTB) message which comprises the ID number of vehicles and its distance from RSU. The levels of the MAC control protocol are RTB and CTB. The following is the basic mechanism underlying the forward node selection process: the source node emits a request-to-broadcast (RTB) packet describing its geographical position and message propagation direction before broadcasting the warning message.
Moreover, it also contains the ID and distance information about a neighbour vehicle. The message arrival of CTB messages has been measured using arrival angle, where all the mutual inter-vehicle distances between neighbouring vehicles can be evaluated by the source vehicle. For every few closer vehicles, they have their distance smaller than a threshold rate, then they can be considered available on the same platoon. After discovering multiple platoons, the RSU selects the uttermost vehicle at each cluster as the platoon head and communicates data messages only to that particular vehicle.
3.2. Trust model
In a homogeneous VANET structure, the vehicles are not allowed to move without the knowledge of platoon heads and are free to travel and get connected with different lanes, until the immediate neighbours estimate their trust ranks.
3.2.1. Direct trust
Direct trust relationships allow them to exchange messages between close cars. Platoon, the repository certificate receives a route request RREQ from the vehicle in the middle “A” to check for the certificate of the neighbour who requires the request from the roadside unit. A roadside unit (RSU) captures location information out of a stationary sensing element across a roadway and sends it to transportation systems or a centralised transportation planning center. These sensors also act as data providers for intelligent cars, allowing them to gather upcoming traffic patterns. When they do not have this certificate, vehicle “A” and its immediate neighbour exchange local self-certificates by sending two unicast messages.
3.2.2. Indirect trust
In similar with the development of direct trust, vehicle “A” scans for the originator’s certificate. When it is unable to find it, the vehicle “A” will send a unicast certificate request for CertA to the neighbour vehicle. On behalf of the originator, a certificate of indirect trust has been established to acquire the certificate of destination, CertB. When the reply message is sent, the indirect trust establishment is considered to be completed. Reply message can be sent based on two conditions. The first condition is to find the platoon head, and the second condition is to find a fresh route for the platoon head. The platoon head must be informed because the platoon leader is in charge of the platoon command and control system, which includes overseeing the unit's activities. The certificate of platoon head is acquired by CertB, to be piggybacked by sending routing reply message RREP on the way to B. Every middle node stocks CertB and update its certificate repository. Secondly, B is found as a fresh route, and the route in between middle node P to sink B along with the route to A from P. Since these routes are directly localised with trust already, and these routes are viewed through the chains of the certificate. The propagated two RREP messages have been transmitted to B with the CertA attached and one to A with the CertB attached.
Algorithm 1 computes the trust computation.
Table
Algorithm 3 Node centric weight-based trust management algorithm is computed using the weights of the vehicles along with direct and indirect trust computation.
3.3. Proposed node-centric weight-based trust management algorithm (NC-WTM)
Following the authority of nodes, the nodes have been classified into three phases: nodes in the high phase (indicated by H), nodes in the medium phase (indicated by M) and nodes in the low phase (indicated by L). Mainly nodes in high phase have been referred to public services such as fire engines and high authority’s vehicle. A network node is a network component that sends, receives, saves, or generates data. It communicates with other network nodes by transmitting data. The topology of a network determines how distinct nodes in the network are connected and communicate with one another. The authority organization has been directly controlled through RSU, and this department has to manage traffic; hence they are considered as high-level nodes with higher authority. Nodes of medium level have been referred to as vehicles such as buses, road maintenance vehicles, manufacturing vehicles, cleanliness trucks, etc., have been handled through a particular department. Nodes of low level have been referred to a private car, taxi, cargo vehicles and etc. It has been majorly handled through individual where they could travel with independence to some range. Generally, a high-phase node with data has been described with enhanced reliability compared with middle-level, low-level nodes with their report. More attention has been paid to the group significance of the trust and the occurrences in traffic here, and define the node N’s weight W(N). Its trustworthiness can be based on the node’s weight and the data reported by it to some degree. A node in VANETs should belong to one of the three levels, and the values are considered 0 ≤ x ≤ 1.
(1)
(1)
The normal load of entire information where that vehicle “x” requested to vehicle “y” to promote, which can be computed by
(2)
(2)
represents the sum of all data’s weight that vehicle “x” asked vehicle “y” to forward.
represents the total amount of data that node “x” asked vehicle “y” to forward.
Ax,y(TotAvg) is the total average weight.
When automobiles collide or recover, there is a greater shift in velocity and hence a greater impact. A stronger acceleration implies that the passengers of the automobiles are subjected to more pressure. Whenever automobiles collide, there is a lesser increase in speed and hence a lower impulse. Because the malevolent impulse of a vehicle is intimately correlated to the normal load of the data failing Mahmood et al. (Citation2019) to be forwarded, vehicle “x” can estimate vehicle’s malicious tendency by
(3)
(3)
F y(w) represents the vehicle y’s malicious tendency.
represents the successful total of the message where vehicle “y” is promoted to vehicle “x”.
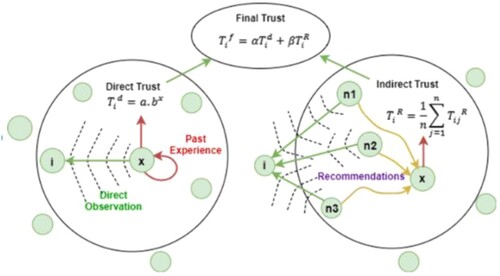
represents the successful sum of the message where vehicle “x” has forwarded for vehicle “y”. The diagrammatic representation of direct and indirect trust is given in .
Once the attack has been detected in the network, the platoon head evaluates the trust by analysing the contents of established data. Meanwhile, the subsequent information is distributed to the destination either directly or by intermediate neighbours; hence, there are two approaches to trust computation are achieved, which are discussed below:
Direct trust (Dir): It indicates the overall capacity of the vehicle to broadcast and discuss the obtained data with the neighbouring vehicles. The exchange of data collected by a quantitative operation to consumers is referred to as dissemination. Providing or transferring factual analysis to consumers is known as data dissemination. Data use to the use of knowledge for medical decisions, scientific techniques, training, programme planning, and the improvement of healthcare resources, among other things. Data should be distributed in readily available forms, supported by clear and concise documentation. Information should be disseminated as soon as possible, and all users should have equal access to it. Hence, we can express a “Data Disseminate Ratio (DDR)” as follows:
(4)
(4)
(5)
(5)
C is the weight of the vehicle communicating data to other vehicles. DMC designates the session of the fallen messages at the vehicle. MD for the genuine vehicles, which have high as the number of messages fallen at the vehicle remain less. D represents the weight of the nodes unable to convey and segment the messages.
Indirect Trust (IDir): The suggested method classifies the estimations provided by “k” neighbour vehicles into two modules: (i) positive estimations (Y) from platoon head and (ii) negative estimations (Z) from platoon head (Singh & Verma, Citation2020).
(6)
(6)
whereas A is the weight of the vehicle transmitting messages towards other vehicles. B signifies the overall weight of the vehicle failing to transmit and share messages. X signifies the unicast message between the neighbours. The final trust calculation consists of direct and indirect trust, i.e. recommendations. Each node computes the direct trust value of its one-hop neighbours by calling direct trust. The node request recommendations to its neighbour node using indirect trust.
4. Performance analysis
In this section, the comparison of our scheme is made with the existing method in various parametric metrics such as precision, recall, F-score, and accuracy. To show our NC-WTM method is more efficient than the existing methods, the graphs are given here. For simulation purposes here, we have chosen Network Simulator −2 version 2.29. It, abbreviated as NS2, is a simple event-driven simulation programme that has proven effective in analysing the dynamic dynamics of communication networks. NS2 can simulate wired and wireless network operations and protocols, such as routing algorithms, TCP, and UDP. In presented about overall simulation setting for the proposed NC-WTM.
Table 1. Simulation parameter.
4.1. Precision (Prec)
It indicates the overall capacity of our trust model of calculating truthful evidence.
(7)
(7)
p(ln) represents the obtained probability value from all vehicles to find as malicious by the genuine vehicle.
p(mn) represents the consolidated likelihood to notice the vehicle as malicious, by the particular malicious vehicle.
4.2. Recall (Rec)
It indicates the overall capacity of our trust model to detect the vehicles by broadcasting malicious content correctly.
(8)
(8)
p(ln) represents the likelihood of noticing a malicious vehicle as a genuine vehicle.
p(mn) represents the consolidated likelihood of our scheme to notice the vehicle as malicious.
4.3. F-score
It is defined as a weighted average of Prec and Rec, depicting the accurateness of our trust model scheme with the higher F-score, the more accuracy, we can get
(9)
(9)
4.4. Trust computation error (TCE)
It is calculated by estimating the mean square error amongst the intended actual trust value calculation of the vehicles. TCE is also predicted by estimating the root mean square of the intended trust computed for all vehicles.
(10)
(10)
MSE represents mean square error.
4.5. End-to-end delay E(delay)
It is defined as the overall time occupied through data to move a platoon from the source vehicle to the destination vehicle. End-to-end network delay is caused by various factors, including transmission delay, propagation delay, processing delay, and queuing delay. For TCP connections, application relays can minimise end-to-end delays and enhance performance. Additional features, such as application relays, media transcoding, and mixers can be added to increase the performance of broadcasting between participants in the overlay.
(11)
(11)
4.6. Average link duration Avg(link)
It is the lifetime approximation of the entire communication link established between the source and destination vehicles to interchange the packets.
(12)
(12)
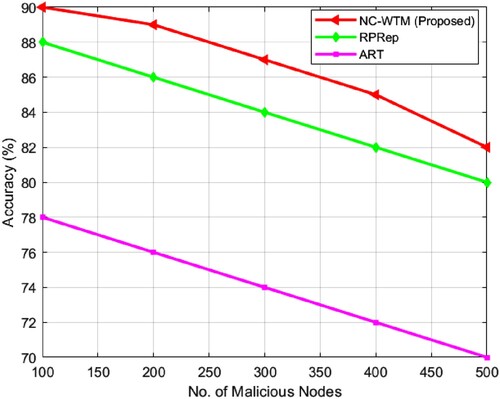
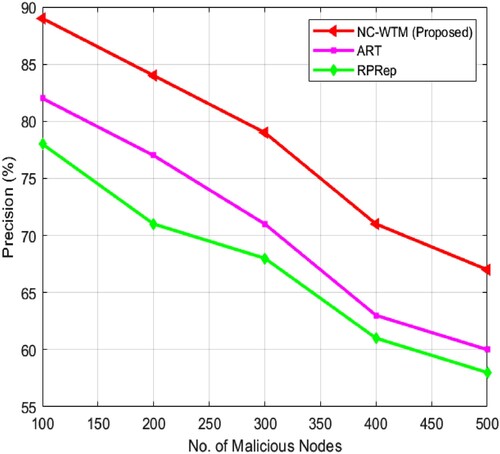
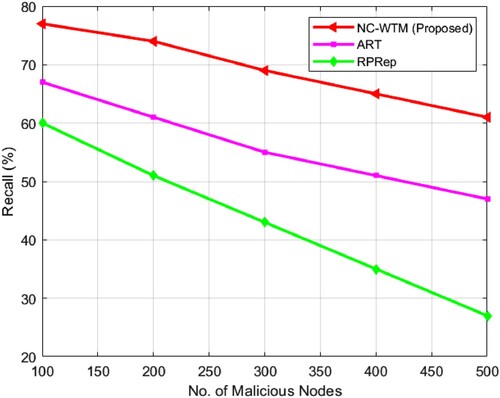
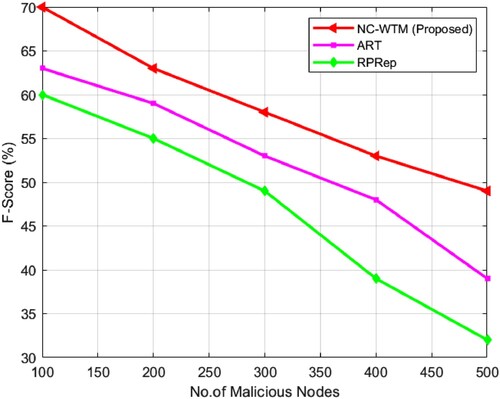
In , a comparative illustration of the proposed NC-WTM with existing ART and RPRep in terms of accuracy is presented. illustrates that the existing method undergoes severe attack by the bad mouth pattern, especially when it contains a number of malicious vehicles, whereas the NC-WTM algorithm can attain over 89% of the accuracy of malicious vehicles, which are directing bad mouth attack. In , a comparative illustration of the proposed NC-WTM with existing ART and RPRep in terms of precision is presented. illustrates that the existing method undergoes severe attack by the bad mouth pattern especially when it contains a large number of malicious vehicles, whereas the NC-WTM algorithm can able to attain over 78% of precision of malicious vehicles, which are directing bad mouth attack. In Table , a comparative analysis of NC-WTM with the existing technique stated that the proposed approach in terms of recall exhibits higher NC-WTM values. In shows the recall comparison of three algorithms and found that NC-WTM achieves the average recall value of 69.3% dealing with bad mouth attackers with its data modification ability, which is significantly higher than the existing ART and RPRep. In Table comparative analysis of the F-score is presented, and measurement is examined for NC-WTM with ART and RPRep. The measured F-score illustrates that the proposed NC-WTM offers a higher F-score. In demonstrates the comparative analysis of the F-score for varying node values. It is found that even under the existence of malicious vehicles, the proposed NC-WTM provides a higher average F-score value of 60.4%.
5. Discussion
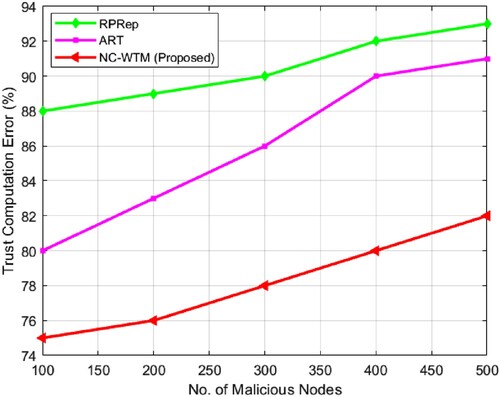
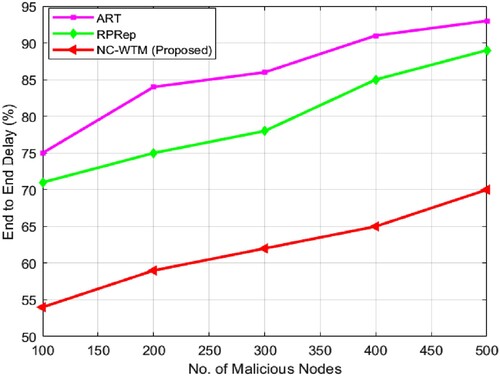
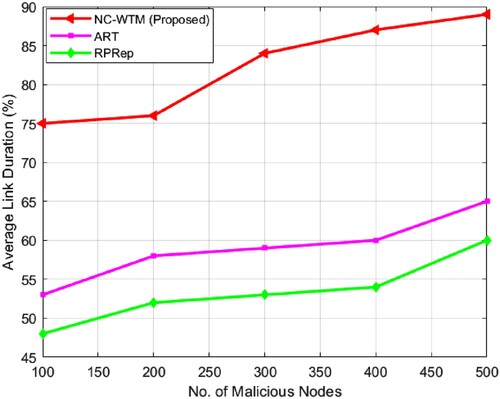
In , trust computation errors measured for the proposed NC-WTM with existing ART and RPRep are presented. From , it is noticed that the proposed NC-WTM algorithm has steadiness between the values of TCE through the upsurge of 100 vehicles at every stage, whereas the ART and RPRep trust algorithms do not have that much steadiness amongst the standards of TCE with 200 vehicles every stage. For the proposed NC-WTM technique minimal computation error value is observed at around 78.2%, which is significantly minimal to the existing technique. In , comparative measured values for End to End Delay are presented for evaluating the performance of the proposed NC-WTM. In describes the overall performance of NC-WTM, and it proves that the algorithm is improved by comparing it with existing trust techniques. It is determined as the average end-to-end delay for the NC-WTM method is almost 62%. The ART and RPRep algorithms achieve 85.8% and 80.2% with lengthier delay. For the proposed NC-WTM average link duration is measured for varying malicious nodes. The measured link duration is presented in . portrays that NC-WTM is more steady and dependable. The average measured link duration was 82.2% for the proposed NC-WTM, which is significantly higher than the existing techniques. So, as the vehicle counts increase in the platoon, NC-WTM preserves link constancy, and a very small gradual alteration is observed in the average link values. shows that the suggested NC-WTM has a higher precision value of 78%, as well as a higher recall and F-score value of 69.3% and 60.4%, respectively. Precision is minimal in terms of ART and RPRep. With increased average link time, the suggested NC-WTM approach provides minimum end-to-end delay and calculation error.
Table 2. Comparison of the accuracy.
Table 3. Comparison of the precision.
Table 4. Comparison of the recall.
Table 5. Comparison of F-score.
Table 6. Comparison of trust computation error.
Table 7. Comparison of end-to-end delay
Table 8. Comparison of average link duration.
Table 9. Comparison of existing and the proposed NC-WTM.
6. Conclusion
In this research, we present the NC-WTM model, which uses a node-centric weight-based trust management algorithm to optimise overall platoon security by quickly recognising and canceling deceptive vehicles and their produced messages. It is used to build a network with badmouth attacks, and the proposed methodology is used to assess the trustworthiness of each vehicle’s input beforehand. The node-centric trust model is simple enough to for instantaneous trustworthy analysis. The proposed NC-WTM is an attack-resistant trust model that detects trusted information with high precision, even in the context of a foul mouth attack. Moreover, the performance of NC-WTM is compared with a robust and privacy-preserving reputation management scheme (RPRep) and Attack-resistant trust management scheme (ART) trust model, which undoubtedly shows that NC-WTM performs better in high precision, recall and F-score. The performance analysis shows that NC-WTM outputs are optimised trust models in precision – 78%, recall – 69.3%, F-score – 60.4% and Accuracy – 89%. Trust establishment models calculate trust based only on direct observation and do not consider the node’s prior behaviour in the network. The advantage of the proposed work is to improve the security of platoon heads when resisting the attacks, and trust management is used for repelling the bad mouth attack. Its limitation is energy efficiency, and it will be considered a future scope and developed properly. The future work concentrates on developing resource allocation algorithms to achieve high-quality platoon service.
Disclosure statement
I/We declare that “it has not been submitted anywhere before and not been published in other journals”. It does not comprise that is outrageous, indecent, deception, stealing, defamatory, or opposing to rules. I/we pursued the Journal’s accepted “Publication ethics and malpractice” declaration provided on the website of the journal in concern part and responsible for the rightness (or copying) and article genuineness.
Data availability statement
Data and coding will be shared whenever it is required for the review.
References
- Altintas, O., Dressler, F., Hagenauer, F., Matsumoto, M., Sepulcre, M., & Sommery, C. (2015). Making cars a main ICT resource in smart cities. In IEEE Conference on Computer Communications workshops (INFOCOM WKSHPS)(pp. 582–587).
- Amoozadeh, M., Raghuramu, A., Chuah, C.-N., Ghosal, D., Zhang, H. M., Rowe, J., & Levitt, K. (2015). Security vulnerabilities of connected vehicle streams and their impact on cooperative driving. IEEE Communications Magazine, 53(6), 126–132. https://doi.org/10.1109/MCOM.2015.7120028
- Arif, M., Wang, G., & Balas, V. E. (2018). Secure VANETs: Trusted communication scheme between vehicles and infrastructure based on fog computing. Studies in Informatics and Control, 27(2), 235–224. https://doi.org/10.24846/v27i2y201811
- Basiri, M. H., Pirani, M., Azad, N. L., & Fischmeister, S. (2019). Security of vehicle platooning: A game-theoretic approach. IEEE Access, 7, 185565–185579. https://doi.org/10.1109/ACCESS.2019.2961002
- Buchegger, S., & Le Boudec, J.-Y. (2005). Self-policing mobile ad hoc networks by reputation systems. IEEE Communications Magazine, 43(7), 101–107. https://doi.org/10.1109/MCOM.2005.1470831
- Chen, J.-M., Li, T.-T., & Panneerselvam, J. (2019). TMEC: A trust management based on evidence combination on attack-resistant and collaborative internet of vehicles. IEEE Access, 7, 148913–148922. https://doi.org/10.1109/ACCESS.2018.2876153
- Dhanasegaran, K., & Soundrapandiyan, R. (2020). DCDS: Data centric dispatcher selection protocol for cellular enabled VANET communication. International Journal of Communication Systems, 33(13), e3936. https://doi.org/10.1002/dac.3936
- Hu, H., Lu, R., & Zhang, Z. (2017). TPSQ: Trust-based platoon service query via vehicular communications. Peer-to-peer Networking and Applications, 10(1), 262–277. https://doi.org/10.1007/s12083-015-0425-0
- Iwendi, C., Uddin, M., Ansere, J. A., Nkurunziza, P., Anajemba, J. H., & Bashir, A. K. (2018). On detection of sybil attack in large-scale VANETS using spider-monkey technique. IEEE Access, 6, 47258–47267. https://doi.org/10.1109/ACCESS.2018.2864111
- Jia, D., Lu, K., Wang, J., Zhang, X., & Shen, X. (2015). A survey on platoon based vehicular cyber-physical systems. IEEE Communications Surveys & Tutorials, 18(1), 263–284. https://doi.org/10.1109/COMST.2015.2410831
- Jia, D., Zhang, R., Lu, K., Wang, J., Bi, Z., & Lei, J. (2014). Improving the uplink performance of drive-thru internet via platoon-based cooperative retransmission. IEEE Transactions on Vehicular Technology, 63(9), 4536–4545. https://doi.org/10.1109/TVT.2014.2315741
- Jiang, D., & Delgrossi, L. (2008). IEEE 802.11 p: Towards an international standard for wireless access in vehicular environments. In VTCSpring 2008-IEEE Vehicular Technology Conference (pp. 2036–2040).
- Jin, D., Kannengiesser, N., Sturm, B., & Sunyaev, A. (2021). Tackling challenges of robustness measures for autonomous agent collaboration in open multi-agent systems.
- Jones, S. (2013). Cooperative adaptive cruise control: Human factors analysis. Tech. Rep. Federal Highway Administration. Office of Safety Research.
- Li, W., & Song, H. (2015). ART: An attack-resistant trust management scheme for securing vehicular ad hoc networks. IEEE Transactions on Intelligent Transportation Systems, 17(4), 960–969. https://doi.org/10.1109/TITS.2015.2494017
- Li, W., & Zhu, X. (2016). BAN-trust: An attack-resilient malicious node detection scheme for body area networks. In International Conference on Computing, Networking and Communications (ICNC) (pp. 1–5).
- Liu, P., Liu, B., Sun, Y., Zhao, B., & You, I. (2018). Mitigating DoS attacks against pseudonymous authentication through puzzle-based co-authentication in 5G-vanet. IEEE Access, 6, 20795–20806. https://doi.org/10.1109/ACCESS.2018.2826518
- Mahmood, A., Zhang, W. E., Sheng, Q. Z., Siddiqui, S. A., & Aljubairy, A. (2019). Trust management for software-defined heterogeneous vehicular ad hoc networks. In Security, privacy and trust in the IoT environment (pp. 203–226). Springer.
- Matin, M. A., & Islam, M. (2012). Overview of wireless sensor network. Wireless Sensor Networks-Technology and Protocols, 1–3.
- Mejri, M. N., & Ben-Othman, J. (2016). GDVAN: A new greedy behavior attack detection algorithm for VANETS. IEEE Transactions on Mobile Computing, 16(3), 759–771. https://doi.org/10.1109/TMC.2016.2577035
- Molina-Gil, J., Caballero-Gil, P., & Caballero-Gil, C. (2014). Aggregation and probabilistic verification for data authentication in vanets. Information Sciences, 262, 172–189. https://doi.org/10.1016/j.ins.2013.07.036
- Nait-Abdesselam, F., Bensaou, B., & Taleb, T. (2008). Detecting and avoiding wormhole attacks in wireless ad hoc networks. IEEE Communications Magazine, 46(4), 127–133. https://doi.org/10.1109/MCOM.2008.4481351
- Patel, D., Faisal, M., Batavia, P., Makhija, S., & Mani, M. (2016). Overview of routing protocols in vanet. International Journal of Computer Applications, 136(9), 4–7. https://doi.org/10.5120/ijca2016908555
- Poongodi, M., Vijayakumar, V., Al-Turjman, F., Hamdi, M., & Ma, M. (2019). Intrusion prevention system for DDoS attack on vanet with recaptcha controller using information based metrics. IEEE Access, 7, 158481–158491. https://doi.org/10.1109/ACCESS.2019.2945682
- Pu, C. (2021). A novel blockchain-based trust management scheme for vehicular networks. In Wireless telecommunications Symposium (WTS) (pp. 1–6).
- Rajakumari, K., Punitha, P., Kumar, L., & Suresh, C. (2022). Improvising packet delivery and reducing delay ratio in mobile ad hoc network using neighbor coverage-based topology control algorithm. International Journal of Communication Systems, 35(2). https://doi.org/10.1002/dac.4260
- Ruan, N., Su, C., & Xie, C. (2020). Securing cooperative adaptive cruise control in vehicular platoons via cooperative message authentication. IEICE Transactions on Information and Systems, 103(2), 256–264. https://doi.org/10.1587/transinf.2019INP0010
- Segata, M., Bloessl, B., Joerer, S., Sommer, C., Gerla, M., Cigno, R. L., & Dressler, F. (2014). Towards inter-vehicle communication strategies for platooning support. In 7th International Workshop on Communication Technologies for Vehicles (Nets4Cars-fall) (pp. 1–6).
- Segata, M., Bloessl, B., Joerer, S., Sommer, C., Gerla, M., Cigno, R. L., & Dressler, F. (2015). Toward communication strategies for platooning: Simulative and experimental evaluation. IEEE Transactions on Vehicular Technology, 64(12), 5411–5423. https://doi.org/10.1109/TVT.2015.2489459
- Singh, K., & Verma, A. K. (2020). TBCS: A trust based clustering scheme for secure communication in flying ad-hoc networks. Wireless Personal Communications, 114(4), 3173–3196. https://doi.org/10.1007/s11277-020-07523-8
- Ucar, S., Ergen, S. C., & Ozkasap, O. (2018). IEEE 802.11 p and visible light hybrid communication based secure autonomous platoon. IEEE Transactions on Vehicular Technology, 67(9), 8667–8681. https://doi.org/10.1109/TVT.2018.2840846
- Yau, P.-W., & Mitchell, C. J. (2003). Security vulnerabilities in ad hoc networks. In Proceedings of the 7th International Symposium on Communication the Ory and Applications (pp. 99–104).
- Wang, J., Zhang, Y., Wang, Y., & Gu, X. (2016). RPRep: A robust and privacy-preserving reputation management scheme for pseudonym-enabled VANETs. International Journal of Distributed Sensor Networks, 12(3), 218–365. http://doi.org/10.1155/2016/6138251
- Zhang, C., Chen, K., Zeng, X., & Xue, X. (2018). Misbehavior detection based on support vector machine and Dempster-Shafer theory of evidence in VANETS. IEEE Access, 6, 59860–59870. https://doi.org/10.1109/ACCESS.2018.2875678