ABSTRACT
Digital entrepreneurs face the liability of newness, like any other entrepreneur. However, this liability of newness is manifested differently: it is mediated by an artefact, in this case a platform. This paper examines how a digital entrepreneur mediated by a platform can build legitimacy, something hitherto thought to be embedded within a social relationship (that is, one that a digital platform may be unable to have). Based on a qualitative research design, we develop the concept of “designed legitimacy”, and we point to how trust may not be enough to overcome the liability of newness. Rather, legitimacy is needed to attract users and resources, and thus for growth and success. We further highlight the means through which a platform may come to be seen as legitimate, namely by designing with legitimacy in mind: by using symbols in design, asymmetric legitimacy building, and sequential two-stage legitimacy building. We end the paper with propositions for further study and the implications of this research for digital entrepreneurship and platforms.
ACCEPTING EDITOR:
ASSOCIATE EDITOR:
1. Introduction
The notion of “digital entrepreneurship” has recently entered academic discourse, with early work arguing that digital technologies have “transformed the nature of uncertainty inherent in entrepreneurial processes and outcomes, as well as the ways of dealing with such uncertainty” (Nambisan, Citation2017, p.1). The vast majority of these digital entrepreneurs conduct their business and form social relationships through a digital artefact, typically a platform or app (Kelestyn & Henfridsson, Citation2014; Tiwana, Konsynski, & Bush, Citation2010). Indeed, the digital artefact is so central to the entrepreneur’s business that the firm and the artefact become indistinguishable. In pursuing their entrepreneurial venture, understanding the dynamic around digital artefacts’ mediation of entrepreneurial processes – and in overcoming uncertainty in particular – is therefore a vital part of understanding how entrepreneurship evolves in the digital age (Nambisan, Citation2017).
One common source of uncertainty among entrepreneurs, digital or otherwise, is overcoming their “liability of newness” (Suchman, Citation1995; Zimmerman & Zeitz, Citation2002). This lack of legitimacy reveals itself in an entrepreneur’s inability to rally resources in the form of financial, human, and social capital (Suchman, Citation1995). Among digital entrepreneurs, this lack of legitimacy may manifest itself in a struggle to attract potential users (Evans, Citation2009), or misunderstandings of the entrepreneurs’ business model, leading to the digital artefact being used for purposes other than those for which its creators intended (Tiwana et al., Citation2010).
Successful digital entrepreneurs are those who, among other things, come to be seen as legitimate. Initial legitimacy leads to user adoption, the success of the business model and, ultimately, financial and social rewards for the entrepreneurs involved (Drori, Honig, & Sheaffer, Citation2009; Stringfellow, Shaw, & Maclean, Citation2013). Although the role of digital artefacts and their design in a two-sided market has been explored by information systems scholars in, for instance, digital product innovation (Eisenmann, Parker, & Van Alstyne, Citation2011), neither the pursuit of two-sided legitimacy, nor its role in digital entrepreneurship has, to our knowledge, been explored.
Appealing to two markets simultaneously is a classic two-sided market problem, already known to platform scholars (eg, Eisenmann et al., Citation2011; Gawer, Citation2009; Rochet & Tirole, Citation2003), and has been labelled a “chicken and egg” game (Evans, Citation2009; Gawer & Cusumano, Citation2014). Take, for instance, Apple’s iStore: in 2017 it raised an estimated 26.5 billion USD for its developers – and by doing so made 11.5 billion USD in profits itself (Jones, Citation2018). The success of the digital artefact, the iStore, relies simultaneously on both those who build upon it – the developers – and those who use what is built – the users.
One particularly interesting two-sided platform that has fascinated Information Systems researchers is the crowdfunding platform (eg, Burtch, Ghose, & Wattal, Citation2013; Gleasure, Citation2015). Building a market on one side of the platform often requires the existence of a market on the other side of the platform, and vice versa. Indeed, extant research on crowdfunding has pointed to how actors might not adopt crowdfunding if they saw doing so as an act of “desperation” or, in our terms, if it does not confer legitimacy (Gleasure, Citation2015). Here, we build upon previous research into how projects using a platform can obtain legitimacy (or not) (Gleasure, Citation2015; Gleasure & Feller, Citation2016a), by exploring how the platform itself can become legitimate, and the role of both its design and users in that pursuit. This is an important question given that the platform’s own legitimacy determines whether users will make initial use of the platform. Once early user bases (on both sides of the platform) have been established, network effects mean that neither group is likely to switch to another platform (Koufaris & Hampton-Sosa, Citation2004).
This paper examines this issue of legitimacy building by a digital entrepreneur mediated by a two-sided platform (“entrepreneurial platform”) and is based on a study of a fast-growing crowdfunding platform in Stockholm, Sweden. More specifically, this digital entrepreneur was a two-sided platform offering investment possibilities to potential funders (“funders”), on the one side, and project providers (“projects”) on the other side, through donation and reward-based crowdfunding. In this form of crowdfunding, funders offer money in exchange for either a symbolic reward, or goodwill (Gleasure & Feller, Citation2016b). In particular, the crowdfunding platform targeted information technology (IT) projects that were active early adopters in the Stockholm context. To conduct our study, we did not enter the field with a specific body of literature or theoretical contribution in mind. Rather we moved gradually towards bodies of literature after iterative open coding of our data from interviewing 29 people to answer our overarching research question: How can a digital entrepreneur, mediated by its two-sided crowdfunding platform, gain legitimacy?
This paper is organised as follows. First, we discuss the concepts of legitimacy and digital entrepreneurship, and examine whether and how a digital entrepreneur, mediated by its platform, can be seen as legitimate. Second, we delve into our research context and methods. We then turn to discussing our findings before presenting the implications of this initial failed attempt at designed legitimacy and a set of propositions for future studies of digital entrepreneurship, platforms, and legitimacy building.
2. Theoretical background
2.1. Entrepreneurial legitimacy in a digital age
When operating in a digital space (Davidson & Vaast, Citation2010; Nambisan, Citation2017), a lack of legitimacy may be because the technologies upon which an entrepreneur relies have not yet received widespread acceptance (Van Lente, Citation2012), or because they operate from the periphery of a field (Henfridsson & Yoo, Citation2014; Wright & Zammuto, Citation2013). However, the inability to obtain legitimacy may be the result of something more simple: the failure to conform to certain normative, structural, and cognitive norms within a field (Suchman, Citation1995), or a failure to communicate conformance to these norms (Garud, Schildt, & Lant, Citation2014).
Legitimacy is best known from sociological theory, and from Weber in particular, who argued that legitimacy stemmed from conformity with both social norms and specific laws produced by hierarchical bureaucracies governed by human agents (Weber, Citation1978). This conception was further refined by Meyer and Rowan to show how “organizations structurally reflect socially constructed reality” (Citation1977, p. 47) with legitimacy resulting from their desire to pursue effectiveness (pragmatic legitimacy), in line with legal mandates (socio-political legitimacy) and collectively valued goals, means, and purposes (normative legitimacy). Ashforth and Gibbs (Citation1990) point out specifically that effectiveness and performance are not enough – normative compliance is necessary. Of note are the cognitive elements implicit in this conception on the part of the person perceiving the legitimacy (but not necessarily on the part of the organisation itself). Specifically, Deephouse and Suchman refer to the importance of “explanation, theorization, and the incomprehensibility of alternatives” in studies of legitimacy (Citation2008, p. 574). Although an organisation, or other entity, is said to be able to build legitimacy (Ashforth & Gibbs, Citation1990; Zimmerman & Zeitz, Citation2002), the implication is that this is not a necessary pre-condition for being considered legitimate. Ultimately, being legitimate rests on a relational assessment, or perception, by other actors in a field.Footnote1
We often discuss technological artefacts as having social, or human, characteristics (Benbasat & Wang, Citation2005; Corritore, Kracher, & Wiedenbeck, Citation2003). However, whether they can take on relational characteristics is not clear. Legitimacy, for instance, is typically seen as a social, relational characteristic and, by implication, one that can only arise between humans or among groups of humans (Suchman, Citation1995; Weber, Citation1978; Zimmerman & Zeitz, Citation2002). How then, if at all, can an entrepreneurial platform gain legitimacy?
The concept of trust once faced a similar impasse. It was widely accepted to be a pre-condition for a piece of technology to be adopted (Gefen, Karahanna, & Straub, Citation2003), but most studies had looked at trust in the humans behind the technologies, rather than considering trust in the technologies themselves. This is because trust, like legitimacy, was thought of as arising within an interpersonal relationship between humans (Sztompka, Citation1999), and one that required consciousness and agency (Friedman, Khan, & Dc, Citation2000). However, research in information systems has shown how it is possible, both conceptually and in practice, for people to trust or even distrust a digital artefact (Benbasat & Wang, Citation2005). This is not least because people do, in fact, treat computers and other digital artefacts as though they are more human than simple tools (Reeves & Nass, Citation1996). In a study of the use of human rituals being used by machines (eg, small talk), Cassell and Bickmore (Citation2000) went so far as to say that trust included elements of both benevolence and credibility.
While studies of trust, and that of Benbasat and Wang (Citation2005) in particular, provide a blueprint for how people develop a human-like relationship with a digital artefact, the nature of the relationship between people and the digital artefact in the context of trust is not the same as the nature of relationship in the context of legitimacy. Trust is defined as the willingness to take a risk (Mayer, Davis, & Schoorman, Citation1995), where an actor bears some responsibility (Muir & Moray, Citation1996). Trust in this conception is about the relationship between actors. Although it may be affected by context or social conventions (Cassell & Bickmore, Citation2000), it is largely about believing that an actor can, and will, do that which it says it will. In contrast, legitimacy looks at an actor through the lens of broader social expectations: “every goal, mean, resource, and control system is necessary, specified, complete, and without alternative” (Meyer & Scott, Citation1983, p. 201). Indeed, while trust might be said to be a necessary condition for a platform to be used, the legitimacy literature suggests that trust on its own may not be sufficient for users to adopt a platform (Garud et al., Citation2014; Suddaby & Greenwood, Citation2005; Zimmerman & Zeitz, Citation2002).
Studies of legitimacy, both within fields and making use of symbols and narratives have seen legitimacy as a relational and social problem, overcome by activities employed by a human actor or organisation. Indeed, legitimacy is not something that has been attributed to a technological artefact as it is instead seen as a primarily social practice (Deephouse & Suchman, Citation2008). This research therefore builds on extant research by extending how legitimacy can be built mediated by characteristics of non-human actors, in this case, a multi-sided platform.
2.2. Legitimacy of a crowdfunding platform
A platform is one digital artefact that mediates as digital entrepreneurs build their venture. A platform is comprised of two elements: an extensible codebase that provides core functions and modules that can be added or subtracted to add functionality. Collectively, these are referred to as a platform ecosystem (Cusumano & Gawer, Citation2002; Tiwana et al., Citation2010). The underlying platform provides an infrastructure that allows heterogeneous users to connect to one another (Rochet & Tirole, Citation2003) and, in so doing, lower the barriers to entry for those wishing to obtain resources and information (Eaton, Elaluf-Calderwood, Sørensen, & Yoo, Citation2015; Gawer, Citation2009). Two-sided platforms are a particular kind of digital artefact and have begun to attract attention, both for the ecosystems that they create (Tiwana et al., Citation2010) and for their efficient allocation of resources (Bakos & Katsamakas, Citation2008; Parker & Alstyne, Citation2012). Indeed, it is this intermediary role, connecting two or more markets, that has made digital entrepreneurship mediated by such platforms lucrative. In the case entrepreneurship through a crowdfunding platform, reducing so-called information and transaction costs incurred by both projects and funders as they screen and identify one another allows the entrepreneur to add a premium to the service, which forms the entrepreneur’s income (Eisenmann et al., Citation2011; Rochet & Tirole, Citation2004).
Platform ecosystems are said to be more dynamic than often imagined (Katz & Shapiro, Citation1994), and the context can often be influential in affecting whether a platform is adopted, how it is perceived, and what it is ultimately used for (Eaton et al., Citation2015; Tiwana et al., Citation2010). Indeed, previous studies of crowdfunding platforms have pointed to how “fear of disclosure, fear of visible failure, and fear of projecting desperation” have deterred projects from even trying out a crowdfunding platform (Gleasure, Citation2015, p. 223). In order to overcome these fears in one of its user groups, namely those providing projects, a crowdfunding platform has to itself provide a service grounded in a broader set of espoused social or ideological values (Burtch et al., Citation2013; Gleasure & Feller, Citation2016a; Mollick, Citation2014).
In other words, it has to take account of the context – both social and digital – of both the platform and its desired user base when building legitimacy. Evans (Citation2009) finds, through a case study of tyre manufacturers, that platform design is just one – albeit an important one – of the variables that drive adoption, and that context is similarly important.
2.2.1. Digitally mediated communication
A key difference between a digital entrepreneur and a traditional entrepreneur is that the former communicates with potential users largely through its digital presence (Gawer & Cusumano, Citation2014; Nambisan, Citation2017). Communication pursuant to legitimacy building by a digital entrepreneur therefore not only involves a new medium, it also involves optimising the message within fluid, and increasingly porous, boundaries (Nambisan, Citation2017). In this paper, we examine this communication through a platform, but it could equally occur through other digital artefacts, for instance through apps.
A platform’s appearance, as with many digital artefacts, is often optimised for its intended user groups. Wheelwright and Clark (Citation1992), for instance, point out that modifying, adding, or subtracting different features can affect how a platform is received by different user groups. This suggests that design and communication are important for a platform’s legitimacy and subsequent adoption. However, there is limited research as to whether a platform itself can be considered legitimate and, if so, how.
The use of symbols, narratives, and the material have elsewhere been linked to legitimacy building and institutional change, most notably in the way in which language and semantics are used (Garud et al., Citation2014; Martens, Jennings, & Jennings, Citation2007), and in the use of physical infrastructures (de Vaujany & Vaast, Citation2014). In crowdfunding research, projects’ language and content have been used to identify fraud (Siering, Koch, & Deokar, Citation2016) and influenced funding decisions (Bretschneider & Leimeister, Citation2017; Burtch, Ghose, & Wattal, Citation2016; Majumdar & Bose, Citationin press). While narratives have been shown to be important when it comes to the consequences of using a crowdfunding platform (eg, in funding decisions and fraud), the use of symbols and narratives in the emergence and legitimacy of the platform itself remain poorly understood. When it comes to the platform’s legitimacy, Garud et al. (Citation2014) find that narratives and stories articulated in the pursuit of legitimacy may themselves create new constraints or barriers to obtaining legitimacy.
2.2.2. Designing for a desired outcome
Digital entrepreneurship has been theorised to be both less bounded, and less pre-defined than its non-digital counterpart (Nambisan, Citation2017). This is thought to be so because of the erosion of temporal and geographic boundaries (ibid.), and because of the flexibility of digital artefacts: they can be re-interpreted, and used in unanticipated ways, or what has been called “generativity” (Yoo, Boland, Lyytinen, & Majchrzak, Citation2012; Zittrain, Citation2006). The generative potential of digital artefacts has been argued to lead to evolution over time (Yoo et al., Citation2012). Consequently, the way in which a product or service is interpreted – and used – is likely to evolve over time, especially as new actors appropriate it (Henfridsson & Bygstad, Citation2013).
Operating a crowdfunding platform is a specific type of digital entrepreneurship. Extant research points to how geography has remained relevant in funder decisions – but that it is not decisive (Lin & Viswanathan, Citation2015). Suggestions that funding timing might become less important have been, in the case of reward-based crowdfunding, largely refuted (Agrawal, Catalini, & Goldfarb, Citation2015; Burtch et al., Citation2013). However, even within clearly bounded geographic and temporal fields, social theorists acknowledge multiple sets of social realities (Meyer & Rowan, Citation1977). This plurality is particularly pronounced in digital realms (Björkdahl, Citation2009; Keen & Williams, Citation2013), making understanding how to work within – or overcome – it as part of an entrepreneurial undertaking particularly interesting. Despite this plurality of social realities, attracting one or more of these key user groups remains an important part of a multi-sided platform’s strategy (Evans, Citation2003).Footnote2
The possibilities around generativity, coupled with the digital’s plurality of realities makes it all the more important that entrepreneurs successfully build early legitimacy and communicate the core of their offering to would-be users. By designing for specific outcomes, a platform can control what it is used for, and by whom (Tiwana et al., Citation2010). While a certain amount of openness allows for diverse actors to make use of a platform, the risk is that this will lead to the platform being re-interpreted and used for ways not intended by its creators. Among crowdfunding platforms, this lack of control on the Kickstarter platform led to the platform becoming a sales platform, rather than a financing one (Wessel, Thies, & Benlian, Citation2017), and has been blamed for the presence of low quality projects on platforms (Colombo, Franzoni, & Rossi-Lamastra, Citation2015). Indeed, the failure to control – whether through design or gatekeeping – a platform could be blamed for a potential user base rejecting it (Gleasure, Citation2015), especially given a platform’s role in matching different potential funders and projects with shared values (Gleasure & Feller, Citation2016a). However, although extant research points to the platform’s legitimacy playing a role in the larger phenomenon, the role of the perception of legitimacy in whether a platform is adopted (and for what purpose) has not been examined.
As legitimacy is a context-driven perception, we argue that it is not only possible for a platform to be perceived as legitimate, but that this perception is a vital part of platform design and commercialisation that has hitherto been neglected. Indeed, the importance of designing for legitimacy may be more important in the digital age than in previous waves of entrepreneurship; digital artefacts’ generativity mean that entrepreneurs cannot afford to be complacent.
Having discussed the background to this research, we now turn to discussing our research context, data, and methods, before presenting our findings. From here on, we refer to the digital entrepreneur mediated by the platform as the “entrepreneurial platform”, both for simplicity and because of the centrality of the platform for entrepreneurial activities.
3. Context, data and methods
3.1. Research design and setting
We relied on the qualitative, theory-building single case study method (Yin, Citation1981, Citation2003) in designing and conducting our research. We began with an empirical problem, namely why crowdfunding was not being adopted by Swedish IT projects, despite its adoption by similar groups elsewhere in the world, and the importance of financing for early stage projects (Erikson, Citation2002; Kerr, Lerner, & Schoar, Citation2014). This study started as an exploratory one, and then zoomed in on the question of platform legitimacy as both an empirically and theoretically rich concept to explore – and one with particular relevance here.
Our research centres on a crowdfunding platform and group of actors in the IT start-up community in Stockholm, Sweden, a city known as an IT project hub (Cheshire, Citation2011). A number of successful software companies, for instance Spotify, iZettle, King, and Skype, have emerged from this city in recent years. In late 2012 it also boasted a small number of crowdfunding platforms, including to IT projects. The presence of a high technology start-up community, high levels of internet connectivity in the country (over 90 percent in 2016, Davidsson & Findahl, Citation2016), and the fact that professional financing is hard to find in Sweden (Avdeitchikova, Citation2008) means that crowdfunding should be an interesting possibility for IT projects within this community. In this paper, we refer to professional financiers not active on crowdfunding platforms as “investors” and those who invest using crowdfunding (both professional and non-professional) as “funders”.
Crowdfunding provides an interesting context for us to examine the concept of platform legitimacy as two-sided platforms are at the core of their operations. In crowdfunding, a two-sided platform can operate in four ways: (1) donation-based crowdfunding, where the crowd gives money as a donation and receives only intangible benefits in return; (2) reward-based crowdfunding, where the crowd gives money in exchange for a symbolic reward, product prototype, or other tangible reward; (3) equity-based crowdfunding, where the crowd invests money in a firm in exchange for an equity share; and (4) debt-based crowdfunding, also known as peer-to-peer lending, where the crowd lends a firm money in exchange for interest on the amount invested and an eventual repayment of the capital amount (Belleflamme, Lambert, & Schwienbacher, Citation2014).
When we collected our data, the crowdfunding platform under examination was one of a small number of such platforms operating in Sweden. It started by offering donation- and reward-based crowdfunding, upon which we focused our case study. Its offices were located in a co-working space with a number of other IT projects, and its employees and founders rubbed shoulders with other IT professionals on a daily basis. Given the physical closeness of the platform founders to a number of IT projects (Porter, Citation2000, Citation1998), and the fact that IT projects have raised funding on crowdfunding platforms elsewhere in the world (Mollick, Citation2014), we identified them as a key user group for this platform.
The platform later expanded operations to elsewhere in Europe and Asia and introduced equity-based and debt-based crowdfunding. Equity and debt-based crowdfunding are, in 2018, the main focus of the platform. At the time of data collection in 2012/2013, other crowdfunding platforms in Sweden catered to niche communities, eg, creative arts, charity projects, while two platforms catered to Stockholm’s IT projects. The first of these is the subject of this study; the latter was a later entrant into the Swedish market and offered only equity-based crowdfunding but, at the time of data collection, had not yet raised any money in the country.
3.2. Data collection and analysis
We collected data through semi-structured interviews with 29 individuals, each lasting 30–75 min, which were recorded and transcribed. We made use of interviews in order to explore the apparent contradiction between the benefits of crowdfunding and IT projects’ failure to adopt it. We began by identifying IT projects at the annual Swedish IT conference, “Internetdagarna 2012” (“Internet Days 2012”) who self-identified themselves as looking for funding. We then relied on snowball sampling to identify other IT projects and individuals in the field. Ultimately, our sample included IT entrepreneurs, platform founders, crowdfunding funders, venture capitalists, angel investors, and other interested third parties like businesses coaches (). The IT projects were largely, but not entirely, entrepreneurs providing software, rather than hardware, as is common in Sweden (Andersson & Wictor, Citation2003; Casper & Whitley, Citation2004). In addition to interviews, we also collected data through (1) participant observations in meetings and conferences, informal meetings with numerous other project providers, and multiple interactions with funders and (2) extensive archival material such as from the crowdfunding platform websites and trade press analysis and documentation. This enabled us to look at the situation of crowdfunding for IT projects in context and from their perspective (Graebner & Eisenhart, Citation2007; Suddaby, Citation2006).
Table 1. List of interviewees.
After each interview we wrote notes around interesting themes that emerged from the interviews and later conducted data analysis using open coding of the interview transcriptions (Corbin & Strauss, Citation1990; Strong et al., Citation2014), triangulating our findings against what we already knew about crowdfunding in the region from our social interactions and archival material.
During open coding, a number of themes began to emerge, and we stopped open coding when no new themes began to emerge (saturation). We then engaged in axial coding, or the creation of more abstract connections, as a way to discover relationships and to explore the most plausible relationships between open codes in the data (Locke, Citation2001; Suddaby, Citation2006). We did not explore the data with a theoretical framework in mind, but rather we allowed meta-level themes to emerge from the data during the process of open coding (Strong et al., Citation2014; Suddaby, Citation2006). In this process, the theme of legitimacy, both with reference to the platform and the IT projects’ need to derive legitimacy from their choice of financing arose repeatedly. Similarly, the features of the digital platform regularly arose as important in that they framed what the IT projects perceived was possible using the platform, and thus whether the platform afforded them the legitimacy that they sought. After several iterations of coding, we found that our codes highlighted a problem of legitimacy – one that stemmed, in large part, from a gulf between the features built into the platform in question, the narratives used by the crowdfunding start-up to convince IT projects to use the platform, and the uses the IT projects ultimately perceived as possible through the platform
The prevalence of the IT Projects’ interpretations was validated through our interviews with other actors in the field not directly involved in crowdfunding (such as business coaches) as well as by following up informally with those interviewed to ensure that we had accurately understood their comments. This process led us to understand how IT Projects did not perceive the crowdfunding platform as affording them with what they needed (i.e., not just financial resources but also the legitimacy that came from getting funding from established, professional investors), contrary to what the platform founders expected when they had designed the platform. This, in turn, affected the platform’s ability to become seen as legitimate. We expand upon these findings below.
4. Empirical findings
Our findings indicate, as earlier suggested, that the entrepreneurial platform founders, as digital entrepreneurs, were aware that they were not yet “taken for granted” in the field in which they found themselves. They were competing in an established and mature field, characterised by clear roles and responsibilities for Projects and Investors, whether business angels or venture capitalists, as well as a clear flow of resources between these actors. Further, the design of their platform did little to enable similar relationships in the digital realm.
Although projects acknowledged that there was some money to be raised through crowdfunding and they did not distrust the entrepreneurial platform, they nevertheless did not see it as conforming to the norms around investment in the field. These norms and expectations, the corresponding platform features, and the tensions that resulted from the combination of the two are summarised and illustrated in . We divided the indicators of legitimacy into three categories, namely the provision of financial capital, the provision of human and social capital, and other intangible indicators of legitimacy.
Table 2. Financing norms in Stockholm, platform features, and the resulting tensions.
Building on this table, how the norms in the field conflicted with the design of the platform, and thus the platform’s attempts at both own its own and others’ legitimacy building are discussed further in this section.
4.1. Norms and expectations around financing
As with any mature field, the investment landscape in Stockholm was well-established when this crowdfunding platform entered the scene. There were established norms around how financiers and projects should behave as well as the relationships between the two. The norms in this field included the idea that investors be well-informed professionals who closely scrutinised an entrepreneurial project before investing, and who invested social and human capital in a firm, not just financial capital. Moreover, projects could choose which investors to approach, and both parties exerted some control over the investment process. These investment relationships were deliberate, long-lasting, and described as relying on extensive prior screening by both investors and IT projects. It also entailed, at a minimum, second-hand knowledge of a project or investor, although direct knowledge and interaction was preferred.
The norms around professional equity investments were the most prominent, and while the entrepreneurial platform did not (at the time) offer equity investment, the projects naturally compared the two. This obvious comparison was reinforced by the platform’s own narrative that it was a “substitute” for other forms of financing.
The single most important thing that projects sought to obtain from a potential investor was a stamp of approval through recognition of both the team and the firm’s product or service. Projects argued the decision to invest was based on a close examination of the firm’s idea, team, and business model by an informed professional:
We weren’t really at the time able to show that we actually lowered returns and increased conversion. It’s hard to get all these stats right – but we had some sort of proof of concept and the seed funding ended up, kind of like, [coming from] a mixture between professional and angels. (Project #11)
The IT project could therefore treat an investor’s decision to invest as a signal to others in the field: that his or her firm was going in the right direction – and had growth potential. This stamp of approval was particularly visible in professional investors’ tendency to invest their time and expertise in a young firm, typically by sitting on the firm’s board and giving the firm advice (human capital):
In particular we, either I or someone in the team, is an active board member… we (also) try to help with hiring management, you have to do some firing sometimes as well, some restructuring of boards and management teams to meet with new challenges that the venture needs after a few years. (Venture Capital investor)
Having a known professional investor on a firm’s board also said something about the firm’s trajectory moving forward. Not only had it attracted a professional investor, but his or her ongoing involvement signalled that the firm was likely to grow and become profitable (social capital):
It’s not just about money. It’s about getting a name into the boardroom. It’s a game of illusions… [which shows that] we are going somewhere because this guy or woman is endorsing us. (Institutional Actor #2)
Moreover, these relationships entailed reciprocity. For investors, investing in a firm that subsequently became a “big” name or made large profits through an ”exit” was key to showing other firms – and investment clients – that they were skilled at their jobs. Moreover, this relationship was mutually beneficial and continued beyond the first investment. It was one that continued for many years as the venture grew and matured, and investors often re-invested in the firm, or introduced firm leadership to investors who would. This allowed the projects to make connections that were otherwise difficult to make in a country with flat hierarchies and tight social networks:
Sweden, I noticed, is a lot, like, relationship based: it’s not that kind of you know you have to have a personal relationship, but they have to have heard about you before, like, somewhere [to invest]. (Project #3)
Furthermore, implicit in this relationship is the idea that both the projects and the investors saw the investment process as one that was clearly defined and tightly controlled (what we have called “exclusive”). That is, few people could do it well and competition for resources was stiff, but, when it occurred, the clear process signalled the value of the firm and the idea:
I kind of feel that if you can’t get, like, if you can’t get money from investors, you’re doing something wrong. (Project #12)
4.2. Tensions between platform features and pre-existing norms
In contrast, the crowdfunding platform was not designed to be exclusive. The platform founders, in building their platform, explained that the features of the platform had been influenced by e-commerce platforms and social networking sites. Indeed, they believed that the use of a fun, social, and inclusive approach to raising funding would be welcomed by projects, among them IT projects, and would provide them with an alternative source of funding. Making the platform “inclusive”, and thus open and attractive to funders beyond traditional, professional ones was part of this strategy:
The concept of crowdfunding means that you can reach across the globe within seconds, thanks to social media and engage people that are willing to give you money or willing to back you or willing to take that chance in order to make things happen. (Platform #2, first interview)
4.2.1. Little to no human or social capital
The overarching understanding of this platform is understood through an examination of its features. When a user clicked through from the platform landing page to see an individual project, the most prominent feature on the project page was a large “Fund this project” button in the centre of the page. Around it were the project’s title, a brief project description, an image or film clip describing the project, and a range of social media icons for a user to share the project with his or her social networks. Below the central button were three tabs, and by default the user landed on the “Project overview” tab. The alternate tabs were “Backers”, or the number of funders, and a “Flag this project” tab in order for a user to easily report concerns around the project (Appendix A).
Beneath the project overview was a comments section in which anyone – whether a funder or curious website visitor – could comment and ask questions about the project. To the right of the page was a bar that tracked the percentage of total funding obtained, the value of the funding obtained (in SEK or EUR) and the time left for the project to receive funding, along with the rewards offered for this particular project. Additionally, scrolling to the bottom again presented the website user with a “Submit your project” button above the bottom menu.
Possible funders were not the subject of much attention on the platform. Beyond an alias, the funders were not required to provide any information about themselves – although some did voluntarily. The backers tab, the second of the three tabs mentioned above, takes the viewer to a list of funders. However, the list contained little information about the backers beyond their aliases and, when they have one, an identifying image. This view of the funder as an anonymous individual, rather than a savvy investor, contrasts with the exclusive and legitimacy-bearing relationship that the IT projects looked for when choosing an investor.
This design points to the idea that raising money from a diverse group of individuals was the primary purpose of the platform. Next, the project and his/her plan were emphasised on the platform. However, the identities and offerings of potential funders were clearly far less important, showing the platform’s asymmetric focus. In particular, the platform primarily provided a platform upon which the (IT) projects could conduct marketing and solicit funding. It did not focus on anything related to the funder, beyond the money he or she invests in the project. Indeed, the platform founders believed that the platform should attract non-professional funders:
Our main goal is two years from now, that lady down there, to get her to say ‘I really love ice cream, where do I go to buy into an ice cream company?’ And then we want [the platform] to be on her tongue and for her to say “Hey, I should look towards a crowdfunding platform and see if I can become an investor in an ice-cream shop”. Because you can’t do that today. (Platform #2, first interview)
As such, the features of the platform provided no information about who potential funders or actual funders were – reinforcing the perception that they are an anonymous “crowd”.
While IT projects acknowledged that they could raise small amounts of money through crowdfunding platforms, they suggested that they could not raise “smart” money since mostly ordinary people – not qualified, savvy investors – would contribute through the platform. Moreover, Sweden’s small population meant that they were unlikely to raise large sums this way. This was reinforced by Swedes’ belief that the high taxes they paid meant that the state should support charitable causes on their behalf. Those who invested via a crowdfunding platform were therefore seen by IT projects as unable to judge the value of a venture. Their investments – both in size and through the lack of demonstrable investor skill – therefore did not signal quality or competence. The inclusivity of the platform, combined with the fact that the IT projects could not screen potential funders, deterred them from using the platform. Indeed, the lack of investor skill made projects feel like they were asking for charity rather than investment:
You basically go out to people without any investment experience, without any knowledge of how to rank or value the start-up, and you ask them [for money]… if you have a decent idea you should be able to get an investor that can do proper due diligence and that can actually get excited about the idea to add some value and not get random people on the street to invest. (Project #11)
4.2.2. One-off transfers of financial capital, reminiscent of e-commerce and charity
The design of the crowdfunding platform’s functions was reminiscent of e-commerce sites in its focus on issues such as simplicity and speed of purchase. The layout of an individual page module was designed to make the process for a funder to choose and fund a project a relatively effortless one requiring only a few clicks, similar to buying any other product or service online – whether used clothing or spare bicycle parts. As one IT project noted:
I think that people are a bit self-conscious. It feels like they’re bragging or something. Because in a way funding a project is a bit like buying a new handbag. It’s just a different demographic. (Project #2)
This observation apparently did not deter Project 2, who together with her team, successfully raised financing through the platform in 2012.
This one-off transaction was not one that appealed to most projects. An alternative use for crowdfunding, beyond investment, was for an IT project to show to potential future investors that he/she is able to communicate well. This possibility emerged but was largely crowded out by the perception that a crowdfunding platform was a marketplace. However, it does indicate that the platform was trusted to deliver (small) amounts of financial capital, but not the other resources that IT projects sought:
So if I would have started this case or this project or company these days, I would definitely have looked into crowd funding, not mainly maybe because I think it, you know, could fully finance you, I wouldn’t see that as the main reason for crowd funding. It will help you a bit with the finance but mainly I would use crowd funding to get attention, to get ambassadors. (Project #8)
4.2.3. No screening, no legitimacy
For professional investors, the fact that they had little control over crowdfunding processes and the lack of long-term influence over a project that had raised crowdfunding was a reason not to use the platform. They also trusted the crowdfunding platform to deliver on its promises, but reacted to their inability to control the process, and thus lose their power to influence the nascent firm’s development. As one investor noted,
A couple of crowdfunding projects have approached us, either as a sponsor or as an investor. And I’ve never taken that up, indeed because partly I feel that we don’t believe enough in crowdfunding to be a sponsor… I’m afraid that our bank trademark could be used as a quality stamp and if we have no impact on the quality of the actual projects then we should not expose our trademark. (Venture Capital investor)
Although crowdfunding had the potential to draw attention to a project, the IT projects did not think that this was enough reason to solicit funding through the platform. In fact, they noted obtaining financing though crowdfunding required considerable effort. Moreover, because of its inclusive nature, both investors and projects felt that they had very little control over the process, as noted above. The feature enabling users to share a project within their social networks meant that the firm’s ideas were spread to anyone anywhere online, and funding from a specific individual could not be rejected. Other IT projects observed that the crowdfunding platform itself did not attract or generate attention on its own. Instead, those projects who had used crowdfunding argued that in order to succeed at crowdfunding, a project had to have built a community prior to undertaking a crowdfunding campaign:
We started to build a community like six months before via Facebook, started a community page, started to reach out and started to do all of this small stuff. And when we actually started the crowdfunding campaign we already had a community of say 400 people that we were already daily talking to, on a daily basis. So that was hugely facilitating because people were like eager for something to happen and then we could just like oh guys now we’re on [platform] so people could give 100 SEK or more. And people gave like 10 000 SEK. (Project #2)
In contrast, crowdfunding was seen as one-off, and projects did not see the potential to enter into a long-term relationship with potential funders. While projects and investors trusted the platform to deliver on its promises, they disliked that they could not control the fundraising process through screening potential funders or limiting who had access to their business idea. The transaction was instead seen as one-off and reminiscent of e-commerce, which made projects think that they had to have something to sell, rather than for funders to invest in. These one-off transactions, conducted with funders who were anonymous and who could not be screened, were seen as typical of crowdfunding.
Having discussed the stumbling block that led to the projects seeing the platform as being trustworthy but not legitimate in the sense of conforming to existing norms and expectations around investment, we now turn to a discussion of the implications of these findings.
5. Discussion and theoretical development
As we found through our research, the entrepreneurial platform needed to provide legitimacy and social and human capital – in addition to financial capital – in order to be considered legitimate. The failure to offer these things meant that the platform not only initially had no legitimacy among IT projects, but also failed to gain the perception of legitimacy among this key potential user group over time. This was due to its failure to conform, either passively or strategically, to existing norms around entrepreneurial finance (Tornikoski & Newbert, Citation2007; Suchman, Citation1995). The fact that IT projects trusted the entrepreneurial platform was not sufficient for them to use it; legitimacy was also required. Below we introduce and substantiate the concept of “designed legitimacy”, building upon the observation that the platform was compared to other, legitimate, actors. We also discuss the implications of these findings and generate propositions for future research.
5.1. Trust and the designed legitimacy of a digital artefact
The single clearest finding in this study is that the entrepreneurial platform was capable of not having legitimacy. For clarity’s sake, this is not the same thing as not being able to have legitimacy. In this case, the projects in question assessed the viability of the platform’s offerings in line with their expectations of a funder and found it lacking in a number of ways, many of which are to do with its design as a platform.
Designed legitimacy requires designing an artefact that, by virtue of its design, is compliant with key actors’ normative expectations in the field. It entails strategic legitimacy building (Suchman, Citation1995) in that the features of the platform, and associated narratives, need to be presented as consistent with existing norms in order to attract key actors. While our data points to the importance of designed legitimacy among crowdfunding platforms, as crowdfunding platforms are a type two-sided platform that creates a marketplace, it is likely that this concept, and the propositions that follow, apply equally to other kinds of two-sided platforms. While the normative content of legitimacy is content-specific, strategic legitimacy building is commonplace where two-sided platforms (especially crowdfunding and crowdsourcing platforms) enter fields with well-established norms. Thus, designed legitimacy may aid those seeking to build and commercialise platforms that behave as online matchmakers or intermediaries (Parker & Van Alstyne, Citation2012; Rochet & Tirole, Citation2003).
5.1.1. Trust and normative conformity
Existing literature has predicted that normative conformity can be a way for a new actor to obtain legitimacy (c.f. Barreto & Baden-Fuller, Citation2006; Deephouse, Citation1996; Dimaggio & Powell, Citation1983; Haveman, Citation1993). However, it has also been observed that normative changes can come from new actors operating from the periphery of a field (Battilana, Leca, & Boxenbaum, Citation2009; Wright & Zammuto, Citation2013), and that digital spaces are known for having many social realities (Björkdahl, Citation2009; Keen & Williams, Citation2013). This begs the question: while legitimacy has clearly been shown to be essential for attracting new users, which norms should be taken into account in the pursuit of legitimacy? Moreover, who are the key users when it comes to gaining legitimacy?
In our case, investment norms were well-established and the platform appealed largely to a geographically bounded set of potential users. These norms governed not only resource transfer but also legitimacy acquisition, notably between the users whom they sought to attract and the funders whom they sought to supplant (). Empirically, the fact that there were no uncertainties or problems with this established set of norms, suggests that conforming to existing norms is, at least at first, necessary. Thus, while potential users trusted the platform, this was not enough to encourage platform use. Incomplete compliance with these norms therefore undermined the platform’s pursuit of legitimacy.
Figure 1. A comparison of the traditional entrepreneurial finance process with that of crowdfunding.
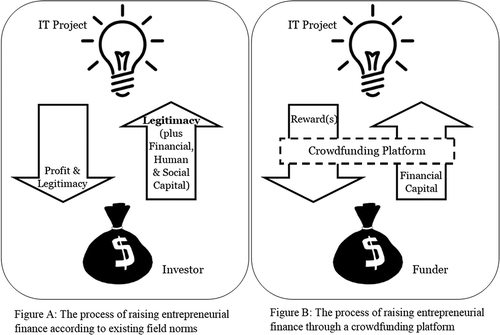
Trust has been seen to be for an entrepreneurial platform to attract new users (Vance, Elie-Dit-Cosaque, & Straub, Citation2008), and it has been treated as sufficient to attract these users (Gefen et al., Citation2003). However, for IT projects to use the platform in this case, the platform not only had to be trustworthy but also had to be seen as a legitimate source of funding by these users. Here, incomplete conformity – by trying to emulate a professional investor without being able to provide the same legitimacy as such an investor might – failed to build legitimacy. While previous research has pointed to the importance of trusting a platform to do what it says it will do (eg, Benbasat & Wang, Citation2005; Gefen, Benbasat, & Pavlou, Citation2008), this research suggests that a platform has to do what it says it will do in the right way. That is, in a way that is consistent with existing norms in the field around how to become – and remain – legitimate.
Proposition 1: Two-sided (crowdfunding) platform adoption requires that a platform gain both trust and legitimacy by key user groups.
The ability of an entrepreneurial platform to comply with these norms, and design such an experience for its users, also depends on which user groups it prioritises. Choosing this key user group is therefore as much a legitimacy question as it is a technical and operational one.
5.1.2. Which users?
In our case, the entrepreneurial platform included several users in its key user group. Among these were IT projects, owing to their digital savviness and their close proximity to the platform founders. The platform was not designed to provide these key users with the same kind of resources as a typical investment relationship. However, that is not to say that it did not provide resources at all. It provided (small amounts of) financial capital, while typical investment relationships delivered some combination of financial, social and human capital. The comparison between the platform and this more human relationship indicates that the platform elicited the same kind of legitimacy assessment as an investor might, which suggests the possibility of designed legitimacy, even if the platform fell short in this case.
In the case of this crowdfunding platform, the platform’s design did not provide an equivalent for the legitimacy that the actor they sought to replace, i.e., the professional financiers, ordinarily provided. Instead, the platform was designed to do what is described in , that is, facilitate the transfer of financial resources. This simple approach relied on an e-commerce-like platform and a narrative that framed the phenomenon as a substitute for existing sources of funding. This design was implemented without reflecting on the legitimacy needs of the actors they were trying to attract, in this case IT projects. Instead, they focused on technical and operational requirements, and overlooked these normative ones.
In this case, one key user group failed to see the platform as legitimate – as the platform could not provide them with the legitimacy they themselves required. The idea that obtaining legitimacy may be contingent on other events or exchanges is one that has been recognised in previous research (Ahlstrom & Bruton, Citation2001; Dart, Citation2004). Garud et al. (Citation2014) find that narratives and stories articulated in the pursuit of legitimacy may themselves create new constraints or barriers to obtaining legitimacy. The case at hand presented a similar paradox, albeit with a double loop effect. Here, obtaining legitimacy by the crowdfunding platform was contingent on being perceived by a key intended user group as providing them with legitimacy:
Proposition 2: A two-sided (crowdfunding) platform derives legitimacy by itself providing legitimacy to a strategically chosen key user group.
By being unable to show IT projects how they could gain legitimacy, the crowdfunding platform could not persuade them to use their service, and consequently could not be seen as legitimate in the eyes of these IT projects. Platform design, in order to attract key users, needed to include normative conformity; the “build it and they will come” approach to design (Markus & Keil, Citation1994) did not work. Instead, attracting a key user group through design becomes a strategic decision that the platform founders need to make.
Pursuant to this line of thinking, we have developed further propositions around designed legitimacy on a platform, or the design of a platform to offer cognitive, structural, and normative compliance with the norms in a field. Three possibilities present themselves, based on this case: the use of symbols and references in design, asymmetric legitimacy building, and multi-stage legitimacy building.
5.2. Digital entrepreneurship and designed legitimacy
It is difficult to see how a platform might provide human and social capital in the same way as an investor might. At best it could form a conduit for these things, but this role is one that platforms are not known for. Instead, two- and multi-sided platforms are better known for price-setting and market transactions (Rochet & Tirole, Citation2003, Citation2004), suggesting that although legitimacy may be theoretically possible, the critical elements needed to facilitate human and social capital flows, and thus legitimacy, need to be designed into a digital artefact.
5.2.1. Mimicry, symbols, and legitimacy building
In our case, legitimacy turned on the ability to screen potential investors and build a long-term relationship. One of the flaws of the design was that the platform was similar to an e-commerce platform, implying a one-off sale instead of a long-term investment. The platform therefore did not provide the possibility for repeated interactions or critical interaction. This feature could, however, be designed into the platform. This is consistent with earlier research around platform adoption, which posits that platform design affects whether, and how, people interact with it (Wheelwright & Clark, Citation1992).
One possible way for legitimacy to be built through a platform is through the use of symbols or symbolic design. It has been observed elsewhere that the use of symbols is often part of legitimacy building (Stringfellow et al., Citation2013; Zott & Huy, Citation2007), but the use of such symbols for legitimacy building has never before been seen in the context of a designed IT artefact, nor, indeed, in the operations of the platform in question.
In this case, the platform did not make explicit use of symbols, but it did emphasise some possibilities over others through design, for instance by making the “fund this project” button more prominent than information about the project itself. By not requiring funders to provide information about themselves, and not displaying what little information was available prominently, the platform also de-emphasised that group of actors, to their detriment. Mimicking existing relationships and hierarchies through design elements would allow platform owners to passively be seen as legitimate.
Proposition 3: Designed legitimacy requires a strategic approach to legitimacy-building.
In this case, the long-term nature of an investment relationship, or temporality, was a key pre-existing norm in the field, and one which had no equivalent in the design of the platform. However, we suggest that it may be possible for designed legitimacy to include temporal elements.
Similarly, design in this case created hierarchies of both features and actors. For instance, the design in the platform under study emphasised the projects and neglected the funders, highlighting one and not the other. Similarly, it highlighted obtaining money rather than obtaining social, financial, and human capital – in conflict with extant norms in the field. However, these hierarchies of norms and perceptions could have been reflected in the platform’s features, suggesting that hierarchies of both features and actors are likely to be key elements of designed legitimacy building.
5.2.2. Asymmetry in legitimacy building
Taking this one step further, one intuitively thinks that a crowdfunding platform’s designed legitimacy might entail gaining legitimacy from both projects and potential funders, to the same extent. However, this paper also finds asymmetry in who was willing to use the crowdfunding platform, implying that encouraging one key user group over another may be of strategic important. Gaining legitimacy from these two groups therefore also requires strategic legitimacy building through design.
Our initial impression was that gaining legitimacy relied, in the first instance, on being seen as legitimate by a key user group, in this case IT projects in the Stockholm context. This was because without interesting and credible projects on the platform, the funders in question would not engage with the crowdfunding platform. This observation is consistent with previous research around projects’ expectations and the role of norms in crowdfunding (Gleasure, Citation2015; Gleasure & Feller, Citation2016a). However, as we looked deeper, the role of the platform’s features in this deterrence became clearer and its importance was highlighted. In short, the platform, in the pursuit of legitimacy, failed to emphasise both user groups in order to asymmetrically gain legitimacy for (and from) the IT projects.
This strategically important way of designing legitimacy stems from the fact that the crowdfunding platform is operating in a field characterised by relationship-driven norms around financing. That is, norms that require that both parties be visible. In our study, the invisibility of the funders and backers meant that the IT projects did not think that the platform could offer human or social capital.
While information asymmetries in legitimacy building are commonplace (Feldman & March, Citation1981; Mavlanova, Benbunan-Fich, & Koufaris, Citation2012), such symmetry in legitimacy building itself has not yet been examined. Indeed, the notion of symmetry in design in order to asymmetrically gain legitimacy is counter-intuitive. Here, not only does the two-sided platform need to strategically design legitimacy, it needs to highlight multiple user groups on the platform in order to gain legitimacy among just one key user group. This is a consequence of the importance of relationships in the prevailing local context.
Proposition 4: Designed legitimacy on a two-sided (crowdfunding) platform requires highlighting multiple user groups in order to gain legitimacy with the key user group.
5.2.3. Sequential legitimacy building
Additionally, such an approach might suggest that in the context of two-sided, or matchmaking, platforms, designed legitimacy might need to take a strategic two-stage approach, focusing at first on one user group and then on the other. In this case, failure to be seen as legitimate by IT projects meant that investors were not interested in the platform. This is because while designing for legitimacy initially relies on being able to offer legitimacy through platform features, attracting subsequent user groups may rely on the platform actually having that legitimacy.
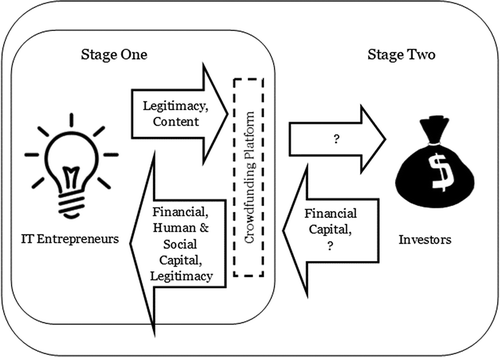
Obtaining legitimacy with the second group would entail providing the first group with legitimacy, and thus being seen as legitimate themselves. Being perceived as legitimate by the second group would thus depend on obtaining legitimacy with the first. Based on this we present our fifth proposition and illustrate this process in .
Proposition 5: Two-stage legitimacy building can drive two-sided (crowdfunding) platform legitimacy.
Figure 2. Legitimacy acquisition by a crowdfunding platform in an asymmetric, and possibly sequential two-stage, model.
Theoretical and empirical examinations have suggested that platforms, particularly two-sided platforms, are complex to design as both their features (Eaton et al., Citation2015; Tiwana et al., Citation2010) and the context in which potential users find themselves (Evans, Citation2009) influence how they are perceived by one, or both, sides of the platform. Indeed, we see here that strategic designed legitimacy is vital for legitimacy building.
The importance of these findings around designing for legitimacy extend beyond just platforms. Given the plurality of ideas that abound online (Björkdahl, Citation2009; Keen & Williams, Citation2013), and the inherent generativity of digital artefacts (Yoo et al., Citation2012; Zittrain, Citation2006), design is one of the ways in which a digital entrepreneur, mediated by a platform, can affect how its product or service is interpreted and used, both in different geographies, and over time. Indeed, these findings highlight the importance of design and normative compliance in digital entrepreneurship more broadly.
5.3. Practical guidelines
Designed legitimacy is likely to be something that becomes more important as more and more economic activity, both entrepreneurial and otherwise, moves into the digital realm. For practitioners, this paper highlights how design is a key part of legitimacy building as described above. Consequently, the design of the platform is an integral part of building the business and something that should be done in a strategic way, taking into account the links between design and norms, not just user experience.
This paper also highlights how design can (and cannot) be used to build relationships with would-be users, especially when it comes to creating hierarchies and long-term relationships. Where these are important norms in a field, practitioners should ensure that they are reflected in a venture’s digital presentation.
6. Conclusion and implications
Our case study revealed an unsuccessful attempt at legitimacy building by a digital entrepreneur mediated by a two-sided platform. Despite the fact that it was trusted, the platform’s initial failure to be perceived as legitimate stemmed largely from the IT projects’ (i.e., a key target user group) perception of the platform. The features and symbols that the platform evoked did not afford IT projects investment possibilities that their owners saw as useful. We derived propositions for further investigation based on these findings.
What these findings, and the linked propositions, suggest is that legitimacy itself is a resource that cannot be overlooked when examining the flow of resources within an established field. This is contrary to a widespread “build it and they will come” approach to IS design (Markus & Keil, Citation1994). Rather, it suggests that the operational and technical focus on building a product that fulfils a perceived need is not enough; that normative elements are also vital to a new platform’s success.
When digital entrepreneurs enter an existing mature field mediated by a platform or artefact, they need to consider that the overt flow of resources, such as financial capital, may only be part of the picture. Indeed, the relationships between parties may include legitimacy, as seen here, and attempts by the digital entrepreneurs behind the platform need to include an alternative source of legitimacy for the user group to which they are appealing.
These findings also indicate that it is possible for a platform to not be seen as legitimate. This is very promising for future studies of platform legitimacy and legitimacy building, and we suggest that it implies that platform legitimacy is similarly possible.
Moreover, framing and the use of symbols by the platform must be consistent with extant norms and mimic offline relationships. Where the two are inconsistent (or the mimicry incomplete), users struggle to ascertain which message to believe, which undermines the platform’s ability to gain legitimacy.
Finally, one group of users may need to be prioritised first when it comes to providing this legitimacy; in this case it was the IT projects. In any event, building a platform in the “build it and they will come” manner without considering that being seen as legitimate by one group of users may be a prerequisite for being seen as legitimate by other groups of users.
This research relied upon a single case study, which may limit the generalisability of our findings (Gibbert, Ruigrok, & Wicki, Citation2008). However, this study points to the importance of strategic and normative compliance (despite the fact that their content is context-specific) in platform development; something that we think is deserving of further investigation.
Moreover, the project owners we interviewed were primarily producing software, rather than hardware, which may affect their perception of the phenomenon. The unique cultural context in which this study was conducted may also mean that it is not generalisable outside of Sweden, a country known for its flat hierarchies and tight social networks (Jonsson & Buhr, Citation2011; Landstrom, Citation1995). Future research could examine other contexts to see how empirically generalisable the findings are as well as to investigate further contingencies and asymmetries in the pursuit of legitimacy in multi-sided platforms.
With this research, we have taken a first step in understanding whether, and how, a platform can gain legitimacy. We also observe that trusting a platform is not always sufficient for adoption, but that legitimacy may pave the way to adoption. In our study we focused on a donation- and reward-based crowdfunding platform in Sweden, but our findings are likely to be generalisable to other crowdfunding, crowdsourcing and other matchmaking, or two-sided, platforms. They also articulate the centrality of a platform for digital entrepreneurship, and how the platform is key to the entrepreneurs’ legitimacy building attempts.
In this case, being seen as legitimate was contingent on providing legitimacy to the platform’s users. Moreover, the features and design of a platform, where they do not match the objectives of the user, can lead to a situation in which the platform in question is perceived as not being legitimate. Lastly, legitimacy building may require asymmetrical efforts even when a platform is two-sided. These theoretical contributions require further examination in different contexts and in taking account both sides of a two-sided platform. They pose unanswered questions around legitimacy and platforms for platform theorists and design science that are ripe for investigation. It also shines a light on the centrality of digital artefacts for digital entrepreneurship, in this case through a crowdfunding platform.
Disclosure statement
No potential conflict of interest was reported by the authors.
Additional information
Funding
Notes
1. Consequently, legitimacy is heavily context-dependent. This poses a challenge for the generalisability of a study of legitimacy when it comes to a phenomenon like crowdfunding. Understanding some of the underlying dynamics whereby legitimacy is obtained, even if its normative content differs, may aid in future theorising around platforms, if not around legitimacy. We thank one of EJIS’s reviewers for this subtle point.
2. Thank you to one of our reviewers for pointing out the challenges involved in being seen as legitimate when one has to appeal to user groups that are likely to have a plurality of social realities.
References
- Agrawal, A., Catalini, C., & Goldfarb, A. (2015). Crowdfunding: Geography, social networks, and the timing of investment decisions. Journal of Economics & Management Strategy, 24(2), 253–274.
- Ahlstrom, D., & Bruton, G. D. (2001). Learning from successful local private firms in China: Establishing legitimacy. The Academy of Management Executive, 15(4), 72–83.
- Andersson, S., & Wictor, I. (2003). Innovative internationalisation in new firms: Born globals – The Swedish case. Journal of International Entrepreneurship, 1(3), 249–275.
- Ashforth, B. E., & Gibbs, B. W. (1990). The double-edge of organizational legitimation. Organization Science, 1(2), 177–194.
- Avdeitchikova, S. (2008). On the structure of the informal venture capital market in Sweden: Developing investment roles. Venture Capital, 10(1), 55–85.
- Bakos, Y., & Katsamakas, E. (2008). Design and ownership of two-sided networks: Implications for internet platforms. Journal of Management Information Systems, 25(2), 171–202.
- Barreto, I., & Baden-Fuller, C. (2006). To conform or to perform? Mimetic behaviour, legitimacy-based groups and performance consequences. Journal of Management Studies, 43(7), 1559–1581.
- Battilana, J., Leca, B., & Boxenbaum, E. (2009). How actors change institutions: Towards a theory of institutional entrepreneurship. The Academy of Management Annals, 3(1), 65–107.
- Belleflamme, P., Lambert, T., & Schwienbacher, A. (2014). Crowdfunding: Tapping the right crowd. Journal of Business Venturing, 29(5), 585–609.
- Benbasat, I., & Wang, W. (2005). Trust in and adoption of online recommendation agents. Journal of the Association for Information Systems, 6(3), 4.
- Björkdahl, J. (2009). Technology cross-fertilization and the business model: The case of integrating ICTs in mechanical engineering products. Research Policy, 38(9), 1468–1477.
- Bretschneider, U., & Leimeister, J. M. (2017). Not just an ego-trip: Exploring backers’ motivation for funding in incentive-based crowdfunding. The Journal of Strategic Information Systems, 26(4), 246–260.
- Burtch, G., Ghose, A., & Wattal, S. (2013). An empirical examination of the antecedents and consequences of contribution patterns in crowd-funded markets. Information Systems Research, 24(3), 499–519.
- Burtch, G., Ghose, A., & Wattal, S. (2016). Secret admirers: An empirical examination of information hiding and contribution dynamics in online crowdfunding. Information Systems Research, 27(3), 478–496.
- Casper, S., & Whitley, R. (2004). Managing competences in entrepreneurial technology firms: A comparative institutional analysis of Germany, Sweden and the UK. Research Policy, 33(1), 89–106.
- Cassell, J., & Bickmore, T. (2000). External manifestations of trustworthiness in the interface. Communications of the ACM, 43(12), 50–56.
- Cheshire, T. (2011). Europe’s hottest startup capitals: Stockholm (Wired UK). https://www.wired.co.uk/article/stockholm-2.
- Colombo, M. G., Franzoni, C., & Rossi-Lamastra, C. (2015). Internal social capital and the attraction of early contributions in crowdfunding. Entrepreneurship Theory and Practice, 39(1), 75–100.
- Corbin, J. M., & Strauss, A. (1990). Grounded theory research: Procedures, canons, and evaluative criteria. London: Sage.
- Corritore, C. L., Kracher, B., & Wiedenbeck, S. (2003). On-line trust: Concepts, evolving themes, a model. International Journal of Human-Computer Studies, 58(6), 737–758.
- Cusumano, M. A., & Gawer, A. (2002). The elements of platform leadership. MIT Sloan Management Review, 43(3), 51.
- Dart, R. (2004). The legitimacy of social enterprise. Nonprofit Management and Leadership, 14(4), 411–424.
- Davidson, E., & Vaast, E. (2010). Digital entrepreneurship and its sociomaterial enactment. In: Proceedings of the Annual Hawaii International Conference on System Sciences. pp. 1–10, IEEE.
- Davidsson, P., & Findahl, O. (2016) Svenskarna och internet 2016. Stockholm Retrieved August 07, 2017, from https://www.iis.se/docs/Svenskarna_och_internet_2016.pdf
- De Vaujany, F-X., & Vaast, E. (2014). If these walls could talk: The mutual construction of organizational space and legitimacy. Organization Science, 25(3), 713–731.
- Deephouse, D. D. L., & Suchman, M. (2008). Legitimacy in organizational institutionalism. In The Sage handbook of organizational institutionalism (pp. 77). London: SAGE Publications Ltd.
- Deephouse, D. L. (1996). Does isomorphism legitimate? Academy of Management Journal, 39(4), 1024–1039.
- Dimaggio, P. J., & Powell, W. W. (1983). The iron cage revisited: Institutional isomorphism and collective rationality in organizational fields. American Sociological Review, 48(2), 147–160.
- Drori, I., Honig, B., & Sheaffer, Z. (2009). The life cycle of an internet firm: Scripts, legitimacy, and identity. Entrepreneurship: Theory and Practice, 33(3), 715–738.
- Eaton, B., Elaluf-Calderwood, S., Sørensen, C., & Yoo, Y. (2015). Distributed tuning of boundary resources: The case of apple’s IOS service system. MIS Quarterly, 39(1), 217–243.
- Eisenmann, T., Parker, G., & Van Alstyne, M. (2011). Platform envelopment. Strategic Management Journal, 32(12), 1270–1285.
- Erikson, T. (2002). Entrepreneurial capital: The emerging venture’s most important asset and competitive advantage. Journal of Business Venturing, 17(3), 275–290.
- Evans, D. S. (2003). Some empirical aspects of multi-sided platform industries. Review of Network Economics, 2, 3.
- Evans, D. S. (2009). How catalysts ignite: The economics of platform-based start-ups. In A. Gawer (Ed.), Platforms, markets and innovation (pp. 99-130). Cheltenham, UK and Northampton, MA, US: Edward Elgar Publishing.
- Feldman, M. S., & March, J. G. (1981). Information in organizations as signal and symbol. Administrative Science Quarterly, 26(2), 171–186.
- Friedman, B., Khan, P. H., JR, & Howe, Dc. (2000). Trust online. Communications of the ACM, 43(12), 34–40.
- Garud, R., Schildt, H., & Lant, T. (2014). Entrepreneurial storytelling, future expectations, and the paradox of legitimacy. Organization Science, 25(5), 1479–1492.
- Gawer, A. (2009). Platforms, markets and innovation. Cheltenham, UK: Edward Elgar Publishing.
- Gawer, A., & Cusumano, M. A. (2014). Industry platforms and ecosystem innovation. Journal of Product Innovation Management, 31(3), 417–433.
- Gefen, D., Benbasat, I., & Pavlou, P. A. (2008). A research agenda for trust in online environments. Journal of Management Information Systems, 24(4), 275–286.
- Gefen, D., Karahanna, E., & Straub, D. W. (2003). Trust and TAM in online shopping: An integrated model. MIS Quarterly, 27(1), 51–90.
- Gibbert, M., Ruigrok, W., & Wicki, B. (2008). What passes as a rigorous case study? Strategic Management Journal, 29, 1465–1474.
- Gleasure, R. (2015). Resistance to crowdfunding among entrepreneurs: An impression management perspective. Journal of Strategic Information Systems, 24(4), 219–233.
- Gleasure, R., & Feller, J. (2016a). A rift in the ground: Theorizing the evolution of anchor values in crowdfunding communities through the oculus rift case study. Journal of the Association of Information Systems, 17(10), 708–736.
- Gleasure, R., & Feller, J. (2016b). Emerging technologies and the democratisation of financial services: A metatriangulation of crowdfunding research. Information and Organization, 26(4), 101–115.
- Graebner, M. E., & Eisenhart, K. M. (2007). Theory building from cases: Opportunities and challenges. Academy of Management Journal, 50(1), 25–32.
- Haveman, H. A. (1993). Follow the leader: Mimetic isomorphism and entry into new markets. Administrative Science Quarterly, 38(4), 593–627.
- Henfridsson, O., & Bygstad, B. (2013). The generative mechanisms of digital infrastructure evolution. MIS Quarterly, 37(3), 907–931.
- Henfridsson, O., & Yoo, Y. (2014). The liminality of trajectory shifts in institutional entrepreneurship. Organization Science, 25(3), 932–950.
- Jones, C. (2018) Apple’s app store generated over $11 Billion in revenue for the company last year. Forbes.com. Retrieved from https://www.forbes.com/sites/chuckjones/2018/01/06/apples-app-store-generated-over-11-billion-in-revenue-for-the-company-last-year/.
- Jonsson, S., & Buhr, H. (2011). The limits of media effects: Field positions and cultural change in a mutual fund market. Organization Science, 22(2), 464–481.
- Katz, M. L., & Shapiro, C. (1994). Systems competition and network effects. Journal of Economic Perspectives, 8(2), 93–115.
- Keen, P., & Williams, R. (2013). Value architectures for digital business: Beyond the business model. MIS Quarterly, 37(2), 642–647.
- Kelestyn, B., & Henfridsson, O. (2014). Everyday digital entrepreneurship: The inception, shifts, and scaling of future shaping practices. International Conference for Information Systems, Auckland, New Zealand.
- Kerr, W. R., Lerner, J., & Schoar, A. (2014). The consequences of entrepreneurial finance: Evidence from angel financings. Review of Financial Studies, 27(1), 20–55.
- Koufaris, M., & Hampton-Sosa, W. (2004). The development of initial trust in an online company by new customers. Information & Management, 41(3), 377–397.
- Landstrom, H. (1995). A pilot study on the investment decision-making behavior of informal investors in sweden. Journal of Small Business Management, 33(3), 67-76.
- Lin, M., & Viswanathan, S. (2015). Home bias in online investments: An empirical study of an online crowdfunding market. Management Science, 62(5), 1393–1414.
- Locke, K. (2001). Grounded theory in management research. London: Sage Publications Ltd.
- Majumdar, A., & Bose, I. (in press). My words for your pizza: An analysis of persuasive narratives in online crowdfunding. Information & Management, 55(6), 781–794.
- Markus, M. L., & Keil, M. (1994). If we build it, they will come: Designing information systems that people want to use. Sloan Management Review, 35, 11.
- Martens, M. L., Jennings, J. E., & Jennings, P. D. (2007). Do the stories they tell get them the money they need? The role of entrepreneurial narratives in resource acquisition. Academy of Management Journal, 50(5), 1107–1132.
- Mavlanova, T., Benbunan-Fich, R., & Koufaris, M. (2012). Signaling theory and information asymmetry in online commerce. Information & Management, 49(5), 240–247.
- Mayer, R. C., Davis, J. H., & Schoorman, F. D. (1995). An integrative model of organizational trust. Academy of Management Review, 20(3), 709–734.
- Meyer, J. W., & Rowan, B. (1977). Institutionalized organizations: Formal structure as myth and ceremony. American Journal of Sociology, 83, 340–363.
- Meyer, J. W, & Scott, W. R. (1983). Organizational environments: ritual and rationality. Beverly Hills: Sage.
- Mollick, E. (2014). The dynamics of crowdfunding: An exploratory study. Journal of Business Venturing, 29(1), 1–16.
- Muir, B. M., & Moray, N. (1996). Trust in automation. Part II. Experimental studies of trust and human intervention in a process control simulation. Ergonomics, 39(3), 429–460.
- Nambisan, S. (2017). Digital entrepreneurship: Toward a digital technology perspective of entrepreneurship. Entrepreneurship Theory and Practice, 41(6), 1029–1055.
- Parker, G. G., & Van Alstyne, M. W. (2012). Two-sided network information effects: A theory of product design. Management Science, 51(10), 1494–1504.
- Porter, M. E. (1998). Clusters and the new economics of competition. Harvard Business Review, 76(6), 77-90
- Porter, M. E. (2000). Location, competition, and economic development: Local clusters in a global economy. Economic Development Quarterly, 14(1), 15–34.
- Reeves, B, & Nass, C. (1996). The media equation: how people treat computers, television, and new media like real people and places. New York, NY: Cambridge University Press.
- Rochet, J.-C., & Tirole, J. (2003). Platform competition in two-sided markets. Journal of the European Economic Association, 1(4), 990–1029.
- Rochet, J.-C., & Tirole, J. (2004). Defining two-sided markets. IDEI Working paper, Toulouse, France.
- Siering, M., Koch, J.-A., & Deokar, A. V. (2016). Detecting fraudulent behavior on crowdfunding platforms: The role of linguistic and content-based cues in static and dynamic contexts. Journal of Management Information Systems, 33(2), 421–455.
- Stringfellow, L., Shaw, E., & Maclean, M. (2013). Apostasy versus legitimacy: Relational dynamics and routes to resource acquisition in entrepreneurial ventures. International Small Business Journal, 32(5), 571–592.
- Strong, D. M., Johnson, S. A., Tulu, B., Trudel, J., Volkoff, O., Pelletier, L. R., … Garber, L. (2014). A theory of organization-EHR affordance actualization. Journal of the Association for Information Systems, 15(2), 53–85.
- Suchman, M. C. (1995). Managing legitimacy: Strategic and institutional approaches. Academy of Management Review, 20(3), 571–610.
- Suddaby, R. (2006). From the editors: What grounded theory is not. Academy of Management Journal, 49(4), 633–642.
- Suddaby, R., & Greenwood, R. (2005). Rhetorical strategies of legitimacy. Administrative Science Quarterly, 50, 35–67.
- Sztompka, P. (1999). Trust: A sociological theory. Cambridge: Cambridge University Press.
- Tiwana, A., Konsynski, B., & Bush, A. (2010). Platform evolution: Coevolution of platform architecture, governance, and environmental dynamics. Information Systems Research, 21(4), 675–687.
- Tornikoski, Et., & Newbert, S. L. (2007). Exploring the determinants of organizational emergence: A legitimacy perspective. Journal of Business Venturing, 22(2), 311–335.
- Van Lente, H. (2012). Navigating foresight in a sea of expectations: Lessons from the sociology of expectations. Technology Analysis & Strategic Management, 24(8), 769–782.
- Vance, A., Elie-Dit-Cosaque, C., & Straub, D. W. (2008). Examining trust in information technology artifacts: The effects of system quality and culture. Journal of Management Information Systems, 24(4), 73–100.
- Weber, M. (1978). Economy and society: An outline of interpretive sociology. Los Angeles: University of California Press.
- Wessel, M., Thies, F., & Benlian, A. (2017). Opening the floodgates: The implications of increasing platform openness in crowdfunding. Journal of Information Technology, 32(4), 344–360.
- Wheelwright, S. C., & Clark, K. B. (1992). Revolutionizing product development: Quantum leaps in speed, efficiency, and quality. New York, NY: Simon and Schuster.
- Wright, A. L., & Zammuto, R. F. (2013). Wielding the willow: Processes of institutional change in english county cricket. Academy of Management Journal, 56(1), 308–330.
- Yin, R. (2003). Applications of case study research (Applied social research methods)4th editio. Thousand Oaks: Sage.
- Yin, R. K. (1981). The case study crisis: Some answers. Administrative Science Quarterly, 26(1), 58–65.
- Yoo, Y., Boland, R. J., Lyytinen, K., & Majchrzak, A. (2012). Organizing for innovation in the digitized world. Organization Science, 23(5), 13–32.
- Zimmerman, M. A., & Zeitz, G. J. (2002). Beyond survival: Achieving new venture growth by building legitimacy. Academy of Management Review, 27(3), 414–431.
- Zittrain, J. L. (2006). The generative internet. Harvard Law Review, 119, 1974–2040.
- Zott, C., & Huy, Q. N. (2007). How entrepreneurs use symbolic management to acquire resources. Administrative Science Quarterly, 52(1), 70–105.