ABSTRACT
Employee behaviour is fundamental to corporate information security (InfoSec) capabilities across the phases of prevention, detection, and response. Unfortunately, despite over a decade of research on the topic, the human aspect of security remains the most vulnerable in many companies today, often rooted in employee disinterest. Two traditions within the InfoSec research that may contribute to this disconnect are 1) emphasis on extrinsic manipulation of behaviour versus cultivation of internalised commitment to organisational InfoSec and 2) emphasis on isolated activities over more integrated perspectives of security behaviour. Addressing these gaps, the current study examines end user InfoSec behaviour through a distinct internal motivational lens. Rooted in Self-Determination Theory, a research model is introduced that highlights workplace factors which drive end users’ internalised commitment to organisational InfoSec by fulfiling fundamental psychological needs (autonomy, competence, and relatedness) within this context. Commitment, which captures internally regulated motivation to contribute to organisational InfoSec performance, is then positioned as a driver of intention to engage in various security behaviours. Overall, the results support the study’s hypotheses and underscore the important roles perceived behavioural control, IT competence, and user-IS department relations have on commitment to organisational InfoSec and resultant behavioural outcomes.
1. Introduction
Employee behaviour is fundamental to corporate information security (InfoSec) capabilities across the phases of prevention, detection, and response (Baskerville et al., Citation2014). In both on-premises and work-from-home contexts, companies rely on end users to protect valuable information from various forms of security threats (Menard et al., Citation2017). Unfortunately, the human aspect of an organisation’s system of security continues to be the most vulnerable in many companies today. Recent estimates suggest that over half of businesses worldwide still consider their own employees to be the biggest weakness in security (Kaspersky, Citation2017), which typically manifests as behaviours that deviate from organisational InfoSec values and goals (Balozian et al., Citation2019). Despite industry’s best efforts to address the issue with technical and process controls, organisations still rely heavily on human intervention (Menard et al., Citation2017), highlighting the ongoing importance of end user behaviour modification in managing organisational InfoSec risk.
A large body of scholarly work on how and why end users contribute to organisational InfoSec performance has highlighted a multitude of isolated behaviours in this context. Extending beyond isolated behaviours, researchers have also delineated different types of security behaviours that constitute the domain. For example, in-role and extra-role behaviours have been highlighted as two mutually exclusive types of security behaviour, distinguished by whether they are formally specified in organisational information security policies (ISPs) (Hsu et al., Citation2015). Along with these contributions, much progress has been made in identifying factors that regulate individuals’ enactment of security behaviours, driving a number of prescribed interventions for enhancing behavioural InfoSec across the enterprise. Factors including fear appeals (Herath & Rao, Citation2009; Johnston & Warkentin, Citation2010; Johnston et al., Citation2015), rewards (Herath & Rao, Citation2009), sanctions (Bulgurcu et al., Citation2010), monitoring, and performance evaluation (Lowry & Moody, Citation2015) have been introduced and validated within this context.
As evidenced above, substantial progress has been made in identifying various drivers of different security behaviours that ultimately contribute to the organisation’s InfoSec posture. Despite this, problems in the human side of organisational InfoSec continue to burden companies, often rooted in employee disinterest in security threats and the behaviours that mitigate them (Johnston et al., Citation2019). A review of the extant literature (Appendix A) reveals two traditions within this stream that may help explain the disconnect between scholarly productivity and performance in practice. The first, reflected in a large proportion of studies, is an emphasis on external regulators (e.g., ancillary consequences and/or rewards) to manipulate security behaviour. Fear appeals, for example, influence security behaviour by inflating the perceived severity of security threats (fear), which drives coping appraisal and ultimately protection motivation (Herath & Rao, Citation2009; Johnston & Warkentin, Citation2010). As another example, tangible rewards inflate perceptions regarding personal benefits gained from security behaviours, triggering motivation to enact them (Bulgurcu et al., Citation2010; Han et al., Citation2017). While demonstrably effective in the short term, external behavioural regulators hold important limitations that can inhibit their utility in practice over time.
For one, external behavioural regulators immediately lose their influence once removed (Kohn, Citation1993). Even with sustained presence, people can become desensitised to external regulators over time, eroding their effectiveness (De Vos et al., Citation2017). Finally, past research demonstrates that use of external behavioural regulators can reduce employees’ intrinsic motivation to perform tasks and cause drop-offs in task-level learning (Lepper & Greene, Citation2015; Ryan & Deci, Citation2017). In contexts where employee persistence and performance are important and the organisation benefits from task-level learning, intrinsic motivational processes should be favoured (Deci & Ryan, Citation1985; Ryan & Deci, Citation2017). Accordingly, more work is needed that investigates factors promoting internal regulation of desirable security behaviour among employees.
A second tradition within this stream is emphasis on isolated security behaviours versus broader conceptualisations of end user behavioural security. Although detailed constructs and powerful explanatory models have resulted from this tradition, the knowledge created from research on isolated behaviours or behaviour subsets may not generalise to the grand structure of security behaviour (Posey et al., Citation2013). In the literature, in-role and extra-role behaviours (Hsu et al., Citation2015) effectively capture the domain of behavioural InfoSec; however, these two subtypes have traditionally been investigated separately. An important risk of this approach is misclassification of activities in certain organisational contexts (e.g., 360-degree evaluations and/or leadership by example), which can affect research results and the recommendations they inform (Hsu et al., Citation2015). Thus, more work is needed that examines broader conceptualisations of InfoSec behaviour (Posey et al., Citation2015, Citation2013).
In response to the ongoing InfoSec problems faced by organisations and the research gaps described above, this study seeks to uncover factors that drive end users’ internalised commitment to organisational InfoSec performance and the effects of that commitment on subsequent intention to engage in a range of security behaviours. In line with prior information systems (IS) research (Menard et al., Citation2017; Wright et al., Citation2014), this study roots in Self-Determination Theory (SDT) (Deci & Ryan, Citation1985), which recognises the existence of multiple different forms of motivated behaviour. Specifically, SDT describes a continuum of behavioural regulation anchored by wholly externally controlled on one end and wholly internally integrated on the other (Deci & Ryan, Citation1985; Gagné & Deci, Citation2005; Wright et al., Citation2014). Moreover, SDT postulates that the values embedded within external regulators can become internalised when three basic psychological needs are fulfilled–autonomy, competence, and relatedness (Deci & Ryan, Citation1985; Ryan & Deci, Citation2017). Here, we apply SDT to understand the intrinsic motivational mechanisms underpinning a range of security behaviours.
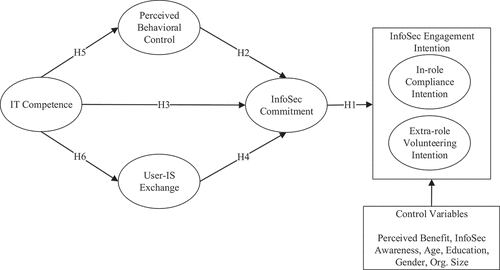
Rooted in SDT, a research model is developed which positions perceived behavioural control (PBC), information technology (IT) competence, and user-IS department exchange as needs-fulfilment factors driving end users’ commitment to organisational InfoSec performance. InfoSec commitment is in turn positioned as an intrinsic motivational driver of intention to engage in various security behaviours. Responding to past calls (Posey et al., Citation2013), security behaviour is captured via a theory-grounded, multidimensional construct labelled InfoSec engagement which subsumes two distinct types of behaviours – in-role compliance and extra-role volunteering. After introducing the constructs and the model, we report the results of testing, which were informed by 993 business end users across a variety of companies and industries. We then discuss important implications of the results for researchers and practitioners. Overall, this study seeks to answer the following research question:
RQ1: What drives end user commitment to organisational InfoSec performance and intention to engage in the range of behaviours contributing to that performance?
2. Theoretical development
Personal motivation, defined as a force that directs individuals towards specific goals (Kettinger et al., Citation2015), is widely regarded as a powerful determinant of an individual’s workplace behaviours. One of the most referenced theories on the nature and psychology of motivation is Self-Determination Theory (SDT) (Deci & Ryan, Citation1985). SDT recognises four different types of motivation – external, introjected, identified, and integrated – which reside as points (in the order presented) along a motivational continuum, distinguished by the degree to which target behaviour is externally versus internally regulated (Ryan & Deci, Citation2017). With external regulation, motivation is initiated and maintained by contingencies outside the person, such as rewards or consequences. Meanwhile, on the opposite end of the continuum, integrated regulation captures motivation initiated by fit between the values embedded in a behavioural contingency and the person’s own value system (Gagné & Deci, Citation2005). Between the two ends, introjected regulation and identified regulation capture varying combinations of external versus internal regulation (Ryan & Deci, Citation2017).
In addition to describing different types of behavioural regulation and the continuum on which they reside, SDT postulates that under certain conditions, an externally regulated behaviour can become internally regulated, as the values embedded within the external contingency become adopted by the individual and incorporated into his/her personal value system. This transformation occurs through a psychological process broadly referred to as internalisation and described as taking in values, beliefs, or behavioural regulations from external sources and transforming them into one’s own (Ryan & Deci, Citation2017). When internalisation occurs, behaviour regulation effectively moves along the continuum, from external to internally integrated (Ryan & Deci, Citation2017).
SDT further explains that internalisation is triggered by satisfaction of three basic psychological needs within a target context – need for autonomy, need for competence, and need for relatedness (Deci & Ryan, Citation1985; Ryan & Deci, Citation2017). Autonomy, as applied in SDT, refers to the innate need of individuals to experience self-endorsement, self-regulation, and control over their actions. Competence captures feeling effective in one’s interactions with the environment. Finally, relatedness captures feeling connected and involved with others and having a sense of belonging (Ryan & Deci, Citation2017). Contexts that aid in the fulfilment of these basic needs foster internalisation of the values embedded in the behavioural contingencies within that context (Deci & Ryan, Citation1985; Ryan & Deci, Citation2017).
Applied to InfoSec, the theoretical tenets of SDT shed valuable light on the fundamental psychological processes underpinning end users’ internalisation of organisational InfoSec performance and subsequent intention to engage in behaviours supporting that performance. Specifically, workplace factors that help fulfil the end user’s basic psychological needs for autonomy, competence, and relatedness in this context should drive internalised commitment to organisational InfoSec performance. Commitment to InfoSec performance then should internally drive end user engagement in desired security behaviours.
3. Construct development
3.1. End user InfoSec engagement intention
Engagement has been conceptualised as a human trait, a situational psychological state, and a behavioural construct in organisational research. While all three are important to understanding differences in how employees approach work, behavioural engagement is uniquely oriented around activity performance and generally considered an outcome of trait and state engagement (Macey & Schneider, Citation2008). Thus, the current study focuses on the behavioural form of engagement. One of the earliest conceptualisations of behavioural engagement, provided by Kahn (Citation1990), describes it as an expression of a person’s preferred self in task behaviours that promote connections to work and others, and full role performance. Macey and Schneider (Citation2008) later defined behavioural engagement as adaptive behaviour intended to serve an organisational purpose. Finally, Xu and Cooper Thomas (Citation2011) described it as the individual making full use of his/her cognitive, emotional, and physical resources to perform work. While nuanced differences exist between these conceptualisations, they all generally capture an employee’s exhibition of behaviours that support organisational goals, both within and beyond his/her assigned duties.
Consistent with the behavioural engagement literature, past research on job performance argues that employees contribute to organisational goals through two distinct types of activities – task activities and contextual activities (Borman & Motowidlo, Citation1993; Motowidlo & Van Scotter, Citation1994). Task activities and contextual activities differ in three important ways. First and foremost, whereas task activities are role prescribed and recognised as part of the job, contextual activities are voluntary in nature (Conway, Citation1999; Motowidlo & Van Scotter, Citation1994). Second, task activities generally contribute directly or indirectly to the organisation’s technical core; meanwhile, contextual activities may not support the technical core as much as they support the organisational, social and psychological environment in which the technical core functions. Finally, task activity performance relies primarily on an individual’s competencies while contextual activity performance relies mainly on volition and predisposition (Borman & Motowidlo, Citation1993; Motowidlo & Van Scotter, Citation1994).
In the InfoSec literature, past conceptualisations of in-role and extra-role security behaviours (Hsu et al., Citation2015) stand out as parallels to the task and contextual forms of behavioural engagement. In-role behaviours, referred to elsewhere as compliance, adhere to the explicit prescriptions of organisational policies governing how technology and information assets are handled and security risks are managed as part of one’s job (Bulgurcu et al., Citation2010; Hsu et al., Citation2015), capturing the task-related facet of engagement. Meanwhile, extra-role volunteering behaviours embody security-related citizenship behaviours that go beyond prescription but nonetheless contribute to the organisational, social, and psychological InfoSec environment (Davis, Citation2013; Hsu et al., Citation2015), capturing the contextual facet of engagement. Given these parallels, security-related behavioural engagement is conceptualised here as a multidimensional construct subsuming two distinct types of security behaviour – in-role compliance and extra-role volunteering.
As it relates to capturing future behaviour, security-related or otherwise, the theory of reasoned action (TRA) (Fishbein & Ajzen, Citation1977) and theory of planned behaviour (TPB) (Ajzen, Citation1991) have emerged as two of the most influential theories on human action. While important differences between them exist, a core argument they share is that intention to perform a behaviour is the primary determinant of actual future behaviour (Ajzen, Citation1991; Fishbein & Ajzen, Citation1977). Consistent with this, prior IS research on end user behaviour has captured and investigated intention to engage in that behaviour.
Applying these theories and past research to the behavioural InfoSec domain, we introduce a new construct labelled InfoSec engagement intention, which captures an end user’s intention to exhibit the range of security behaviours that contribute to organisational InfoSec performance. As a multidimensional construct, InfoSec engagement intention possesses two distinct facets – in-role compliance intention and extra-role volunteering intention – which are distinguished primarily by the extent to which target behaviour is prescribed by the organisation’s ISPs. Further consistent with the literature, InfoSec engagement intention captures intention to enact security behaviours but not the intended consequences of those behaviours (Borman & Motowidlo, Citation1993; Conway, Citation1999; Motowidlo & Van Scotter, Citation1994).
3.2. InfoSec commitment
One way of capturing internalisation is by way of personal commitment (Deci & Ryan, Citation1985). Laying the foundation for contemporary views of personal commitment, social influence theory (Kelman, Citation1958) postulates that changes in attitude about target behaviours occur at different levels – compliance, identification, and internalisation – underpinned by differing targets of psychological attachment (Kelman, Citation1958). Compliance captures change based on the expected attainment of reward or avoidance of punishment, with little-to-no psychological attachment to the content of an induced behaviour. Identification captures change motivated by the establishment or maintenance of a self-defining relationship with someone or something. Finally, internalisation captures change rooted in the incorporation of the values and ideas embedded within a behaviour, into the individual’s value system (Kelman, Citation1958).
Applying these tenets to the workplace context, Meyer and Allen (Citation1991) present three distinct conceptualisations of organisational commitment, distinguished by their underlying motivational processes: 1) continuance commitment, which captures attachment rooted in need to do so (e.g., the perceived costs associated with leaving the organisation); 2) normative commitment, which captures feelings of obligation; and 3) affective commitment, which captures high levels of psychological attachment rooted in identification and internalisation motives (Meyer & Allen, Citation1991). Mapping these three distinct conceptualisations to SDT’s motivational continuum, Meyer et al. (Citation2004) postulate that continuance commitment captures the external regulation end of the motivation continuum, affective commitment captures the internal regulation end, and normative commitment falls somewhere in between (Meyer et al., Citation2004).
Provided the current study’s focus on internal regulation of security behaviour and consistent with the literature, internalisation is captured via affective commitment. While the vast majority of InfoSec-related work involving affective commitment has examined organisational commitment (see Cram et al., Citation2017 for a review), individuals can become psychologically attached to any recognisable entity, abstract concept, or intended outcome of a course of action (Meyer & Allen, Citation1991; Meyer et al., Citation2004). Here, we specify organisational InfoSec performance as the target of commitment and use the term InfoSec commitment to capture a business end user’s feelings of identification with, attachment to, and involvement in organisational InfoSec performance. InfoSec commitment manifests as valuing one’s role in organisational InfoSec, taking personal responsibility for organisational InfoSec performance, and dedication to remaining competent in it.
3.3. Perceived behavioural control
SDT scholars argue that the most impactful psychological need driving internalisation is need for autonomy (Gagné & Deci, Citation2005). An important outcome of autonomy is an established sense of behavioural control (Hagger et al., Citation2006). Among the various constructs capturing a person’s control over computing behaviour, perceived behavioural control (PBC) – the perceived ease or difficulty of performing a specific behaviour, within a specific context (Ajzen, Citation2002) – stands as one of the most validated. Introduced in TPB, “PBC simply denotes subjective degree of control over the behaviour itself” and therefore, to avoid confusion, should be read as “perceived control over performance of a behaviour” (Ajzen, Citation2002, p. 668). Adapted to behavioural InfoSec, PBC captures the end user’s perceived degree of control over his/her InfoSec behaviours and use of security technologies in the organisation (Hu et al., Citation2012). Importantly, perceived control over behaviour and regulation of behaviour are not equivalent concepts. For example, an employee may be internally committed to supporting organisational InfoSec but lack sufficient resources, authority, and/or ability to do so. Given this distinction and in line with SDT, we capture an individual’s fulfilment of need for autonomy in this context via PBC.
3.4. IT competence
Personal competence is a fundamental enabler of internally regulated behaviour (Ryan & Deci, Citation2017). In the IS literature, past research has conceptualised individually-held IT competence as the IT-related knowledge and experience possessed by an individual that enables him or her to contribute to the technical side of the organisation (Davis, Citation2013; Davis et al., Citation2009). Furthermore, IT competence has been consistently described as comprising five distinct domains of knowledge and skill – technology, applications, system development, management of IT, and access to other IT knowledge (Bassellier et al., Citation2001; Davis, Citation2013; Davis et al., Citation2009). Together, these five domains enable an end user to influence the technical side of his/her organisation, including matters related to InfoSec. Thus, we capture fulfilment of the psychological need for competence in this context via self-assessed IT competence.
3.5. User-IS exchange
At the centre of the psychological need for relatedness is the desire for a sense of belonging and affiliation with other individuals and groups (Baumeister & Leary, Citation1995). An employee who feels connected with relevant others in a particular work context is more likely to have his/her need for relatedness fulfilled (Markus & Kitayama, Citation1991), especially when he/she feels free to express work-related and personal troubles (Van Den Broeck et al., Citation2008). In the organisational InfoSec context, the IS department serves as an entity with the potential to fulfil an end user’s need for relatedness. One measure of relationship quality between the user and the IS department is user-IS exchange, which captures the end user’s perceived quality of his/her relationship with the IS department (Davis, Citation2013). Consistent with SDT’s depiction of relatedness, high-quality user-IS exchange is characterised by the IS department’s recognition of the user’s potential to contribute to the technical side of the organisation, the IS department’s willingness to give and receive suggestions for improving IT in the business, and mutual consideration for the interdependence between IT and functional-area work (Davis, Citation2013; Van Den Broeck et al., Citation2008). Given the relevance of the IS department to organisational InfoSec, we capture fulfilment of the end user’s need for relatedness in this context via user-IS exchange.
4. Research model
The research model guiding this study () extends the knowledge base by expanding our understanding of workplace factors that shape internally motivated engagement in organisational InfoSec. Rooted in SDT, PBC, IT competence, and user-IS department exchange are positioned as drivers of InfoSec commitment. InfoSec commitment is in turn positioned as an internal motivational driver of InfoSec engagement intention.
5. Hypothesis development
A committed end user understands and values his/her role in organisational InfoSec performance and as a result, should be more interested in exhibiting the full range of security behaviours that contribute to it. Understanding of organisational InfoSec can take the form of recognising opportunities to behave more securely. It can also take the form of knowing more about specific security techniques and best practices. Meanwhile, valuing one’s role in organisational InfoSec often results in seizing opportunities to act on those values. Because a committed end user is also dedicated to remaining competent in the field, he/she possesses the motivation and ability required to perform security behaviours when opportunities are realised. The knowledge, motivation, and ability that accompany commitment to organisational InfoSec performance should bear direct influence on one’s intention to engage in the various behaviours contributing to that performance. As a result, InfoSec commitment is expected to have a direct positive impact on InfoSec engagement intention.
H1: InfoSec commitment is positively associated with InfoSec engagement intention.
An end user’s sense of control over security behaviour and security technologies in the workplace should promote commitment to organisational InfoSec performance for three important reasons. First, the self-regulation that comes with perceived control can create a stronger sense of ownership of and personal responsibility for InfoSec related outcomes, supporting InfoSec commitment. Second, organisational investments towards empowering and equipping end users with the ability to contribute to organisational InfoSec performance sends a strong signal about its importance to leadership, promoting buy-in. Thirdly, such investments relay important organisational support for the end user in this context which can drive reciprocation in the form of end user behaviours that support the organisation’s InfoSec values and goals (Davis, Citation2013). By instilling a sense of ownership of InfoSec performance and obligation to the organisation, PBC should bear direct positive influence on InfoSec commitment.
H2: Perceived behavioural control is positively associated with InfoSec commitment.
Technical competence underpins the end user’s ability to understand and identify with the technical aspects of organisational performance (Davis et al., Citation2009). As such, an IT competent end user is more likely to recognise the important limitations of technical controls in any effort to protect digital assets and hence, the critical need for robust behavioural InfoSec. In addition, IT competence supports a deeper comprehension of matters related to organisational InfoSec and the severity of specific threats across the landscape. This deeper IT knowledge base should increase appreciation for organisational efforts towards mitigating risk. Additionally, this deeper IT knowledge base should support the end user’s ability to absorb new security knowledge as it comes available, easing the burden of remaining competent over time and hence, committed to organisational InfoSec performance. Given the foundational role IT competence can play in comprehending the value of behavioural InfoSec and remaining sufficiently competent in the field to contribute, it is expected to have a direct positive effect on InfoSec commitment.
H3: IT competence is positively associated with InfoSec commitment.
While the formal charges associated with enterprise InfoSec typically land within the IS department, many aspects – such as behavioural InfoSec – require levels of shared responsibility across the IS-user divide to be effective. In situations like these, where dual ownership and joint accountability drive success, the ability to obtain shared understanding, clear communication, and smooth coordination between IS and user groups is paramount (Davis et al., Citation2009). Clear communication and coordination, especially around points where responsibility passes between technical and behavioural layers of the organisation’s InfoSec architecture, helps the end user comprehend precisely when/how/why responsibility changes hands, reinforcing personal ownership of security. Finally, high-quality exchange can ease tensions that might otherwise occur when new security controls are introduced and change how work is accomplished, often by introducing less convenient approaches. Through these mechanisms, a strong user-IS department relationship can increase the value an end user places on organisational InfoSec and his/her role in it. Thus, user-IS exchange should have a direct positive effect on InfoSec commitment.
H4: User-IS exchange is positively associated with InfoSec commitment.
It is reasonable to expect an end user’s IT-related knowledge and experience to enhance his/her perceived control over security behaviour and usage of the organisation’s security technologies. InfoSec behaviour frequently occurs in the context of technology use. As such, the technical knowledge and skill requirements across the range of ways employees contribute to InfoSec performance are more likely to be satisfied by underlying IT competence, enhancing PBC. Thus, end user IT competence should influence perceived control over security behaviour.
H5: IT Competence is positively associated with perceived behavioural control.
End user IT competence should also bear influence on the quality of exchange between the user and the IS department. IT competence helps establish overlapping knowledge bases and shared mental models with the IS department about organisational InfoSec, which facilitate quality exchange between the different groups. Additionally, IT competence can create a sense of empathy and mutual respect for how one side affects the other’s work in this context (Davis, Citation2013; Davis et al., Citation2009). Empathy and mutual respect set the stage for higher quality exchange between these relational partners; hence, we expect IT competence to have a direct positive influence on User-IS exchange.
H6: IT Competence is positively associated with User-IS Exchange.
5.1. Control variables
In addition to the constructs of interest, several factors that may also influence InfoSec engagement intention were introduced as controls. General security awareness – an employee’s overall knowledge and understanding of potential issues related to information security and their ramifications – has been shown to influence ISP compliance intention (Bulgurcu et al., Citation2010) and as such, was controlled for in the model. Similarly, we controlled for perceived benefits, which is a well-validated external regulator in this context (Bulgurcu et al., Citation2010). Because large organisations are more likely to have well-documented security policies in place and resources dedicated to diffusion and enforcement (Bulgurcu et al., Citation2010; Herath & Rao, Citation2009), organisational size was also controlled for. Finally, to account for possible individual differences we controlled for the demographic variables gender, age, and education.
6. Research method
The survey method was used to test the model. In an effort to establish cumulative tradition and ensure the validity and reliability of the measurement model, pre-existing measurement items were used wherever possible. As necessary, existing scale items were adapted to the InfoSec context. The unit of analysis for this study is the business end user – an individual employee who works in a non-IS/IT job role in an organisation, but uses IT to accomplish work.
6.1. Instrument development
Scale items were refined with the help of multiple IS faculty members who were well-versed in social science research and the survey methodology. Each construct was measured based on a seven-point Likert scale anchored by 1 (strongly disagree) and 7 (strongly agree). Consistent with prior work on hierarchical latent variable modelling, InfoSec engagement intention was modelled as reflective-formative in nature (Becker et al., Citation2012). More specifically, in-role compliance intention and extra-role volunteering intention were modelled as formative dimensions of the higher-order InfoSec engagement intention construct; meanwhile, in-role compliance intention and extra-role volunteering intention were modelled as reflective constructs (Becker et al., Citation2012). In addition, consistent with prior research (Davis, Citation2013; Davis et al., Citation2009), IT competence was modelled as formative in nature. All other constructs in the model were framed as single-order reflective constructs.
In-role compliance intention was measured using a three-item scale borrowed from Bulgurcu et al. (Citation2010). Extra-role volunteering intention was captured using a three-item scale adapted from Griffin and Neal (Citation2000). A four-item scale adapted from Hofmann and Morgeson (Citation1999) was used to measure InfoSec commitment. Perceived behavioural control was measured via a three-item scale adapted from Hu et al. (Citation2012). To capture IT competence, the five-item scale introduced by Davis et al. (Citation2009) was used. Finally, user-IS exchange was measured via a six-item scale borrowed from Davis (Citation2013). The control variables perceived benefits and InfoSec awareness were measured using scales from Bulgurcu et al. (Citation2010), while all of the demographic control variables were measured using single items. Appendix B presents all of the scales with their measurement items.
6.2. Data collection approach
Consistent with prior IS research (Bulgurcu et al., Citation2010; Posey et al., Citation2015), the data for this study was collected using a survey panel requisitioned by a panel provider (Qualtrics). Participants targeted by the service provider were employees with non-IS/IT job roles, in U.S. based companies with more than 100 employees. A sample of 2,000 panel members received an email with a link to participate in the online survey in return for rewards points. Participants’ identities were kept confidential by the panel provider. To further ensure the validity of the results, initial survey questions captured organisation size and the nature of the participant’s job, and were used to eliminate observations not meeting the target criteria. Participants were not aware that these questions would be used as exclusion criteria. A total of 1,481 invited participants (74.1%) responded. Of them, 1,092 were allowed to proceed. After removing an additional 118 incomplete responses, 993 complete and usable responses () remained, for an effective response rate of 49.7%. Appendix C provides the exclusion criteria and the flow of the participants throughout the survey.
Table 1. Respondents’ profiles.
7. Data analysis
The research model was tested using Partial Least Squares (PLS-SEM) estimation as implemented in the software package SmartPLS version 3.2.7 (Ringle et al., Citation2015). PLS-SEM is a component-based approach to structural equation modelling which is recommended when testing a theoretical framework from a prediction perspective (Hair et al., Citation2019). It is also a recommended approach when the path model includes one or more formative constructs (Hair et al., Citation2019). Because InfoSec engagement intention was modelled as a second-order reflective-formative latent variable, we employed PLS’s repeated indicator approach with Mode B (formative specification) for higher-order repeated indicators, along with the path weighting scheme as outlined by Becker et al. (Citation2012). Means and standard deviations for each of the constructs in the model are provided in .
Table 2. Reliability analysis of reflective measures.
7.1. Measurement model assessment
The psychometric properties of all reflective constructs in the model were assessed using measures of internal consistency reliability, convergent validity, and discriminant validity. As illustrated in , Cronbach’s alpha and composite reliability scores for all the constructs were above 0.7, indicating good reliability of the measures. Meanwhile, each measurement item loaded significantly on its intended construct with a value greater than 0.7 (Appendix D) and all average variance extracted (AVE) values () were higher than 0.5, demonstrating satisfactory convergent validity (Fornell & Larcker, Citation1981). Additionally, each item loaded higher on its intended construct than any other construct in the model (Appendix D) and each inter-construct correlation () was lower than the value of the corresponding square root of the AVE (diagonal value), indicating good discriminant validity (Fornell & Larcker, Citation1981).
Table 3. Validity analysis of reflective measures.
The psychometric properties of the formative constructs were assessed following the validation steps recommended by Petter et al. (Citation2007). As shown in , the weights of both dimensions of InfoSec engagement intention – in-role compliance intention and extra-role volunteering intention – were significant with VIF values below the recommended cut-off of 3.3 (Petter et al., Citation2007). Meanwhile, all but two items forming the IT competence construct had significant weights. Non-significant item weights were tied to items capturing knowledge and experience regarding the different software applications used in the organisation as well as the vision, goal setting, resource allocation, and performance monitoring regarding IT in the organisation. While non-significant in this study, prior work validating the IT competence construct (Davis, Citation2013; Davis et al., Citation2009) indicates these items are essential to content validity and so were kept in the model. VIF values for the IT competence items () ranged from 1.57 to 2.75, indicating multicollinearity is not a problem.
Table 4. Reliability and validity analysis for formative measures.
7.2. Testing for common method variance
To rule out potential effects of common method variance (CMV), Harman’s one-factor test was conducted on the reflective constructs in the model. Six factors emerged from testing, with no factor explaining more than 36.7 percent of the variance, suggesting CMV is not a problem. Additional CMV testing was conducted using the PLS approach as outlined by Liang et al. (Citation2007). The results (Appendix E) indicated average substantively explained variance of the indicators (73.7%) is much larger than the average method-based variance (0.3%), allowing us to conclude that CMV is unlikely to be a serious concern (Liang et al., Citation2007).
7.3. Structural model results
Structural model assessment was accomplished using standardised path coefficients and variance explained in the dependent constructs, as derived from a bootstrapping procedure employing 1,000 subsamples.
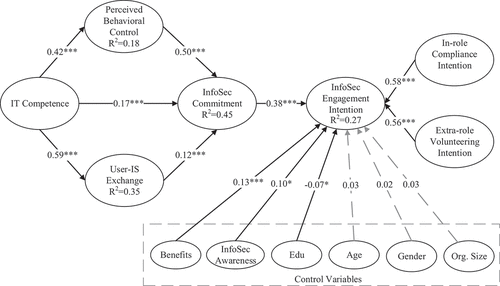
Overall, the results of model testing () strongly support all the hypotheses. InfoSec commitment (β = 0.38; p< 0.001) significantly predicted InfoSec engagement intention, supporting hypothesis H1. Perceived control (β = 0.50; p < 0.001), IT competence (β = 0.17; p< 0.001), and user IS-exchange (β = 0.12; p< 0.001) significantly predicted InfoSec commitment, supporting hypotheses H2, H3, and H4 respectively. Additionally, hypotheses H5 and H6 regarding IT competence’s influence on PBC (β = 0.42; p< 0.001) and user-IS exchange (β = 0.59; p< 0.001), were supported. Among the control variables, perceived benefits (β = 0.13; p < 0.001) and InfoSec awareness (β = 0.10; p < 0.05) had significant positive effects, while education (β = −0.07; p < 0.05) had a marginal negative effect, on InfoSec engagement intention. summarises the results of hypothesis testing.
Table 5. Hypothesis testing results.
8. Discussion and implications
Employee behaviour is fundamental to corporate InfoSec capabilities across the phases of prevention, detection, and response (Baskerville et al., Citation2014). Unfortunately, despite more than a decade of research on the human side of organisational InfoSec, people are often still identified as the weakest link, rooted in disinterest in security threats and the behaviours that mitigate them (Johnston et al., Citation2019). Motivated by this disconnect, the current study extends the knowledge base by uncovering workplace factors that drive internalised commitment to organisational InfoSec performance and resultant behavioural outcomes.
Overall, the findings shed new light on the motivational mechanisms underpinning end user engagement in organisational InfoSec. Specifically, PBC, IT competence, and user-IS exchange were found to drive personal commitment to organisational InfoSec performance by fulfiling critical psychological needs that promote internalisation of organisational InfoSec goals. Commitment in turn internally drives engagement intention. Supporting the theoretical tenets of SDT, the results demonstrate that need for autonomy, as captured by perceived control over security behaviour, bears the most influence on this process. Extending SDT, the current study provides support for the possible existence of relationships between psychological needs. Specifically, we found evidence that fulfilment of the psychological need for competence, as captured by self-assessed IT competence, bears influence on fulfilment of needs for autonomy and relatedness in the InfoSec context. While the influence of IT competence on user-IS exchange has been validated in the past, our finding of IT competence’s impact on PBC validates another benefit of building the general IT competence of individual end users. Overall, these findings expand our understanding of psychological underpinnings of security behaviour, responding to past calls (Posey et al., Citation2015, Citation2013).
In addition, as has also been called for in prior research (Posey et al., Citation2015, Citation2013), this study contributes a new theory-grounded construct to the behavioural InfoSec literature labelled InfoSec engagement intention, which captures the superset of InfoSec behaviours. Recognising that the knowledge created from research on isolated behaviours or behaviour subsets may not generalise to the grand structure of security behaviour (Posey et al., Citation2013), we present security behaviour as a holistic construct subsuming in-role compliance and extra-role volunteering. While future studies on isolated behaviours are certainly appropriate, our results indicate that future work should also consider more aggregate perspectives of security behaviour in the overarching effort to enhance organisational InfoSec.
For practitioners, the findings point to three specific targets for enhancing InfoSec engagement through cultivating commitment to organisational InfoSec performance. First and foremost, the results suggest that managers identify opportunities to support employee control over security behaviour, rather than force it. As such, this study lends empirical support for past recommendations in the practitioner literature, that organisations simplify regulatory approaches to behavioural InfoSec and instead focus on enablement and support (Van Horenbeeck, Citation2017). The results also suggest professional development efforts geared towards building the general IT competence of end users can have important downstream behavioural impacts, including internal regulation of security behaviour and enhanced engagement. Furthermore, the results demonstrate the value of nurturing relationships between the IS department and individuals within the user base, which creates an environment that can engender commitment and ultimately enhance the organisation’s InfoSec posture. As such, they provide empirical support for prior suggestions that companies work to improve the relationship between end users and the IS department as part of broader efforts to improve end user security (Van Horenbeeck, Citation2017).
A final practical implication of this study is that managers should take more comprehensive approaches to managing the human side of corporate InfoSec. By providing a more holistic conceptualisation of the grand structure of security behaviour, this study lays the groundwork for better evaluating the security posture of individual end users. With a rapidly changing threat landscape, managers should extend beyond the ISP creation/diffusion/compliance approach to managing the threat landscape and also target user engagement in activities that support the organisational, social, and psychological environment related to information security.
9. Limitations and future research
Certain limitations should be considered when interpreting this study’s results. For one, this study was cross-sectional in nature. While the model is theory-grounded, reciprocal relationships may exist between certain factors in the model, such as IT competence and user-IS exchange. Future research should take a longitudinal approach to examining the relationships between these factors. In addition, all of the variables were measured using single informants. While rigorous testing for CMV indicated no serious problems with method variance, certain constructs in the model may be better captured using other informants. A final limitation to consider when interpreting the results is the use of intention as a surrogate for actual engagement. Although theoretically justified, the results should be interpreted with caution. Future research could measure actual engagement using a matched-pair approach to model testing that includes third-party (e.g., immediate supervisor) evaluations of InfoSec engagement.
10. Conclusion
The current study extends the IS research by shedding new light on the psychological processes influencing behavioural InfoSec within the user base and the workplace factors influencing those processes. Overall, the results present new perspectives on motivating security behaviour that emphasise internalised commitment over extrinsic manipulation and provide broader perspectives on user security behaviour than has been in the past. In doing so, this study paves the way for future research that further explores the intrinsic motivational underpinnings of behavioural InfoSec across the enterprise.
Disclosure of potential conflicts of interest
No potential conflict of interest was reported by the author(s).
Supplemental Material
Download MS Word (58.1 KB)Supplementary material
Supplemental data for this article can be accessed here.
References
- Ajzen, I. (1991). The theory of planned behavior. Organizational Behavior and Human Decision Processes, 50(2), 179–211. https://doi.org/10.1016/0749-5978(91)90020-T
- Ajzen, I. (2002). Perceived behavioral control, self‐efficacy, locus of control, and the theory of planned behavior. Journal of Applied Social Psychology, 32(4), 665–683. https://doi.org/10.1111/j.1559-1816.2002.tb00236.x
- Balozian, P., Leidner, D., & Warkentin, M. (2019). Managers’ and employees’ differing responses to security approaches. Journal of Computer Information Systems, 59(3), 197–210. https://doi.org/10.1080/08874417.2017.1318687
- Baskerville, R., Spagnoletti, P., & Kim, J. (2014). Incident-Centered information security: Managing a strategic balance between prevention and response. Information & Management, 51(1), 138–151. https://doi.org/10.1016/j.im.2013.11.004
- Bassellier, G., Reich, B. H., & Benbasat, I. (2001). Information Technology competence of business managers: A definition and research model. Journal of Management Information Systems, 17(4), 159–182. https://doi.org/10.1080/07421222.2001.11045660
- Baumeister, R. F., & Leary, M. R. (1995). The need to belong: Desire for interpersonal attachments as a fundamental human motivation. Psychological Bulletin, 117(3), 497. https://doi.org/10.1037/0033-2909.117.3.497
- Becker, J.-M., Klein, K., & Wetzels, M. (2012). Hierarchical latent variable models in PLS-SEM: Guidelines for using reflective-formative type models. Long Range Planning, 45(5–6), 359–394. https://doi.org/10.1016/j.lrp.2012.10.001
- Borman, W. C., & Motowidlo, S. (1993). Expanding the criterion domain to include elements of contextual performance. Jossey-Bass.
- Bulgurcu, B., Cavusoglu, H., & Benbasat, I. (2010). Information security policy compliance: An empirical study of rationality-based beliefs and information security awareness. MIS Quarterly, 34(3), 523–548. https://doi.org/10.2307/25750690
- Conway, J. M. (1999). Distinguishing contextual performance from task performance for managerial jobs. Journal of Applied Psychology, 84(1), 3. https://doi.org/10.1037/0021-9010.84.1.3
- Cram, W. A., Proudfoot, J. G., & D’arcy, J. (2017). Organizational information security policies: a review and research framework. European Journal of Information Systems,26(6), 605–641. https://doi.org/10.1057/s41303-017-0059–9
- Davis, J. M. (2013). Leveraging the IT competence of non-IS workers: Social exchange and the good corporate citizen. European Journal of Information Systems, 22(4), 403–415. https://doi.org/10.1057/ejis.2012.36
- Davis, J. M., Kettinger, W. J., & Kunev, D. G. (2009). When users are IT experts too: The effects of joint IT competence and partnership on satisfaction with enterprise-level systems implementation. European Journal of Information Systems, 18(1), 26–37. https://doi.org/10.1057/ejis.2009.4
- De Vos, S., Crouch, R., Quester, P., & Ilicic, J. (2017). Examining the effectiveness of fear appeals in prompting help‐seeking: The case of at‐risk gamblers. Psychology & Marketing, 34(6), 648–660. https://doi.org/10.1002/mar.21012
- Deci, E. L., & Ryan, R. M. (1985). The general causality orientations scale: Self-determination in personality. Journal of Research in Personality, 19(2), 109–134. https://doi.org/10.1016/0092-6566(85)90023-6
- Fishbein, M., & Ajzen, I. (1977). Belief, attitude, intention, and behavior: An introduction to theory and research. Addison-Wesley.
- Fornell, C., & Larcker, D. F. (1981). Structural equation models with unobservable variables and measurement error: Algebra and statistics. Journal of Marketing Research, 18(3), 382–388. https://doi.org/10.2307/3150980
- Gagné, M., & Deci, E. L. (2005). Self‐determination theory and work motivation. Journal of Organizational Behavior, 26(4), 331–362. https://doi.org/10.1002/job.322
- Griffin, M. A., & Neal, A. (2000). Perceptions of safety at work: A framework for linking safety climate to safety performance, knowledge, and motivation. Journal of Occupational Health Psychology, 5(3), 347. https://doi.org/10.1037/1076-8998.5.3.347
- Hagger, M. S., Chatzisarantis, N. L., & Harris, J. (2006). From psychological need satisfaction to intentional behavior: Testing a motivational sequence in two behavioral contexts. Personality and Social Psychology Bulletin, 32(2), 131–148. https://doi.org/10.1177/0146167205279905
- Hair, J. F., Risher, J. J., Sarstedt, M., & Ringle, C. M. (2019). When to use and how to report the results of PLS-SEM. European Business Review, 31(1), 2–24. https://doi.org/10.1108/EBR-11-2018-0203
- Han, J., Kim, Y. J., & Kim, H. (2017). An integrative model of information security policy compliance with psychological contract: Examining a bilateral perspective. Computers & Security, 66(1), 52–65. https://doi.org/10.1016/j.cose.2016.12.016
- Herath, T., & Rao, H. R. (2009). Protection motivation and deterrence: A framework for security policy compliance in organisations. European Journal of Information Systems, 18(2), 106–125. https://doi.org/10.1057/ejis.2009.6
- Hofmann, D. A., & Morgeson, F. P. (1999). Safety-related behavior as a social exchange: The role of perceived organizational support and leader–member exchange. Journal of Applied Psychology, 84(2), 286. https://doi.org/10.1037/0021-9010.84.2.286
- Hsu, J. S.-C., Shih, S.-P., Hung, Y. W., & Lowry, P. B. (2015). The role of extra-role behaviors and social controls in information security policy effectiveness. Information Systems Research, 26(2), 282–300. https://doi.org/10.1287/isre.2015.0569
- Hu, Q., Dinev, T., Hart, P., & Cooke, D. (2012). Managing employee compliance with information security policies: The critical role of top management and organizational culture. Decision Sciences, 43(4), 615–660. https://doi.org/10.1111/j.1540-5915.2012.00361.x
- Johnston, A. C., & Warkentin, M. (2010). Fear appeals and information security behaviors: An empirical study. MIS Quarterly, 34(3), 549–566. https://doi.org/10.2307/25750691
- Johnston, A. C., Warkentin, M., Dennis, A. R., & Siponen, M. (2019). Speak their language: Designing effective messages to improve employees’ information security decision making. Decision Sciences, 50(2), 245–284. https://doi.org/10.1111/deci.12328
- Johnston, A. C., Warkentin, M., & Siponen, M. (2015). An enhanced fear appeal rhetorical framework: Leveraging threats to the human asset through sanctioning rhetoric. MIS Quarterly, 39(1), 113–134. https://doi.org/10.25300/MISQ/2015/39.1.06
- Kahn, W. A. (1990). Psychological conditions of personal engagement and disengagement at work. Academy of Management Journal, 33(4), 692–724. https://doi.org/10.5465/256287
- Kaspersky. (2017). The human factor in IT security. https://media.kasperskycontenthub.com/wp-content/uploads/sites/100/2017/11/10083900/20170710_Report_Human-Factor-In-ITSec_eng_final.pdf
- Kelman, H. C. (1958). Compliance, identification, and internalization: Three processes of attitude change. Journal of Conflict Resolution, 2(1), 51–60. https://doi.org/10.1177/002200275800200106
- Kettinger, W. J., Li, Y., Davis, J. M., & Kettinger, L. (2015). The roles of psychological climate, information management capabilities, and IT support on knowledge-sharing: An MOA perspective. European Journal of Information Systems, 24(1), 59–75. https://doi.org/10.1057/ejis.2013.25
- Kohn, A. (1993). Why incentive plans cannot work. Harvard Business Review, 71(5), 54–60.
- Lepper, M. R., & Greene, D. (2015). The hidden costs of reward: New perspectives on the psychology of human motivation. Psychology Press.
- Liang, H., Saraf, N., & Xue, Y. (2007). Assimilation of enterprise systems: The effect of institutional pressures and the mediating role of top management. MIS Quarterly, 31(1), 59–87. https://doi.org/10.2307/25148781
- Lowry, P. B., & Moody, G. D. (2015). Proposing the control‐reactance compliance model (CRCM) to explain opposing motivations to comply with organisational information security policies. Information Systems Journal, 25(5), 433–463. https://doi.org/10.1111/isj.12043
- Macey, W. H., & Schneider, B. (2008). The meaning of employee engagement. Industrial and Organizational Psychology, 1(1), 3–30. https://doi.org/10.1111/j.1754-9434.2007.0002.x
- Markus, H. R., & Kitayama, S. (1991). Culture and the self: Implications for cognition, emotion, and motivation. Psychological Review, 98(2), 224–253. https://doi.org/10.1037/0033-295X.98.2.224
- Menard, P., Bott, G. J., & Crossler, R. E. (2017). User motivations in protecting information security: Protection motivation theory versus self-determination theory. Journal of Management Information Systems, 34(4), 1203–1230. https://doi.org/10.1080/07421222.2017.1394083
- Meyer, J. P., & Allen, N. J. (1991). A three-component conceptualization of organizational commitment. Human Resource Management Review, 1(1), 61–89. https://doi.org/10.1016/1053-4822(91)90011-Z
- Meyer, J. P., Becker, T. E., & Vandenberghe, C. (2004). Employee commitment and motivation: A conceptual analysis and integrative model. Journal of Applied Psychology, 89(6), 991–1007. https://doi.org/10.1037/0021-9010.89.6.991
- Motowidlo, S. J., & Van Scotter, J. R. (1994). Evidence that task performance should be distinguished from contextual performance. Journal of Applied Psychology, 79(4), 475–480. https://doi.org/10.1037/0021-9010.79.4.475
- Petter, S., Straub, D. W., & Rai, A. (2007). Specifying formative constructs in information systems research. MIS Quarterly, 31(4), 623–656. https://doi.org/10.2307/25148814
- Posey, C., Roberts, T. L., & Lowry, P. B. (2015). The impact of organizational commitment on insiders’ motivation to protect organizational information assets. Journal of Management Information Systems, 32(4), 179–214. https://doi.org/10.1080/07421222.2015.1138374
- Posey, C., Roberts, T. L., Lowry, P. B., Bennett, R. J., & Courtney, J. F. (2013). Insiders’ protection of organizational information assets: Development of a systematics-based taxonomy and theory of diversity for protection-motivated behaviors. MIS Quarterly, 37(4), 1189–1210. https://doi.org/10.25300/MISQ/2013/37.4.09
- Ringle, Christian M., Wende, Sven, & Becker, Jan-Michael. (2015). SmartPLS 3. Bönningstedt: SmartPLS. Retrieved from http://www.smartpls.com
- Ryan, R. M., & Deci, E. L. (2017). Self-determination theory: Basic psychological needs in motivation, development, and wellness. Guilford Publications.
- Van Den Broeck, A., Vansteenkiste, M., De Witte, H., & Lens, W. (2008). Explaining the relationships between job characteristics, burnout, and engagement: The role of basic psychological need satisfaction. Work & Stress, 22(3), 277–294. https://doi.org/10.1080/02678370802393672
- Van Horenbeeck, M. (2017). The key to better cybersecurity: Keep employee rules simple. Harvard Business Review. Retrieved May 13, 2020, from.https://hbr.org/2017/11/the-key-to-better-cybersecurity-keep-employee-rules-simple
- Wright, R. T., Jensen, M. L., Thatcher, J. B., Dinger, M., & Marett, K. (2014). Influence techniques in phishing attacks: An examination of vulnerability and resistance. Information Systems Research, 25(2), 385–400. https://doi.org/10.1287/isre.2014.0522
- Xu, J., & Cooper Thomas, H. (2011). How can leaders achieve high employee engagement? Leadership & Organization Development Journal, 32(4), 399–416. https://doi.org/10.1108/01437731111134661