?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.
?Mathematical formulae have been encoded as MathML and are displayed in this HTML version using MathJax in order to improve their display. Uncheck the box to turn MathJax off. This feature requires Javascript. Click on a formula to zoom.Abstract
Ensuring the confidentiality of transmitting sensitive image data is paramount. Cryptography recreates a critical function in safeguarding information from potential risks and confirming the identity of authorised individuals, thereby addressing the growing demand for enhanced image security. This paper presents a novel AES-permuted Feistel Blowfish (APFB) model that aims to improve image data security cost-effectively and enhance data protection by incorporating AES and Blowfish algorithms. The proposed model's utility over existing approaches stems from its computational efficiency and speed. The proposed model's resilience and security against several attack modalities are validated through a comprehensive range of methods, including extensive experimentation, histogram analysis, PSNR, entropy, MSE, CC, computational time, and NIST statistical tests. The outcomes yielded a PSNR of 67.26, NPCR of 99.6354, and UACI of 33.412. Additionally, the applicability of the proposed model is validated by utilising a practical case analysis. The outcomes exhibit the relevance of the proposed model in real-world applications.
1. Introduction
The enhancement of communication technology and availability have profoundly impacted all areas of our business, enterprise, and day-to-day work. These advancements have facilitated the production of substantial quantities of data with greater ease and at a reduced expense. In addition to these progressions, the past two decades have witnessed the extensive integration of mobile technology, resulting in images becoming the predominant form of data (Ben Slimane et al., Citation2018). Digital images have become important in our everyday life. However, the extensive usage of digital images also poses a potential threat to the confidentiality and integrity of several types of visual content, including personal photographs and secret business documents (Ullah et al., Citation2023). The importance of image encryption in today's interconnected world cannot be overstated. It converts image data into an incomprehensible and nonsensical format for individuals who lack the appropriate decryption key, thereby safeguarding sensitive information (Veera et al., Citation2024). Given the increasing risk of data breaches, cyber-threats (Barik et al., Citation2022), adversarial attacks (Barik et al., Citation2024), and unauthorised access, ensuring digital image security throughout storage, transmission, and retrieval is mandatory (Güvenoğlu, Citation2024).
Techniques for encryption and decryption are critical to achieving this objective. Image encryption is the process of using cryptographic methods to convert the pixel values of an image into an incomprehensible and senseless format, rendering it indecipherable to anyone who does not possess the correct decryption key (Wen et al., Citation2024). Encrypting digital images makes it possible to securely communicate and retain sensitive information within them without the threat of interception or unlawful dissemination. Image encryption techniques can be classified into three basic types: symmetric, asymmetric, and hybrid (Elkandoz & Alexan, Citation2022). Symmetric encryption utilises a solitary secret key for all the encryption and decryption procedures, offering a comparatively uncomplicated and effective option (Chowdhary et al., Citation2020). Asymmetric encryption employs a set of keys, consisting of a public key for encryption and a private key for decryption, which offers heightened security but requires more computing complexity. Hybrid encryption is a cryptographic technique that leverages the advantages of symmetric and asymmetric encryption to balance security and efficiency (Pourjabbar Kari et al., Citation2021).
Encrypting image data presents greater challenges than encrypting text data (Hasan et al., Citation2021). Firstly, in practical scenarios, the size of image data is greater than that of text data. Encrypting images within a reasonable timeframe becomes challenging due to this. In the second scenario, significant correlations exist between neighbouring pixels in the image data, which attackers can exploit using statistical attacks to access the original images (Feng et al., Citation2024). Encryption techniques are only effective if they provide sufficient strength. Hence, standard encryption methods like Data Encryption Standard (DES) (Mehta et al., Citation2024), Triple DES (TDES), Advanced Encryption Standard (AES), and Rivest-Shamir-Adleman (RSA) (Ahmad & Hasan, Citation2021), which are extensively employed for encrypting text data, are not appropriate for encrypting image data. Encrypting image data requires incorporating many methods. Over time, many image encryption techniques have been presented to cater to digital images’ distinctive features and needs. Image encryption has seen the adaptation and optimisation of traditional encryption methods, such as DES and AES. Furthermore, there have been advancements in encryption algorithms that utilise chaotic systems, Substitution boxes, DNA sequences (Akkasaligar & Biradar, Citation2020), and RNA (Cun et al., Citation2023). These algorithms provide enhanced security features and are resistant to attacks.
Image encryption algorithms are typically based on standardized structure and comprise confusion and diffusion (Man et al., Citation2021). The objective of the confusion phase is to disrupt the relationship between neighbouring pixels in the original image by rearranging their positions while keeping their values unchanged. During diffusion, pixel values are systematically altered to change the image's statistical characteristics (Toktas et al., Citation2024). For thorough literature on image encryption and decryption, interested readers are encouraged to review the works of (Singh & Singh, Citation2022; Pourasad et al., Citation2021; Zhang et al., Citation2023). In addition, there are different methods, such as (Gao et al., Citation2023; Rakheja & Khurana, Citation2023; Yu et al., Citation2023; Mansoor & Parah, Citation2023; Soppari & Chandra, Citation2023).
1.1. Motivation
Considering the advancements in image encryption, some limitations remain (Gull & Parah, Citation2024; Chai et al., Citation2022). Distributing and storing encryption keys securely remains a major difficulty in key management. The intricacy of encryption methods and the requirement for instantaneous encryption can present practical constraints. Also, the existing models require high computing resources and processing time and are complex while implemented in the real world. Moreover, the resilience of encryption systems against other types of attacks, such as brute-force and statistical attacks, necessitates ongoing monitoring and enhancement (Herbadji et al., Citation2024). Our work is motivated by the need to address the existing challenges by presenting cost-effective, reduced computing resources, fast processing, easy-to-implement, and efficient hybrid encryption and decryption techniques. Blockchain technology is used for secure data storage.
1.2. Contributions
The work presents a novel cryptographic model, APFB (AES-permuted Feistel Blowfish), that integrates AES (Hadj Brahim et al., Citation2024) and Blowfish algorithms (Nampalle et al., Citation2023) during encryption and decryption. When encrypting image data, special encryption needs are considered. The proposed solution is a hybrid system that utilises the Feistel structure to resist different cryptographic catalysts, allowing for mixing more complex data through substitution and permutation operations. Despite its multi-layered nature, the encryption and decryption techniques are easily implemented, which makes it well-suited for real-world issues due to its low computing resources. The significant contributions of the study are as follows:
This study proposed a novel hybrid APFB model to enhance image security during transmission. The presented model is simple to implement with low compute resource requirements.
The proposed model takes an average of 0.011 s to encrypt and 0.073 s to decrypt a standard 256 *256 image. This reduced time complexity allows the approach to be applicable in practical scenarios where efficiency is crucial.
Encrypting an image using hybrid methods entails the creation of in-between secret keys from the cryptographic process and the real image. Even the smallest alteration to the original image or the secret key results in a completely distinct encrypted image, making differential attacks ineffective. It possesses an extensive range of possible keys and is highly responsive to alterations in the key. Additionally, the data is stored using a hashing algorithm in the blockchain.
The proposed model's randomness is validated utilising the National Institute of Standards and Technology (NIST) SP 800-22 statistical tool.
Different systematic experiments are performed to validate the proposed model's outcome and compare it with existing studies.
A practical case study further depicts the proposed model's applicability.
This theoretical contribution aligns with the fundamental ideas of cryptography by demonstrating the significance of confusion and dispersion for enhanced encryption with reduced computing resources, low processing time, and ease of implementation. Additionally, using blockchain technology for secure storage enhances data security with a cost-effective and efficient option.
The remaining paper is formulated as follows: Section 2 concerns related works with different methods and algorithms. Section 3 demonstrates in detail the methodology of the proposed model, including encryption and decryption. Section 4 demonstrates systematic experimentation, statistical tests, and validation using practical case studies. Section 5 presents the discussion, limitations, and future research. Finally, the paper is concluded in Section 6.
2. Literature review
This section highlights the existing research studies focusing on image security and cryptographic techniques. Singh and Sunitha (Citation2022) proposed a secure method for exchanging images using blockchain and pallier map-based authentication. It is based on the cloud and ensures the integrity and security of image data. The authors demonstrated authentication accuracy by 23%; the analysis showed a 32% reduction in the false positive rate and a 22% decrease in the computational cost. Hafsa et al. (Citation2022) presented an improved AES (IAES) technique that enhances the ciphered video's diffusion and confusion. The chaotic attractor's beginning conditions are created using the SHA-3 hash algorithm. For real-time video transmission, this activity is crucial since it reduces the run time. The chaotic attractor's initial conditions are built using the SHA-3 hash algorithm. The presented outcomes boost the encrypted video's entropy by 15% and reduce the complexity time for encryption and decryption. Daoui et al. (Citation2022) proposed a novel 2D chaotic system sensitive to any change in its control parameters. A novel encryption system is built using QFrMMs to uncover the signal and image processing applications of the suggested FrMP map. Its primary use is the encryption of several types of biomedical data, including various grayscale and colour medical images. The authors demonstrated that sage exchanges image data over the publicly available communication system. El Azzaoui et al. (Citation2022) proposed that using quantum computing and blockchain technology makes smart healthcare systems effective, scalable, and secure. The experimental findings show that the architecture is feasible and that the implemented Q-OTP encryption is secure.
Gupta et al. (Citation2023) proposed an effective solution for encrypting images that combines cryptography and watermarking. It depends on two-tiered security to provide safe and error-free image data transfer. Patel and Thanikaiselvan (Citation2023) presented a study on the image encryption method using neural networks, Latin squares, and other machine-learning methods. The authors suggested creating a chaotic sequence for various uses using a fresh pseudo-random number generator based on neural networks. Sarosh et al. (Citation2023) developed two new two-dimensional chaotic maps, the Logistic Regulated Quadratic map (LRQ) and the Quadratic Regulated Quadratic map (QRQ) for healthcare systems. These maps display compound chaotic features and a large chaotic range. Guo et al. (Citation2024) proposed the ACGAN-FTL federated transfer learning system, built on an auxiliary classifier generative adversarial network, which could fix this. An internal transfer learning process moves data from the system's global model to a user-specific one using a small sample size. Lin et al. (Citation2024) presented a study using an M-based cryptography scheme and a symmetric cryptography technique to safeguard information medical images.
Xie et al. (Citation2023) proposed a medical image encryption technique that uses deoxyribonucleic acid encoding in conjunction with a quick and reliable fuzzy C means clustering image segmentation algorithm. The study demonstrates robust encryption and safety against various attacks. Zhu et al. (Citation2023) proposed a system model that uses a one-dimensional piece-wise quadratic polynomial chaotic map (PWQPCM) to enhance its chaotic properties. It is especially suitable for cryptography applications as it displays strong decentralised conduct across a broader set of continuous parameters. A secure image encryption method that utilises the presented model and a strong S-box construction. Elmoasry et al. (Citation2022) presented a dual-layer data strategy consisting of a data concealing technique after the encrypted medical images. The encryption system has two components: diffusion and confusion. To create confusion, it uses logistics and tent maps to create S-boxes. Al-Hyari et al. (2022) presented a safe and effective method for storing digitally coloured images. This method offers a high level of protection using a complicated secret key that the sender and the recipient have agreed upon. Arif et al. (Citation2022) addressed problems in current image encryption methods by presenting a novel method that relies on chaos theory and uses a single substitution box to perform permutations and substitutions. John and Kumar (Citation2023) presented encrypting images using a linear feedback shift register. It shuffles the pixel location and produces pseudo-random integers. The original image can be recovered by the receiver side node decrypting the data after the encrypted image has been delivered via a cloud platform.
Abd-El-Atty et al. (Citation2023) suggested a unique logistic mapping and quantum walk-based double medical image encryption method. The proposed method splits the two plain images in half, with one copy containing each image's high-bit and the other the low-bit versions. Abdelfatah et al. (Citation2023) presented an image encryption method that overcomes these limitations using innovative multi-chaotic map design and adaptive DNA code bases. DNA coding is a powerful tool for improving computational efficiency and data transport capabilities. A multi-chaotic map of the Henson Gaussian logistic was combined to create more chaotic pseudo-random sequences. El-Shafai et al. (Citation2023) offered that the hybrid optical-based solution securely transmits colour and grayscale medical images over unreliable networks by utilising efficient hashing, steganography, and encryption techniques. Patil et al. (Citation2016) proposed an algorithm based on the user's needs. They presented the comparisons by implementing and analysing the cost and performance of used cryptographic algorithms such as DES, 3DES, AES, RSA, and blowfish.
Sahlabadi et al. (Citation2022) presented a novel image encryption algorithm, combining Cycling 3D Chaotic Map with DNA sequences. The study aimed to enhance security by using aggressive violence and genetic design. The method enables strong encryption in image communication and storage applications. Lin et al. (Citation2023) presented a novel method for extracting recognisable watermarks from images using DL technology. Their method demonstrates an efficient removal method and offers versatile applications where watermark removal is required. Saberikamarposti et al. (2024) discussed classification, challenges, and future directions and examined image storage in detail. It examined different approaches to image storage, identified existing challenges, and proposed avenues for future research to improve it. It provided valuable insights into enhancing image security. Arian et al. (Citation2024) presented a new approach to image storage by combining DNA sequences with excess chaos. It introduced an approach that used the chaotic dynamics of hyperchaotic systems to enhance encryption security. Integrating DNA sequences adds robustness and complexity to the encryption process, promising better protection of sensitive image data. Ghorbani et al. (Citation2022) presented a novel image storage system combining ribonucleic acid (RNA) and Hénon maps. Taking advantage of RNA's unique properties and the Henan map's chaotic nature, the system provides enhanced security for image storage. The authors demonstrated promising results regarding encryption efficiency and resistance to attack.
Ali et al. (Citation2024) presented a study on medical image encryption techniques to enhance textual confusion using s-box and novel techniques based on linear fractional transformation. They presented the usefulness of image security by encrypting using an S box. The authors evaluated the proposed method using different evaluation parameters. Huang et al. (Citation2022) proposed image encryption using SHA 3 and sensing an embedded image using asymmetric cryptography. The integer wavelet transform is employed to transform the courier image. The study results demonstrate that the proposed technique has robust imperceptibility and key sensitivity. The author presented a PSNR value of 43 dB and a carrier image value of 0.9999. Alexan et al. (Citation2023) proposed a novel image encryption algorithm using Chaos and KAA maps. The authors presented an extensive mathematical analysis to exhibit the method's robustness. It is effective and can address statistical, differential, and brute-force attacks. The study was further validated using the NIST SP 800 statistical test. Inam et al. (Citation2024) presented an image encryption study using a blockchain-based framework. The authors proposed a novel method using chaotic Arnold's cat map encryption. The data is stored after encryption into the blockchain for enhanced security. They evaluated the method using various parameters and found it effective compared to existing studies. Ahuja et al. (Citation2023) proposed a hybrid encryption method based on Lorenz-Gauss-Logistic image encryption. The authors validated the method using the NIST statistical test. The outcome illustrates the impressive scrambling impact of the presented method, which can significantly enhance image security. The summary of existing studies is outlined in Table .
Table 1. Summary of existing studies.
The literature review identifies different gaps and limitations in the existing research. Though multiple encryption techniques have been proposed, further evaluations are demanded to ensure data integrity, lower computing costs, and robustness against the exponential growth of various attacks. The present systems often rely on specific encryption algorithms, ignoring the potential advantages of hybrid encryption approaches and integration with prospective technologies such as blockchain. The efficiency of encryption systems can vary based on image type, size, and complexity, emphasising the importance of adaptable and scalable encryption solutions customised to a wide range of imaging settings. Cryptographic techniques that reduce computing resources, fast processing, cost-efficient, and easy-to-implement practical solutions are highly demanded. The presented APFB model aims to enhance robust encryption and decryption with reduced computing resources, low processing time, and ease of implementation to address the existing research gap. The private key of APFB is the advancement and fusion of two advanced encryption techniques, AES and Blowfish. Fusing different cryptographic methodologies presents a complex model for protecting confidential data. A theoretical development is represented by the APFB model's combination of Blowfish and AES. By fusing the effectiveness of AES with the Feistel network topology of Blowfish, this hybridisation makes the most of the benefits of both algorithms. By reducing possible flaws brought about by using a single encryption method, the synergy between these cryptographic primitives seeks to provide a greater degree of security. The Feistel network included in the Blowfish segment of the APFB facilitates improved confusion and dispersion. The Feistel structure resists different cryptographic catalysts, allowing for mixing more complex data through substitution and permutation operations. Further, blockchain technology is employed for secure storage to enhance data security with a cost-effective and efficient option.
3. Proposed methodology
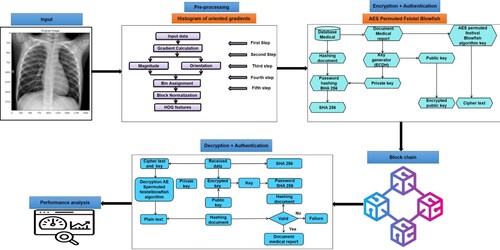
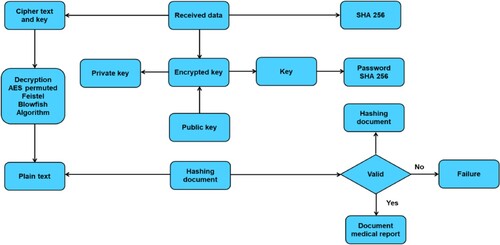
This section depicts the proposed methodology employed in this study. First, Kaggle datasets are collected and then pre-processed using Histogram of Oriented Gradients (HOG). Subsequently, the proposed AES-permuted Feistel Blowfish method is performed to protect the confidentiality of sensitive data sent using image data. Blockchains, a distributed database updated by network nodes, are used in this study to safeguard data. Figure illustrates the proposed model.
3.1. Dataset
This study uses the datasets collected from Kaggle (https://www.kaggle.com/datasets/sachinkumar413/covid-pneumonia-normal-chest-xray-images). The medical image data contains chest X-ray images in three subfolders: COVID-19, NORMAL, and PNEUMONIA. COVID has 1626 images, NORMAL has 1802 images, and PNEUMONIA has 1800 images. All images are preprocessed and are downsized to 256 by 256 PNG format.
3.2. Pre-processing using histogram of oriented gradients
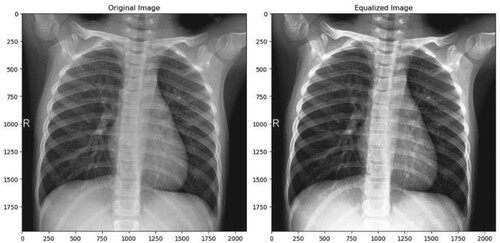
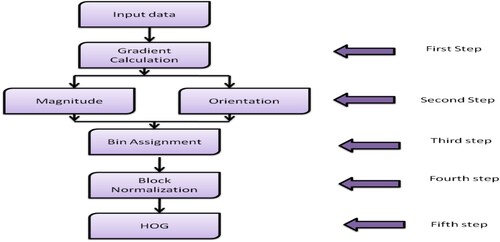
The image contrast and quality can be increased for improved analysis and diagnosis of chest disorders with data pre-processing that employs histograms of gradients. Initially, individuals are identified using a histogram of oriented gradient (HOG) algorithm (Zhou et al., Citation2020). The data is pre-processed before the gradient can be calculated, oriented, and normalised, as shown in Figure .
Noises are diminished first through preprocessing. If the reduction is present, the gradient matrices are returned correctly. Filters are used for preprocessing by convolving the signal with them. The result of applying the filter to an image and multiplying it would be a kernel or a mask. It only takes a simple filter slide over an image to reproduce or convolve the signal. The Gradient computation is utilised in image feature extraction to obtain correct shape and appearance gradients. The resulting compounds of functions and
are computed at each pixel coordinate to produce this function. The magnitude can be calculated using equation Equation1
(1)
(1) .
(1)
(1) The direction can be specified once the gradient is determined using equation Equation2
(2)
(2) .
(2)
(2) where
denotes the resulting angle
components that are called components along
and
directions.
Equations Equation3(3)
(3) to Equation5
(5)
(5) are used for normalisation, where
is an integer corresponding to the block's histogram after merging
, an insignificant variable. Users can determine the HOG normalised featured vector. Figure presents the flow of HOG.
(3)
(3)
(4)
(4)
(5)
(5)
3.3. AES permuted feistel blowfish (APFB) model
The popular symmetric encryption technique AES (Advanced Encryption Standard) offers robust protection for sensitive data, including image security. Sensitive information is often included in images, and protecting this information is essential to adhering to privacy laws (Abu-Faraj et al., Citation2022). AES encryption is a dependable technique for protecting these images during transmission and storage (Nadhan & Jeena Jacob, Citation2024). The AES encryption uses a symmetric key to translate the image's pixel data into cipher text. This symmetric key is essential for decryption and encryption, enhancing security. The cipher text can quickly identify a change in the key since the AES Sub Bytes transformation was changed to be round key-dependenthe round key matrix's 16 bytes are used to XOR all the bytes in the corresponding to create 4 eight-bit keys,
, and
by
as shown in equations Equation6
(6)
(6) and Equation7
(7)
(7) . Each
, It is appended to every byte using equations Equation8
(8)
(8) to Equation1
(1)
(1) 1 in the appropriate (Rowi) values in the S-Box, and the state matrix is substituted after the acquisition of the XOR keys. The given a round key K and a state S, which are represented as 4 × 4 matrices:
(6)
(6)
(7)
(7)
(8)
(8)
(9)
(9)
(10)
(10)
(11)
(11)
The resultant state matrix
(12)
(12)
Equation 12 illustrates replacing bytes in the S-Box replacement table using the standard Sub Bytes technique operations upon receiving the new state matrix S′.
3.3.1. Modified inverse sub-bytes transformation
Equation 13 illustrates that the Sub bytes translation is invertible, allowing the inverse Sub Bytes operation to be modified.
(13)
(13) To get the value
, that is, two hexadecimal values can be supplied, the outcome of adding BF to ED using a special OR procedure. ED is represented by the binary integers 11101101 and BF by 10111111. Below is an illustration of the operation:
In Galois Field (GF
), it is possible to express ED and BF using the polynomials
and
, respectively.
(14)
(14)
(15)
(15)
Therefore
(16)
(16)
. The binary representation is 52, whereas the hexadecimal representation is 52. Using the polynomials
, it can demonstrate that
= (
)
=
,
(17)
(17)
Since , It has been shown that the Sub byte operation is invertible. Prior to performing an XOR operation on the state matrix and the Rkeyb, the replacement is performed during the inverse Sub byte operation.
(18)
(18) Afterward, the replacement yields the matrix S′ in this way:
The initial state is recovered by using equation Equation1(1)
(1) 9 to XOR the
matrix with the XOR keyy.
(19)
(19) The matrix displaying the inverse of the Sub Bytes operation is as under
The following steps create the resulting matrix S, representing the initial state.
The argument above shows the inevitability of the Sub Bytes operation.
Where
to 3, for each i from 0 to 3.
3.3.2. Shift rows transformation
Randomising the method to perform the Shift Rows operation is important. The procedure depends on an integer known as the Ranking Number (RNo) instead of the constant offset (Vandic et al., Citation2024). This value may be retrieved by finding the state matrix row corresponding to the round key matrices. The state's rows are reorganised using the derived rank number. The first algorithm's rank was determined by two matrices, a circular key matrix K and a state matrix S. The rank detection using state and the round key matrix is presented in Algorithm 1.
Table
Equation 20 is used to create the state key vector
(20)
(20) Further reduction of equation Equation2
(2)
(2) 1, which in turn allows for
(21)
(21)
Equations Equation22(22)
(22) to Equation2
(2)
(2) 5 can be used to break down equation Equation1
(1)
(1) 6.
(22)
(22)
(23)
(23)
(24)
(24)
(25)
(25)
Equation 26 is used to derive the Rank Values , such that:
(26)
(26)
Equation Equation2(2)
(2) 6 can be divided into four separate equations that reflect each row of the condition shown in equations Equation27
(27)
(27) to Equation30
(30)
(30) .
(27)
(27)
(28)
(28)
(29)
(29)
(30)
(30)
The Rank Number is appended to each of the Rank Values
starting with the lowest
and going all the way up to the largest
in ascending order.
Following the acquisition of the Rank Values (), the values are assigned a Rank Number
in ascending order, wherein the largest
is assigned an
of 4 and the smallest
is assigned an
of 1.
The state's rows are then all moved. places to the left. The row with
is thus not moved, whereas the rows with
= 2 and
3 are shifted one, two, and three bytes correspondingly to the left, and lastly, The highest-ranking row has three bytes shifted to its left,
The modified Shift Rows operation is explained below, using the matrices. for states and
for round keys.
Now, it can get the state key
vectors, the following steps are followed.
Next, it gets the Rank Values by following these steps:
Each row's rank number determines how much room each row needs, which is one less than the row's value, as presented in Table . Row 0 will remain unchanged, row 1 will relocate two bytes to the left, row 2 will move three bytes to the left, and row 3 will move to the left-hand side. These Shift Rows operations are performed on the provided state using the lowest rank value and should be used first for each state row (rows 0 through 3) for the state matrix after the modification.
3.3.3. Inverse shift rows transformation
Decryption uses a backward reading of the round keys, which means that the rank number computation for the Inverse Shift Rows operation is identical to that of the modified Shift Rows operation (Benoit et al., Citation2024). Aside from the change in direction, both methods involve shifting to the state matrix's rows. When turning the tables around, according to their rank, the rows are moved to the right (Rahman et al., Citation2024). The AES-128 algorithm is described in Algorithm 2.
Table 2. The RVals, RNos, and state row numbers correlate to the rank values.
Blowfish is a symmetric cipher system that encrypts and protects images (Gadde et al., Citation2023). It works for safeguarding medical images since it employs a length of the key that might vary between 32 and 448 bits. The Blowfish symmetric block cipher is 64 bits long and uses keys of varying lengths (Abbas et al., Citation2021). The procedure has two parts: one that encrypts images and another that increases keys. The key extension requires several sub-key arrays totaling 4168 bytes for keys with a maximum of 448 bits. The data is encrypted through a Feistel network of 16 rounds. It is only appropriate for applications such as automated file encryption or communications links when the key is the same. The Blowfish algorithm is presented in Algorithm 3.
Table
This work presents a hybrid cryptography technique using AES Permuted Feistel Blowfish. These symmetric techniques can lengthen the time it takes to encrypt and decode images obtained from medical image directory databases (Nagarajan et al., Citation2022). Figures and illustrate the proposed model for hybrid encryption and decryption. The proposed APFB model algorithm is illustrated in Algorithm 4.
Table
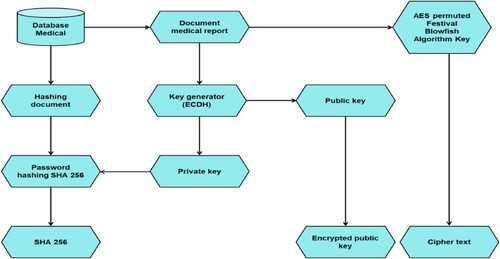
In blockchain, encrypted data is stored through hashing. When information is added to a block, it undergoes a cryptographic hash function, generating a fixed-size string of characters that uniquely represents the data (Alfrhan et al., Citation2021). This hash is stored along with the previous block's hash, forming a chain. Encrypted data is transformed using a cryptographic hash function in a stored process through hashing. This hash uniquely represents the encrypted data the blockchain keeps (Barik et al., Citation2023). The hash serves as a fingerprint for the data and ensures its integrity. The hash changes drastically if the data is altered, even by a single character. Moreover, since each block references the previous block's hash, any interference with a block necessitates altering subsequent blocks, making the stored process secure and resistant to unauthorised modifications. The user should initiate the decryption process by requesting the decryption of data. Data that needs to be decrypted is retrieved in response to user requests. The first step in decoding is getting the encryption keys. The encryption transformations are reversed using the same keys used for encryption. Figure demonstrates the decryption process of the proposed model.
4. Experimental results and analysis
This section discusses the proposed model's outcome. This study is conducted on a laptop with an Intel Core i7 8550 CPU, 1.8 GHz, 4 cores, MS Windows 11 64-bit OS, 32 GB of RAM, and 500 GB of SSD storage. The model is implemented in the Python environment. Different evaluation metrics are considered, i.e., MSE, PSNR, CC, Entropy, NPCR, and UACI, and computed using equations Equation31(31)
(31) and Equation3
(3)
(3) 7, respectively.
(31)
(31)
(32)
(32)
(33)
(33)
(34)
(34)
(35)
(35)
(36)
(36)
(37)
(37)
and
are the chipper images corresponding to two security keys.
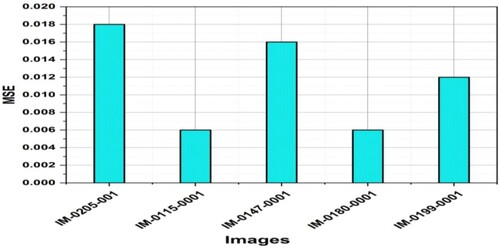
Mean Squared Error (MSE) is utilised to evaluate the efficacy of image encryption techniques. It quantifies the average squared difference between an image's pre- and post-encryption pixel values. A lower MSE shows minimum distortion between the original and encrypted images, and a lower MSE presents greater preservation of image quality throughout the encryption process. Figure illustrates the test outcome of the MSE values for five specific images.
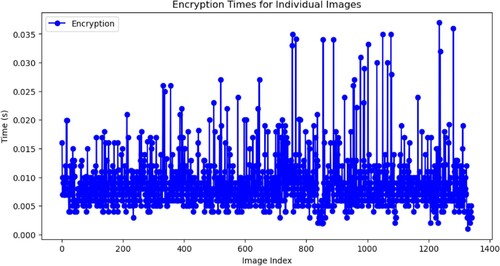
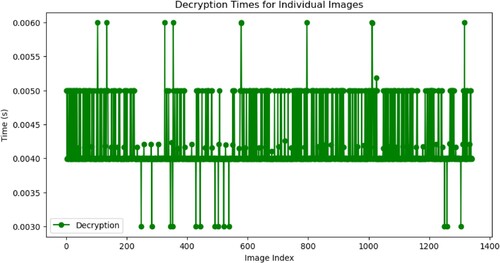
The encryption and decryption durations for specific images are contingent upon several elements, such as the encryption technique employed, the image's dimensions, and the hardware's computing capacity. The original image should be converted into a coded format to safeguard its information. This process is reversed to retrieve the original image during decryption. Fast encryption and decryption times are necessary for efficient data transfer and real-time applications. Processing times can be significantly decreased by using hardware-accelerated advanced encryption methods. However, additional processing power and time might be needed for encryption and decryption of higher image sizes. Figures and illustrate the duration of encrypting and decrypting each of the five images and the image index.
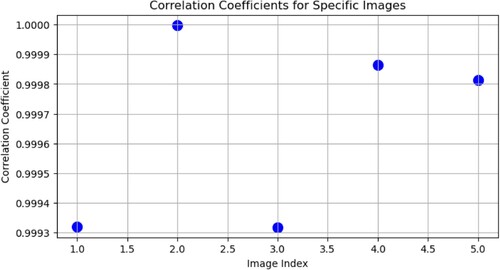
The correlation coefficient (CC) indicates the image's pixel redundancy. The plain image has duplication, although the encrypted image should have a high CC value. This signifies the encrypted image with the lowest level of redundancy. It provides the degree of correlation coefficient analysis, the degree to which two adjacent pixels in an image are similar for each of the five images, as pictured in Figure .
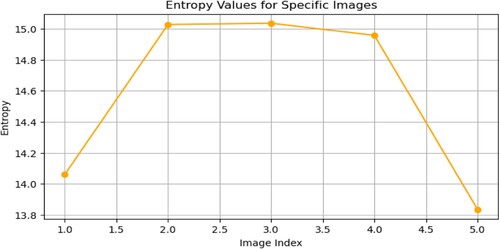
Entropy is used to access images of unpredictability. In this study, entropy is employed as a criterion for evaluating the relevance of the ciphering approach. Figure illustrates the test outcome of the entropy values for specific image analysis for each of the five individual images.
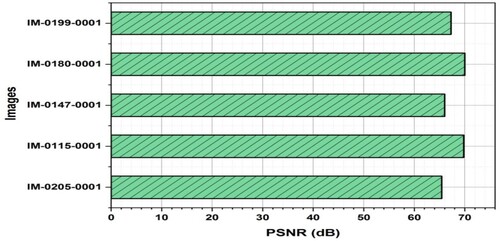
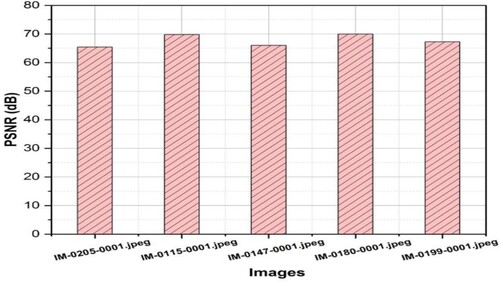
A common metric for evaluating the effectiveness of image encryption is the PSNR. The ratio of the greatest potential power of a signal (the original image) to the power of the noise created during encryption is known as PSNR. Figure depicts the test results of the PSNR values for a particular image analysis for each of the five distinct encrypted images.
Figure depicts the test results of the PSNR values for a particular image analysis for each of the five distinct decrypted images.
Table illustrates the outcome of the proposed model. The image is encoded using the optimal technique that enables a safe transmission. After two-fold encryption, the image can be sent safely. The last step recovers the original image using a hybrid decryption method. Encryption is obtained twice during transmission. The other user uses the blowfish decryption technique to execute design encryption and decryption after receiving the information.
Table 3. Analysis of the proposed model's outcomes using different input image data.
The five selected images were chosen to compute the encryption and decryption time of the proposed mode, and the outcome is presented in Table .
Table 4. Encryption and decryption time of five images.
4.1. Robustness analysis
Robustness refers to encryption systems’ ability to address and remain unaffected against attacks, making it an essential quality. We conducted experiments using plaintext, noise, and JPEG compression attacks using 256 *256 images to evaluate the resilience of the proposed model.
4.1.1 Plaintext attacks
The analysis should include a dedicated segment on the chosen plaintext attack, examining its potential vulnerabilities and countermeasures within the proposed encryption system (Yuan et al., Citation2024). The model is evaluated using the Number of Pixels Change Rate (NPCR) and the Unified Average Changing Intensity (UACI). Table illustrates the experimental outcomes of NPCR and UACI values in different images. The proposed encryption system can address plaintext attacks, as exhibited in Figures , , 11, 12, and Tables and .
Table 5. Experimental outcomes of NPCR and UACI for different images.
4.1.2. Noise attacks
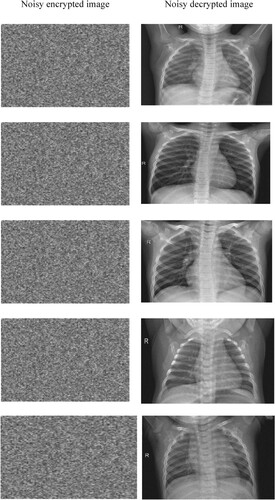
This experiment employs salt and pepper noise attacks, with the noise strength K for the recommended encryption approach of 0.01 in five images. Figure exhibits the encrypted text visuals and the related decoded images for those visuals under different noise attacks and intensities. Although the quality of the decrypted image deteriorates with increasing noise levels, the approach can resist noise attacks over a wider range of intensities. Table displays the PSNR values of encrypted images subjected to noise attacks. Consequently, the proposed model is more resilient against attacks that rely on salt and pepper noise.
Table 6. PSNR value of noise attacks.
4.1.3. JPEG compression attacks
It leverages the extensively utilised JPEG compression method, which employs lossy compression techniques to lessen image record sizes (Yuan et al., Citation2024). The attacks aim to exploit the lossy nature of JPEG compression to degrade the first-rate decrypted images, introducing distortions and artifacts that decrease the image's fidelity and reliability. The JPEG compression is applied, and Figure shows the outcome of five selected images. The proposed model improves defences against JPEG compression attacks. Hybrid encryption techniques strengthen encryption via random key integration inside the Feistel shape.
4.1.4. Physical brute-force attack
The attacker can access data physically by disassembling the devices and obtaining the disk. Also, the emergency access option can be enabled on most devices, granting access to essential tasks without authentication (Jiang et al., Citation2024). Therefore, it is important to prevent physical brute force by designing adequate physical defence measures. The proposed model combines the advantages of APFB to strengthen encryption against brute-force attacks. The Permuted Feistel Network adds another layer of complexity to resist brute-force attacks. Combining hybrid techniques produces a robust encryption mechanism with complicated key recovery that makes brute-force attacks challenging.
4.1.5. Man-in-the-middle attack
A Man-in-the-Middle (MITM) attack happens when an unauthorised third party eavesdrops on and manipulates the conversations between two parties. The attackers can steal important information or introduce malicious code by infiltrating the transmission process (Al-Hawawreh & Hossain, Citation2023). The AES offers robust encryption, and data security is enhanced by the random integration of keys within the permuted Feistel structure. Incorporating Blowfish enhances the encryption diversity, thereby augmenting the level of security. The multilayered technique creates a complex and dynamic cryptographic environment to protect against unauthorised access and tampering, effectively preventing any attempts of MITM attacks.
4.1.6. Insider attack
When authorised users do destructive or accidental things with a company's systems or data, it is known as an insider threat (Randive et al., Citation2023). While AES ensures strong encryption, permuted Feistel uses permutation functions to offer added protection. Blowfish's complex substitution-permutation network and key-dependent s-boxes strengthen defences against unauthorised access.
4.2. Statistical analysis
The proposed approach involves the sequential application of mixing procedures to pixels. The randomness of the randomised pixel is evaluated. The SP 800-22 test tool consists of 16 components developed by the National Institute of Standards and Technology (NIST) to test the randomness of the model (Yang et al., Citation2020). In this testing tool, a test is deemed successful if the P-value is greater than or equal to α. Here, α is equal to 0.01 and reflects the significance threshold. The test results from NIST are demonstrated in Table . Based on the test results, the P-values exceed the significance level α = 0.01, which indicates a high level of randomness in the pixel arrays developed by the model.
Table 7. NIST test outcome.
4.3. Comparative analysis with existing studies
Table displays the comparative analysis with the existing studies. However, it should be noted that the existing studies were performed in different environments, datasets, and techniques.
Table 8. A comparative study with the existing methods.
4.4. Case study
This case study considers a small health case solution with 30 employees. The organisation manages medical imaging data for patients and shares it with a third party as required. They have branches in two different cities. The organisation needs to enhance image security and transmission quickly, with optimal computing resources, and cost-effectively. The proposed APFB model is implemented to handle the existing challenges and store the image data through blockchain for secure data transmission. Adequate training sessions and awareness programs have been conducted for employees about the significance of image security, the key features, and the model's applicability. The proposed model reduced the encryption and decryption time with enhanced image security and reduced compute resources. The improved cryptographic technique and access controls helped control unauthorised access to patient images, improving confidentiality and privacy. The model prevents attacks like plaintext, noise, man in the middle, JPEG compression, and physical brute-force attacks. The experience of HealthCare Solutions serves as a realistic example of how companies can effectively address image security concerns to protect sensitive image information. This case study illustrates the practical application of the APFB model in enhancing image data security in a healthcare company.
5. Discussion, study limitation, and future studies
This study presented a novel APFB model for enhancing image security using hybrid cryptographic techniques. The effectiveness of this model is illustrated through comprehensive analysis using different evaluation matrices. The proposed model is easy to implement, fast, and reduces computing resources. This study presented a novel APFB model for enhancing image security with cost efficiency and reduced computing resources using hybrid cryptographic methods. The effectiveness of this model is illustrated through comprehensive analysis using different evaluation matrices. The proposed model is easy to implement, fast, and reduces computing resources. Experimental outcomes with PSNR, entropy, MSE, CC, NPCR, UACI, and processing time signify promising results. The proposed model is tested with the NIST randomness test, and the outcomes signify that the sequences utilised have reasonably adequate randomness. It is observed that the proposed model takes an average of 0.011 s to encrypt and 0.073 s to decrypt a standard 256 *256 image. This reduced time complexity makes the approach useful in practical scenarios where efficiency is important. The proposed model is further validated with a practical case study analysis.
5.1. Study limitations
This study has thoroughly examined image data security. However, it is important to note the study's limitations and constraints outlined below.
The proposed model is validated using a limited set of data.
The study employed limited computing resources for processing. A high-speed computer and different evaluation matrices can be explored for model evaluation.
With the proposed model, compatibility between different cryptographic algorithms can be challenging, especially when negotiating with various devices, platforms, or applications.
The proposed model may require significant memory for key management, especially in scenarios with large numbers of users or when handling vast datasets.
5.2. Future studies
The future studies are outlined under
As technology advances, attackers can employ more complex techniques to compromise encryption systems. Additional research is required to create hybrid encryption methods that resist sophisticated cryptanalysis techniques and adversarial attacks.
Encryption algorithms must balance between ensuring security and optimising computational performance. Subsequent future studies can prioritise the development of encryption methods that offer strong security while reducing processing resources.
Future studies should analyse the development of effective and flexible key management strategies. This will assist in safely overseeing encryption keys in extensive systems.
Future studies can explore the potential collaboration between image encryption and developing techniques, namely deep learning and edge computing, to create innovative methods that offer improved protection and enactment.
6. Conclusion
This study presented the hybrid APEB model for robust security, combining AES and Blowfish algorithms. This primary goal is to present and assess an exclusive method that combines cryptographic algorithms to strengthen data security. The encrypted and decrypted data is stored in the blockchain to ensure security. The proposed model is demonstrated to protect sensitive information during transmission to maintain confidentiality and authenticity for image data. The proposed model achieved a PSNR of 67.2697, an entropy of 14.4321, an MSE of 0.01219, an NPCR of 99.6354, and a UACI of 33.412 and is compared with existing studies. The proposed model is tested with the NIST statistical suite. Additionally, the applicability of the proposed model is validated with a practical case study. The proposed model significantly reduces computation costs and computation time. The proposed model can be further enhanced to improve performance and provide secure multimedia files like audio and video. Incorporating image encryption with the latest technologies can provide new research opportunities.
Acknowledgments
The authors are thankful to their departments for providing the research environments and facilities to perform this research. They also sincerely thank the anonymous reviewers for taking the time and effort to review the manuscript and appreciate all useful comments and recommendations, which helped improve quality.
Disclosure statement
No potential conflict of interest was reported by the author(s).
Additional information
Funding
References
- Abbas, S. Z., Ibrahim, H., & Khan, M. (2021). A hybrid chaotic blowfish encryption for high-resolution satellite imagery. Multimedia Tools and Applications, 80(17), 26069–26091. https://doi.org/10.1007/s11042-021-10898-w
- Abd-El-Atty, B., El-Affendi, M. A., Chelloug, S. A., & Abd El-Latif, A. A. (2023). Double Medical Image Cryptosystem Based on Quantum Walk. IEEE Access, 11, 69164–69176. https://doi.org/10.1109/ACCESS.2023.3289932
- Abdelfatah, R. I., Saqr, H. M., & Nasr, M. E. (2023). An efficient medical image encryption scheme for (WBAN) based on adaptive DNA and modern multi chaotic map. Multimedia Tools and Applications, 82(14), 22213–22227. https://doi.org/10.1007/s11042-022-13343-8
- Abu-Faraj, M., Al-Hyari, A., Al-Taharwa, I., Al-Ahmad, B., & Alqadi, Z. (2022). CASDC: A Cryptographically Secure Data System Based on Two Private Key Images. IEEE Access, 10, 126304–126314. https://doi.org/10.1109/ACCESS.2022.3226319
- Ahmad, N., & Hasan, S. M. R. (2021). A new ASIC implementation of an advanced encryption standard (AES) crypto-hardware accelerator. Microelectronics Journal, 117, 105255. https://doi.org/10.1016/j.mejo.2021.105255
- Ahuja, B., Doriya, R., Salunke, S., Hashmi, M. F., Gupta, A., & Bokde, N. D. (2023). HDIEA: high dimensional color image encryption architecture using five-dimensional Gauss-logistic and Lorenz system. Connection Science, 35(1), 2175792. https://doi.org/10.1080/09540091.2023.2175792
- Akkasaligar, P. T., & Biradar, S. (2020). Selective medical image encryption using DNA cryptography. Information Security Journal: A Global Perspective, 29(2), 91–101. https://doi.org/10.1080/19393555.2020.1718248
- Al-Hawawreh, M., & Hossain, M. S. (2023). A privacy-aware framework for detecting cyber attacks on internet of medical things systems using data fusion and quantum deep learning. Information Fusion, 99, 101889. https://doi.org/10.1016/j.inffus.2023.101889
- Alexan, W., Elkandoz, M., Mashaly, M., Azab, E., & Aboshousha, A. (2023). Color Image Encryption Through Chaos and KAA Map. IEEE Access, 11, 11541–11554. https://doi.org/10.1109/ACCESS.2023.3242311
- Alfrhan, A., Moulahi, T., & Alabdulatif, A. (2021). Comparative study on hash functions for lightweight blockchain in Internet of Things (IoT). Blockchain: Research and Applications, 2(4), 100036. https://doi.org/10.1016/j.bcra.2021.100036
- Ali, J., Jamil, M. K., Alali, A. S., Ali, R., & Gulraiz, G. (2024). A medical image encryption scheme based on Mobius transformation and Galois field. Heliyon, 10(1), e23652. https://doi.org/10.1016/j.heliyon.2023.e23652
- Arian, M., Saberi Kamarposhti, M., & Broumandnia, A. (2024). A New Method for Image Encryption Using DNA Sequences and Hyper Chaos. In M. Awang, H. H. Al-Kayiem, T. C. Bor, & S. S. Emamian (Eds.), in Advances in Material Science and Engineering (pp. 371–378). Springer Nature Singapore.
- Arif, J., Khan, M. A., Ghaleb, B., Ahmad, J., Munir, A., Rashid, U., & Al-Dubai, A.Y. (2022). A Novel Chaotic Permutation-Substitution Image Encryption Scheme Based on Logistic Map and Random Substitution. IEEE Access, 10, 12966–12982. https://doi.org/10.1109/ACCESS.2022.3146792
- Barik, K., Misra, S., & Fernandez-Sanz, L. (2024). Adversarial attack detection framework based on optimized weighted conditional stepwise adversarial network. International Journal of Information Security, 23, 2353–2376. https://doi.org/10.1007/s10207-024-00844-w
- Barik, K., Misra, S., Konar, K., Fernandez-Sanz, L., & Koyuncu, M. (2022). Cybersecurity Deep: Approaches, Attacks Dataset, and Comparative Study. Applied Artificial Intelligence, 36(1), 2055399. https://doi.org/10.1080/08839514.2022.2055399
- Barik, K., Misra, S., Ray, A. K., & Shukla, A. (2023). A blockchain-based evaluation approach to analyse customer satisfaction using AI techniques. Heliyon, 9(6), e16766. https://doi.org/10.1016/j.heliyon.2023.e16766
- Benoit, G., Raguideau, S., James, R., Phillippy, A. M., Chikhi, R., & Quince, C. (2024). High-quality metagenome assembly from long accurate reads with metaMDBG. Nature Biotechnology, 1–6. https://doi.org/10.1038/s41587-023-01983-6
- Ben Slimane, N., Aouf, N., Bouallegue, K., & Machhout, M. (2018). A novel chaotic image cryptosystem based on DNA sequence operations and single neuron model. Multimedia Tools and Applications, 77(23), 30993–31019. https://doi.org/10.1007/s11042-018-6145-8
- Chai, X., Fu, J., Gan, Z., Lu, Y., & Zhang, Y. (2022). An image encryption scheme based on multi-objective optimization and block compressed sensing. Nonlinear Dynamics, 108(3), 2671–2704. https://doi.org/10.1007/s11071-022-07328-3
- Chowdhary, C. L., Patel, P. V., Kathrotia, K. J., Attique, M., Perumal, K., & Ijaz, M. F. (2020). Analytical Study of Hybrid Techniques for Image Encryption and Decryption. Sensors, 20(18), 5162. https://doi.org/10.3390/s20185162
- Cun, Q., Tong, X., Wang, Z., & Zhang, M. (2023). A new chaotic image encryption algorithm based on dynamic DNA coding and RNA computing. The Visual Computer, 39(12), 6589–6608. https://doi.org/10.1007/s00371-022-02750-5
- Daoui, A., Yamni, M., Karmouni, H., Sayyouri, M., Qjidaa, H., Ahmad, M., & Abd El-Latif, A. A. (2022). Biomedical Multimedia Encryption by Fractional-Order Meixner Polynomials Map and Quaternion Fractional-Order Meixner Moments. IEEE Access, 10, 102599–102617. https://doi.org/10.1109/ACCESS.2022.3203067
- El-Shafai, W., Almomani, I., Ara, A., & Alkhayer, A. (2023). An optical-based encryption and authentication algorithm for color and grayscale medical images. Multimedia Tools and Applications, 82(15), 23735–23770. https://doi.org/10.1007/s11042-022-14093-3
- El Azzaoui, A., Sharma, P. K., & Park, J. H. (2022). Blockchain-based delegated Quantum Cloud architecture for medical big data security. Journal of Network and Computer Applications, 198, 103304. https://doi.org/10.1016/j.jnca.2021.103304
- Elkandoz, M. T., & Alexan, W. (2022). Image encryption based on a combination of multiple chaotic maps. Multimedia Tools and Applications, 81(18), 25497–25518. https://doi.org/10.1007/s11042-022-12595-8
- Elmoasry, A., Khan, L. S., Khan, M., & Hussain, I. (2022). A dual layer security scheme for medical images using Hessenberg and singular value decompositions. Multimedia Tools and Applications, 81(10), 14001–14022. https://doi.org/10.1007/s11042-022-12480-4
- Feng, W., Zhang, J., Chen, Y., Qin, Z., Zhang, Y., Ahmad, M., & Woźniak, M. (2024). Exploiting robust quadratic polynomial hyperchaotic map and pixel fusion strategy for efficient image encryption. Expert Systems with Applications, 246, 123190. https://doi.org/10.1016/j.eswa.2024.123190
- Gadde, S., Amutharaj, J., & Usha, S. (2023). A security model to protect the isolation of medical data in the cloud using hybrid cryptography. Journal of Information Security and Applications, 73, 103412. https://doi.org/10.1016/j.jisa.2022.103412
- Gao, X., Mou, J., Banerjee, S., & Zhang, Y. (2023). Color-Gray Multi-Image Hybrid Compression–Encryption Scheme Based on BP Neural Network and Knight Tour. IEEE Transactions on Cybernetics, 53(8), 5037–5047. https://doi.org/10.1109/TCYB.2023.3267785
- Ghorbani, A., Saberikamarposhti, M., & Yadollahi, M. (2022). Using Ribonucleic acid (RNA) and Hénon map in new image encryption scheme. Optik, 259, 168961. https://doi.org/10.1016/j.ijleo.2022.168961
- Gull, S., & Parah, S. A. (2024). Advances in medical image watermarking: a state of the art review. Multimedia Tools and Applications, 83(1), 1407–1447. https://doi.org/10.1007/s11042-023-15396-9
- Guo, W., Wang, Y., Chen, X., & Jiang, P. (2024). Federated transfer learning for auxiliary classifier generative adversarial networks: framework and industrial application. Journal of Intelligent Manufacturing, 35(4), 1439–1454. https://doi.org/10.1007/s10845-023-02126-z
- Gupta, M., Singh, V. P., Gupta, K. K., & Shukla, P. K. (2023). An efficient image encryption technique based on two-level security for internet of things. Multimedia Tools and Applications, 82(4), 5091–5111. https://doi.org/10.1007/s11042-022-12169-8
- Güvenoğlu, E. (2024). An image encryption algorithm based on multi-layered chaotic maps and its security analysis. Connection Science, 36(1), 2312108. https://doi.org/10.1080/09540091.2024.2312108
- Hadj Brahim, A., Ali Pacha, A., & Hadj Said, N. (2024). An image encryption scheme based on a modified AES algorithm by using a variable S-box. Journal of Optics, 53(2), 1170–1185. https://doi.org/10.1007/s12596-023-01232-8
- Hafsa, A., Fradi, M., Sghaier, A., Malek, J., & Machhout, M. (2022). Real-time video security system using chaos- improved advanced encryption standard (IAES). Multimedia Tools and Applications, 81(2), 2275–2298. https://doi.org/10.1007/s11042-021-11668-4
- Hasan, M. K., Islam, S., Sulaiman, R., Khan, S., Hashim, A. H. A., Habib, S., Islam, M., Alyahya, S., Ahmed, M. M., Kamil, S., & Hassan, M. A. (2021). Lightweight Encryption Technique to Enhance Medical Image Security on Internet of Medical Things Applications. IEEE Access, 9, 47731–47742. https://doi.org/10.1109/ACCESS.2021.3061710
- Herbadji, D., Herbadji, A., Haddad, I., Kahia, H., Belmeguenai, A., & Derouiche, N. (2024). An enhanced logistic chaotic map based tweakable speech encryption algorithm. Integration (tokyo, Japan), 97, 102192. https://doi.org/10.1016/j.vlsi.2024.102192
- Huang, X., Dong, Y., Zhu, H., & Ye, G. (2022). Visually asymmetric image encryption algorithm based on SHA-3 and compressive sensing by embedding encrypted image. Alexandria Engineering Journal, 61(10), 7637–7647. https://doi.org/10.1016/j.aej.2022.01.015
- Inam, S., Kanwal, S., Firdous, R., & Hajjej, F. (2024). Blockchain based medical image encryption using Arnold’s cat map in a cloud environment. Scientific Reports, 14(1), 5678. https://doi.org/10.1038/s41598-024-56364-z
- Jiang, D., Tsafack, N., Boulila, W., Ahmad, J., & Barba-Franco, J. J. (2024). ASB-CS: Adaptive sparse basis compressive sensing model and its application to medical image encryption. Expert Systems with Applications, 236, 121378. https://doi.org/10.1016/j.eswa.2023.121378
- John, S., & Kumar, S. N. (2023). IoT based medical image encryption using linear feedback shift register – Towards ensuring security for teleradiology applications. Measurement: Sensors, 25, 100676. https://doi.org/10.1016/j.measen.2023.100676
- Kiran, P., & Parameshachari, B. D. (2022). Resource Optimized Selective Image Encryption of Medical Images Using Multiple Chaotic Systems. Microprocessors and Microsystems, 91, 104546. https://doi.org/10.1016/j.micpro.2022.104546
- Lin, C.-H., Lai, H.-Y., Huang, P.-T., Chen, P.-Y., Pai, N.-S., & Zhang, F.-Z. (2024). Combining Riemann–Lebesgue-Based Key Generator and Machine-Learning-Based Intelligent Encryption Scheme for IoMT Images Infosecurity. IEEE Internet of Things Journal, 11(1), 1344–1360. https://doi.org/10.1109/JIOT.2023.3288678
- Lin, C.-C., Wang, P.-Y., Lin, Y.-H., Huang, H.-C., & Saberikamposhti, M. (2023). Visible Watermark Removal with Deep Learning Technology. In 2023 Sixth International Symposium on Computer, Consumer and Control (IS3C) (pp. 186–189). IEEE. https://doi.org/10.1109/IS3C57901.2023.00057.
- Man, Z., Li, J., Di, X., Sheng, Y., & Liu, Z. (2021). Double image encryption algorithm based on neural network and chaos. Chaos, Solitons & Fractals, 152, 111318. https://doi.org/10.1016/j.chaos.2021.111318
- Mansoor, S., & Parah, S. A. (2023). HAIE: a hybrid adaptive image encryption algorithm using Chaos and DNA computing. Multimedia Tools and Applications, 82(19), 28769–28796. https://doi.org/10.1007/s11042-023-14542-7
- Mehta, D., Jha, M., Suhagiya, H., & Mangrulkar, R. (2024). DieRoll: A Unique Key Generation and Encryption Technique. Journal of Applied Security Research, 19(2), 168–195. https://doi.org/10.1080/19361610.2022.2124589
- Nadhan, A. S., & Jeena Jacob, I. (2024). Enhancing healthcare security in the digital era: Safeguarding medical images with lightweight cryptographic techniques in IoT healthcare applications. Biomedical Signal Processing and Control, 88, 105511. https://doi.org/10.1016/j.bspc.2023.105511
- Nagarajan, S. M., Deverajan, G. G., Kumaran, U., Thirunavukkarasan, M., Alshehri, M. D., & Alkhalaf, S. (2022). Secure Data Transmission in Internet of Medical Things Using RES-256 Algorithm. IEEE Transactions on Industrial Informatics, 18(12), 8876–8884. https://doi.org/10.1109/TII.2021.3126119
- Nampalle, K. B., Manhas, S., & Raman, B. (2023). Medical image security and authenticity via dual encryption. Applied Intelligence, 53(17), 20647–20659. https://doi.org/10.1007/s10489-023-04550-3
- Patel, S., & Thanikaiselvan, V. (2023). Latin Square and Machine Learning Techniques Combined Algorithm for Image Encryption. Circuits, Systems, and Signal Processing, 42(11), 6829–6853. https://doi.org/10.1007/s00034-023-02427-x
- Patil, P., Narayankar, P., Narayan, D. G., & Meena, S. M. (2016). A Comprehensive Evaluation of Cryptographic Algorithms: DES, 3DES, AES, RSA and Blowfish. Procedia Computer Science, 78, 617–624. https://doi.org/10.1016/j.procs.2016.02.108
- Pourasad, Y., Ranjbarzadeh, R., & Mardani, A. (2021). A New Algorithm for Digital Image Encryption Based on Chaos Theory. Entropy, 23(3), 341. https://doi.org/10.3390/e23030341
- Pourjabbar Kari, A., Habibizad Navin, A., Bidgoli, A. M., & Mirnia, M. (2021). A new image encryption scheme based on hybrid chaotic maps. Multimedia Tools and Applications, 80(2), 2753–2772. https://doi.org/10.1007/s11042-020-09648-1
- Rahman, M., Murmu, A., Kumar, P., Moparthi, N. R., & Namasudra, S. (2024). A novel compression-based 2D-chaotic sine map for enhancing privacy and security of biometric identification systems. Journal of Information Security and Applications, 80, 103677. https://doi.org/10.1016/j.jisa.2023.103677
- Rakheja, P., & Khurana, M. (2023). Multiple iris image encryption using phase retrieval mask, QZ algorithm and umbrella map in hybrid transform domain. Optical and Quantum Electronics, 55(10), 878. https://doi.org/10.1007/s11082-023-05131-x
- Randive, K., Mohan, R., & Sivakrishna, A. M. (2023). An efficient pattern-based approach for insider threat classification using the image-based feature representation. Journal of Information Security and Applications, 73, 103434. https://doi.org/10.1016/j.jisa.2023.103434
- Sahlabadi, M., Saberikamarposhti, M., Muniyandi, R. C., & Shukur, Z. (Oct. 2022). Using Cycling 3D Chaotic Map and DNA Sequences for Introducing a Novel Algorithm for Color Image Encryption. In 2022 International Conference on Cyber Resilience (ICCR) (pp. 1–7). IEEE.
- Sarosh, P., Parah, S. A., Malik, B. A., Hijji, M., & Muhammad, K. (2023). Real-Time Medical Data Security Solution for Smart Healthcare. IEEE Transactions on Industrial Informatics, 19(7), 8137–8147. https://doi.org/10.1109/TII.2022.3217039
- Singh, K. N., & Singh, A. K. (2022). Towards Integrating Image Encryption with Compression: A Survey. ACM Transactions on Multimedia Computing, Communications, and Applications, 18(3), 1–21. https://doi.org/10.1145/3498342
- Singh, C. E. J., & Sunitha, C. A. (2022). Chaotic and Paillier secure image data sharing based on blockchain and cloud security. Expert Systems with Applications, 198, 116874. https://doi.org/10.1016/j.eswa.2022.116874
- Soppari, K., & Chandra, N. S. (2023). Automated digital image watermarking based on multi-objective hybrid meta-heuristic-based clustering approach. International Journal of Intelligent Robotics and Applications, 7(1), 164–189. https://doi.org/10.1007/s41315-022-00241-3
- Toktas, A., Erkan, U., Gao, S., & Pak, C. (2024). A robust bit-level image encryption based on Bessel map. Applied Mathematics and Computation, 462, 128340. https://doi.org/10.1016/j.amc.2023.128340
- Ullah, S., Zheng, J., Din, N., Hussain, M. T., Ullah, F., & Yousaf, M. (2023). Elliptic Curve Cryptography; Applications, challenges, recent advances, and future trends: A comprehensive survey. Computer Science Review, 47, 100530. https://doi.org/10.1016/j.cosrev.2022.100530
- Vandic, D., Nederstigt, L. J., Frasincar, F., Kaymak, U., & Ido, E. (2024). A framework for approximate product search using faceted navigation and user preference ranking. Data & Knowledge Engineering, 149, 102241. https://doi.org/10.1016/j.datak.2023.102241
- Veera, D., Mangrulkar, R., Bhadane, C., Bhowmick, K., & Chavan, P. (2024). Modified Caesar Cipher and Card Deck Shuffle Rearrangement Algorithm for Image Encryption. Journal of Information and Telecommunication, 8(2), 280–300. https://doi.org/10.1080/24751839.2023.2285549
- Wen, H., Lin, Y., Yang, L., & Chen, R. (2024). Cryptanalysis of an image encryption scheme using variant Hill cipher and chaos. Expert Systems with Applications, 250, 123748. https://doi.org/10.1016/j.eswa.2024.123748
- Xie, H., Zhang, Y., Zhang, H., & Li, Z. (2023). Novel medical image cryptogram technology based on segmentation and DNA encoding. Multimedia Tools and Applications, 82(18), 27593–27613. https://doi.org/10.1007/s11042-023-14546-3
- Yang, F., Mou, J., Sun, K., & Chu, R. (2020). Lossless image compression-encryption algorithm based on BP neural network and chaotic system. Multimedia Tools and Applications, 79(27–28), 19963–19992. https://doi.org/10.1007/s11042-020-08821-w
- Yu, C., Zhang, X., Qin, C., & Tang, Z. (2023). Reversible Data Hiding in Encrypted Images With Secret Sharing and Hybrid Coding. IEEE Transactions on Circuits and Systems for Video Technology, 33(11), 6443–6458. https://doi.org/10.1109/TCSVT.2023.3270882
- Yuan, Y., He, H., Chen, F., & Qu, L. (2024). On the security of JPEG image encryption with RS pairs permutation. Journal of Information Security and Applications, 82, 103722. https://doi.org/10.1016/j.jisa.2024.103722
- Zhang, B., Rahmatullah, B., Wang, S. L., Zaidan, A. A., Zaidan, B. B., & Liu, P. (2023). A review of research on medical image confidentiality related technology coherent taxonomy, motivations, open challenges and recommendations. Multimedia Tools and Applications, 82(14), 21867–21906. https://doi.org/10.1007/s11042-020-09629-4
- Zhou, W., Gao, S., Zhang, L., & Lou, X. (2020). Histogram of Oriented Gradients Feature Extraction From Raw Bayer Pattern Images. IEEE Transactions on Circuits and Systems II: Express Briefs, 67(5), 946–950. https://doi.org/10.1109/TCSII.2020.2980557
- Zhu, S., Deng, X., Zhang, W., & Zhu, C. (2023). Secure image encryption scheme based on a new robust chaotic map and strong S-box. Mathematics and Computers in Simulation, 207, 322–346. https://doi.org/10.1016/j.matcom.2022.12.025