ABSTRACT
Whilst NATO speaks increasingly publicly about the military use of cyber operations, adaptation to the cyber domain has reportedly been challenging for most militaries. Little research has sought to understand the nature of these challenges. This study seeks to address this gap through a case study of the Netherlands. By utilizing a range of primary and secondary sources, this article reveals that the Dutch Defense Cyber Command has faced significant constraints in its adaptation to the cyber domain, primarily due to issues related to organizational structure, operational mandate, and the availability of skills and resources. A cyber command that lacks regular opportunities for day-to-day operations and where personnel may not have continuous learning opportunities to acquire and refine their skills will encounter difficulties in recruiting, training, and retaining a proficient workforce. These findings highlight the tendency of observers to mistakenly equate the mere establishment of a cyber command with the existence of a robust military cyber capability – namely, the ability to effectively carry out and sustain a range of cyber operations for tactical or strategic purposes.
The establishment of military cyber commands has become increasingly prevalent among NATO countries. By 2018, there were 61 countries worldwide with active-duty military organizations (often referred to as ‘cyber forces’ in this context) possessing the capability and authority to conduct cyberspace operations, influencing diplomatic and military interactions.Footnote1 Among them, 23 were NATO members. This represents a significant surge compared to 2007 when only ten countries, including three NATO nations, had military cyber forces. Additionally, numerous countries have expressed their willingness to contribute sovereign cyber effects to NATO missions if the need arises.
However, it is important to exercise caution when assessing the extent of this advancement. While the establishment of cyber commands is widespread, many NATO-allied militaries have encountered challenges in adapting to the complexities of the cyber domain. Only a few NATO allies have been recognized for conducting cyber effect operations, which involve disruptive, denying, degrading, and potentially destructive actions.Footnote2 Several states continue to grapple with the integration of cyber operations into their strategic outlook and legal framework. Notably, scholars Matthias Schulze and Sven Herpig highlight Germany’s efforts to build offensive cyber capabilities without a clearly defined strategic purpose, reflecting a recurring problem in German national security policy.Footnote3
Despite the significance of developing a military cyber capacity, there has been a dearth of research dedicated to examining the challenges associated with this endeavor. Gaining a deeper understanding of these challenges is important, however, as it directly impacts our understanding of the militarization of cyberspace and shapes the trajectory of cyber conflict in the future.
The lack of critical attention towards understanding the challenges of developing a military cyber capacity can be attributed to two potential reasons. Firstly, scholarly research has primarily focused on studying the United States and a limited set of other prominent actors, such as Russia, China, North Korea, and Iran, who are extensively engaged in cyberspace activities. Not as much attention is paid to less active militaries. Secondly, investigating the military adaptation of states to the cyber domain necessitates delving into the internal workings of these states, which presents inherent difficulties due to the sensitive nature of such information. This requirement to ‘open the black box’ and gain insights into internal processes often poses significant challenges.
This study helps to address this gap through an exploratory case study of the Dutch Defence Cyber Command (DCC), established in June 2015.Footnote4 Exploratory case studies as a qualitative method are useful as a form of analysis in fields where data collection is challenging and there is no single set of (predetermined) outcomes.Footnote5 For this case study, I rely on various publicly available sources, such as reports of parliamentary debates, official government statements and publications, the academic literature, and media reports. I complement these sources with my own anonymized interview data with key individuals from the intelligence services, defence forces, private sector, think tanks and academia, and non-anonymized interview data from existing research and journalistic reporting.
The analysis of the case study highlights the challenges faced by the Dutch Defense Cyber Command (DCC) in developing an operational capacity. These challenges stem from the interaction between its strategic outlook, operational mandate, and the availability of skills and resources. As Rosen points out, ‘[a]lmost every government bureaucracy has a function it executes on a day-to-day basis. Military organizations, in contrast, exist in order to fight a foreign enemy, and do not execute this function every day. Most of the time, the countries they serve are at peace. Military organizations plan and prepare for war, but they do not fight’.Footnote6 Similarly, the Dutch cyber command operates with a wartime mission and does not engage in day-to-day combat. However, its ability to effectively plan and prepare for war during peacetime is limited. One of the key challenges arises from the fact that the DCC lacks a mandate to conduct reconnaissance, making it difficult to identify potential targets and adequately prepare operations well in advance.
Moreover, the case study underscores the interplay between strategy development and the development of cyber capabilities. At its core, building a cyber capability hinges on the skills and knowledge of individuals involved. The strategic approach adopted by countries has profound implications for their capacity to cultivate a skilled and capable cyber force. A cyber command that lacks regular opportunities for day-to-day operations and where personnel may not have continuous learning opportunities to acquire and refine their skills will encounter difficulties in recruiting, training, and retaining a proficient workforce.
These findings indicate that there is a tendency among observers to mistakenly equate the mere establishment of a cyber command with the presence of a robust military cyber capability. In reality, a meaningful military cyber capability refers to the ability to effectively execute and sustain a range of cyber operations that serve tactical or strategic purposes. This misconception often leads to exaggerated media reports regarding advancements in cyber warfare, highlighting the need for caution when referencing indices that measure states’ cyber power. Moreover, the results of this study underscore the limited extent to which allies are adopting the proactive approach of US Cyber Command in cyberspace, commonly referred to as persistent engagement.Footnote7
This article is outlined as follows. The next section puts the DCC’s establishment in historical context and provides a budget overview of the organization. Section two subsequently discusses the strategic role of the DCC. In Section three, I then look at the organizational and legal mandate of the military command vis-à-vis the intelligence agencies. Section four brings the insights from the previous sections together to show the challenges for the DCC to develop a capability considering its limited (peacetime) mandate. The final section summarizes the main arguments and discusses the several implications of this study.
A modern military force on the cheap
In 2012, the Dutch Ministry of Defence established a ‘Taskforce Cyber’ with the objective of strengthening the digital capabilities of the Ministry. As a result, the Defence Cyber Command (DCC) was established in June 2015.Footnote8 Initially, the DCC was organizationally situated within the Royal Netherlands Army. However, in July 2018, it was elevated to a command component directly reporting to the Chief of Defence of the Armed Forces.
During a period characterized by a significant decline in Dutch defense spending, the institutional establishment and development of the Defense Cyber Command (DCC) unfolded. The Dutch government had been steadily reducing the defense budget since the early 1990s,Footnote9 resulting in a critical juncture in 2013–2014 when the budget reached an unprecedented low. At that time, the Netherlands allocated just slightly above one percent of its gross national product towards defense expenditure.Footnote10
However, despite the downsizing of the military forces, there was still room for investment in cyber operations.Footnote11 In fact, this investment can be viewed as a significant factor since the relatively modest allocation of resources towards cyber operations allowed the Dutch government to showcase the modernization of their armed forces during a period marked by extensive austerity measures and reductions in the defense budget. A letter dated 8 April 2011, from the Dutch Minister of Defence to the House of Representatives effectively captures this sentiment.Footnote12 The opening statement of the letter reads as follows: ‘The state of the national budget forces the government to take drastic measures. The Ministry of Defence is not exempt from this and is faced with the tough task of structurally cutting € 635 million within the next few years, approximately 9% of the part of the defence budget that can be affected’.Footnote13 The letter then continuous providing a long list of required budget cuts for the armed forces. But, the Minister of Defence notes ‘[a] military that does not prepare for the future is vulnerable. That is why it is important to create room for intensifications and innovation in the coming years’.Footnote14 For this reason, the Minister further writes ‘Cyber is for the military a weapon system in development. To ensure the deployability of the Dutch armed forces and to increase its effectiveness, Defence will strengthen its digital resilience in the coming years and develop the capacity to carry out cyber operations’.Footnote15
provides the budget overview of the cyber command and taskforce ‘cyber’.Footnote16 The presented data illustrates that the annual expenditure of the DCC on the development of their cyber force has not exceeded 25 million euros, with particularly limited structural investments. While drawing definitive conclusions solely based on budget figures is challenging, the available data implies that the Dutch cyber command lacks the necessary resources to sustain a comprehensive range of complex operations. However, it is plausible that the DCC could potentially carry out smaller-scale cyber effect operations effectively, given efficient resource allocation. The allocated budget for personnel should be adequate for recruiting and retaining skilled operators, developers, analysts, and other essential personnel.Footnote17
Figure 1. Overview budget Dutch defence cyber command and taskforce ‘cyber’ 2012–2019.
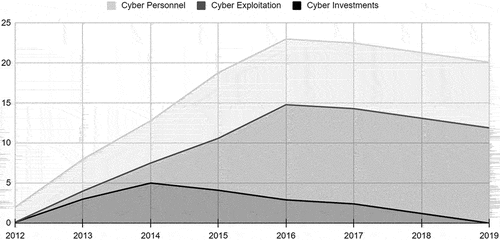
Furthermore, a shift in the perception of the necessary resources and level of sophistication for operations has occurred. Initially, earlier reports, such as the 2012 defense cyber strategy, emphasized the requirement for complex operations. However, DCC officials have subsequently highlighted the potential effectiveness of less advanced activities that can still achieve the desired objectives. This change in perspective acknowledges the value of more streamlined approaches in accomplishing the mission. As brigadier-general Paul Ducheine notes after the cyber command was launched, ‘[the DCC commander] does for sure have a toolbox with cyber weapons. However, it does not necessarily have to be an advanced, tailor-made tool à la Stuxnet. With a standard DDoS you can also shut down a website. Sometimes a bow and arrow can be enough’.Footnote18
Operating during conflict and beyond?
The primary role of the DCC has consistently been to offer military assistance to other forces during times of armed conflict. The initial Defense Cyber Strategy, released in 2012, asserts that it is imperative for the Defense organization to possess adequate knowledge and capabilities to engage in offensive operations in cyberspace. This capability is crucial not only for mounting a robust defense but also for supporting military operations effectively. The strategy emphasizes the need to develop sophisticated and technologically advanced assets, methodologies, and expertise that are specifically designed to enhance the military capability of the Netherlands.Footnote19 The strategy furthermore states that “[a] cyber attack on an air defence system may thus increase the effectiveness of an air attack while reducing the risk of collateral damage. An offensive cyber capability can be a force multiplier and thus increase the armed forces’ effectiveness. By developing a robust cyber capability, the Netherlands can play an important role within NATO in this respect”.Footnote20
In 2015, the Dutch Ministry of Defence published their second strategy. It followed the same line of thinking about the need to ‘strengthen the use of cyber in military missions’.Footnote21 The concept of employing cyber operations as a valuable asset during armed conflict was reiterated frequently in media interviews with military commanders. This highlights the recognition and emphasis placed on the strategic significance of cyber operations in the context of military engagements. For example, general Hans Folmer, the first Commander of the Dutch cyber command rhetorically asks a news reporter: ‘Why would you throw a bomb on a power plant if it can also be disabled with a computer attack? This damage is temporary and therefore the population suffers much less’.Footnote22
The publication of the third cyber defense strategy in 2018 reaffirms the significant role of cyber operations as an integral component of military operational planning. According to the strategy ‘The digital aspect is considered at an early stage of the planning phase of each (potential) mission. This is expressed in (military) advice and analyzes by the Operations Directorate and in subsequent (operations) plans’.Footnote23 To this extent, the Dutch government is one of the first countries that has signed on to offer their ‘sovereign cyber effect’ to the NATO alliance if the need arises.Footnote24
A notable shift in the latest strategy is its increased emphasis on the role of deterrence.Footnote25 According to the 2018 Cyber Defence Strategy: ‘The operational capabilities of the Defence cyber command contribute to the total arsenal of deterrent means available to the government. Deterrence makes the Netherlands less attractive as a target for (cyber) attacks and is therefore above all a tool for conflict prevention’.Footnote26 As stated by one of the principal authors of the strategy, ‘Good deterrence is about visible, credible and offensive capacity. Defence in itself is not a deterrent. It is not without reason that there are military parades on the Red Square or the Champs-Élysées. Something like that should also be done in the field of cyber’.Footnote27
This implies that the Dutch government’s approach to cybersecurity deviates from the emerging perspectives in the United States regarding the role of US Cyber Command. In 2018, the US Cyber Command unveiled its vision of Persistent Engagement, along with the Department of Defense’s introduction of the Defend Forward strategy.Footnote28 Jason Healey described the release of these documents as the most significant expression of cyber policy in the last two decades.Footnote29 The US Cyber Command vision offers ‘a roadmap for USCYBERCOM to achieve and maintain superiority in cyberspace as we direct, synchronize, and coordinate cyberspace planning and operations to defend and advance national interests in collaboration with domestic and foreign partners’.Footnote30 The vision emphasizes continual and persistent engagement against malicious cyberspace actors. According to Fischerkeller and Harknett, ‘persistent engagement recognizes that cyberspace’s structural feature of interconnectedness and its core condition of constant contact creates a strategic necessity to operate continuously in cyberspace’.Footnote31 Cyber Command’s transition towards persistent engagement stems from an alternative perception of the threat landscape. Departing from the conventional notion that cyber operations primarily involve tactical espionage, subversion, or sporadic instances of theft and crime, this perspective recognizes these operations as significant tools within the realm of great power competition. By linking a series of cyber operations below the threshold of an armed attack, cohesive campaigns can yield strategic outcomes of strategic importance.Footnote32 The Dutch government increasingly recognizes the strategic importance of below the threshold activity.Footnote33 The 2018 Defense Strategy also states: ‘State actors and criminal groups are operating less and less cautiously in the digital domain. Cyber attacks and incidents are the order of the day. They can no longer be seen as stand-alone, isolated incidents. More and more often these are interrelated incidents, which together form a campaign of state actors and their proxies, intended to undermine the economic revenue model, the vital infrastructure, the military capabilities or the democratic order of countries’.Footnote34 Furthermore, there is a recognition that deterring this specific form of activity presents inherent difficulties. Nevertheless, the government shows reluctance in embracing the approach employed by the United States, which entails granting the DCC a more proactive role in persistently disrupting adversarial behavior in cyberspace.Footnote35
Organizational and legal mandate
An effective operation in cyberspace hinges on having superior knowledge of your adversary’s networks. While it is sometimes assumed that cyber activity occurs instantaneously, the truth is that cyber operations require time. As these operations must be customized to the specific computer systems and networks involved, advanced actors often invest significant time in establishing the foundation for future attacks, a process known as operational preparation of the environment (OPE).Footnote36 Hence, if the DCC would like to generate ‘effects’ in conflicts, it has to anticipate this well in advance to ensure it has the right level of access to the systems it would like to target. However, the DCC lacks the authority to carry out such preparatory activities. Instead, this authority rests with the Dutch intelligence services, which are organizationally distinct from the DCC.Footnote37
While the Dutch Defense Cyber Command (DCC) operates within the jurisdiction of the Armed Forces, the Military Intelligence and Security Service (MIVD) operates under the purview of the Secretary-General. This distinction has implications for the working methodology and legal framework of the DCC.Footnote38 The Dutch armed forces operate under the authority and guidance of the Chief of Defence (Commandant der Strijdkrachten), as specified by Article 97 of the Dutch constitution.Footnote39 The deployment of military assets within the Netherlands necessitates a decision by the government. Alternatively, a more discreet process can be followed through the Article 100 procedure, whereby the Ministerial Core Group Special Operations (Ministeriële Kerngroep voor Speciale Operaties) assumes responsibility for making deployment decisions.Footnote40
The mandate of the MIVD is derived from the Intelligence and Security Services Act (Wet op de Inlichtingen en Veiligheidsdiensten, WIV).Footnote41 The Chief of Defense does not possess authority over the MIVD. In cases where it is deemed necessary for national security, the MIVD may engage in hacking activities targeting systems or networks. However, DCC is prohibited from gathering information during times of peace.Footnote42 This authority lies with the MIVD.
In 2014, the MIVD collaborated with the civilian General Intelligence and Security Service (AIVD) to create the Joint SIGINT Cyber Unit (JSCU) as part of the collaborative initiative known as ‘Project Symbolon’.Footnote43 The JSCU is responsible for conducting cyber operations involving signals interception and intelligence collection, as mentioned earlier. It was also the unit that successfully infiltrated the computer networks of Russian hacker group(s) in mid-2014. However, it is important to note that carrying out specific effects on target systems falls within the jurisdiction of the Ministry of Defence and is not covered by the provisions of the Intelligence and Security Services Act.Footnote44
The organizational structure and mandates in place create challenges for the operations of the DCC. As Pijpers notes, ‘in principle, the roles and tasks are clear, but the problem lies in the preparation. How will the DCC ever fulfill its role (cyber [operations] during armed conflict) if it is not allowed to do anything in peacetime?’Footnote45
Transferring relevant access from the intelligence services to the DCC is not a straightforward process. As highlighted by two anonymous employees from the MIVD, explicit information regarding access positions, such as login credentials and command-and-control server (C2 server) operations, is often only effective when combined with extensive implicit knowledge about the target and its environment.Footnote46
The strategy-capability linkage: recruiting, training, and retaining talent
The preceding discussion unveils that the establishment of the Dutch cyber command primarily aimed at conducting operations during wartime. However, the DCC is not permitted to carry out cyber effects or even engage in reconnaissance during peacetime. This absence of a peacetime mission and operational activity consequently hampers their capacity to cultivate an effective cyber force.Footnote47
The fundamental aspect in building a military cyber force lies not in the acquisition of material resources, but in the recruitment, training, and retention of skilled individuals.Footnote48 One often hears that a compelling aspect of working at a cyber command, which attracts capable personnel, is the opportunity to engage in activities that are typically prohibited in the private sector.Footnote49 However, due to the limitations imposed on the DCC, this notion is hardly applicable. Moreover, it becomes challenging to cultivate and enhance skills among personnel if the cyber command operators are prohibited from engaging in actual operations. As Boekholt-O’Sullivan also states “The young and highly motivated cyber experts within the DCC are having problems with the current mandate and its legal framework. Lawyers are blocking the cyber experts’ imagination, improvisation, and creativity which are necessary for future cyber scenarios”.Footnote50
In order to facilitate the development of its workforce, the DCC has pursued three approaches. Firstly, it has established a cyber range and actively participates in cyber exercises. In 2016, Thales constructed a cybersecurity training and testing facility, known as a ‘cyber range’, specifically for the DCC’s use.Footnote51 As general Folmer, then commander of the DCC notes, ‘It is a facility at which many forms of cyber operations can be simulated. This is essential for training our staff and testing our systems’.Footnote52 The Dutch DCC officers (together with personnel from other departments such as the CERT) are also participating in international cyber security exercises. The largest international cyber defence exercise offering ‘the most complex technical live-fire challenge in the world’ is Locked Shields, organized by the NATO Cooperative Cyber Defence Centre of Excellence.Footnote53 The Dutch participated for the first time in 2013. During the exercise, defending ‘blue’ teams had to defend a pre-built network consisting of roughly 35 virtual machines against the attacking ‘red’ teams.Footnote54 In 2014 and 2015, the Dutch participated with a combined team together with Germany (the first multinational team to join the exercise in history).Footnote55 In the years that followed, the Dutch has always participated with at least one blue team.Footnote56
Second, the DCC decided early on to rely on reservists: these are civilian cyber specialists the cyber command can call upon in case they require their assistance.Footnote57 In 2016, the DCC had appointed thirteen cyber reservists, while another ten people were going through the appointment procedure.Footnote58 In November 2018, the number of reservists had increased to 30, but was still far below the initial target of 150.Footnote59 The Ministry of Defense therefore set up a pilot project to recruit more cyber reserves in late 2018.Footnote60 The government regularly organized ‘matching days’ throughout the year to identify potential cyber reservists who would be suitable for the role. Unlike other military personnel, these candidates could be exempted from certain physical and medical requirements. By October 2019, the number of reservists had reached 72, indicating an increase in their ranks.Footnote61 Furthermore, there are an additional 48 aspiring cyber reservists who have been selected, with nine of them undergoing a modified procedure that exempts them from the usual physical tests required to join the armed forces. These individuals are currently awaiting their official appointments.Footnote62
Third, the Dutch government has established joint cyber mission teams. The joint cyber mission teams, as the name suggests, are mission-focused and consist of operators from both the cyber command and the JSCU. The 2018 cyber strategy explains the rationale behind these teams: ‘With a view to making military capability possible in the cyber domain, in-depth knowledge about vulnerabilities in the systems of potential opponents must be acquired at an early stage. By virtue of its constitutional tasks, the MIVD supports the DCC with intelligence that is necessary for effective military deployment in the cyber domain. The knowledge and skills necessary for intelligence operations and military operations in the cyber domain are similar. Following the example given by other countries, cyber mission teams will therefore be formed from MIVD personnel and personnel from the armed forces. The designated personnel will operate within the regulatory framework of the Intelligence and Security Services Act. When the armed forces are deployed, they will be placed under the command of the Chief of Defence within the relevant mandate’.Footnote63
Conclusion
An increasing number of NATO members have established military cyber commands to address the challenges of the cyber domain. This study focused on the Netherlands as a case study to highlight the key challenges faced by militaries in establishing their cyber warfighting structures. The analysis revealed that the Dutch Defence Cyber Command encounters a range of interconnected challenges, impeding the development of an operational capacity. These challenges include strategic outlook and organizational mandates that restrict the organization’s ability to execute operations efficiently, hinder organizational and individual learning, and pose difficulties in talent retention.
The capacity of cyber commands to recruit, train, and retain skilled individuals is likely to vary based on their specific mandate. When comparing similar factors, a cyber command that focuses on deterring adversarial activity and operates exclusively within adversary networks during wartime will face greater challenges in maintaining the skills and knowledge of their cyber warriors. It becomes more difficult for such a command to ensure continuous development and up-to-date expertise.
The Dutch cyber command, as an exploratory case study, has outlined three options to reduce the (negative) linkages between strategy development and capability generation. This thus leads to a set of questions for further research: how effective are each of these policies? An early assessment suggests that there are significant limits to each policy. Firstly, cyber exercises can only provide a partial simulation of real cyber operations, making it challenging for cyber commands to establish comprehensive standard operating procedures based solely on these activities.Footnote64 Secondly, while input from the private sector is valuable, it introduces additional complexities and obstacles of its own.Footnote65 Effective defense or offense in cyberspace necessitates a deep understanding of the target system. This renders a ‘plug and play’ approach with reserves less than ideal.Footnote66 Additionally, national security clearances pose a challenge. The thorough screening of reservists to ensure their compatibility with the intelligence services and their integration into DCC teams is both time-consuming and costly.Footnote67 Ultimately, the cyber mission teams emerge as the most hopeful initiative, although the Dutch Ministry of Defense did not deem it necessary to test the concept through the Article 100 procedure during missions in Mali or Iraq. However, as Boeke points out, even if cyber mission teams are deployed, it would only result in a DCC with restricted capabilities for minor interventions – a sort of miniature cyber staffing agency. In reality, the majority of expertise remains within the JSCU.Footnote68
Disclosure statement
No potential conflict of interest was reported by the author(s).
Additional information
Notes on contributors
Max Smeets
Max Smeets is a Senior Researcher at the Center for Security Studies (CSS) at ETH Zurich and Director of the European Cyber Conflict Research Initiative. He is the author of 'No Shortcuts: Why States Struggle to Develop a Military Cyber- Force’ (Oxford University Press & Hurst Publishers, 2022) and co-editor of ‘Deter, Disrupt or Deceive? Assessing Cyber Conflict as an Intelligence Contest’ (Georgetown University Press, 2023) and 'Cyberspace and Instability' (Edinburgh University Press, 2023).
Notes
1. Blessing, ‘The Diffusion of Cyber Forces’.; also see: Smeets, “NATO Members’ Organizational Path Towards Conducting Offensive Cyber Operations”.
2. The definition of cyber effect operations is based upon the U.S. intelligence concept of Computer Network Attack (CNA). It can be distinguished from Computer Network Exploitation (CNE), commonly referred to as cyber espionage. For a longer discussion see: Wiener, “Penetrate, Exploit, Disrupt, Destroy; Monte, Network Attacks and Exploitation; This is not to say NATO members have been inactive in cyberspace altogether. The Cyber Operations Tracker by the Council on Foreign Relations, one of the most comprehensive databases of publicly known state-sponsored cyber activity, attributes a wide number of cyber espionage activities to the intelligence agencies of various NATO countries. However, it only has NATO entries for the United States and the United Kingdom conducting cyber effect operations. Council on Foreign Relations, ‘Cyber Operations Tracker’.
3. Matthias Schulze and Sven Herpig, ‘Germany Develops Offensive Cyber Capabilities Without A Coherent Strategy of What to Do With Them’, Council on Foreign Relations, (2018, December 3), https://www.cfr.org/blog/germany-develops-offensive-cyber-capabilities-without-coherent-strategy-what-dothem
4. The Netherlands is at about the median of the NATO alliance in terms of resources officially allocated to the cyber command, spending about 10–25 million euros a year on cyber warfare. This spending is slightly higher compared to some allies – such as Spain or Denmark – but below that of the larger powers in the alliance such as Germany and France.
5. Yin, Applications of Case Study Research; Yin, ‘Case Study Evaluations’
6. Rosen, Winning the next War.
7. For a discussion on different strategic understandings of cyber behavior see: Robert Chesney and Max Smeets (Eds.), Deter, Disrupt, or Deceive: Assessing Cyber Conflict as an Intelligence Contest, (Washington DC: Georgetown University Press: 2023)
8. Ministerie van Defensie, ‘Defensie Cyber Strategie 2018’; also see Ducheine and Arnold, ‘Besluitvorming Bij Cyberoperaties’. Ducheine, Arnold, and Pijpers, ‘Decision-Making and Parliamentary Control for International Military (Cyber) Operations by the Netherlands Armed Forces’.
9. SIPRI, ‘SIPRI Military Expenditure Database | SIPRI’.|‘SIPRI Military Expenditure Database | SIPRI’.; Bentinck, ‘Why the Dutch Military Punches below Its Weight’.
10. Since 2016 defence spending has gone up in the Netherlands. Budgets are however as the government has changed its definition of ‘defence spending’. For example, in recent years the defence budget also included spending the coastal guard and ‘international safety’ of foreign development aid to make it seem as if spending was not at a historical low. Schramade, ‘Defensiebudget Historisch Laag … ’ Ministry of Defense, ‘Opnieuw Extra Geld Voor Defensie in 2016–01 – Defensiekrant’. Striek, ‘Meer Geld?’.
11. The only two projects which stand out from the early 2000s in the Dutch context are the F-35 Joint Strike Fighter (JSF) program and the establishment of the DCC. The JSF program is a program intended to replace a wide range of existing fighter, strike, and ground attack aircraft for a number of Western countries. See: U.S. Government, ‘The F-35 Lightning II’. A potential third programme would concern the use of four medium-altitude long-endurance unmanned aerial vehicles (MALE UAV). See: Clingendael Institute, ‘Ambitieniveau Defensie Op Droevig Dieptepunt’.
12. Ministerie van Defensie, ‘Defensie Cyber Strategie 2018’.
13. Author’s translation. Ibid.
14. Author’s translation. Ibid.
15. Minister van Defensie, ‘Defensie Cyber Strategie’.
16. Claver, ‘Governance of cyber warfare in the Netherlands’.; It is hard to provide a comprehensive overview of the Dutch budget over the years considering the inconsistencies and changes in budget structure. See for example: Adviesraad Internationale Vraagstukken, ‘Digitale Oorlogvoering’; Boere, ‘Leger Zoekt 150 Whizzkids Voor Cyber Commando’. Ministerie van Algemene Zaken, ‘Antwoord Op Kamervragen over de Vaststelling van de Begrotingsstaten van Het Ministerie van Defensie (X) Voor Het Jaar 2022 - Kamerstuk – Rijksoverheid.nl’.
17. For an overview of key workforce requirements see: Smeets, No Shortcuts, Chapter 5.
18. Alberts and Lensink, ‘Te Land, Ter Zee En Op Het Web’; Also: Author’s interview 21, 2015, The Hague; Author’s interview 22, 2015, The Hague.
19. Author’s translation. The Ministry of Defence, ‘The Defence Cyber Strategy’.
20. Author’s translation. Ibid.
21. The Ministry of Defence, ‘The Defence Cyber Strategy’, (2016); also see: Tweede Kamer der Staten-Generaal, ‘Defensie Cyber Strategie’. Tweede Kamer der Staten-Generaal, ‘Voortgangsrapportage over de uitvoering van de Defensie Cyber Strategie’.
22. Boere, ‘Leger Zoekt 150 Whizzkids Voor Cyber Commando’.
23. Ministerie van Defensie, ‘Defensie Cyber Strategie 2018’.
24. NATO – as an organization – does not own military cyber capabilities, but has developed the Sovereign Cyber Effects Provided Voluntarily by Allies (SCEPVA) mechanism, coordinated through the new Cyber Operations Center established in 2018. NATO, ‘Allied Joint Doctrine for Cyberspace Operations’. Discussions on this type of command structure go back since at least 2016. See: Alatalu, ‘One Year after Warsaw’
25. Author’s interview 25, 2018, The Hague.
26. Ministerie van Defensie, ‘Defensie Cyber Strategie 2018’.
27. Lonkhuyzen and Versteegh, ‘“Cyberleger”’; also see: Maarten, ‘Geloofwaardige Afschrikking in Het Cyberdomein?’.
28. The relationship between the concepts Persistent Engagement and Defend Forward remains contested. The common understanding is that persistent engagement as an operationalization of the defend forward strategy. See for example, Goldman, ‘From Reaction to Action’.
29. Healey, ‘The implications of persistent (and permanent) engagement in cyberspace’.
30. United States Cyber Command, ‘Achieve and Maintain Cyberspace Superiority’,p.2; also see Harknett, ‘United States Cyber Command’s New Vision’.
31. Fischerkeller and Harknett, “Persistent Engagement and Tacit Bargaining.
32. Also see: Harknett and Fischerkeller, ‘Deterrence Is Not a Credible Strategy for Cyberspace’; Harknett and Smeets, ‘Cyber campaigns and strategic outcomes’.
33. Also, at the Brussels Summit in June 2021, allies recognized ‘that the impact of significant malicious cumulative cyber activities might, in certain circumstances, be considered as amounting to an armed attack’. NATO, ‘Brussels Summit Communiqué’.
34. Author’s translation. Ministerie van Defensie, ‘Defensie Cyber Strategie 2018 Investeren in digitale slagkracht voor Nederland’, p. 6.
35. For more general discussion on the conceptualization of the cyber operations: Chesney and Smeets (eds.), Deter, Disrupt, or Deceive.
36. Buchanan, The Cybersecurity Dilemma
37. A number of public revelations have boosted the Dutch intelligence services public image of competence and effectiveness. In February 2018, reporters revealed that a joint team from the General Intelligence and Security Service (AIVD) and the Dutch Military Intelligence and Security Service (MIVD) gained access to the computer systems and networks of ‘Cozy Bear’, an infamous hacking group that is linked to the Russian intelligence agencies. The JSCU shared the information with their U.S. counterparts, which helped to oust the hacking group considering to be responsible for the hacking of the Democratic National Committee during the 2016 U.S. presidential campaign. Six months later, in October 2018, the Dutch government disclosed that the intelligence services successfully disrupted hacking attempts by the Russian military intelligence service GRU against the Organisation for the Prohibition of Chemical Weapons (OPCW). In 2019, it was reported that an Iranian mole, recruited by the Dutch intelligence services, provided critical access that helped the United States and Israel in their cyber campaign, known as Olympic Games or Stuxnet, targeting the nuclear centrifuges in Natanz, Iran. Bosch van Rosenthal, ‘Dutch Intelligence First to Alert U.S. About Russian Hack of Democratic Party’.; Modderkolk, ‘Hackers AIVD Leverden Cruciaal Bewijs over Russische Inmenging in Amerikaanse Verkiezingen’.; For a timeline of how the Dutch intelligence service caught the GRU officers see: Odell, ‘How Dutch Security Service Caught Alleged Russian Spies’. Egloff and Smeets, ‘Publicly Attributing Cyber Attacks’; On the Iranian mole recruited by the Dutch intelligence services see: Zetter and Modderkolk, ‘Revealed’
38. This point has also been made in Boeke, ‘Hackers, Wiz Kids, En Offensieve Cyberoperaties: Uitdagingen Voor Het Defensie Cyber Commando’. also see: Boeke, ‘First Responder or Last Resort?’.
39. ‘Article 97–1. There shall be armed forces for the defence and protection of the interests of the Kingdom, and in order to maintain and promote the international legal order. − 2. The Government shall have supreme authority over the armed forces’. De Nederlandse Grondwet, ‘Artikel 97’
40. Ducheine and Arnold, ‘Besluitvorming Bij Cyberoperaties’; For parliamentary explanation see: Tweede Kamer der Staten Generaal, ‘Vaststelling Begroting van Het Ministerie van Defensie (X) Voor 2000’.
41. Ministerie van Binnenlandse Zaken en Koninkrijksrelaties, ‘Wet Op de Inlichtingen’.
42. This is not only because the WIV only applies to the MIVD and the AIVD, but above all because the Dutch explanation of the AVG (GDPR) does not allow it, see Ministerie van Binnenlandse Zaken en Koninkrijksrelaties, ‘Uitvoeringswet Algemene Verordening Gegevensbescherming’.
43. Ministerie van Binnenlandse Zaken en Koninkrijksrelaties, ‘Joint Sigint Cyber Unit AIVD En MIVD van Start’.
44. There would be additional procedural considerations operating as part of a NATO mission. On the Intelligence and Security Services Act see: Ministerie van Algemene Zaken, ‘Besluit van 6 Juli 2018 Als Bedoeld in Artikel 6, Eerste Lid, van de Wet Op de Inlichtingen- En Veiligheidsdiensten 2017’.
45. Email Correspondence, Pijpers. Also see: Ducheine, Pijpers, and Pouw, ‘Information Manoeuvre and the Netherlands Armed Forces: Legal Challenges Ahead’.
46. Ibid.
47. On the challenges of recruitment also see: NOS, ‘Te Weinig Mensen Willen Hacken Voor Het Vaderland’.
48. Smeets, ‘Cyber Arms Transfer: Meaning, Limits, and Implications’. Smeets, ‘Building a Cyber Force Is Even Harder than You Thought’.
49. According to a study by CSIS, ‘cybersecurity workforce shortfall range from one to two million positions unfilled by 2019’. Center for Strategic & International Studies, ‘Hacking the Skills Shortage’.
50. Interview transcript is provided in the appendix of: Jonas Van Hooren, ‘Calhoun’.
51. Thales, ‘Thales to Build “Cyber Range”, a Cybersecurity Training and Testing Facility for the Dutch Defence Cyber Command’.
52. Ibid.
53. CCDCOE, ‘Locked Shields’.
54. CCDCOE, ‘Cyber Defence Exercise Locked Shields 2013’.
55. CCDCOE, ‘Locked Shields 2014 after Action Report’.
56. In the 2022 edition of Locked Shields, there was also a Benelux team.
57. de Graaf and Harskamp, ‘Reservisten En Cyberoperations’,; for a general discussion on the role of the private sector see: Pattison, ‘From Defence to Offence’.
58. Tweede Kamer der Staten-Generaal, ‘Brief Regering; Nadere Toelichting Op de Inzetgereedheidsnorm van de Nationale Reserve (Natres) En Voortgang Aanstelling Cyberreservisten’.
59. Tweede Kamer der Staten-Generaal, ‘Pilot Cyberreservisten’.
60. Ibid. Tweede Kamer der Staten-Generaal, ‘Initiatiefnota van Het Lid van Den Bosch over Een Ambitieus Reservistenbeleid’.
61. Ibid.
62. Ibid.
63. Ministerie van Defensie, ‘Defensie Cyber Strategie 2018 - Investeren in Digitale Slagkracht Nederland – Publicatie – Defensie.nl’.
64. Achberger and Smeets, The Opportunities and Challenges of Military Cyber Exercises; Smeets, The Role of Military Cyber Exercises.
65. For an excellent overview of the limits of reserve units see also: Libicki, H4cker5 Wanted; also see Collier, ‘Cyber Reserves Are Not a Silver Bullet’.
66. Forensics might be the exception.
67. Also see: NOS, ‘Te Weinig Mensen Willen Hacken Voor Het Vaderland’.
68. Boeke, ‘Hackers, Wiz Kids, En Offensieve Cyberoperaties’.
Bibliography
- Achberger, Brita, and Max Smeets. “The Opportunities and Challenges of Military Cyber Excercises.” Council on Foreign Relations: Net Politics (2022). https://www.cfr.org/blog/opportunities-and-challenges-military-cyber-exercises.
- Adviesraad Internationale Vraagstukken. “Digitale Oorlogvoering.” December 16, 2011. https://www.adviesraadinternationalevraagstukken.nl/documenten/publicaties/2011/12/16/digitale-oorlogvoering.
- Alatalu, Siim. “One Year after Warsaw: The Growing Need for a NATO Cyber Command.” 2017 International Conference on Cyber Conflict (CyCon U.S.), November 2017. doi:10.1109/cyconus.2017.8167513.
- Alberts, Jaco, and Harry Lensink. “Te Land, Ter Zee En Op Het Web; Profiel van Ons Cyberleger.” Vrij Nederland. 2014.
- Anonymous, “All about access: Inzichten en implicaties van MIVD-cyberoperaties voor digitale slagkracht,” Militaire Spectator. September 19, 2022.https://www.militairespectator.nl/thema/operaties-inlichtingen/artikel/all-about-access
- Baader Meika, Sophia. “Froebel and the Rise of Educational Theory in the United States.” Studies in Philosophy and Education 23, no. 5–6 (September 2004): 427–444. doi:10.1007/s11217-004-4453-0.
- Bentinck, Marc. “Why the Dutch Military Punches below Its Weight.” Carnegie Europe (2018). https://carnegieeurope.eu/strategiceurope/75484.
- Betz, David J, Tim Stevens, and International Institute For Strategic Studies London. Cyberspace and the State : Toward a Strategy for Cyber-Power. Abingdon: Routledge, 2011.
- Blessing, Jason. “The Diffusion of Cyber Forces: Military Innovation and the Dynamic Implementation of Cyber Force Structure Dynamic Implementation of Cyber Force Structure,” 2020. https://surface.syr.edu/cgi/viewcontent.cgi?article=2191&context=etd.
- Boeke, Sergei. “First Responder or Last Resort? The Role of the Ministry of Defence in National Cyber Crisis Management in Four European Countries.” Handle.net. Universiteit Leiden, September 2016. https://hdl.handle.net/1887/46615.
- Boeke, Sergei. “Hackers, Wiz Kids, En Offensieve Cyberoperaties: Uitdagingen Voor Het Defensie Cyber Commando.” Atlantisch Perspectief 42, no. 5 (2018): 27–30. https://www.jstor.org/stable/48581451#metadata_info_tab_contents.
- Boere, Raymond. “Leger Zoekt 150 Whizzkids Voor Cyber Commando.” AD (2013). https://www.ad.nl/binnenland/leger-zoekt-150-whizzkids-voor-cyber-commando~a2e242d5/?referrer=https%3A%2F%2Fwww.google.com%2F.
- Buchanan, Ben. The Cybersecurity Dilemma: Hacking, Trust and Fear Between Nations. New York: Oxford University Press, 2016.
- CCDCOE. “Cyber Defence Exercise Locked Shields 2013. After Action Report.” Ccdcoe org (2013). https://ccdcoe.org/library/publications/cyber-defence-exercise-locked-shields-2013-after-action-report/
- CCDCOE. “Locked Shields 2014 after Action Report,” 2014. https://ccdcoe.org/uploads/2018/10/LS14_After_Action_Report_Executive_Summary.pdf.
- CCDCOE. “Locked Shields.” Ccdcoe org (2022). https://ccdcoe.org/exercises/locked-shields/
- Chesney, Robert, and Max Smeets, eds. Deter, Disrupt, or Deceive: Assessing Cyber Conflict as an Intelligence Contest. Washington DC: Georgetown University Press, 2023.
- Clingendael Institute. “Ambitieniveau Defensie Op Droevig Dieptepunt.” Clingendael (2013). https://www.clingendael.org/nl/publicatie/ambitieniveau-defensie-op-droevig-dieptepunt
- Collier, Jamie. “Cyber Reserves Are Not a Silver Bullet.” War on the Rocks, May 22, 2020. https://warontherocks.com/2020/05/cyber-reserves-are-not-a-silver-bullet/.
- De, Telegraaf. “Militair Moet Zelf Pang-Pang Roepen.” De Telegraaf (2015). https://www.telegraaf.nl/nieuws/549324/militair-moet-zelf-pang-pang-roepen.
- Defensie, Ministerie van. “Defensie Cyber Strategie 2018 - Investeren in Digitale Slagkracht Nederland - Publicatie - Defensie.nl.” November 12, 2018. https://www.defensie.nl/downloads/publicaties/2018/11/12/defensie-cyber-strategie-2018.
- De Graaf, Patrick, and Jurjen Harskamp. “Reservisten En Cyberoperations: Schaarse Expertise Veiligstellen Voor Calamiteiten En Militaire Operaties.” March 6, 2012. https://www.militairespectator.nl/thema/cyberoperations/artikel/reservisten-en-cyberoperations.
- Ducheine, Paul. A. L., and K. Arnold. “Besluitvorming Bij Cyberoperaties.” Militaire Spectator 184 (2015). https://hdl.handle.net/11245/1.502386.
- Ducheine, Paul. and Kraesten Arnold. “Besluitvorming Bij Cyberoperaties.” February 20, 2015. https://www.militairespectator.nl/thema/recht-cyberoperations/artikel/besluitvorming-bij-cyberoperaties.
- Ducheine, Paul., Arnold, Kraesten, and B. M. J. Pijpers. Peter. “Decision-Making and Parliamentary Control for International Military (Cyber) Operations by the Netherlands Armed Forces.” Military Operations and the Notion of Control under International Law: 59–81. September 5, 2020. doi:10.1007/978-94-6265-395-5_5.
- Ducheine, Paul., B. M. J. Pijpers Peter, and Eric Pouw. “Information Manoeuvre and the Netherlands Armed Forces: Legal Challenges Ahead.” Papers.ssrn.com. Rochester, NY, May 18, 2022. https://papers.ssrn.com/sol3/papers.cfm?abstract_id=4113046.
- Egloff, Florian, and Max Smeets. “Publicly attributing cyber attacks: a framework.” Journal of Strategic Studies 46, no. 3 (2021): 502–533. doi:https://doi.org/10.1080/01402390.2021.1895117.
- Fischerkeller, Michael P., and Richard J. Harknett. “Persistent Engagement and Tacit Bargaining: A Path toward Constructing Norms in Cyberspace.” Lawfare, November 9, 2018. https://www.lawfareblog.com/persistent-engagement-and-tacit-bargaining-path-toward-constructing-norms-cyberspace.
- Fischerkeller, Michael P., and Richard J. Harknett. “Deterrence Is Not a Credible Strategy for Cyberspace.” Orbis 61, no. 3 (2017): 381–393. doi:10.1016/j.orbis.2017.05.003.
- Fogarty, Stephen G., and Jamie O. Nasi. “Special Operations Forces Truths — Cyber Truths.” The Cyber Defense Review 1, no. 2 (2016): 19–28. https://www.jstor.org/stable/26267355.
- Goldman, Emily O. “From Reaction to Action: Adopting a Competitive Posture in Cyber Diplomacy (Fall 2020).” Texas National Security Review (2020). doi:10.26153/tsw/10950.
- Harknett, Richard J. “United States Cyber Command’s New Vision: What It Entails and Why It Matters.” Lawfare, March 23, 2018. https://www.lawfareblog.com/united-states-cyber-commands-new-vision-what-it-entails-and-why-it-matters.
- Harknett, Richard J., and Michael P. Fischerkeller. “A Response on Persistent Engagement and Agreed Competition.” Lawfare, June 27, 2019. https://www.lawfareblog.com/response-persistent-engagement-and-agreed-competition.
- Harknett, Richard J., and Max Smeets. “Cyber Campaigns and Strategic Outcomes.” Journal of Strategic Studies 45, no. 4 (March 4, 2020): 534–567. doi:10.1080/01402390.2020.1732354.
- Healey, Jason. “The Implications of Persistent (and Permanent) Engagement in Cyberspace.” Journal of Cybersecurity, 5, no.1, January 1, 2019. 10.1093/cybsec/tyz008
- Jacobsen, Jeppe T. “Cyber Offense in NATO: Challenges and Opportunities.” International Affairs 97, no. 3 (March 31, 2021): 703–720. doi:10.1093/ia/iiab010.
- Jinghua, Lyu. “A Chinese Perspective on the Pentagon’s Cyber Strategy: From ‘Active Cyber Defense’ to ‘Defending Forward.’.” Carnegie Endowment for International Peace (2018). https://carnegieendowment.org/2018/10/19/chinese-perspective-on-pentagon-s-cyber-strategy-from-active-cyber-defense-to-defending-forward-pub-77540.
- Joyce, Rob. “Disrupting Nation State Hackers.” USENIX Enigma (2016). https://www.usenix.org/sites/default/files/conference/protected-files/engima2016_transcript_joyce_v2.pdf.
- Koninkrijksrelaties, Ministerie van Binnenlandse Zaken en. “Joint Sigint Cyber Unit AIVD En MIVD van Start - Nieuwsbericht - AIVD.” July 3, 2014. https://www.aivd.nl/actueel/nieuws/2014/07/03/joint-sigint-cyber-unit-aivd-en-mivd-van-start.
- Koninkrijksrelaties, Ministerie van Binnenlandse Zaken en. “Wet Op de Inlichtingen- En Veiligheidsdiensten 2017.” Wetten overheid nl (2017). https://wetten.overheid.nl/BWBR0039896/2022-05-01
- Koninkrijksrelaties, Ministerie van Binnenlandse Zaken en. “Uitvoeringswet Algemene Verordening Gegevensbescherming.” Wetten overheid nl (2018). https://wetten.overheid.nl/BWBR0040940/2018-05-25
- Libicki, Martin C., David Senty, Julia Pollak, and Rand Corporation. “H4cker5 Wanted: An Examination of the Cybersecurity Labor Market.” Library Catalog (Blacklight). Santa Monica, California: RAND Corporation, 2014. https://searchworks.stanford.edu/view/12974884
- Liebschner, Joachim. A Child’s Work : Freedom and Play in Froebel’s Educational Theory and Practice/Monograph. Cambridge, England: Lutterworth Press, 2006.
- Liff, Adam P. “Cyberwar: A New ‘Absolute Weapon’? The Proliferation of Cyberwarfare Capabilities and Interstate War.” Journal of Strategic Studies 35, no. 3 (June 2012): 401–428. doi:10.1080/01402390.2012.663252.
- Maarten. “Geloofwaardige Afschrikking in Het Cyberdomein?” January 19, 2021. https://www.militairespectator.nl/thema/cyberoperations-strategie/artikel/geloofwaardige-afschrikking-het-cyberdomein.
- Mills, Albert J., Gabrielle Durepos, and Elden Wiebe, eds. Exploratory Case Study - SAGE Research Methods. Methods sagepub.com, n.d. https://methods.sagepub.com/reference/encyc-of-case-study-research/n139.xml#:~:text=The%20exploratory%20case%20study%20investigates.
- Ministerie van Algemene Zaken. “Besluit van 6 Juli 2018 Als Bedoeld in Artikel 6, Eerste Lid, van de Wet Op de Inlichtingen- En Veiligheidsdiensten 2017 (Geïntegreerde Aanwijzing Inlichtingen En Veiligheid 2018–2022).” Zoek officielebekendmakingen nl (2018). https://zoek.officielebekendmakingen.nl/stcrt-2018-39232.html
- Ministerie van Defensie. “Defensie Cyber Strategie 2018 - Investeren in Digitale Slagkracht Nederland - Publicatie - Defensie.nl.” November 12, 2018. https://www.defensie.nl/downloads/publicaties/2018/11/12/defensie-cyber-strategie-2018#:~:text=Defensie.nl%20Downloads-.
- The Ministry of Defence. “The Defence Cyber Strategy,” 2012. https://www.itu.int/en/ITU-D/Cybersecurity/Documents/National_Strategies_Repository/Netherlands_2012_NDL-Cyber_StrategyEng.pdf.
- Ministry of Defense. “Opnieuw Extra Geld Voor Defensie in 2016 - 01 - Defensiekrant.” Magazines.defensie.nl, 2015. https://magazines.defensie.nl/defensiekrant/2015/18/01-prinsjesdag.
- Modderkolk, Huib. “Hackers AIVD Leverden Cruciaal Bewijs over Russische Inmenging in Amerikaanse Verkiezingen.” De Volkskrant, January 26, 2018. https://www.volkskrant.nl/nieuws-achtergrond/hackers-aivd-leverden-cruciaal-bewijs-over-russische-inmenging-in-amerikaanse-verkiezingen~b32c6077/.
- Nakasone, Paul. “A Cyber Force for Persistent Operations,” 2019. https://ndupress.ndu.edu/Portals/68/Documents/jfq/jfq-92/jfq-92_10-14_Nakasone.pdf.
- NATO. “Allied Joint Doctrine for Cyberspace Operations,” 2020. https://assets.publishing.service.gov.uk/government/uploads/system/uploads/attachment_data/file/899678/doctrine_nato_cyberspace_operations_ajp_3_20_1_.pdf.
- NATO. “Brussels Summit Communiqué.” 2021. https://www.nato.int/cps/en/natohq/news_185000.htm
- Nederlandse Grondwet, De. “Artikel 97: Krijgsmacht - Nederlandse Grondwet.” Accessed September 21, 2022. https://www.denederlandsegrondwet.nl/id/via0fzbuo6zv/artikel_97_krijgsmacht.
- NOS. “Te Weinig Mensen Willen Hacken Voor Het Vaderland.” Nos.nl, December 1, 2016. https://nos.nl/artikel/2146002-te-weinig-mensen-willen-hacken-voor-het-vaderland.
- Odell, Mark. “How Dutch Security Service Caught Alleged Russian Spies.” Financial Times, October 4, 2018. https://www.ft.com/content/b1fb5240-c7db-11e8-ba8f-ee390057b8c9.
- Pattison, James. “From Defence to Offence: The Ethics of Private Cybersecurity.” European Journal of International Security 5, no. 2: 233–254. (May 19, 2020). doi:10.1017/eis.2020.6.
- Pijpers, Peter, and Michael Smits. “Persistent Engagement: De Nieuwe Cyberstrategie Voor Nederland?” February 17, 2022. https://www.militairespectator.nl/thema/cyberoperations/artikel/persistent-engagement.
- Rid, Thomas. “Cyber War Will Not Take Place.” Journal of Strategic Studies 35, no. 1 (February 2012): 5–32. doi:10.1080/01402390.2011.608939.
- Rosen, Stephen Peter. Winning the next War. Ithaca: Cornell University Press, 1991.
- Rovner, Joshua. “Warfighting in Cyberspace.” War on the Rocks. March 17, 2021.https://warontherocks.com/2021/03/warfighting-in-cyberspace/
- RTL Nieuws. “Hennis: Grappen over ‘Pang Pang’ Vernietigend,” August 14, 2015. https://www.rtlnieuws.nl/nieuws/nederland/artikel/1022381/hennis-grappen-over-pang-pang-vernietigend.
- Schramade, Krijn. “Defensiebudget Historisch Laag.” Follow the Money - Platform Voor Onderzoeksjournalistiek, September 30, 2013. https://www.ftm.nl/artikelen/defensiebudget-historisch-laag.
- SIPRI. “SIPRI Military Expenditure Database.” Sipri org (2018). https://www.sipri.org/databases/milex
- Smeets, Max. “Building a Cyber Force Is Even Harder than You Thought.” War on the Rocks, May 12, 2022. https://warontherocks.com/2022/05/building-a-cyber-force-is-even-harder-than-you-thought/.
- Smeets, Max. “Cyber Arms Transfer: Meaning, Limits, and Implications.” Security Studies 31, no. 1 (February 23, 2022): 65–91. doi:10.1080/09636412.2022.2041081.
- Smeets, Max. No Shortcuts: Why States Struggle to Develop a Military Cyber-Force. New York: Oxford University Press, 2022.
- Smeets, Max. The Role of Military Cyber Exercises: A Case Study of Locked Shields. 2022 14th International Conference on Cyber Conflict. Tallinn, Estonia.
- Striek, Peter. “Meer Geld? Defensie Krijgt Juist Nog Veel Minder Geld.” De Volkskrant, 2014. http://www.volkskrant.nl/binnenland/-meer-geld-defensie-krijgt-juist-nog-veel-minder-geld~a3755100/.
- Thales. “Thales to Build ‘Cyber Range’, a Cybersecurity Training and Testing Facility for the Dutch Defence Cyber Command.” Thales Group (2016). https://www.thalesgroup.com/en/worldwide/press-release/thales-build-cyber-range-cybersecurity-training-and-testing-facility-dutch
- Turgenev, Ivan Sergeevich. Virgin Soil. New York: New York Review Books, 2000. Translated by Constance Garnett.
- Tweede Kamer der Staten Generaal. “Vaststelling Begroting van Het Ministerie van Defensie (X) Voor 2000; Verslag Houdende Een Lijst van Vragen En Antwoorden.” NDFR (2000). https://www.ndfr.nl/content/kst-26800-X-12
- Tweede Kamer der Staten-Generaal. “Brief Regering; Nadere Toelichting Op de Inzetgereedheidsnorm van de Nationale Reserve (Natres) En Voortgang Aanstelling Cyberreservisten - Vaststelling van de Begrotingsstaten van Het Ministerie van Defensie (X) Voor Het Jaar 2016 - Parlementaire Monitor.” (2016). https://www.parlementairemonitor.nl/9353000/1/j9vvij5epmj1ey0/vk5hbdtr32ye
- Tweede Kamer der Staten-Generaal. “Initiatiefnota van Het Lid van Den Bosch over Een Ambitieus Reservistenbeleid.” (2019). https://www.tweedekamer.nl/kamerstukken/brieven_regering/detail?id=2019D02204&did=2019D02204
- Tweede Kamer der Staten-Generaal “Pilot Cyberreservisten.” 2019. https://www.tweedekamer.nl/kamerstukken/brieven_regering/detail?id=2019Z20386&did=2019D42637.
- U.S. Cyber Command. “Achieve and Maintain Cyberspace Superiority: Command Vision for US Cyber Command,” 2018. https://s3.documentcloud.org/documents/4419681/Command-Vision-for-USCYBERCOM-23-Mar-18.pdf.
- U.S. Cyber Command. “Hunt Forward.” 2022. https://www.cybercom.mil/Media/News/Tag/182880/hunt-forward/
- U.S. Government. “The F-35 Lightning II,” http://www.jsf.mil/;.
- Van Hooren, Jonas. “The Imperative Symbiotic Relationship Between SOF and Cyber: How Dutch Special operation Forces Can Support Cyber Operations.” 2019. https://upload.wikimedia.org/wikipedia/commons/0/06/THE_IMPERATIVE_SYMBIOTIC_RELATIONSHIP_BETWEEN_SOF_AND_CYBER-_HOW_DUTCH_SPECIAL_OPERATION_FORCES_CAN_SUPPORT_CYBER_OPERATIONS_%28IA_theimperativesym1094564086%29.pdf.
- van Lonkhuyzen, Liza, and Kees Versteegh. “‘Cyberleger’ Moet Inbrekers Afschrikken.” NRC (2018). https://www.nrc.nl/nieuws/2018/11/13/cyberleger-moet-inbrekers-afschrikken-a2754956.
- van Rosenthal, Eelco Bosch. “Dutch Intelligence First to Alert U.S. About Russian Hack of Democratic Party.” Nos.nl, January 25, 2018. https://nos.nl/nieuwsuur/artikel/2213767-dutch-intelligence-first-to-alert-u-s-about-russian-hack-of-democratic-party.
- Wiltjer, Davidson. “Cyber Commando Voor Het Eerst Op Missie.” Algemeen Nederlands Persbureau (2017).
- Yin, Robert K. “Case Study Evaluations: A Decade of Progress?” New Directions for Evaluation.” New Directions for Evaluation 1997, no. 76 (1997): 69–78. September 1997. doi:10.1002/ev.1088.
- Yin, Robert K. Applications of Case Study Research. 3rd ed. Los Angeles: Sage, 2011.
- Zaken, Ministerie van Algemene. “Antwoord Op Kamervragen over de Vaststelling van de Begrotingsstaten van Het Ministerie van Defensie (X) Voor Het Jaar 2022 - Kamerstuk - Rijksoverheid.nl.” October 22, 2021. https://www.rijksoverheid.nl/documenten/kamerstukken/2021/10/22/beantwoording-feitelijke-vragen-over-de-vaststelling-van-de-begrotingsstaten-van-het-ministerie-van-defensie-x-voor-het-jaar-2022.
- Zetter, Kim, and Huib Modderkolk. “Revealed: How a Secret Dutch Mole Aided the U.S.-Israeli Stuxnet Cyberattack on Iran.” Yahoo! News (2019). https://news.yahoo.com/revealed-how-a-secret-dutch-mole-aided-the-us-israeli-stuxnet-cyber-attack-on-iran-160026018.html?guccounter=1&guce_referrer=aHR0cHM6Ly93d3cuZ29vZ2xlLmNvbS8&guce_referrer_sig=AQAAAB9FYBRbzUyjZPF6_6WWXIqu-Kc2FgxENlkBD8dk67Js7Ki-2rQcYTmtXWbHENQ_fGWkmPPwP84ffcl4VwiGCzN3yssvjeIwawlVNyNATcbhqCMkl4IyLdyN-0eft0UPIDu1d4Jz8EEni60MQVAVRpAJkbBNoiuZ1KgNZfaRH1ul.
