?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.Abstract
Offloading data to cloud storage has changed the way people live and work, which reduces data management costs and increases productivity. People can use their devices to download data from cloud storage regardless of location and time. It means that data can be shared across domains through cloud storage. However, offloading data to cloud storage brings convenience as well as various challenges, such as how to solve the performance bottleneck of cloud storage and how to achieve secure data sharing in cloud storage. Blockchain has played an important role in secure data sharing based on its tamper-evident nature. In this paper, a blockchain-assisted data sharing scheme is proposed which implements the detection of deduplicated data and completes the ciphertext combination after deduplication. In order to verify the legitimacy of the ciphertext, blockchain is used to assist in verifying the ciphertext based on its tamper-evident nature. Furthermore, partial ciphertext parameters are calculated at free time to improve server operation efficiency. Finally, we simulated all algorithm of the proposed scheme on the PBC library and the results show that it achieves a balance between usability and performance.
1. Introduction
With deeper exploration of cloud storage, the ways in which files are stored have changed dramatically. Storing data on an external server makes life and work easier, allowing access to the data in the server using electronic devices. Date is interacting in the cloud server every minute. It not only facilitates life and work but also brings challenges. Cloud server is a third-party entity which wants to collect more information to derive profit. Achieving secure data sharing is an urgent issue at present, which concerns the profit of each user. Attribute-based encryption (ABE) (Sahai & Waters, Citation2005) is widely used for data interaction. Each user can be described by attributes (e.g. “student”, “18 years old”). Users can set who can correctly recover files when they are encrypted. When the ciphertext is downloaded, only legitimate users (i.e.the attributes are satisfied) can decrypt it correctly. Furthermore, the server malicious insiders also cannot access information about the file. There have been many studies on ABE, but with the development of smart devices (C. Wang et al., Citation2023), traditional ABE calculations are expensive and not suitable for easily portable devices. Portable devices have low computational power and small storage space, so it is necessary to design an efficient and secure data sharing.
On one hand, the data in the server is increasing exponentially compared to previous years. Huge amounts of files are being outsourced and stored in the server, putting enormous pressure on memory management. A large number of invalid files and duplicate data consume server resources, which is not conducive to sustainable development of cloud storage. However, it is difficult for the server to determine which is the duplicate data. Since ABE is used to encrypt files, the files are difficult to distinguish for the server. In order to overcome the performance bottleneck of cloud storage, resource rationalisation is a critical issue to be addressed today. It is a challenge for the server to be able to identify duplicate data without compromising data privacy. On the other hand, incorrect files being sent to users will bring huge losses due to carelessness or laziness of the server. Once a mismatched file is sent to the user in a traditional ABE scheme, the user cannot determine the legitimacy of the file. It will not only cause the user to make a wrong decision, but also reduce the credit rating of the server provider.
At the same time, blockchain as a decentralised database technology, many researches (H. Yang et al., Citation2021; Z. Zheng et al., Citation2018) have been proposed. Information is stored in blocks, which are connected by creation time. Blockchain (X. Li et al., Citation2020) is used in a variety of scenarios based on its unforgeable and untamperable properties. Although blockchain storage has stronger security compared to traditional cloud storage, the storage is lower in efficiency in blockchain systems. If distributed storage is combined with traditional centralised storage (Deebak et al., Citation2022), security and utility will be balanced.
Designing an efficient data sharing scheme can effectively drive industrial development. On the one hand, when data can be circulated in an orderly manner and fully shared, it can flow to the place where it can generate the greatest value, and then push the multiplier effect on the economy and society to the maximum. On the other hand, data sharing can drive industry towards digital transformation. It will better meet the digital collaboration of industry in different businesses such as R&D and production to optimise industry as a whole.
1.1. Contributions
This paper is an expanded version of the conference paper (T. Zhang, Wang, et al., Citation2022). The ciphertext combination algorithm has been improved by using a method where some of the ciphertext parameters are generated by the offline phase to improve the efficiency of the server operation. In addition, the security and performance analysis in this paper is expanded, selective CPA security is confirmed and a comparison of related work is done.
A data sharing scheme using ABE cryptographic primitive is proposed which supports deduplication. After the deduplication, a combined ciphertext is formed to ensure that all legitimate users can decrypt it correctly. What's more, based on its tamper-evident nature, the blockchain is used to assist users in verifying the legitimacy of files. The proposed scheme not only reduces the storage cost but also improves the decryption efficiency of users. The decryption complexity of the data user is . The contributions are shown below.
A data sharing scheme using ABE cryptographic primitives is proposed which supports deduplication. In the proposed scheme, files are encrypted and uploaded to cloud server. A server deduplication algorithm is designed and run when multiple ciphertexts are received by the server. Particularly, key blinding is used to offload the expensive computational operations of traditional ABE. The decryption computation complexity is
.
The combined deduplication method is designed so that legitimate users in the deduplication access policy can access the file. In order to reduce the waste of storage space, a data combination algorithm is designed for the server. What's more, considering the data processing latency of cloud servers, re-randomisation techniques are employed to improve the efficiency of server operation.
Blockchain is adopted to assist users in verifying file integrity, and only legitimate users can successfully verify. Based on the tamper-evident nature of blockchain, blockchain is adopted to assist users in completing cryptographic verification of the centralised server storage.
The proposed scheme achieves a balance between security and practicality. The security proof of scheme is given and scheme is simulated in PBC library. The simulation results show that the proposed scheme has a lower computational overhead compared to the related schemes.
1.2. Related works
Since ABE was introduced, it has been widely used for data sharing. It solves one-to-many communication compared to identity-based encryption (IBE). In 2005, ABE was first introduced in Sahai and Waters (Citation2005), which is a derivative of IBE. Then, there is a large amount of research on ABE. In Bethencourt et al. (Citation2007), the construction of CPABE was first proposed. Keys are randomised to achieve resistance against collusion attacks. However, this scheme only proved security under the random oracle model. Then, Cheung and Newport (Citation2007) proposed the first CPABE scheme under the standard model. There has been a lot of related works (Ge et al., Citation2021a; Jammula et al., Citation2022; Xiao et al., Citation2022) about CPABE.
In traditional ABE, full control of the file can be achieved. Users can specify who has access to the files. However, with the development of smart devices, various easy-to-deploy devices have been designed. These devices have characteristics such as easy portability and limited computing power. The computational overhead of traditional ABE is no longer suitable for these devices for data sharing. In Green et al. (Citation2011), a new paradigm is proposed to reduce the computational overhead of the decryption device. But with the changing needs of life, it is not enough to consider the overhead of decryption device. Securely offloading computational overhead to third parties has become a growing focus of research. A novel paradigm (Zhou & Huang, Citation2012) is proposed to outsource encryption and decryption, which realises a constant level of overhead on the user side. However, access structure is AND gate in Zhou and Huang (Citation2012). To support arbitrary access structures, J. Li et al. (Citation2012) proposed an outsourced encryption using MapReduce. On the other hand, a technique to split the algorithm into two phases is presented. Hohenberger and Waters (Citation2014) proposed the Online/Offline technique to reduce system online overhead. Although, many schemes (Tu et al., Citation2021; L. Zhang et al., Citation2021) improve the efficiency of system operation, little work is done to consider that the cloud server will send an error file to the user because of laziness. J. Li et al. (Citation2017) proposed a verifiable ABE which achieves a constant ciphertext size. Ge et al. (Citation2021b) proposed a verifiable and fair ABE which can detect the return ciphertext.
Meanwhile, some works are combining cloud storage with blockchain. Blockchain is a distributed database shared among the nodes of a computer network with features such as decentralisation, traceability, and immutability. Rahulamathavan et al. (Citation2017) proposed a blockchain architecture using ABE for privacy protection. H. Wang and Song (Citation2018) combined ABE and blockchain to construct an electronic medical data system. In H. Zheng et al. (Citation2020), blockchain and sampling are adopted to ensure fairness between users and servers. Liu et al. (Citation2020) proposed a blockchain-assisted ABE scheme which supports efficient revocation. In Liu et al. (Citation2020), the revocation operation is performed by the blockchain. There is no longer a need to update the ciphertext and key compared to traditional revocable ABE. L. Zhang, Zou, et al. (Citation2022) proposed a novel blockchain-based data sharing scheme (BDSS) which can achieve efficient revocation. Cui et al. (Citation2016) offloaded the overhead caused by user revocation to an untrusted server. In this scheme, each user only needs to store a constant size key. In 2015, Qin et al. (Citation2015) presented a ciphertext conversion method to achieve efficient decryption by users. However, the verification overhead in this scheme is expensive for lightweight devices. To reduce the verification overhead of ABE-based schemes, X. Yang and Zhang (Citation2022) proposed a cloud-chain collaborative ABE scheme which enables user verification efficiently. J. Ma et al. (Citation2021) designed an ABE algorithm using blockchain in vehicular networking environment. Vehicles with different attributes will access different information bulletins. Based on the decentralised and tamper-evident nature of blockchain, C. Wang et al. (Citation2020) proposed a blockchain-assisted trustworthiness calculation to reduce the overhead of vehicle authentication. To prevent data tampering, H. Yang et al. (Citation2021) proposed a data transfer protocol using blockchain. W. Wang et al. (Citation2022) integrate the smart contract and mobile devices to establish a secure, interactive, and fair blockchain-based MCS system. Shifting the data evaluation process to the requester side reduces the computational cost of blockchain nodes.
In terms of deduplication, T. Zhang et al. (Citation2023) proposed a multi-server assisted attribute-based encryption scheme which can support deduplication. In this scheme, users can achieve lightweight encryption and support data duplication detection. H. Ma et al. (Citation2019) proposed an attribute-based encryption scheme that supports efficient deduplication and attributes revocation for eHealth systems. Xu et al. (Citation2019) proposed an ABE-based deduplication which can support access policy update. Based on edge computing and blockchain technology, Wu et al. (Citation2022) proposed a secure deduplication framework to achieve one-to-many data sharing. Although many ABE-based deduplication schemes have been proposed, it remains a challenge to achieve efficient verification of outsourced data.
2. Preliminary
2.1. Bilinear map
Definition 2.1
Given two cyclic group ,
with prime oder p, a linear map e:
. The bilinear pairing satisfies the following propertie:
Bilinearity: for all
and
, we have
.
Nondegeneracy: for all
,
whenever
.
Computable: for all
,
is computable.
2.2. Linear secret-sharing scheme
Definition 2.2
A secret sharing P is called linear if
Each party involved can be represented by a vector.
The share-generating matrix is
and each row is labelled by a party
. Suppose that s,
,..,
are randomly chosen and s is the secret to be shared; then,
is the vector of l shares of the secret s according to
. The share
is owned by the party
.
3. System & security model
3.1. System model
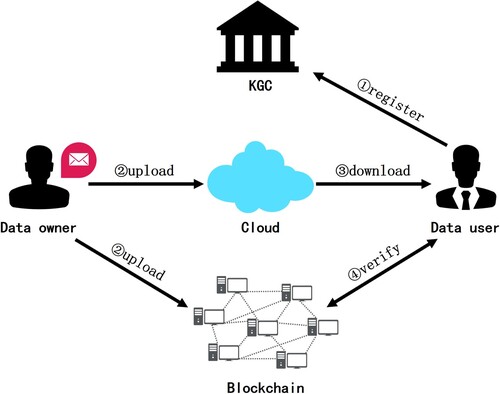
As shown in Figure , data storage in cloud computing environment is considered, which includes five entities. The description of each entity is given as follows. First, Du needs to complete the registration. Files are encrypted and uploaded to CS and blockchain by Do. Du downloads data from the cloud when it needs to be used. Du uses private key to recover files and complete verification using the blockchain.
Key Generation Center(KGC): KGC is recognised as a trusted authority. It is responsible for checking user legitimacy and distributing keys for legitimate users. The system is also initialised by KGC.
Data Owner(Do): Before uploading the file, Do encrypts it to achieve data privacy protection. At the same time, Do chooses who can access the data. Then, the encrypted file is uploaded to CS to store it.
Data User(Du): Du submits a collection
to KGC. As a response, the private key is sent to Du. The download request is sent to cloud sever when data needs to be downloaded. Files are recovered using the private key and verified using the blockchain.
Cloud Server(CS): CS is a semi-trusted entity. It is responsible for storing the file uploaded by Du. In addition, the ciphertext is transmitted to Du and the legitimate download request is verified.
Blockchain: Blockchain is a chained data structure combining blocks of data in a sequentially linked format. Blockchain is unforgeable and untamperable due to its structure and set characteristics. Note that the proposed scheme uploads the tags used for verification into the blockchain to achieve secure verification of decrypted data.
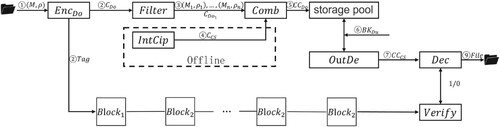
Meanwhile, the system flow is further provided in Figure . In the proposed scheme, it can be divided into 9 steps. The first step is for Do to select an access policy to complete the encryption of the file. The ciphertext
and tag Tag generated by the encryption
are uploaded to CS and Blockchain respectively. In the cloud server, the ciphertext is successively filtered and combined. Then,
is stored in the storage pool. CS completes the ciphertext conversion when a conversion request
is received from the user. As a result,
is sent to Du. Finally, Du downloads the tag from the blockchain to complete the verification and recover the file.
3.2. Formal definition
3.2.1. KGC side
At the KGC side, algorithms are designed to make an initial system and a user registration. SETUP is run to initialise the system and parameters SP and MK are output as a response. KGen is run to help Dus to register and the tuple is output when receiving the set Att where B is the Du's blinded key and Rk is the recover key. Note that SP is public to other entities. The algorithms are defined as follows.
SETUP is run by KGC. Output SP and MK when ζ is input.
KGen is run by KGC. Output the tuple
when the set Att and MK are input.
3.2.2. Owner side
At the owner side, algorithms are designed to help Do complete file F encryption. To protect the security of file, Do needs to complete encryption of the file before uploading to an external server. ABE cryptographic primitives are adopted in the proposed scheme. Thus, the user is able to specify who can access the file. Let be an access structure. Particularly, access structure is
in this paper. Enc is run by Do to encrypt F and
and a tag is output when receiving F and
. The algorithm is defined as follows.
Enc is run by Do. Output
and Tag when the file F and
are input.
3.2.3. Server side
At the server side, algorithms are designed to complete file filtering and file combination. In particular, InCip is run when the server is free. Filter is run to filter the encrypted files When multiple encrypted files are uploaded. With the designed algorithm, duplicate data will be removed after filtering. Then, Comb is run to combine the encrypted files so that the legitimate user of the filtered file can be accessed. In order to increase the speed of server operation, pre-deployment is used to reduce the computational overhead of the online phase. InCip is run to generate partially encrypted files. After the combination is completed, is sent to storage pool.
is converted to
when receiving the blinded key sent by a legitimate user. In response, the result of the conversion is sent to Du. The algorithms are defined as follows.
CS filters the ciphertexts before storing them. CS runs the Filter algorithm to check if
and
are duplicate data. If
and
are duplicate data, output 1; otherwise, output 0.
CS generates pre-deployment ciphertext
in offline phase which is prepared for Comb algorithm. Let ψ is the number of assumed attributes.
New access structure
combined by CS. The combined ciphertext
is generated and stored in CS.
OutDe is run to convert
and the result of the conversion is
. The conversion process is triggered by the receipt of the blinded key Bk from the legitimate user. Then, CS sends
to Du.
3.2.4. User side
At the user side, algorithms are designed to help Du to complete the recovery of files and verify them. Du downloads the encrypted file from CS. BK is sent to CS to complete the ciphertext conversion. The file F is recovered using the private key when Du receives from CS. Then, Tag is downloaded from blockchain and V erify is run to verify the legitimacy of the file. The algorithms are defined as follows.
Du downloads the
from CS. Then, the file F is recovered using the recover key
. Finally, V erify is run to check the legitimacy of file. If V erify outputs 1, the file is output; otherwise, ⊥ is output.
The V erify algorithm is run to verify the validity of F when F is recovered.
3.3. Security model
Suppose that there is an interaction which occurs between an adversary A and the challenger B. The details are summarised as follows.
Init: is chosen by A and sent to B.
Setup: B generates some system parameters SP and sends it to A.
Query1: A can adaptively initiate a query to B about the private key. B runs KGen when receives a key query with the attribute set Att. Then, the private key will be sent to A. Particularly, the only restriction is .
Challenge: A chooses two data ,
with the same bit and sends them to B.
Query2: A can adaptively initiate the same query as .
Guess: A guess b is output.
Definition 3.1
The proposed scheme is selective CPA-secure if there is no adversary can win the above game.
Suppose that there is an interaction which occurs between an adversary A and the challenger B. The details are summarised as follows.
Setup: B runs SETUP and sends SP to A.
Challenge: A selects an attribute set and sends it to B. Then, B runs KGen to obtain
and sends it to A.
Output: The tuple is output, where
is an original ciphertext,
is the blinded key,
is the recover key,
is the tag,
,
are the converted ciphertexts. A wins the game if
.
.
.
Definition 3.2
The proposed scheme is verifiable if there is no adversary can win the above game.
4. Specific construction
4.1. The construction of the proposed scheme
4.1.1. KGC side
: When the system starts, the security parameter ζ is inputted. Then, the security bilinear mapping
is chosen according to ζ. KGC chooses five random elements g, u, h, w, v from
and a random number η. The system parameters SP and the master key MK are shown as follows, where H is a hash function chosen by KGC. Note that SP is public and MK is secret.
(1)
(1)
Du completes registration using the attribute set Att. First, KGC randomly chooses numbers r and
in
, where j is from 1 to n. Then, KGC computes
and
.
(2)
(2)
Second,
and
are computed for each
.
(3)
(3)
Finally, KGC chooses
as the recover key and computes
As a response, Bk and
are returned to Du.
4.1.2. Owner side
The file F is encrypted by Do to protect file privacy. First,
is computed and uploaded to blockchain. Then, Do chooses who can access F and uses it to encrypt the file. A secret value s and n−1 random numbers
are chosen by Do. Then a vector
can be obtained and
. Second, Do computes T,
,
and
as follows.
(4)
(4)
In addition,
,
and
are computed for each row in the matrix M. The details of these parameters are shown as follows.
(5)
(5)
Finally,
is uploaded to CS, where
.
4.1.3. Server side
: The Filter algorithm is run by CS to filter duplicate file before storing file. CS runs the Filter algorithm when multiple files are taken as input. Suppose the input is
and
. The details of the construction are given as follows.
CS computes
and
.
(6)
(6)
If (Equation6
(6)
(6) ) holds,
is filtered and
is input to the Comb algorithm.
: To improve the efficiency of server operation, CS generates some pre-deployed ciphertext
. First, a secret value
and
random numbers
are chosen, where ψ is the number of assumed attributes. Then, the vector
can be obtained. CS randomly chooses
and computes
and
.
(7)
(7)
For each assumed attribute, CS computes
,
and
.
(8)
(8)
Finally, the pre-deployed ciphertext is
.
: CS runs the Comb algorithm to combine the encrypted files so that the legitimate user of the filtered file can be accessed.
is assumed to be the combined access structure. CS computes
and
as follows.
(9)
(9)
(10)
(10)
For each row of
, CS computes
,
,
, and
.
(11)
(11)
(12)
(12)
(13)
(13)
Finally, the combined ciphertext
is stored into the storage pool.
: When BK is received from a legitimate user, CS computes
Finally, the converted ciphertext
is sent to Du.
4.1.4. User side
: When
is received from CS, Du computes key and recovers the file F.
(14)
(14)
Then, V erify is run to verify the legitimacy of F. If V erify output 1, F is legal and output; otherwise, ⊥ is output.
: File legitimacy is verified by determining whether the equation
holds, where Tag is downloaded from blockchain. If it holds, output 1; Otherwise, output 0.
5. Security analysis
5.1. Correctness
Here, the correctness of the server-side conversion process is shown as follows.
5.2. Security proof
Theorem 5.1
The proposed scheme is selectively CPA-secure under the assumption that ACM2013 (Rouselakis & Waters, Citation2013) is a selectively CPA-secure CPABE scheme.
Proof.
We assume that A can break the selectively CPA-secure of the proposed scheme and C is a challenger of ACM2013. Then, a simulator B can be designed to train A. The details of the game are shown as below.
Init: The challenge access structure is sent to B. Then, B sends
to C.
Setup: C generates PK and sends it to B. B sends SP to A, where Pk has the same distribution as SP.
Query1: B builds a table table. A can initiate queries adaptively.
B receives the private key query from A, then passes it to C to obtain SK. B chooses a random number
as the recover key and computes
,
,
,
. B stores
in table.
B checks whether
in table. If so, it returns Bk. Otherwise, it returns ⊥.
Challenge. A chooses two data with same bits and sends to B. Then,
are sent to C to generate the ciphertext
. C randomly chooses
and computes
,
, where
. For each row in
, C computes
,
,
. B computes
and
to A. B runs OutDe to obtain
.
: A outputs a guess c.
We can find that this paper has the same distribution as the ciphertext of ACM2013. The security of ACM is proven under the DBDH assumption. If A can win the above game, then B will successfully use A's method to break the selectively CPA-secure in ACM2013. It means that the DBDH assumption will be broken.
Theorem 5.2
The proposed scheme is verifiable under the assumption that hash function can resist collision.
Proof.
We assume that adversary A can break the verifiability of the proposed scheme. B is a challenger of the proposed scheme. The details of the game are shown as follows.
Setup: B runs SETUP to generate the public parameters SP and the master key MK.
Challenge: A selects an attribute set
and sends it to B. Then, B runs KGen to obtain
and sends it to A.
Output: The tuple is output, where
is an original ciphertext,
is the blinded key,
is the recover key,
is the tag,
,
are the converted ciphertexts. Then, the following conditions hold:
.
.
.
It can be found that A has ,
by verification. It means that
and
, where
. However, hash functions are known to satisfy the collision resistance property. Therefore, the proposed scheme is verifiable.
6. Performance analysis
6.1. Theoretical analysis
Function Comparison. The functional comparison of the schemes is shown in Table . We can find that the proposed scheme is compared with X. Yang and Zhang (Citation2022), Qin et al. (Citation2015) and Cui et al. (Citation2016) in terms of functionality. The proposed scheme has a rich functionality compared to them. Based on the tamper-evident property of blockchain, the proposed scheme achieves efficient decryption and verification. To reduce invalid data in the cloud server, file filtering and file combination are further supported in the proposed scheme. In X. Yang and Zhang (Citation2022), a blockchain-based ABE scheme is proposed. In Qin et al. (Citation2015), hash function is used to verify the decryption result. In Cui et al. (Citation2016), efficient decryption by users is achieved. However, it does not implement verification of the decryption result. Therefore, the proposed scheme is rich in functionality compared with related schemes.
Table 1. Function comparison.
Communication cost comparison: The communication comparison of the schemes is shown in Table . Table compares the communication cost of the proposed scheme with X. Yang and Zhang (Citation2022), Qin et al. (Citation2015) and Cui et al. (Citation2016). is an element size in
,
is an element size in
,
is an element size in
and n is the number of attribute in Att. The size of Bk is
in X. Yang and Zhang (Citation2022) and the size of ours is
. Although the overhead of BK in the proposed scheme is higher than X. Yang and Zhang (Citation2022), our scheme has advantages compared to other schemes. The size of
in the proposed scheme is
and
is used to complete the filtering of files. Compared with Cui2016, the performance of the proposed scheme is similar to that of the scheme. Most of the computational cost of decryption is delegated to an untrusted server, while the data user only needs to perform an exponentiation operation to decrypt a ciphertext. Both Cui et al. (Citation2016) and the proposed scheme can achieve efficient decryption by users and the computational overhead is lightweight. However, based on the characteristics of blockchain, the proposed scheme achieves efficient user verification of the decryption results and ensures the correctness of the file. Therefore, we insist that the proposed solution has good performance.
Table 2. Communication cost comparison.
6.2. Experimental analysis
To further illustrate the performance of the scheme, the experimental simulations was done on a VMware Workstation. All algorithms of the proposed scheme were simulated based on the PBC library.
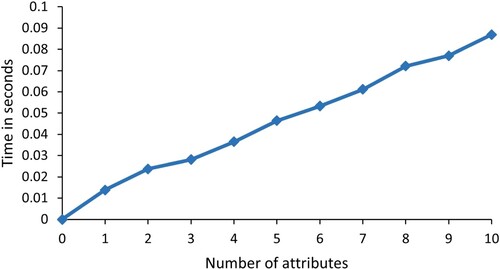
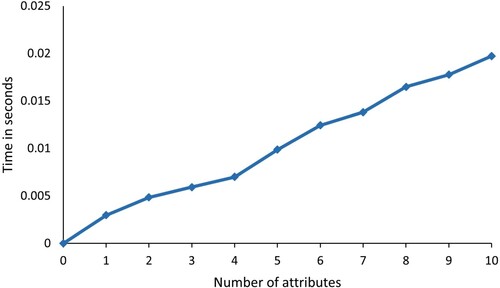
As shown in Figure , we simulated the computational overhead of KGC. In our simulation, we consider the number of Atts from 0 to 10. The number of Atts is reasonable considering the actual application. We can find that the computational overhead of KGen grows as the number of Atts grows. If the error is ignored, the overhead of KGen grows linearly. KGen runtime is 0.086 seconds when the number of Atts reaches 10. This means that it takes only 0.086 seconds to complete user registration for a user assuming he has ten attributes. The user registration overhead of the proposed scheme is acceptable for a cloud storage system. At the same time, the ciphertext combination Comb algorithm is also simulated and the simulation results are given in Figure . We can see that the Comb time overhead is 0.02 seconds when the number of Atts is 10. This means that if the user has ten attributes, it takes only 0.02 seconds for the server to complete the ciphertext combination. The server can complete the combination of data with low latency.
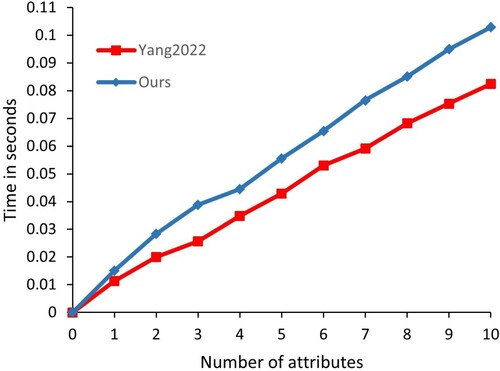
The Enc computation overhead is also simulated and the simulation results are given in Figure . In our simulation, we consider the number of Atts from 0 to 10. The number of user attributes is reasonable considering the actual application. We can find that the computational overhead of both X. Yang and Zhang (Citation2022) and ours grows with the number of Atts. As the number of Atts grows, the proposed scheme has a higher computational overhead than X. Yang and Zhang (Citation2022). However, we can find that the difference between X. Yang and Zhang (Citation2022) and ours is only 0.02 seconds when the number of attributes is 10. We think this is acceptable and the proposed scheme has more functionality compared to X. Yang and Zhang (Citation2022).
7. Conclusion
In this paper, a data sharing scheme using ABE cryptographic primitive is proposed, which further supports deduplication. Blockchain technology is applied to achieve quick verification of ciphertext legitimacy by users. To improve memory space, the data is checked if it is a duplicate ciphertext. Moreover, re-randomisation technology is used to improve the efficiency of combining ciphertexts on cloud servers. Finally, we simulate the algorithm of the proposed scheme on the PBC library and the experimental results show that it achieves a balance between usability and performance.
Disclosure statement
No potential conflict of interest was reported by the author(s).
Additional information
Funding
References
- Bethencourt, J., Sahai, A., & Waters, B. (2007, May 20–23). Ciphertext-policy attribute-based encryption. 2007 IEEE Symposium on Security and Privacy (SP’07), Berkeley, CA, USA.
- Cheung, L., & Newport, C. (2007, November 2). Provably secure ciphertext policy ABE. 14th ACM Conference on Computer and Communications Security 2007, Alexandria Virginia, USA.
- Cui, H., Deng, R. H., Li, Y., & Qin, B. (2016, September 26–30). Server-aided revocable attribute-based encryption. Computer Security–ESORICS 2016: 21st European Symposium on Research in Computer Security, Heraklion, Greece.
- Deebak, B., Memon, F. H., Khowaja, S. A., Dev, K., Wang, W., Qureshi, N. M. F., & Su, C. (2022). Lightweight blockchain based remote mutual authentication for AI-empowered IoT sustainable computing systems. IEEE Internet of Things Journal, 1(2022), 1–1. https://doi.org/10.1109/JIOT.2022.3152546
- Ge, C., Susilo, W., Baek, J., Liu, Z., Xia, J., & Fang, L. (2021a). Revocable attribute-based encryption with data integrity in clouds. IEEE Transactions on Dependable and Secure Computing, 19(5), 2864–2872. https://doi.org/10.1109/TDSC.2021.3065999
- Ge, C., Susilo, W., Baek, J., Liu, Z., Xia, J., & Fang, L. (2021b). A verifiable and fair attribute-based proxy re-encryption scheme for data sharing in clouds. IEEE Transactions on Dependable and Secure Computing, 19(5), 2907–2919. https://doi.org/10.1109/TDSC.2021.3076580
- Green, M., Hohenberger, S., & Waters, B. (2011, August 8–12). Outsourcing the decryption of abe ciphertexts. USENIX security symposium, San Francisco, CA.
- Hohenberger, S., & Waters, B. (2014, March 26–28). Online/offline attribute-based encryption. Public-Key Cryptography–PKC 2014: 17th International Conference on Practice and Theory in Public-Key Cryptography, Buenos Aires, Argentina.
- Jammula, M., Vakamulla, V. M., & Kondoju, S. K. (2022). Hybrid lightweight cryptography with attribute-based encryption standard for secure and scalable IoT system. Connection Science, 34(1), 2431–2447. https://doi.org/10.1080/09540091.2022.2124957
- Li, J., Jia, C., Li, J., & Chen, X. (2012, October 29–31). Outsourcing encryption of attribute-based encryption with mapreduce. Information and Communications Security: 14th International Conference, Hong Kong, China.
- Li, J., Sha, F., Zhang, Y., Huang, X., & Shen, J. (2017). Verifiable outsourced decryption of attribute-based encryption with constant ciphertext length. Security and Communication Networks, 2017(2017), 1–11. https://doi.org/10.1155/2017/3596205
- Li, X., Jiang, P., Chen, T., Luo, X., & Wen, Q. (2020). A survey on the security of blockchain systems. Future Generation Computer Systems, 107(2020), 841–853. https://doi.org/10.1016/j.future.2017.08.020
- Liu, S., Yu, J., Xiao, Y., Wan, Z., Wang, S., & Yan, B. (2020). BC-SABE: Blockchain-aided searchable attribute-based encryption for cloud-IoT. IEEE Internet of Things Journal, 7(9), 7851–7867. https://doi.org/10.1109/JIoT.6488907
- Ma, H., Xie, Y., Wang, J., Tian, G., & Liu, Z. (2019). Revocable attribute-based encryption scheme with efficient deduplication for ehealth systems. IEEE Access, 7(2019), 89205–89217. https://doi.org/10.1109/Access.6287639
- Ma, J., Li, T., Cui, J., Ying, Z., & Cheng, J. (2021). Attribute-based secure announcement sharing among vehicles using blockchain. IEEE Internet of Things Journal, 8(13), 10873–10883. https://doi.org/10.1109/JIOT.2021.3050802
- Qin, B., Deng, R. H., Liu, S., & Ma, S. (2015). Attribute-based encryption with efficient verifiable outsourced decryption. IEEE Transactions on Information Forensics and Security, 10(7), 1384–1393. https://doi.org/10.1109/TIFS.2015.2410137
- Rahulamathavan, Y., Phan, R. C. W., Rajarajan, M., Misra, S., & Kondoz, A. (2017, December 17–20). Privacy-preserving blockchain based IoT ecosystem using attribute-based encryption. 2017 IEEE International Conference on Advanced Networks and Telecommunications Systems (ANTS), Bhubaneswar, India.
- Rouselakis, Y., & Waters, B. (2013, November 4–8). Practical constructions and new proof methods for large universe attribute-based encryption. Proceedings of the 2013 ACM SIGSAC conference on Computer & communications security, Berlin.
- Sahai, A., & Waters, B. (2005, May 22–26). Fuzzy identity-based encryption. Advances in Cryptology–EUROCRYPT 2005: 24th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Aarhus, Denmark.
- Tu, S., Waqas, M., Huang, F., Abbas, G., & Abbas, Z. H. (2021). A revocable and outsourced multi-authority attribute-based encryption scheme in fog computing. Computer Networks, 195(2021), Article 108196. https://doi.org/10.1016/j.comnet.2021.108196
- Wang, C., Shen, J., Lai, J. F., & Liu, J. (2020). B-TSCA: Blockchain assisted trustworthiness scalable computation for V2I authentication in VANETs. IEEE Transactions on Emerging Topics in Computing, 9(3), 1386–1396. https://doi.org/10.1109/TETC.2020.2978866
- Wang, C., Zhou, T., Shen, J., Wang, W., & Zhou, X. (2023). Searchable and secure edge pre-cache scheme for intelligent 6G wireless systems. Future Generation Computer Systems, 140(2023), 129–137. https://doi.org/10.1016/j.future.2022.10.012
- Wang, H., & Song, Y. (2018). Secure cloud-based EHR system using attribute-based cryptosystem and blockchain. Journal of Medical Systems, 42(8), 1–9. https://doi.org/10.1007/s10916-018-0994-6
- Wang, W., Yang, Y., Yin, Z., Dev, K., Zhou, X., Li, X., Qureshi, N. M. F., & Su, C. (2022). BSIF: Blockchain-based secure, interactive, and fair Mobile crowdsensing. IEEE Journal on Selected Areas in Communications, 40(12), 3452–3469. https://doi.org/10.1109/JSAC.2022.3213306
- Wu, Z., Huang, H., Zhou, Y., & Wu, C. (2022). A secure and efficient data deduplication framework for the internet of things via edge computing and blockchain. Connection Science, 34(1), 1999–2025. https://doi.org/10.1080/09540091.2022.2090514
- Xiao, M., Li, H., Huang, Q., Yu, S., & Susilo, W. (2022). Attribute-based hierarchical access control with extendable policy. IEEE Transactions on Information Forensics and Security, 17(2022), 1868–1883. https://doi.org/10.1109/TIFS.2022.3173412
- Xu, R., Joshi, J., & Krishnamurthy, P. (2019). An integrated privacy preserving attribute-based access control framework supporting secure deduplication. IEEE Transactions on Dependable and Secure Computing, 18(2), 706–721. https://doi.org/10.1109/TDSC.8858
- Yang, H., Shen, J., Lu, J., Zhou, T., Xia, X., & Ji, S. (2021). A privacy-preserving data transmission scheme based on oblivious transfer and blockchain technology in the smart healthcare. Security and Communication Networks, 2021(2021), 1–12. https://doi.org/10.1155/2021/5781354
- Yang, X., & Zhang, C. (2022). Blockchain-based multiple authorities attribute-based encryption for EHR access control scheme. Applied Sciences, 12(21), 10812. https://doi.org/10.3390/app122110812
- Zhang, L., You, W., & Mu, Y. (2021). Secure outsourced attribute-based sharing framework for lightweight devices in smart health systems. IEEE Transactions on Services Computing, 15(5), 3019–3030. https://doi.org/10.1109/TSC.2021.3073740
- Zhang, L., Zou, Y., Yousuf, M. H., Wang, W., Jin, Z., Su, Y., & Kim, S. (2022). BDSS: Blockchain-based data sharing scheme with fine-grained access control and permission revocation in medical environment. KSII Transactions on Internet and Information Systems (TIIS), 16(5), 1634–1652. https://doi.org/10.3837/tiis.2022.05.012
- Zhang, T., Shen, J., Lai, C. F., Ji, S., & Ren, Y. (2023). Multi-server assisted data sharing supporting secure deduplication for metaverse healthcare systems. Future Generation Computer Systems, 140(2023), 299–310. https://doi.org/10.1016/j.future.2022.10.031
- Zhang, T., Wang, C., & Chandrasena, M. I. U. (2022, October 16–18). Efficient attribute-based proxy re-encryption for secure deduplication. Security and Privacy in Social Networks and Big Data: 8th International Symposium, Xi’an, China.
- Zheng, H., Shao, J., & Wei, G. (2020). Attribute-based encryption with outsourced decryption in blockchain. Peer-to-Peer Networking and Applications, 13(5), 1643–1655. https://doi.org/10.1007/s12083-020-00918-1
- Zheng, Z., Xie, S., Dai, H. N., Chen, X., & Wang, H. (2018). Blockchain challenges and opportunities: A survey. International Journal of Web and Grid Services, 14(4), 352–375. https://doi.org/10.1504/IJWGS.2018.095647
- Zhou, Z., & Huang, D. (2012, October 22–26). Efficient and secure data storage operations for mobile cloud computing. 2012 8th international conference on network and service management (cnsm) and 2012 workshop on systems virtualiztion management (svm), Las Vegas, NV, USA.