?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.Abstract
The concept of the Internet of Medical Robotics Things (IoMRT) is where intelligent robots assess surrounding events, combine information from their sensors, use both local and dispersed intelligence to determine the best course of action, and move or command objects. Telesurgery is one application of IoMRT (TS). With 5G-enabled Tactile Internet (TI) enabling telesurgery (TS), there is ample opportunity to provide exceptional, accurate, ultra-responsive, and real-time virtual surgical procedures. The potential for accurate surgical diagnosis involving the exchange of patient electronic medical records (EMR) with several doctors using an assistant robot (AR) could be greatly useful in the medical field. As a part of this, permission delegation has emerged as a novel approach for data sharing in TI. Robust control of access guidelines combined with a configurable permission scheme promise secure EMR exchange. The present research proposes a multi-hop permission delegation strategy for EMR exchange based on blockchain technology and with configurable delegation depth. Furthermore, the original EMRs are stored on the interplanetary file system (IPFS). Permission delegation uses smart contracts and proxy re-encryption technology. Attribute-based encryption, which offers fine-grained management of access, is used to guarantee data security. Blockchain is also utilized to accomplish immutability and traceability. Delegators may regulate the depth of delegation by using smart contracts. The suggested approach satisfies the intended aims, according to analysis of the protocol. Lastly, the Ethereum test chain is used to assess and put the suggested method into practice. The outcomes of the conducted experiments demonstrate that the suggested protocol operates better than the competitors.
1. Introduction
Globally, medical care is a critical issue for every person and every country. Doctors oversee and keep an eye on each patient's health, either in person or virtually. In the past, this was achieved manually, where patients had to come to the hospital to speak with doctors about their concerns. This meant it was an expensive, difficult, and drawn-out procedure. Later, as a result of developments in technology for communication, physicians can now virtually expand their practices using a novel approach known as telemedicine (Tanwar et al., Citation2020). This makes it easier to provide real-time healthcare services remotely. As a consequence of rapidly developing information technology, the Internet of Medical Robotic Things (IoMRT) is growing popular in the medical field. For example, telesurgery (TS), sometimes known as remote surgery, is one of the most interesting areas in the field of telemedicine (Gupta et al., Citation2020). Using surgical robots at one end, telesurgery helps physicians to perform live surgery remotely over wireless communication channels (WCC). Real-time and live applications, such as TS, do not accept any delay or inaccurate patient information and thus it may lead to the death. In this work, patient information that is shared by the delegator is the key point for investigating. Sharing electronic health records (EMRs) enables physicians to provide patients with excellent medical treatment (Alamer & Basudan, Citation2022; Basudan, Citation2022; Gao et al., Citation2022; Liu et al., Citation2023). An assistant robot (AR) is used to distribute medical history data for this purpose. Consequently, it has progressively decreased medical resource asymmetry, expenses, and isolated islands of medical knowledge, while increasing efficiency and modernizing the siloed nature of the conventional medical industry.
EMRs are subject to stringent privacy control measures; data security is therefore essential for data sharing (Agarwal et al., Citation2023; Alamer, Citation2024b, Citation2024a; Alamer & Basudan, Citation2022; Das & Namasudra, Citation2023; Xu et al., Citation2023). Patients ought to be in complete control of their health information. Generally, access control is an essential strategy for guaranteeing data security in networks that share data. The majority of access control systems in use today depend on permission from the data owner. The ongoing communication among data owners and users is necessary for such systems. Patients find it challenging to stay online all the time and are opposed to repeated disruption. Granting authorization to a delegatee, or an AR, in order to relieve the data owners of some of their burden, is a viable alternative. Scherrer and Perrig (Citation2021) describes in details the security, privacy, trust, and anonymity issues. Furthermore,in order to use simulated real-life in cybersecurity scenarios, Deng et al. (Citation2021) applied Problem-based learning with Knowledge Graph (KG)-based guidance for hands-on labs in cybersecurity training by using an online laboratory environment. In the SDN-based Iot models, Wani and Khaliq (Citation2021) proposed an intrusion detection system for to address the issues of an optimum protection against prevailing powerful threats in cyber world that produced in lightweight security protocols.Regarding intrusion detection systems, Hooshmand and Hosahalli (Citation2022) proposed a model using one-dimensional in Convolutional neural networks architecture. They applied transformation the performance towards the task of network anomaly detection in cybersecurity. By granting flexible permission assignment to other users, like physicians, access control can be implemented.
The majority of permission delegation systems are cloud-based that also offers significant amounts of storage capacity and thus the cloud can make it easier for different stakeholders to share information (Sivan & Zukarnain, Citation2021). Using the Amazon cloud platform, Joshi et al. (Citation2019) created an authorization system for EMR services that enabled medical service providers to receive permissions from cloud-based EMRs. The ciphertext-policy attribute-based encryption (CP-ABE) library was utilized in this project. By decentralizing various levels of key publishing authority, Ahuja and Mohanty (Citation2017) integrated CP-ABE with an organizational framework to create an extendable permission delegation system. In order to address the issue of key delegation misuse during the authorization delegation procedure, the cloud was deployed as a trusted storage solution. Chen et al. (Citation2020) also suggested a ciphertext-policy hierarchical attribute-based encryption system called CP-HABE-AKDA, which guards against key-delegation misuse. To guarantee key delegation privacy, a rigorous top-to-bottom key delegation was implemented using an ordered graph. In addition, the concept for implementing searchable functionalities using cloud computing was initially put up by Xu et al. (Citation2019) and may achieve multi-keyword and key range searches in digital medical networks. However, there was a limitation in that the data was limited to being accessed by patients or their doctors. Subjects were given the flexibility to organize multi-hop delegation paths based on their judgments, in a study from Wang et al. (Citation2021). Healthcare practitioners may search for and access data that is prioritized from high to low based on urgency by using autonomous delegation of authorization. However, because the cloud is an observant but reliable semi-entity, cloud-based permission delegation systems are susceptible to security threats including collusion attacks and single point of failure. Despite this, research indicates the use of blockchain is a viable solution to address these issues (Zhang & Lin, Citation2018).
Decentralization, openness, anonymity, and robustness are some benefits of blockchain. Blockchain is extensively utilized in the domains of finance, healthcare, and the internet of vehicle (IoV) (Alamer, Citation2024a; Assiri, Citation2023; Haleem et al., Citation2021; Li et al., Citation2023; Liu et al., Citation2023; Sharma et al., Citation2023; Wang et al., Citation2022; Xu et al., Citation2023; Yaqoob et al., Citation2021). Permission delegation was first included in the Bitcoin blockchain by researchers, who also tokenized permissions and managed token transfers using transactions (Zyskind & Nathan, Citation2015). Thus, the integration of federated learning (FL) and blockchain leads to a new paradigm which potentially transforms into decentralized, secure, and privacy-enhancing systems (Alamer, Citation2024b). Liu et al. (Citation2023) used generative adversarial networks, blockchain, and differential privacy to create a new privacy protection framework (BFG) for decentralized environments. The framework can effectively resist attacks and successfully avoid a single point of failure. A blockchain application for a healthcare management system with strict authentication was presented by Deepa et al. (Citation2022). The SHA-256 hash technique was utilized to provide the network with strong security protocols through strict authentication in the cloud. Ethereum blockchain technology is used in this application to provide decentralized storage. Using Internet of Things resources, Alamer (Citation2024b) presented a privacy-preserving federated learning with a secure collaborative for malware detection models. To improve the security of the delegation process, Deebak and Hwang (Citation2023) included the period's validation in the permission procedure. Lacking the support of any reliable third parties, Chen et al. (Citation2023) established broad capabilities via smart contracts for the IoT by employing blockchain events. Further to this, Wang et al. (Citation2023) committed to solve the problem of unauthorized access weaknesses in permission delegation. Additionally, Sharma et al. (Citation2023) presented a Distributed Application (DA) that protects privacy and uses blockchain technology for the creation and upkeep of healthcare certificates. In order to generate and issue medical records, the distributed program acts as an interface between the blockchain network and system objects such as healthcare facilities, verifiers, and conventional authorities. In a cloud context, Vidhya and Kalaivani (Citation2023) employed blockchain to finish permission delegation, but they were unable to grant access to additional users. A Blockchain-based architecture for health data sharing was proposed by Sabrina et al. (Citation2023) to facilitate the sharing of electronic health records between clinicians and patients inside the country's healthcare system. The scenario was used to create a safe Blockchain-based data exchange episode in a lab simulation setting, which should spark a new trend of patients and healthcare providers exchanging electronic health records. Using attribute-based encryption (ABE), Srinivas et al. (Citation2023) introduced a unique framework to store and share the data in a safe manner. Still, these systems only account for one-hop delegation. The benefit of the decentralized InterPlanetary File System (IPFS) protocol is modified in the suggested method in order to facilitate data storage in a blockchain setting. Consequently, a distributed data storage-based paradigm that is dependable, safe, and effective is needed.
Rights of access are not restricted to single-hop permission delegation in real-world healthcare circumstances. Patients struggling financially look for organizations and groups that might be willing to pay for their medical records. Owing to their physical and energetic constraints, patients lack sufficient energy and time to individually answer each permission request. It is necessary to be granted access permission in order to assign others such permission. Patients utilizing delegators who are able to assign authority to more individuals. Delegating multiple hop access rights can increase data availability flexibility while lessening the need for authorization from data owners. Finding a balance between data security and permission delegation is crucial.
To address these issues, the EMR sharing system develops a multi-hop permission delegation approach with configurable delegation depth. A patient may assign access privileges to an assignee. To optimize the significance of the information and expand the versatility of the information exchange system, delegates with access rights can subsequently grant rights to additional users, like surgeons. A transmission chain is formed by authorized users. Patients can make certain that they oversee their data on the transmission chain by configuring policies for access control and delegation depth. The principal contributions are outlined below.
To facilitate the exchange of data, a multi-hop delegation paradigm combining blockchain and IPFS is developed. The initial EMR is transmitted to IPFS for distributed storage, with symmetric encryption techniques utilized to guarantee data security during storage. The symmetric key is encrypted using CP-ABE and a policy monitoring access control is established to limit the delegatee's characteristics. The intended ciphertext conversion is completed with the help of the proxy re-encryption technique. Only those who have paid for the service and complied with the terms of access are able to decode this. Blockchain technology assures data storage and transaction security through the utilization of smart contracts that faithfully carry out multi-hop delegation supervision and ciphertext conversion.
A method of encryption known as ciphertext-policy attribute-based proxy re-encryption (CP-PRABE) is developed, enabling multi-hop delegation and offering users granular access. The patient formulates the policy for access on the ciphertext and uses CP-ABE to provide fine-grained access control. In order to accomplish effective ciphertext conversion without altering the patient's access policy, the proxy re-encryption key construction is enhanced. As a result, computing overhead is greatly reduced. Through smart contracts, the patient determines the degree of delegation of access authority for each data transfer chain. By doing this, throughout the multi-hop delegation process, the patient maintains control over the data.
The deployed smart contracts are the access smart contract (ASC), the delegation depth smart contract (DDSC), and the delegation smart contract (DSC). The patient can restrict the delegatee's ability to access data via DDSC by changing the delegation depth for each delegatee. A delegatee with zero delegation depth can no longer exchange data. DSC has the ability to convert ciphertext into forms that different delegatees can decode and fill out. Furthermore, there is a substantial decrease in communication overhead as this method does not call for contact among the delegator and delegatee. In order to provide identity verification, ASC searches delegation data within a predetermined time frame. Furthermore, the Ethereum platform is used to implement the smart contracts, and assessments are carried out regarding the protocol effectiveness and smart contract time cost.
The structure of this article is as follows. The problem description, system architecture, and security objectives are presented in Section 2, while the fundamental ideas of the proposed authentication protocol are shown in Section 3. Section 4 presents the proposed protocol, which is a blockchain-based multi-hop permission delegation mechanism. Section 5 reports a security analysis, and Section 6 assesses the suggested protocol's performance. This work is summarized in Section 7.
2. Problem statement
The problem statement section analyzes the system architecture and also conducts an in-depth examination of the security threats and finally outlines the goals.
2.1. System architecture
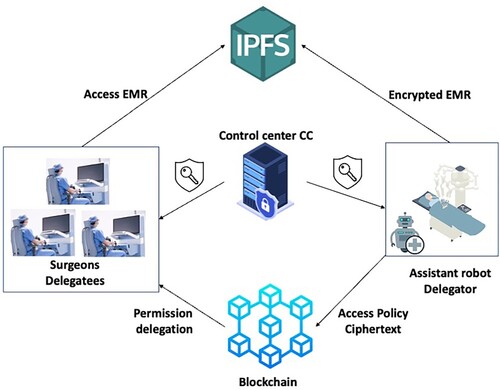
Figure illustrates the system model, which includes the blockchain network, IPFS, control center (CC), delegator, and delegatees. Smart contracts and blockchain ledgers make up the blockchain network. Presume that the data user in the specified blockchain has the authority to grant access to the EMRs. The protocol encrypts HER and stores them in IPFS using symmetric encryption. Additionally, the ciphertext-policy attribute-based encryption transforms the symmetric key and file location data, which is then recorded in the blockchain. The network and proxy re-encryption facilitate delegation rights between the stakeholders involved as the smart contract manages the delegation depth. For example, a patient may direct to a hospital for important diagnosis that may lead to surgical intervention. He can have the AR from the hospital to be alongside with him and can authorize him to communicate with surgeons from external hospitals (telesurgery). In this way, the AR has the access for patient health records and thus it can delegate different surgeons to access the patient health records.
Control center (CC) generates system parameters which are then keyed in into the blockchain and can be accessed publicly. The delegatees are given private keys based on the specific features of the CC.
A delegator may be a patient or any authorized user. In the proposed system model, the patient can provide two types of authorization for the AR. First authorization is to allow the AR to access the EMRs. Furthermore, the AR will also have a right to delegate other surgeons to access the EMRs. Second authorization is related to data generated during surgery. Patient can also authorize the AR to collect the data during surgery and store it in the blockchain. They are the ones who generate, upload and preserve the encrypted EMRs. Besides, they are in charge of designing control policies and delegating permission to the surgeons who may need to access the EMRs. They are also the ones who handle the delegation depth. Authorized users such as AR, can choose to re-delegate their access permission.
Delegatees are the other data users like the surgeons who aim to access EMRs from delegators. They must conform to the access control policies because they can be granted access rights and assigned authority by the delegator. They can either be a new delegator who will deploy their access rights.
InterPlanetary File System (IPFS) is a distributed storage. It can safely share and preserve different types of files if it has the hash value designed to match he file content. All the EMRs that are encrypted are stored in the IPFS and the users can access them using the hash address provided.
Blockchain and smart contracts. Blockchain preserves the key ciphertext, re-encrypted keys and system parameters. On the other hand, smart contracts provide re-encrypted ciphertexts and manage the depth of delegation.
2.2. Security threat
In the system model, the blockchain is defined as a distributed technology used for permanent data storage. The smart manages preset functions but permanently operates after its set. The delegator is the only person that can be fully trusted with the system. When there is a malicious threat or attack, the processes are altered with and the EMR are at risk. There are instances where the delegatee collaborates with other data users are forcefully try to gain the right over the data.
2.3. Security goals
In order to address this threat, the protocol seeks to achieve these goals:
To maintain data confidentiality and integrity. The system aims to protect data integrity and confidentiality as they share the data. In instances where there are gaps on the integrity of the records, the medical officers are likely to offer substandard treatment or even result to medical complications. Besides, it is a privacy violation to leak the medical information of the patient. This also affects the healthcare institution and the medical experts involved because their reputation is at stake. Therefore, it is important for only the users and authorized individuals to gain access to the EMRs because they cannot risk tampering with them.
To resist conspiracy attacks. There are various semi-trusted agencies such as the attacker collaborating with the proxy to access the data or a multi-hop delegation situation which enables patients or healthcare providers to private access the data by working with other delegatees. Thus, the system should be made to protect the patient data even if there are attempts of malicious attacks that conspire with the authorized users.
Fine-grained access control. There must be a fine-grained access control which can be achieved by only allowing the delegator to manage the policies on data access. It is impossible for the external attackers to get the access that is determined by the original owner.
Multi-hop delegation. It is important to design this to minimize the user's workloads. There are also instances when the patients find it challenging to manage the delegation depth. Therefore, it is recommended to implement a multi-hop delegation system that will facilitate patient control and security.
3. Preliminaries
3.1. Bilinear pairing
Definition 3.1
Bilinear Pairing
Assume that G is a prime order additive group of order p. P is the generator of G. is a multiplicative cyclic group of the same prime order p. An
bilinear map If
meets the following criteria, it can be considered an admissible bilinear map.
Bilinear: For all
,
.
Nondegenerate: There exists
such that
.
Computable:
is efficiently computable.
3.2. Complexity assumptions
The access structure for linear secret-sharing schemes (LSSS) is defined, where φ is an injective function from
features, and τ is a
matrix. Take into consideration the column vector
, which represents the vector of l shares of the secret s, s being the secret to be shared, and
representing the random choices. It is the share of
that is
. Since S meets the access structure, defined as
, let us assume that
is an authorized set. Then, if
are legitimate shares of any secret s, then there are constants
such that
.
3.3. Ciphertext-policy attribute-based proxy re-encryption (CP-ABPRE) framework
The implementation of a multi-hop CP-ABPRE protocol which has below processes (Liang et al., Citation2013):
: Consider the security parameter η and an attribute universe Uni as input, it outputs the public parameter
and has a master secret key msk.
: Given the public parameter
, the master key msk and an attribute set S as input, the private key
is outputted.
: In order to send the ciphertext, it outputs a re-encryption key
upon receiving
, the secret value
for user j.
: It produces an original ciphertext
that can be further encrypted after receiving
, an access structure
, and plaintext m.
: It outputs the
level ciphertext
given the input of the
level ciphertext
, the public parameter
, and a re-encryption key
.
: The plaintext m is output given the input of an original ciphertext
, the private key
, and the public parameter
.
: Given the public parameter
, the private key
and
level ciphertext
as input, the plaintext m is outputted.
3.4. Blockchain
This is a technology that supports the crypto-currency in the form of a Bitcoin (Nakamoto & Bitcoin, Citation2008). Its features include decentralized, irreversible and programmable. In other words, it is defined as a data storage and verification mechanism that is managed by encrypted data blocks. There is also an agreement algorithm designed from a distributed nodes that collect and manage all the data uploaded in the system. The smart contract or automated scripts are also used in the system to manage the data. The technology can be grouped into, public, private, and consortium (Yuan & Wang, Citation2016). Consortium blockchain can only be accessed by the consortium users. These people control those who access the transactions based on the regulations that they set. Moreover, smart contracts are also decentralized and autonomous. They are automatically integrated after the contract is officially implemented. The smart contracts are implemented using the decentralized storage and the confirmation program codes. This makes it possible to confirm the fairness and impartiality of the system (Bodkhe et al., Citation2020). The propose protocol uses blockchain to delegate permission and manage all the important information.
4. Proposed protocol
This section provides a summary of the proposed protocol as illustrated in Figure , followed by discussing the protocol in detail and smart contract design.
4.1. Protocol overview
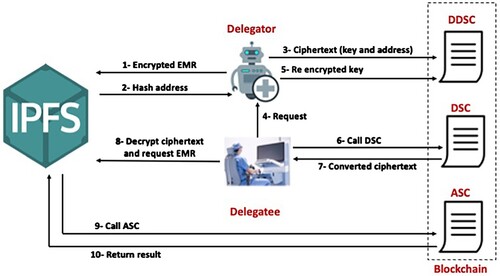
The system workflow is consider as follows:
The system setup stage is where all the users register their account in the consortium blockchain for them to access the services. The CC generates limits and attribute keys
that are provided to the people depending on their features. Then the patients upload their EMR
that is encrypted to the IPFS which is hashed and passed to the hash address
. After this, they send the encrypted symmetric key and hash address
. There are nodes hat verify the data that has been uploaded and creates another block based on a consensus mechanism.
The delegation stage is where the data users who seek to access the data send their request by sending a fee to the delegator. The DDSC confirms if the user is authorized to re-deploy. If it fails, then they are refunded their payment. If it agrees the delegator that had re-assigned the data rights creates a matching re-encryption key
and sends it to the blockchain having the address of the user. They also create the depth De of delegation for the delegatee. After the DSC gets the re-encryption key
, it confirms that the ciphertext
located in the upper part is secure. The DSC re-encrypt it
with
if he confirms that all the conditions are addressed. This verified delegatee can be tasked as the new delegator to realize multi-hop delegation. They are the ones who would then handle the same procedure in case there are other individuals who seek delegation permission. However, this automatically stops once their depth De of delegation completes and gets to zero.
The final is the data sharing stage whereby the delegatee receives the symmetric key and hash address after they have decrypted the ciphertext
. They then transfer the access request to IPFS while attaching it to the address. The IPFS generates the access smart contract (ASC) that examines if they have the permission to get the data. It then passes the result and the delegatee gets the original ciphertext
from IPFS. They then decrypt it.
4.2. Protocol description
System setup stage. This stage is done by CC and performs the following:
The system takes into account the attribute universe Uni and a security parameter η. Next, the CC chooses random generators
, and
, as well as a random value
.
Chooses a bilinear pairing
, and sets the following three hash functions:
,
,
.
Public parameters for the system are as follows:
.
All users must register with the CC, including delegators and delegatees. Based on these system users' characteristics, the CC issues private keys. To be more specific, it selects a random value
and computes
,
,
, where χ is an attribute in the attribute set S.
CC transmits the private key
to these user using a secure channel. They must ensure that their private keys are secure.
Delegation stage. This stage is done either by the patient or AR and performs the following:
Encrypting the original EMR.
– Using symmetric encryption, the delegator encrypts the original EMR before sending it to IPFS. The hash address
of these data is sent by the IPFS.
– The delegator delivers
to the system after coding the symmetric key
and hash address
into
.
– An LSSS
is chosen by the delegator; τ is a
matrix, and
is the function that connects the rows of τ to features.
– The delegator sets
and a random vector
where
. He/she also sets
for i=1 to l, where
is the vector equivalent to the
row of τ.
– The delegator selects
, set
.
– Finally, the delegator generates original ciphertext
are the attributes that make up the access system
.
Re-encryption keys and re-encryption ciphertext. Given the
conversion of the level ciphertext. It is only the
delegatee that has the freedom to decrypt it. The stage entails producing re-encryption keys and re-encryption ciphertext. Anyone wanting to access the EMR transfer tokens to the delegator using an account activating DDSC. This DDSC determines the level of the delegation depth
. If the delegation depth is zero, they are refunded their payment. The ReKeyGen performs as includes:
During the delegation stage, the system signal DSC which concludes the proxy re-encryption process. This procedure can either re-encrypt the– The delegator uses the re-encryption keys for the requesters other than the private key generation. The delegator examines the credibility status of the requesters to identify if they can achieve the multi-hop delegation. The delegator is also in charge of choosing the maximum number of users to delegate and he delegation depths using parameter De.
– Delegatees that want an access rights requests it from the delegator, who then sends then a secret value
for user j, and signs the
.
– The delegator sends
to the user and then sends to DSC by generating the re-encryption key
.
– The delegation depth
is set and transmitted to the DDSC.
ciphertext to the
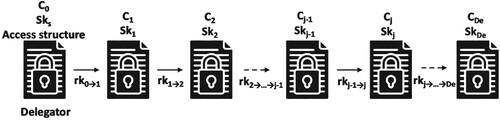
, or re-encrypt the ciphertext that was originally delivered to the first stage. The
delegation's re-encryption procedure is demonstrated as an example in the following. The multi-hop delegation techniques are the same in the actual world; Figure shows how they relate to one another. Re-encrypt
's
ciphertext to
's ciphertext as follows:
and re-encryption key
, where
Verify the– ,
– ,
– ,
– ,
– ,
– .
ciphertext by determining if the ensuing equations are true.
(1)
(1)
(2)
(2)
(3)
(3) Unless Equation Equation1
(1)
(1) holds, output ⊥. Otherwise, continue to compute the following:
Data sharing stage. This stage discusses the process of data access using the users, who can be delegator and the delegatee. The phase covers the following algorithms:
DecByDelegator. Decryption by the delegator DecByDelegator, the delegator uses their provate key to decrypt the original ciphertext. Parse the original ciphertext
, and the private key
(for an attribute set S) as
. Output ⊥ in the event that Equation Equation1
(1)
(1) fails. As an alternative, keep calculating the following:
– Compute
, and
.
– Output
if
, and output ⊥ otherwise.
DecByDelegatee. Delegatees' decryption DecByDelegatee: The delegatees use the private keys they were given to decrypt the ciphertext after they have the re-encrypted version of the attributes matched to the access policies. This results in the first level ciphertext's
description, which is subsequently sent to the multi-hop delegated ciphertext decryption.
Given the re-encrypted ciphertext
and the private key
, and compute the following:
– Compute
, and
.
– Output
if
, and output ⊥ otherwise.
Data storage stage. In this stage, the AR will collect data about patients during their surgery and the data will be encrypted using the encrypted scheme in (Nie et al., Citation2022). Following that, a transaction containing the ciphertext will be transmitted to the patient's blockchain profile.
Correctness:
4.3. Smart contract
Smart contracts are useful in assisting the system to achieve all the requirements. The interface between smart contracts for Ethereum involves the following phases:
The delegators are required to create the depth of delegation for their delegatees using DDSC. The DDSC then authenticates if all the delegators are qualified before they are permitted to re-delegation. Besides, this is only possible if they achieve all the conditions under delegation depth. A new encryption key is transmitted to DSC and it completes the delegation algorithm of re-encrypting the ciphertext for the delegatee to decrypt. The delegatee requests IPFS to send a file address as the IPFS signals the ASC to verify if the delegatee is authorized to access it.
The primary functions of the smart contract are to authorize, delegate and verify. A user
transfers token to a delegator
or the patient through blockchain in order to get the EMR of the patient. The system performs the authorize function during a transaction. This is achieved when the DDSC examines if the delegation depth level
of the delegator and if it is more than zero. The delegator is permitted to produce a re-encryption key
for the user's use if they have enough delegation depth. With the use of DDSC, the delegator additionally assigns delegation depth
to the delegatee. The delegatee's depth of delegation is stored by DDSC, which also displays the progress to the delegator. The delegation function in the DSC is then generated by
, and it uses the Delegation algorithm to change the ciphertext. The function then undergoes IPFS whereby after the system gets the access request from the user, it performs the verifying function. This helps to determine if the system contains all the records on blockchain if the process takes less than ten minutes to complete. The results are then returned to the IPFS.
For more information regarding security definition and security Proof, it is worth pointing out to Deng et al. (Citation2020), Wang and Zhang (Citation2020), Gao et al. (Citation2022) in order to avoid rewriting the wheel.
5. Security analysis
The security analysis part examines how this protocol accomplishes its anticipated goals as required. Then, comparisons of security properties with other competitive schemes are described.
5.1. Security goals achievements
The anticipated scheme has the potential to attain data confidentiality and integrity. This is achieved through the use of encryption and signatures. Encryptions in this case entail using both symmetric and attribute-based proxy re-encryption. After the EMRs are encrypted using the symmetric key, they are condensed into the IPFS. It is the delegator that overlooks the access of the key and provides the file address using the CP-ABPRE. Most importantly, it is only the symmetric key and the file location that can facilitate the de-encryption of the original data. The delegator then includes a signature into the algorithm. They are then stored in blockchain Exactly, the security of the
ciphertext
is determined by the equation
. The symmetric key
is placed in
, and other limits are designed to ensure the safety of the original information. This is evident from the Equation Equation3
(3)
(3) , whereby, is a signature.
are controlled by F. The honesty of
is controlled by
as seen in the Equation Equation2
(2)
(2) which guarantees that the access policy are protected and effective. Altering the data in any way results to an invalid equation Equation1
(1)
(1) , which forces the system to continue with the decryption process.
This proposed scheme can attain collusion resistance. There are possibilities that malicious attackers may collaborate with proxy to get the private information if these existing proxy schemes are used. This is because they are re-encrypted. Thus, this proposed one uses trustworthy blockchain instead of proxy which makes it impossible to conspire with intruders. There are also chances that the intermediate authorized delegatee may conspire with system attackers and get the patient information. This is achieved by ensuring that the ciphertext changes into a strong encryption form that only the authorized user can reach. This is done during the delegation phase. Besides, this system makes it impossible for intruders to decrypt the data even if the delegatee publicizes their access features. Even if the file location and symmetric key
are accessed by attackers, then they will still be unable to reach the information. This is because the system is designed in a way that hinders the smart contract from opening the consent record. Finally, the unchangeable feature of blockchain makes it challenging to trace the evil delegatee.
Fine-grained access control is achievable with the proposed protocol. Aspects at S of user j are added to the private key
to generate the key. Here,
,
,
, and
are the parameters. The delegator creates access policy in the ciphertext using the attribute-based encryption. In this phase, they can decrypt the ciphertext partly. However, it I only possible if the attribution of the users align with the access policy generated by delegator. This also provides
. However, the system fails to decrypt the ciphertext if they fail to match the access policy.
Multi-hop delegation can be achieved with the proposed protocol. Since the patient will control the delegation depth, multi-hop delegation can be achieved. This will be achieved through generating a secret value
and passing it to the users. This facilitates the generation of the re-encryption key. The delegator employs DDSC to determine the appropriate delegation depth De for the users. Besides, it also enables the ciphertext to be converted in a way that it will only be decrypted by the patients when in the DSC. They then decrypt it using the private key that they generated and
. If there is the need to re-delegate, then they will repeat the same process until the depth De gets to zero.
5.2. Comparisons of security properties
Table compares the proposed scheme security properties with those of other schemes (Joshi et al., Citation2019), Xu et al. (Citation2019), Wang et al. (Citation2021). The results show that each of these protocols meet privacy protection as they share their data or searches. Researchers, Joshi et al. (Citation2019) and Wang et al. (Citation2021) employed the use of CPABE to attain fine-grained access control. Joshi et al. (Citation2019) used a broker to ensure there is access control but they failed to consider the impacts of the broker on the system. As a result, they were unable to attain collusion resistance. Xu et al. (Citation2019) used data search and focused on health testing as they strived to keep the patient information confidential. However, they failed to realized data sharing and multi-hop delegation. They also made their assumption on the surgeon being reliable rather than confirming if it was valid. They failed to develop fine-grained access control, and failed to show what would happen if there was a malicious attack. Despite this, Wang et al. (Citation2021) was able to achieve multi-hop delegation. The only issue was that the system users was to be determined prior by the patients. Thus, is evident that it was not flexible enough. Another issue from the system by Wang et al. (Citation2021) was that they made an assumption that the cloud server was safe and would not be impacted by other users, hence they were unable to prove if the system was resistance to collusion. An analysis of these results from the Table illustrates that the proposed scheme has the capability to address all these issues and achieve the delegation goal.
Table 1. Comparison of security properties.
6. Performance evaluation
6.1. Experimental environment
The section uses Java and the JPBC library to apply the algorithm. Besides, it also employed an Ethereum test platform in Ubuntu to organize the smart contracts. The system outlines the parameter setting and then goes further to present an analysis of the computation and interaction overhead of this anticipated protocol. The final phase is an analysis and designing of the smart contract on the Ethereum test platform. The system security parameter . It also uses type A combination on the elliptic curve on field
for some prime p=3mod4. Besides, cryptographic primitives are implemented using Java and the JPBC library. The description of the computer used was Intel(R) Core i7 with a CPU of @1.90GHz, an 8 GB RAM and a Windows 11 operating system.
The system constructed an Ubuntu test chain from Ganache which was a client version. It was encoded onto smart contracts in a solidity language prior to being keyed in to the blockchain. The structure employed Nodejs Web3js library to enable the smart contract to associate with the blockchain and determining the time it takes to facilitate a transaction. This is due to its inability to directly record the time as it is being published in the smart contracts. All the users are required to create a blockchain account so that they can access EMR and facilitate a transaction to their delegator. First, the conversion signals the DDSC to determine the delegation depth for the specific delegatees and transmits it to the blockchain. The delegator then activates the DCS to transmit the ciphertext after they transit the re0encryption code to it. The delegatees are requires to request the delegators to provide them with the original EMR from the IPFS and triggers the ASC to confirm if they meet the conditions for access.
6.2. Communication overhead
Table describes , and
. Its size in
is tiny and must be recognized. The findings by Wang and Zhang (Citation2020) help to show the comparison with other related works.
shows the total number of users' attributes, and
shows those found in the attribute structure. Communication overhead is determined during registration, data storage and sharing. The registration step shows how the CC transmits the private key that has been created to all the users. The keys have three parts,
. The length of
is based on the attribute
. This brings the total length to
. The delegation phase, determines the cost from the interaction between the delegator and smart contract and it is a result of
, that Its length is
. When the original ciphertext
is transmitted, it facilitates the most communication costs, especially when the data are being stored. This adds the total length to
. The computational cost in the data sharing process is based from analysing all the three levels of ciphertext
,
,
so that to provide performance. Their lengths are constant which makes
. This is compared to Wang and Zhang (Citation2020) and Deng et al. (Citation2020) as shown in Table .
Table 2. Proposed protocol communication overhead.
Table 3. Communication overhead of ,
and
ciphertexts.
Table 4. Experimental parameters.
The communication overhead is compared with Wang and Zhang (Citation2020) and Deng et al. (Citation2020) as shown in Table . The benefits can be seen in the delegation and data sharing stages. The re-encryption code size for this projected scheme is . It is also worth noting that it is only the user, who is the patient that has the control on access strategy due to security purposes. Based on the comparison, the other schemes, Wang and Zhang (Citation2020) and Deng et al. (Citation2020) recreates the access policy after the re-encryption key is created. Moreover, the solution failed to meet the multi-hop delegation. However, Wang and Zhang (Citation2020) protocol can achieve multi-hop delegation. This is because it applies LSSS in all the ciphertext levels. This results to communication overhead. Generally, this overhead that occurs between the delegatee and the delegator stays constant in this proposed scheme.
6.3. Computational cost
The computational cost was determined by simulating the cryptographic algorithms on all stakeholders including the patient, CC, delegator and delegatee. Wang and Zhang (Citation2020) determined the computational cost and is demonstrated in Figure and Figure . The results are then recorded by creating various delegation levels and features. The first is the system setup phase whereby the algorithm produces key system features and master keys. The second which is the registration phase provides a dissimilar key for all stakeholders depending on their attributes. The delegator provides ciphertext after an algorithm encrypt in the next phase which is data storage. During the delegation stage which is where the delegator creates a re-encryption code through ReKeyGen. It is the DSC that facilitates the algorithm. This is to provide a ciphertext to be given to the delegatee. The data access phase is where the delegator decrypts the ciphertexts deploys them to the DecByDelegator and DecByDelegatees algorithms. This is also where level 1 and ciphertext are used to explain this computation.
Figure 6. Computational cost comparison. (a) CC computation (b) patients computation (c) delegators computation and(d) delegatees computation.
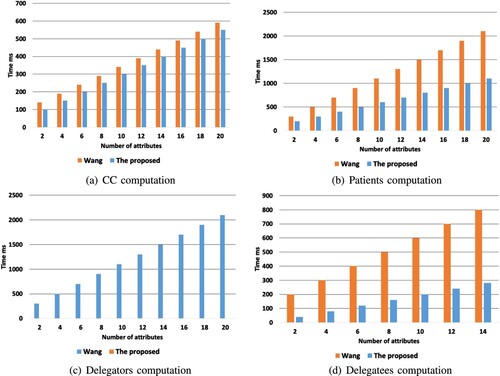
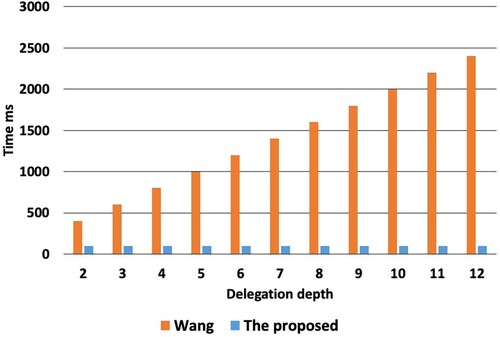
The computational cost of the delegatee is experienced by DecByDelegatees procedure, and influenced by the depth of delegation. Figure demonstrates the delegation depth which is set from two to twelve and the costs are recorded. Based on the illustration, the computational cost of this proposed scheme remains constant and small despite how many levels of delegation depths are added. This is different from the one demonstrated by Wang and Zhang (Citation2020) whereby the computational growth is expected to increase by about two hundred ms as the delegation depths are added. The findings are different because Wang and Zhang (Citation2020) created a protocol where level ciphertext decrypts. It also decrypts j−1 level ciphertexts one at a time. This is unlike the proposed one where it is expected that the current ciphertext level will be the one that decrypts.
Moreover, the users attributes in a given system also contribute to the computational overhead. Figure demonstrate how the computational overhead of the delegate, patient, CC and delegator change based on the number of attributes. When there are many attributes, the computational cost grows. See Figure (a) to identify how the computational cost is impacts by CC during the registration phase. Further the computational overhead as demonstrated by Wang and Zhang (Citation2020) shows is higher compared to this projected protocol. This is because the current one does not give search keys. Moreover, Wang and Zhang (Citation2020) had a higher and costly computational overhead than the current one due to encrypt algorithm (see Figure ). This is because (Wang & Zhang, Citation2020) integrated a random filling mechanism to help in attaining the XOR operation rather than using multiplication. The algorithm encrypt does not facilitate operations with XOR.
The computational cost of ReKeyGen algorithm used by users in the delegation phase as shown in Figure (c), show that the one by Wang and Zhang (Citation2020) is better compared to the proposed one. This is because the one by Wang and Zhang (Citation2020) only resets the policy that grant access and makes the computational overhead similar to the Encrypt. However, the proposed scheme must create a bilinear map which makes the computational overhead to be close to 7 ms. Figure (d)shows the computational overhead needed to decrypt with the algorithm DecByDelegatee. Both of them demonstrate that the computational cost of the delegatees grows based on the attributed. This is due to the fact that they all employ the linear secret sharing scheme. Besides, its timing depends on the attribute. Generally, if the proposed scheme is paralleled to the one by Wang and Zhang (Citation2020), then it is evident that the proposed one needs less computational costs. This is because the original ciphertext is authenticated and stored in the blockchain as the delegation process continues. Moreover, one of the features of blockchain is that it cannot be tampered with hence no need for repeat verification process.
6.4. Smart contracts time cost
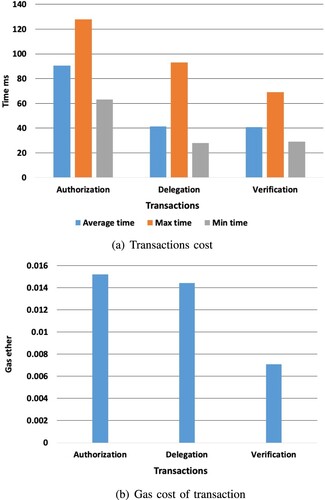
The Figure demonstrates that it takes about 90.42 ms for authorize transaction to reach the blockchain. Thus, the transaction cost comes from the implementation of the rekey algorithm in DDSC. To implement a delegation algorithm in the DSC, it requires close to 41.30 ms transaction delegation cost. Verifying a transaction takes close to 40.77 ms and this is due to having to determine if the user is valid and determining the access time. Generally, the total gas cost for all the three is approximately 0.015201, 0.014408, and 0.007101 ethers. The consumption of time and gas are between the allowed range.
7. Conclusions and future work
In this article, a multi-hop permission delegation technique built around blockchain technology with configurable delegation depth is demonstrated in the EMR system. Delegatees with access privileges can assign those rights to additional users to optimize the data value and flexibility of the data sharing network. The method of symmetric encryption is used for uploading the original EMR encrypted to IPFS for distributed storage. A policy for access control is established to limit the delegatee's characteristics and accomplish the required ciphertext transformation, and the symmetric key is encrypted. Blockchain technology ensures data storage and transaction security; on Ethereum, smart contracts faithfully carry out multi-hop delegation monitoring and ciphertext versioning. The computing expenses and communication overhead of the algorithms are compared and experimented with. As part of future research work, federated learning will be integrated to facilitate the Internet of Medical Robotics Things (IoMRT) applications to achieve the machine learning model. The plan is to deploy trustworthy Federated Learning Model for the Internet of Robotic Things.
Disclosure statement
No potential conflict of interest was reported by the author(s).
Additional information
Funding
References
- Agarwal, A., Joshi, R., Arora, H., & Kaushik., R. (2023). Privacy and security of healthcare data in cloud based on the blockchain technology. In 2023 7th International conference on computing methodologies and communication (ICCMC) (pp. 87–92). IEEE.
- Ahuja, R., & Mohanty, S. K. (2017). A scalable attribute-based access control scheme with flexible delegation cum sharing of access privileges for cloud storage. IEEE Transactions on Cloud Computing, 8(1), 32–44. https://doi.org/10.1109/TCC.6245519
- Alamer, A. M. A. (2024a). A secure and privacy blockchain-based data sharing scheme in mobile edge caching system. Expert Systems with Applications, 237, 121572. https://doi.org/10.1016/j.eswa.2023.121572
- Alamer, A. (2024b). A privacy-preserving federated learning with a secure collaborative for malware detection models using internet of things resources. Internet of Things, 25, 101015. https://doi.org/10.1016/j.iot.2023.101015
- Alamer, A., & Basudan, S. (2022). Security and privacy of network transmitted system in the internet of robotic things. The Journal of Supercomputing, 78(16), 18361–18378. https://doi.org/10.1007/s11227-022-04612-2
- Assiri, B. (2023). A modified and effective blockchain model for e-healthcare systems. Applied Sciences, 13(23), 12630. https://doi.org/10.3390/app132312630
- Basudan, S. (2022). A puncturable attribute-based data sharing scheme for the internet of medical robotic things. Library Hi Tech, 40(4), 1064–1080. https://doi.org/10.1108/LHT-08-2021-0254
- Bodkhe, U., Mehta, D., Tanwar, S., Bhattacharya, P., Singh, P. K., & Hong, W.-C. (2020). A survey on decentralized consensus mechanisms for cyber physical systems. IEEE Access, 8, 54371–54401. https://doi.org/10.1109/Access.6287639
- Chen, X., Liu, Y., Chao, H.-C., & Li, Y. (2020). Ciphertext-policy hierarchical attribute-based encryption against key-delegation abuse for iot-connected healthcare system. IEEE Access, 8, 86630–86650. https://doi.org/10.1109/Access.6287639
- Chen, D., Zhang, L., Liao, Z., Dai, H.-N., Zhang, N., Shen, X., & Pang, M. (2023). Flexible and fine-grained access control for ehr in blockchain-assisted e-healthcare systems. IEEE Internet of Things Journal, 11(6), 10992–11007.
- Das, S., & Namasudra, S. (2023). Lightweight and efficient privacy-preserving mutual authentication scheme to secure internet of things-based smart healthcare. Transactions on Emerging Telecommunications Technologies, 34(11), e4716. https://doi.org/10.1002/ett.v34.11
- Deebak, B., & Hwang, S. O. (2023). Healthcare applications using blockchain with a cloud-assisted decentralized privacy-preserving framework. IEEE Transactions on Mobile Computing, 23(5), 5897–5916.
- Deepa, N., Devi, T., Gayathri, N., & Kumar, S. R. (2022). Decentralized healthcare management system using blockchain to secure sensitive medical data for users. Blockchain Security in Cloud Computing, 265–282. https://doi.org/10.1007/978-3-030-70501-5
- Deng, H., Qin, Z., Wu, Q., Guan, Z., & Zhou, Y. (2020). Flexible attribute-based proxy re-encryption for efficient data sharing. Information Sciences, 511, 94–113. https://doi.org/10.1016/j.ins.2019.09.052
- Deng, Y., Zeng, Z., Jha, K., & Huang, D. (2021). Problem-based cybersecurity lab with knowledge graph as guidance. Journal of Artificial Intelligence and Technology, 2022(2), 55–61.
- Gao, Y., Zhang, A., Wu, S., & Chen, J. (2022). Blockchain-based multi-hop permission delegation scheme with controllable delegation depth for electronic health record sharing. High-Confidence Computing, 2(4), 100084. https://doi.org/10.1016/j.hcc.2022.100084
- Gupta, R., Shukla, A., & Tanwar., S. (2020). Aayush: A smart contract-based telesurgery system for healthcare 4.0. In 2020 IEEE International conference on communications workshops (ICC Workshops). (pp. 1–6). IEEE.
- Haleem, A., Javaid, M., Singh, R. P., Suman, R., & Rab, S. (2021). Blockchain technology applications in healthcare: An overview. International Journal of Intelligent Networks, 2, 130–139. https://doi.org/10.1016/j.ijin.2021.09.005
- Hooshmand, M. K., & Hosahalli, D. (2022). Network anomaly detection using deep learning techniques. CAAI Transactions on Intelligence Technology, 7(2), 228–243. https://doi.org/10.1049/cit2.v7.2
- Joshi, M., Joshi, K. P., & Finin, T. (2019). Delegated authorization framework for ehr services using attribute-based encryption. IEEE Transactions on Services Computing, 14(6), 1612–1623. https://doi.org/10.1109/TSC.2019.2917438
- Li, N., Zhang, R., Zhu, C., Ou, W., Han, W., & Zhang, Q. (2023). A data sharing method for remote medical system based on federated distillation learning and consortium blockchain. Connection Science, 35(1), 2186315. https://doi.org/10.1080/09540091.2023.2186315
- Liang, K., Fang, L., Susilo, W., & Wong., D. S. (2013). A ciphertext-policy attribute-based proxy re-encryption with chosen-ciphertext security,” In 2013 5th International conference on intelligent networking and collaborative systems (pp. 552–559). IEEE.
- Liu, W., He, Y., Wang, X., Duan, Z., Liang, W., & Liu, Y. (2023). Bfg: Privacy protection framework for internet of medical things based on blockchain and federated learning. Connection Science, 35(1), 2199951. https://doi.org/10.1080/09540091.2023.2199951
- Nakamoto, S., & Bitcoin, A. (2008). A peer-to-peer electronic cash system. Bitcoin.–https://bitcoin.org/bitcoin.pdf, 4(2), 15.
- Nie, X., Zhang, A., Chen, J., Qu, Y., & Yu, S. (2022). Blockchain-empowered secure and privacy-preserving health data sharing in edge-based iomt. Security and Communication Networks, 2022(1), 8293716.
- Sabrina, F., Sahama, T., Rashid, M. M., & Gordon., S. (2023). Empowering patients to delegate and revoke access to blockchain-based electronic health records. In Proceedings of the 2023 Australasian computer science week. (pp. 66–71).
- Scherrer, S., & Perrig, A. (2021). Security, anonymity, privacy, and trust. Future Networks, Services and Management: Underlay and Overlay, Edge, Applications, Slicing, Cloud, Space, AI/ML, and Quantum Computing, 367–381. https://doi.org/10.1007/978-3-030-81961-3
- Sharma, P., Namasudra, S., Chilamkurti, N., Kim, B.-G., & R. Gonzalez Crespo (2023). Blockchain-based privacy preservation for iot-enabled healthcare system. ACM Transactions on Sensor Networks, 19(3), 1–17. https://doi.org/10.1145/3577926
- Sivan, R., & Zukarnain, Z. A. (2021). Security and privacy in cloud-based e-health system. Symmetry, 13(5), 742. https://doi.org/10.3390/sym13050742
- Srinivas, D., Deepika, K., Rohith, H., & Lakshmi., H. (2023). Securing sharable electronic health records on cloud storage,” In 2023 7th International conference on computing methodologies and communication (ICCMC) (pp. 1054–1059). IEEE.
- Tanwar, S., Parekh, K., & Evans, R. (2020). Blockchain-based electronic healthcare record system for healthcare 4.0 applications. Journal of Information Security and Applications, 50, 102407. https://doi.org/10.1016/j.jisa.2019.102407
- Vidhya, S., & Kalaivani, V. (2023). A blockchain based secure and privacy aware medical data sharing using smart contract and encryption scheme. Peer-to-Peer Networking and Applications, 16(2), 900–913.
- Wang, Q., Lai, C., Lu, R., & Zheng, D. (2021). Searchable encryption with autonomous path delegation function and its application in healthcare cloud. IEEE Transactions on Cloud Computing, 11(1), 879–896.
- Wang, H., Xie, Y., Liu, Y., Li, X., & Dorje, P. (2023). Data verifiable personalized access control electronic healthcare record sharing based on blockchain in iot environment. IEEE Internet of Things Journal, 11(4), 5696–5707.
- Wang, M., Yi, H., Jiang, F., Lin, L., & Gao, M. (2022). Review on offloading of vehicle edge computing. International Journal of Artificial Intelligence.
- Wang, D., & Zhang, X. (2020). Secure data sharing and customized services for intelligent transportation based on a consortium blockchain. IEEE Access, 8, 56045–56059. https://doi.org/10.1109/Access.6287639
- Wani, A., & Khaliq, R. (2021). Sdn-based intrusion detection system for iot using deep learning classifier (idsiot-sdl). CAAI Transactions on Intelligence Technology, 6(3), 281–290. https://doi.org/10.1049/cit2.v6.3
- Xu, C., Wang, N., Zhu, L., Sharif, K., & Zhang, C. (2019). Achieving searchable and privacy-preserving data sharing for cloud-assisted e-healthcare system. IEEE Internet of Things Journal, 6(5), 8345–8356. https://doi.org/10.1109/JIoT.6488907
- Xu, S., Zhong, J., Wang, L., He, D., Zhang, S., & Shao, W. (2023). A privacy-preserving and efficient data sharing scheme with trust authentication based on blockchain for mhealth. Connection Science, 35(1), 2186316. https://doi.org/10.1080/09540091.2023.2186316
- Yaqoob, I., Salah, K., Jayaraman, R., & Al-Hammadi, Y. (2021). Blockchain for healthcare data management: Opportunities, challenges, and future recommendations. Neural Computing and Applications, 34, 1–16.
- Yuan, Y., & Wang, F.-Y. (2016). Blockchain: The state of the art and future trends. Acta Automatica Sinica, 42(4), 481–494.
- Zhang, A., & Lin, X. (2018). Towards secure and privacy-preserving data sharing in e-health systems via consortium blockchain. Journal of Medical Systems, 42(8), 140. https://doi.org/10.1007/s10916-018-0995-5
- Zyskind, G., & Nathan., O. (2015). Decentralizing privacy: Using blockchain to protect personal data. In 2015 IEEE security and privacy workshops (pp. 180–184). IEEE.